Cyber Security - Palo Alto Firewall V-Wires
Leveraging V-Wires
- Bridge two physical connections and apply security
- Policies without influencing any routing decision(transparent Firewall inspection)
- Inspect per VLAN traffic by creating V-Wire sub interfaces.
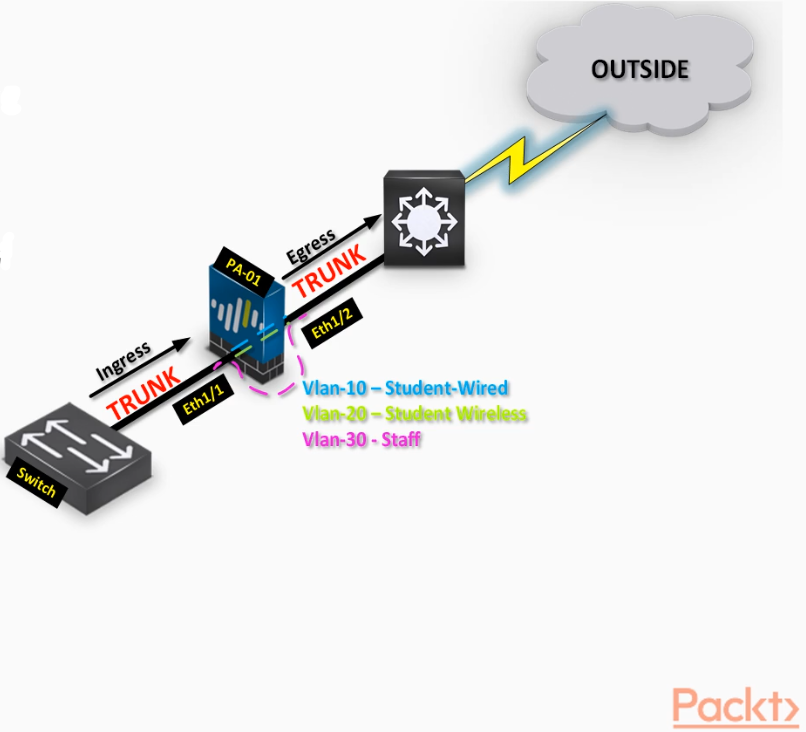
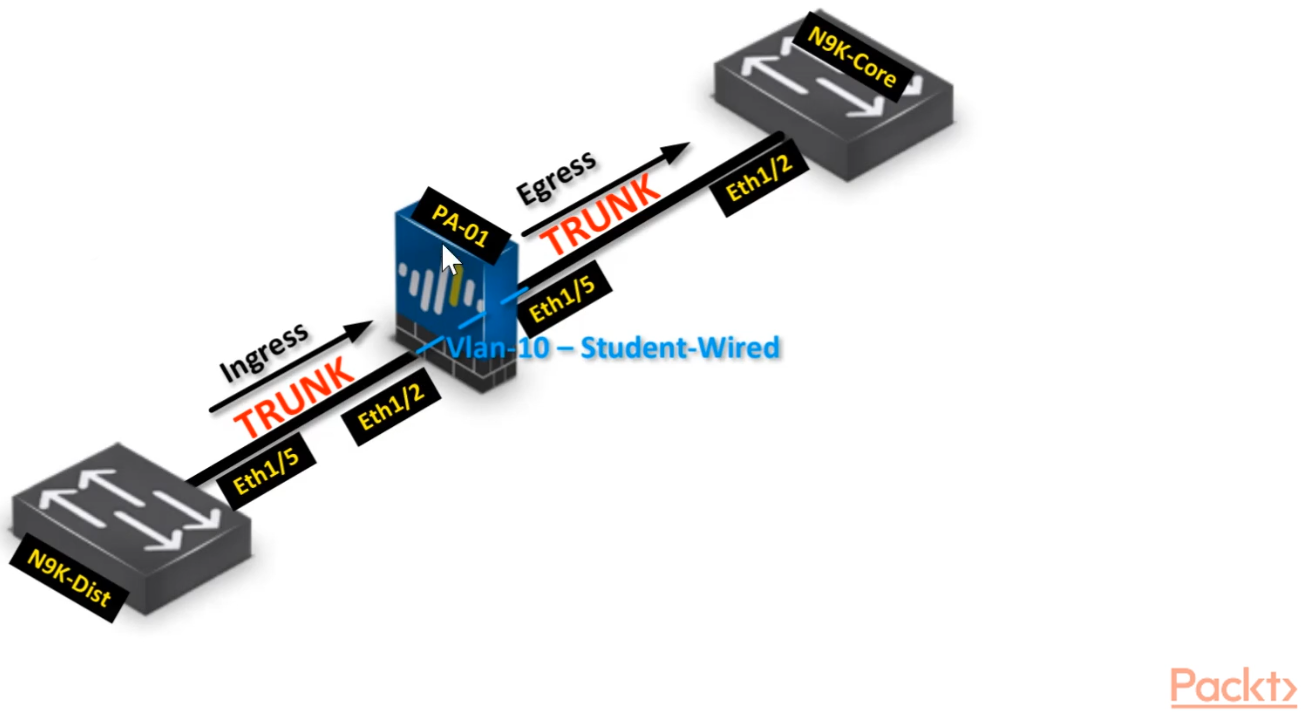
Interface configuration>>
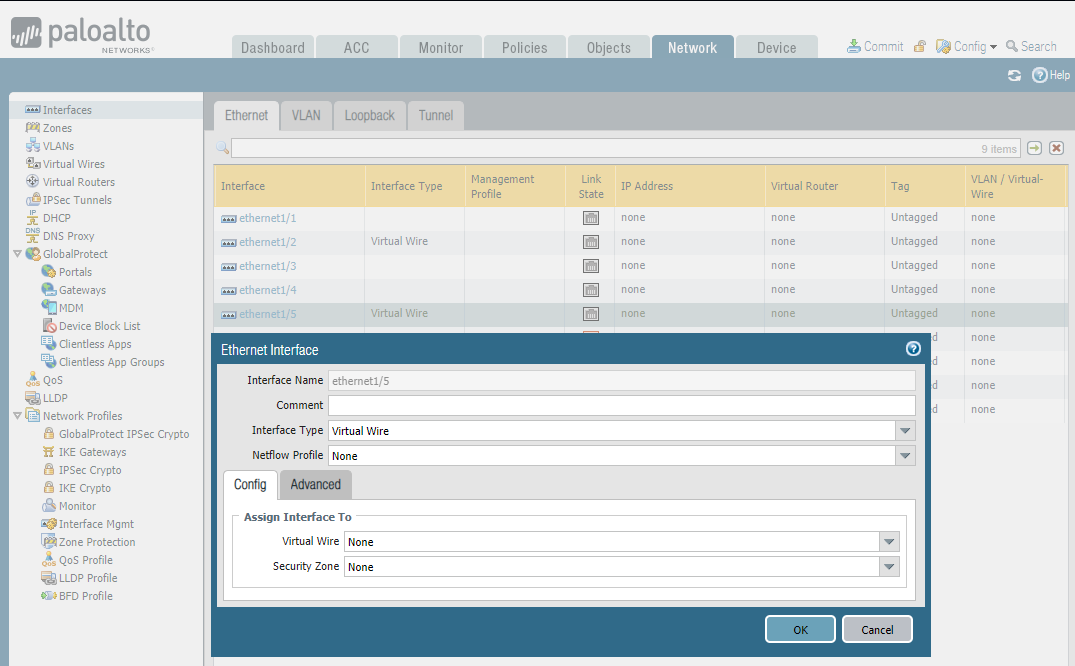
