Ethical Hacking - GAINING ACCESS(9)
Server Side Attack
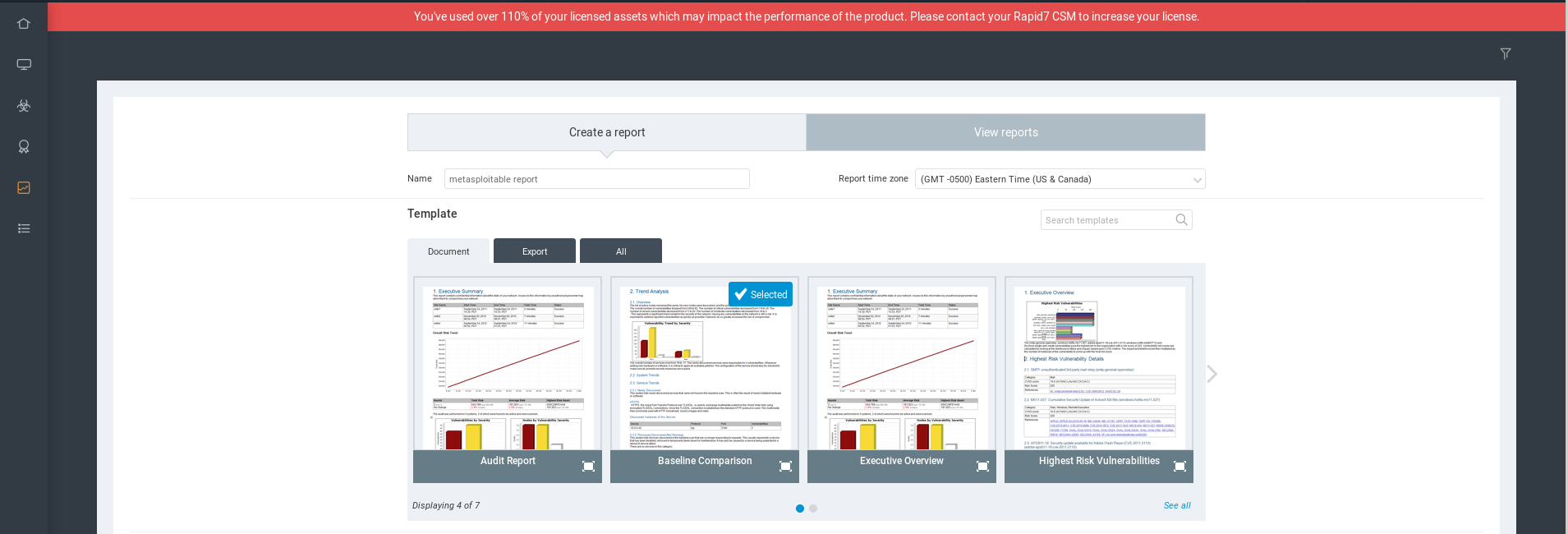
Nexpose - Analysing Scan Results