Lab 9-3
Analyze the malware found in the file Lab09-03.exe using OllyDbg and IDA Pro. This malware loads three included DLLs (DLL1.dll, DLL2.dll, and DLL3.dll) that are all built to request the same memory load location. Therefore, when viewing these DLLs in OllyDbg versus IDA Pro, code may appear at different memory locations. The purpose of this lab is to make you comfortable with finding the correct location of code within IDA Pro when you are looking at code in OllyDbg.
Questions and Short Answers
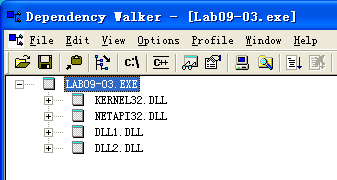
What DLLs are imported by Lab09-03.exe?
A: The import table contains kernel32.dll, NetAPI32.dll, DLL1.dll, and DLL2.dll. The malware dynamically loads user32.dll and DLL3.dll.
What is the base address requested by DLL1.dll, DLL2.dll, and DLL3.dll?
A: All three DLLs request the same base address: 0x10000000.
When you use OllyDbg to debug Lab09-03.exe, what is the assigned based address for: DLL1.dll, DLL2.dll, and DLL3.dll?
A: DLL1.dll is loaded at 0x10000000, DLL2.dll is loaded at 0x320000, and DLL3.dll is loaded at 0x380000 (this may be slightly different on your machine).
When Lab09-03.exe calls an import function from DLL1.dll, what does this import function do?
A:
DLL1Printis called, and it prints “DLL 1 mystery data,” followed by the contents of a global variable.When Lab09-03.exe calls
WriteFile, what is the filename it writes to?A:
DLL2ReturnJreturns a filename of temp.txt which is passed to the call toWriteFile.When Lab09-03.exe creates a job using
NetScheduleJobAdd, where does it get the data for the second parameter?A: Lab09-03.exe gets the buffer for the call to
