Kali linux2.0里Metasploit的服务类型探测
不多说,直接上干货!

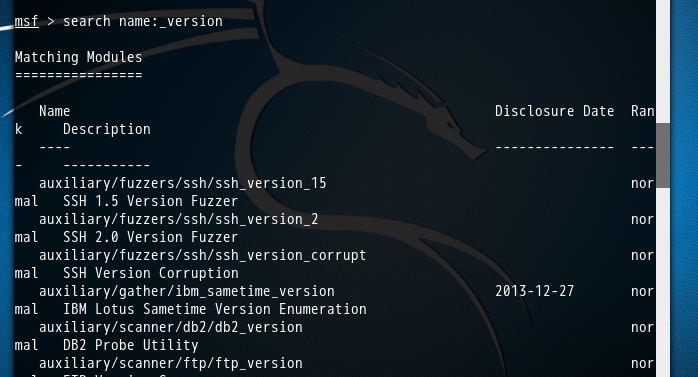
在MSF终端中,可以输入search name:_version命令查看所有可用的服务查点模块
该命令的执行结果如下:
- root@kali:~# msfconsole
- ......
msf > search name:_version
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
auxiliary/fuzzers/ssh/ssh_version_15 normal SSH 1.5 Version Fuzzer
auxiliary/fuzzers/ssh/ssh_version_2 normal SSH 2.0 Version Fuzzer
auxiliary/fuzzers/ssh/ssh_version_corrupt normal SSH Version Corruption
auxiliary/gather/ibm_sametime_version 2013-12-27 normal IBM Lotus Sametime Version Enumeration
auxiliary/scanner/db2/db2_version normal DB2 Probe Utility
auxiliary/scanner/ftp/ftp_version normal FTP Version Scanner
auxiliary/scanner/h323/h323_version normal H.323 Version Scanner
auxiliary/scanner/http/coldfusion_version normal ColdFusion Version Scanner
auxiliary/scanner/http/http_version normal HTTP Version Detection
auxiliary/scanner/http/joomla_version normal Joomla Version Scanner
auxiliary/scanner/http/sap_businessobjects_version_enum normal SAP BusinessObjects Version Detection
auxiliary/scanner/http/ssl_version 2014-10-14 normal HTTP SSL/TLS Version Detection (POODLE scanner)
auxiliary/scanner/http/svn_scanner normal HTTP Subversion Scanner
auxiliary/scanner/imap/imap_version normal IMAP4 Banner Grabber
auxiliary/scanner/ipmi/ipmi_version normal IPMI Information Discovery
auxiliary/scanner/lotus/lotus_domino_version normal Lotus Domino Version
auxiliary/scanner/mysql/mysql_version normal MySQL Server Version Enumeration
auxiliary/scanner/oracle/tnslsnr_version 2009-01-07 normal Oracle TNS Listener Service Version Query
auxiliary/scanner/pop3/pop3_version normal POP3 Banner Grabber
auxiliary/scanner/postgres/postgres_version normal PostgreSQL Version Probe
auxiliary/scanner/printer/printer_version_info normal Printer Version Information Scanner
auxiliary/scanner/sap/sap_mgmt_con_version normal SAP Management Console Version Detection
auxiliary/scanner/scada/digi_addp_version normal Digi ADDP Information Discovery
auxiliary/scanner/scada/digi_realport_version normal Digi RealPort Serial Server Version
auxiliary/scanner/scada/modbusdetect 2011-11-01 normal Modbus Version Scanner
auxiliary/scanner/smb/smb_version normal SMB Version Detection
auxiliary/scanner/smtp/smtp_version normal SMTP Banner Grabber
auxiliary/scanner/snmp/aix_version normal AIX SNMP Scanner Auxiliary Module
auxiliary/scanner/ssh/ssh_version normal SSH Version Scanner
auxiliary/scanner/telnet/lantronix_telnet_version normal Lantronix Telnet Service Banner Detection
auxiliary/scanner/telnet/telnet_version normal Telnet Service Banner Detection
auxiliary/scanner/vmware/vmauthd_version normal VMWare Authentication Daemon Version Scanner