and Generating Reports
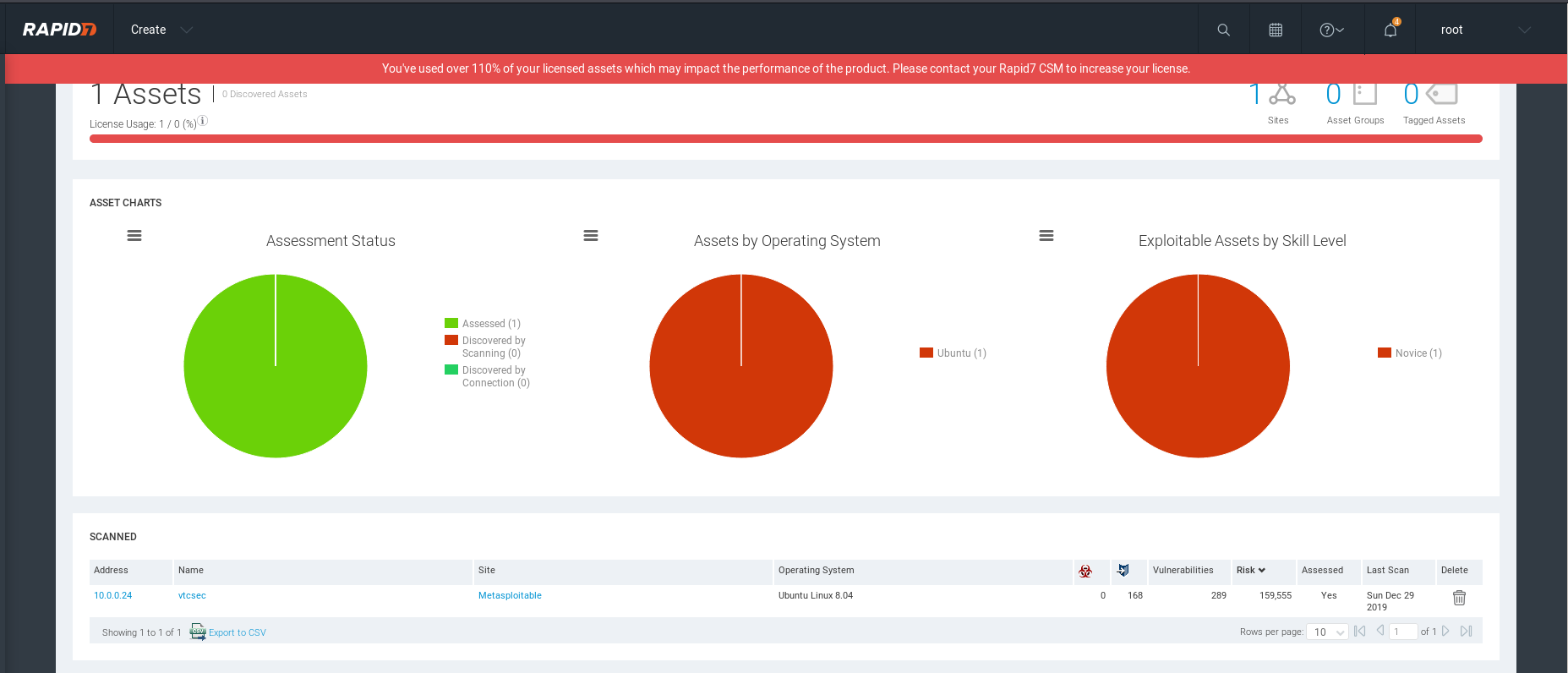
OS and Software Inforation.
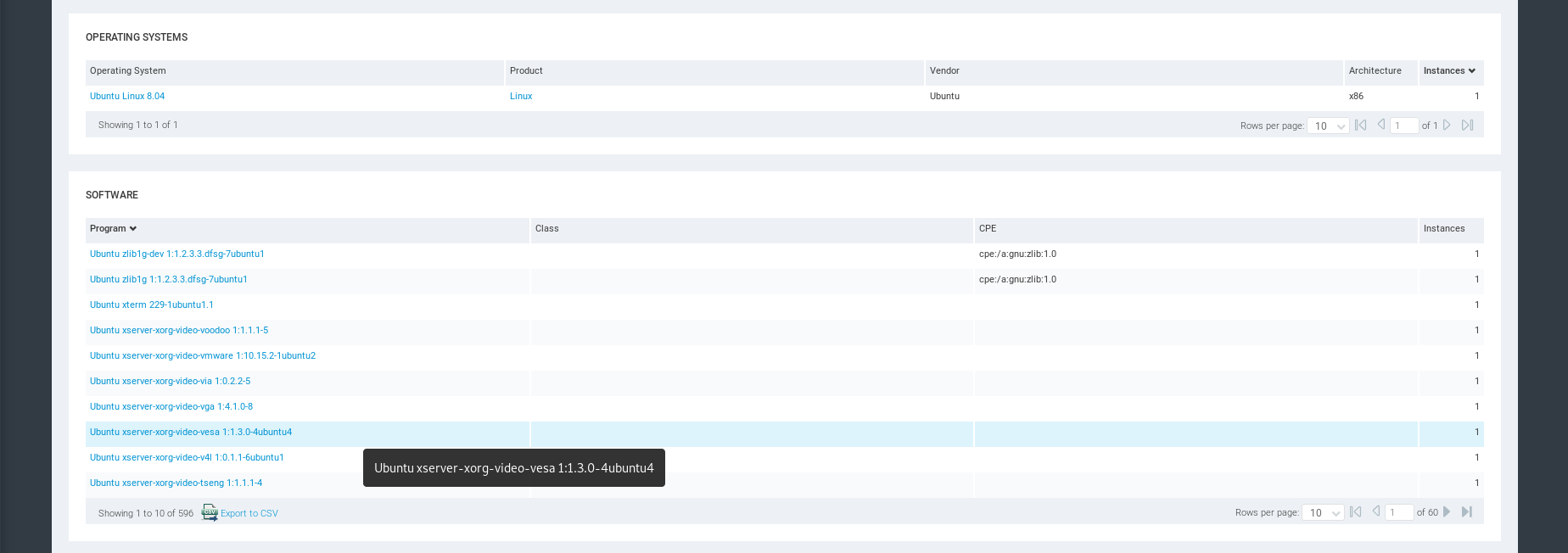
