Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM
Goal -> Check if MAC address was changed.
Steps:
1. Execute and read ifconfig.
2. Read the mac address from the output.
3. Check if MAC in ifconfig is what the user requested.
4. Print appropriate message.
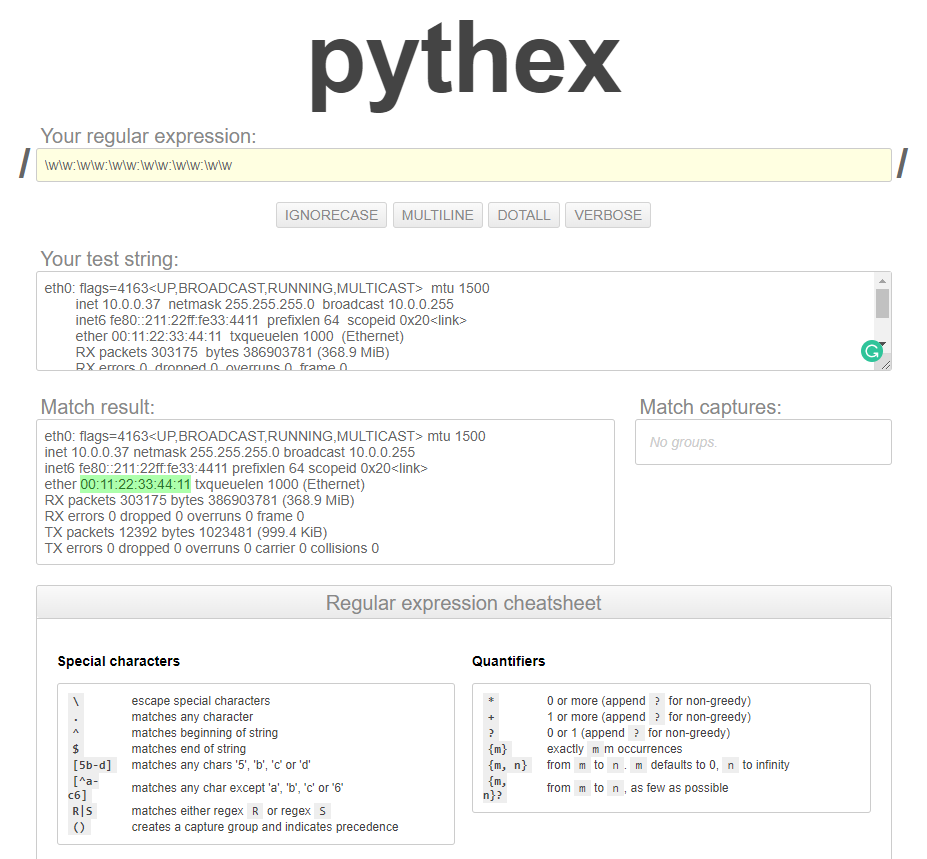
To find the MAC address, we can use the Pythex tool.
https://docs.python.org/2.7/library/re.html
https://pythex.org/?regex=%5Cw%5Cw%3A%5Cw%5Cw%3A%5Cw%5Cw%3A%5Cw%5Cw%3A%5Cw%5Cw%3A%5Cw%5Cw&test_string=eth0%3A%20flags%3D4163%3CUP%2CBROADCAST%2CRUNNING%2CMULTICAST%3E%20%20mtu%201500%0A%20%20%20%20%20%20%20%20inet%2010.0.0.37%20%20netmask%20255.255.255.0%20%20broadcast%2010.0.0.255%0A%20%20%20%20%20%20%20%20inet6%20fe80%3A%3A211%3A22ff%3Afe33%3A4411%20%20prefixlen%2064%20%20scopeid%200x20%3Clink%3E%0A%20%20%20%20%20%20%20%20ether%2000%3A11%3A22%3A33%3A44%3A11%20%20txqueuelen%201000%20%20(Ethernet)%0A%20%20%20%20%20%20%20%20RX%20packets%20303175%20%20bytes%20386903781%20(368.9%20MiB)%0A%20%20%20%20%20%20%20%20RX%20errors%200%20%20dropped%200%20%20overruns%200%20%20frame%200%0A%20%20%20%20%20%20%20%20TX%20packets%2012392%20%20bytes%201023481%20(999.4%20KiB)%0A%20%20%20%20%20%20%20%20TX%20errors%200%20%20dropped%200%20overruns%200%20%20carrier%200%20%20collisions%200%0A&ignorecase=0&multiline=0&dotall=0&verbose=0
EX: Python Code
#!/usr/bin/env python import subprocess
import optparse
import re def get_arguments():
parser = optparse.OptionParser()
parser.add_option("-i", "--interface", dest="interface", help="Interface to change its MAC address")
parser.add_option("-m", "--mac", dest="new_mac", help="New MAC address")
(options, arguments) = parser.parse_args()
if not options.interface:
parser.error("[-] Please specify an interface, use --help for more info.")
elif not options.new_mac:
parser.error("[-] Please specify a new mac, use --help for more info.")