STEP1: Configure parent Virtual Wire interfaces - ethernet 1/2 and ethernet 1/5
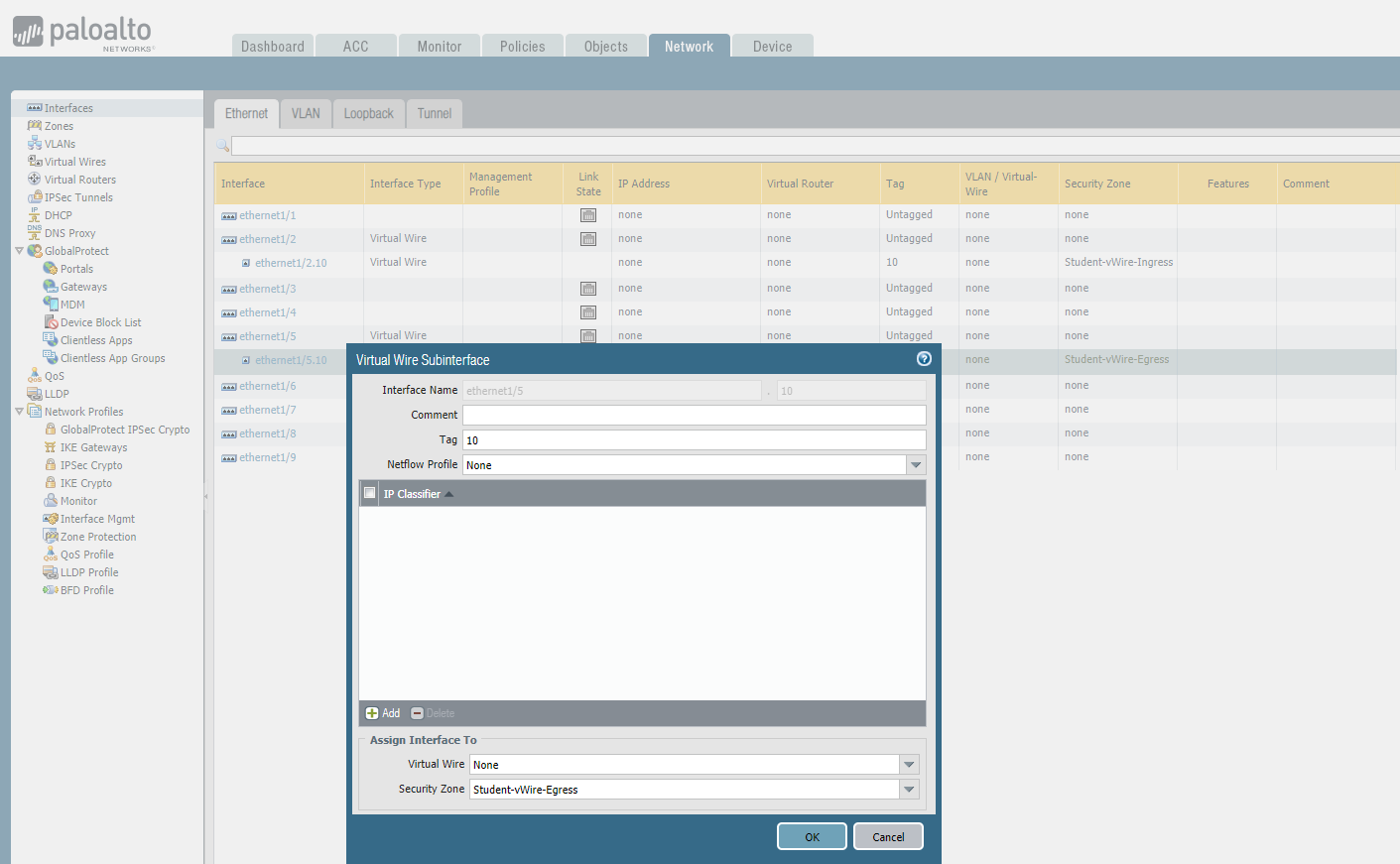
STEP2: Configure subinterface - ethernet1/2.10 and ethernet 1/5/10