Services Information
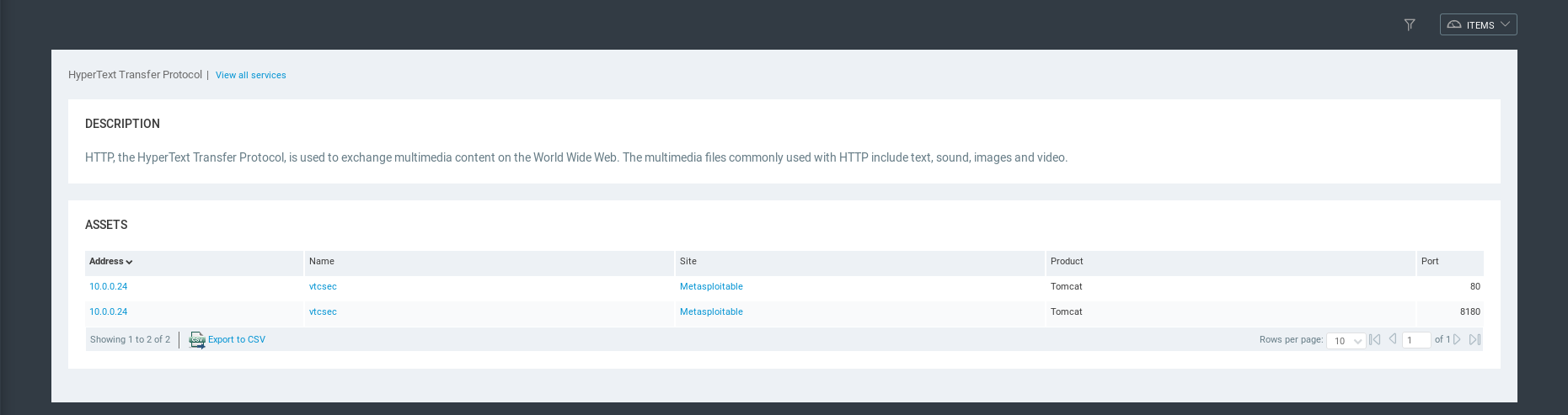
HTTP Service Detailed Information.
Vulnerability Information
