CAS 5.x搭建常见问题系列(2).PKIX path building failed
错误原因
服务端的证书是不安全的,Cas的客户端在调用时因为安全提醒造成调用失败。
CAS的客户端需要导入服务端的证书后,就正常了。
具体操作步骤如下:
1. 首先启动tomcat,看下之前搭建的cas server启动是否正常
双击D:\casoverlay\apache-tomcat-8.5.31\bin\startup.bat
访问 https://cas.example.org:8443/cas/login
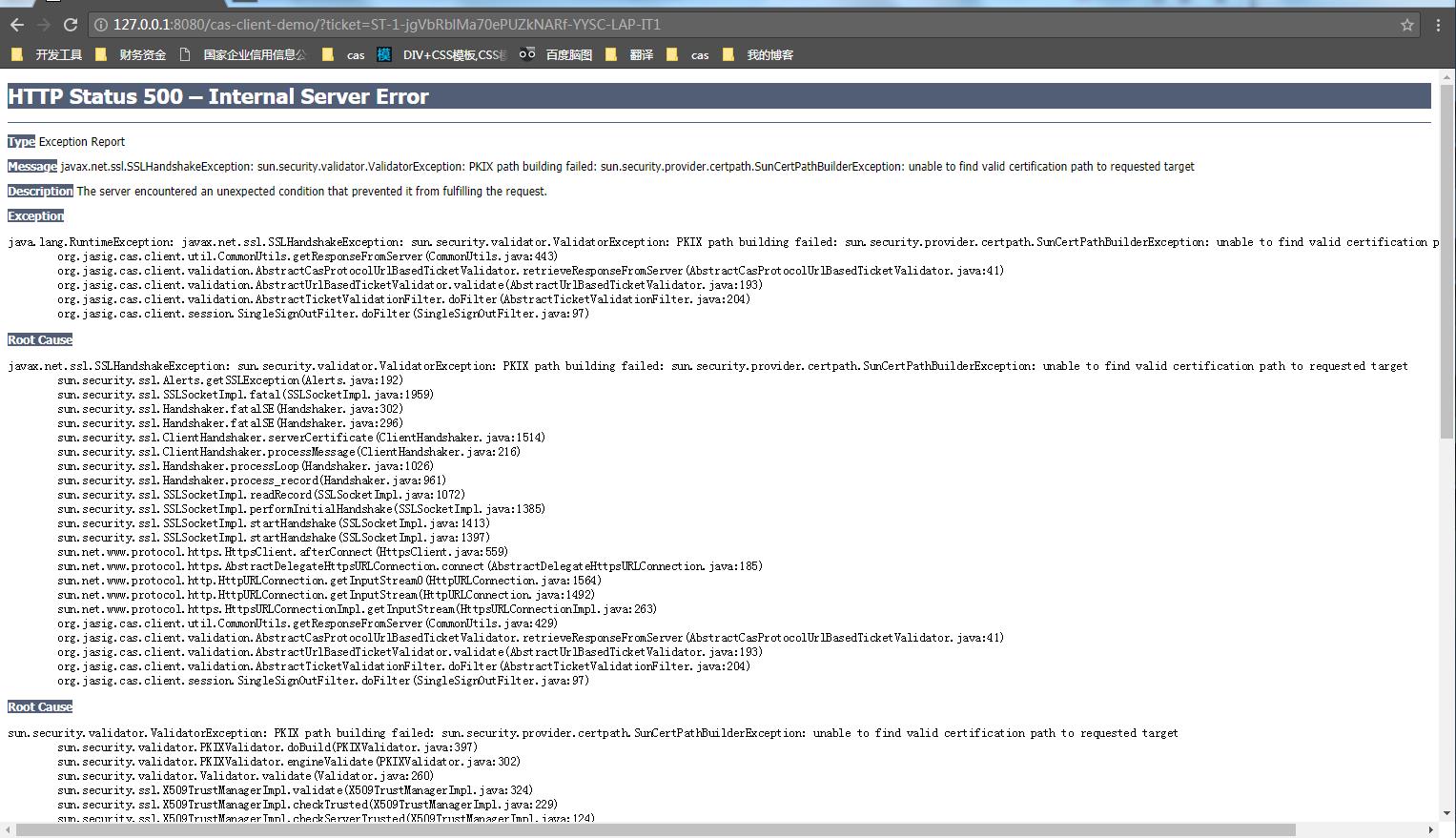
如对对cas的搭建有疑问,可看文章《轻松搭建CAS 5.x系列文章》
·2. 创建生成证书的目录
cd D:\casoverlay
mkdir cert
-3. 创建文件InstallCert.java
具体内容如下:
import java.io.*;
import java.net.URL; import java.security.*;
import java.security.cert.*; import javax.net.ssl.*; public class InstallCert { public static void main(String[] args) throws Exception {
String host;
int port;
char[] passphrase;
if ((args.length == 1) || (args.length == 2)) {
String[] c = args[0].split(":");
host = c[0];
port = (c.length == 1) ? 443 : Integer.parseInt(c[1]);
String p = (args.length == 1) ? "changeit" : args[1];
passphrase = p.toCharArray();
} else {
System.out.println("Usage: java InstallCert <host>[:port] [passphrase]");
return;
} File file = new File("jssecacerts");
if (file.isFile() == false) {
char SEP = File.separatorChar;
File dir = new File(System.getProperty("java.home") + SEP
+ "lib" + SEP + "security");
file = new File(dir, "jssecacerts");
if (file.isFile() == false) {
file = new File(dir, "cacerts");
}
}
System.out.println("Loading KeyStore " + file + "...");
InputStream in = new FileInputStream(file);
KeyStore ks = KeyStore.getInstance(KeyStore.getDefaultType());
ks.load(in, passphrase);
in.close(); SSLContext context = SSLContext.getInstance("TLS");
TrustManagerFactory tmf =
TrustManagerFactory.getInstance(TrustManagerFactory.getDefaultAlgorithm());
tmf.init(ks);
X509TrustManager defaultTrustManager = (X509TrustManager)tmf.getTrustManagers()[0];
SavingTrustManager tm = new SavingTrustManager(defaultTrustManager);
context.init(null, new TrustManager[] {tm}, null);
SSLSocketFactory factory = context.getSocketFactory(); System.out.println("Opening connection to " + host + ":" + port + "...");
SSLSocket socket = (SSLSocket)factory.createSocket(host, port);
socket.setSoTimeout(10000);
try {
System.out.println("Starting SSL handshake...");
socket.startHandshake();
socket.close();
System.out.println();
System.out.println("No errors, certificate is already trusted");
} catch (SSLException e) {
System.out.println();
e.printStackTrace(System.out);
} X509Certificate[] chain = tm.chain;
if (chain == null) {
System.out.println("Could not obtain server certificate chain");
return;
} BufferedReader reader =
new BufferedReader(new InputStreamReader(System.in)); System.out.println();
System.out.println("Server sent " + chain.length + " certificate(s):");
