Win7 x64下进程保护与文件保护(ObRegisterCallbacks)
进程保护部分参考 http://bbs.pediy.com/showthread.php?t=168023
进程保护,在任务管理器不能结束进程
#ifndef CXX_PROTECTPROCESSX64_H
#define CXX_PROTECTPROCESSX64_H #include <ntifs.h> #define PROCESS_TERMINATE 0x0001
#define PROCESS_VM_OPERATION 0x0008
#define PROCESS_VM_READ 0x0010
#define PROCESS_VM_WRITE 0x0020 NTSTATUS DriverEntry(IN PDRIVER_OBJECT pDriverObj, IN PUNICODE_STRING pRegistryString); VOID DriverUnload(IN PDRIVER_OBJECT pDriverObj); typedef struct _LDR_DATA_TABLE_ENTRY64
{
LIST_ENTRY64 InLoadOrderLinks;
LIST_ENTRY64 InMemoryOrderLinks;
LIST_ENTRY64 InInitializationOrderLinks;
PVOID DllBase;
PVOID EntryPoint;
ULONG SizeOfImage;
UNICODE_STRING FullDllName;
UNICODE_STRING BaseDllName;
ULONG Flags;
USHORT LoadCount;
USHORT TlsIndex;
PVOID SectionPointer;
ULONG CheckSum;
PVOID LoadedImports;
PVOID EntryPointActivationContext;
PVOID PatchInformation;
LIST_ENTRY64 ForwarderLinks;
LIST_ENTRY64 ServiceTagLinks;
LIST_ENTRY64 StaticLinks;
PVOID ContextInformation;
ULONG64 OriginalBase;
LARGE_INTEGER LoadTime;
} LDR_DATA_TABLE_ENTRY64, *PLDR_DATA_TABLE_ENTRY64; extern
UCHAR *
PsGetProcessImageFileName(
__in PEPROCESS Process
);
char*
GetProcessImageNameByProcessID(ULONG ulProcessID); NTSTATUS ProtectProcess(BOOLEAN Enable); OB_PREOP_CALLBACK_STATUS
preCall(PVOID RegistrationContext, POB_PRE_OPERATION_INFORMATION pOperationInformation); #endif #ifndef CXX_PROTECTPROCESSX64_H
# include "ProtectProcessx64.h"
#endif PVOID obHandle;//定义一个void*类型的变量,它将会作为ObRegisterCallbacks函数的第二个参数。 NTSTATUS
DriverEntry(IN PDRIVER_OBJECT pDriverObj, IN PUNICODE_STRING pRegistryString)
{
NTSTATUS status = STATUS_SUCCESS;
PLDR_DATA_TABLE_ENTRY64 ldr; pDriverObj->DriverUnload = DriverUnload;
// 绕过MmVerifyCallbackFunction。
ldr = (PLDR_DATA_TABLE_ENTRY64)pDriverObj->DriverSection;
ldr->Flags |= 0x20; ProtectProcess(TRUE); return STATUS_SUCCESS;
} NTSTATUS ProtectProcess(BOOLEAN Enable)
{ OB_CALLBACK_REGISTRATION obReg;
OB_OPERATION_REGISTRATION opReg; memset(&obReg, , sizeof(obReg));
obReg.Version = ObGetFilterVersion();
obReg.OperationRegistrationCount = ;
obReg.RegistrationContext = NULL;
RtlInitUnicodeString(&obReg.Altitude, L"");
memset(&opReg, , sizeof(opReg)); //初始化结构体变量 //下面请注意这个结构体的成员字段的设置
opReg.ObjectType = PsProcessType;
opReg.Operations = OB_OPERATION_HANDLE_CREATE|OB_OPERATION_HANDLE_DUPLICATE; opReg.PreOperation = (POB_PRE_OPERATION_CALLBACK)&preCall; //在这里注册一个回调函数指针 obReg.OperationRegistration = &opReg; //注意这一条语句 return ObRegisterCallbacks(&obReg, &obHandle); //在这里注册回调函数
} OB_PREOP_CALLBACK_STATUS
preCall(PVOID RegistrationContext, POB_PRE_OPERATION_INFORMATION pOperationInformation)
{
HANDLE pid = PsGetProcessId((PEPROCESS)pOperationInformation->Object);
char szProcName[]={};
UNREFERENCED_PARAMETER(RegistrationContext);
strcpy(szProcName,GetProcessImageNameByProcessID((ULONG)pid));
if( !_stricmp(szProcName,"calc.exe") )
{
if (pOperationInformation->Operation == OB_OPERATION_HANDLE_CREATE)
{
if ((pOperationInformation->Parameters->CreateHandleInformation.OriginalDesiredAccess & PROCESS_TERMINATE) == PROCESS_TERMINATE)
{
//Terminate the process, such as by calling the user-mode TerminateProcess routine..
