Subnet Routing Examples
Routing Table
- Each row in routing table contains:
- Destination IP address
- IP address of next-hop router
- Physical address
- Statistics information
- Flags
- H=1 (0) indicates route is to a host (network)
- G=1 (0) indicates route is to a router (directly connected destination)
Routing Search and Actions
- Routing table search order & action
- Complete destination address; send as per next-hop & G flag
- Destination network ID; send as per next-hop & G flag
- Default router entry; send as per next-hop
- Declare packet undeliverable; send ICMP “host unreachable error” packet to originating host
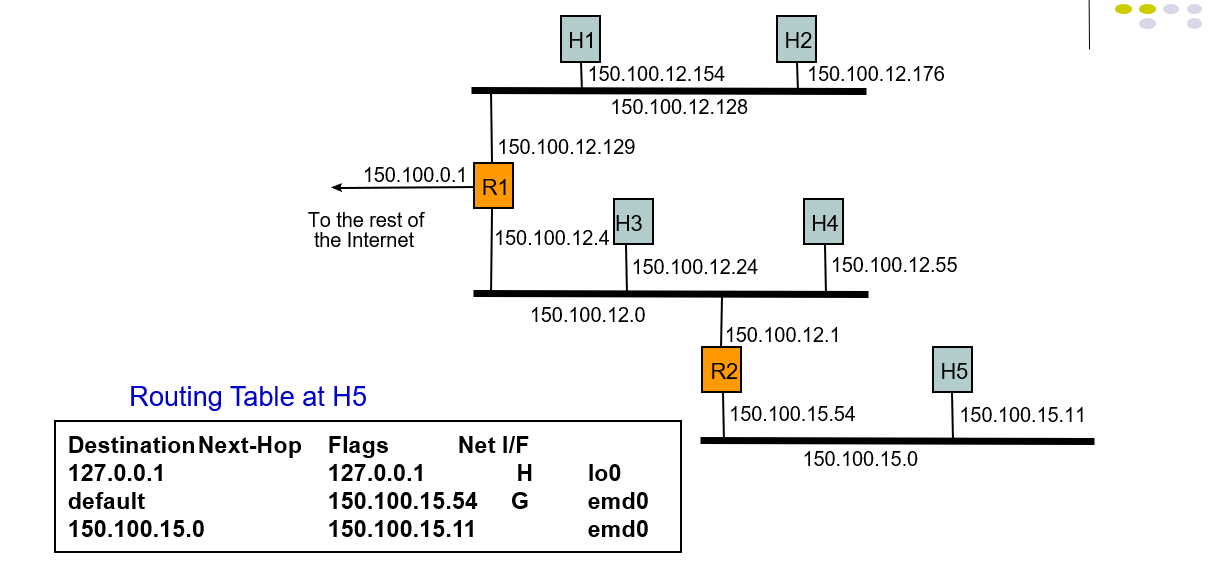
Example 1: A packet with 150.100.15.11 arrives at R1
- Host5 want to send a packet to Rout1, it firstly searches 150.100.0.1 in the routing table, but not match.
- So it send the packet to R2 as the default IP address.
Example 1: Subnetting Scheme
- H and R find next hop in this way.
- IP address 150.100.15.11 in binary string is
10010110 01100100 00001111 00001011 - Apply subnet mask to IP addresses to find corresponding subnet
- IP address = 10010110 01100100 00001111 00001011
- Mask = 11111111 11111111 11111111 10000000
- AND = 10110110 01100100 00001111 00000000
- Subnet = 150.100.15.0
Example 2: Host H5 sends packet to host H2
- The routing table contains:destination next-hop,flags,default next-hop,physical interface.
- H5 searches the routing table but doesn't find destination next-hop, so it send the packet as the default next-hop.
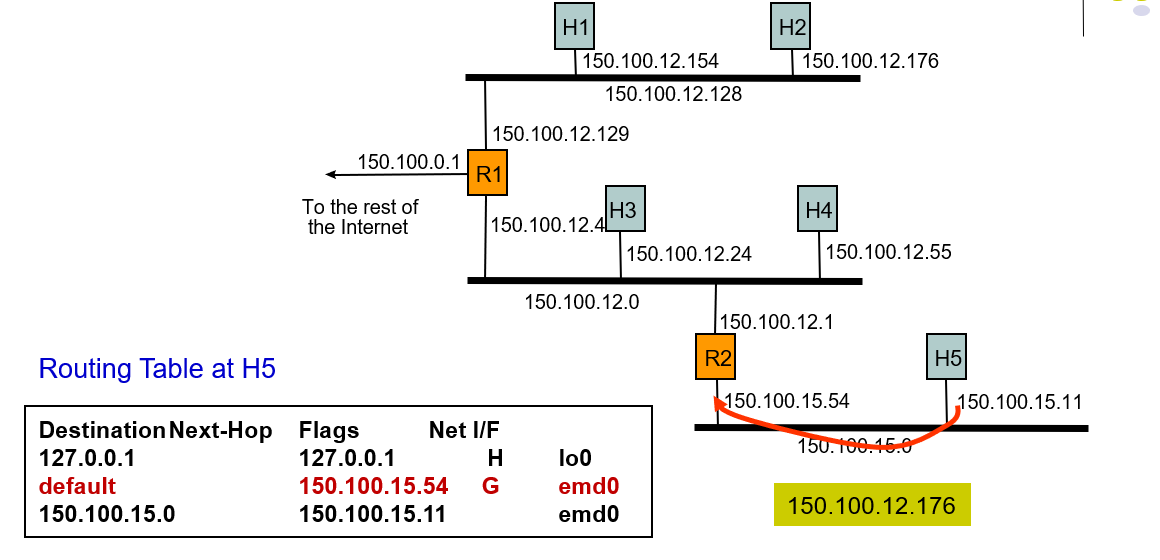
Example 2: Host H5 sends packet to host H2
- 127.0.0.1 is the native address.
