A simple introduction to Three kinds of Delegation of Kerberos
1.What is Delegation?
Just like the name. Delegation is that a server pretend to behalf of a user and to authenticate with kerberos protocol.There are three kinds of delegations.
| Kinds of Delegations | Limitions | Protocol | Note |
|---|---|---|---|
| Unconstrained Delegation | None | Just forward the TGT ticket which is able to be forwarded | None |
| Constrained Delegation | Front-End Server decide which Back-End service can receive delegation | 1.S4U2Proxy -> Forward the TGT ticket 2.S4U2Self -> Receive information of NTLM Authentication(Username&NTLM-Hash) And use that to get TGT and send TGT and receive TGS from KDC |
AD administrator account |
| Resource-Based Constrained Delegation | Back-End Services decide which Front-End service's delegation can be received | The same as Constrained Delegation | 1.S4U2Proxy -> Can Forward TGT ticket which is not to be able to forwarded. 2.You can use this cross the domain. 3.Service administrator account |
2.Unconstrained Delegation
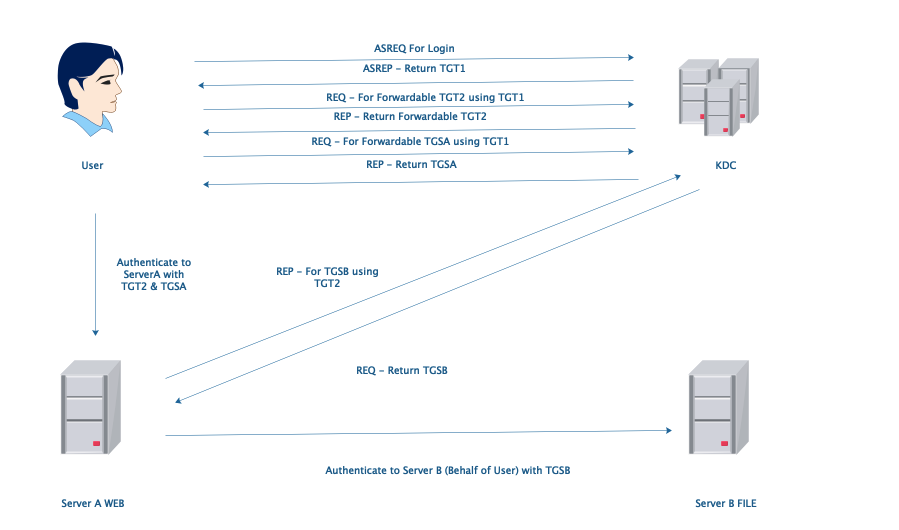
Unconstrained Delegation: ServerA can authenticate to any server in this domain behalf of user with TGT2. It is too dangerous.
3.Constrained Delegation
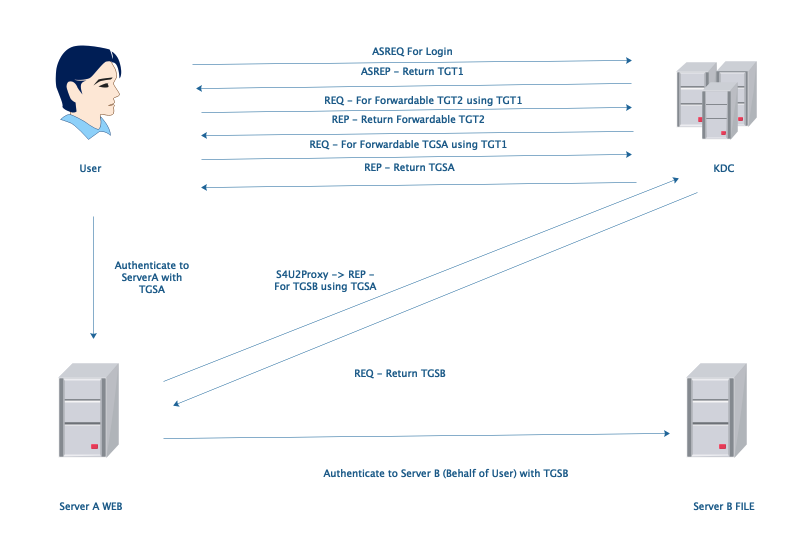
Only S4U2Proxy is what we need, if user use kerberos ticket to authenticate. Otherwise we need both S4U2Self and S4U2Proxy if user use NTLM hash to authenticate. In this condition, AD administrators can configure which service(SPNs) can receive ServerA’s delegation in ServerA's msDC-AllowedToDelegateTo property.