auxiliary/scanner/vxworks/wdbrpc_version normal VxWorks WDB Agent Version Scanner
exploit/multi/svn/svnserve_date 2004-05-19 average Subversion Date Svnserve
exploit/windows/browser/crystal_reports_printcontrol 2010-12-14 normal Crystal Reports CrystalPrintControl ActiveX ServerResourceVersion Property Overflow
exploit/windows/fileformat/digital_music_pad_pls 2010-09-17 normal Digital Music Pad Version 8.2.3.3.4 Stack Buffer Overflow
exploit/windows/fileformat/orbit_download_failed_bof 2008-04-03 normal Orbit Downloader URL Unicode Conversion Overflow
exploit/windows/fileformat/realplayer_ver_attribute_bof 2013-12-20 normal RealNetworks RealPlayer Version Attribute Buffer Overflow
exploit/windows/ftp/filecopa_list_overflow 2006-07-19 average FileCopa FTP Server Pre 18 Jul Version
exploit/windows/scada/iconics_genbroker 2011-03-21 good Iconics GENESIS32 Integer Overflow Version 9.21.201.01
msf >
很多很多。
下面呢,博主我,以常见的网络服务扫描。
1、Telnet服务扫描
telnet服务的常用端口是23

服务,为下一步进行网络嗅探或口令猜测做好准备。如下所示。
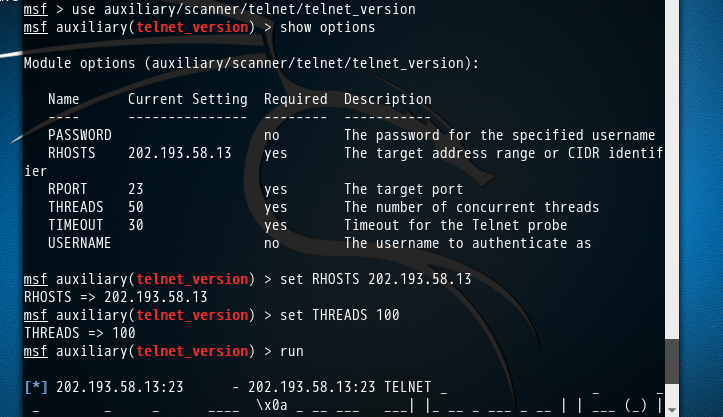
- msf > use auxiliary/scanner/telnet/telnet_version
- msf auxiliary(telnet_version) > show options
- Module options (auxiliary/scanner/telnet/telnet_version):
- Name Current Setting Required Description
- ---- --------------- -------- -----------
- PASSWORD no The password for the specified username
- RHOSTS 202.193.58.13 yes The target address range or CIDR identifier
- RPORT yes The target port
- THREADS yes The number of concurrent threads
- TIMEOUT yes Timeout for the Telnet probe
- USERNAME no The username to authenticate as
- msf auxiliary(telnet_version) > set RHOSTS 202.193.58.13
- RHOSTS => 202.193.58.13
- msf auxiliary(telnet_version) > set THREADS
- THREADS =>
- msf auxiliary(telnet_version) > run
- [*] 202.193.58.13: - 202.193.58.13: TELNET _ _ _ _ _ _ ____ \x0a _ __ ___ ___| |_ __ _ ___ _ __ | | ___ (_) |_ __ _| |__ | | ___|___ \ \x0a| '_ ` _ \ / _ \ __/ _` / __| '_ \| |/ _ \| | __/ _` | '_ \| |/ _ \ __) |\x0a| | | | | | __/ || (_| \__ \ |_) | | (_) | | || (_| | |_) | | __// __/ \x0a|_| |_| |_|\___|\__\__,_|___/ .__/|_|\___/|_|\__\__,_|_.__/|_|\___|_____|\x0a |_| \x0a\x0a\x0aWarning: Never expose this VM to an untrusted network!\x0a\x0aContact: msfdev[at]metasploit.com\x0a\x0aLogin with msfadmin/msfadmin to get started\x0a\x0a\x0ametasploitable login:
- [*] Scanned of hosts (% complete)
- [*] Auxiliary module execution completed
- msf auxiliary(telnet_version) >
或者
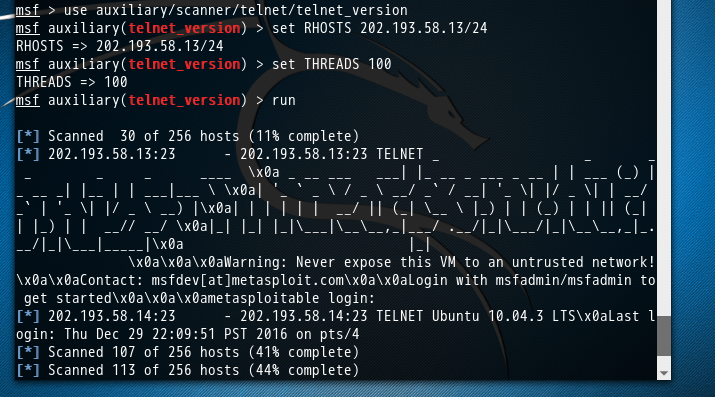
- msf > use auxiliary/scanner/telnet/telnet_version
- msf auxiliary(telnet_version) > set RHOSTS 202.193.58.13/
- RHOSTS => 202.193.58.13/
- msf auxiliary(telnet_version) > set THREADS
- THREADS =>
- msf auxiliary(telnet_version) > run
