Lab 6-2
Analyze the malware found in the file Lab06-02.exe.
Questions and Short Answers
What operation does the first subroutine called by main perform?
A: The first subroutine at 0x401000 is the same as in Lab 6-1. It’s an
ifstatement that checks for an active Internet connection.What is the subroutine located at 0x40117F?
A:
printfis the subroutine located at 0x40117F.What does the second subroutine called by main do?
A: The second function called from main is located at 0x401040. It downloads the web page located at: http://www.practicalmalwareanalysis.com/cc.htm and parses an HTML comment from the beginning of the page.
What type of code construct is used in this subroutine?
A: This subroutine uses a character array filled with data from the call to InternetReadFile. This array is compared one byte at a time to parse an HTML comment.
Are there any network-based indicators for this program?
A: There are two network-based indicators. The program uses the HTTP User-Agent Internet Explorer 7.5/pma and downloads the web page located at: http://www.practicalmalwareanalysis.com/cc.htm.
What is the purpose of this malware?
A: First, the program checks for an active Internet connection. If none is found, the program terminates. Otherwise, the program attempts to download a web page using a unique User-Agent. This web page contains an embedded HTML comment starting with <!--. The next character is parsed from this comment and printed to the screen in the format “Success: Parsed command is X,” where X is the character parsed from the HTML comment. If successful, the program will sleep for 1 minute and then terminate.
Detailed Analysis
We begin by performing basic static analysis on the binary. We see several new strings of interest, as shown in Listing 6-1L.(使用 IDA 也可以查看字符串,但是没有这个全。IDA 可能有遗漏)
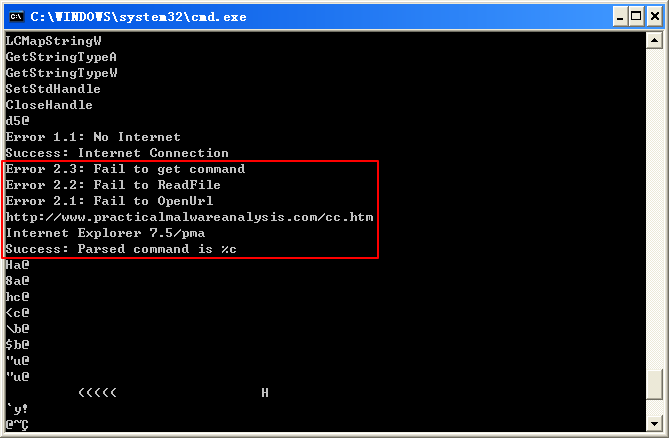
Listing 6-1L: Interesting new strings contained in Lab 6-2
The three error message strings that we see suggest that the program may open a web page and parse a command. We also notice a URL for an HTML web page, http://www.practicalmalwareanalysis.com/cc.htm. This domain can be used immediately as a network-based indicator.
These imports contain several new Windows API functions used for networking, as shown in Listing 6-2L.
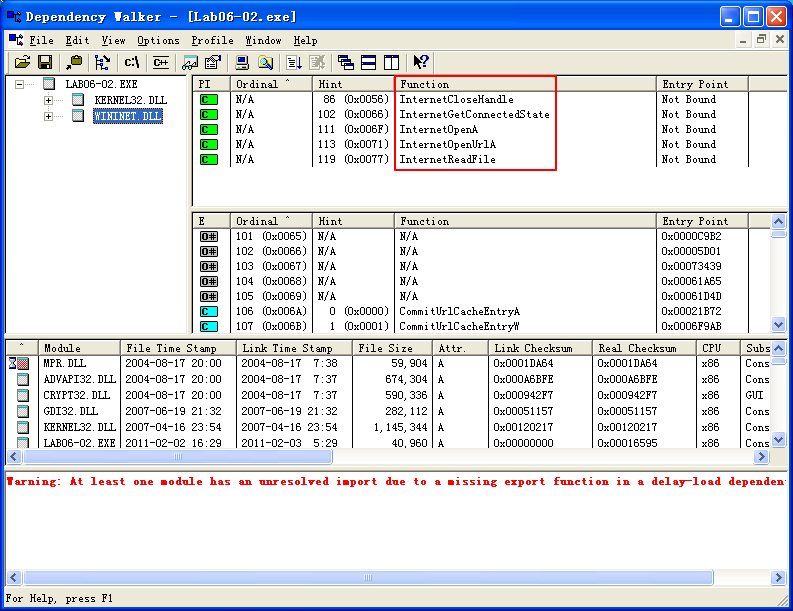
Listing 6-2L: Interesting new import functions contained in Lab 6-2
All of these functions are part of WinINet, a simple API for using HTTP over a network. They work as follows:
- InternetOpenA is used to initialize the use of the WinINet library, and it sets the User-Agent used for HTTP communication.
