Lab 3-1
Analyze the malware found in the file Lab03-01.exe using basic dynamic analysis tools.
Questions and Short Answers
What are this malware’s imports and strings?
A: The malware appears to be packed. The only import is ExitProcess, although the strings appear to be mostly clear and not obfuscated.
PEiD 截图如下:

Dependency Walker 截图印证了这一点:

What are the malware’s host-based indicators?
A: The malware creates a mutex named WinVMX32, copies itself into C:\Windows\System32\vmx32to64.exe. and installs itself to run on system startup by creating the registry key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\VideoDriver set to the copy location.
Are there any useful network-based signatures for this malware? If so, what are they?
A: The malware beacons a consistently sized 256-byte packet containing seemingly random data after resolving www.practicalmalwareanalysis.com.
Detailed Analysis
We begin with basic static analysis techniques, by looking at the malware’s PE file structure and strings. Figure 3-1L shows that only kernel32.dll is imported.
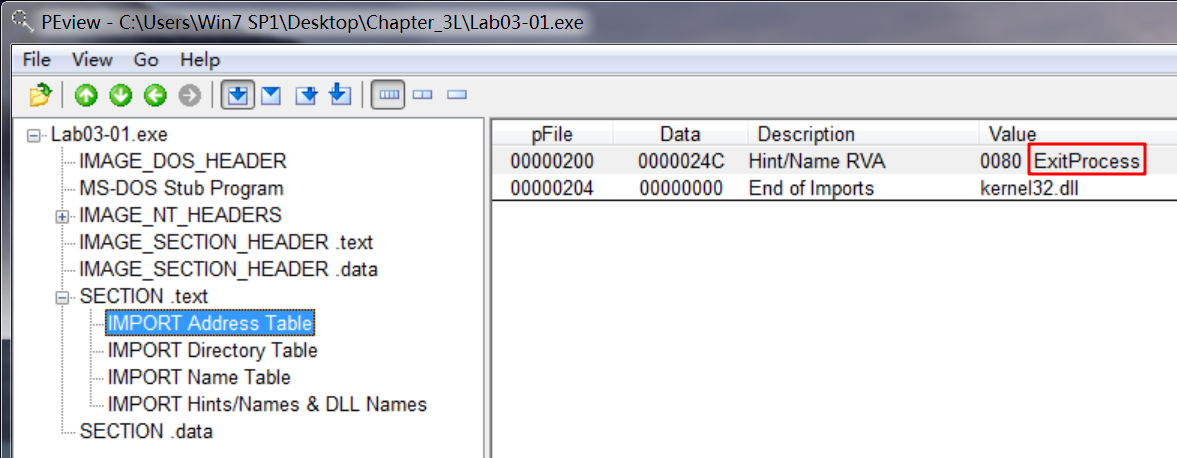
Figure 3-1L: PEview of Lab03-01.exe showing only one import
There is only one import to this binary, ExitProcess, as seen in the import address table. Without any imports, it is tough to guess the program’s functionality. This program may be packed, since the imports will likely be resolved at runtime.
Next, we look at the strings, as shown in the following listing.

IDA -> View -> Opensubviews -> Strings 显示如下:
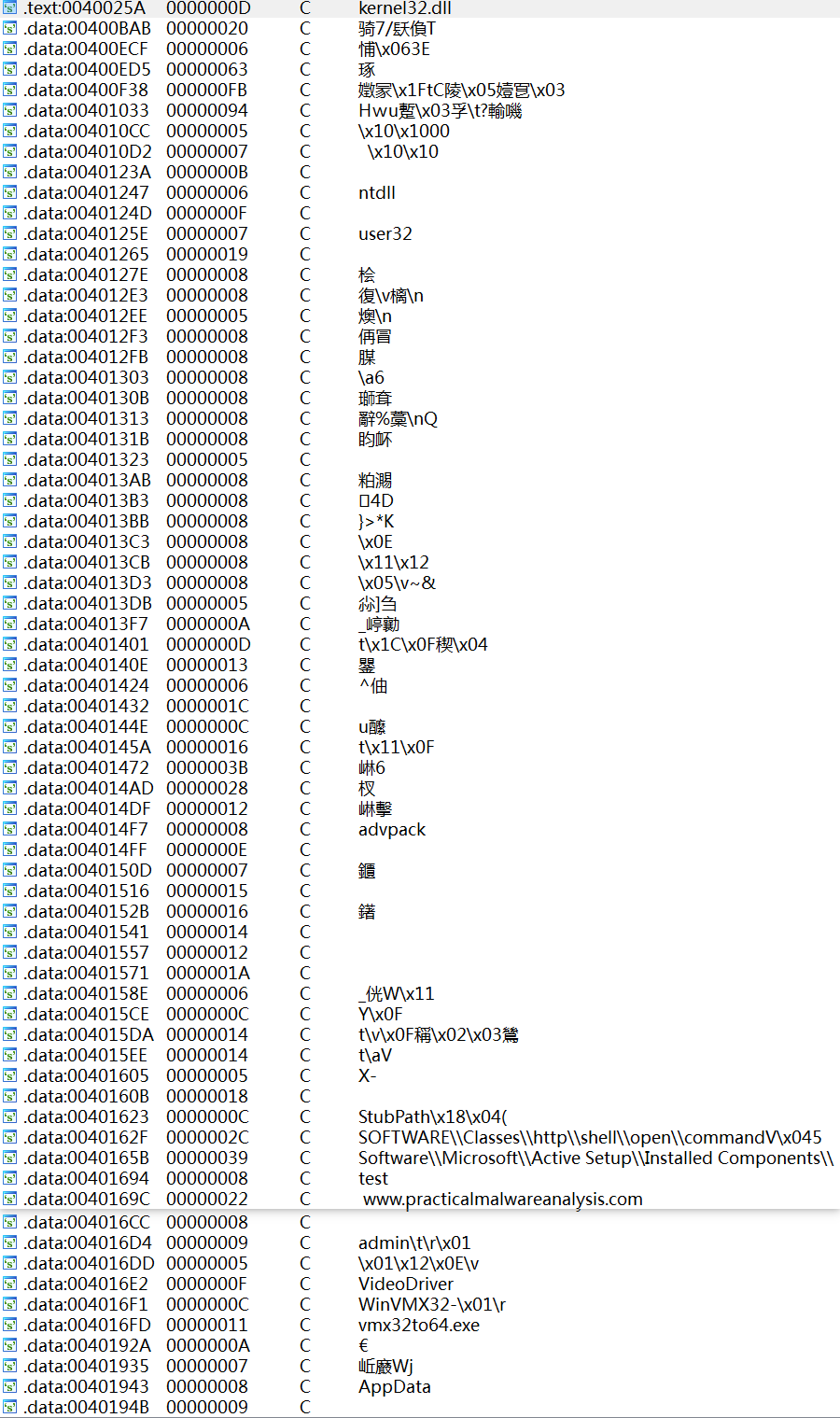
We wouldn’t expect to see strings, since the imports led us to believe that the file is packed, but there are many interesting strings, such as registry locations and a domain name, as well as WinVMX32, VideoDriver, and vmx32to64.exe. Let’s see if basic dynamic analysis techniques will show us how these strings are used.