- [*] Scanned of hosts (% complete)
- [*] 202.193.58.13: - 202.193.58.13: TELNET _ _ _ _ _ _ ____ \x0a _ __ ___ ___| |_ __ _ ___ _ __ | | ___ (_) |_ __ _| |__ | | ___|___ \ \x0a| '_ ` _ \ / _ \ __/ _` / __| '_ \| |/ _ \| | __/ _` | '_ \| |/ _ \ __) |\x0a| | | | | | __/ || (_| \__ \ |_) | | (_) | | || (_| | |_) | | __// __/ \x0a|_| |_| |_|\___|\__\__,_|___/ .__/|_|\___/|_|\__\__,_|_.__/|_|\___|_____|\x0a |_| \x0a\x0a\x0aWarning: Never expose this VM to an untrusted network!\x0a\x0aContact: msfdev[at]metasploit.com\x0a\x0aLogin with msfadmin/msfadmin to get started\x0a\x0a\x0ametasploitable login:
- [*] 202.193.58.14: - 202.193.58.14: TELNET Ubuntu 10.04. LTS\x0aLast login: Thu Dec :: PST on pts/
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Auxiliary module execution completed
- msf auxiliary(telnet_version) >
当然,大家可以拿这个主机扫描
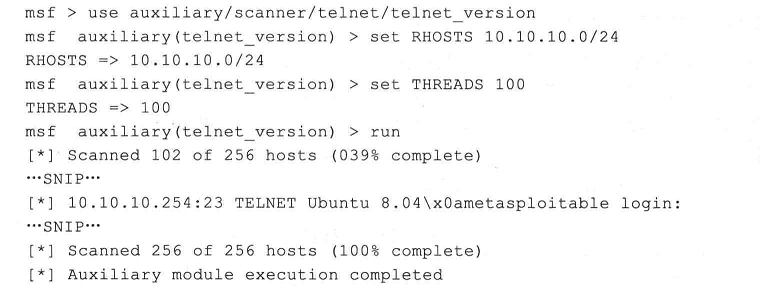

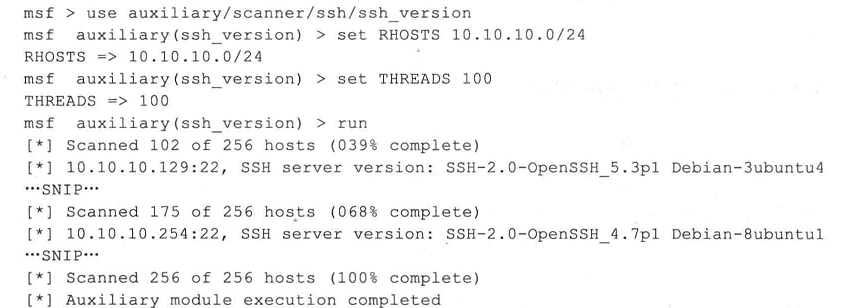
2、ssh服务扫描
ssh服务常用端口为22


了相应登录用户的所有权限。对网络中开放了SSH服务的主机进行了扫描。

- msf > use auxiliary/scanner/ssh/ssh_version
- msf auxiliary(ssh_version) > set RHOSTS 202.193.58.13/
- RHOSTS => 202.193.58.13/
- msf auxiliary(ssh_version) > set THREADS
- THREADS =>
- msf auxiliary(ssh_version) > run
- [*] 202.193.58.9: - SSH server version: SSH-2.0-OpenSSH_5.3p1 Debian-3ubuntu4 ( service.version=.3p1 openssh.comment=Debian-3ubuntu4 service.vendor=OpenBSD service.family=OpenSSH service.product=OpenSSH os.vendor=Ubuntu os.device=General os.family=Linux os.product=Linux os.version=10.04 )
- [*] 202.193.58.14: - SSH server version: SSH-2.0-OpenSSH_5.3p1 Debian-3ubuntu7 ( service.version=.3p1 openssh.comment=Debian-3ubuntu7 service.vendor=OpenBSD service.family=OpenSSH service.product=OpenSSH os.vendor=Ubuntu os.device=General os.family=Linux os.product=Linux os.version=10.04 )
- [*] 202.193.58.33: - SSH server version: SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2. ( service.version=.2p2 openssh.comment=Ubuntu-4ubuntu2. service.vendor=OpenBSD service.family=OpenSSH service.product=OpenSSH os.vendor=Ubuntu os.device=General os.family=Linux os.product=Linux os.certainty=0.75 )
- [*] 202.193.58.55: - SSH server version: SSH-2.0-OpenSSH_7.2p2 Ubuntu-
- [*] 202.193.58.11: - SSH server version: SSH-2.0-OpenSSH_5.3p1 Debian-3ubuntu4 ( service.version=.3p1 openssh.comment=Debian-3ubuntu4 service.vendor=OpenBSD service.family=OpenSSH service.product=OpenSSH os.vendor=Ubuntu os.device=General os.family=Linux os.product=Linux os.version=10.04 )
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Auxiliary module execution completed
- msf auxiliary(ssh_version) >
当然,大家可以拿这个来扫描

- msf > search name:_login
- Matching Modules
- ================
