容器技术之Docker网络
上一篇博客我们主要聊了下docker镜像相关的说明以及怎样基于现有镜像制作镜像、分发镜像到docker仓库中的相关测试;回顾请参考https://www.cnblogs.com/qiuhom-1874/p/12941508.html;今天我们来聊一聊docker的网络相关说明;
在使用vm虚拟机时,我们知道一个虚拟机可以有三种虚拟网络接口,第一种网络是桥接网络,第二种是NAT网络,第三种是仅主机网络;这三种虚拟网络接口后面对应的都是一个个不同的虚拟网络;我们要想让虚拟机在那个网络中工作就把对应接口更换成那个接口即可;相对于docker来讲,docker内部也有三种虚拟网络接口,它们分别是bridge,host,none这三种;bridge是docker容器默认的网络类型,启动容器不指定网络时默认是bridge,该网络类型是桥接到宿主机的docker0桥上的,而docker0桥上一个NAT桥;host在docker里不是仅主机网络类型,它这里的意思是共享宿主机网络,即同宿主机共享同一网络名称空间;none表示空网络类型,在docker的网络中表现形式就是我们启动容器指定网络类型为none,在容器内部除了lo接口就没有别的其他网络接口,这意味着该容器网络只能自己和自己通信,有点类似vm里的仅主机网络;其实除了以上三种网络,docker也支持自定义网络;自定义网络就是可以创建网络名称空间,docker支持的网络类型有bridge host ipvlan macvlan null overlay;
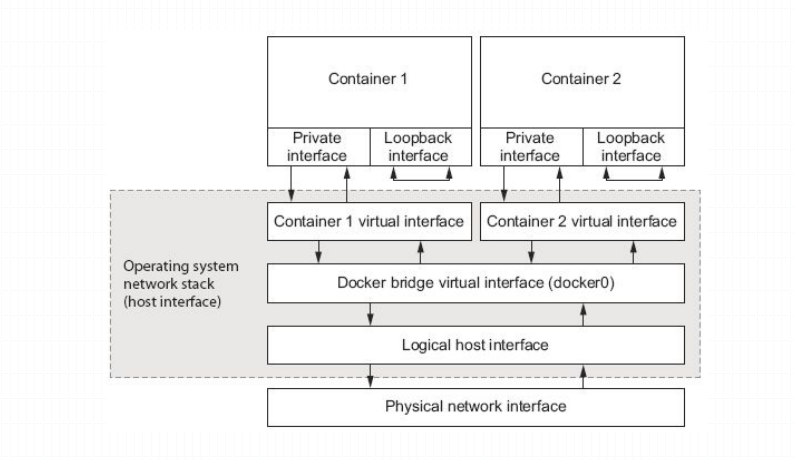
提示:以上这张图描述了两个容器的网络。默认情况下启动docker容器都是bridge网络,桥接到docker0桥;对于docker容器来讲,各个容器之间的网络上相互隔离的;相互隔离就表示在第一个容器里监听某个端口,对于第二个容器是不可见的;对于宿主机来讲,两个容器的网络都是共享docker0桥的网络;同时在宿主机上的网络名称空间中是可以看到两个容器的虚拟接口是连接到docker0桥的;所以默认情况启动的容器相互之间是可以基于docker0来通信;我们可以把docker0桥理解成连接两个容器的交换机;
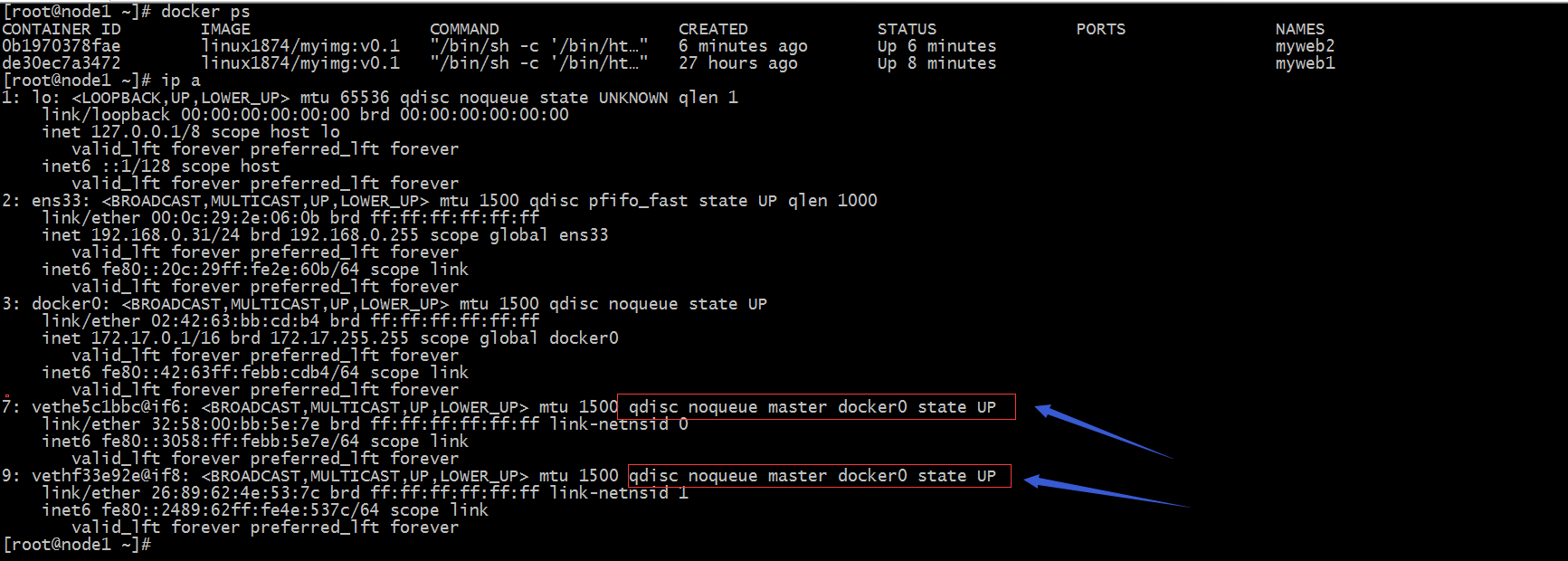
提示:可以看到宿主机上跑了两个容器,他们的虚拟网络接口都是链在docker0桥的;所以这两个容器是可以相互通信的;但是对于宿主机以外的主机,他俩是不可见;宿主机以外的主机上没法和这两个容器通信的,原因是docker是一个nat桥;如下所示
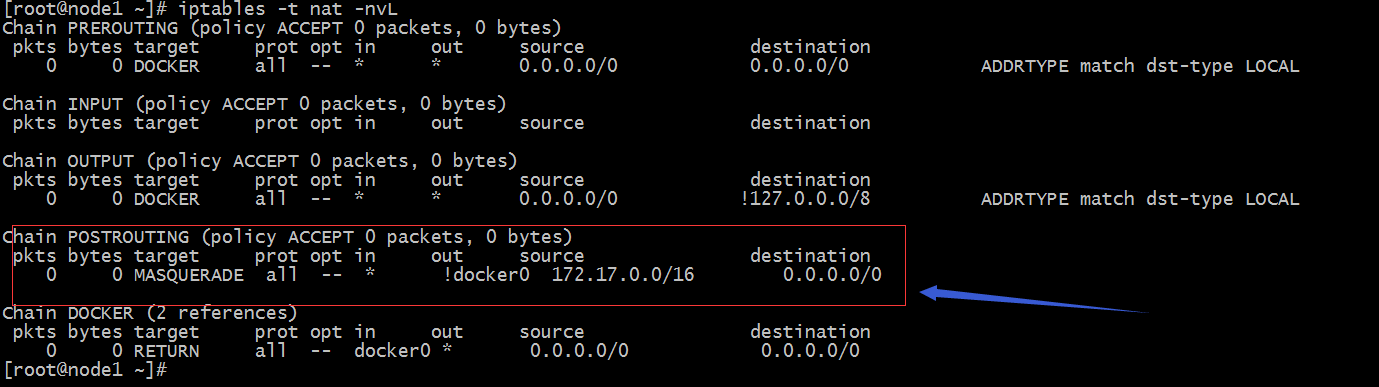
提示:以上规则表示源地址为172.17.0.0/16并且不从docker0桥出去的报文,在通过POSTROUTING链时会做地址伪装(SNAT);从上面的信息我们就可以确定docker0桥就是一个nat桥;
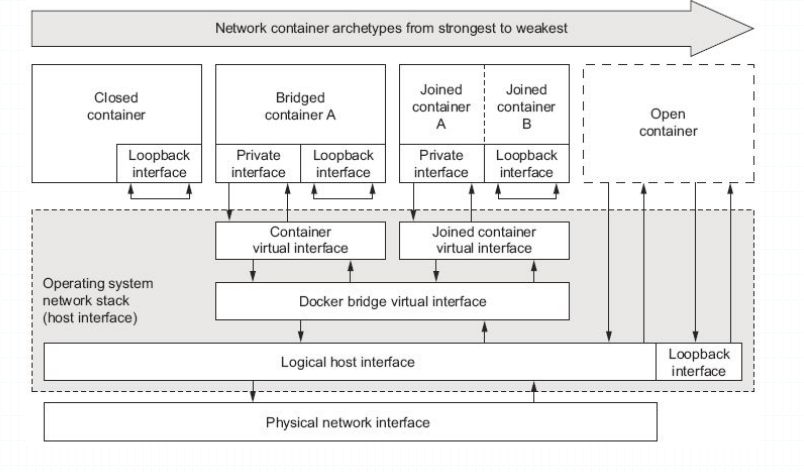
提示:以上图片展示了docker的三种网络,closed container这个容器只有一个lo接口,和其他容器相互隔离,只能自己和自己通信;bridged container这种桥接式网络容器,通常都会有两个接口,一个lo回环接口,一个连接至宿主机上的docker0桥的以太网接口;docker daemon 启动时默认会创建一个名为docker0的网络桥,并且创建的容器为桥接式容器(就是创建的容器的网络桥接至docker0上的)用docker运行容器时我们可以使用--net或--network来指定容器的网络,默认是--net bridage;docker0桥上一个nat桥,因此,桥接式容器可以通过自己的桥接口访问到外部网络,但是防火墙规则组织了一切从外部网络访问桥接式容器的请求;对于open container来讲其实就是共享宿主机的网络名称空间,相当于在网络这层资源上不和宿主机隔离;joined container 我们理解为联盟式网络容器;该容器的网络资源是链接到其他容器的网络资源;本质上就是多个容器共享一个网络空间;
示例:bridge网络的容器创建
[root@node1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
[root@node1 ~]# docker run --name web1 -d --net bridge linux1874/myimg:v0.1
bced86e3dcb2e8144ade7cfc5b8c0dcfb5ee0af5e9d729904c7eb971d9c1117f
[root@node1 ~]# docker run --name web2 -d --net bridge linux1874/myimg:v0.1
d39dea20d5ea0b52c42c67a8a9a36dcbc2ef78d654dfb9e1d88013306f2f5a50
[root@node1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
d39dea20d5ea linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 6 seconds ago Up 5 seconds web2
bced86e3dcb2 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 11 seconds ago Up 11 seconds web1
[root@node1 ~]# docker container inspect myweb1 -f {{.NetworkSettings.Networks.bridge.NetworkID}} Error: No such container: myweb1
[root@node1 ~]# docker container inspect web1 -f {{.NetworkSettings.Networks.bridge.NetworkID}}
2ae9aa6566561e8f1f5c98f4877b34b29a14ed8dd645933926b0615e9e0b2567
[root@node1 ~]# docker container inspect web2 -f {{.NetworkSettings.Networks.bridge.NetworkID}}
2ae9aa6566561e8f1f5c98f4877b34b29a14ed8dd645933926b0615e9e0b2567
[root@node1 ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
2ae9aa656656 bridge bridge local
93347fb33d89 host host local
a99b876eee4d none null local
[root@node1 ~]# docker container exec web1 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
10: eth0@if11: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
[root@node1 ~]# docker container exec web2 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
12: eth0@if13: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:ac:11:00:03 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.3/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
[root@node1 ~]# docker container exec web2 wget -O - -q 172.17.0.2
this test file
[root@node1 ~]# docker container exec web1 wget -O - -q 172.17.0.3
this test file
提示:桥接式网络的容器间是可以通过docker0桥来通信;我们可以理解为同一桥上的网络为一个网络,他们的网络ID都是相同;上面两个容器的网络ID都是bridge的ID;
示例:none网络容器的创建
[root@node1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
d39dea20d5ea linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 8 minutes ago Up 8 minutes web2
bced86e3dcb2 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 9 minutes ago Up 9 minutes web1