NetScheduleJobAddfromDLL3GetStructure, which it dynamically resolves.While running or debugging the program, you will see that it prints out three pieces of mystery data. What are the following: DLL 1 mystery data 1, DLL 2 mystery data 2, and DLL 3 mystery data 3?
A: Mystery data 1 is the current process identifier, mystery data 2 is the handle to the open temp.txt file, and mystery data 3 is the location in memory of the string
ping www.malwareanalysisbook.com.How can you load DLL2.dll into IDA Pro so that it matches the load address used by OllyDbg?
A: Select Manual Load when loading the DLL with IDA Pro, and then type the new image base address when prompted. In this case, the address is 0x320000.
Detailed Analysis
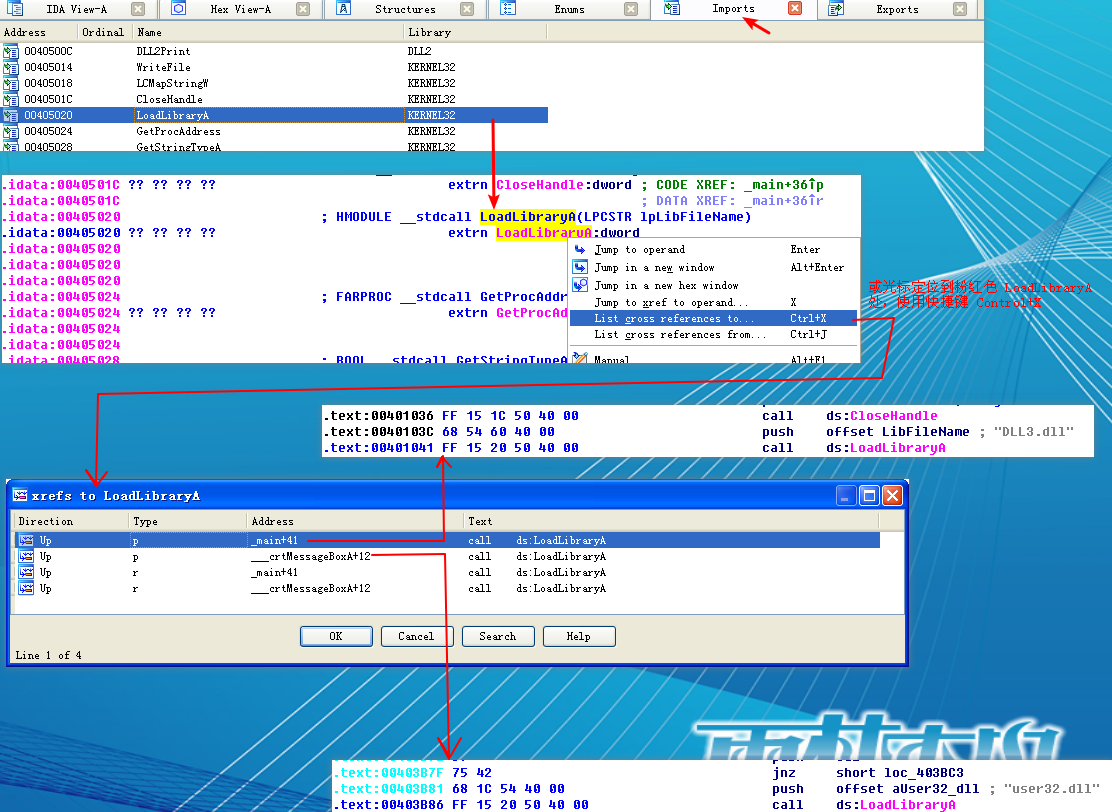
We start by examining the import table of Lab09-03.exe and it contains kernel32.dll, NetAPI32.dll, DLL1.dll, and DLL2.dll. Next, we load Lab09-03.exe into IDA Pro. We look for calls to LoadLibrary and check which strings are pushed on the stack before the call. We see two cross-references to LoadLibrary that push user32.dll and DLL3.dll respectively, so that these DLLs may be loaded dynamically during runtime.
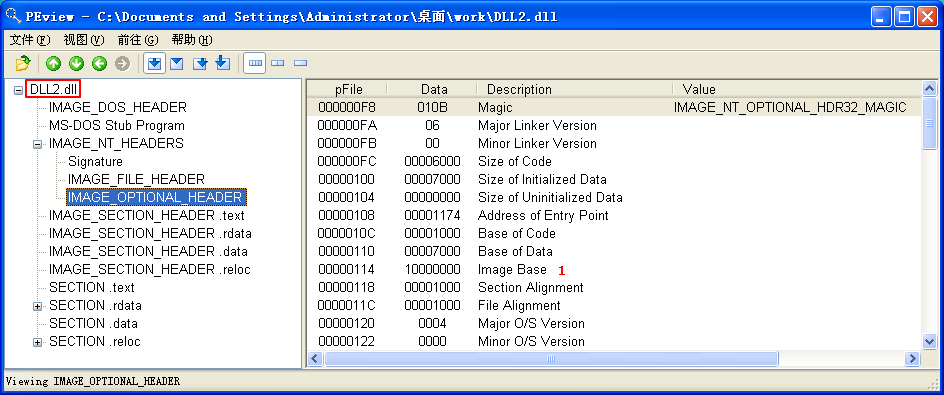
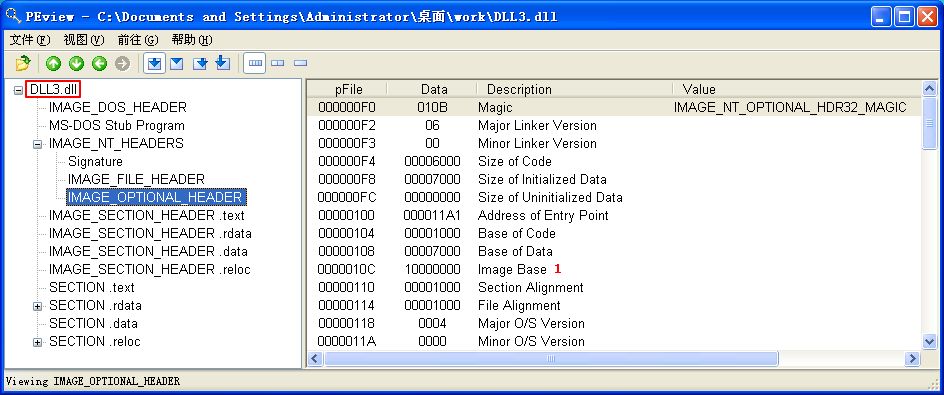
We can check the base address requested by the DLLs by using PEview, as shown in Figure 9-10L. After loading DLL1.dll into PEview, click the IMAGE_OPTIONAL_HEADER and look at the value of Image Base, as shown at \({\color {red} 1}\) in the figure. We repeat this process with DLL2.dll and DLL3.dll, and see that they all request a base address of 0x10000000.