pOperationInformation->Parameters->CreateHandleInformation.DesiredAccess &= ~PROCESS_TERMINATE;
}
if ((pOperationInformation->Parameters->CreateHandleInformation.OriginalDesiredAccess & PROCESS_VM_OPERATION) == PROCESS_VM_OPERATION)
{
//Modify the address space of the process, such as by calling the user-mode WriteProcessMemory and VirtualProtectEx routines.
pOperationInformation->Parameters->CreateHandleInformation.DesiredAccess &= ~PROCESS_VM_OPERATION;
}
if ((pOperationInformation->Parameters->CreateHandleInformation.OriginalDesiredAccess & PROCESS_VM_READ) == PROCESS_VM_READ)
{
//Read to the address space of the process, such as by calling the user-mode ReadProcessMemory routine.
pOperationInformation->Parameters->CreateHandleInformation.DesiredAccess &= ~PROCESS_VM_READ;
}
if ((pOperationInformation->Parameters->CreateHandleInformation.OriginalDesiredAccess & PROCESS_VM_WRITE) == PROCESS_VM_WRITE)
{
//Write to the address space of the process, such as by calling the user-mode WriteProcessMemory routine.
pOperationInformation->Parameters->CreateHandleInformation.DesiredAccess &= ~PROCESS_VM_WRITE;
}
}
}
return OB_PREOP_SUCCESS;
} /*
OpenProcess 会一直走入回调中 直接蓝屏
char*
GetProcessImageNameByProcessID(ULONG ulProcessID)
{
CLIENT_ID Cid;
HANDLE hProcess;
NTSTATUS Status;
OBJECT_ATTRIBUTES oa;
PEPROCESS EProcess = NULL; Cid.UniqueProcess = (HANDLE)ulProcessID;
Cid.UniqueThread = 0; InitializeObjectAttributes(&oa,0,0,0,0);
Status = ZwOpenProcess(&hProcess,PROCESS_ALL_ACCESS,&oa,&Cid); //hProcess
//强打开进程获得句柄
if (!NT_SUCCESS(Status))
{
return FALSE;
}
Status = ObReferenceObjectByHandle(hProcess,FILE_READ_DATA,0,
KernelMode,&EProcess, 0);
//通过句柄括获取EProcess
if (!NT_SUCCESS(Status))
{
ZwClose(hProcess);
return FALSE;
}
ObDereferenceObject(EProcess);
//最好判断
ZwClose(hProcess);
//通过EProcess获得进程名称
return (char*)PsGetProcessImageFileName(EProcess); }
*/ char*
GetProcessImageNameByProcessID(ULONG ulProcessID)
{
NTSTATUS Status;
PEPROCESS EProcess = NULL; Status = PsLookupProcessByProcessId((HANDLE)ulProcessID,&EProcess); //EPROCESS //通过句柄获取EProcess
if (!NT_SUCCESS(Status))
{
return FALSE;