Before we run the malware, we run procmon and clear out all events; start Process Explorer; and set up a virtual network, including ApateDNS, Netcat (listening on ports 80 and 443), and network capturing with Wireshark.
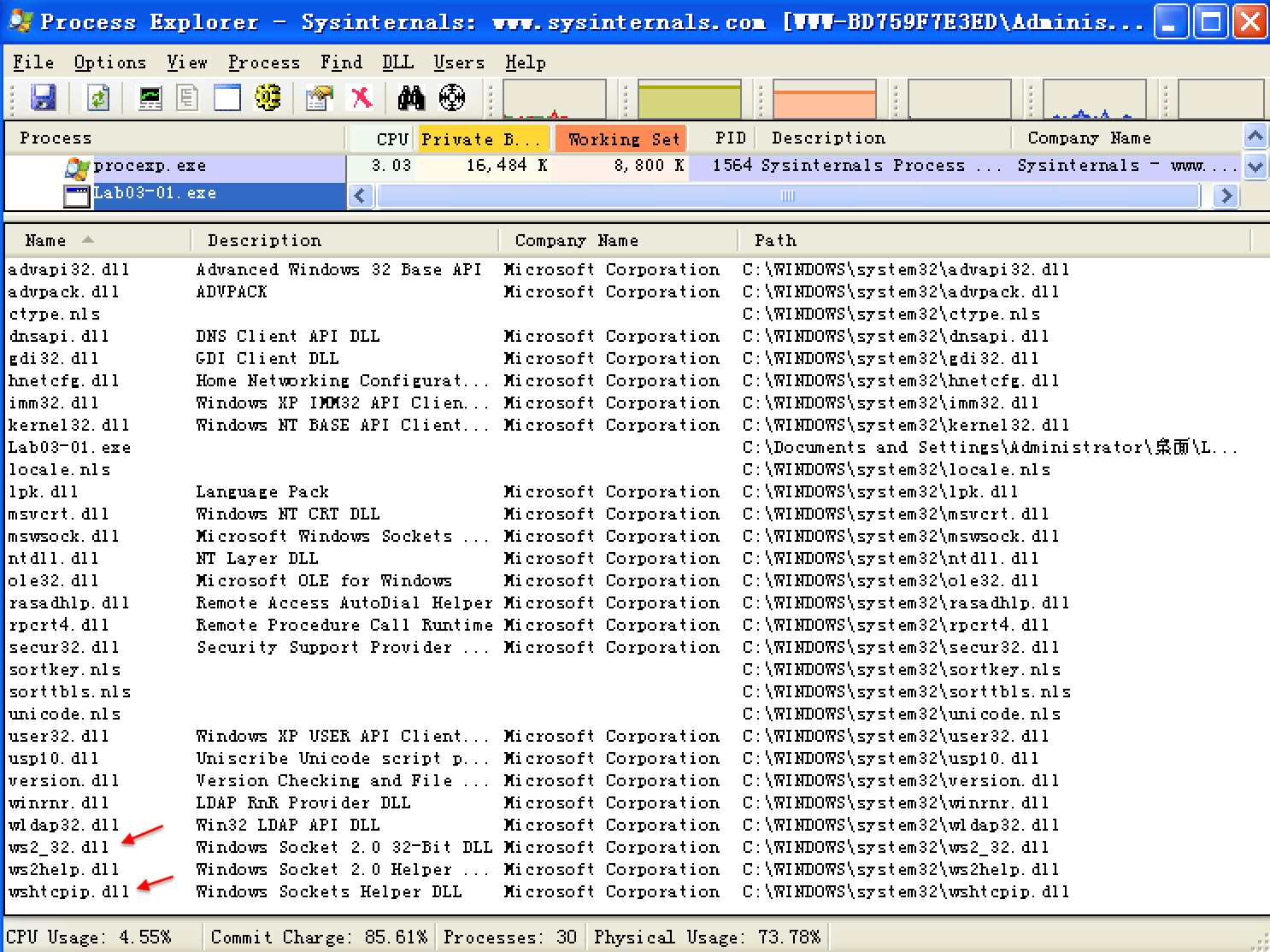
Once we run the malware, we start examining the process in Process Explorer, as shown in Figure 3-2L. We begin by clicking Lab03-01.exe in the process listing and select View -> Lower Pane View -> Handles. In this view, we can see that the malware has created the mutex named WinVMX32. We also select View -> Lower Pane View -> DLLs and see that the malware has dynamically loaded DLLs such as ws2_32.dll and wshtcpip.dll, which means that it has networking functionality.(这些信息在我们静态分析时是无法获取的,因为 Lab03-01.exe 加了壳。)
起初在win7下常识运行Lab03-01.exe,但是出现下列错误。
改为Windows XP可以运行。

Figure 3-2L: Process Explorer view of Lab03-01.exe showing the mutex it creates
Next, we use procmon to look for additional information. We bring up the Filter dialog by selecting Filter -> Filter, and then set three filters: one on the Process Name (to show what Lab03-01.exe does to the system), and two more on Operation, as shown in Figure 3-3L. We include RegSetValue and WriteFile to show changes the malware makes to the filesystem and registry.