STEP3: Connect virtual wires - Parent-vWire
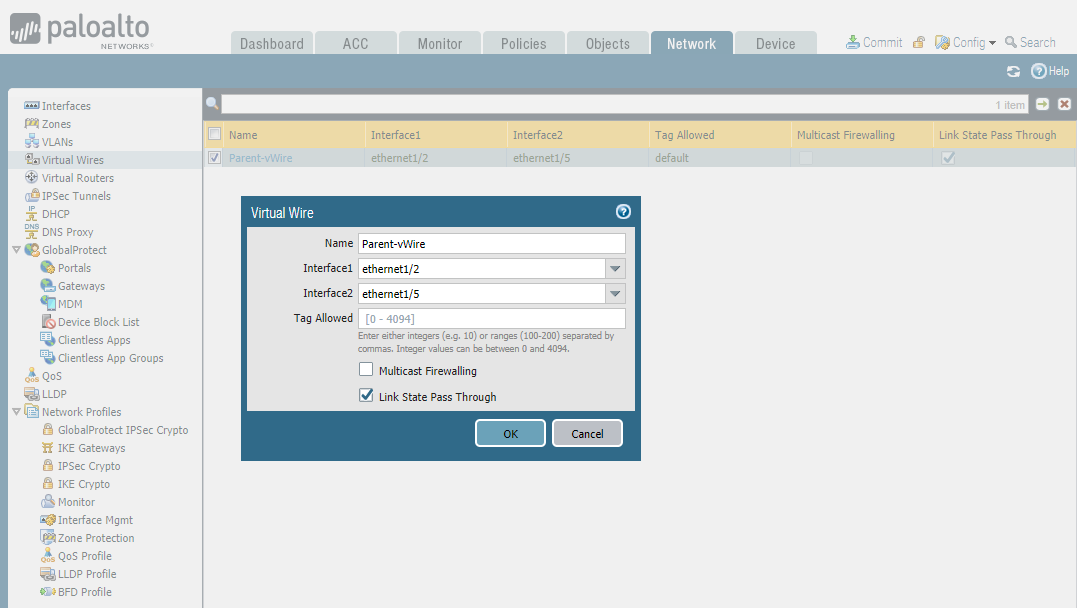
STEP4: Connect virtual wires - Sub-vWire
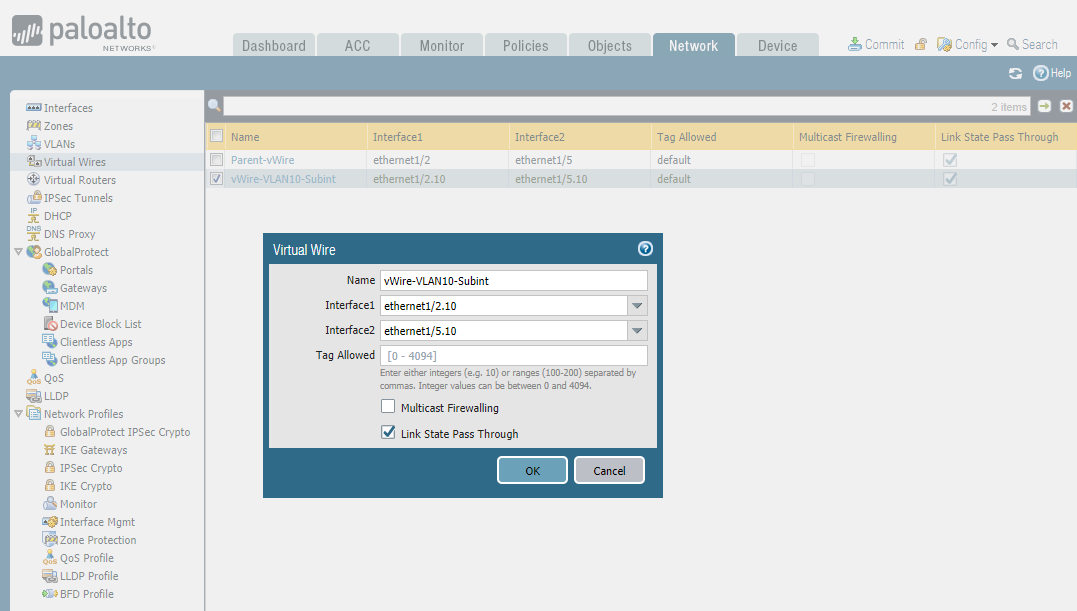
STEP5: Configure security policies.