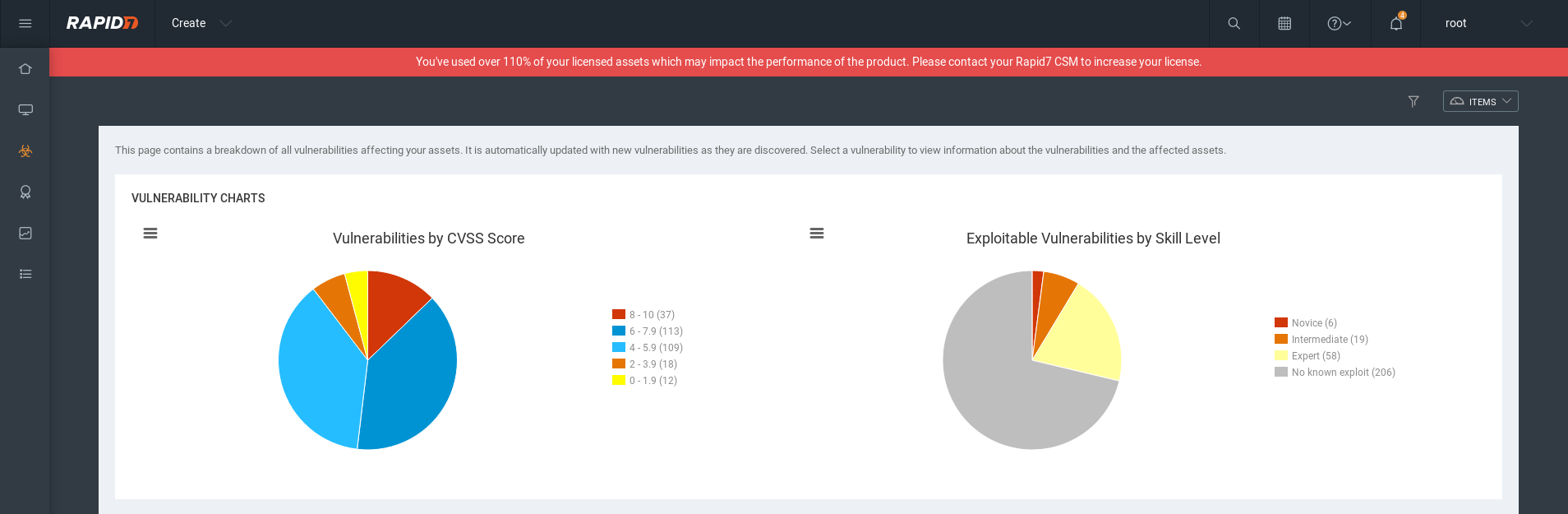
Vulnerabilities list:
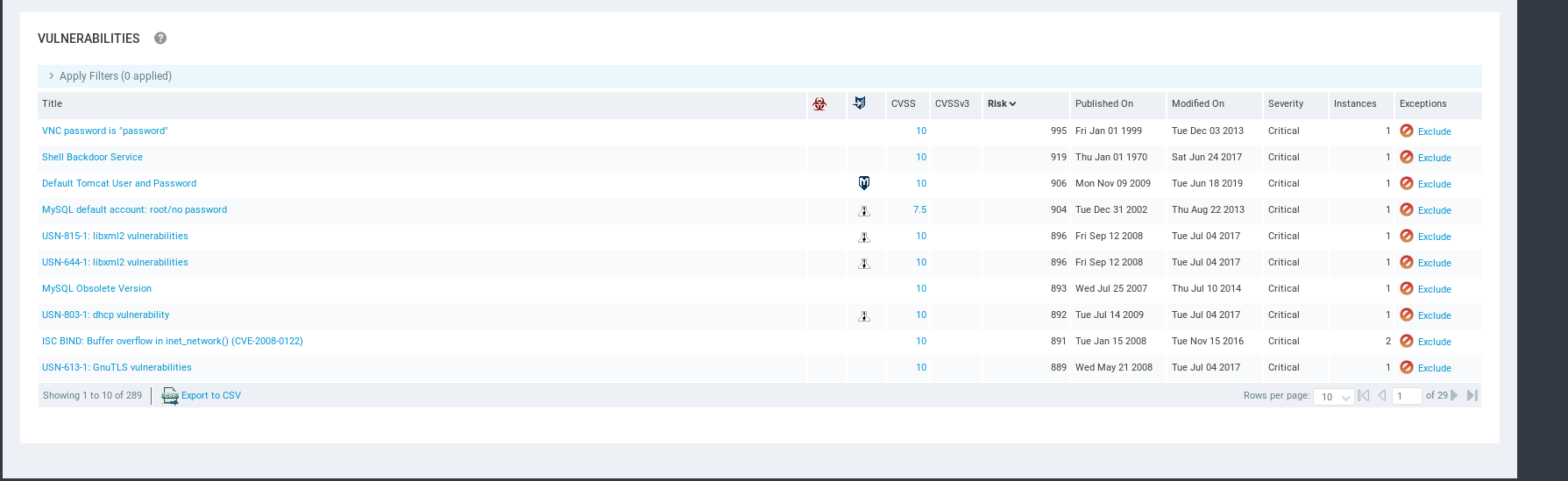
Detailed Vulnerability Information - Affects