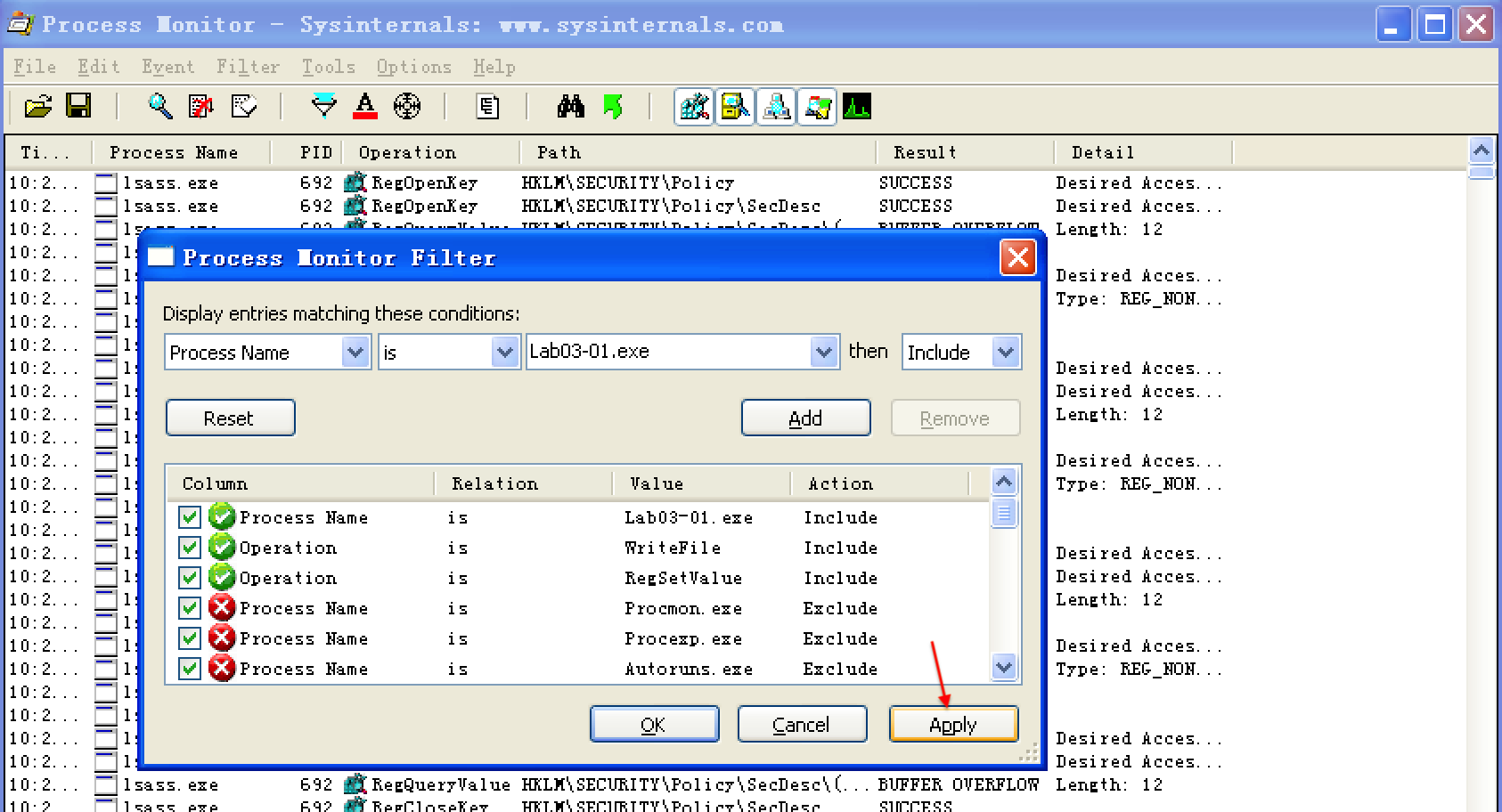
Figure 3-3L: Process Monitor Filter dialog showing filters set on Process Name and Operation
Having set our filters, we click Apply to see the filtered result. The entries are reduced from thousands to just the 10 seen in Figure 3-4L. Notice that there is only one entry for WriteFile, and there are nine entries for RegSetValue.