- Name Disclosure Date Rank Description
- ---- --------------- ---- -----------
- auxiliary/admin/mssql/mssql_enum_sql_logins normal Microsoft SQL Server SUSER_SNAME SQL Logins Enumeration
- auxiliary/admin/oracle/oracle_login -- normal Oracle Account Discovery
- auxiliary/admin/vmware/terminate_esx_sessions normal VMWare Terminate ESX Login Sessions
- auxiliary/fuzzers/smb/smb_ntlm1_login_corrupt normal SMB NTLMv1 Login Request Corruption
- auxiliary/fuzzers/tds/tds_login_corrupt normal TDS Protocol Login Request Corruption Fuzzer
- auxiliary/fuzzers/tds/tds_login_username normal TDS Protocol Login Request Username Fuzzer
- auxiliary/scanner/acpp/login normal Apple Airport ACPP Authentication Scanner
- auxiliary/scanner/afp/afp_login normal Apple Filing Protocol Login Utility
- auxiliary/scanner/couchdb/couchdb_login normal CouchDB Login Utility
- auxiliary/scanner/ftp/ftp_login normal FTP Authentication Scanner
- auxiliary/scanner/http/appletv_login normal AppleTV AirPlay Login Utility
- auxiliary/scanner/http/axis_login normal Apache Axis2 Brute Force Utility
- auxiliary/scanner/http/buffalo_login normal Buffalo NAS Login Utility
- auxiliary/scanner/http/caidao_bruteforce_login normal Chinese Caidao Backdoor Bruteforce
- auxiliary/scanner/http/chef_webui_login normal Chef Web UI Brute Force Utility
- auxiliary/scanner/http/cisco_asa_asdm normal Cisco ASA ASDM Bruteforce Login Utility
- auxiliary/scanner/http/cisco_ironport_enum normal Cisco Ironport Bruteforce Login Utility
- auxiliary/scanner/http/cisco_ssl_vpn normal Cisco SSL VPN Bruteforce Login Utility
- auxiliary/scanner/http/dell_idrac normal Dell iDRAC Default Login
- auxiliary/scanner/http/dlink_dir_300_615_http_login normal D-Link DIR-300A / DIR- / DIR-615D HTTP Login Utility
- auxiliary/scanner/http/dlink_dir_615h_http_login normal D-Link DIR-615H HTTP Login Utility
- auxiliary/scanner/http/dlink_dir_session_cgi_http_login normal D-Link DIR-300B / DIR-600B / DIR- / DIR- HTTP Login Utility
- auxiliary/scanner/http/dolibarr_login normal Dolibarr ERP/CRM Login Utility
- auxiliary/scanner/http/etherpad_duo_login normal EtherPAD Duo Login Bruteforce Utility
- auxiliary/scanner/http/frontpage_login normal FrontPage Server Extensions Anonymous Login Scanner
- auxiliary/scanner/http/gitlab_login normal GitLab Login Utility
- auxiliary/scanner/http/glassfish_login normal GlassFish Brute Force Utility
- auxiliary/scanner/http/hp_sys_mgmt_login normal HP System Management Homepage Login Utility
- auxiliary/scanner/http/http_login normal HTTP Login Utility
- auxiliary/scanner/http/infovista_enum normal InfoVista VistaPortal Application Bruteforce Login Utility
- auxiliary/scanner/http/ipboard_login normal IP Board Login Auxiliary Module