Figure 9-10L: Finding the requested base address with PEview
Using the Memory Map to Locate DLLs
Next, we want to figure out at which memory address the three DLLs are loaded during runtime. DLL1.dll and DLL2.dll are loaded immediately because they’re in the import table. Since DLL3.dll is loaded dynamically, we will need to run the LoadLibrary function located at 0x401041. We can do this by loading Lab09-03.exe into OllyDbg, setting a breakpoint at 0x401041, and clicking play. Once the breakpoint hits, we can step over(F8, 步过) the call to LoadLibrary. At this point, all three DLLs are loaded into Lab09-03.exe.
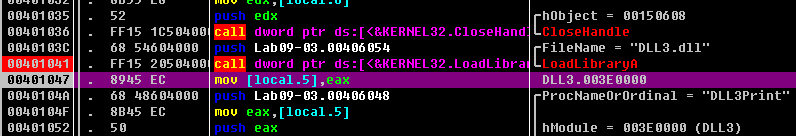
We bring up the memory map by selecting View -> Memory. The memory map is shown in Figure 9-11L (it may appear slightly different on your machine). At \({\color{red} 1}\), we see that DLL1.dll gets its preferred base address of 0x10000000. At \({\color{red} 2}\), we see that DLL2.dll didn’t get its preferred base address because DLL1.dll was already loaded at that location, so DLL2.dll is loaded at 0x380000. Finally, at \({\color{red} 3}\), we see that DLL3.dll is loaded at 0x3E0000.
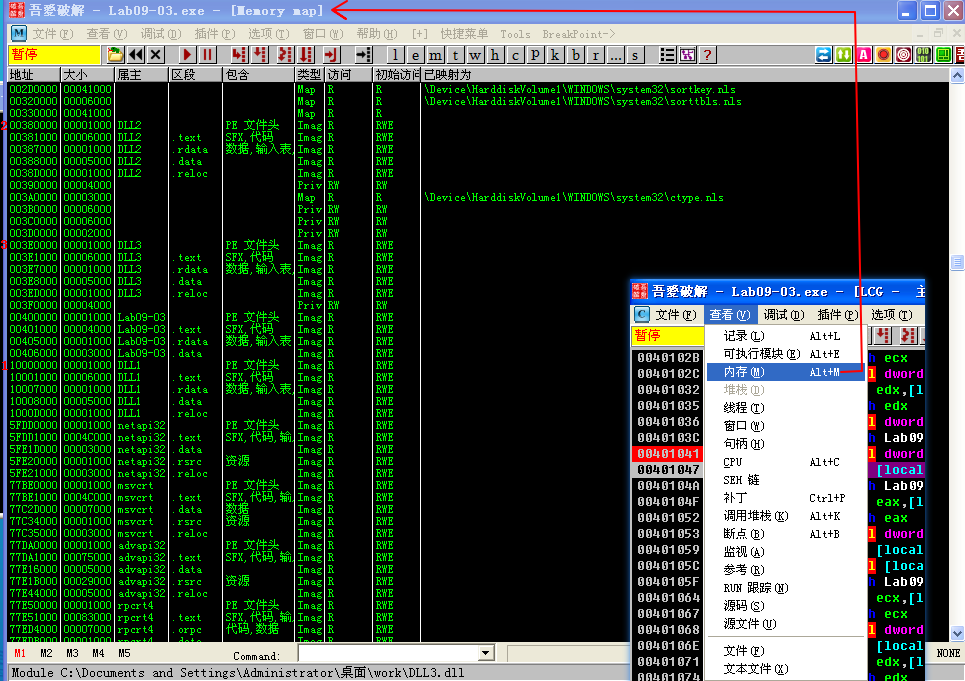
Figure 9-11L: Using the OllyDbg memory map to examine DLL load locations
Listing 9-9L shows the calls to the exports of DLL1.dll and DLL2.dll.