}
ObDereferenceObject(EProcess);
//通过EProcess获得进程名称
return (char*)PsGetProcessImageFileName(EProcess); } VOID
DriverUnload(IN PDRIVER_OBJECT pDriverObj)
{
UNREFERENCED_PARAMETER(pDriverObj);
DbgPrint("driver unloading...\n"); ObUnRegisterCallbacks(obHandle); //obHandle是上面定义的 PVOID obHandle;
}
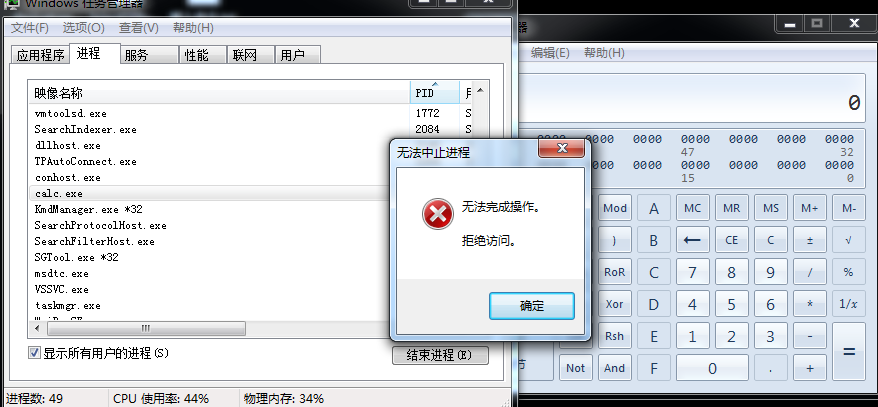
我们使用任务管理器结束进程
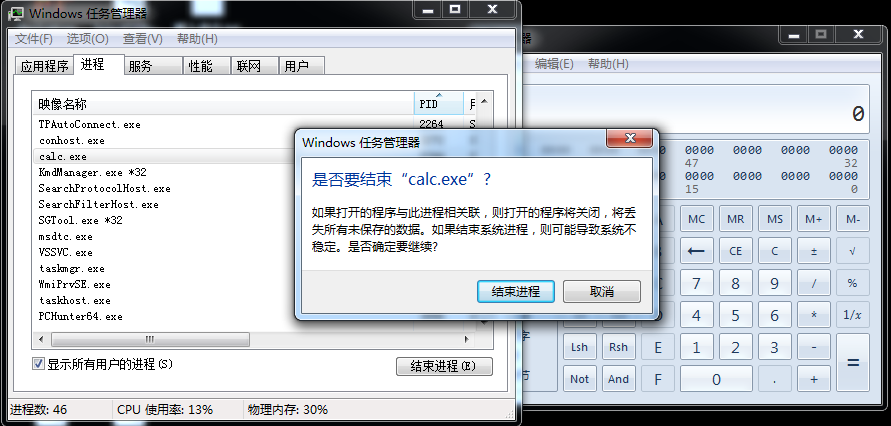
结果是不能关闭的
文件保护
#ifndef CXX_FILEPROTECTX64_H
#define CXX_FILEPROTECTX64_H
#include <ntifs.h>
#include <devioctl.h>
NTSTATUS
DriverEntry(IN PDRIVER_OBJECT DriverObject, IN PUNICODE_STRING RegisterPath);
VOID UnloadDriver(PDRIVER_OBJECT DriverObject);
typedef struct _LDR_DATA_TABLE_ENTRY64
{
LIST_ENTRY64 InLoadOrderLinks;
LIST_ENTRY64 InMemoryOrderLinks;
LIST_ENTRY64 InInitializationOrderLinks;
PVOID DllBase;
PVOID EntryPoint;
ULONG SizeOfImage;
UNICODE_STRING FullDllName;
UNICODE_STRING BaseDllName;
ULONG Flags;
USHORT LoadCount;
USHORT TlsIndex;
PVOID SectionPointer;
ULONG CheckSum;
PVOID LoadedImports;
PVOID EntryPointActivationContext;
PVOID PatchInformation;
LIST_ENTRY64 ForwarderLinks;
LIST_ENTRY64 ServiceTagLinks;
LIST_ENTRY64 StaticLinks;
PVOID ContextInformation;
ULONG64 OriginalBase;
LARGE_INTEGER LoadTime;
} LDR_DATA_TABLE_ENTRY64, *PLDR_DATA_TABLE_ENTRY64; typedef struct _OBJECT_TYPE_INITIALIZER
{
UINT16 Length;
union
{
UINT8 ObjectTypeFlags;
struct
{
UINT8 CaseInsensitive : ; UINT8 UnnamedObjectsOnly : ; UINT8 UseDefaultObject : ; UINT8 SecurityRequired : ; UINT8 MaintainHandleCount : ; UINT8 MaintainTypeList : ; UINT8 SupportsObjectCallbacks : ;
};
};
ULONG32 ObjectTypeCode;
ULONG32 InvalidAttributes;
struct _GENERIC_MAPPING GenericMapping;
ULONG32 ValidAccessMask;
ULONG32 RetainAccess;
enum _POOL_TYPE PoolType;
ULONG32 DefaultPagedPoolCharge;
ULONG32 DefaultNonPagedPoolCharge;
PVOID DumpProcedure;
PVOID OpenProcedure;
PVOID CloseProcedure;
PVOID DeleteProcedure;
PVOID ParseProcedure;
PVOID SecurityProcedure;
PVOID QueryNameProcedure;
PVOID OkayToCloseProcedure;
}OBJECT_TYPE_INITIALIZER, *POBJECT_TYPE_INITIALIZER; typedef struct _OBJECT_TYPE_TEMP
{
struct _LIST_ENTRY TypeList;
