OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks
1. Crack using the tool - john (Too slow in real world)
Locate the rockyou file.

john --wordlist=/usr/share/wordlists/rockyou.txt windows
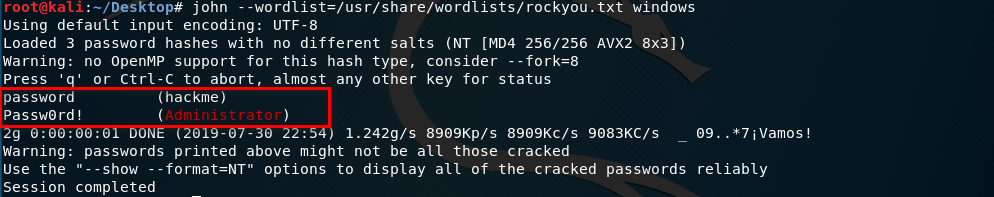
john --show windows

Conbine the files and save as unshadow.
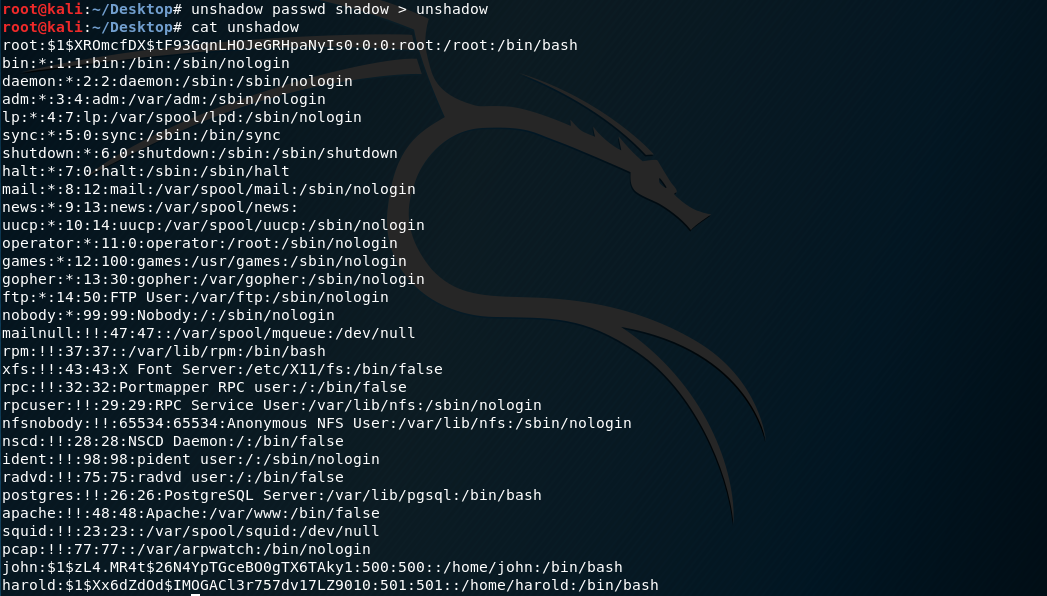
john --rules --wordlist=/usr/share/wordlists/rockyou.txt unshadow

2.Using Hash craker on the Internet. (Suggested)
