Nginx HTTPS功能部署实践
本文出处:http://oldboy.blog.51cto.com/2561410/1889346
30.1 文档目的
本文目的提高自己文档的写作能力及排版能力,加强上课所讲的内容得以锻炼也方便自己以后查阅特写此文档。
30.2 文档内容
本章内容包括:单向和双向认证的概念、openssl的介绍、Nginx单向ssl的配置前提、使用openssl制作证书(单向认证与双向认证)。
30.3 单向认证与双向认证的概念
30.3.1 什么是单向认证
单项认证就是比如你有个密码用户名然后和服务器上的用户信息进行比对一致的话你们就可以建立连接.
30.3.2 什么是双向认证
SSL的双向认证就是客户端要获取服务端的证书,检查下服务端是不是我可以信任的主机,否则我就认为那个站点的内容不可信任,不应该去访问你(浏览器会告诉你),同时服务端也要检查客户端的证书,客户端如果不是服务端所信任的,那服务端也会认为,你不是我的合法用户,我拒绝给你提供服务。所以要让 HTTPS的双向认证顺利完成,就要在服务端给定一个证书,这个证书是浏览器可信任的,同时客户端(浏览器)也要发送给服务端一个证书,服务器端也要信任这个证书。
要想让浏览器纯自然地就去信任服务端的证书,那服务端所使用的证书就得是那几大已经被大家所信任的证书机构给他签名,不过一般要钱。
通俗点来讲就是你有个密码用户名你先发给服务器进行比对,如果一致服务器再把它的密码用户名发到你机器上与你机器上保留的用户信息进行比对如果还一致则建立链接!
30.4 openssl的介绍
openssl为开源软件,在Linux(或UNIX/Cygwin)下创建一个简单的CA。(certification authority)是以构建在公钥基础设施pki(public key infrastructure)基础之上的产生和确定数字证书的第三方可信机构)我们可以利用这个CA进行PKI、数字证书相关的测试。比如,在测试用Tomcat或Apache构建HTTPS双向认证时,我们可以利用自己建立的测试CA来为服务器端颁发服务器数字证书,为客户端(浏览器)生成文件形式的数字证书(可以同时利用openssl生成客户端私钥。
30.5 Nginx单双向ssl的配置前提
LNMP环境的前提下
编译安装Nginx时候安装的两个参数--with-http_stub_status_module、(是为了启用nginx的NginxStatus 功能,用来监控nginx的当前状态)--with-http_ssl_module(启动ssl模块)
安装openssl openssl-devel
[root@LNMP ~]# /application/nginx/sbin/nginx -V
nginx version: nginx/1.6.2
built by gcc 4.4.7 20120313 (Red Hat 4.4.7-11)(GCC)
configure arguments: --user=nginx --group=nginx--prefix=/application/nginx-1.6.2 --with-http_stub_status_module--with-http_ssl_module
30.6 使用openssl制作证书
30.6.1 服务器单项认证
30.6.1.1 创建并进入sslkey存放目录
[root@LNMP ~]# mkdir -p /application/nginx/sslkey
[root@LNMP ~]# cd /application/nginx/sslkey/
30.6.1.2 生成RSA密钥
[root@LNMP sslkey]# openssl genrsa -out key.pem2048
30.6.1.3 生成一个证书请求
[root@LNMP sslkey]# openssl req -new -key key.pem-out cert.csr
You are about to be asked to enter informationthat will be incorporatedThere are quite a few fields but you can leave someblank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
Country Name (2 letter code) [XX]:cn //输入国家名字
State or Province Name (full name) []:bj //输入省市
Locality Name (eg, city) [Default City]:bj //输入省市
Organization Name (eg, company) [Default CompanyLtd]:bj //输入公司名称
Organizational Unit Name (eg, section) []:bj //组织名字