- InternetOpenUrlA is used to open a handle to a location specified by a complete FTP or HTTP URL. (Programs use handles to access something that has been opened. We discuss handles in Chapter 7.)
- InternetReadFile is used to read data from the handle opened by InternetOpenUrlA.
- InternetCloseHandle is used to close the handles opened by these files.
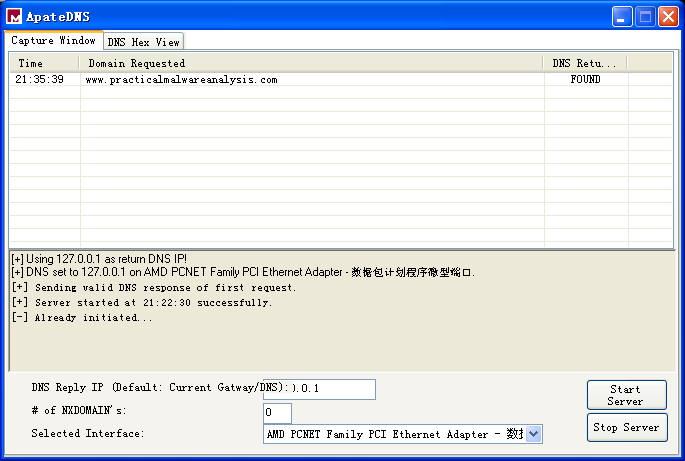
Next, we perform dynamic analysis. We choose to listen on port 80 because WinINet often uses HTTP and we saw a URL in the strings. If we set up Netcat to listen on port 80 and redirect the DNS accordingly, we will see a DNS query for www.practicalmalwareanalysis.com, after which the program requests a web page from the URL, as shown in Listing 6-3L. This tells us that this web page has some significance to the malware, but we won’t know what that is until we analyze the disassembly.
利用 ApateDNS,把对 www.practicalmalwareanalysis.com 的 DNS 查询请求重定向到本机 127.0.0.1。假设恶意代码是出去访问 80 端口的(这也是一种普遍的选择),我们就可以在执行恶意代码之前,用 Netcat 监听连接。
恶意代码频繁使用 80 端口或 443 端口(HTTP 或 HTTPS 端口),因为它们作为外出连接目标端口通常不会被封禁或者监听。
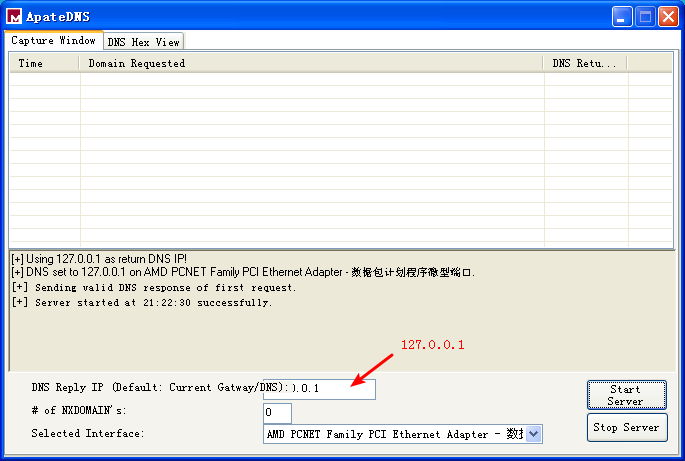
点击 Start Server,然后使用 Natcat 监听 80 端口:
执行 Lab06-02.exe:
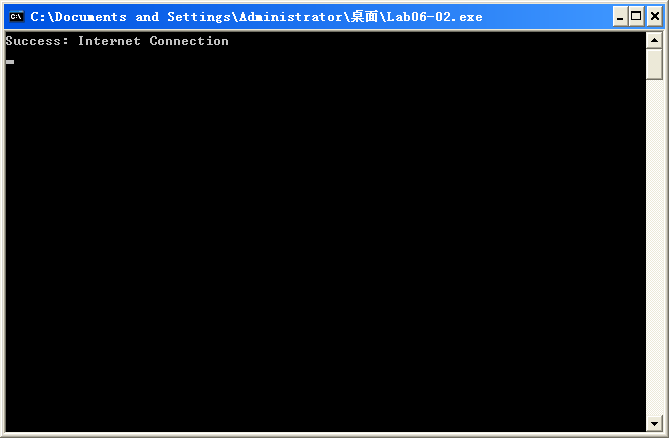

Listing 6-3L: Netcat output when listening on port 80
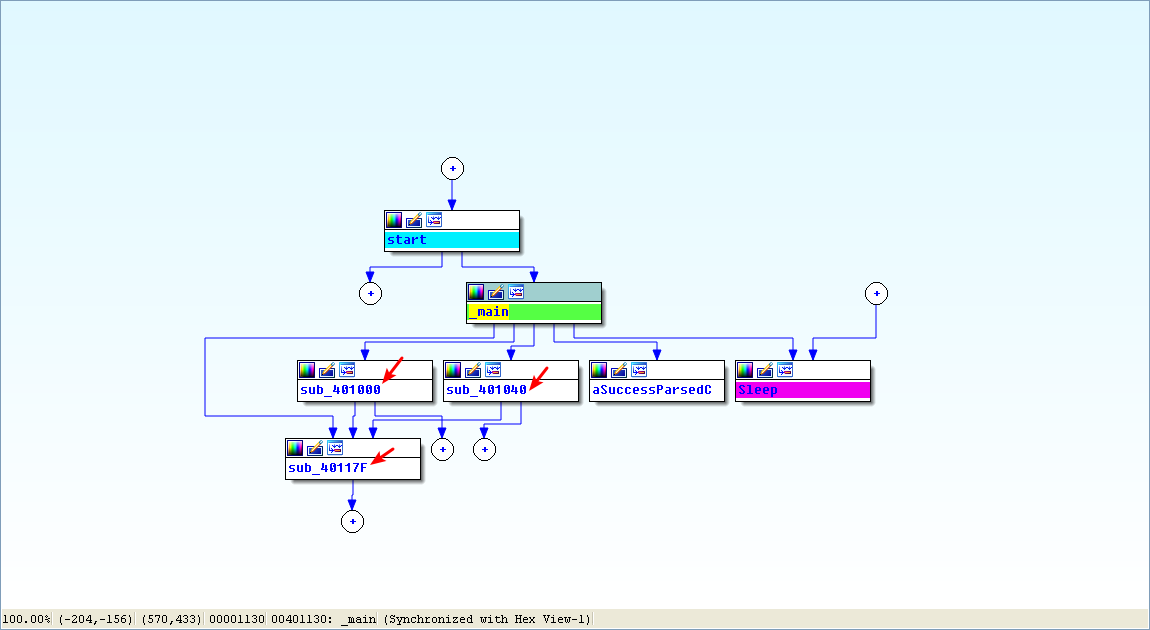
Finally, we load the executable into IDA Pro. We begin our analysis with the main method since much of the other code is generated by the compiler. Looking at the disassembly for main, we notice that it calls the same method at 0x401000 that we saw in Lab 6-1. However, two new calls (401040 and 40117F) in the main method were not in Lab 6-1.