- auxiliary/scanner/http/jenkins_login normal Jenkins-CI Login Utility
- auxiliary/scanner/http/joomla_bruteforce_login normal Joomla Bruteforce Login Utility
- auxiliary/scanner/http/manageengine_desktop_central_login normal ManageEngine Desktop Central Login Utility
- auxiliary/scanner/http/mybook_live_login normal Western Digital MyBook Live Login Utility
- auxiliary/scanner/http/octopusdeploy_login normal Octopus Deploy Login Utility
- auxiliary/scanner/http/openmind_messageos_login normal OpenMind Message-OS Portal Login Brute Force Utility
- auxiliary/scanner/http/oracle_ilom_login normal Oracle ILO Manager Login Brute Force Utility
- auxiliary/scanner/http/owa_ews_login normal OWA Exchange Web Services (EWS) Login Scanner
- auxiliary/scanner/http/owa_login normal Outlook Web App (OWA) Brute Force Utility
- auxiliary/scanner/http/pocketpad_login normal PocketPAD Login Bruteforce Force Utility
- auxiliary/scanner/http/radware_appdirector_enum normal Radware AppDirector Bruteforce Login Utility
- auxiliary/scanner/http/rfcode_reader_enum normal RFCode Reader Web Interface Login / Bruteforce Utility
- auxiliary/scanner/http/sentry_cdu_enum normal Sentry Switched CDU Bruteforce Login Utility
- auxiliary/scanner/http/sevone_enum -- normal SevOne Network Performance Management Application Brute Force Login Utility
- auxiliary/scanner/http/splunk_web_login normal Splunk Web Interface Login Utility
- auxiliary/scanner/http/symantec_web_gateway_login normal Symantec Web Gateway Login Utility
- auxiliary/scanner/http/tomcat_mgr_login normal Tomcat Application Manager Login Utility
- auxiliary/scanner/http/typo3_bruteforce normal Typo3 Login Bruteforcer
- auxiliary/scanner/http/vcms_login normal V-CMS Login Utility
- auxiliary/scanner/http/wordpress_login_enum normal WordPress Brute Force and User Enumeration Utility
- auxiliary/scanner/http/wordpress_xmlrpc_login normal Wordpress XML-RPC Username/Password Login Scanner
- auxiliary/scanner/http/zabbix_login normal Zabbix Server Brute Force Utility
- auxiliary/scanner/lotus/lotus_domino_login normal Lotus Domino Brute Force Utility
- auxiliary/scanner/misc/cctv_dvr_login normal CCTV DVR Login Scanning Utility
- auxiliary/scanner/misc/oki_scanner normal OKI Printer Default Login Credential Scanner
- auxiliary/scanner/mongodb/mongodb_login normal MongoDB Login Utility
- auxiliary/scanner/msf/msf_rpc_login normal Metasploit RPC Interface Login Utility
- auxiliary/scanner/msf/msf_web_login normal Metasploit Web Interface Login Utility
- auxiliary/scanner/mssql/mssql_login normal MSSQL Login Utility
- auxiliary/scanner/mysql/mysql_login normal MySQL Login Utility
- auxiliary/scanner/nessus/nessus_ntp_login normal Nessus NTP Login Utility