4.Resource-Based Constrained Delegation
There is one important difference between Constrained Delegation and Resource-Based Constrained Delegation. In Constrained Delegation, administrators of AD can configure which service can receive ServerA's delegation in their msDS-AllowedToActOnBehalfOfOtherIdentity properties. However, In Resource-Based Constrained Delegation, administrators of services can decide if those service will receive the ServerA's delegation or not. And it should be configured on the computers which is running those services. Do you think Resource-Based Constrained Delegation is much more safe than Constrained Delegation? No, Resource-Based Constrained Delegation has a big problem. In this condition, S4U2Proxy can forward unforwardable TGT and KDC will return TGS back. So if we could get the TGT which is not able to forward, We also could use it to do something bad.
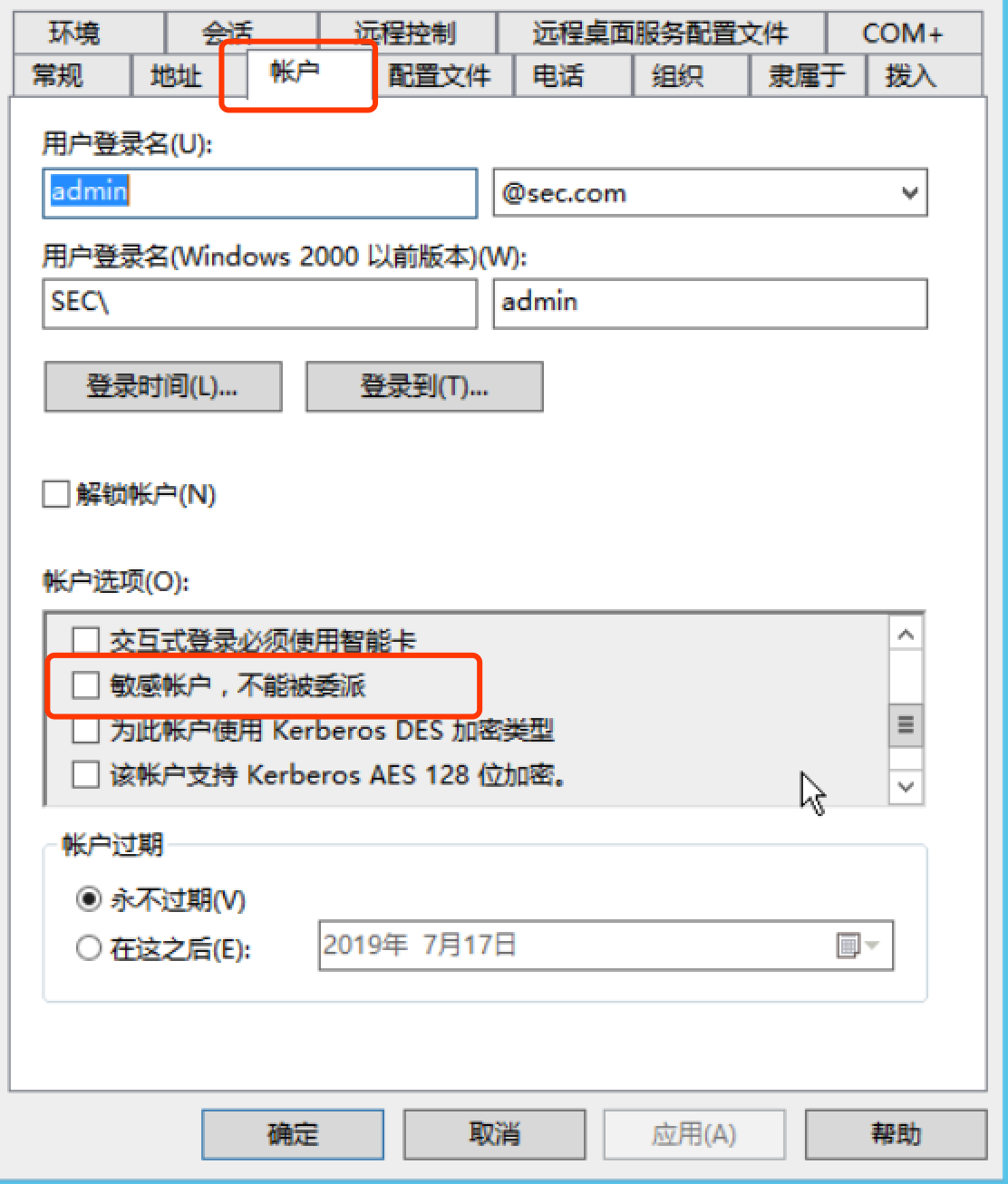
5. What we can do to make it a little more safe?
** We can do a lot of things to make it more safe. Plus, the first one is to configure like this.**
A simple introduction to Three kinds of Delegation of Kerberos的更多相关文章
- A Simple Introduction To Computer Networking
Most networking discussions are a jumble of acronyms. Forget the configuration details - what are th ...