Listing 9-9L: Calls to the exports of DLL1.dll and DLL2.dll from Lab09-03.exe
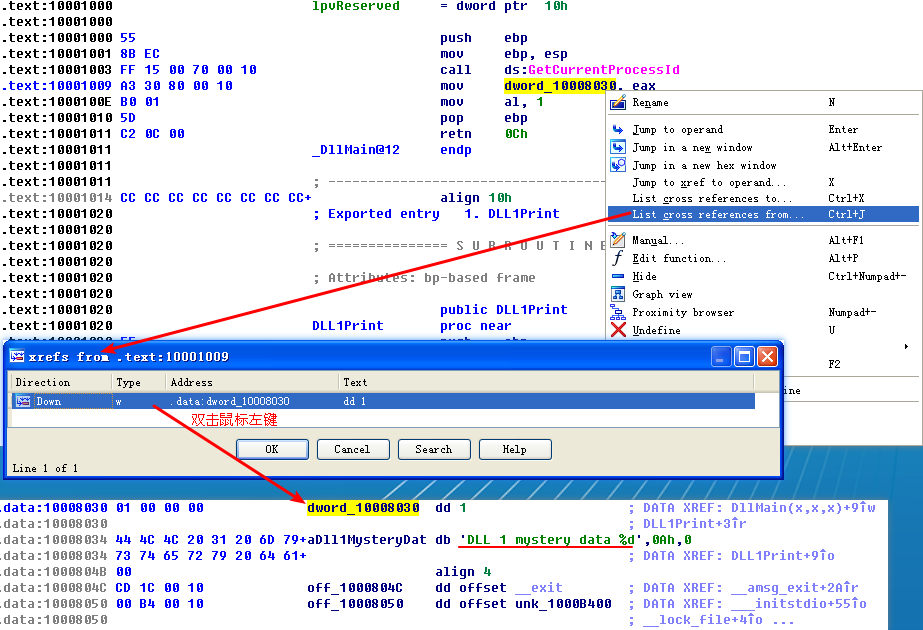
At the start of Listing 9-9L, we see a call to DLL1Print, which is an export of DLL1.dll. We disassemble DLL1.dll with IDA Pro and see that the function prints “DLL 1 mystery data,” followed by the contents of a global variable, dword_10008030. If we examine the cross-references to dword_10008030, we see that it is accessed in DllMain when the return value from the call GetCurrentProcessId is moved into it. Therefore, we can conclude that DLL1Print prints the current process ID, which it determines when the DLL is first loaded into the process.
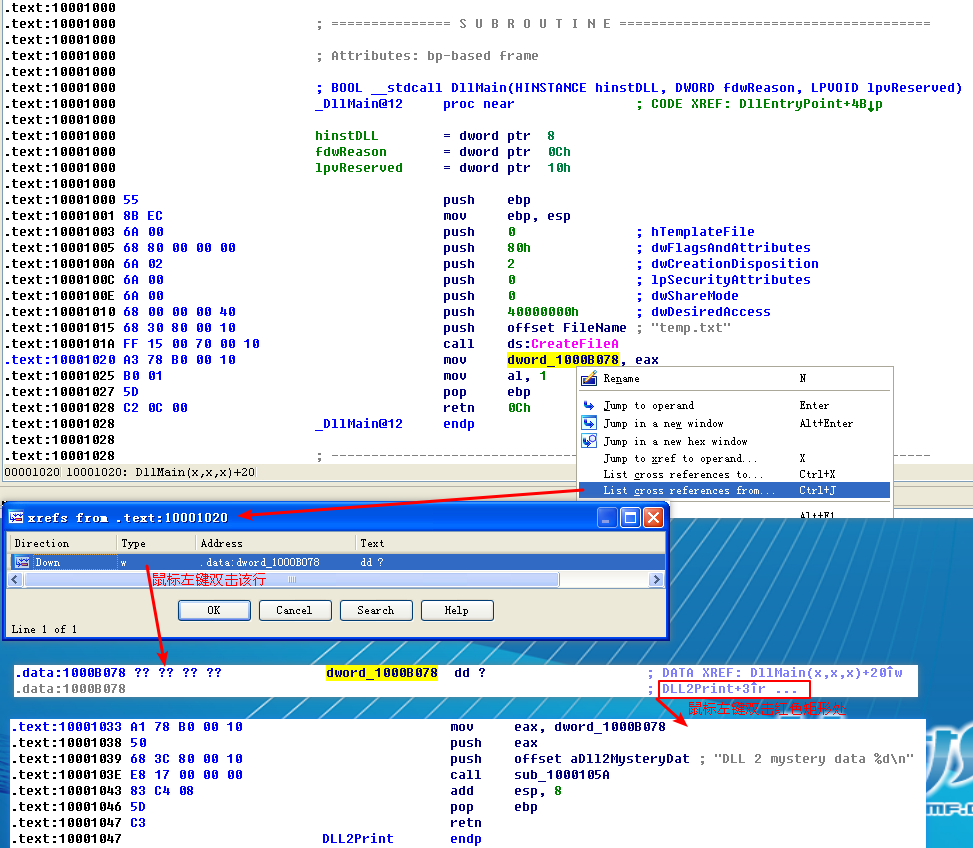
In Listing 9-9L, we see calls to two exports from DLL2.dll: DLL2Print and DLL2ReturnJ. We can disassemble DLL2.dll with IDA Pro and examine DLL2Print to see that it prints “DLL 2 mystery data,” followed by the contents of a global variable, dword_1000B078. If we examine the cross-references to dword_1000B078, we see that it is accessed in DllMain when the handle to CreateFileA is moved into it. The CreateFileA function opens a file handle to temp.txt, which the function creates if it doesn’t already exist. DLL2Print apparently prints the value of the handle for temp.txt. We can look at the DLL2ReturnJ export and find that it returns the same handle that DLL2Print prints. Further in Listing 9-9L, at \({\color{red} 1}\), the handle is moved into hObject, which is passed to WriteFile at \({\color{red} 2}\) defining where malwareanalysisbook.com is written.
