Python Ethical Hacking - Intercepting and Modifying Packets
INTERCEPTING & MODIFYING PACKETS
Scapy can be used to:
- Create packets.
- Analyze packets.
- Send/receive packets.
But it can't be used to intercept packets/flows.
CLASSIC MITM SCENARIO

MITM - SNIFFING DATA
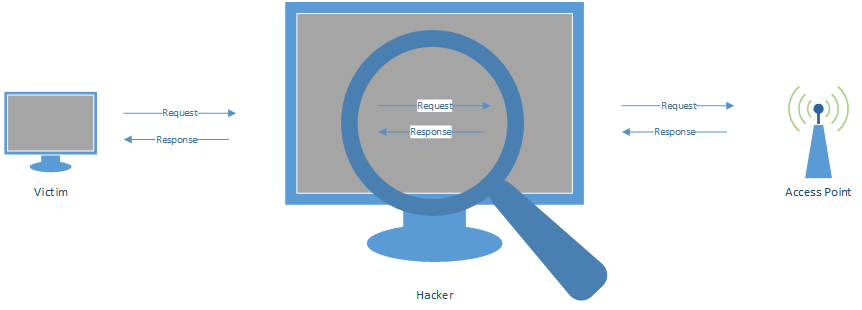
MITM - MODIFYING DATA


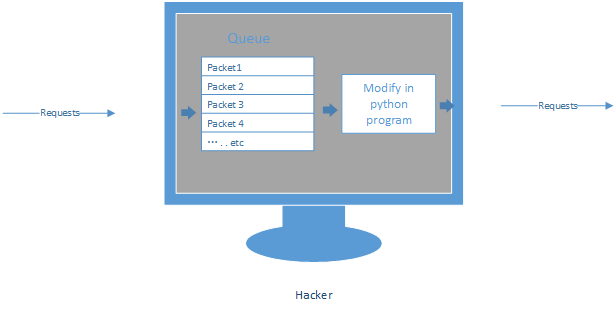
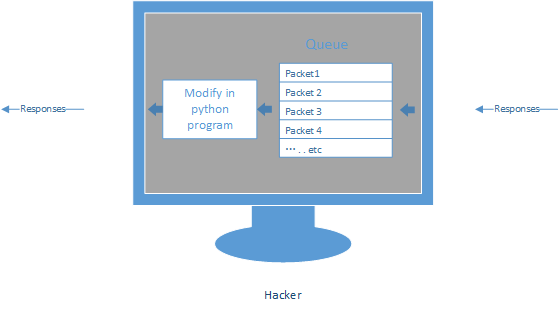
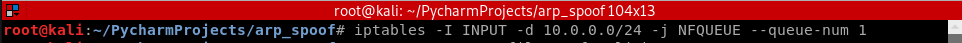
1. Execute the command - iptables to capture the packets into a queue.
iptables -I INPUT -d 10.0.0.0/ -j NFQUEUE --queue-num
2. Access the Packets queue.
Install the module netfilterqueue first.
pip3 install -U git+https://github.com/kti/python-netfilterqueue

3. Write the Python script to intercept and process the packets.
#!/usr/bin/env python
from netfilterqueue import NetfilterQueue def process_packet(packet):
print(packet)
packet.accept() queue = NetfilterQueue()
queue.bind(1, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')

We can also drop the packets through function packet.drop().