8846F7EAEE8FB117AD06BDD830B7586C

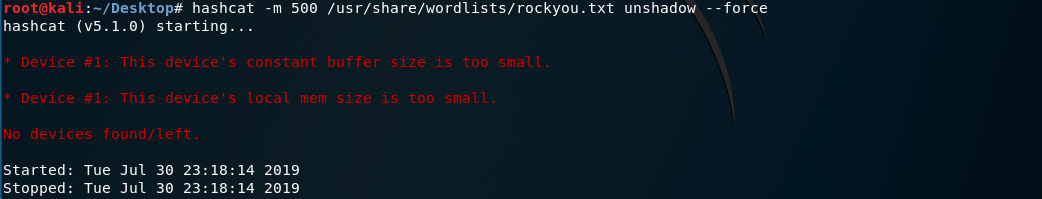
3. Use the tool hashcat
On Kali Linux.(Too slow locally)
hashcat -m /usr/share/wordlists/rockyou.txt unshadow --force
On Windows
hashcat64.exe -m 500 unshadow.txt rockyou.txt
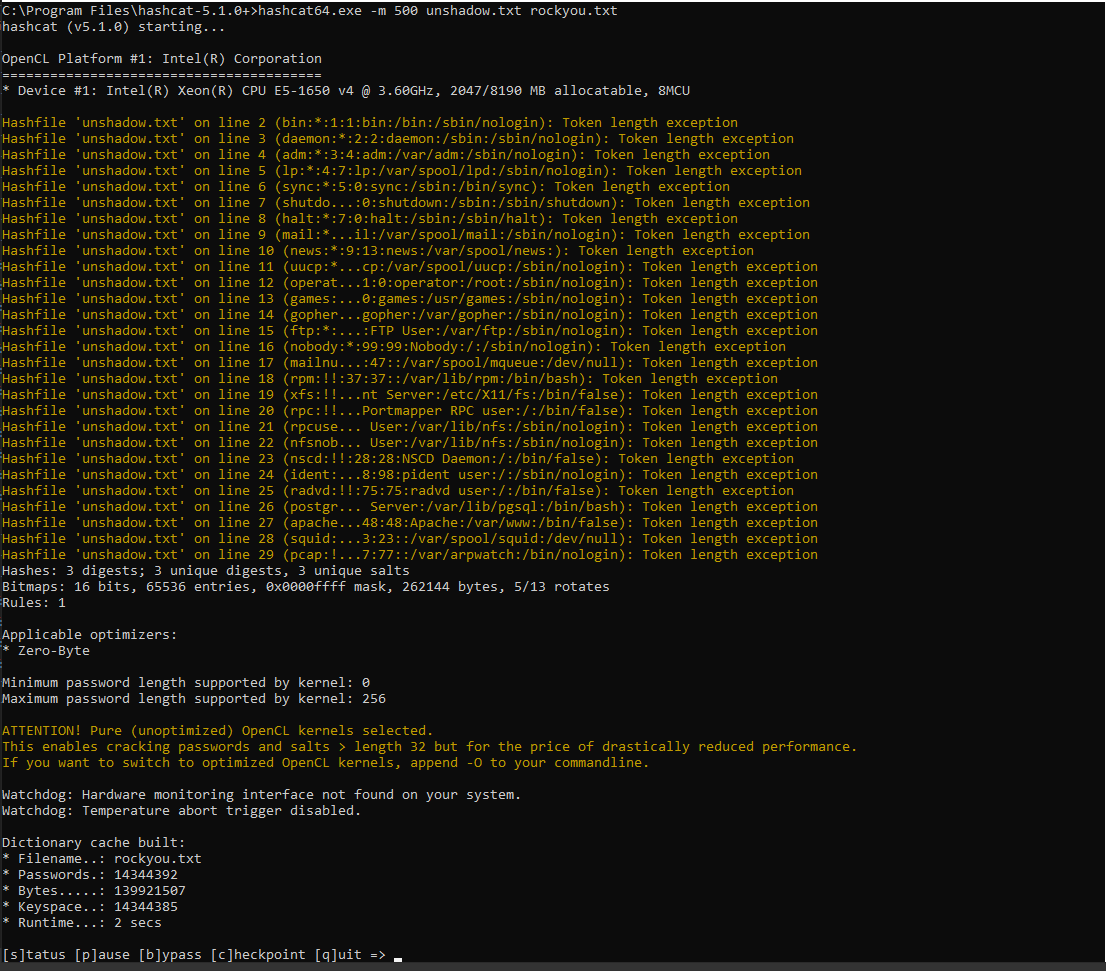
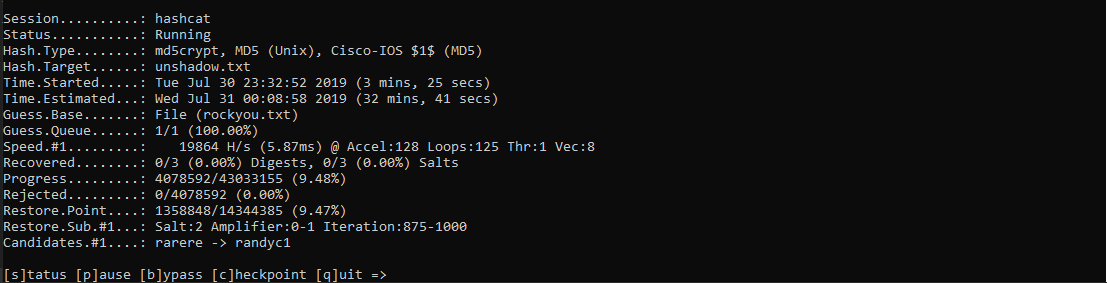
Hash Craker Websites:
Tips: If it is hard to crack the password, do not waste time on it. Just skip it and find another way.