After the WriteFile in Lab09-03.exe, DLL3.dll is loaded with a call to LoadLibrary, followed by the dynamic resolution of DLL3Print and DLL3GetStructure using GetProcAddress. First, it calls DLL3Print, which prints “DLL 3 mystery data,” followed by the contents of a global variable found at 0x1000B0C0. When we check the cross-references for the global variable, we see that it is initialized in DllMain to the string ping www.malwareanalysisbook.com, so the memory location of the string will again be printed. DLL3GetStructure appears to return a pointer to the global dword_1000B0A0, but it is unclear what data is in that location. DllMain appears to initialize some sort of structure at this location using data and the string. Since DLL3GetStructure sets a pointer to this structure, we will need to see how Lab09-03.exe uses the data to figure out the contents of the structure. Listing 9-10L shows the call to DLL3GetStructure at \({\color {red} 1}\).

Listing 9-10L: Calls to DLL3GetStructure followed by NetScheduleJobAdd in Lab09-03.exe

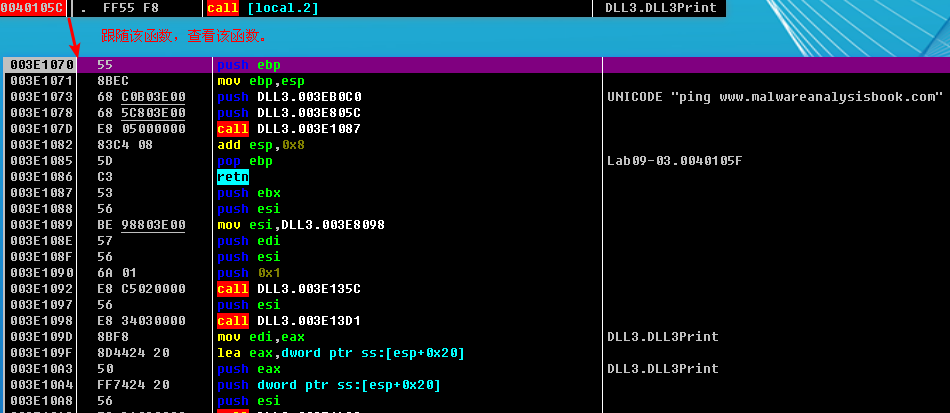
It appears that the result of that call is the structure pointed to by Buffer, which is subsequently passed to NetScheduleJobAdd. Viewing the MSDN page for NetScheduleJobAdd tells us that Buffer is a pointer to an AT_INFO structure.
Applying a Structure in IDA Pro
The AT_INFO structure can be applied to the data in DLL3.dll. First, load DLL3.dll into IDA Pro, press the INSERT key within the Structures window, and add the standard structure AT_INFO. Next, go to dword_1000B0A0 in memory and select Edit -> Struct Var and click AT_INFO. This will cause the data to be more readable, as shown in Listing 9-11L. We can see that the scheduled job will be set to ping malwareanalysisbook.com every day of the week at 1:00 AM.