System.out.println();
MessageDigest sha1 = MessageDigest.getInstance("SHA1");
MessageDigest md5 = MessageDigest.getInstance("MD5");
for (int i = 0; i < chain.length; i++) {
X509Certificate cert = chain[i];
System.out.println
(" " + (i + 1) + " Subject " + cert.getSubjectDN());
System.out.println(" Issuer " + cert.getIssuerDN());
sha1.update(cert.getEncoded());
System.out.println(" sha1 " + toHexString(sha1.digest()));
md5.update(cert.getEncoded());
System.out.println(" md5 " + toHexString(md5.digest()));
System.out.println();
} System.out.println("Enter certificate to add to trusted keystore or 'q' to quit: [1]");
String line = reader.readLine().trim();
int k;
try {
k = (line.length() == 0) ? 0 : Integer.parseInt(line) - 1;
} catch (NumberFormatException e) {
System.out.println("KeyStore not changed");
return;
} X509Certificate cert = chain[k];
String alias = host + "-" + (k + 1);
ks.setCertificateEntry(alias, cert); OutputStream out = new FileOutputStream("jssecacerts");
ks.store(out, passphrase);
out.close(); System.out.println();
System.out.println(cert);
System.out.println();
System.out.println
("Added certificate to keystore 'jssecacerts' using alias '"
+ alias + "'");
} private static final char[] HEXDIGITS = "0123456789abcdef".toCharArray(); private static String toHexString(byte[] bytes) {
StringBuilder sb = new StringBuilder(bytes.length * 3);
for (int b : bytes) {
b &= 0xff;
sb.append(HEXDIGITS[b >> 4]);
sb.append(HEXDIGITS[b & 15]);
sb.append(' ');
}
return sb.toString();
} private static class SavingTrustManager implements X509TrustManager { private final X509TrustManager tm;
private X509Certificate[] chain; SavingTrustManager(X509TrustManager tm) {
this.tm = tm;
} public X509Certificate[] getAcceptedIssuers() {
//throw new UnsupportedOperationException();
return new X509Certificate[0];
} public void checkClientTrusted(X509Certificate[] chain, String authType)
throws CertificateException {
throw new UnsupportedOperationException();
} public void checkServerTrusted(X509Certificate[] chain, String authType)
throws CertificateException {
this.chain = chain;
tm.checkServerTrusted(chain, authType);
}
} }
-4. 编辑InstallCert.java
cd D:\casoverlay\cert
javac InstallCert.java
此时目录会生成对应的class文件
-5. 生成客户端证书
cd D:\casoverlay\cert
java InstallCert cas.example.org:8443
填写您的域名和端口,运行InstallCert。
运行过程中,出现了错误提示后,根据提示输入1,命令就自动生成了证书
D:\casoverlay\cert>java InstallCert cas.example.org:8443
Loading KeyStore C:\Program Files\Java\jre1.8.0_151\lib\security\cacerts...
Opening connection to cas.example.org:8443...
Starting SSL handshake... javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.
provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
at sun.security.ssl.Alerts.getSSLException(Unknown Source)
at sun.security.ssl.SSLSocketImpl.fatal(Unknown Source)
at sun.security.ssl.Handshaker.fatalSE(Unknown Source)
at sun.security.ssl.Handshaker.fatalSE(Unknown Source)
at sun.security.ssl.ClientHandshaker.serverCertificate(Unknown Source)
at sun.security.ssl.ClientHandshaker.processMessage(Unknown Source)
at sun.security.ssl.Handshaker.processLoop(Unknown Source)
at sun.security.ssl.Handshaker.process_record(Unknown Source)
at sun.security.ssl.SSLSocketImpl.readRecord(Unknown Source)
at sun.security.ssl.SSLSocketImpl.performInitialHandshake(Unknown Source)
at sun.security.ssl.SSLSocketImpl.startHandshake(Unknown Source)
at sun.security.ssl.SSLSocketImpl.startHandshake(Unknown Source)
at InstallCert.main(InstallCert.java:87)
Caused by: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertP
athBuilderException: unable to find valid certification path to requested target
at sun.security.validator.PKIXValidator.doBuild(Unknown Source)
at sun.security.validator.PKIXValidator.engineValidate(Unknown Source)
at sun.security.validator.Validator.validate(Unknown Source)
at sun.security.ssl.X509TrustManagerImpl.validate(Unknown Source)
at sun.security.ssl.X509TrustManagerImpl.checkTrusted(Unknown Source)
at sun.security.ssl.X509TrustManagerImpl.checkServerTrusted(Unknown Source)
at InstallCert$SavingTrustManager.checkServerTrusted(InstallCert.java:183)
at sun.security.ssl.AbstractTrustManagerWrapper.checkServerTrusted(Unknown Source)
... 9 more
Caused by: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to reques
ted target
at sun.security.provider.certpath.SunCertPathBuilder.build(Unknown Source)
at sun.security.provider.certpath.SunCertPathBuilder.engineBuild(Unknown Source)
at java.security.cert.CertPathBuilder.build(Unknown Source)
... 17 more Server sent 1 certificate(s): 1 Subject CN=cas.example.org, OU=casexampleorg, O=casexampleorg, L=casexampleorg, ST=casexampleorg, C=CN
Issuer CN=cas.example.org, OU=casexampleorg, O=casexampleorg, L=casexampleorg, ST=casexampleorg, C=CN
sha1 6e 6f 9e 68 9b 17 00 cb 24 00 c6 dd 5b 3e 98 1c dd 93 3b 58
md5 34 06 43 82 a3 89 30 73 77 37 e2 8b 22 2a a0 8a Enter certificate to add to trusted keystore or 'q' to quit: [1]
1 [
[
Version: V3
Subject: CN=cas.example.org, OU=casexampleorg, O=casexampleorg, L=casexampleorg, ST=casexampleorg, C=CN
Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11 Key: Sun RSA public key, 2048 bits
modulus: 1690620466251730075410187335527176539575574279164656191301268616376011867351755314109432788128763792853957685