[root@node1 ~]# docker run --name web3 -d --net none linux1874/myimg:v0.1
a0039645d551ef7089d7ff0e588864da48c68a0b301e28728e48d0b520a006ba
[root@node1 ~]# docker container inspect web3 -f {{.NetworkSettings.Networks.none.NetworkID}}
a99b876eee4d028f6d6410749ac863915711482e6f55aaf38071aabaae53ee2e
[root@node1 ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
2ae9aa656656 bridge bridge local
93347fb33d89 host host local
a99b876eee4d none null local
[root@node1 ~]# docker container exec web3 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
[root@node1 ~]#
提示:可以看到none网络的容器网络ID是none的网络ID相同,内部也只有一个lo接口;
示例:共享式网络容器的创建
[root@node1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
a0039645d551 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 2 minutes ago Up 2 minutes web3
d39dea20d5ea linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 12 minutes ago Up 12 minutes web2
bced86e3dcb2 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 12 minutes ago Up 12 minutes web1
[root@node1 ~]# docker run --name web4 -d --net host linux1874/myimg:v0.1
f2dc3d0bb6992b6f0f93b3db50d952574c45473911a7133b735ae1b633855962
[root@node1 ~]# docker container inspect web4 -f {{.NetworkSettings.Networks.host.NetworkID}}
93347fb33d89a5abd7781ab1a01b51ad46dde4b2409b88d3d5f2e4a7bd0aed2e
[root@node1 ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
2ae9aa656656 bridge bridge local
93347fb33d89 host host local
a99b876eee4d none null local
[root@node1 ~]# docker container exec ip a
Error: No such container: ip
[root@node1 ~]# docker container exec web4 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast qlen 1000
link/ether 00:0c:29:2e:06:0b brd ff:ff:ff:ff:ff:ff
inet 192.168.0.31/24 brd 192.168.0.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe2e:60b/64 scope link
valid_lft forever preferred_lft forever
3: docker0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue
link/ether 02:42:63:bb:cd:b4 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
inet6 fe80::42:63ff:febb:cdb4/64 scope link
valid_lft forever preferred_lft forever
11: vethffac5a0@if10: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue master docker0
link/ether 82:b0:23:49:92:de brd ff:ff:ff:ff:ff:ff
inet6 fe80::80b0:23ff:fe49:92de/64 scope link
valid_lft forever preferred_lft forever
13: veth9e7a8c4@if12: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue master docker0
link/ether a6:d3:a2:c9:9f:45 brd ff:ff:ff:ff:ff:ff
inet6 fe80::a4d3:a2ff:fec9:9f45/64 scope link
valid_lft forever preferred_lft forever
[root@node1 ~]# docker container exec web4 hostname
node1
[root@node1 ~]# hostname
node1
[root@node1 ~]#
提示:host网络是共享宿主机的网络名称空间,所以我们在容器内部看到的网络接口同宿主机上的网络接口一样;
示例:联盟式网络容器创建
[root@node1 ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
linux1874/myimg v0.1 e408b1c6e04f 29 hours ago 1.22MB
busybox latest 78096d0a5478 10 days ago 1.22MB
centos 7 b5b4d78bc90c 2 weeks ago 203MB
nginx stable-alpine ab94f84cc474 4 weeks ago 21.3MB
[root@node1 ~]# docker run --name b1 --net container:web4 -it busybox
/ # [root@node1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
2b7517adb2ad busybox "sh" 13 seconds ago Up 13 seconds b1
f2dc3d0bb699 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 22 minutes ago Up 22 minutes web4
a0039645d551 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 27 minutes ago Up 27 minutes web3
d39dea20d5ea linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 36 minutes ago Up 36 minutes web2
bced86e3dcb2 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 36 minutes ago Up 36 minutes web1
[root@node1 ~]# docker container exec b1 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast qlen 1000
link/ether 00:0c:29:2e:06:0b brd ff:ff:ff:ff:ff:ff
inet 192.168.0.31/24 brd 192.168.0.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe2e:60b/64 scope link
valid_lft forever preferred_lft forever
3: docker0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue
link/ether 02:42:63:bb:cd:b4 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