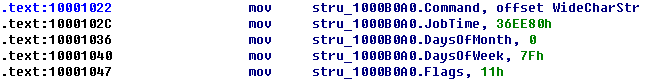
Listing 9-11L: AT_INFO Structure

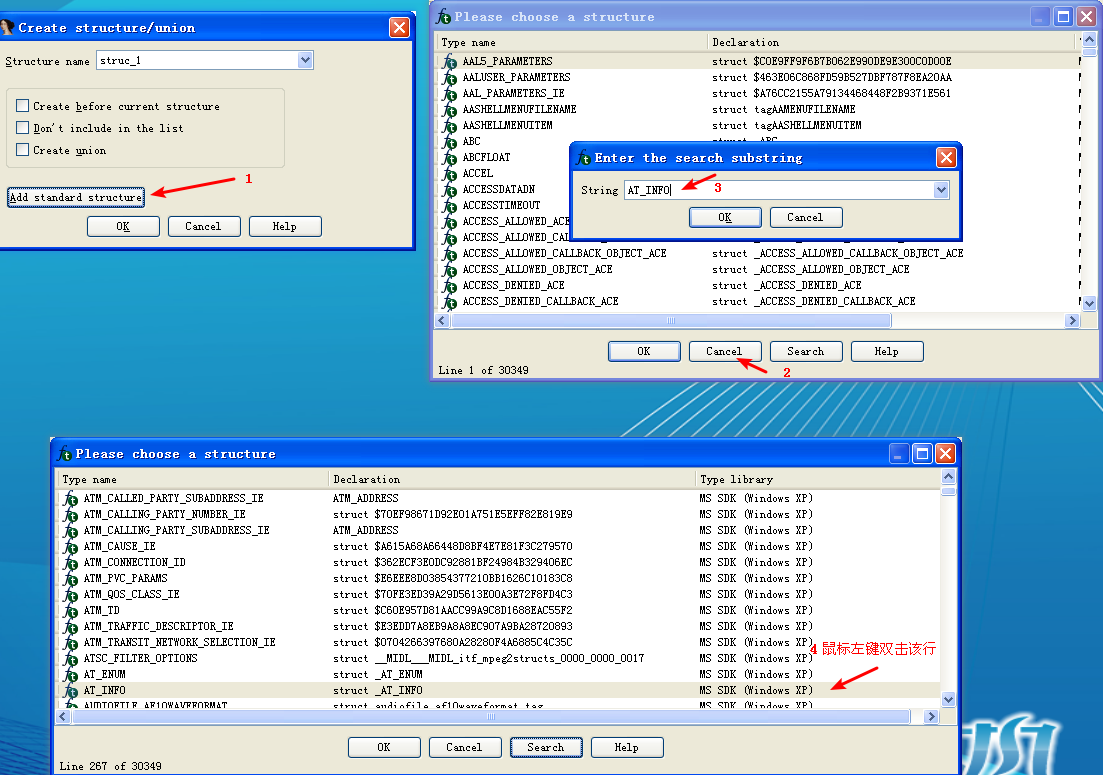
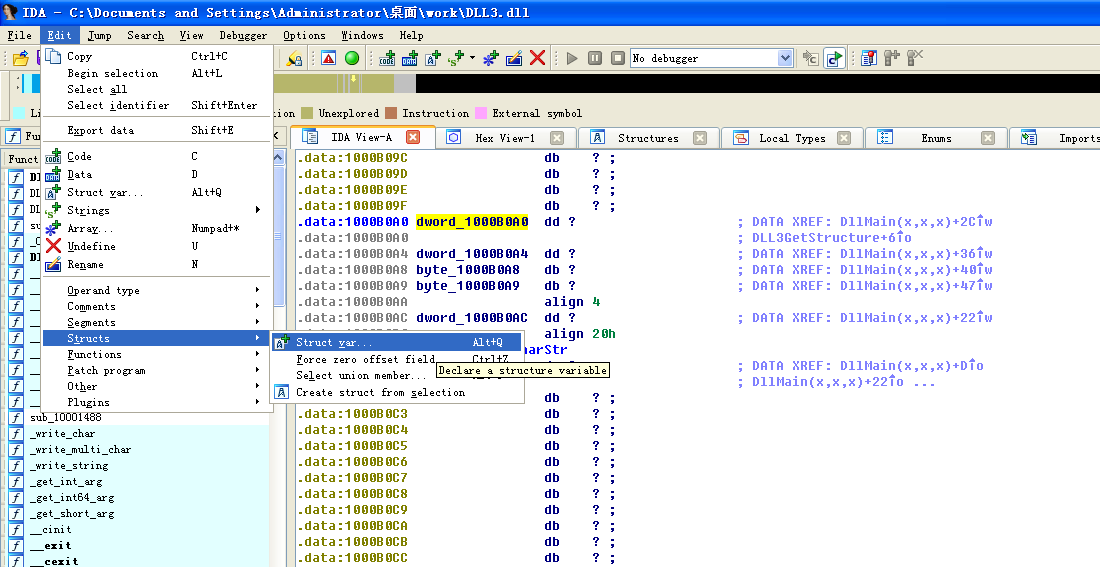

然后键盘按 G 字母键,输入地址 10001022,就能看到效果了:
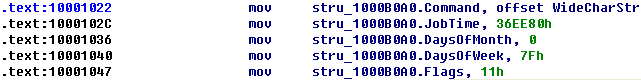
附一张未修改前的:

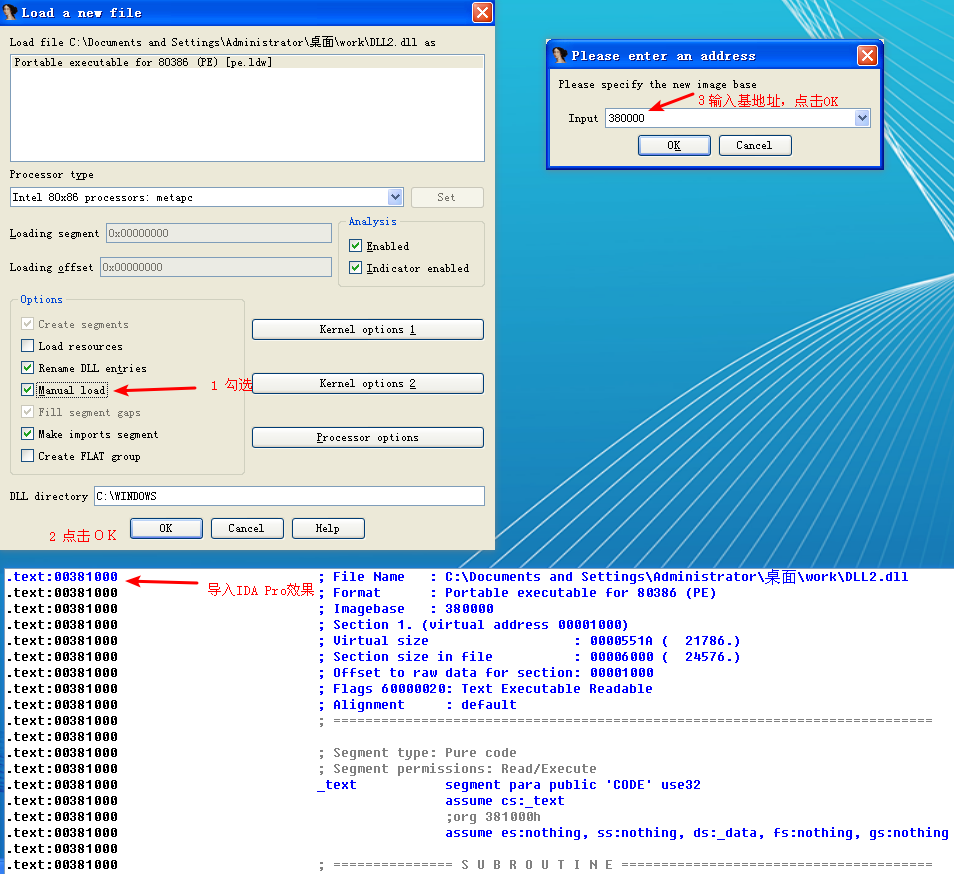
Specifying a New Image Base with IDA Pro
We can load DLL2.dll into IDA Pro in a different location by checking the Manual Load box when loading the DLL. In the field that says Please specify the new image base, we type 380000. IDA Pro will do the rest to adjust all of the offsets, just as OllyDbg did when loading the DLL.