4. Use the following command to stop the packet capturing.
iptables --flush
Converting Packets to Scapy Packets
1. Execute the iptables command to capture the OUTPUT and INPUT packets.
iptables -I OUTPUT -j NFQUEUE --queue-num iptables -I INPUT -j NFQUEUE --queue-num
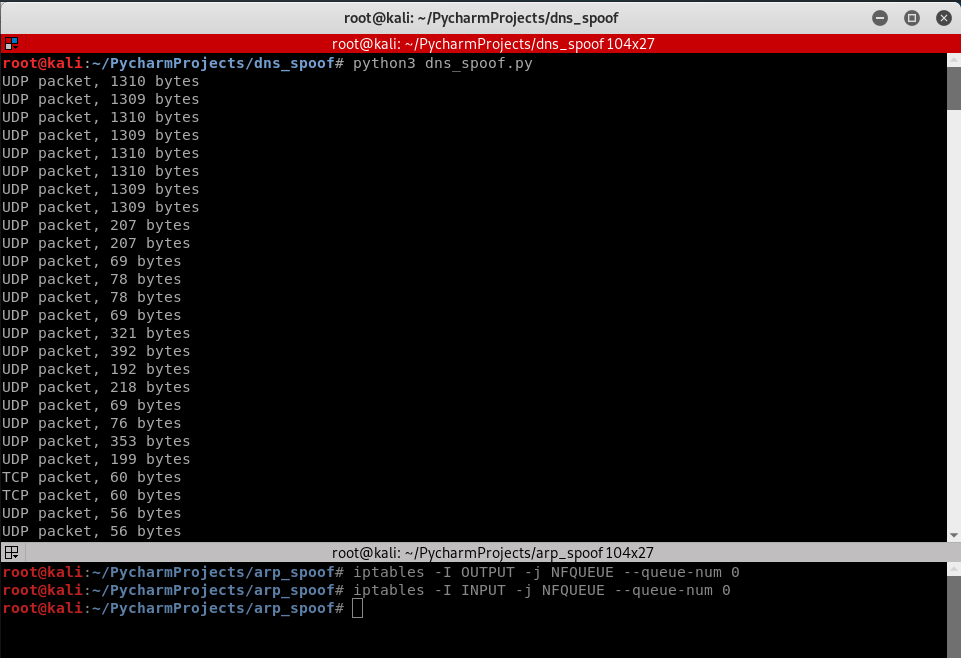
2. Execute the following Python script to process the captured packets.
#!/usr/bin/env python
from netfilterqueue import NetfilterQueue def process_packet(packet):
print(packet)
packet.accept() queue = NetfilterQueue()
queue.bind(0, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')