inet6 fe80::42:63ff:febb:cdb4/64 scope link
valid_lft forever preferred_lft forever
11: vethffac5a0@if10: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue master docker0
link/ether 82:b0:23:49:92:de brd ff:ff:ff:ff:ff:ff
inet6 fe80::80b0:23ff:fe49:92de/64 scope link
valid_lft forever preferred_lft forever
13: veth9e7a8c4@if12: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue master docker0
link/ether a6:d3:a2:c9:9f:45 brd ff:ff:ff:ff:ff:ff
inet6 fe80::a4d3:a2ff:fec9:9f45/64 scope link
valid_lft forever preferred_lft forever
提示:运行bubybox容器要注意容器前台跑什么程序,如果前台没有跑程序,容器一启动就会处于退出状态;我上面是先交互式运行/bin/sh,然后在用ctrl+p松开,然后再按ctrl+q两个组合键来剥离当前终端,使得b1容器运行起来;从上面的信息来看,我们把b1容器的网络加入到web4容器的网络,b1和web4就都处于同一网络名称空间;web4是共享宿主机网络名称空间,所以b1的网络里也是能够看到宿主机上的网络接口的;
[root@node1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
2b7517adb2ad busybox "sh" 15 minutes ago Up 15 minutes b1
f2dc3d0bb699 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 38 minutes ago Up 38 minutes web4
a0039645d551 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 42 minutes ago Up 42 minutes web3
d39dea20d5ea linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 52 minutes ago Up 52 minutes web2
bced86e3dcb2 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 52 minutes ago Up 52 minutes web1
[root@node1 ~]# ss -tnl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 9 :::80 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
[root@node1 ~]# docker attach b1
/ # netstat -tnl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN
tcp 0 0 :::80 :::* LISTEN
tcp 0 0 :::22 :::* LISTEN
tcp 0 0 ::1:25 :::* LISTEN
/ # read escape sequence
[root@node1 ~]# docker container exec -it web4 /bin/sh
/ # netstat -ntl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN
tcp 0 0 :::80 :::* LISTEN
tcp 0 0 :::22 :::* LISTEN
tcp 0 0 ::1:25 :::* LISTEN
/ # exit
[root@node1 ~]#
提示:b1和web4和宿主机都处于同一网络名称空间,在web4上监听的80,在宿主机和b1上是能够看到的,同时宿主机上监听的其他端口,在b1和web4上也能够看到;进入剥离的终端容器,需要用docker attach 命令进入;这样一来我们就可以通过访问宿主机的80端口访问到容器内部的服务;也可以通过访问b1主机的lo接口访问到web4上的服务
[root@node1 ~]# docker attach b1
/ # ps aux
PID USER TIME COMMAND
1 root 0:00 sh
14 root 0:00 ps aux
/ # wget -O - -q http://127.0.0.1
this test file
/ # read escape sequence
[root@node1 ~]#
提示:虽然通过lo接口可以访问到web4上的服务,但他们的其他资源还是相互隔离的,只是网络名称空间是共享的同一个;
除此以外,我们在运行容器时还可以通过docker run 的一些选项来注入一些信息到容器内部
示例:注入hostname到容器内部
[root@node1 ~]# docker run --name web01 -it --rm --net bridge --hostname www.ilinux.io linux1874/myimg:v0.1 /bin/sh
/ # hostname
www.ilinux.io
/ # exit
[root@node1 ~]#
提示:可以看到在容器内部主机名就是我们运行容器时给定的主机名;--rm表示退出容器时删除容器;-d 和--rm不能同时使用,这两个选项是相互排斥的;
示例:从外部指定hostname与主机地址解析列表
[root@node1 ~]# docker run --name web01 -it --rm --net bridge --hostname www.ilinux.io --add-host www.test.com:1.1.1.1 --add-host www.test2.com:2.2.2.2 linux1874/myimg:v0.1 /bin/sh
/ # cat /etc/hosts
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
1.1.1.1 www.test.com
2.2.2.2 www.test2.com
172.17.0.4 www.ilinux.io www
/ # exit
[root@node1 ~]#
提示:--add-host选项可以重复使用很多次;应用场景,如果多容器间通信需要用到解析主机名的方式,那么我们就需要用到注入主机名到主机的解析;
示例:注入dns服务器地址到容器
[root@node1 ~]# docker run --name web01 -it --rm --net bridge --hostname www.ilinux.io --add-host www.test.com:1.1.1.1 --add-host www.test2.com:2.2.2.2 --dns 3.3.3.3 --dns 4.4.4.4 linux1874/myimg:v0.1 /bin/sh
/ # cat /etc/resolv.conf
nameserver 3.3.3.3
nameserver 4.4.4.4
/ # exit
[root@node1 ~]#
提示:--dns表示指定dns服务器地址;该选项也可同时使用多次用来指定多个dns服务器地址;
示例:注入dns search
[root@node1 ~]# docker run --name web01 -it --rm --net bridge --hostname www.ilinux.io --add-host www.test.com:1.1.1.1 --add-host www.test2.com:2.2.2.2 --dns 3.3.3.3 --dns 4.4.4.4 --dns-search test.com --dns-search test2.com linux1874/myimg:v0.1 /bin/sh
/ # cat /etc/resolv.conf
search test.com test2.com
nameserver 3.3.3.3
nameserver 4.4.4.4
/ # exit
[root@node1 ~]#
提示:--dns-search 选项表示指定dns search;该选项也可同时使用多次,用来指定多个dns search;
示例:注入ip地址为容器ip地址
[root@node1 ~]# docker run --name web01 -it --rm --net bridge --hostname www.ilinux.io --add-host www.test.com:1.1.1.1 --add-host www.test2.com:2.2.2.2 --dns 3.3.3.3 --dns 4.4.4.4 --dns-search test.com --dns-search test2.com --ip 172.17.0.20 linux1874/myimg:v0.1 /bin/sh