Common Name (eg, your name or your server'shostname) []:www.etiantian.org //要配置的ssl域名
Email Address []:260428042@qq.com //Email地址
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456 //密码
An optional company name []:123456 //密码
30.6.1.4 修改nginx的主配置文件
[root@LNMP ~]# cat/application/nginx/conf/nginx.conf
worker_processes 1;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 65;
server{
listen 443;
server_name www.etiantian.org;
ssl on;
ssl_certificate /application/nginx/sslkey/server.crt;
ssl_certificate_key /application/nginx/sslkey/server.key;
ssl_session_timeout 5m;
ssl_protocols SSLv3 TLSv1;
ssl_ciphers HIGH:!ADH:!EXPORT56:RC4+RSA:+MEDIUM;
ssl_prefer_server_ciphers on;
location/ {
root html/blog;
index index.html index.htm;
}
}
}
[root@LNMP ~]# /application/nginx/sbin/nginx –t //检查语法
[root@LNMP ~]# /application/nginx/sbin/nginx -sreload //重新启动
30.6.1.5验证结果
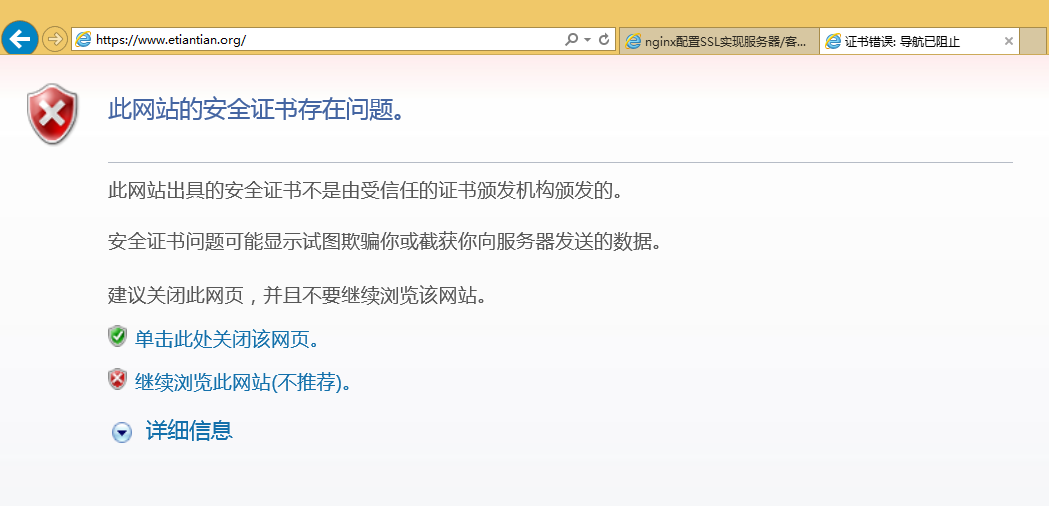
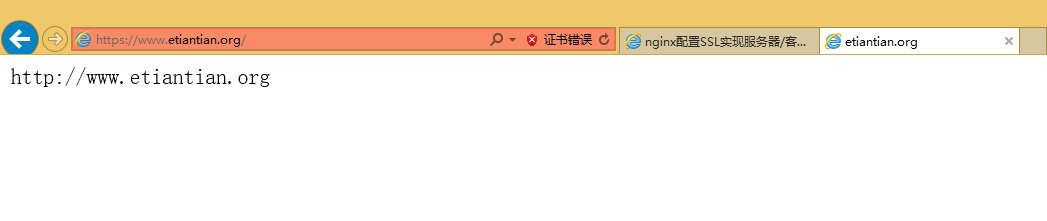
30.6.2 服务器客户端双向认证
30.6.2.1 分别创建证书各自存放目录
[root@LNMP~]# mkdir /application/nginx/ca
[root@LNMP~]# cd /application/nginx/ca
[root@LNMPca]# mkdir newcerts private conf server
newcerts子目录将存放CA签署(颁发)过的数字证书(证书备份目录)。
private目录用于存放CA的私钥。
conf只是用于存放一些简化参数。
Server 目录用于存放自己的证书。
1、在conf目录创建文件openssl.conf配置文件
[root@LNMP~]# cat /application/nginx/ca/conf/openssl.conf
[ ca ]
default_ca = foo #默认ca的段名配置好后 openssl 就会
寻找相同段名的配置
[ foo ]
dir =/application/nginx/ca #ca 的顶级目录
database =/application/nginx/ca/index.txt #的数据库索引文件
new_certs_dir = /application/nginx/ca/newcerts#新生成的CA目录
certificate = /application/nginx/ca/private/ca.crt #CA证书
serial = /application/nginx/ca/serial #CA序列号文件
private_key = /application/nginx/ca/private/ca.key # CA私钥
RANDFILE =/application/nginx/ca/private/.rand #随机数文件
default_days = 365 # CA证书的有效期
default_crl_days= 30 #CA证书过期前多久提示
default_md = md5 # 加密方法
#unique_subject = no
policy =policy_any #客户端默认设置
[ policy_any ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = match
localityName = optional
commonName = supplied
emailAddress = optional
30.6.2.2 使用脚本创建新根CA证书
1、查看脚本内容
[root@LNMP ~]# cat/application/nginx/ca/new_ca.sh
#!/bin/sh
生成CA私钥
openssl genrsa -out private/ca.key
生成证书请求