return options def change_mac(interface, new_mac):
print("[+] Changing MAC address for " + interface + " to " + new_mac)
subprocess.call(["ifconfig", interface, "down"])
subprocess.call(["ifconfig", interface, "hw", "ether", new_mac])
subprocess.call(["ifconfig", interface, "up"]) def get_current_mac(interface):
ifconfig_result = subprocess.check_output(["ifconfig", interface])
mac_address_search_result = re.search(r"\w\w:\w\w:\w\w:\w\w:\w\w:\w\w", ifconfig_result) if mac_address_search_result:
return mac_address_search_result.group(0)
else:
print("[-] Could not read MAC address.") options = get_arguments() current_mac = get_current_mac(options.interface)
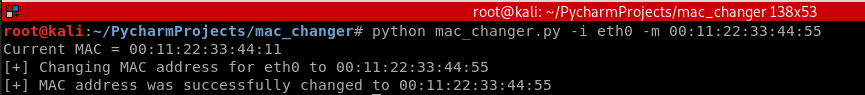
print("Current MAC = " + str(current_mac)) change_mac(options.interface, options.new_mac) current_mac = get_current_mac(options.interface)
if current_mac == options.new_mac:
print("[+] MAC address was successfully changed to " + current_mac)
else:
print("[-] MAC address did not get changed.")
Execute the following command to test the Python code:
python mac_changer.py -i eth0 -m :::::
Python Ethical Hacking - MAC Address & How to Change(3)的更多相关文章
- Python Ethical Hacking - MAC Address & How to Change(2)
FUNCTIONS Set of instructions to carry out a task. Can take input, and return a result. Make the cod ...
- Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS Media Access Control Permanent Physical Unique Assigned by manufacturer WHY CHANGE THE M ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
- Python Ethical Hacking - BeEF Framework(1)
Browser Exploitation Framework. Allows us to launch a number of attacks on a hooked target. Targets ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(7)
Handling Errors: If the client or server crashes, the connection will be lost. Backdoor crashes if: ...
随机推荐
- SSM-框架搭建-tank后台学习系统
一.前言 最近收到很多网友给我私信,学习软件开发有点吃力,不知道从何处开始学习,会点基础但是做不出来什么项目, 都想放弃了.我就回复道:当下互联网飞速发展,软件开发行业非常吃香而且前景相当不错.希望能 ...
- 看完这篇 HashMap,和面试官扯皮就没问题了
HashMap 概述 如果你没有时间细抠本文,可以直接看 HashMap 概述,能让你对 HashMap 有个大致的了解. HashMap 是 Map 接口的实现,HashMap 允许空的 key-v ...
- Linux 集群安装zookeeper
系统:CentOs 7 环境:jdk 8 Zookeeper 下载地址: http://www-eu.apache.org/dist/zookeeper/stable/ 上传至服务器并解压,本人放在 ...
- vue cli3项目中使用qrcodejs2生成二维码
组件的形式创建 1.下载依赖 npm install qrcodejs2 2.创建一个.vue的组件放置代码(我创建的是qrcodejs2.vue) //template中的代码 <templa ...
- vue全家桶(3.3)
4.7.作为vue的插件使用 在vue中,我们不需要在每个组件中都去引入axios,这样使用起来比较麻烦,我们可以结合插件vue-axios,让操作更简化 1.安装插件 npm install vue ...
- 使用CImage双缓冲
一普通显示:现在的VC显示图片非常方便,远不是VC6.0那个年代的技术可比,而且支持多种格式的如JPG,PNG. CImage _img; 初始化: _img.Load(L"map.png& ...
- 【部分】ASP.NET MVC的Controller接收输入详解
原文:https://blog.csdn.net/lxrj2008/article/details/79455360 ASP.NET mvc的Controller要正确的响应用户发出的请求就要获取到用 ...
- 数据库周刊28│开发者最喜爱的数据库是什么?阿里云脱口秀聊程序员转型;MySQL update误操作;PG流复制踩坑;PG异机归档;MySQL架构选型;Oracle技能表;Oracle文件损坏处理……
热门资讯 1.Stackoverflow 2020年度报告出炉!开发者最喜爱的数据库是什么?[摘要]2020年2月,近6.5万名开发者参与了 Stackoverflow 的 2020 年度调查,这份报 ...
- 部署Redis Cluster 6.0 集群并开启密码认证 和 Redis-cluster-proxy负载
部署Redis Cluster集群并开启密码认证 如果只想简单的搭建Redis Cluster,不需要设置密码和公网访问,可以参考官方文档. 节点介绍 Cluster模式推荐最少有6个节点,本次实验搭 ...
- 使用现代CSS的响应式版面
为一个网站选择类型尺寸是项艰巨的任务. 标题和段落的尺寸在网页布局和可读性方面处理起来很棘手. 谢天谢地, 我们有模块化缩放可以引导我们. 模块化缩放是一个数字序列以某种方式关联另一个序列. Tim ...