docker: Error response from daemon: user specified IP address is supported on user defined networks only.
[root@node1 ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
2ae9aa656656 bridge bridge local
93347fb33d89 host host local
a99b876eee4d none null local
[root@node1 ~]# docker network create --subnet 10.0.0.0/24 mynet
e80b4e4cc6e9f2c772797c27b0cd81b93cc874e0ffbc5cc2ea2d3a1d9d5530fb
[root@node1 ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
2ae9aa656656 bridge bridge local
93347fb33d89 host host local
e80b4e4cc6e9 mynet bridge local
a99b876eee4d none null local
[root@node1 ~]# docker run --name web01 -it --rm --net mynet --hostname www.ilinux.io --add-host www.test.com:1.1.1.1 --add-host www.test2.com:2.2.2.2 --dns 3.3.3.3 --dns 4.4.4.4 --dns-search test.com --dns-search test2.com --ip 10.0.0.200 linux1874/myimg:v0.1 /bin/sh
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
29: eth0@if30: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:0a:00:00:c8 brd ff:ff:ff:ff:ff:ff
inet 10.0.0.200/24 brd 10.0.0.255 scope global eth0
valid_lft forever preferred_lft forever
/ # exit
[root@node1 ~]#
提示:docker 默认情况是不支持启动容器指定ip地址的,指定ip地址只允许在自定义网络上指定;所以要想给容器指定ip地址,首先要自己创建一个网络名称空间;运行容器时通过--net或--network指定网络,然后在指定IP地址就没有问题了;
示例:给容器连接多个网络
[root@node1 ~]# docker run --name web1 -it --rm --network bridge linux1874/myimg:v0.1 /bin/sh
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
52: eth0@if53: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
/ # [root@node1 ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
03e2689873d0 bridge bridge local
93347fb33d89 host host local
e80b4e4cc6e9 mynet bridge local
a99b876eee4d none null local
[root@node1 ~]# docker network connect mynet web1
[root@node1 ~]# docker attach web1
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
52: eth0@if53: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
54: eth1@if55: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether 02:42:0a:00:00:02 brd ff:ff:ff:ff:ff:ff
inet 10.0.0.2/24 brd 10.0.0.255 scope global eth1
valid_lft forever preferred_lft forever
/ #
提示:docker nerwork connect 类似给容器添加一块网络,然后将容器里的网卡连接至我们指定的网络;
端口暴露
通常情况下我们运行docker容器都是使用的bridge网络,只有特殊场景才会用到自定义网络和其他网络;使用bridge网络有一个问题就是容器里的服务怎么让外界的主机访问到呢?首先要让外部访问到容器内部的网络,这一层是不太可能了,原因是docker0桥是一个nat桥,它只可让内部容器访问外部主机,不可用外部主机访问内部容器;如果要访问,我们需要修改iptables的规则,很麻烦;除此之外还可以在宿主机上搭建一个反向代理,外部通过访问代理,然后代理访问容器内部服务,这样的方式可行,但通常不这么做;除此之外就只有把容器里跑的服务端口映射到宿主机上某端口,外部通过访问宿主机的某端口,通过iptables规则做DNAT;通过端口映射到方式让外部主机可以访问到容器内部的服务;其实docker container run这个命令有一个-p的选项就是用来做这个事的;我们用-p选项来指定把宿主机的那个ip或端口映射到容器的某个ip或端口上;它的原理就是通过修改宿主机的iptables规则,做DNAT实现的;
示例:将容器80端口映射至宿主机某动态端口
[root@node1 ~]# docker run --name web01 -d -p 80 linux1874/myimg:v0.1
7dd827a920f07badc79911120aa9fee5dc74d8d9959f554ac9c19d911befd31c
[root@node1 ~]# docker container port web01
80/tcp -> 0.0.0.0:32768
[root@node1 ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
11 852 DOCKER all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 1 packets, 76 bytes)
pkts bytes target prot opt in out source destination
0 0 DOCKER all -- * * 0.0.0.0/0 !127.0.0.0/8 ADDRTYPE match dst-type LOCAL Chain POSTROUTING (policy ACCEPT 1 packets, 76 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * !br-e80b4e4cc6e9 10.0.0.0/24 0.0.0.0/0
6 379 MASQUERADE all -- * !docker0 172.17.0.0/16 0.0.0.0/0
0 0 MASQUERADE tcp -- * * 172.17.0.4 172.17.0.4 tcp dpt:80 Chain DOCKER (2 references)
pkts bytes target prot opt in out source destination
0 0 RETURN all -- br-e80b4e4cc6e9 * 0.0.0.0/0 0.0.0.0/0
0 0 RETURN all -- docker0 * 0.0.0.0/0 0.0.0.0/0
0 0 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32768 to:172.17.0.4:80
[root@node1 ~]#
提示:-p 指定容器里服务的端口,表示把容器的该端口映射到宿主机上的一个随机端口,通常这个随机端口是从32768开始;从上面的接口可以看到我们把80端口映射到宿主机上的32768端口上,随之docker会在宿主机的iptables的nat表上添加一条DNAT规则;现在我们就可以通过访问宿主机的32768端口来访问容器内部的服务;通常我们不建议把容器里的服务随机映射到宿主机上的一个端口;原因是客户端不知道随机端口后面的服务是什么,当然访问也就受限;
测试:访问宿主机的32768端口看看是否能够访问到容器内部的web服务?
