Python Ethical Hacking - VULNERABILITY SCANNER(7)
VULNERABILITY_SCANNER
How to discover a vulnerability in a web application?
1. Go into every possible page.
2. Look for ways to send data to the web application(URL + Forms).
3. Send payloads to discover vulnerabilities.
4. Analyze the response to check of the website is vulnerable.
->General steps are the same regardless of the vulnerability.
Login the metasploitable VM and modify the security of DVWA from high to medium.(dvwaPage.inc.php in /var/www/dvwa/dvwa/includes)

Submit the following script on the Reflected Cross Site Scripting(XSS)
<sCript>alert('test')</scriPt>
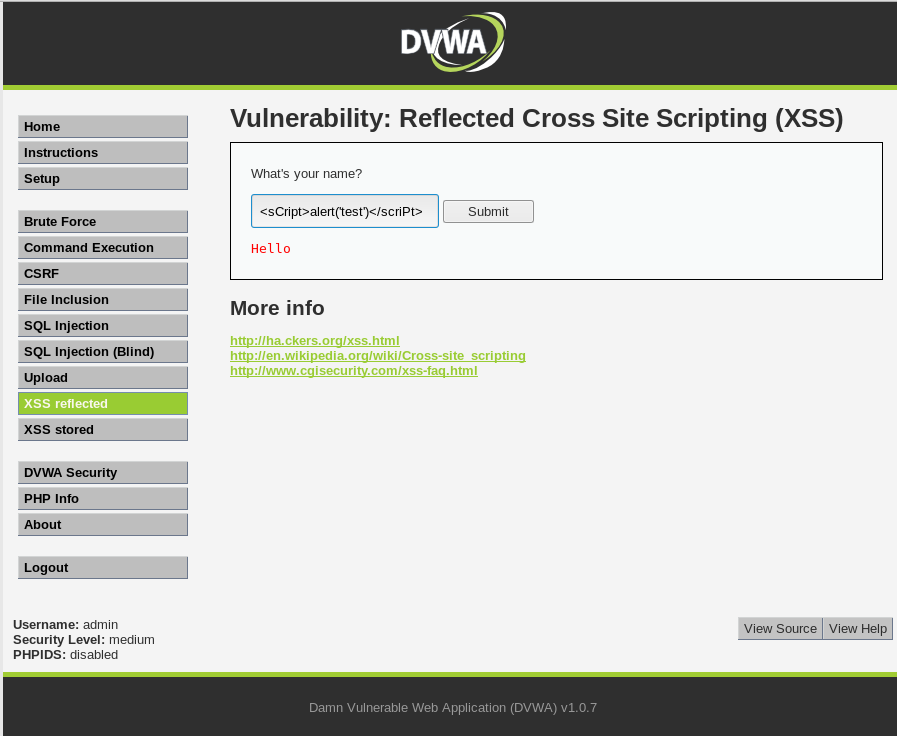
You can find the script in the source code.
Add the new feature - test_xss_in_form in Scanner class.
#!/usr/bin/env python import requests
import re
from bs4 import BeautifulSoup
from urllib.parse import urljoin class Scanner:
def __init__(self, url, ignore_links):
self.session = requests.Session()
self.target_url = url
self.target_links = []
self.links_to_ignore = ignore_links def extract_links_from(self, url):
response = self.session.get(url)
return re.findall('(?:href=")(.*?)"', response.content.decode(errors='ignore')) def crawl(self, url=None):
if url == None:
url = self.target_url
href_links = self.extract_links_from(url)
for link in href_links:
link = urljoin(url, link) if "#" in link:
link = link.split("#")[0] if self.target_url in link and link not in self.target_links and link not in self.links_to_ignore:
self.target_links.append(link)
print(link)
self.crawl(link) def extract_forms(self, url):
response = self.session.get(url)
parsed_html = BeautifulSoup(response.content.decode(), features="lxml")
return parsed_html.findAll("form") def submit_form(self, form, value, url):
action = form.get("action")
post_url = urljoin(url, action)
method = form.get("method") inputs_list = form.findAll("input")
post_data = {}
for input in inputs_list:
input_name = input.get("name")
input_type = input.get("type")
input_value = input.get("value")
if input_type == "text":
input_value = value post_data[input_name] = input_value
if method == "post":
return requests.post(post_url, data=post_data)
return self.session.get(post_url, params=post_data) def run_scanner(self):
for link in self.target_links:
forms = self.extract_forms(link)
for form in forms:
print("[+] Testing form in " + link) if "=" in link:
print("[+] Testing " + link) def test_xss_in_form(self, form, url):
xss_test_script = "<sCript>alert('test')</scriPt>"
response = self.submit_form(form, xss_test_script, url)
if xss_test_script in response.content.decode():
return True
Modify the vulnerability scanner code and test it.
