Openssl s_server命令
一、简介
s_server是openssl提供的一个SSL服务程序。使用此程序前,需要生成各种证书。本命令可以用来测试ssl客户端,比如各种浏览器的https协议支持
二、语法
openssl s_server [-accept port] [-context id] [-verify depth] [-Verify depth] [-crl_check] [-crl_check_all] [-cert filename] [-certform DER|PEM] [-key filename] [-keyform DER|PEM] [-pass arg] [-dcert filename] [-dcertform DER|PEM ] [-dkey keyfile] [-dkeyform DER|PEM ] [-dpass arg] [-dhparam filename] [-name_curve arg][-nbio] [-nbio_test] [-crlf] [-debug] [-msg] [-state] [-CApath directory] [-CAfile filename] [-nocert] [-cipher cipherlist] [-quiet] [-no_tmp_rsa] [-ssl2] [-ssl3] [-tls1_1] [-tls1_2] [-tls1] [-dtls1] [-timeout] [-mtu] [-chain] [-no_ssl2][-no_ssl3] [-no_tls1] [-no_tls1_1] [-no_tls1_2] [-no_dhe] [-no_ecdhe][-bugs] [-hack] [-www] [-WWW] [-HTTP][-engine id] [-tlsextdebug] [-no_ticket] [-id_prefix arg] [-rand file(s)]
选项
-accept arg - port to accept on (default is )
-context arg - set session ID context
-verify arg - turn on peer certificate verification
-Verify arg - turn on peer certificate verification, must have a cert.
-cert arg - certificate file to use
(default is server.pem)
-crl_check - check the peer certificate has not been revoked by its CA.
The CRL(s) are appended to the certificate file
-crl_check_all - check the peer certificate has not been revoked by its CA
or any other CRL in the CA chain. CRL(s) are appened to the
the certificate file.
-certform arg - certificate format (PEM or DER) PEM default
-key arg - Private Key file to use, in cert file if
not specified (default is server.pem)
-keyform arg - key format (PEM, DER or ENGINE) PEM default
-pass arg - private key file pass phrase source
-dcert arg - second certificate file to use (usually for DSA)
-dcertform x - second certificate format (PEM or DER) PEM default
-dkey arg - second private key file to use (usually for DSA)
-dkeyform arg - second key format (PEM, DER or ENGINE) PEM default
-dpass arg - second private key file pass phrase source
-dhparam arg - DH parameter file to use, in cert file if not specified
or a default set of parameters is used
-named_curve arg - Elliptic curve name to use for ephemeral ECDH keys.
Use "openssl ecparam -list_curves" for all names
(default is nistp256).
-nbio - Run with non-blocking IO
-nbio_test - test with the non-blocking test bio
-crlf - convert LF from terminal into CRLF
-debug - Print more output
-msg - Show protocol messages
-state - Print the SSL states
-CApath arg - PEM format directory of CA's
-CAfile arg - PEM format file of CA's
-trusted_first - Use trusted CA's first when building the trust chain
-nocert - Don't use any certificates (Anon-DH)
-cipher arg - play with 'openssl ciphers' to see what goes here
-serverpref - Use server's cipher preferences
-quiet - No server output
-no_tmp_rsa - Do not generate a tmp RSA key
-psk_hint arg - PSK identity hint to use
-psk arg - PSK in hex (without 0x)
-ssl2 - Just talk SSLv2
-ssl3 - Just talk SSLv3
-tls1_2 - Just talk TLSv1.
-tls1_1 - Just talk TLSv1.
-tls1 - Just talk TLSv1
-dtls1 - Just talk DTLSv1
-timeout - Enable timeouts
-mtu - Set link layer MTU
-chain - Read a certificate chain
-no_ssl2 - Just disable SSLv2
-no_ssl3 - Just disable SSLv3
-no_tls1 - Just disable TLSv1
-no_tls1_1 - Just disable TLSv1.
-no_tls1_2 - Just disable TLSv1.
-no_dhe - Disable ephemeral DH
-no_ecdhe - Disable ephemeral ECDH
-bugs - Turn on SSL bug compatibility
-www - Respond to a 'GET /' with a status page
-WWW - Respond to a 'GET /<path> HTTP/1.0' with file ./<path>
-HTTP - Respond to a 'GET /<path> HTTP/1.0' with file ./<path>
with the assumption it contains a complete HTTP response.
-engine id - Initialise and use the specified engine
-id_prefix arg - Generate SSL/TLS session IDs prefixed by 'arg'
-rand file:file:...