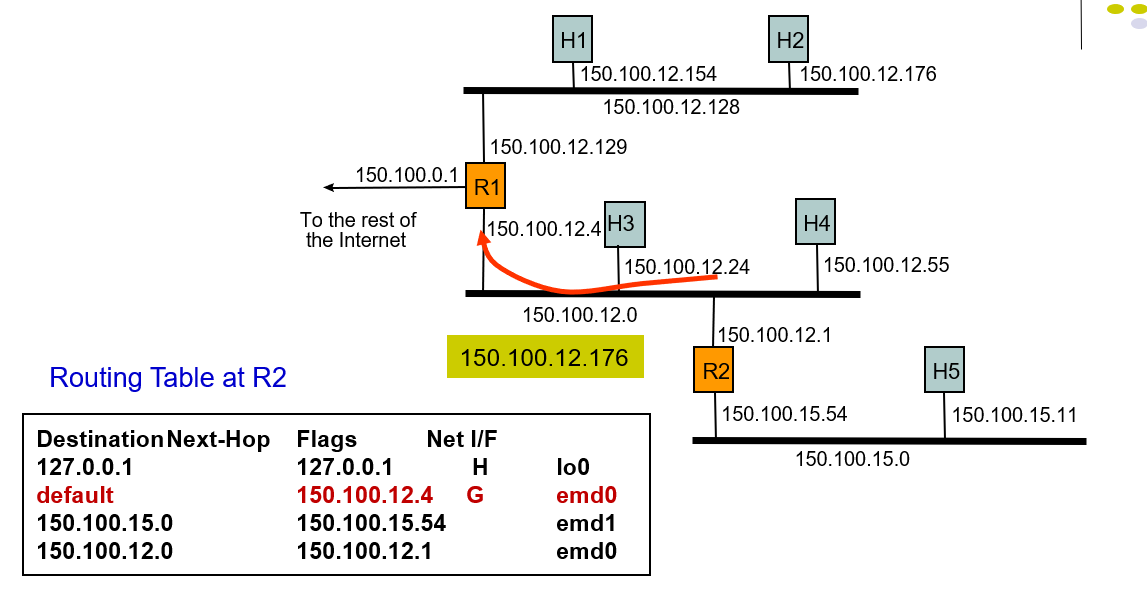
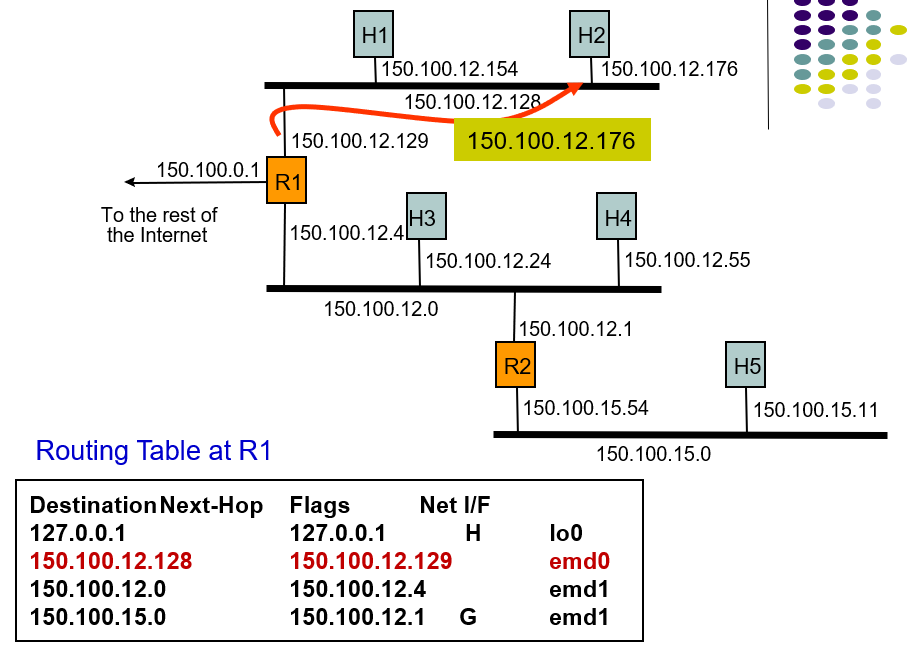
Example: Host H5 sends packet to host H2
- It sned a packet so the network interface which delivers a packet to the local are network by broadcasting and host H2 receive the packet.