#!/usr/bin/env python import scanner target_url = "http://10.0.0.45/dvwa/"
links_to_ignore = "http://10.0.0.45/dvwa/logout.php" data_dict = {"username": "admin", "password": "password", "Login": "submit"} vuln_scanner = scanner.Scanner(target_url, links_to_ignore)
vuln_scanner.session.post("http://10.0.0.45/dvwa/login.php", data=data_dict) # vuln_scanner.crawl()
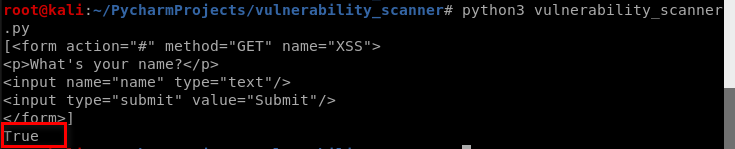
forms = vuln_scanner.extract_forms("http://10.0.0.45/dvwa/vulnerabilities/xss_r/")
print(forms)
response = vuln_scanner.test_xss_in_form(forms[0], "http://10.0.0.45/dvwa/vulnerabilities/xss_r/")
print(response)
Aha! We find customized vulnerability.
Python Ethical Hacking - VULNERABILITY SCANNER(7)的更多相关文章
- Python Ethical Hacking - VULNERABILITY SCANNER(9)
Automatically Discovering Vulnerabilities Using the Vulnerability Scanner 1. Modify the run_scanner ...
- Python Ethical Hacking - VULNERABILITY SCANNER(4)
Extracting & Submitting Forms Automatically Target website:http://10.0.0.45/dvwa/vulnerabilities ...
- Python Ethical Hacking - VULNERABILITY SCANNER(2)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(8)
Implementing Code To Discover XSS in Parameters 1. Watch the URL of the XSS reflected page carefully ...
- Python Ethical Hacking - VULNERABILITY SCANNER(3)
Polish the Python code using sending requests in a session Class Scanner. #!/usr/bin/env python impo ...
- Python Ethical Hacking - VULNERABILITY SCANNER(1)
HTTP REQUESTS BASIC INFORMATION FLOW The user clicks on a link. HTML website generates a request(cli ...
- Python Ethical Hacking - VULNERABILITY SCANNER(6)
EXPLOITATION - XSS VULNS EXPLOITING XSS Run any javascript code. Beef framework can be used to hook ...
- Python Ethical Hacking - VULNERABILITY SCANNER(5)
EXPLOITATION - XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript cod ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- thinkphp3.2 where 条件查询
thinkphp3.2 where 条件查询 在连贯操作中条件where的操作有时候自己很晕,所以整理下,有助于使用 查询条件 支持的表达式查询,tp不区分大小写 含义 TP运算符 SQL运算符 例子 ...
- 多语言工作者の十日冲刺<1/10>
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 这个作业要求在哪里 团队作业第五次--Alpha冲刺 这个作业的目标 团队进行Alpha冲刺--第一天(04.30) 作业正文 ...
- RocketMQ(1)---架构原理及环境搭建
一.架构简述 RocketMQ阿里开源的一个分布式消息传递和流媒体平台,具有低延迟,高性能和可靠性, 万亿级容量和灵活的可伸缩性.跟其它中间件相比,RocketMQ的特点是纯JAVA实现,在发生宕机和 ...
- 详述@Responsebody和HTTP异步请求的关系
Map.ModelAndView.User.List等对象都可以作为返回值.上述这两种对象都可以使用此注解.使用此注解即表示是在同一次请求的响应体里返回.浏览器以异步http的方式来接收.比如后端的M ...
- 尚硅谷ajax视频教程2
7.7. 尚硅谷_佟刚_Ajax_典型应用_验证用户名是否可用 整个项目的目录路径如下所示 我们首先新建立一个web工程,在webroot下面新建立一个script的文件夹,导入jquer文件 接下来 ...
- Nginx基本知识,nginx安装使用方法
Nginx 是一款高性能的Web服务器软件. - 具有极高的并发性能 - 利用Nginx与Tomcat组合使用, 搭建反向代理集群 - Nginx 反向代理集群可以解决网站的高并发问题! 1.安装 Y ...
- 入门大数据---Spark_Streaming整合Kafka
一.版本说明 Spark 针对 Kafka 的不同版本,提供了两套整合方案:spark-streaming-kafka-0-8 和 spark-streaming-kafka-0-10,其主要区别如下 ...
- 入门大数据---Elasticsearch搭建与应用
项目版本 构建需要: JDK1.7 Elasticsearch2.2.1 junit4.10 log4j1.2.17 spring-context3.2.0.RELEASE spring-core3. ...
- vue全家桶(2.7)
3.11.1.vue-router中的全局钩子函数 在vue-router中,路由发生变化,我们可以做一些事情,例如:可以决定是否进入导航,可以决定跳转到哪里,官方文档中又叫做导航守卫 首先来看一个全 ...
- C# 特性篇 Attributes
特性[Required] (必修的) /// <summary> /// 操作人EmpID /// </summary> [Required] public string Op ...