-servername host - servername for HostName TLS extension
-servername_fatal - on mismatch send fatal alert (default warning alert)
-cert2 arg - certificate file to use for servername
(default is server2.pem)
-key2 arg - Private Key file to use for servername, in cert file if
not specified (default is server2.pem)
-tlsextdebug - hex dump of all TLS extensions received
-no_ticket - disable use of RFC4507bis session tickets
-legacy_renegotiation - enable use of legacy renegotiation (dangerous)
-nextprotoneg arg - set the advertised protocols for the NPN extension (comma-separated list)
-use_srtp profiles - Offer SRTP key management with a colon-separated profile list
-keymatexport label - Export keying material using label
-keymatexportlen len - Export len bytes of keying material (default )
三、实例
1、启动s_server服务(站点证书及私钥,证书链,协议版本,算法组合)
openssl s_server -accept 2009 -key serverprikey.pem -cert server.pem -ssl3 -cipher EXP-KRB5-RC4-MD5 -chain -debug -msg
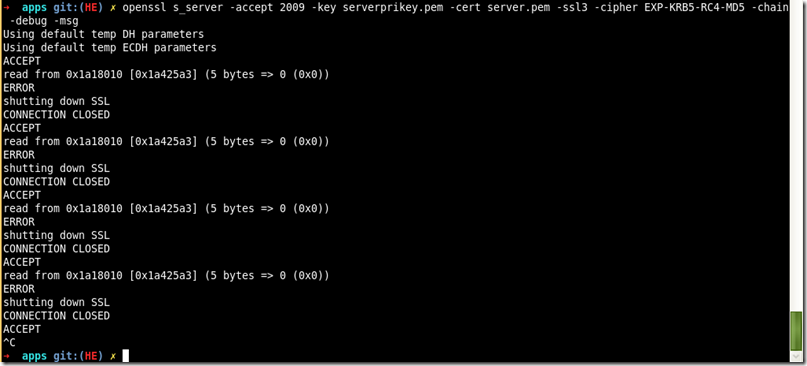
参考:http://blog.csdn.net/as3luyuan123/article/details/16850727 http://www.tuicool.com/articles/6ny6Fv
Openssl s_server命令的更多相关文章
- OpenSSL s_server / s_client 应用实例
netkiller openssl tls 目录[-] 12.6. s_server / s_client 12.6.1. SSL POP3 / SMTP / IMAP 12.6.2. server ...
- openssl常用命令行汇总
openssl常用命令行汇总 随机数 openssl rand -out rand.dat -base64 32 摘要 直接做摘要 openssl dgst -sha1 -out dgst.dat p ...
- (转)openssl 命令: openssl req 命令详解
openssl req命令主要的功能有,生成证书请求文件, 查看验证证书请求文件,还有就是生成自签名证书.本文就主要记录一下open ...
- Openssl asn1parse命令
一.简介 asn1parse命令是一种用来诊断ASN.1结构的工具,也能用于从ASN1.1数据中提取数据 二.语法 openssl asn1parse [-inform PEM|DER] [-in f ...
- Openssl pkcs7命令
一.简介 pkcs7命令用于处理DER或者PEM格式的pkcs#7文件. 二.语法 openssl pkcs7 [-inform PEM|DER] [-outform PEM|DER] [-in ...
- Openssl crl2pkcs7命令
一.简介 crl2pkcs命令用来根据CRL或证书来生成pkcs#7消息. 二.语法 openssl crl2pkcs7 [-inform PEM|DER ] [-outform PEM|DER ...
- Openssl verify命令
一.简介 verify命令对证书的有效性进行验证,verify 指令会沿着证书链一直向上验证,直到一个自签名的CA 二.语法 openssl verify [-CApath directory] [- ...
- Openssl rsa命令
一.简介 Rsa命令用于处理RSA密钥.格式转换和打印信息 二.语法 openssl rsa [-inform PEM|NET|DER] [-outform PEM|NET|DER] [-in fil ...
- Openssl pkeyutl命令
一.简介 pkeyutl命令能够测试所支持的密钥算法的性能 二.语法 openssl rsautl [-in file] [-out file] [-sigfile file] [-inkey fil ...
随机推荐
- windows10 vs2015编译 带nginx-rtmp-module 模块的32位nginx
1 下载必要软件 从 http://xhmikosr.1f0.de/tools/msys/下载msys:http://xhmikosr.1f0.de/tools/msys/MSYS_MinGW-w6 ...
- 杂项-数学软件:MATLAB
ylbtech-杂项-数学软件:MATLAB MATLAB是美国MathWorks公司出品的商业数学软件,用于算法开发.数据可视化.数据分析以及数值计算的高级技术计算语言和交互式环境,主要包括MATL ...
- [转]SVN 乱码问题
以下来自:http://godchenmeng.iteye.com/blog/797727 最近研究SVN.发现在创建补丁包的时候出现这种情况. 在文件顶部不论是什么代码都会变成乱码.在文件中如果有注 ...
- 018:InnoDB 存储引擎、表空间
目录 一.InnoDB 存储引擎 1. InnoDB的历史 2. InnoDB的特点 3. InnoDB存储引擎的文件 3.1 概述 3.2 InnoDB - 表空间 3.3 General表空间 3 ...
- HTML转义字符表
- 浅谈PHP面向对象编程(一、简介)
传统的面向过程 将要完成的工作,分作若干个步骤,或再细分为子步骤,然后后步骤从前往后一步一步完成,最初达致目标. 现代的面向对象 将要完成的工作拆分为“一个一个对象”的任务(功能),每个对象独自完成自 ...
- 快速安装laravel和依赖
http://pkg.phpcomposer.com CMD敲命令: composer config -g repositories.packagist composer http://packagi ...
- 十年Java架构师分享
看到一篇十年java架构师分享需要掌握的技术点,有时间对照一下,好好学习一下. ------------------------------------------------------------ ...
- Tkinter Colors(颜色)
Tkinter Colors: Tkinter的代表与字符串的颜色.一般有两种方式来指定Tkinter的颜色 Tkinter的代表与字符串的颜色.一般有两种方式来指定Tkinter的颜色: ...
- Python与快速排序
这个算法系列主要是自己学习算法过程中动手实践一下,写这个文章作为笔记和分享个人心得,如有错误请各位提出. 注:转载请说明出处 问题提出: 将以下数据升序排列:5, 2, 8, 6, 4, 9, 7, ...