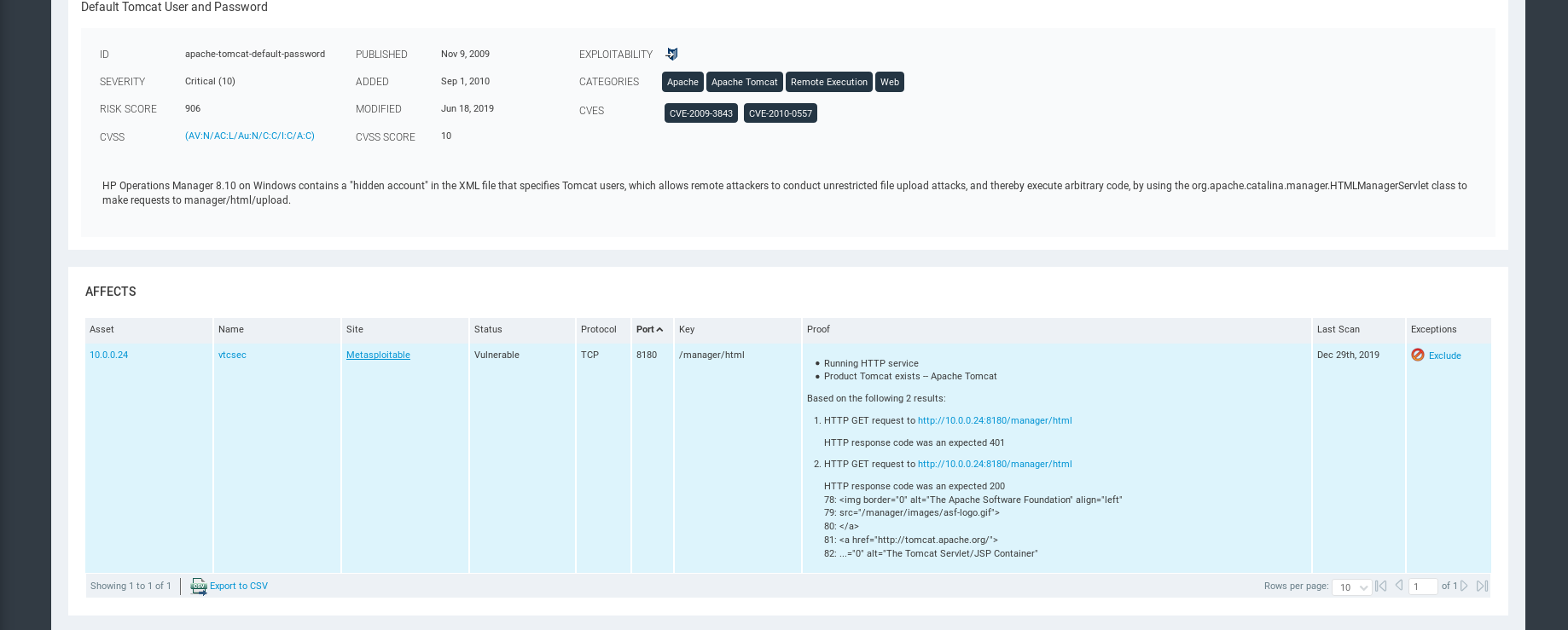
Exploits can be used in Metasploit.
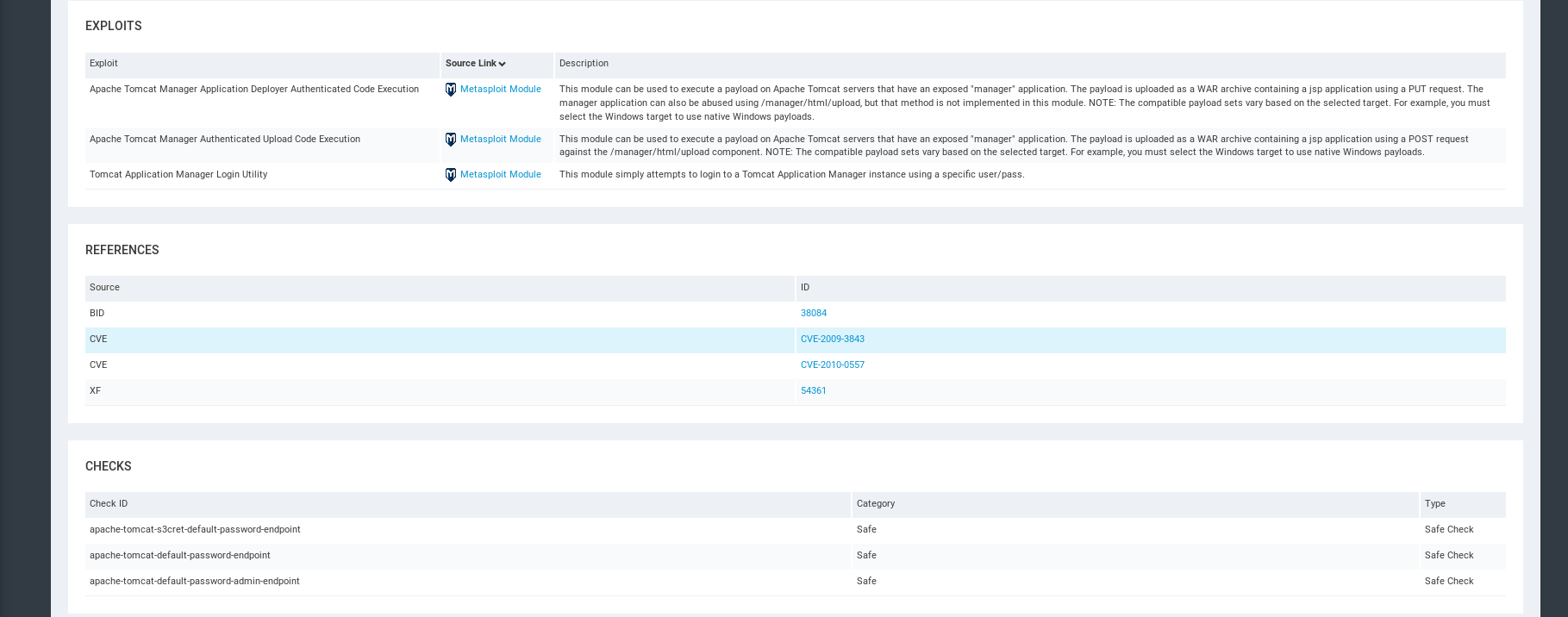