struct _UNICODE_STRING Name;
VOID* DefaultObject;
UINT8 Index;
UINT8 _PADDING0_[0x3];
ULONG32 TotalNumberOfObjects;
ULONG32 TotalNumberOfHandles;
ULONG32 HighWaterNumberOfObjects;
ULONG32 HighWaterNumberOfHandles;
UINT8 _PADDING1_[0x4];
struct _OBJECT_TYPE_INITIALIZER TypeInfo;
ULONG64 TypeLock;
ULONG32 Key;
UINT8 _PADDING2_[0x4];
struct _LIST_ENTRY CallbackList;
}OBJECT_TYPE_TEMP, *POBJECT_TYPE_TEMP; VOID EnableObType(POBJECT_TYPE ObjectType);
UNICODE_STRING GetFilePathByFileObject(PVOID FileObject);
OB_PREOP_CALLBACK_STATUS PreCallBack(PVOID RegistrationContext, POB_PRE_OPERATION_INFORMATION OperationInformation);
NTSTATUS ProtectFileByObRegisterCallbacks();
#endif #ifndef CXX_FILEPROTECTX64_H
# include "FileProtectX64.h"
#endif
PVOID CallBackHandle = NULL;
NTSTATUS
DriverEntry(IN PDRIVER_OBJECT DriverObject, IN PUNICODE_STRING RegisterPath)
{ PLDR_DATA_TABLE_ENTRY64 ldr;
DriverObject->DriverUnload = UnloadDriver;
ldr = (PLDR_DATA_TABLE_ENTRY64)DriverObject->DriverSection;
ldr->Flags |= 0x20;
ProtectFileByObRegisterCallbacks();
return STATUS_SUCCESS;
}
NTSTATUS ProtectFileByObRegisterCallbacks()
{
OB_CALLBACK_REGISTRATION CallBackReg;
OB_OPERATION_REGISTRATION OperationReg;
NTSTATUS Status; EnableObType(*IoFileObjectType); //开启文件对象回调
memset(&CallBackReg, , sizeof(OB_CALLBACK_REGISTRATION));
CallBackReg.Version = ObGetFilterVersion();
CallBackReg.OperationRegistrationCount = ;
CallBackReg.RegistrationContext = NULL;
RtlInitUnicodeString(&CallBackReg.Altitude, L"");
memset(&OperationReg, , sizeof(OB_OPERATION_REGISTRATION)); //初始化结构体变量 OperationReg.ObjectType = IoFileObjectType;
OperationReg.Operations = OB_OPERATION_HANDLE_CREATE|OB_OPERATION_HANDLE_DUPLICATE; OperationReg.PreOperation = (POB_PRE_OPERATION_CALLBACK)&PreCallBack; //在这里注册一个回调函数指针
CallBackReg.OperationRegistration = &OperationReg; //注意这一条语句 将结构体信息放入大结构体
Status = ObRegisterCallbacks(&CallBackReg, &CallBackHandle);
if (!NT_SUCCESS(Status))
{
Status = STATUS_UNSUCCESSFUL;
}
else
{
Status = STATUS_SUCCESS;
}
return Status;
} OB_PREOP_CALLBACK_STATUS PreCallBack(PVOID RegistrationContext, POB_PRE_OPERATION_INFORMATION OperationInformation)