openssl req -new -key private/ca.key -outprivate/ca.csr
签名 CA 证书请求,使用自己的私钥来给这个 CA 证书请求签名
openssl x509 -req -days 365 -in private/ca.csr-signkey private/ca.key -out private/ca.crt
以下三行与创建 CA 秘钥数据库索引文件有关
echo FACE > serial
touch index.txt
openssl ca -gencrl -out/application/nginx/ca/private/ca.crl -crldays 7 -config"/application/nginx/ca/conf/openssl.conf"
2、执行脚本创建根CA证书
[root@LNMP ca]# sh new_ca.sh
Generating RSA private key, 1024 bit long modulus
.......................................++++++
.++++++
e is 65537 (0x10001)
You are about to be asked to enter informationthat will be incorporated
into your certificate request.
What you are about to enter is what is called aDistinguished Name or a DN.
There are quite a few fields but you can leavesome blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:bj
Locality Name (eg, city) [Default City]:bj
Organization Name (eg, company) [Default CompanyLtd]:bj
Organizational Unit Name (eg, section) []:bj
Common Name (eg, your name or your server'shostname) []:www.etiantian.org
Email Address []:260428042@qq.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:123456
Signature ok
subject=/C=cn/ST=bj/L=bj/O=bj/OU=bj/CN=www.etiantian.org/emailAddress=60428042@qq.com
Getting Private key
Using configuration from/application/nginx/ca/conf/openssl.conf
3、查看生成的CA证书并保证里边有内容
30.6.2.3 使用脚本生成服务器证书
1、查看脚本内容
[root@LNMP ~]# cd /application/nginx/ca/
[root@LNMP ca]# cat new_server.sh
# Create us a key. Don't bother putting apassword on it since you will need it to start apache. If you have a betterwork around I'd love to hear it.
创建服务器私钥
openssl genrsa -out server/server.key
利用私钥创建一个证书签名请求
openssl req -new -key server/server.key -outserver/server.csr
openssl ca -in server/server.csr -certprivate/ca.crt -keyfile private/ca.key -out server/server.crt -config"/application/nginx/ca/conf/openssl.conf"
2、执行脚本创建生成服务器证书
[root@LNMP ca]#sh new_server.sh
Generating RSAprivate key, 1024 bit long modulus
.....................++++++
...........................................................++++++
e is 65537(0x10001)
You are about tobe asked to enter information that will be incorporated
into yourcertificate request.