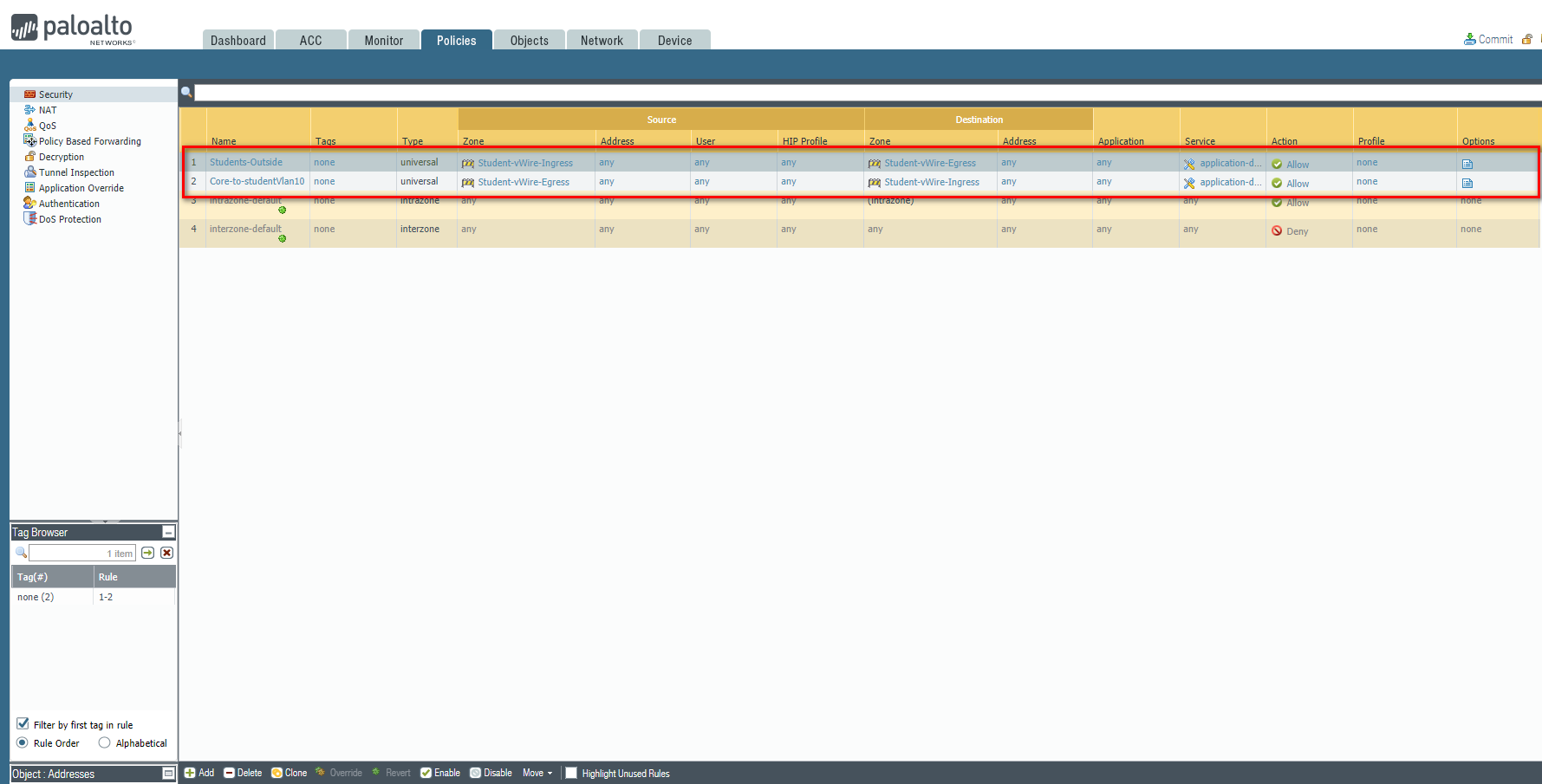
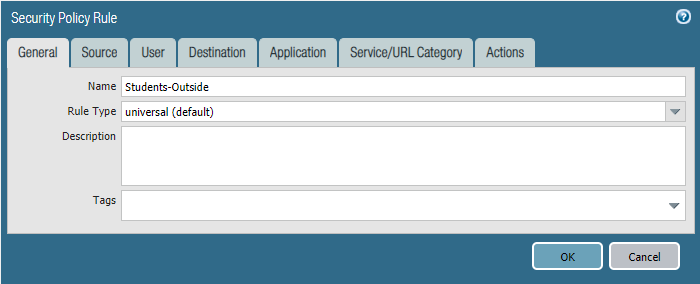
Students-Outside
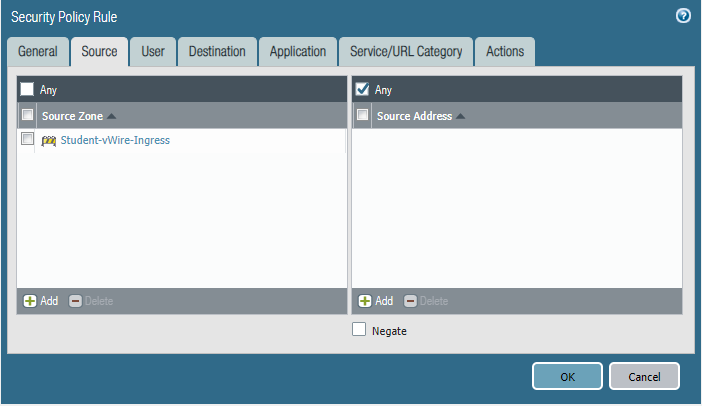