Remediations.
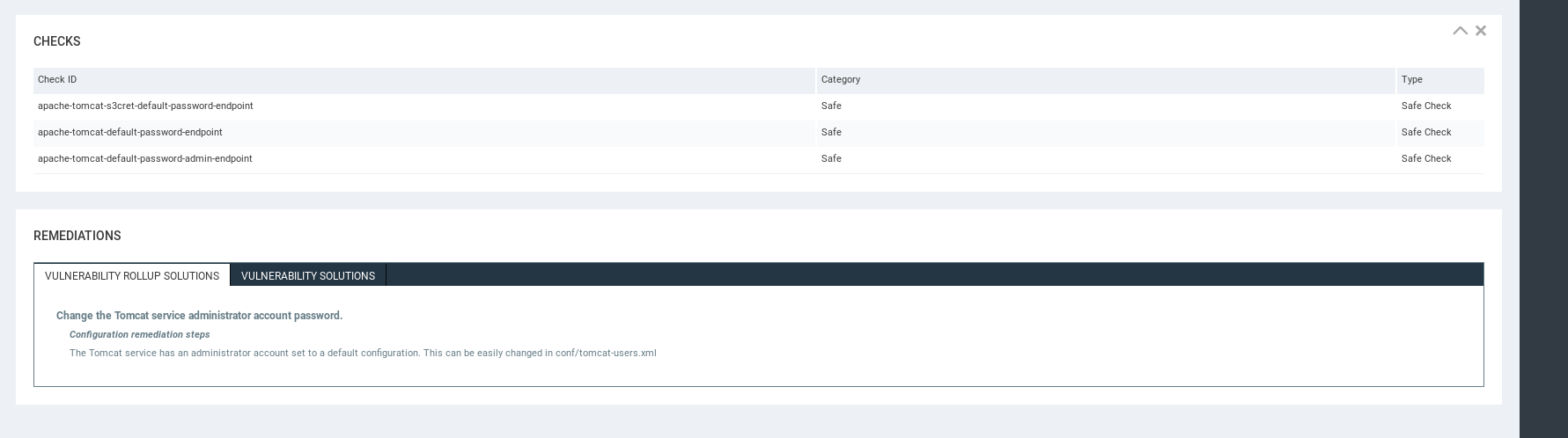
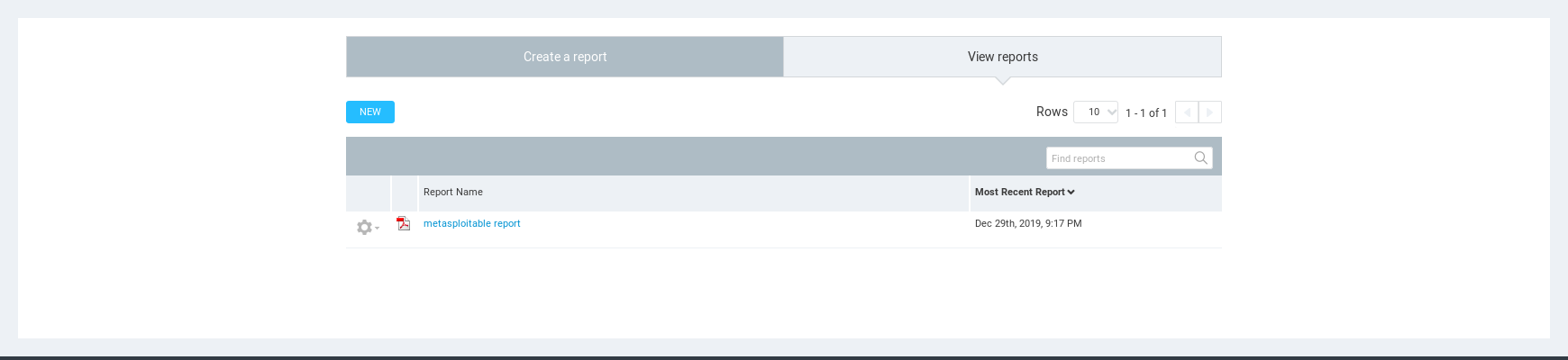
Report
Select the template first.