509850737657313044903867516296492688699327787967525657153944349196906172329911432006555223477421064086655769564280443085
752416260227648518507908266556286126488172636414552577201541577021778173696705348205206800885112095634757232838095194599
467840130327744042458608666642772670848884551427300132389186144347259187506374891023727125201882125947109668529124319064
780959421387991371315373185390093486540418719240509126192650469625947655340408578607406180180595247169589979804514097709
6461946148979540598598705209
public exponent: 65537
Validity: [From: Fri Jun 29 23:49:33 CST 2018,
To: Thu Sep 27 23:49:33 CST 2018]
Issuer: CN=cas.example.org, OU=casexampleorg, O=casexampleorg, L=casexampleorg, ST=casexampleorg, C=CN
SerialNumber: [ 56261ad8] Certificate Extensions: 1
[1]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 45 84 BF 42 27 F5 B1 33 36 F4 6B CC 15 82 5D B0 E..B'..36.k...].
0010: AC AD 2A 9B ..*.
]
] ]
Algorithm: [SHA256withRSA]
Signature:
0000: 0B C8 FA 28 E6 86 AC DE FA 99 5C BE 96 B2 E3 00 ...(......\.....
0010: 2A 40 92 9C FF 44 D8 35 EF 3C 7C C2 DF 7A FB 9F *@...D.5.<...z..
0020: 23 E0 AC 2B 8D 2A AD 18 60 FC B4 33 E1 06 54 DB #..+.*..`..3..T.
0030: 51 C8 94 4D 61 1C 97 3D 63 07 13 C7 90 B3 26 D6 Q..Ma..=c.....&.
0040: 68 EB 87 D7 04 FA 36 14 FE 70 42 C9 25 90 CB 09 h.....6..pB.%...
0050: 07 4B 96 79 2D 29 F1 D5 29 57 90 71 32 09 AE A6 .K.y-)..)W.q2...
0060: 51 4F D9 79 09 D1 0D 84 F5 D4 C3 AE 71 A2 D3 28 QO.y........q..(
0070: B9 09 0C 21 DB 1E 37 33 3B CF 4A 0B 52 89 4A 4D ...!..73;.J.R.JM
0080: 9D E4 40 8C 09 FA 93 77 5C 53 A5 D0 E0 DD C0 4F ..@....w\S.....O
0090: 9B 30 0F C3 72 69 72 3D 90 90 20 30 5C 86 D2 A5 .0..rir=.. 0\...
00A0: 05 CF 9C 1D C3 2F 8E 1C 13 75 F2 A7 C3 65 92 61 ...../...u...e.a
00B0: 5C A9 DD C7 D6 90 6B 87 29 00 82 DD B3 28 05 AD \.....k.)....(..
00C0: C8 BD EF 25 F3 5C 6C C9 50 62 C7 3B 8B 7B 8D 4D ...%.\l.Pb.;...M
00D0: 92 DB D1 BE 87 D4 C3 F8 F4 5A FD 54 27 07 FF 18 .........Z.T'...
00E0: 14 C5 DB 77 A8 2D D8 38 58 0D 14 75 DC C1 61 42 ...w.-.8X..u..aB
00F0: 90 2E D1 94 B5 B9 9B FA 70 2F 25 3A 0D 61 8B 38 ........p/%:.a.8 ] Added certificate to keystore 'jssecacerts' using alias 'cas.example.org-1' D:\casoverlay\cert>
-6. 检查下证书是否OK
重新运行运行InstallCert,就不会有错误提示了
java InstallCert cas.example.org:8443
-7. 最后一步,安装证书到客户端JVM
就是将生成的文件jssecacerts复制到 %java_home%\jre\lib\security目录下
-8. 重新启动,CAS 客户端登录下试试
如果操作正确,就没有错误了能正常登录了
CAS 5.x搭建常见问题系列(2).PKIX path building failed的更多相关文章
- 解决CAS单点登录出现PKIX path building failed的问题
在一次调试中,出现了这个错误: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderExceptio ...