OSCP Learning Notes - Post Exploitation(3)的更多相关文章
- OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation Target Server: IE8-Win 7 VM 1. Download and upload the fgdump, PwDump7, wc ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Post Exploitation(4)
Pivoting 1. Edit the virtual network settings of the Vmware. 2. Set the Network Adapter(s) of Kali L ...
- OSCP Learning Notes - WebApp Exploitation(5)
Remote File Inclusion[RFI] Prepare: Download the DVWA from the following website and deploy it on yo ...
- OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI] Target Pentester Lab: Download from the following website: https://www.vul ...
- OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi] Refrence: SQL Injection Authentication Bypass Cheat Sheet https://pentestlab.blo ...
- OSCP Learning Notes - WebApp Exploitation(2)
Cross-Site Scripting(XSS) 1. Using the tool - netdiscover to find the IP of target server. netdiscov ...
- OSCP Learning Notes - WebApp Exploitation(1)
Installing XSS&MySQL FILE Download the Pentester Lab: XSS and MySQL FILE from the following webs ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
随机推荐
- spring boot actuator端点高级进阶metris指标详解、git配置详解、自定义扩展详解
https://www.cnblogs.com/duanxz/p/3508267.html 前言 接着上一篇<Springboot Actuator之一:执行器Actuator入门介绍>a ...
- hystrix信号量和线程池的区别
- Web安全之暴力破解
暴力破解,顾名思义简单粗暴直接,我理解为将所有的“答案”都进行尝试直到找到正确的“答案", 当然我们不可能将所有的“答案”都进行尝试,所以我们只能将所有最有可能是正确的“答案”进行尝试即可 ...
- FastAPI 快速搭建一个REST API 服务
最近正好在看好的接口文档方便的工具, 突然看到这个, 试了一下确实挺方便 快速示例 from fastapi import FastAPI from pydantic import BaseModel ...
- Apache POI 操作Excel(1)--POI简介
Apache POI(http://poi.apache.org/)是一个用于读取和编写Microsoft Office文件格式开源的Java项目,现在已经可以操作Excel,PowerPoint,W ...
- EntityFramework Core 迁移忽略主外键关系
前言 本文来源于一位公众号童鞋私信我的问题,在我若加思索后给出了其中一种方案,在此之前我也思考过这个问题,借此机会我稍微看了下,目前能够想到的也只是本文所述方案. 为何要忽略主外键关系 我们不仅疑惑为 ...
- html实现邮箱发送邮件_js发送邮件至指定邮箱功能
在前端开发中,JavaScript并没有提供直接操作Email邮箱的功能方法,但是遇到这样的需求,我们应该如何实现js发送邮件至指定邮箱功能呢?下面列举能够在通过前端实现邮件发送的几种方式: 方式一: ...
- LeetCode题解【题2】:两数相加
原题链接:https://leetcode-cn.com/problems/add-two-numbers/ 查看请另起链接打开. 解题思路执行用时 :2 ms, 在所有 Java 提交中击败了99. ...
- return 关键字
return关键字:1.使用范围:使用在方法体中2.作用: ① 结束方法 ② 针对于返回值类型的方法,使用"return 数据"方法返回所要的数据.3.注意点:return关键字后 ...
- Numerical Sequence (Hard vision) 题解
The only difference between the easy and the hard versions is the maximum value of \(k\). You are gi ...