What you areabout to enter is what is called a Distinguished Name or a DN.
There are quitea few fields but you can leave some blank
For some fieldsthere will be a default value,
If you enter'.', the field will be left blank.
Country Name (2letter code) [XX]:cn
State orProvince Name (full name) []:bj
Locality Name(eg, city) [Default City]:bj
OrganizationName (eg, company) [Default Company Ltd]:bj
OrganizationalUnit Name (eg, section) []:bj
Common Name (eg,your name or your server's hostname) []:www.etiantian.org
Email Address[]:260428042@qq.com
Please enter thefollowing 'extra' attributes
to be sent withyour certificate request
A challengepassword []:123456
An optionalcompany name []:123456
Using configurationfrom /application/nginx/ca/conf/openssl.conf
Check that therequest matches the signature
Signature ok
The Subject'sDistinguished Name is as follows
countryName :PRINTABLE:'cn'
stateOrProvinceName :ASN.1 12:'bj'
localityName :ASN.1 12:'bj'
organizationName :ASN.1 12:'bj'
organizationalUnitName:ASN.112:'bj'
commonName :ASN.1 12:'www.etiantian.org'
emailAddress :IA5STRING:'60428042@qq.com'
Certificate isto be certified until Mar 5 10:14:252016 GMT (365 days)
Sign thecertificate? [y/n]:y
1 out of 1certificate requests certified, commit? [y/n]y
Write outdatabase with 1 new entries
3、查看生成的服务器证书里边有内容否则后边会报错
30.6.2.4 配置Nginx的主配置文件
[root@LNMP ~]#cat /application/nginx/conf/nginx.conf
worker_processes 1;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 65;
# HTTPSserver
server {
listen 443;
root html/blog;
index index.phpindex.html index.htm;
server_name www.etiantian.org;
ssi on;
ssi_silent_errorson;
ssi_typestext/shtml;
ssl on;
ssl_certificate /application/nginx/ca/server/server.crt;
ssl_certificate_key /application/nginx/ca/server/server.key;
ssl_client_certificate/application/nginx/ca/private/ca.crt;
ssl_session_timeout 5m;
ssl_verify_clienton;
ssl_protocols SSLv2 SSLv3 TLSv1;
ssl_ciphersALL:!ADH:!EXPORT56:RC4+RSA:+HIGH:+MEDIUM:+LOW:+SSLv2:+EXP;