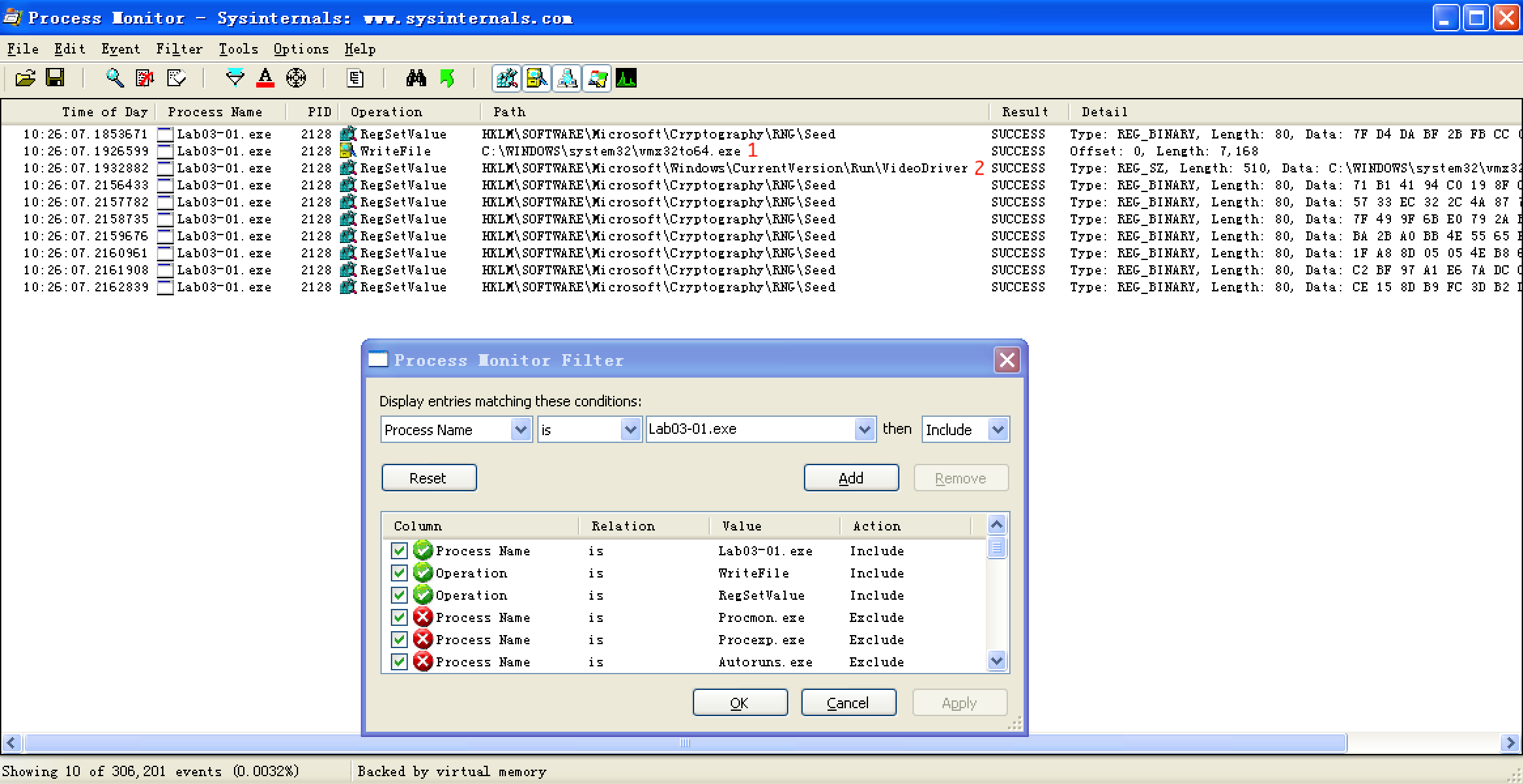
Figure 3-4L: Procmon filtered results (with three filters set)
As discussed in Chapter 3, we often need to filter out a certain amount of noise, such as entries 0 and 3 through 9 in Figure 3-4L. The RegSetValue on HKLM\SOFTWARE\Microsoft\Cryptography\RNG\Seed is typical noise in the results because the random number generator seed is constantly updated in the registry by software.