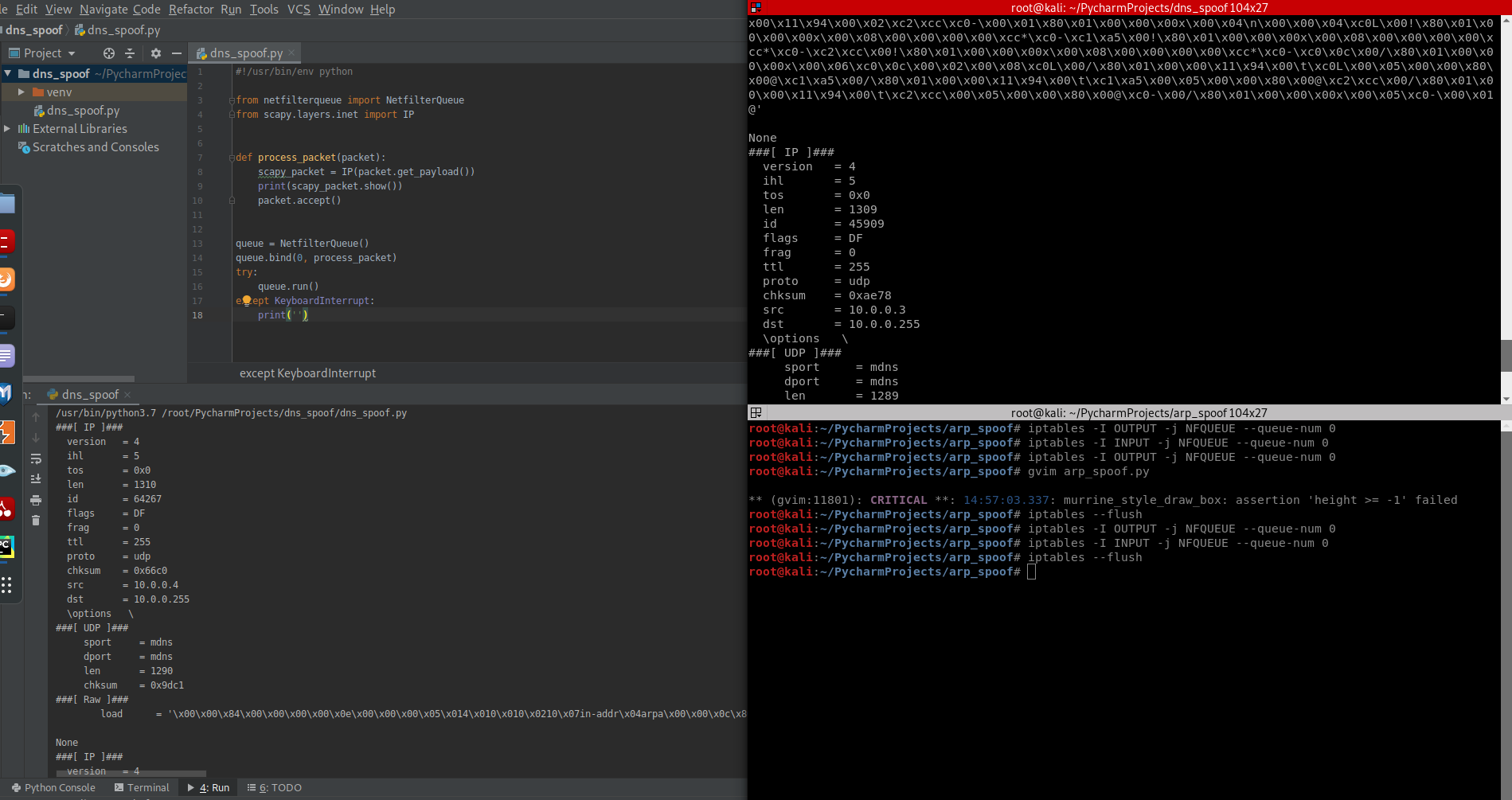
3. Convert the packet to scapy packet and show on the screen.
#!/usr/bin/env python from netfilterqueue import NetfilterQueue
from scapy.layers.inet import IP def process_packet(packet):
scapy_packet = IP(packet.get_payload())
print(scapy_packet.show())
packet.accept() queue = NetfilterQueue()
queue.bind(0, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')
4. Stop the capture of the packet by the command.
iptables --flush
Python Ethical Hacking - Intercepting and Modifying Packets的更多相关文章
- Python Ethical Hacking - Packet Sniffer(1)
PACKET_SNIFFER Capture data flowing through an interface. Filter this data. Display Interesting info ...
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(2)
MODIFYING DATA IN HTTP LAYER Edit requests/responses. Replace download requests. Inject code(html/Ja ...
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(1)
MODIFYING DATA IN HTTP LAYER Edit requests/responses. Replace download requests. Inject code(html/Ja ...
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(3)
Recalculating Content-Length: #!/usr/bin/env python import re from netfilterqueue import NetfilterQu ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - Bypass HTTPS(1)
HTTPS: Problem: Data in HTTP is sent as plain text. A MITM can read and edit requests and responses. ...
- Python Ethical Hacking - Packet Sniffer(2)
Capturing passwords from any computer connected to the same network. ARP_SPOOF + PACKET_SNIFFER Ta ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
随机推荐
- cb28a_c++_STL_算法_查找算法_(1)find_find_if
cb28a_c++_STL_算法_查找算法_(1)find_find_iffind() //线性查找,比较慢.pos1 = find(ilist.begin(), ilist.end(), 5);fi ...
- .Net Core踩坑记:读取txt中文乱码
迁移.net framework的项目,有块读取txt中文转码的问题,普通的不能再普通的代码,想都没想直接copy过去,也没测,结果今天就被坑了.Core是3.1版本,这是原来的代码: string ...
- 利用bat文件打开浏览器指定网页,提示 windows找不到chrome.exe。请确定文件名是否正确,再试一次 的解决经历
1.在网上找到一些bat命令,原来电脑可以正常使用,效果就是执行后打开谷歌浏览器并全屏展示某网页,但是在昨天换个一个电脑后发现不能用了,提示以下截图的错误 2.找了半天发现问题所在: 把chrom ...
- SpringBoot -- 项目结构+启动流程
一.简述: 项目结构 二.简述:启动流程 说springboot的启动流程,当然少不了springboot启动入口类 @SpringBootApplication public class Sprin ...
- 黑马程序员spring data jpa 2019年第一版本
第一步首先创建一个maven工程,导入对于的pom依赖 <project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xs ...
- 第三模块 :微服务网关Zuul架构和实践
52.Zuul网关架构剖析~1.mp4 请求过来之后首先会通过前置过滤器,然后到路由过滤器,路由过滤器是真正访问后台远程服务的,经过路由器之后,最后会传递给后置过滤器 在三个过滤器处理的过程中任何一个 ...
- 四层发现-TCP和UDP发现简介
虽然这里使用到了端口发现,但是四层发现阶段并不对端口进行解析,而是通过端口进行对ip是否存活的判断. 这里是对主机的发现,而不是对端口的识别. 四层发现的结果比三层发现的结果更加精确,基本不会被防火墙 ...
- 入门大数据---Flink核心概念综述
一.Flink 简介 Apache Flink 诞生于柏林工业大学的一个研究性项目,原名 StratoSphere .2014 年,由 StratoSphere 项目孵化出 Flink,并于同年捐赠 ...
- github知名企业开源项目索引
亚马逊:https://github.com/amzn 饿了么 https://github.com/ElemeFEhttp://lrd.ele.me/腾讯 https://github.com/Te ...
- 报错 version `GLIBCXX_3.4.22' not found
from . import pypocketfft as pfft ImportError: /usr/lib/x86_64-linux-gnu/libstdc++.so.6: version `GL ...