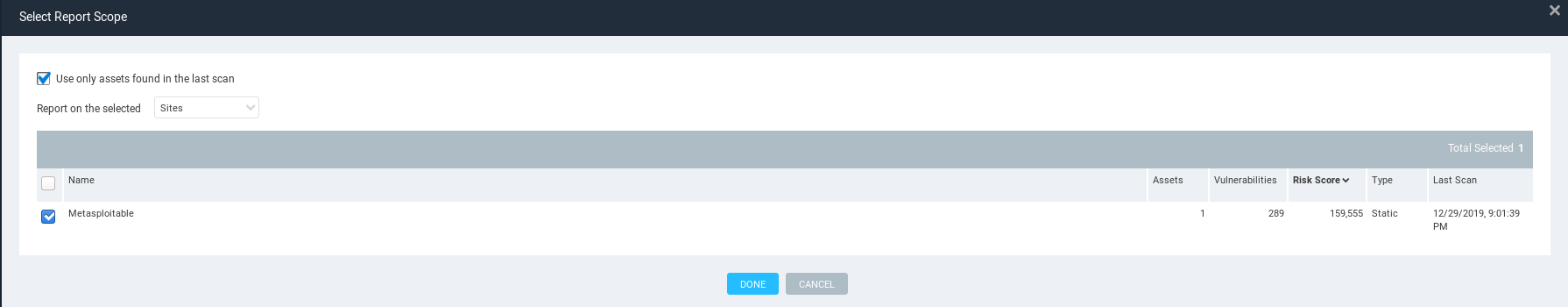
Select Report Scope
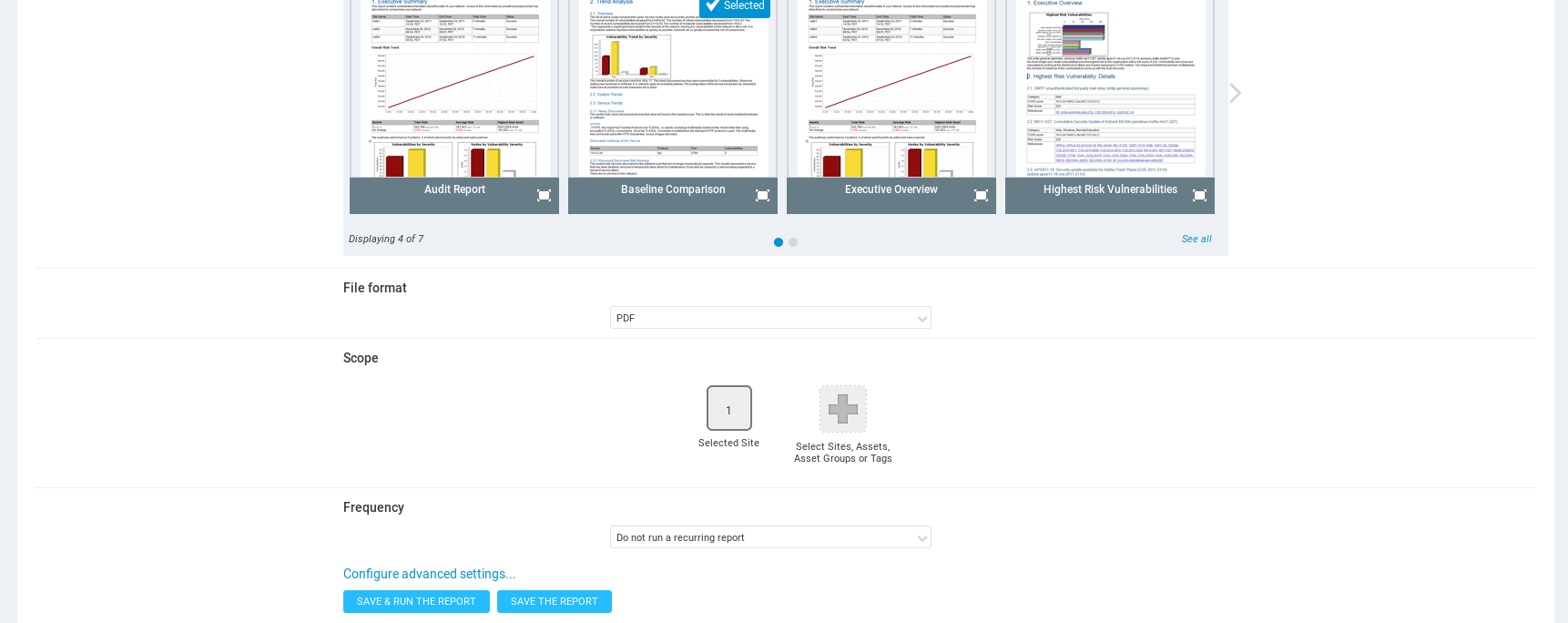
Save and run the report.
View the report result.

Ethical Hacking - GAINING ACCESS(9)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
- Ethical Hacking - GAINING ACCESS(18)
CLIENT SIDE ATTACKS Backdooring ANY file Combine backdoor with any file - Generic solution. Users ar ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
随机推荐
- 'ipconfig' 不是内部或外部命令,也不是可运行的程序 或批处理文件
今天在学习的时候需要找本地ip地址,可是在命令行窗口却显示 百度之后发现原来是环境变量没配置的问题(其实之前是ok的,但应该是anconda安装的时候点了那个一键设置环境变量搞得本地的path里的数据 ...
- python-判断、循环、列表、字典
一.如何将两个列表合并成一个字典 运用dict(zip()) 例如: usernames = ['xiaohei', 'xiaobai', 'xiaoming'] passwords = ['1234 ...
- Flutter学习笔记(38)--自定义控件之组合控件
如需转载,请注明出处:Flutter学习笔记(38)--自定义控件之组合控件 在开始之前想先写点其他的,emm...就是今天在学习到自定义控件的时候,由于自定义控件这块一直是我的短板,无论是Andro ...