- auxiliary/scanner/nessus/nessus_rest_login normal Nessus RPC Interface Login Utility
- auxiliary/scanner/nessus/nessus_xmlrpc_login normal Nessus XMLRPC Interface Login Utility
- auxiliary/scanner/nexpose/nexpose_api_login normal NeXpose API Interface Login Utility
- auxiliary/scanner/openvas/openvas_gsad_login normal OpenVAS gsad Web Interface Login Utility
- auxiliary/scanner/openvas/openvas_omp_login normal OpenVAS OMP Login Utility
- auxiliary/scanner/openvas/openvas_otp_login normal OpenVAS OTP Login Utility
- auxiliary/scanner/oracle/isqlplus_login normal Oracle iSQL*Plus Login Utility
- auxiliary/scanner/oracle/oracle_login normal Oracle RDBMS Login Utility
- auxiliary/scanner/pcanywhere/pcanywhere_login normal PcAnywhere Login Scanner
- auxiliary/scanner/pop3/pop3_login normal POP3 Login Utility
- auxiliary/scanner/postgres/postgres_login normal PostgreSQL Login Utility
- auxiliary/scanner/redis/redis_login normal Redis Login Utility
- auxiliary/scanner/rservices/rexec_login normal rexec Authentication Scanner
- auxiliary/scanner/rservices/rlogin_login normal rlogin Authentication Scanner
- auxiliary/scanner/rservices/rsh_login normal rsh Authentication Scanner
- auxiliary/scanner/sap/sap_mgmt_con_brute_login normal SAP Management Console Brute Force
- auxiliary/scanner/sap/sap_soap_rfc_brute_login normal SAP SOAP Service RFC_PING Login Brute Forcer
- auxiliary/scanner/sap/sap_web_gui_brute_login normal SAP Web GUI Login Brute Forcer
- auxiliary/scanner/scada/koyo_login -- normal Koyo DirectLogic PLC Password Brute Force Utility
- auxiliary/scanner/smb/smb_login normal SMB Login Check Scanner
- auxiliary/scanner/snmp/snmp_login normal SNMP Community Login Scanner
- auxiliary/scanner/ssh/karaf_login normal Apache Karaf Login Utility
- auxiliary/scanner/ssh/ssh_login normal SSH Login Check Scanner
- auxiliary/scanner/ssh/ssh_login_pubkey normal SSH Public Key Login Scanner
- auxiliary/scanner/telnet/brocade_enable_login normal Brocade Enable Login Check Scanner
- auxiliary/scanner/telnet/telnet_login normal Telnet Login Check Scanner
- auxiliary/scanner/vmware/vmauthd_login normal VMWare Authentication Daemon Login Scanner
- auxiliary/scanner/vmware/vmware_http_login normal VMWare Web Login Scanner
- auxiliary/scanner/vnc/vnc_login normal VNC Authentication Scanner
- auxiliary/scanner/winrm/winrm_login normal WinRM Login Utility
- auxiliary/voip/asterisk_login normal Asterisk Manager Login Utility
- exploit/dialup/multi/login/manyargs -- good System V Derived /bin/login Extraneous Arguments Buffer Overflow
- exploit/linux/http/airties_login_cgi_bof -- normal Airties login-cgi Buffer Overflow