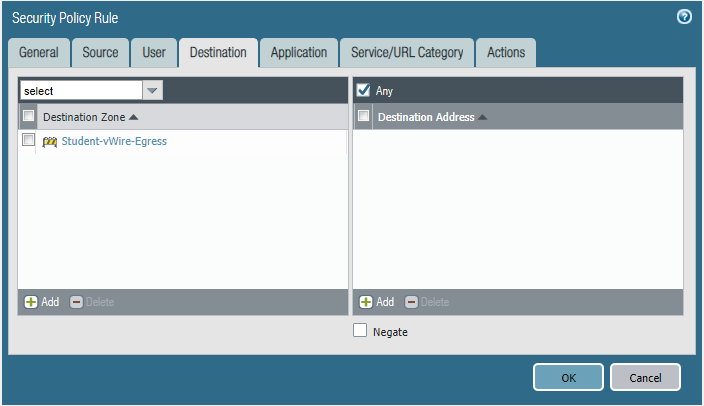
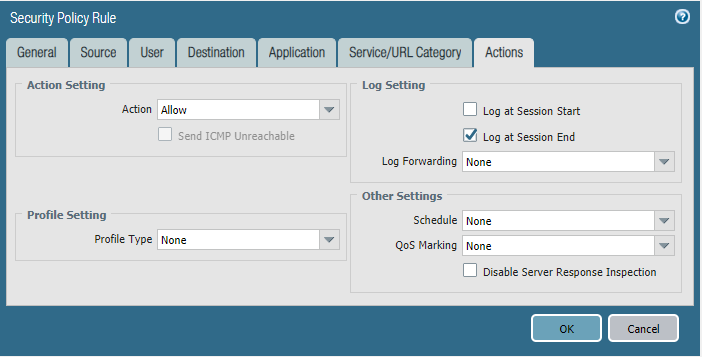
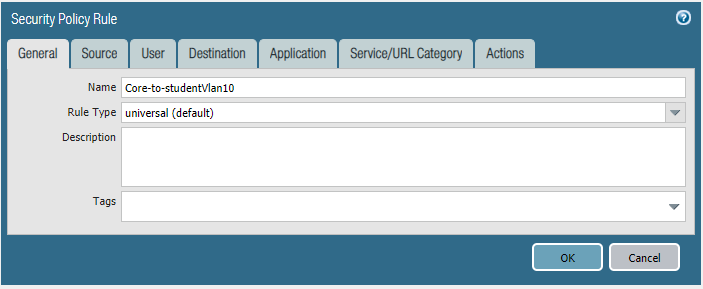
Core-to-studentVlan10