[root@docker_node1 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:22:36:7f brd ff:ff:ff:ff:ff:ff
inet 192.168.0.22/24 brd 192.168.0.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe22:367f/64 scope link
valid_lft forever preferred_lft forever
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN
link/ether 02:42:72:cb:66:6d brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
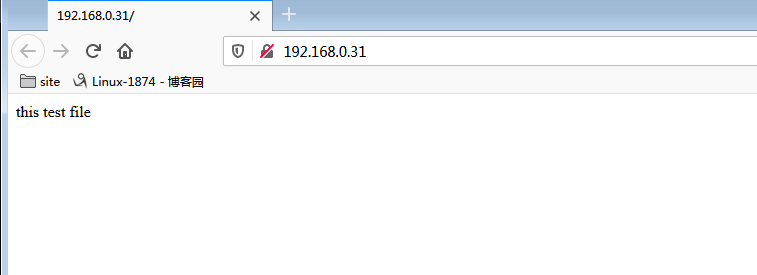
[root@docker_node1 ~]# curl 192.168.0.31:32768
this test file
[root@docker_node1 ~]#
示例:将容器端口映射到指定主机端口
[root@node1 ~]# docker run --name web02 -d --net bridge -p 80:80 linux1874/myimg:v0.1
351ed7833aa1908c43abc061f5acdc7bd5e083ea097b26c1f4d4a7422bfbfcfa
[root@node1 ~]# docker container port web02
80/tcp -> 0.0.0.0:80
[root@node1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
351ed7833aa1 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 23 seconds ago Up 21 seconds 0.0.0.0:80->80/tcp web02
7dd827a920f0 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 10 minutes ago Up 10 minutes 0.0.0.0:32768->80/tcp web01
[root@node1 ~]# ss -tnl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 :::80 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
LISTEN 0 128 :::32768 :::*
[root@node1 ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 2 packets, 466 bytes)
pkts bytes target prot opt in out source destination
12 912 DOCKER all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL Chain INPUT (policy ACCEPT 2 packets, 466 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 1 packets, 76 bytes)
pkts bytes target prot opt in out source destination
0 0 DOCKER all -- * * 0.0.0.0/0 !127.0.0.0/8 ADDRTYPE match dst-type LOCAL Chain POSTROUTING (policy ACCEPT 1 packets, 76 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * !br-e80b4e4cc6e9 10.0.0.0/24 0.0.0.0/0
6 379 MASQUERADE all -- * !docker0 172.17.0.0/16 0.0.0.0/0
0 0 MASQUERADE tcp -- * * 172.17.0.4 172.17.0.4 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.2 172.17.0.2 tcp dpt:80 Chain DOCKER (2 references)
pkts bytes target prot opt in out source destination
0 0 RETURN all -- br-e80b4e4cc6e9 * 0.0.0.0/0 0.0.0.0/0
0 0 RETURN all -- docker0 * 0.0.0.0/0 0.0.0.0/0
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32768 to:172.17.0.4:80
0 0 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 to:172.17.0.2:80
[root@node1 ~]#
提示:可以看到我们指定把容器的80端口映射到宿主机的80端口,宿主机上的80端口就处于监听状态了;同时iptables的nat表上又生成了一条新的DNT规则;
测试:通过其他主机访问宿主机上的80看看是否能够访问到容器里的80服务?
[root@docker_node1 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:22:36:7f brd ff:ff:ff:ff:ff:ff
inet 192.168.0.22/24 brd 192.168.0.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe22:367f/64 scope link
valid_lft forever preferred_lft forever
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN
link/ether 02:42:72:cb:66:6d brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
[root@docker_node1 ~]# curl 192.168.0.31
this test file
[root@docker_node1 ~]#
示例:将指定的容器端口映射到宿主机的指定ip上的动态端口
[root@node1 ~]# docker run --name web03 -d --net bridge -p 192.168.0.214::80 linux1874/myimg:v0.1
b4276ea0d0c0265a608b8111d64655a8667871f1b19cf971b42921a9a464c020
[root@node1 ~]# docker container port web03
80/tcp -> 192.168.0.214:32769
[root@node1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
b4276ea0d0c0 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 15 seconds ago Up 15 seconds 192.168.0.214:32769->80/tcp web03
351ed7833aa1 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 10 minutes ago Up 10 minutes 0.0.0.0:80->80/tcp web02
7dd827a920f0 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 20 minutes ago Up 20 minutes 0.0.0.0:32768->80/tcp web01
[root@node1 ~]# ss -tnl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 192.168.0.214:32769 *:*
LISTEN 0 128 :::80 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
LISTEN 0 128 :::32768 :::*
[root@node1 ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
15 1068 DOCKER all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 2 packets, 152 bytes)
pkts bytes target prot opt in out source destination
0 0 DOCKER all -- * * 0.0.0.0/0 !127.0.0.0/8 ADDRTYPE match dst-type LOCAL Chain POSTROUTING (policy ACCEPT 2 packets, 152 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * !br-e80b4e4cc6e9 10.0.0.0/24 0.0.0.0/0
6 379 MASQUERADE all -- * !docker0 172.17.0.0/16 0.0.0.0/0
0 0 MASQUERADE tcp -- * * 172.17.0.4 172.17.0.4 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.2 172.17.0.2 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.3 172.17.0.3 tcp dpt:80 Chain DOCKER (2 references)
pkts bytes target prot opt in out source destination
0 0 RETURN all -- br-e80b4e4cc6e9 * 0.0.0.0/0 0.0.0.0/0
0 0 RETURN all -- docker0 * 0.0.0.0/0 0.0.0.0/0
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32768 to:172.17.0.4:80
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 to:172.17.0.2:80
0 0 DNAT tcp -- !docker0 * 0.0.0.0/0 192.168.0.214 tcp dpt:32769 to:172.17.0.3:80
[root@node1 ~]#
提示:可以看到宿主机上的192.168.0.214的32769处于监听状体;同时iptables的nat表示也新增了一条DNAT规则;
测试:通过其他主机访问宿主机的192.168.0.214的32769端口,看看是否能够访问到容器内部的80服务?