- 尚学堂 217 java中的字节码操作2
package com.bjsxt.test; @Author(name="gaoqi", year=2014) public class Emp { private int em ...
- 信息收集-DNS
首先更正一个小白很普遍的错误观点,www.baidu.com(严格上是www.baidu.com. 这个点是根的意思,所有的记录从这里开始)并不是一个真正意义上的域名,而是百度服务器的A记录,baid ...
- vue cli3项目中使用qrcodejs2生成二维码
组件的形式创建 1.下载依赖 npm install qrcodejs2 2.创建一个.vue的组件放置代码(我创建的是qrcodejs2.vue) //template中的代码 <templa ...
- Web安全之验证码绕过
一,验证码绕过(on client) 首先让burpsuite处于抓包状态,打开pikachu的验证码绕过(on client)随意输入账号和密码,验证码先不输入,点击login,会提示验证码错误 然 ...
- Python实用笔记 (16)函数式编程——偏函数
假设要转换大量的二进制字符串,每次都传入int(x, base=2)非常麻烦,于是,我们想到,可以定义一个int2()的函数,默认把base=2传进去: def int2(x, base=2): re ...
- java List的初始化
今天在处理生成excel的时候用到了java的list,但是需要直接赋值固定的几个变量,如果先初始化然后add的方法: List<String> name = new ArrayList( ...
- win中mysql安装
mysql安装: https://www.mysql.com/>官网 下载 [DOWNLOADS]----[MySQL Community Server]社区版---5.6---No thank ...