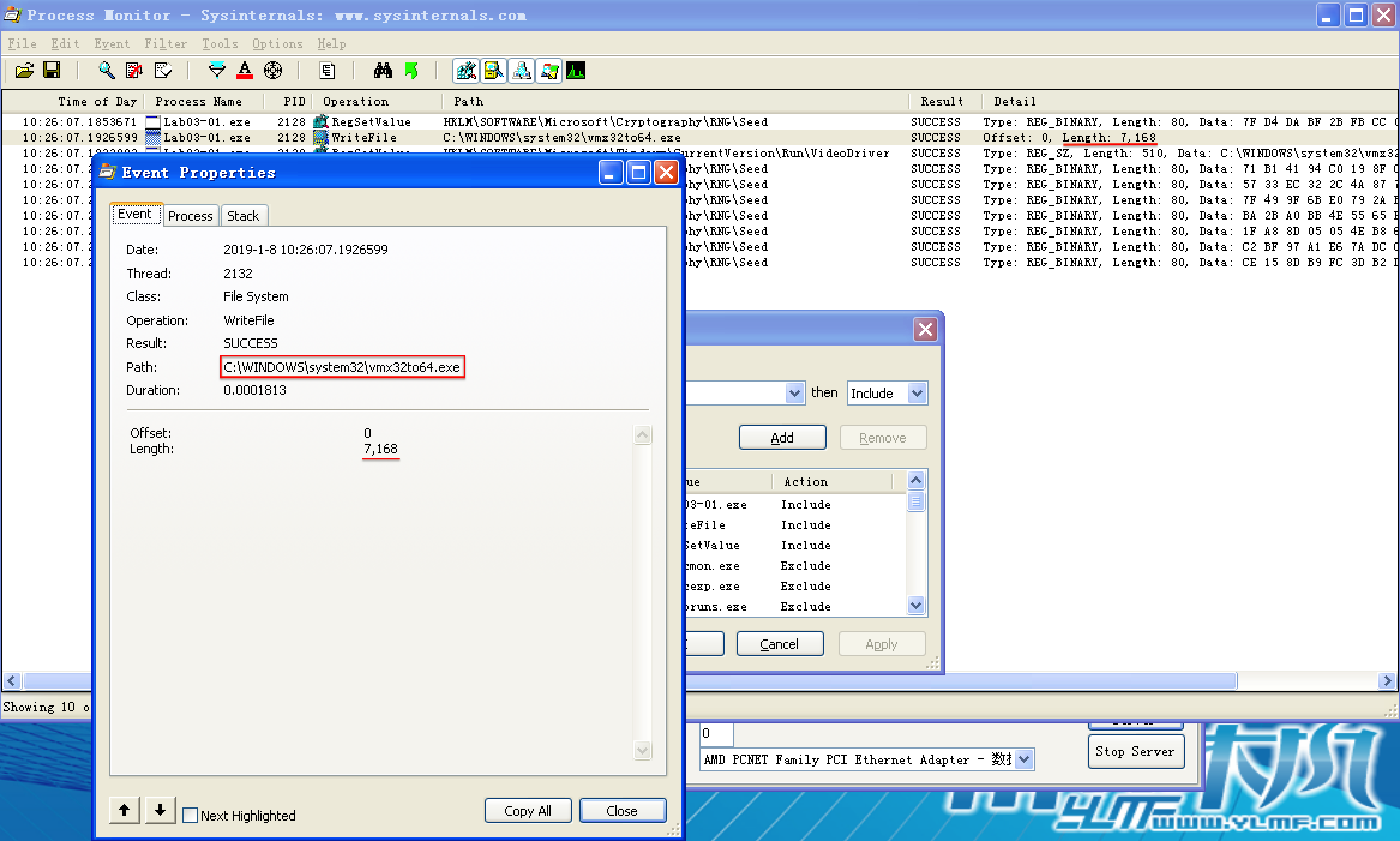
We are left with two interesting entries, as shown in Figure 3-4L at \({\color{Red}1}\) and \({\color{Red}2}\). The first is the WriteFile operation at \({\color{Red}1}\). Double-clicking this entry tells us that it wrote 7,168 bytes to C:\WINDOWS\system32\vmx32to64.exe, which happens to be the same size as that of the file Lab03-01.exe. Opening Windows Explorer and browsing to that location shows that this newly created file has the same MD5 hash as Lab03-01.exe, which tells us that the malware has copied itself to that name and location. This can be a useful host-based indicator for the malware because it uses a hard-coded filename.


Next, we double-click the entry at \({\color{Red}2}\) in the figure, and see that the malware wrote the following data to the registry:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\VideoDriver:C:\WINDOWS\system32\vmx32to64.exe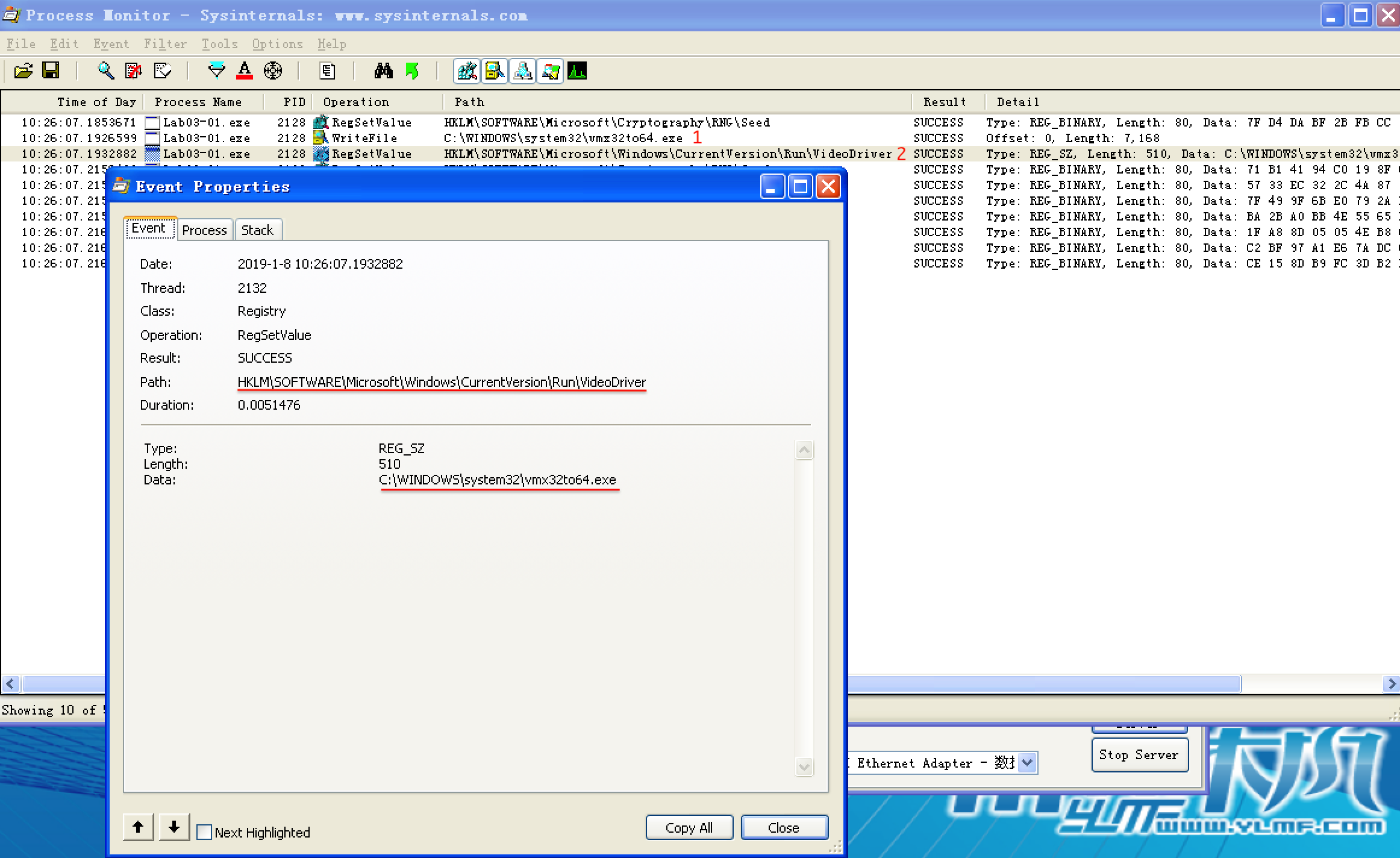