{
UNICODE_STRING uniDosName;
UNICODE_STRING uniFilePath;
PFILE_OBJECT FileObject = (PFILE_OBJECT)OperationInformation->Object;
HANDLE CurrentProcessId = PsGetCurrentProcessId();
if( OperationInformation->ObjectType!=*IoFileObjectType)
{
return OB_PREOP_SUCCESS;
}
//过滤无效指针
if( FileObject->FileName.Buffer==NULL ||
!MmIsAddressValid(FileObject->FileName.Buffer) ||
FileObject->DeviceObject==NULL ||
!MmIsAddressValid(FileObject->DeviceObject) )
{
return OB_PREOP_SUCCESS;
}
uniFilePath = GetFilePathByFileObject(FileObject);
if (uniFilePath.Buffer==NULL||uniFilePath.Length==)
{
return OB_PREOP_SUCCESS;
}
if(wcsstr(uniFilePath.Buffer,L"D:\\Test.txt"))
{
if (FileObject->DeleteAccess==TRUE||FileObject->WriteAccess==TRUE)
{
if (OperationInformation->Operation == OB_OPERATION_HANDLE_CREATE)
{
OperationInformation->Parameters->CreateHandleInformation.DesiredAccess=;
}
if(OperationInformation->Operation == OB_OPERATION_HANDLE_DUPLICATE)
{
OperationInformation->Parameters->DuplicateHandleInformation.DesiredAccess=;
}
}
}
RtlVolumeDeviceToDosName(FileObject->DeviceObject, &uniDosName);
DbgPrint("PID : %ld File : %wZ %wZ\r\n", (ULONG64)CurrentProcessId, &uniDosName, &uniFilePath);
return OB_PREOP_SUCCESS;
}
UNICODE_STRING GetFilePathByFileObject(PVOID FileObject)
{
POBJECT_NAME_INFORMATION ObjetNameInfor;
if (NT_SUCCESS(IoQueryFileDosDeviceName((PFILE_OBJECT)FileObject, &ObjetNameInfor)))
{
return ObjetNameInfor->Name;
}
}
VOID EnableObType(POBJECT_TYPE ObjectType)
{
POBJECT_TYPE_TEMP ObjectTypeTemp = (POBJECT_TYPE_TEMP)ObjectType;
ObjectTypeTemp->TypeInfo.SupportsObjectCallbacks = ;
}
VOID UnloadDriver(PDRIVER_OBJECT DriverObject)
{
if (CallBackHandle!=NULL)
{
ObUnRegisterCallbacks(CallBackHandle);
}
DbgPrint("UnloadDriver\r\n");
}
Win7 x64下进程保护与文件保护(ObRegisterCallbacks)的更多相关文章
- x64下进程保护HOOK
目录 x64(32)下的进程保护回调. 一丶进程保护线程保护 1.简介以及原理 1.2 代码 1.3注意的问题 二丶丶回调函数写法 2.1 遇到的问题. 2.2 回调代码 x64(32)下的进程保护回 ...
- [转载] 关于Win7 x64下过TP保护的一些思路,内核层过保护,驱动过保护
首先特别感谢梦老大,本人一直没搞懂异常处理机制,看了他的教程之后终于明白了.在他的教程里我学到了不少东西.第一次在论坛发帖,就说说Win7 x64位下怎么过TP保护.如果有讲错的地方,还望指出.说不定 ...