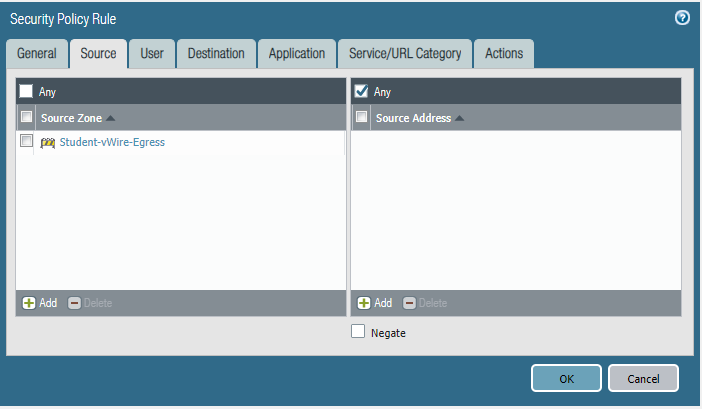
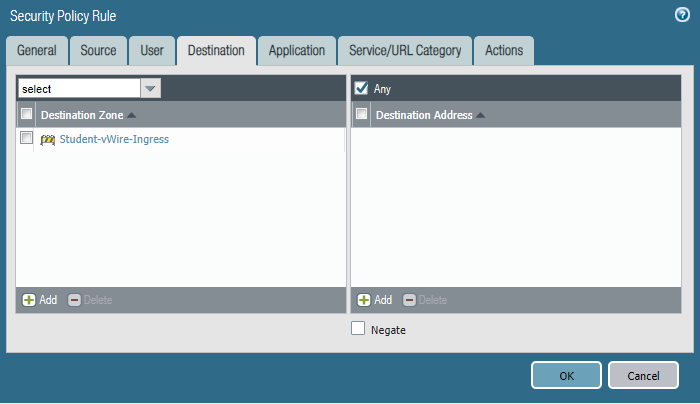
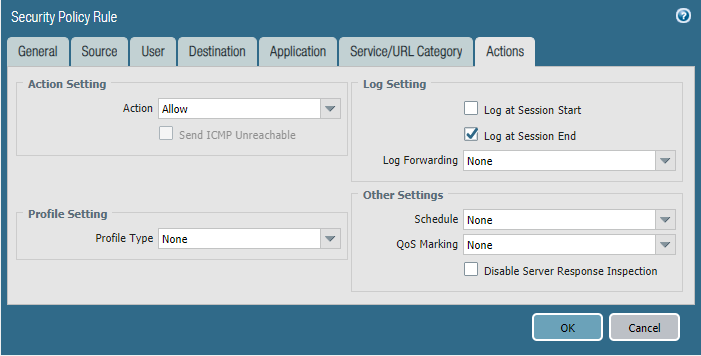
Commit the configuration and test.