This newly created registry entry is used to run vmx32to64.exe on system startup using the HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run location and creating a key named VideoDriver. We can now bring up procmon’s Filter dialog, remove the Operation filters, and slowly comb through the entries for any information we may have missed.
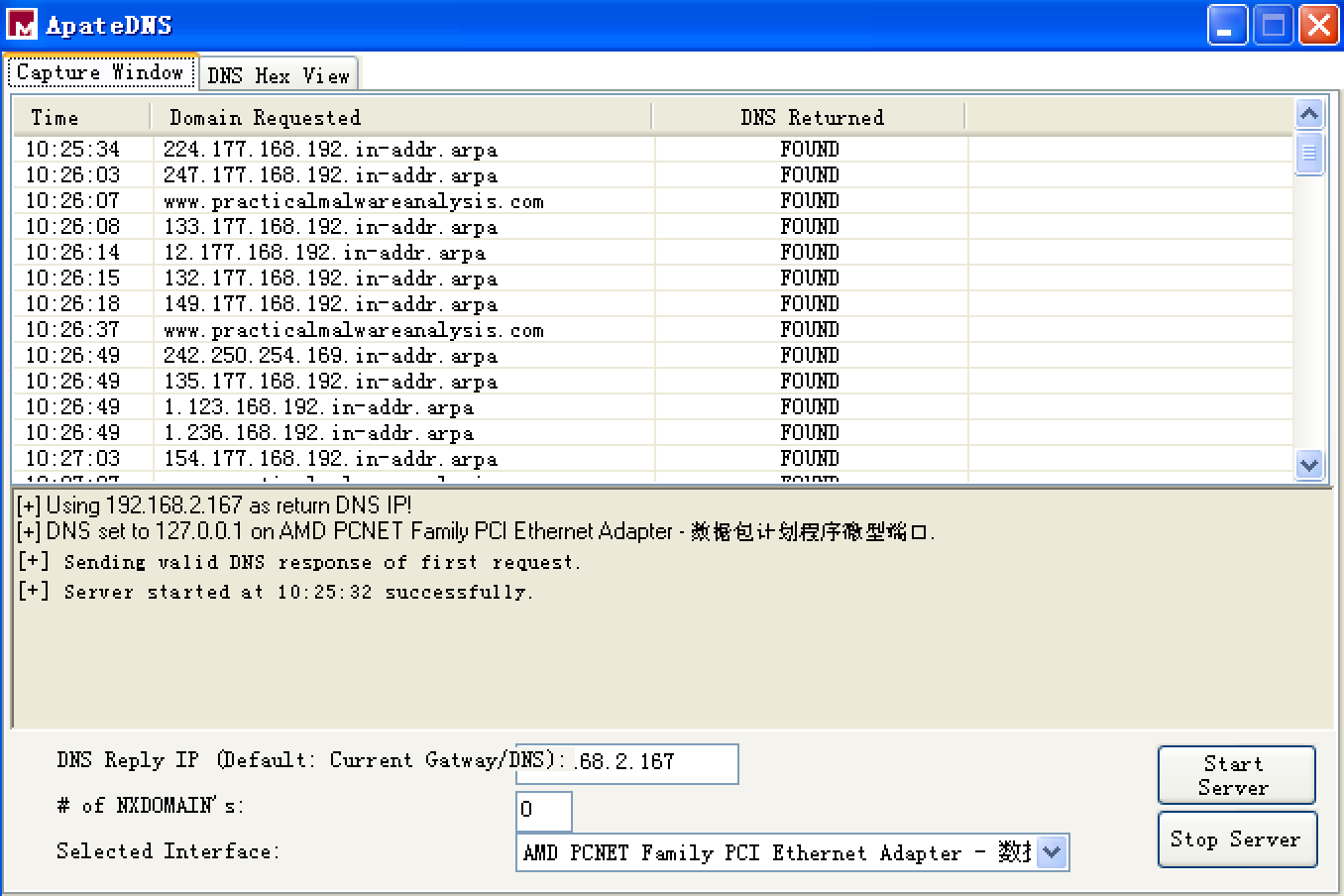
Next, we turn our attention to the network analysis tools we set up for basic dynamic analysis. First we check ApateDNS to see if the malware performed any DNS requests. Examining the output, we see a request for www.practicalmalwareanalysis.com, which matches the strings listing shown earlier. (To be sure that the malware has a chance to make additional DNS requests, if any, perform the analysis process a couple of times to see if the DNS request changes or use the NXDOMAIN functionality of ApateDNS.)