[root@docker_node1 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:22:36:7f brd ff:ff:ff:ff:ff:ff
inet 192.168.0.22/24 brd 192.168.0.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe22:367f/64 scope link
valid_lft forever preferred_lft forever
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN
link/ether 02:42:72:cb:66:6d brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
[root@docker_node1 ~]# curl 192.168.0.214:32769
this test file
[root@docker_node1 ~]#
示例:将容器的端口映射至宿主机的指定ip的指定端口
[root@node1 ~]# docker run --name web04 -d --net bridge -p 192.168.0.214:81:80 linux1874/myimg:v0.1
1f58cd21b2c861b8761032a07d9e47d3bf1a2c072816d931918171ea38a9c090
[root@node1 ~]# docker container port web04
80/tcp -> 192.168.0.214:81
[root@node1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
1f58cd21b2c8 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 19 seconds ago Up 17 seconds 192.168.0.214:81->80/tcp web04
b4276ea0d0c0 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 7 minutes ago Up 7 minutes 192.168.0.214:32769->80/tcp web03
351ed7833aa1 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 17 minutes ago Up 17 minutes 0.0.0.0:80->80/tcp web02
7dd827a920f0 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 27 minutes ago Up 27 minutes 0.0.0.0:32768->80/tcp web01
[root@node1 ~]# ss -tnl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 192.168.0.214:81 *:*
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 192.168.0.214:32769 *:*
LISTEN 0 128 :::80 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
LISTEN 0 128 :::32768 :::*
[root@node1 ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
16 1128 DOCKER all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 1 packets, 76 bytes)
pkts bytes target prot opt in out source destination
0 0 DOCKER all -- * * 0.0.0.0/0 !127.0.0.0/8 ADDRTYPE match dst-type LOCAL Chain POSTROUTING (policy ACCEPT 1 packets, 76 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * !br-e80b4e4cc6e9 10.0.0.0/24 0.0.0.0/0
6 379 MASQUERADE all -- * !docker0 172.17.0.0/16 0.0.0.0/0
0 0 MASQUERADE tcp -- * * 172.17.0.4 172.17.0.4 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.2 172.17.0.2 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.3 172.17.0.3 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.5 172.17.0.5 tcp dpt:80 Chain DOCKER (2 references)
pkts bytes target prot opt in out source destination
0 0 RETURN all -- br-e80b4e4cc6e9 * 0.0.0.0/0 0.0.0.0/0
0 0 RETURN all -- docker0 * 0.0.0.0/0 0.0.0.0/0
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32768 to:172.17.0.4:80
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 to:172.17.0.2:80
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 192.168.0.214 tcp dpt:32769 to:172.17.0.3:80
0 0 DNAT tcp -- !docker0 * 0.0.0.0/0 192.168.0.214 tcp dpt:81 to:172.17.0.5:80
[root@node1 ~]#
提示:可以看到宿主机上的81端口处于监听状态,同时iptables中的nat表也新加了一条DNAT规则;
测试:用其他主机访问192.168.0.214的81端口看看是否能够访问到容器里80服务?
[root@docker_node1 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:22:36:7f brd ff:ff:ff:ff:ff:ff
inet 192.168.0.22/24 brd 192.168.0.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe22:367f/64 scope link
valid_lft forever preferred_lft forever
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN
link/ether 02:42:72:cb:66:6d brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
[root@docker_node1 ~]# curl 192.168.0.214:81
this test file
[root@docker_node1 ~]#
示例:将容器多个端口映射到宿主机
[root@node1 ~]# docker run --name web05 -d --net bridge -p 80 -p 443 linux1874/myimg:v0.1
898e99cf0f37104954913488717969584d35677a0660874a52a502934599caf7
[root@node1 ~]# docker container port web05
443/tcp -> 0.0.0.0:32770
80/tcp -> 0.0.0.0:32771
[root@node1 ~]# ss -ntl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 192.168.0.214:81 *:*
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 192.168.0.214:32769 *:*
LISTEN 0 128 :::80 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
LISTEN 0 128 :::32768 :::*
LISTEN 0 128 :::32770 :::*
LISTEN 0 128 :::32771 :::*
[root@node1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
898e99cf0f37 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 31 seconds ago Up 29 seconds 0.0.0.0:32771->80/tcp, 0.0.0.0:32770->443/tcp web05