In the new call to 0x40117F, we notice that two parameters are pushed on the stack before the call. One parameter is the format string Success: Parsed command is %c, and the other is the byte returned from the previous call at 0x401148. Format characters such as %c and %d tell us that we’re looking at a format string. Therefore, we can deduce that printf is the subroutine located at 0x40117F, and we should rename it as such, so that it’s renamed everywhere it is referenced. The printf subroutine will print the string with the %c replaced by the other parameter pushed on the stack.

Next, we examine the new call to 0x401040. This function contains all of the WinINet API calls we discovered during the basic static analysis process. It first calls InternetOpen, which initializes the use of the WinINet library. Notice that Internet Explorer 7.5/pma is pushed on the stack, matching the User-Agent we noticed during dynamic analysis. The next call is to InternetOpenUrl, which opens the static web page pushed onto the stack as a parameter. This function caused the DNS request we saw during dynamic analysis.

Listing 6-4L shows the InternetOpenUrlA and the InternetReadFile calls.
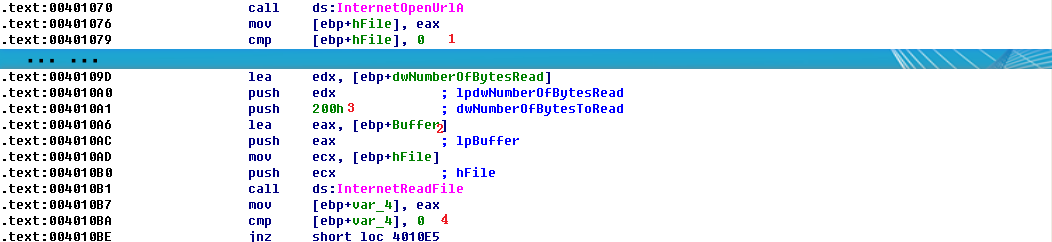
Listing 6-4L: InternetOpenUrlA and InternetReadFile calls
We can see that the return value from InternetOpenUrlA is moved into the local variable hFile and compared to 0 at \({\color{red}1}\). If it is 0, this function will be terminated; otherwise, the hFile variable will be passed to the next function, InternetReadFile. The hFile variable is a handle—a way to access something that has been opened. This handle is accessing a URL.