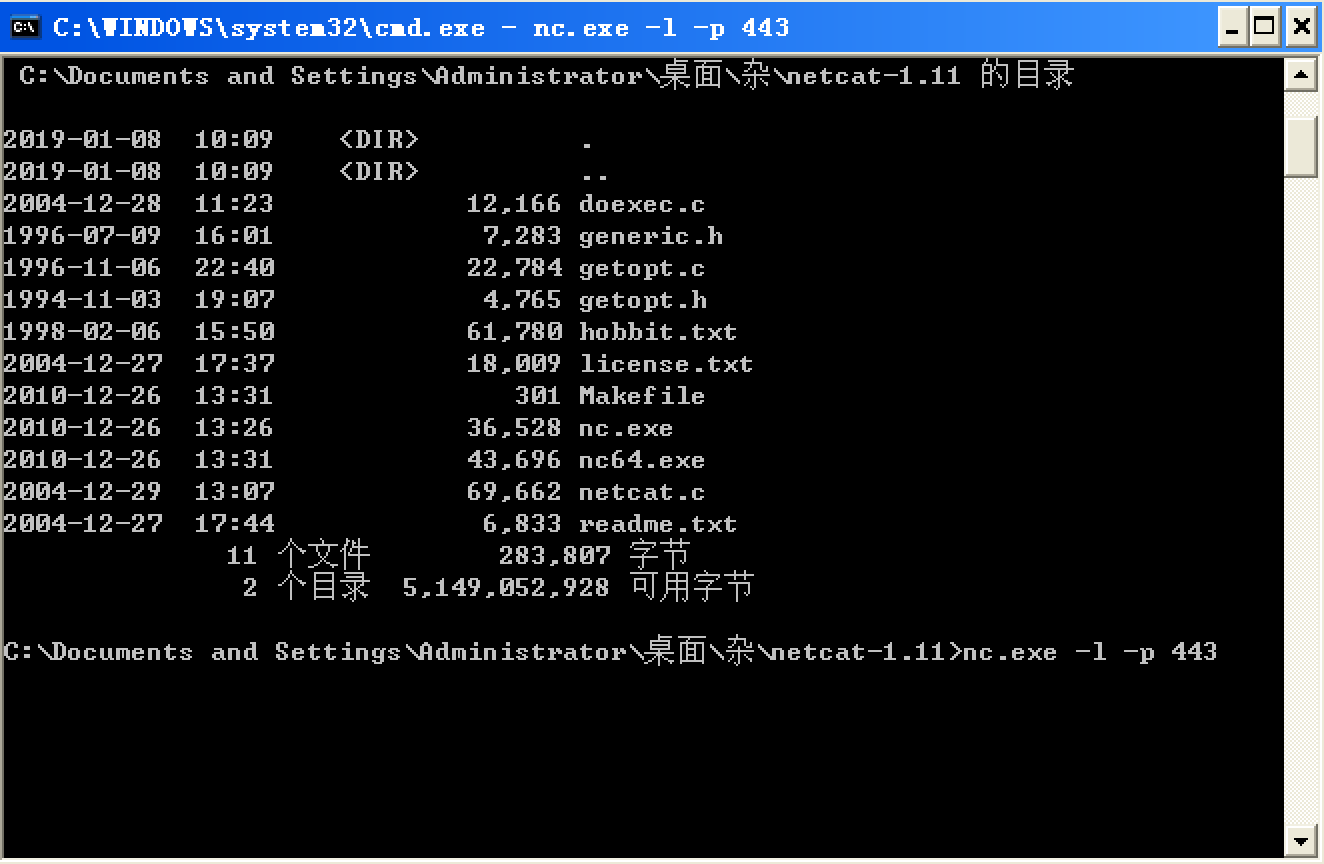
We complete the network analysis by examining the Netcat results, as shown in the following listing.