- 关于Win7 x64下过TP保护(应用层)(转)
非常感谢大家那么支持我上一篇教程.Win10 快出了,所以我打算尽快把应用层的部分说完. 调试对象:DXF调试工具:CE.OD.PCHunter.Windbg调试先言:TP的应用层保护做得比较多,包括 ...
- Oracle学习笔记1:win7 x64下安装Oracle10g
oracle 10g在win7x64下的安装: 第一次直接双击setup,出错了…… 可能是兼容性的问题,所以试着 右击setup-->属性-->兼容性-->勾上"以兼容模 ...
- WIN7 X64 下 VS2008升级补丁 (显示隐藏按钮)
原文地址:http://blog.sina.com.cn/s/blog_57b5da120100gk7l.html 更新列表: 2010年3月26日:增加对日文版的支持. 2010年3月3日:更新代码 ...
- pcl 1.8 + VS 2010 在win7 x64下的配置
https://blog.csdn.net/zhangping560/article/details/53978011 版权声明:(转载请注明作者和出处:http://blog.csdn.net/zh ...
- WIN7 x64下java 8的环境变量配置
Oracle官网下载JDK进行安装:我下载的是Java 8 JDK,地址:http://www.oracle.com/technetwork/java/javase/downloads/jdk8-do ...
- X64下MmIsAddressValid的逆向及内存寻址解析
标 题: [原创]X64下MmIsAddressValid的逆向及内存寻址解析 作 者: 普通朋友 时 间: 2015-10-21,20:03:52 链 接: http://bbs.pediy.com ...
- 如何在Win7 x64上的配置32位的PostgreSQL ODBC数据源
在Win7 x64下安装最新版的PostgreSQL 9.x 后,从其官网下载最新的 ODBC驱动,分为普通的32位和64位版本,正常安装后,从已安装软件列表里可以看到两个版本的驱动都已经正确显示出来 ...
随机推荐
- spring的声明式事务内部图
- jQuery事件绑定方式(转)
bind() 简要描述 bind()向匹配元素添加一个或多个事件处理器. 使用方式 $(selector).bind(event,data,function) event:必需项:添加到元素的一个或多 ...
- 【javascript】js 判断微信浏览器
上周接到个需求,需求是这样的:用户扫一扫二维码会产生一个链接,该链接会向后端发送个请求,返回一个 apk 的下载地址,用户点击下载按钮可以下载此 apk.然后就发生了问题,经过测试,发现用微信扫一扫打 ...
- Linux makefile教程之总述二[转]
Makefile 总述——————— 一.Makefile里有什么? Makefile里主要包含了五个东西:显式规则.隐晦规则.变量定义.文件指示和注释. 1.显式规则.显式规则说明了,如何生成一个或 ...
- js实现密码加密
http://www.cnblogs.com/mofish/archive/2012/02/25/2367858.html 1.base64加密 在页面中引入base64.js文件,调用方法为: &l ...
- jQuery遮罩插件jQuery.blockUI.js简介
利用Jquery.blockui.js创建可拖动.自定义内容的弹出层 利用Jquery.blockui.js创建可拖动.自定义内容的弹出层 目标 : 1 . 弹出层的内容可以自定义任意的HTML元素 ...
- 【剑指offer 面试题47】不用加减乘除做加法
思路: 利用位运算 C++: #include <iostream> using namespace std; int main() { , b = ; int sum, carry; d ...
- 九度 Online Judge 之《剑指 Offer》一书相关题目解答
前段时间准备华为机试,正好之前看了一遍<剑指 Offer>,就在九度 Online Judge 上刷了书中的题目,使用的语言为 C++:只有3题没做,其他的都做了. 正如 Linus To ...
- Web前端开发工程师编程能力飞升之路
[背景] 如果你是刚进入web前端研发领域,想试试这潭水有多深,看这篇文章吧:如果你是做了两三年web产品前端研发,迷茫找不着提高之路,看这篇文章吧:如果你是四五年的前端开发高手,没有难题能难得住你的 ...
- C语言实现strlen
strlen: #ifndef STRLEN_H #define STRLEN_H #include <stdio.h> // 参考微软的写法 int cat_strlen(const c ...