ssl_prefer_server_ciphers on;
location / {
root html/blog;
index index.php index.html index.htm;
}
}
}
[root@LNMP ~]#/application/nginx/sbin/nginx –t //检查语法
[root@LNMP ~]#/application/nginx/sbin/nginx -s reload //重新启动
30.6.2.5 验证结果
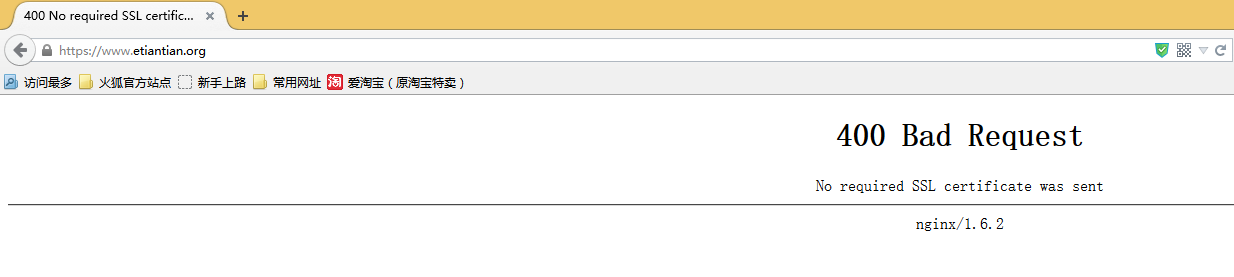
30.6.2.6 访问出现400 Bad Reques解决办法生成客户端证书
1、查看脚本内容
[root@LNMP ~]#cat /application/nginx/ca/new_user.sh
#!/bin/sh
base="/application//nginx/ca"
mkdir -p$base/users/
生成客户端私钥
openssl genrsa-des3 -out $base/users/client.key 1024
根据证书生成私钥请求
openssl req -new-key $base/users/client.key -out $base/users/client.csr
生成客户端证书
openssl ca -in$base/users/client.csr -cert $base/private/ca.crt -keyfile $base/private/ca.key-out $base/users/client.crt -config "/application/nginx/ca/conf/openssl.conf"
将客户端证书转为PKCS(Personal Information Exchange)12 后缀,使大多数浏览器都能接
openssl pkcs12-export -clcerts -in $base/users/client.crt -inkey $base/users/client.key -out$base/users/client.p12
2、执行脚本生成客户端证书
[root@LNMP ca]#sh new_user.sh
Generating RSAprivate key, 1024 bit long modulus
....++++++
...................................................++++++
e is 65537(0x10001)
Enter passphrase for /application//nginx/ca/users/client.key:
Verifying -Enter pass phrase for /application//nginx/ca/users/client.key:
Enter pass phrasefor /application//nginx/ca/users/client.key:
You are about tobe asked to enter information that will be incorporated
into yourcertificate request.
What you areabout to enter is what is called a Distinguished Name or a DN.
There are quitea few fields but you can leave some blank
For some fieldsthere will be a default value,
If you enter'.', the field will be left blank.
-----
Country Name (2letter code) [XX]:cn
State orProvince Name (full name) []:bj
Locality Name(eg, city) [Default City]:bj
OrganizationName (eg, company) [Default Company Ltd]:bj
OrganizationalUnit Name (eg, section) []:bj
Common Name (eg,your name or your server's hostname) []:www.etiantian.org