- The Most Simple Introduction to Hypothesis Testing
https://www.youtube.com/watch?v=UApFKiK4Hi8
- 转:Simple Introduction to Dirichlet Process
来源:http://hi.baidu.com/vyfrcemnsnbgxyd/item/2f10ecc3fc35597dced4f88b Dirichlet Process(DP)是一个很重要的统计模 ...
- An Introduction to Variational Methods (5.1)
在这篇文章中,我引用Bishop书中的一个例子,来简单介绍一下Variational Methods的应用.想要更详细地理解这个例子,可以参考Bishop的书Pattern Recongnition ...
- 深度强化学习(Deep Reinforcement Learning)入门:RL base & DQN-DDPG-A3C introduction
转自https://zhuanlan.zhihu.com/p/25239682 过去的一段时间在深度强化学习领域投入了不少精力,工作中也在应用DRL解决业务问题.子曰:温故而知新,在进一步深入研究和应 ...
- ML Lecture 0-1: Introduction of Machine Learning
本博客是针对李宏毅教授在Youtube上上传的课程视频<ML Lecture 0-1: Introduction of Machine Learning>的学习笔记.在Github上也po ...
- CI Weekly #6 | 再谈 Docker / CI / CD 实践经验
CI Weekly 围绕『 软件工程效率提升』 进行一系列技术内容分享,包括国内外持续集成.持续交付,持续部署.自动化测试. DevOps 等实践教程.工具与资源,以及一些工程师文化相关的程序员 Ti ...
- 理解callback function in javascript
以下内容主要摘自[1,2] (1)In javascript, functions are first-class objects, which means functions can be used ...
- Discovering the Computer Science Behind Postgres Indexes
This is the last in a series of Postgres posts that Pat Shaughnessy wrote based on his presentation ...
随机推荐
- loadrunner 集合点设置2
1.集合点的含义 当通过controller虚拟多个用户执行该脚本时.用户的启动或运行步骤不一定都是同步的,集合点是在脚本的某处设置一个标记.当有虚拟用户运行到这个标记处时,停下等待,直到 ...
- oracle中having与where的区别
1.where 不能放在group by 的后面 2.HAVING 是跟GROUP BY 连在一起用的,放在GROUP BY 后面,此时的作用相当于WHERE 3.WHERE 后面的条件中不能有聚集函 ...
- 论文阅读笔记五十九:Res2Net: A New Multi-scale Backbone Architecture(CVPR2019)
论文原址:https://arxiv.org/abs/1904.01169 摘要 视觉任务中多尺寸的特征表示十分重要,作为backbone的CNN的对尺寸表征能力越强,性能提升越大.目前,大多数多尺寸 ...
- c# 多线程多个参数
for (int i = 0; i <count; i++) //根据选择的串口号数量创建对应数量的线程 { thread = new Thread(new ParameterizedThrea ...
- windows下sed回车换行符处理
windows下sed回车换行符处理如果用sed for windows对整个文件进行了编辑,编辑之后一般需要处理回车换行符:rem windows的回车换行符是\r\n,linux的是\n,所以要替 ...
- python读写、创建文件、文件夹等等
python中对文件.文件夹(文件操作函数)的操作需要涉及到os模块和shutil模块. 得到当前工作目录,即当前Python脚本工作的目录路径: os.getcwd() 返回指定目录下的所有文件和目 ...
- [LeetCode] 395. Longest Substring with At Least K Repeating Characters 至少有K个重复字符的最长子字符串
Find the length of the longest substring T of a given string (consists of lowercase letters only) su ...
- [LeetCode] 286. Walls and Gates 墙和门
You are given a m x n 2D grid initialized with these three possible values. -1 - A wall or an obstac ...
- 小程序根据数字做for循环
笔记:小程序根据具体一个数值做for循环 n为想循环的次数 <view wx:for="{{n - 0}}"> <text>{{index}}</te ...
- Windows下MySQL安装流程,8.0以上版本ROOT密码报错及修改
官网下载MySQL安装后,解压,添加环境变量,以管理员方式运行cmd,运行以下命令 mysqld --initialize --console mysqld -install net start my ...