- exploit/linux/http/belkin_login_bof -- normal Belkin Play N750 login.cgi Buffer Overflow
- exploit/linux/misc/hp_vsa_login_bof -- normal HP StorageWorks P4000 Virtual SAN Appliance Login Buffer Overflow
- exploit/multi/http/coldfusion_rds -- great Adobe ColdFusion Administrative Login Bypass
- exploit/osx/afp/loginext -- average AppleFileServer LoginExt PathName Overflow
- exploit/windows/brightstor/lgserver_rxrlogin -- average CA BrightStor ARCserve for Laptops and Desktops LGServer Buffer Overflow
- exploit/windows/http/hp_power_manager_login -- average Hewlett-Packard Power Manager Administration Buffer Overflow
- exploit/windows/http/integard_password_bof -- great Race River Integard Home/Pro LoginAdmin Password Stack Buffer Overflow
- exploit/windows/http/solarwinds_fsm_userlogin -- excellent Solarwinds Firewall Security Manager 6.6. Client Session Handling Vulnerability
- exploit/windows/imap/mailenable_login -- great MailEnable IMAPD (2.34/2.35) Login Request Buffer Overflow
- exploit/windows/imap/mercur_login -- average Mercur Messaging IMAP Login Buffer Overflow
- exploit/windows/imap/mercury_login -- average Mercury/ LOGIN Buffer Overflow
- exploit/windows/misc/hp_dataprotector_dtbclslogin -- normal HP Data Protector DtbClsLogin Buffer Overflow
- exploit/windows/scada/realwin_on_fcs_login -- great RealWin SCADA Server DATAC Login Buffer Overflow
- post/osx/gather/autologin_password normal OSX Gather Autologin Password as Root
- post/windows/gather/credentials/windows_autologin normal Windows Gather AutoLogin User Credential Extractor
- msf >
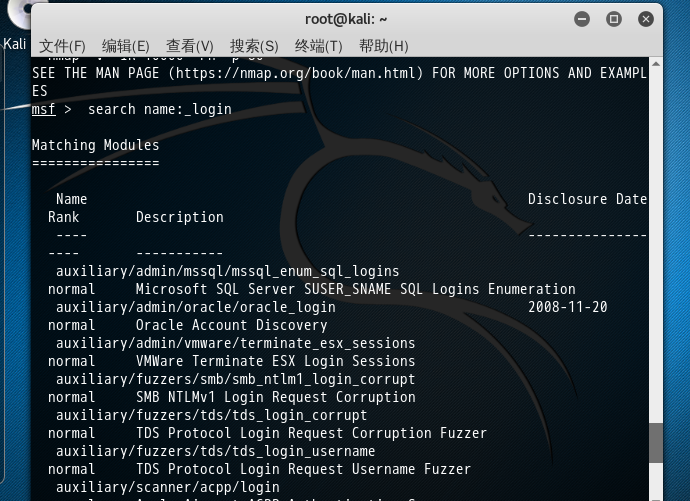
同时,还可以利用ssh_login模块进行SSH服务口令破解。
通过暴力破解知道密码为ubuntu,
可以看到通过口令破解已经获得了一个10.10.10.254机器的shell
可以对该机器再进一步提权获得更多信息
当然,使用的字典还是非常重要的,还需要使用社会工程学加以完善
3、Orcal数据库服务查点
oracle数据库监听器tnslsnr默认端口为1521

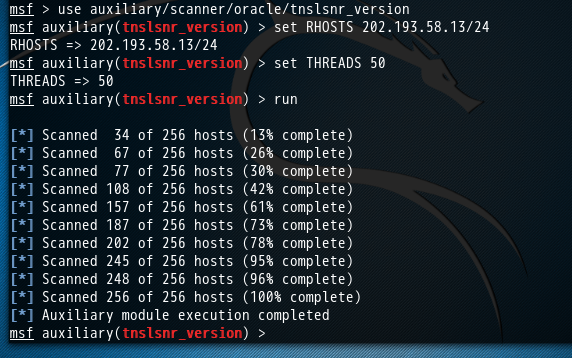
- msf > use auxiliary/scanner/oracle/tnslsnr_version
- msf auxiliary(tnslsnr_version) > set RHOSTS 202.193.58.13/
- RHOSTS => 202.193.58.13/
- msf auxiliary(tnslsnr_version) > set THREADS
- THREADS =>
- msf auxiliary(tnslsnr_version) > run
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Scanned of hosts (% complete)
- [*] Auxiliary module execution completed
- msf auxiliary(tnslsnr_version) >
当然,大家也可以拿下面的主机来,

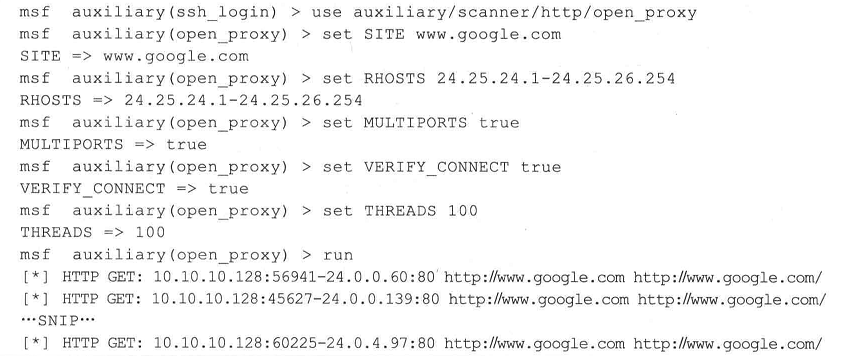
4、代理服务器探测
当如果靶机开启了代理服务器来隐藏自己身份的时候,我们使用auxiliary/scanner/http/open_proxy,可以探测到代理服务器的使用

Kali linux2.0里Metasploit的服务类型探测的更多相关文章
- Kali linux2.0里Metasploit的postgresql selected, no connection问题解决
说在前面的话 1.在kali中metasploit默认使用postgresql作为它的数据库: 想要开启metasploit服务首先得打开postgresql数据库, 命令如下:(或者:/etc/in ...
- kali 2.0 启动metasploit服务
kali 2.0 已经没有metasploit 这个服务了,所以service metasploit start 的方式不起作用. 在kali 2.0中启动带数据库支持的MSF方式如下: 首先启动po ...