Email Address[]:260428042@qq.com
Please enter thefollowing 'extra' attributes
to be sent withyour certificate request
A challengepassword []:123456
An optionalcompany name []:123456
Usingconfiguration from /application/nginx/ca/conf/openssl.conf
Check that therequest matches the signature
Signature ok
The Subject'sDistinguished Name is as follows
countryName :PRINTABLE:'cn'
stateOrProvinceName :ASN.1 12:'bj'
localityName :ASN.1 12:'bj'
organizationName :ASN.1 12:'bj'
organizationalUnitName:ASN.112:'bj'
commonName :ASN.1 12:'www.etiantian.org'
emailAddress :IA5STRING:'60428042@qq.com'
Certificate isto be certified until Mar 5 10:24:172016 GMT (365 days)
Sign thecertificate? [y/n]:y
1 out of 1certificate requests certified, commit? [y/n]y
Write outdatabase with 1 new entries
Data BaseUpdated
Enter passphrase for /application//nginx/ca/users/client.key:
Enter ExportPassword:
Verifying -Enter Export Password:
3、查看生成的证书
将client.p12下载到本地桌面
[root@LNMP ~]#cd /application/nginx-1.6.2/ca/users/
[root@LNMPusers]# sz -y client.p12
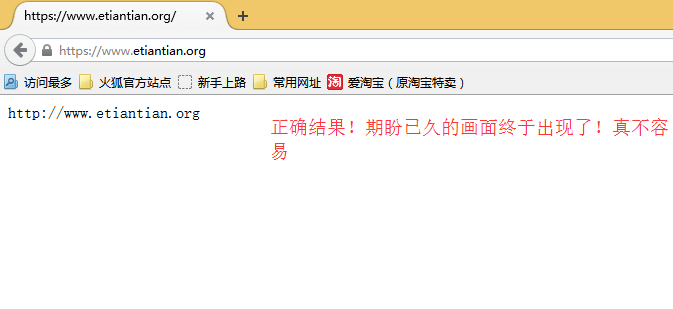
30.6.2.7 再次验证结果
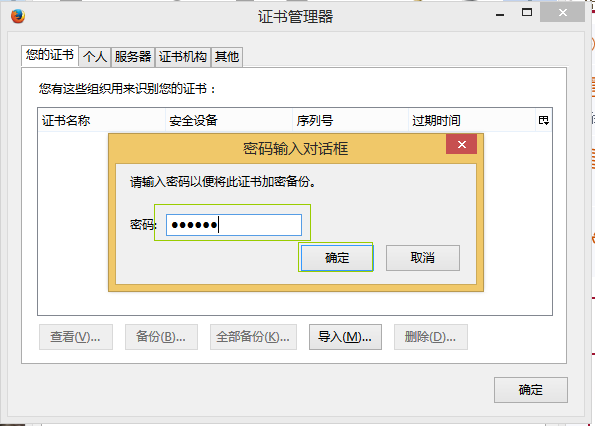
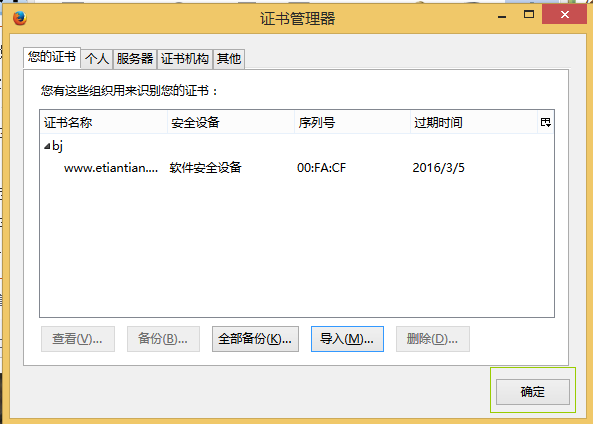
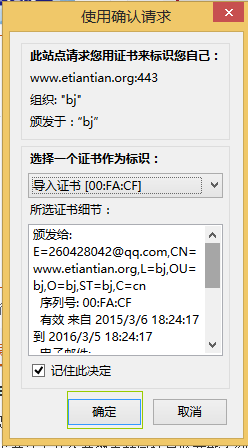
在浏览器中输入https://www.etiantian.org访问添加刚才下载下来的证书就可以正常访问了!
在这里是将你刚才从服务器上下载下来的client.p12导入就OK了!
30.6.2.8 做Nginx-SSL注意事项
1、制作证书时会提示输入密码,服务器证书和客户端证书密码可以不相同。
2、服务器证书和客户端证书制作时提示输入省份、城市、域名信息等,需保持一致。
3、Nginx默认未开启SSI,上面配置已开启。
Nginx HTTPS功能部署实践的更多相关文章
- Nginx https证书部署
1 获取证书 Nginx文件夹内获得SSL证书文件 1_www.domain.com_bundle.crt 和私钥文件 2_www.domain.com.key,1_www.domain.com_bu ...
- 应用八:Vue之在nginx下的部署实践
最近有时间研究了下前端项目如何在nginx服务器下进行部署,折腾了两天总算有所收获,汗~~ 所以就想着写篇文章来总结一下,主要包括以下三个方面: 1.打包好的vue项目如何进行部署. 2.如何反向代理 ...
- 17、Nginx HTTPS 实践
1.HTTPS安全证书基本概述 为什么需要使用HTTPS, 因为HTTP不安全.当我们使用http网站时,会遭到劫持和篡改,如果采用https协议,那么数据在传输过程中是加密的,所以黑客无法窃取或者篡 ...
- 基于 Nginx 的 HTTPS 性能优化实践
前言 分享一个卓见云的较多客户遇到HTTPS优化案例. 随着相关浏览器对HTTP协议的“不安全”.红色页面警告等严格措施的出台,以及向 iOS 应用的 ATS 要求和微信.支付宝小程序强制 HTTPS ...
