An overview of network penetration testing
1、 an SQLi vulnerability will allow you to do the following
- query the database using select statement forezample users table. you might get the password or usersname
- Bypass the login page executing successfuly query results
- Execute system commands in the database in oreder compromise the web server
- Execute inserts.delete commands to manipulate the records in the database
2、Command Injection
we can append other commands after the variable and the application will be to execute it for us , my goal is to make the backend execute someting like this [nslookup [domain name variable ] && [other command ]
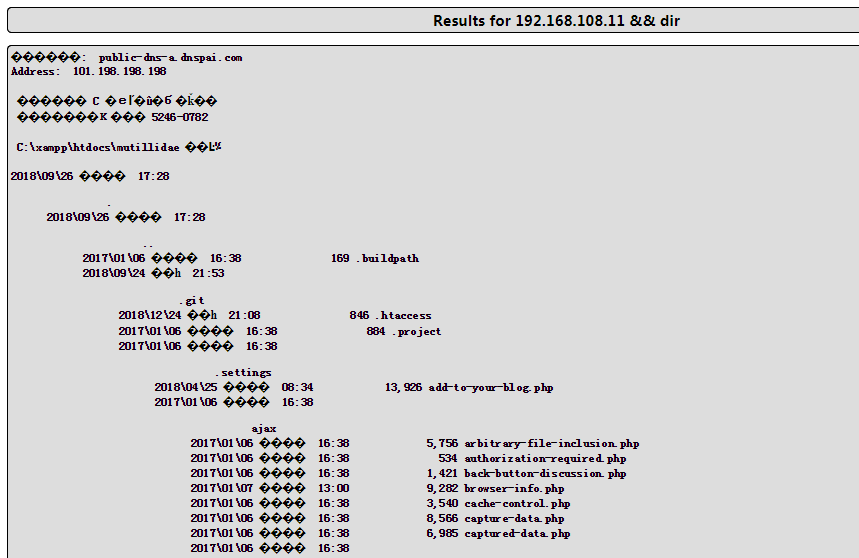
3、OWASP top 10
Injection-----> when a attacker can inject and execute a custom command in the backend because of missing sanitization,besides it ,command Injection are more like LDAP、XPath、NoSQLo XML Parsers、STMTP Header
Broken Authentication ------> a hacker finds the user's idntity, credentials bouth name and password or web session
Sesitive Data 、 XML External Entities \ Broken Access Control \ Security Misconfig \Cross-site Scripting \ Insecure Deserialization \ Using Components with know vulnerability\ Insufficient logging
4、邮件信息收集
theharverster -d [目标网络域名地址] -l [邮件地址数量] -b [使用的搜索的公共知识库] eg : theharvester -d yalong.cn -l 20 -b baidu
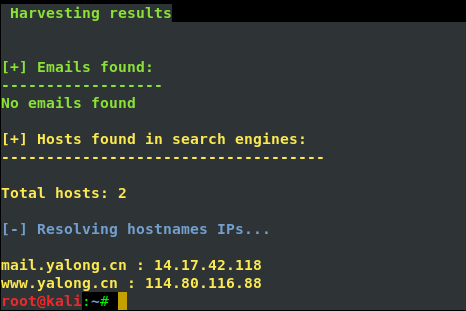

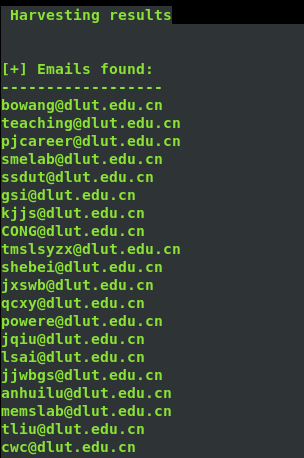
5、 use Whois search DNS and ip register name and phone number and email
step one we can use the Whois.net the url: http:www.whois.net or another website is NetCraft the url :https://www.netcraft.com/
step two: use the command whois ,the screenshout as follow

another wegit tools is host it can translate ip to hostname
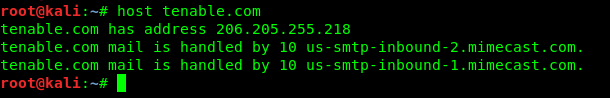
nslookup id find DNS
6、Reconnaissance or information gathering
a pen tester gather information an attacker's perspective ,anything that is useful is necessary to be collected:
- network Digrams、 application and their version、security defences such IDS IPS
- IP address baidu & Social or perfessional networking websites
- Domain names \sites\ Monster.com 、 IP Registries 、DNS registrars \
- Device name the company websites
7、nslookup is a windows tool to find the ip address associated with the given domain name
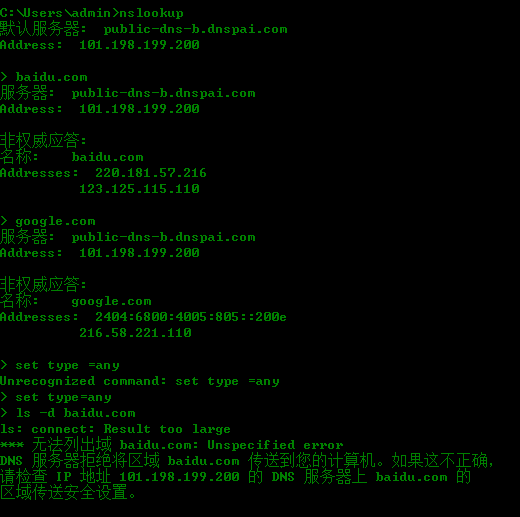
8、Scanning to finding live address