Discuss
- Discuss the difficulties with using actual time in the Time-to-Live field
- TTL restricts the max hops in the network, even if it was called "Time to live", but it is hops instead of time. The distance is different in all kinds of network, and the delay time in every stops is not the same. So it difficult to confirm the actual time, using hops to stand for time to live is a better choose.
Subnet Routing Examples的更多相关文章
- ip 子网掩码 网关 DNS
这一篇文章也很好: 原文引用于: http://www.cnblogs.com/jiqing9006/p/3365939.html 内外网ip: IP地址: IPv4地址分为A.B.C.D.E五类, ...
- IP子网掩码划分及设置
IP子网掩码划分及设置 定长子网掩码: 一.子网掩码的计算 TCP/IP网间网技术产生于大型主流机环境中,它能发展到今天的规模是当初的设计者们始料未及的.网间网规模的迅速扩展对IP地址模式的威胁并不是 ...
- HCNP学习笔记之子网掩码的计算和划分详细
0x00 子网掩码的计算 TCP/IP网间网技术产生于大型主流机环境中,它能发展到今天的规模是当初的设计者们始料未及的.网间网规模的迅速扩展对IP地址模式的威胁并不是它不能保证主机地址的唯一性,而是会 ...
- Routing 功能概述 - 每天5分钟玩转 OpenStack(98)
路由服务(Routing)提供跨 subnet 互联互通功能. 例如前面我们搭建了实验环境: cirros-vm1 172.16.100.3 vlan100 cirros-vm ...
- 理解 OpenStack 高可用(HA)(3):Neutron 分布式虚拟路由(Neutron Distributed Virtual Routing)
本系列会分析OpenStack 的高可用性(HA)概念和解决方案: (1)OpenStack 高可用方案概述 (2)Neutron L3 Agent HA - VRRP (虚拟路由冗余协议) (3)N ...
- Examples of MIB Variables - SNMP Tutorial
30.5 Examples of MIB Variables Versions 1 and 2 of SNMP each collected variables together in a singl ...
- 东大OJ-1588: Routing Table
题目描述 In the computer network, a Router is a device which finds an optimal way to transmit the datagr ...
- ural 1072. Routing
1072. Routing Time limit: 1.0 secondMemory limit: 64 MB There is a TCP/IP net of several computers. ...
- Top 30 Nmap Command Examples For Sys/Network Admins
Nmap is short for Network Mapper. It is an open source security tool for network exploration, securi ...
随机推荐
- 基于easyUI实现系统日志管理
此文章是基于 EasyUI+Knockout实现经典表单的查看.编辑 一. 相关文件介绍 1. log.jsp:系统日志管理界面 <!DOCTYPE html PUBLIC "-//W ...
- pycharm下 os.system os.popen执行命令返回有中文乱码
原文 settings:
- json转换工具类
using System;using System.Collections.Generic;using System.Text;using Newtonsoft.Json;using System.I ...
- 在C#中执行带有GO的批量sql语句
引用 思海网络 在用C#中调用ADO执行批量SQL语句的时候,会出现无法识别GO语句的错误.这个时候,我们以GO语句为分割点,把整个批量语句分割成N块独立的SQL语句代码块(不包含GO语句),然后再 ...
- vue-cli项目打包多个与static文件同级的静态资源目录(copy-webpack-plugin插件的使用)
场景 业务要求能够直接通过 "域名+/file"的方式访问静态资源的html,然而产品绝对static暴露在url中不好看又不能直接将html放在static中.所以想到了既然st ...
- 原生js操作DOM基础-笔记
原文参考http://mp.weixin.qq.com/s?__biz=MzU3MDA0NTMzMA==&mid=2247485490&idx=1&sn=15197b4b53e ...
- Python爬虫教程-16-破解js加密实例(有道在线翻译)
python爬虫教程-16-破解js加密实例(有道在线翻译) 在爬虫爬取网站的时候,经常遇到一些反爬虫技术,比如: 加cookie,身份验证UserAgent 图形验证,还有很难破解的滑动验证 js签 ...
- centos aws 修改使用密码ssh登录
因为使用pem登录有很多局限性,在此修改为用密码但不是root登录 1.关闭selinux(要重启) vi /etc/selinux/config SELINUX=disabled 2.重置root密 ...
- 从Microsoft SQL Server迁移到MySQL指南
转自 https://www.mysql.com/why-mysql/white-papers/sql-server-to-mysql-zh/ 由于 MySQL 将节约成本.自由选择平台.特性丰富等优 ...
- .Net ->> iTextSharp工具读取PDF文本内容
分享一个开源的C#DLL,可以读取PDF文本内容. 地址:http://sourceforge.net/projects/itextsharp/ 这里还有相关的链接:http://www.codepr ...