Students-Outside
Cyber Security - Palo Alto Firewall V-Wires的更多相关文章
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)
LDAP Authentication and Remote Users and Groups Create Remote User Objects and LDAP Integration: sam ...
- Cyber Security - Palo Alto Firewall Interface Types
Multiple options to integrate the Palo Alto Firewall into your: Network Layer 2 interfaces and VLAN ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)
Address Objects and Groups Creating address objects. Organizing address objects with address groups ...
- Cyber Security - Palo Alto Firewall Security Zones
Firewall Security Zones Zones: The foundational aspect of every Firewall. Police network traffic Enf ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(2)
Users Objects and Groups Creating local user objects. Creating local user groups. https://docs.paloa ...
- Cyber Security - Palo Alto Security Policies(2)
Task 3 The SOC(Security Operation Center) monitoring team dashboard reported more 1,000 requests to ...
- Cyber Security - Palo Alto Security Policies(1)
Security policies: Enforcing network traffic by configuring rules of what is allowed or denied to co ...
- Cyber Security - Palo Alto Basic Introduction
Preparation of the Lab Environment: Download and Install Pan-OS from the following website https://d ...
- Palo Alto GlobalProtect上的PreAuth RCE
0x00 前言 SSL VPN虽然可以保护企业资产免受互联网被攻击的风险影响,但如果SSL VPN本身容易受到攻击呢?它们暴露在互联网上,可以可靠并安全地连接到内网中.一旦SSL VPN服务器遭到入侵 ...
随机推荐
- PageHelper支持GreenPlum
greenplum是pivotal在postgresql的基础上修改的一个数据库,语法和postgresql通用.使用PageHelper做分页插件的时候,发现目前没有针对greenplum做支持,但 ...
- APP自动化1——Appium+pycharm自动化环境搭建全流程
1. 安装python3,pycharm,可参考之前写的文档:https://www.cnblogs.com/chenweitoag/p/13154815.html 2. 准备以下必要工具: 基于wi ...
- s7-200高速脉冲输出与高速计数器讲解
s7-200高速脉冲输出与高速计数器讲解
- HTTP协议简要
HTTP协议简要 HTTP协议是指超文本传输协议,简单来说就是一种规则,允许将HTML文档从Web服务器传送到Web浏览器. HTTP请求 HTTP请求包括三部分:请求行(请求方法),请求头(消息报头 ...
- .Net Core微服务入门全纪录(六)——EventBus-事件总线
前言 上一篇[.Net Core微服务入门全纪录(五)--Ocelot-API网关(下)]中已经完成了Ocelot + Consul的搭建,这一篇简单说一下EventBus. EventBus-事件总 ...
- JavaWeb网上图书商城完整项目--day02-19.修改密码功能流程分析
我们来看看修改密码的业务流程操作:
- java中HashMap和Hashtable的区别
1.HashMap是Hashtable的轻量级实现(非线程安全的实现),他们都完成了Map接口,主要区别在于HashMap允许空(null)键值(key),由于非线程安全,在只有一个线程访问的情况下, ...
- 入门大数据---Redis集群分布式学习
Redis是什么? 官方介绍: Redis 是一个开源(BSD许可)的,内存中的数据结构存储系统,它可以用作数据库.缓存和消息中间件. 它支持多种类型的数据结构,如 字符串(strings), 散列( ...
- 关于Maven我应该知道的事
https://www.cnblogs.com/best/p/9676515.html bilibili 这里不是入门指南, 而是一些个人使用遇到的问题参考 一.环境 Maven 版本JDK要求 Ma ...
- css3中样式计算属性calc()的使用和总结
calc的介绍 在css3样式中有一个类似与函数的计算属性calc(),它主要用于指定元素的长度,无论是border.margin.pading.font-size和width等属性都可以使用calc ...