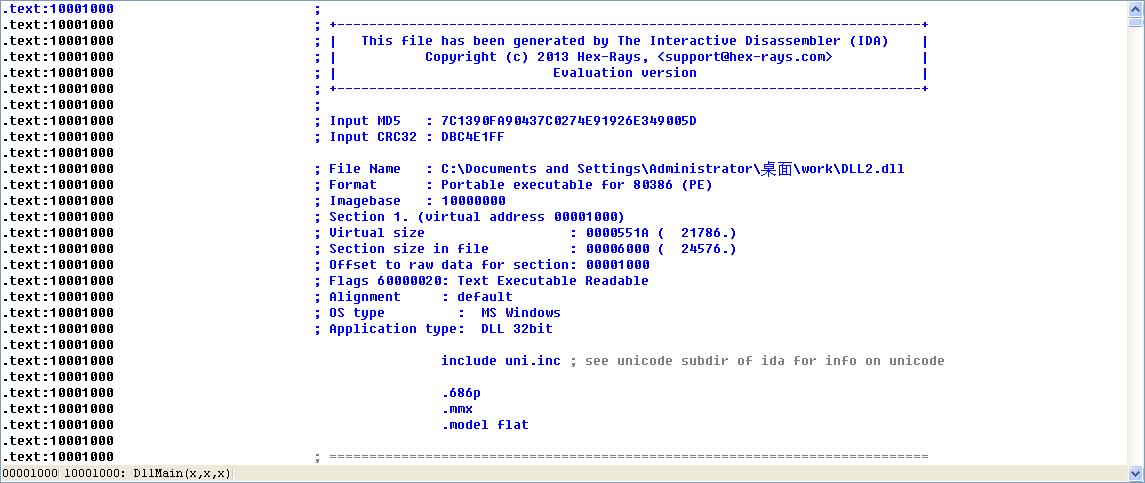
附一张 DLL2.dll 导入 IDA Pro 时没有勾选 Manual Load 的效果:
Malware Summary
This lab demonstrated how to determine where three DLLs are loaded into Lab09-03.exe using OllyDbg. We loaded these DLLs into IDA Pro to perform full analysis, and then figured out the mystery data printed by the malware: mystery data 1 is the current process identifier, mystery data 2 is the handle to the open temp.txt, and mystery data 3 is the location in memory of the string ping www.malwareanalysisbook.com. Finally, we applied the Windows AT_INFO structure within IDA Pro to aid our analysis of DLL3.dll.
Preference
Lab 9-3的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- SQL- 行转列,多行转多列 - max 函数
效果如图,把同一个 code, 按 cate 列相同行的进行合并后分两行,把mode 每种类型转换成 列名 ,主要用到了 max 函数,很实用 if exists(select * from temp ...
- 【SW4STM32生成 hex文件的设置方法】
SW4STM32生成 hex文件的设置方法 开发环境:WIN7_64 + SW4STM32 联系方式:yexiaopeng1992@126.com 修改: 2018年1月21日 在这周,有一个热心的 ...
- linux下tomcat的https访问
1.安装JDK(省略…) 2.安装tomcat(省略…) 3.配置SSL 进入JDK的安装目录 # cd /usr/java/jdk1..0_03/bin # ./keytool -genkey -a ...
- 2018-2019-2 20165215《网络对抗技术》Exp5 MSF基础应用
目录 实验内容 实验原理 实验步骤 (一)一个主动攻击实践 ms08_067(成功) (二)一个针对浏览器的攻击 ms14_064(成功) (三)一个针对客户端的攻击 Adobe(成功) CVE-20 ...
- Spring restful
1. RESTful 不是一项技术,也不是一个标准,而是一种风格,跟servlet不在一个层面上,根本无法比较.一个基于servlet的application也是可以是符合RESTful风格的,换言之 ...
- MyBatis笔记(一) 最简单的select
小白学习MyBatis的第一天,学习资料包括MyBatis3的官方文档,以及孤傲苍狼大佬的博客.这里先致敬大佬. · 首先,什么是MyBatis? 引用官网的一段话,“MyBatis 是一款优秀的持久 ...
- python3 error 机器学习 错误
AttributeError: 'NoneType' object has no attribute 'sqrt' 这个错误其实是因为 plt.scatter(x[:,0],x[:,1],x[:,2] ...
- AES256对称加密
需要引入bouncycastle库的jar包 package test; import java.io.UnsupportedEncodingException; import java.securi ...
- MySQL5.7 JSON类型及其相关函数的学习
mysql> CREATE TABLE `json_table` ( `id` int(11) NOT NULL AUTO_INCREMENT, `info` json NOT NULL, PR ...
- tcp的三次握手,四次挥手
为了更好的记住知识点,所以将最近学习的知识点记录下来: 最开始A和B都处于closed(关闭连接状态) 1.tcp的第一次握手:客户端A 向服务器端B 发送请求连接报文段(包含SYN=1,初始序号s ...