这里我没有看到书中的信息。书中的信息如下:

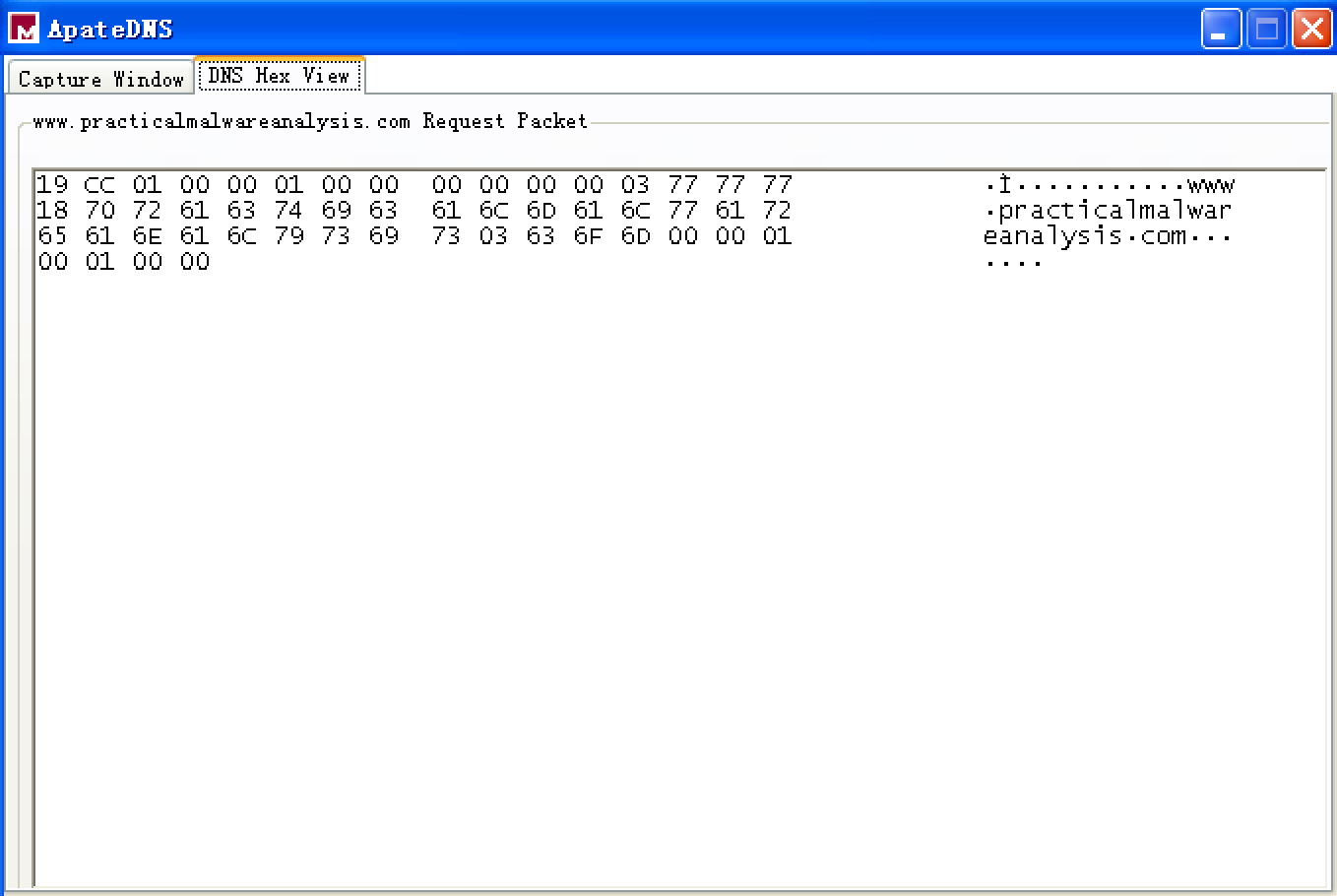
不过双击 ApateDNS 的 Capture Window 窗口的 Domain Requested 相应条目,能够显示 DNS Hex View,如下:
It looks like we got lucky: The malware appears to beacon out over port 443, and we were listening with Netcat over ports 80 and 443. (Use INetSim to listen on all ports at once.) We run this test several times, and the data appears to be random each time.
A follow-up in Wireshark tells us that the beacon packets are of consistent size (256 bytes) and appear to contain random data not related to the SSL protocol that normally operates over port 443.
Preference
Lab 3-1的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- 【Python028--引入文件】
一.打开文件 1.open()函数 打开模式 执行操作 ‘r’ 以只读方式打开文件(默认) ‘w’ 以写入的方式打开文件,会覆盖已存在的文件 ‘x’ 如果文件已经存在,使用此模式打开将引发异常 ...
- iOS 允许后台任务吗?
个人整理 1,用户层: 低电量模式 App后台数据刷新 的开关会影响App后台运行 2, 10分钟时间 后台任务: 在AppDelegate中加入以下代码:不受1影响 - (void)applic ...
- 通过SIMPLE_DEV_PM_OPS定义suspend和resume函数【转】
本文转载自:https://blog.csdn.net/tiantao2012/article/details/77851782 通过SIMPLE_DEV_PM_OPS 定义这个驱动的suspend和 ...
- SpringBoot 消息转换器 HttpMessageConverter
1.简介: Spring在处理请求时,由合适的消息转换器将请求报文绑定为方法中的形参对象,在这里,同一个对象就有可能出现多种不同的消息形式,比如json和xml.同样,当响应请求时,方法的返回值也同样 ...
- 【做题】HDU6331 Walking Plan——矩阵&分块
题意:给出一个有\(n\)个结点的有向图,边有边权.有\(q\)组询问,每次给出\(s,t,k\),问从\(s\)到\(t\)至少经过\(k\)条边的最短路. \(n \leq 50, \, q \l ...
- python 之 文件I/0
打开和关闭文件 open()函数 必须要open()内置函数打开一个文件,创建一个file对象,相关的方法才可以调用它进行读写. 语法 file object=open(file_name [,acc ...
- 论文笔记:A Review on Deep Learning Techniques Applied to Semantic Segmentation
A Review on Deep Learning Techniques Applied to Semantic Segmentation 2018-02-22 10:38:12 1. Intr ...
- [ECharts] - ECharts使用中国地图
格式1: https://www.cnblogs.com/luna666/p/9007263.html (非官方) <!DOCTYPE html> <html lang=" ...
- 什么是SpringCloud
SpringCloud是在SpringBoot的基础上构建的,用于简化分布式系统构建的工具集. 该工具集为微服务架构中所涉及的配置管理,服务发现,智能路由,断路器,微代理和控制总线等操作 提供了一种简 ...
- 异步编程- async和await
使用目的 避免阻塞主线程 提高程序响应能力 C#中使用 C# 中的 Async 和 Await 关键字是异步编程的核心. 疑惑 The async and await keywords don't c ...