InternetReadFile is used to read the web page opened by InternetOpenUrlA. If we read the MSDN page on this API function, we can learn about the other parameters. The most important of these parameters is the second one, which IDA Pro has labels Buffer, as shown at \({\color{red}2}\). Buffer is an array of data, and in this case, we will be reading up to 0x200 bytes worth of data, as shown by the NumberOfBytesToRead parameter at \({\color{red}3}\). Since we know that this function is reading an HTML web page, we can think of Buffer as an array of characters.
Following the call to InternetReadFile, code at \({\color{red}4}\) checks to see if the return value (EAX) is 0. If it is 0, the function closes the handles and terminates; if not, the code immediately following this line compares Buffer one character at a time, as shown in Listing 6-5L. Notice that each time, the index into Buffer goes up by 1 before it is moved into a register, and then compared.

Listing 6-5L: Buffer handling
At \({\color{red}5}\), the cmp instruction checks to see if the first character is equal to 0x3C, which corresponds to the < symbol in ASCII. We can right-click on 3Ch, and IDA Pro will offer to change it to display <. In the same way, we can do this throughout the listing for 21h, 2Dh, and 2Dh. If we combine the characters, we will have the string <!--, which happens to be the start of a comment in HTML. (HTML comments are not displayed when viewing web pages in a browser, but you can see them by viewing the web page source.)
Notice at \({\color{red}6}\) that Buffer+1 is moved into EDX before it is compared to 0x21 (! in ASCII). Therefore, we can assume that Buffer is an array of characters from the web page downloaded by InternetReadFile. Since Buffer points to the start of the web page, the four cmp instructions are used to check for an HTML comment immediately at the start of the web page. If all comparisons are successful, the web page starts with the embedded HTML comment, and the code at \({\color{red}7}\) is executed. (Unfortunately, IDA Pro fails to realize that the local variable Buffer is of size 512 and has displayed a local variable named var_20C instead.)
We need to fix the stack of this function to display a 512-byte array in order for the Buffer array to be labeled properly throughout the function. We can do this by pressing CTRL-K anywhere within the function. For example, the left side of Figure 6-2L shows the initial stack view. To fix the stack, we right-click on the first byte of Buffer and define an array 1 byte wide and 512 bytes large. The down side of the figure shows what the corrected stack should look like.

Figure 6-2L: Creating an array and fixing the stack
Manually adjusting the stack like this will cause the instruction numbered \({\color{red} 7 }\) in Listing 6-5L to be displayed as [ebp+Buffer+4]. Therefore, if the first four characters (Buffer[0]-Buffer[3]) match <!--, the fifth character will be moved into AL and returned from this function.
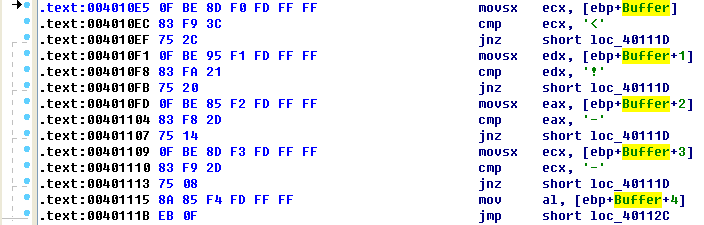
注:对照着 Listing 6-5L 看
Returning to the main method, let’s analyze what happens after the 0x401040 function returns. If this function returns a nonzero value, the main method will print as “Success: Parsed command is X,” where X is the character parsed from the HTML comment, followed by a call to the Sleep function at 0x401173. Using MSDN, we learn that the Sleep function takes a single parameter containing the number of milliseconds to sleep. It pushes 0xEA60 on the stack, which corresponds to sleeping for one minute (60,000 milliseconds).