- Nginx SSL TLS部署最佳实践
本文介绍nginx在提供HTTPS时使用的一些其他配置选项. 虽然这些功能有助于优化nginx的SSL和TLS,但这不是一个完整对加固nginx的介绍. 确保您的服务器安全的最佳方法是不仅需要正确的配 ...
- Nginx配置支持https协议-应用实践
Nginx配置支持https协议-应用实践 https简介 HTTPS 是运行在 TLS/SSL 之上的 HTTP,与普通的 HTTP 相比,在数据传输的安全性上有很大的提升. TLS是传输层安全协议 ...
- nginx+tomat https ssl 部署 完美解决方案
关于nginx+tomcat https的部署之前网上一直有2种说法: 1.nginx和tomcat都要部署ssl证书 2.nginx部署ssl证书,tomcat增加ssl支持 在实际的部署过程中ng ...
- Nginx 高级配置-https 功能
Nginx 高级配置-https 功能 作者:尹正杰 版权声明:原创作品,谢绝转载!否则将追究法律责任. 一.HTTPS工作过程 1>.SSL/TLS SSL(Secure Socket Lay ...
- [技术博客]ubuntu+nginx+uwsgi+Django+https的部署
ubuntu+nginx+uwsgi+Django+https部署文档 配置机器介绍 操作系统:Ubuntu 18.04.2 LTS 64位 python版本:Python 3.6.7 Django版 ...
随机推荐
- mahout 使用
最近在做mahout源码调用的时候,发现一个参数:startPhase和endPhase,这两个参数是什么意思呢?比如运行RecommenderJob时,可以看到10个MR任务,所以猜测是否是一个ph ...
- leetcode树专题894.897,919,951
满二叉树是一类二叉树,其中每个结点恰好有 0 或 2 个子结点. 返回包含 N 个结点的所有可能满二叉树的列表. 答案的每个元素都是一个可能树的根结点. 答案中每个树的每个结点都必须有 node.va ...
- 子序列个数(fzu2129)
子序列个数 Time Limit:2000MS Memory Limit:32768KB 64bit IO Format:%I64d & %I64u Submit Status ...
- php+xml有什么用
很多招聘网上找php程序员的时候都说要懂xml,这个xml+php在web网站开发方面到底有什么应用呢,希望有知道的朋友能给我具体说说,谢谢了! 我说的是在网站中的实际应用有哪些,不是网上抄的xml的 ...
- CSS计数器(序列数字字符自动递增)详解———张鑫旭
by zhangxinxu from http://www.zhangxinxu.com本文地址:http://www.zhangxinxu.com/wordpress/?p=4303 一.挖坟不可耻 ...
- vue 相对路径的图片 不显示问题
例如 data () { return { img: '../../images/jifen/index/img_list_default_pic.jpg' //路径也没问题啊,怎么不显示呢,难道他瞎 ...
- vue2.0 移动端,下拉刷新,上拉加载更多 插件
本人正在基于 vue2.0 + webpack + es6 搭建前端架构,整理了部分插件,下面这个是下拉更新 上拉更多的,挺好用的,分享给大家. 直接上代码,不懂的多看几遍,下面我换会告诉大家如何使用 ...
- linux根目录下的文件夹及文件
bin->放置执行文件的目录,但毕竟特殊,其下放置的是在单用户维护模式下还能被操作的命令.主要有cat.chmod.date. mv.mkdir.cp.bash等常用命令.dev->存放设 ...
- Selenium win7+selenium2.0+python+JetBrains PyCharm环境搭建
win7+selenium2.0+python+JetBrains PyCharm环境搭建 by:授客 QQ:1033553122 步骤1:下载python 担心最新版的支持不太好,这里我下载的是py ...
- 【three.js练习程序】随机生成100个方块
<!DOCTYPE html> <html> <head> <meta charset="utf-8"> <title> ...