1f58cd21b2c8 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 19 minutes ago Up 19 minutes 192.168.0.214:81->80/tcp web04
b4276ea0d0c0 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 26 minutes ago Up 26 minutes 192.168.0.214:32769->80/tcp web03
351ed7833aa1 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 35 minutes ago Up 35 minutes 0.0.0.0:80->80/tcp web02
7dd827a920f0 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 46 minutes ago Up 46 minutes 0.0.0.0:32768->80/tcp web01
[root@node1 ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
17 1188 DOCKER all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 3 packets, 228 bytes)
pkts bytes target prot opt in out source destination
0 0 DOCKER all -- * * 0.0.0.0/0 !127.0.0.0/8 ADDRTYPE match dst-type LOCAL Chain POSTROUTING (policy ACCEPT 3 packets, 228 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * !br-e80b4e4cc6e9 10.0.0.0/24 0.0.0.0/0
6 379 MASQUERADE all -- * !docker0 172.17.0.0/16 0.0.0.0/0
0 0 MASQUERADE tcp -- * * 172.17.0.4 172.17.0.4 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.2 172.17.0.2 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.3 172.17.0.3 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.5 172.17.0.5 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.6 172.17.0.6 tcp dpt:443
0 0 MASQUERADE tcp -- * * 172.17.0.6 172.17.0.6 tcp dpt:80 Chain DOCKER (2 references)
pkts bytes target prot opt in out source destination
0 0 RETURN all -- br-e80b4e4cc6e9 * 0.0.0.0/0 0.0.0.0/0
0 0 RETURN all -- docker0 * 0.0.0.0/0 0.0.0.0/0
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32768 to:172.17.0.4:80
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 to:172.17.0.2:80
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 192.168.0.214 tcp dpt:32769 to:172.17.0.3:80
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 192.168.0.214 tcp dpt:81 to:172.17.0.5:80
0 0 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32770 to:172.17.0.6:443
0 0 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32771 to:172.17.0.6:80
[root@node1 ~]#
提示:-p选项可以使用多次,来指定需要映射端口和宿主机的端口映射关系;除此还可以使用-P(大写) 加--expose来指定要映射的端口
[root@node1 ~]# docker run --name web06 -d --net bridge -P --expose 80 --expose 443 linux1874/myimg:v0.1
b377f6d380828ece81d69fd83cf7678800466f45689850a7e47dde1619602ffa
[root@node1 ~]# docker container port web06
443/tcp -> 0.0.0.0:32772
80/tcp -> 0.0.0.0:32773
[root@node1 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
b377f6d38082 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 19 seconds ago Up 18 seconds 0.0.0.0:32773->80/tcp, 0.0.0.0:32772->443/tcp web06
898e99cf0f37 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 3 minutes ago Up 3 minutes 0.0.0.0:32771->80/tcp, 0.0.0.0:32770->443/tcp web05
1f58cd21b2c8 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 22 minutes ago Up 22 minutes 192.168.0.214:81->80/tcp web04
b4276ea0d0c0 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 29 minutes ago Up 29 minutes 192.168.0.214:32769->80/tcp web03
351ed7833aa1 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 39 minutes ago Up 39 minutes 0.0.0.0:80->80/tcp web02
7dd827a920f0 linux1874/myimg:v0.1 "/bin/sh -c '/bin/ht…" 49 minutes ago Up 49 minutes 0.0.0.0:32768->80/tcp web01
[root@node1 ~]# ss -tnl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 192.168.0.214:81 *:*
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 192.168.0.214:32769 *:*
LISTEN 0 128 :::80 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
LISTEN 0 128 :::32768 :::*
LISTEN 0 128 :::32770 :::*
LISTEN 0 128 :::32771 :::*
LISTEN 0 128 :::32772 :::*
LISTEN 0 128 :::32773 :::*
[root@node1 ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
17 1188 DOCKER all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 3 packets, 228 bytes)
pkts bytes target prot opt in out source destination
0 0 DOCKER all -- * * 0.0.0.0/0 !127.0.0.0/8 ADDRTYPE match dst-type LOCAL Chain POSTROUTING (policy ACCEPT 3 packets, 228 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * !br-e80b4e4cc6e9 10.0.0.0/24 0.0.0.0/0
6 379 MASQUERADE all -- * !docker0 172.17.0.0/16 0.0.0.0/0