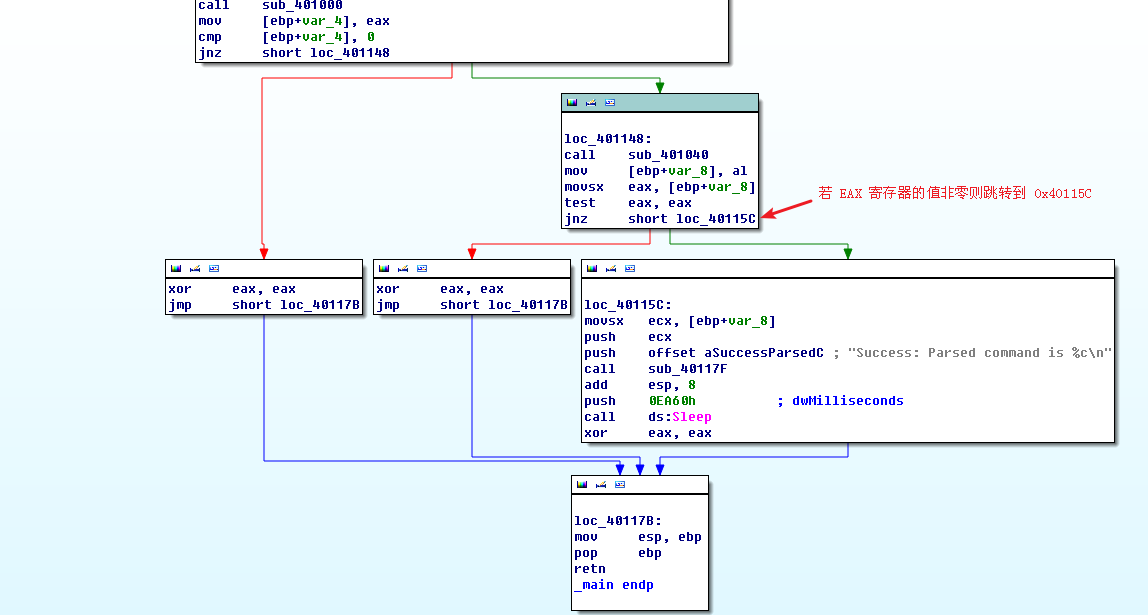
To summarize, this program checks for an active Internet connection, and then downloads a web page containing the string <!--, the start of a comment in HTML. An HTML comment will not be displayed in a web browser, but you can view it by looking at the HTML page source. This technique of hiding commands in HTML comments is used frequently by attackers to send commands to malware while having the malware appear as if it were going to a normal web page.
Preference
Lab 6-2的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- IDEA安装与破解
今天下午偶然在知乎上看到IDEA和eclipse的软件分析,所以装了一个IDEA,不过肯定是破解,不会购买激活码 IDEA官网:http://www.jetbrains.com/idea/ 安装教程: ...
- django基础 -- 1. 前奏 web框架的本质
一. http协议 1.请求方法(get和post) 1.GET提交的数据会放在URL之后,也就是请求行里面,以?分割URL和传输数据,参数之间以&相连,如EditBook?name=test ...
- Django框架(九) Django之ORM常用字段和参数
ORM字段 AutoField int自增列,必须填入参数 primary_key=True.当model中如果没有自增列,则自动会创建一个列名为id的列. IntegerField 一个整数类型,范 ...
- 流程控制if,while,for
if语句 什么是if语句 判断一个条件如果成立则做...不成立则做....为何要有if语句 让计算机能够像人一样具有判断的能力 如何用if语句 语法1: if 条件1: code1 code2 cod ...
- centos在图形界面和命令行之间切换的快捷键是什么?
答: ctrl+alt+F1 或者ctrl+alt+F2 1.当前处于图形界面时,按ctrl+alt+F2可进入命令行模式 2. 当前处于命令行模式,按ctrl+alt+F1可进入图形界面
- Why database migrations?
https://flywaydb.org/getstarted/why First, let's start from the beginning and assume we have a proje ...
- 浅谈 Make 命令
代码变成可执行文件,叫做编译(compile):先编译这个,还是先编译那个(即编译的安排),叫做构建(build). Make是最常用的构建工具,诞生于1977年,主要用于C语言的项目.但是实际上 , ...
- pom.xml中build标签
1.分类 (1)全局配置(project build) 针对整个项目的所有情况都有效 (2)配置(profile build) 针对不同的profile配置 <project xmlns=&qu ...
- BMv2 simple_switch 运行时切换P4程序
参考: [P4-dev] swapping p4 program using load_new_config and swap_configs commands BMv2 运行时切换P4程序 相关演示 ...
- jquery.validate使用详解
一.简单应用实例: 1.用class样式进行验证,用法简单,但不能自定义错误信息,只能修改jquery-1.4.1.min.js中的内置消息,也不支持高级验证规则. <script type=& ...