- 解决PKIX path building failed的问题
Java在请求某些不受信任的https网站时会报:PKIX path building failed 解决方法一:使用keytool手动导入证书,为JRE环境导入信任证书 参考:http://www. ...
- Flutter配置环境报错“PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target”
背景:最近看了很多Flutter漂亮的项目,想要尝试一下.所有环境都搭建好之后,按照文档一步一步配置(抄袭),但始终报如下图错误. PKIX path building failed: sun.sec ...
- 解决 java 使用ssl过程中出现"PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target"
今天,封装HttpClient使用ssl时报一下错误: javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorExc ...
- 解决PKIX(PKIX path building failed) 问题 unable to find valid certification path to requested target
最近在写java的一个服务,需要给远程服务器发送post请求,认证方式为Basic Authentication,在请求过程中出现了 PKIX path building failed: sun.se ...
- jsoup访问页面: PKIX path building failed
在用jsoup访问页面时报错javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX p ...
- 抓取https网页时,报错sun.security.validator.ValidatorException: PKIX path building failed 解决办法
抓取https网页时,报错sun.security.validator.ValidatorException: PKIX path building failed 解决办法 原因是https证书问题, ...
- 彻底弄懂“PKIX path building failed”问题
SSL的基础知识 SSL的全称是Secure Socket Layer.它的通信流程如下图所示,客户端与服务端会通过几次通信,通过非对称加密创建出一个加密密钥,用于以后的对称信息加密. 1,客户端明文 ...
- javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed
1.使用HttpClient4.3 调用https出现如下错误: javax.net.ssl.SSLHandshakeException: sun.security.validator.Validat ...
随机推荐
- Go -- IP to int ip字符串和十进制相互转化
package main import ( "fmt" "net" "reflect" "github.com/thinkerid ...
- laravel 查询数据库first()返回的数据转数组
使用 get_object_vars()可以将他抓转为数组get_object_vars — 返回由对象属性组成的关联数组: 在laravel中其实还可以用 toArray(); json_decod ...
- Webpack中的sourcemap以及如何在生产和开发环境中合理的设置
一 . 从Sourcemap和Data URL说起 (1)什么是Sourcemap? 我们在打包中,将开发环境中源代码经过压缩,去空格,babel编译转化,最终可以得到适用于生产环境的项目代码,这样处 ...
- PHP try catch 如何使用
<?php try { if (file_exists('test_try_catch.php')) { require ('test_try_catch.php'); } else { ...
- SpringBoot持久层技术
一.Springboot整合mybatis maven中添加对数据库与mybatis的依赖 <dependencies> <dependency> <groupId> ...
- linux操作利器alias用法
写在前边 学习这件事,有时候并不一定很刻意,而是从生活,从经验中去积累,不知道什么时候就发生了. type 命令 一般情况下,type命令被用于判断另外一个命令是否是内置命令,但是它实际上有更多的用法 ...
- 37 Flutter仿京东商城项目 结算页面布局
加群452892873 下载对应34课文件,运行方法,建好项目,直接替换lib目录 CheckOut.dart import 'package:flutter/material.dart'; impo ...
- AtomicInteger的CAS算法浅析
之前浅析过自旋锁(自旋锁浅析),我们知道它的实现原理就是CAS算法.CAS(Compare and Swap)即比较并交换,作为著名的无锁算法,它也是乐观锁的实现方式之一.JDK并发包里也有许多代码中 ...
- mysql无法导入函数和存储过程解决方法
1. mysql> SET GLOBAL log_bin_trust_function_creators = 1; 2. 系统启动时 --log-bin-trust-function-creat ...
- SpringBoot集成tk mybatis插入数据,回显主键为null
实体信息如下 @Data public class ApiCertificate{ @Id @GeneratedValue(generator = "JDBC") private ...