ICMP scanning use command Nmap -sP [ip range] 、 SYN scanning Commands Nmap -sS -P0 [ip range] 、all port scanning commamds Nmap -sS -p1=65535 -P0 -max-rtt-timeout<time> [iprange]
Specific Prot scanning we know the ususlly port 80` 443 wecan use command Nmap -sS -p80,443 -P0 [ip range]
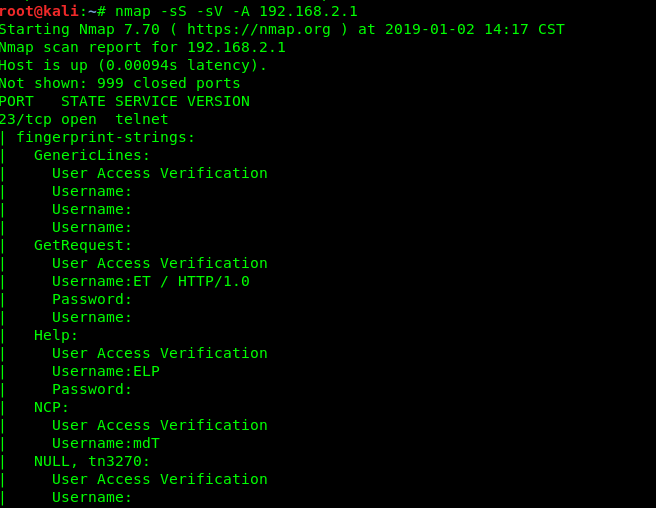
9、OS ans service FingerPrintering
OS detecting is to be done find out the system ,by which know vulnerabilities can be exploited .we can use the commands Namp -O [ip range ] or use Namp -sS -sV -O -P0[ip range] of cose can use the comand to find all port Nmap -sS -sV -O -P0 -p1-65535 -max-rrt-timeout<time> [ip range]
10、Vulnerability Scanning
Nmap has the vulnerability scan switch ,we can run the nmap vulnerability scan the command ; nmap -sS --sV -P0 -p1 -65535 -A --max-rate 500 --reason iL<inputfile.txt><outputfile.txt>
another way we can use nessus nskipfish ,BurpSuite
11、make a conclusion
The reported Vulnerability have to to be tested manually and confirmed since the vulnerability repprted by the scanners my be false positives at times.
An overview of network penetration testing的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- yum设置本地源
创建本地源的文件要放入yum.repos.d目录下,名字随便取,但是后缀要求是.repo 1创建目录 mkdir -p /mnt/cdrom 2虚拟机挂载光盘 mount /dev/cdrom /mn ...
- max-height、min-height、height优先级的问题
前言 我们在实际开发中可能会限制元素的最大高度,那么我们使用的属性必定是max-height,那么不知道大家有没有考虑过如果同时设置max-height和height会发生什么呢? max-heigh ...
- $(function(){})简述
用jQ的人很多人都是这么开始写脚本的: $(function(){ // do something }); 其实这个就是jq ready()的简写,他等价于: $(document).ready(fu ...
- codeforces721C
Journey CodeForces - 721C Recently Irina arrived to one of the most famous cities of Berland — the B ...
- iOS 利用高德地图WMS服务
Demo: https://github.com/xushiyou23/AMapTesting 转: 版权声明:本文为博主原创文章,未经博主允许不得转载. https://blog.csdn.net ...
- Nginx ServerName指令
L:47
- 【NLP】Conditional Language Modeling with Attention
Review: Conditional LMs Note that, in the Encoder part, we reverse the input to the ‘RNN’ and it per ...
- @RequestParam、@RequestBody和@ModelAttribute区别
一.@RequestParamGET和POST请求传的参数会自动转换赋值到@RequestParam 所注解的变量上1. @RequestParam(org.springframework.web.b ...
- [OI]Noip 2018总结(普及)
考砸了,还有原谅我代码十分有限的可读性. 一个人的真正伟大之处就在于他能够认识到自己的渺小.——保罗 从一年前初一九月到现在18年10月接触OI已经有一年了.几次模拟赛也自我感觉良好,都过了一等的线, ...
- SpringBoot之普通类获取Spring容器中的bean
package com.geostar.geostack.git_branch_manager.common; import org.springframework.beans.BeansExcept ...