- Kali 2.0 下 Metasploit 初始化配置
在kali 2.0中,命令行中直接输入msfconsole 提示不能连接到数据库 ,是由于postgresql 未启动.因此,需要开启postgresql,并且进行postgresql 的初始化配置. ...
- 给kali linux2.0装一个中文输入法
没有中文输入法好痛苦啊.. 毕竟做了无限网卡,虚拟机和主机可以完完全全当两台设备使用了,所以kali还是需要一个中文输入法才方便. 由于使用的是比较新的kali版本和源,现在安装fcitx已经可以直接 ...
- 折腾kali linux2.0
偶然的机会了解到了kali linux这个用于渗透测试的linux发行版,于是就从官网下了iso,但是制作启动盘老出错.网上查了下说在linux下用dd命令特别简单,于是转到ubuntu下制作启动盘, ...
- kali linux2.0安装vega
1.到官网下载安装包(选择版本:我这里以Linux64位为例) vega下载地址:https://subgraph.com/vega/download/ 2.解压到指定目录: unzip VegaBu ...
- Kali linux 2016.2(Rolling)里Metasploit的数据库
为什么要在Metasploit里提及到数据库? 大家都知道,这么多信息,我怎样才能把它们整理好并保存起来?怎么展现给老大看,最后怎么体现在要提交的渗透测试报告中呢? 你的担忧真的很有必要,因为啊, ...
- Kali linux 2016.2(Rolling)里Metasploit的OpenVAS
不多说,直接上干货! 关于OpenAVS的概念,我这里不多赘述. 前提得,大家要先安装好OpenVAS!!! 我们都知道,BT5中已经预先安装好了OpenVAS网络漏洞扫描工具,我们只需进行一些配置即 ...
- Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库之后的切换到指定的工作空间
不多说,直接上干货! 为什么要这么做? 答: 方便我们将扫描不同的目标或目标的不同段,进行归类.为了更好的后续工作! 前期博客 Kali linux 2016.2(Rolling)里Metasploi ...
随机推荐
- mydumper安装及安装故障汇总
mydumper是针对mysql数据库备份的一个轻量级第三方的开源工具,备份方式术语逻辑备份.它支持多线程.备份速度远高于原生态的mysqldump以及众多优异特性. 因此该工具是DBA们的不二选 ...
- Codeforces 676E The Last Fight Between Human and AI 规律
链接 Codeforces 676E The Last Fight Between Human and AI 题意 给一个多项式,有些系数不确定.人和机器轮流填系数,系数可以是任何数,问是否能使得最后 ...
- quartz.net定时任务框架详解
C#做定时任务:一是Timer:而是Quartz.net:本文就学习一下Quartz.net框架 Quartz.net非常的灵活,开发人员能用很少的代码就能完成“每隔一小时执行”.“每天2点执行”.“ ...
- js小结2
1.includes和contains 对于字符串,数组来说,判断包含是includes,对classList是contains 2.编辑span内容,enter提交(如何避免keydown之后换行: ...
- Sublime使用随记
1.安装 Package Control Ctrl+` 打开命令行,执行如下代码: 适用于 Sublime Text 3: import urllib.request,os;pf='Package C ...
- RocketMQ学习笔记(2)----Broker的集群四种方式
RocketMQ推荐了几种Broker集群方式,这里的Slave不可写,但可读,类似于Mysql主备方式 1. 单个Master 这是一种风险比较大的集群方式,因为一旦Borker重启或宕机期间,将会 ...
- js 将数组中的每一项安装奇偶重新组合成一个数组对象
<!DOCTYPE html> <html> <head> <meta charset="UTF-8"> <title> ...
- 解决PNG图片在IE6中背景不透明方法_解决IE6中PNG背
解决PNG图片在IE6中背景不透明方法_解决IE6中PNG背 目录 解决代码 解决png图片在html中 解决png作为网页背景-css 1.解决PNG图片在IE6中背景不透明的CSS与JS代码 ...
- obaa源码加注
这个是dntzhang写的用于监听变量更改的库obaa,加上一点注释方便理解~ 传送门 /* obaa 1.0.0 * By dntzhang * Github: https://github.com ...
- [SCOI2012]喵星球上的点名(树状数组+后缀数组)
我们把所有的名,姓,询问都拼起来构成一个新的长串,然后跑一边SA.排完序后对于每一个询问,我们可以二分求出它所对应的区间(即满足这个区间的前缀都是这个询问串).然后问题就转化为很多区间问区间出现过的不 ...