0 0 MASQUERADE tcp -- * * 172.17.0.4 172.17.0.4 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.2 172.17.0.2 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.3 172.17.0.3 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.5 172.17.0.5 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.6 172.17.0.6 tcp dpt:443
0 0 MASQUERADE tcp -- * * 172.17.0.6 172.17.0.6 tcp dpt:80
0 0 MASQUERADE tcp -- * * 172.17.0.7 172.17.0.7 tcp dpt:443
0 0 MASQUERADE tcp -- * * 172.17.0.7 172.17.0.7 tcp dpt:80 Chain DOCKER (2 references)
pkts bytes target prot opt in out source destination
0 0 RETURN all -- br-e80b4e4cc6e9 * 0.0.0.0/0 0.0.0.0/0
0 0 RETURN all -- docker0 * 0.0.0.0/0 0.0.0.0/0
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32768 to:172.17.0.4:80
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 to:172.17.0.2:80
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 192.168.0.214 tcp dpt:32769 to:172.17.0.3:80
1 60 DNAT tcp -- !docker0 * 0.0.0.0/0 192.168.0.214 tcp dpt:81 to:172.17.0.5:80
0 0 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32770 to:172.17.0.6:443
0 0 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32771 to:172.17.0.6:80
0 0 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32772 to:172.17.0.7:443
0 0 DNAT tcp -- !docker0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:32773 to:172.17.0.7:80
[root@node1 ~]#
提示:使用-P(大写) --expose 的方式暴露端口,不可以选择暴露给宿主机的某个ip的某个端口或随机端口,只能暴露给宿主机的所有ip的随机端口;简单说就是不能指定固定宿主机的IP和端口;
示例:修改docker0桥的网络属性
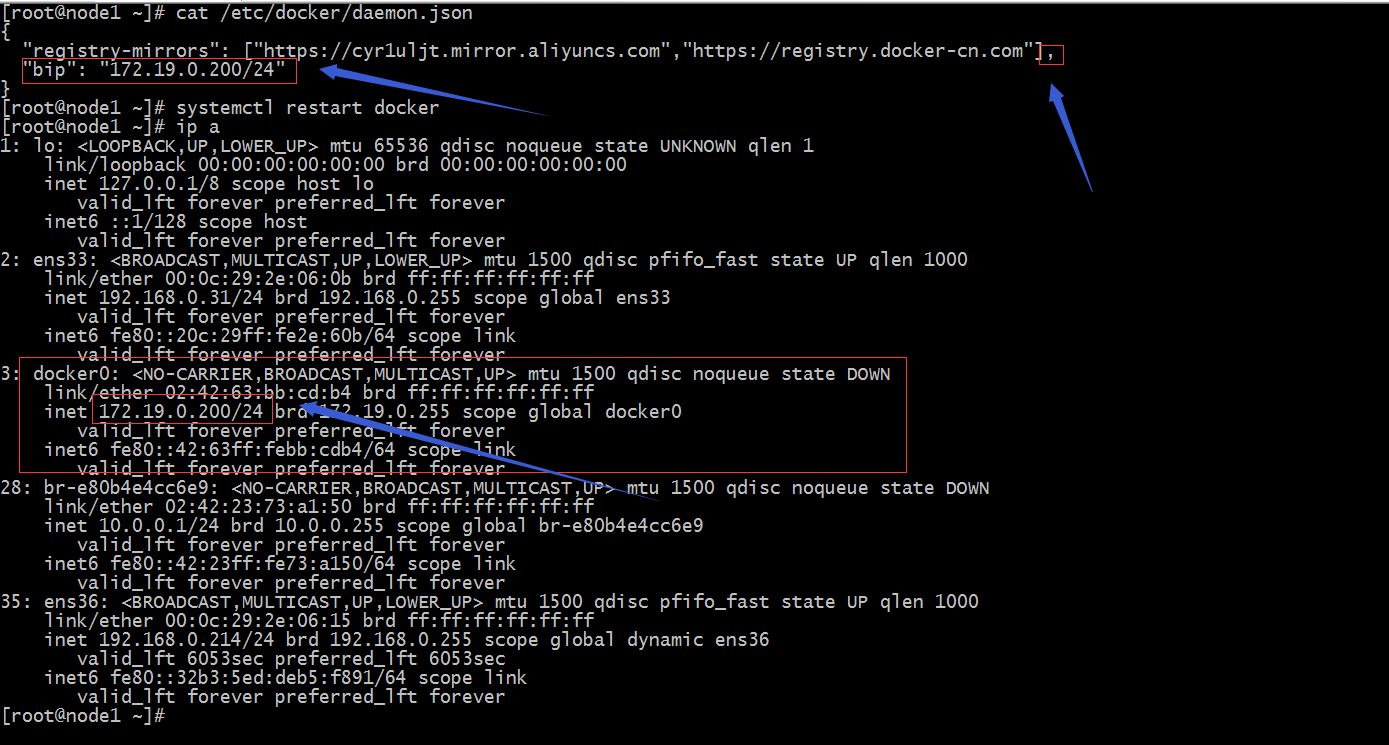
提示:修改docker0桥的网络信息,我们需要在/etc/docker/daemon.json这个文件中添加一项bip来指定docker0桥的网络地址;这里需要注意一点的是如果这个文件没有内容我们直接用大括号加“bip”: "ip地址和子网掩码"即可,如果有其他项需要注意后面的逗号,如上所示;如果后续还有其他配置,需要在最后的一项后面加逗号,然后在添加其他配置;末尾可以不写逗号;其实这个文件中可以添加很多配置,对于配置docker0桥的属性也有很多,但核心配置选项就是bip,它主要是用来指定docker0桥的ip地址和子网掩码信息;其他的选项可以不用指定,它们都可以通过bip这个选项自动计算生成;有关/etc/docker/daemon.json文件的相关说明可以参考官方文档https://docs.docker.com/engine/reference/commandline/dockerd/#run-multiple-daemons;
容器技术之Docker网络的更多相关文章
- linux容器技术和Docker
linux容器技术和Docker 概述 Docker在一定程度上是LXC的增强版,早期的Docker使用LXC作为容器引擎,所以也可以说Docker是LXC的二次封装发行版,目前docker使用的容器 ...
- 容器技术|Docker三剑客之docker-compose
三剑客简介 docker-machine docker技术是基于Linux内核的cgroup技术实现的,那么问题来了,在非Linux平台上是否就不能使用docker技术了呢?答案是可以的,不过显然需要 ...
- 容器技术与docker
名词介绍 IaaS:基础设施即服务,要搭建上层数据应用,先得通过互联网获得基础性设施服务 PaaS:平台即服务,搭建平台,集成应用产品,整合起来提供服务 SaaS:软件即服务,通过网络提供程序应用类服 ...
- 容器技术|Docker三剑客之docker-machine
docker-machine是什么? ocker-machine就是docker公司官方提出的,用于在各种平台上快速创建具有docker服务的虚拟机的技术,甚至可以通过指定driver来定制虚拟机的实 ...
- Docker容器技术-优化Docker镜像
一.优化Docker镜像 1.降低部署时间 一个大的Docker应用是如何影响在新Docker宿主机上的部署时间. (1)编写Dockerfile创建一个大Docker镜像 [root@bogon ~ ...
- 容器技术之Docker镜像
前文我们聊了下docker的基础使用方法,大概介绍了下docker的架构,管理镜像.运行容器.管理容器的一些相关命令说明:回顾请参考https://www.cnblogs.com/qiuhom-187 ...
- 容器技术之Docker数据卷
前一篇随笔中我们了解了docker的网络相关说明,回顾请参考https://www.cnblogs.com/qiuhom-1874/p/12952616.html:今天我们来聊一聊docker的数据管 ...
- 容器技术之Docker常用命令说明
前面我们聊了docker的基本概念.架构.镜像.网络.数据卷,回顾请参考https://www.cnblogs.com/qiuhom-1874/category/1766327.html:今天这篇博客 ...
- 容器技术之Docker基础入门
前文我们了解了下LXC的基础用法以及图形管理工具LXC WEB Panel的简单使用,有兴趣的朋友可以参考https://www.cnblogs.com/qiuhom-1874/p/12904188. ...
随机推荐
- UVA10599:Robots(II)(最长上升子序列)
Your company provides robots that can be used to pick up litter from fields after sporting events an ...
- mac OS 安装配置 Tomcat
Apache Tomcat官网 http://tomcat.apache.org/ 选择一个版本 本文以tomcat 9为例 选择Mac OS 对应的压缩包下载 把文件解压然后 在主用户里新建一个目 ...
- python selenium(键盘事件 Keys 类)
1.导入Keys类 from selenium.webdriver.common.keys import Keys Keys.BACK_SPACE 删除输入框内结尾的单个字符 Keys.SPACE ...
- zabbix监控hbase
项目地址:https://github.com/Staroon/zabbix-hadoop-template/tree/master/hbase-master-template (1).下载脚本,将其 ...
- OSG程序设计之osg::NodeVisitor
本文所有内容来自<OpenSceneGraph三维渲染引擎设计与实践>一书. 本文主要讨论的是OSG中节点的访问. 对于节点的访问是从节点接收一个访问器开始的,用户执行某个节点的accep ...
- springboot中json转换LocalDateTime失败的bug解决过程
环境:jdk1.8.maven.springboot 问题:前端通过json传了一个日期:date:2019-03-01(我限制不了前端开发给到后端的日期为固定格式,有些人就是这么不配合), ...
- P2432 zxbsmk爱查错
描述:https://www.luogu.com.cn/problem/P2432 给你一个主串以及若干个子串,求最少需要删除几个字母,使得主串能由一些子串组成. dp [ i ] 表示前 i 个字符 ...
- 使用 if elseif else 指定条件
nrows = 4; ncols = 6; A = ones(nrows,ncols); 遍历矩阵并为每个元素指定一个新值.对主对角线赋值 2,对相邻对角线赋值 -1,对其他位置赋值 0. for c ...
- Collection接口【集合】和Iterator迭代器类
1.1集合的概述 前面基础学习并使用过集合ArrayList<E>,那么集合究竟是什么呢? 集合:集合是Java中提供的一种容器,可以用来存储多个数据. 那么意思就是说集合是容器,但是容器 ...
- Synchronized加锁、锁升级和java对象内存结构
首先了解一下JMM中定义的内存操作: 一个线程操作数据时候都是从主内存(堆内存)读取到自己工作内存(线程私有的数据区域)中再进行操作.对于硬件内存来说,并没有工作内存和主内存的区分,这都是java内存 ...
