容器编排系统K8s之Dashboard部署
前文我们了解了k8s的访问控制第三关准入控制相关插件的使用,回顾请参考:https://www.cnblogs.com/qiuhom-1874/p/14220402.html;今天我们来了解下k8s的web ui 组件的安装和用户授权相关话题;
k8s的webui是一个插件运行在k8s之上,以pod的方式提供服务;它能够给使用k8s用户提供一个web面板,我们可以基于这个web面板来管理k8s集群;比如创建pod,创建svc,部署应用等等;在部署之前,先说一下dashboard认证过程;dashboard是以pod的形式运行在k8s之上,它本身没有做访问权限认证相关的功能,它只是把用户的认证信息代理到k8s集群上,具体的认证授权还是由k8s的apiserver进行;所以我们登录dashboard必须是k8s上的用户;其次它是一个pod形式把我们的认证信息代理到apiserver上,所以我们登录dashboard的用户必须是一个sa用户,它不支持常规用户;简单讲dashboard就是一个代理服务;它把我们所有操作通过https协议代理到apiserver做相应的操作;dashboard是一个多用户的插件,它支持同时多个用户以不同身份登录到dashboard上做操作;对于dashboard本身来讲,它就是k8s上的一个web服务以pod形式运行,我们可以通过ingrss把它发布出来,也可以通过service把它发布出来;选择其中一种方式即可;
dashboard部署前准备
dashboard对外提供服务的是一个https服务,如果我们需要将其发布到集群外部供互联网访问,我们需要把对应域名的证书先用secret资源加载到k8s上,然后在部署dashboard时,引用对应的secret即可;
生成私钥,证书签署请求文件csr,然后发送给对应CA签署(如果对应域名的证书都申请好了,这一步直接跳过)
[root@master01 ~]# mkdir dashboard
[root@master01 ~]# cd dashboard
[root@master01 dashboard]# openssl genrsa -out dashboard.key 2048
Generating RSA private key, 2048 bit long modulus
................................................................................................+++
..................+++
e is 65537 (0x10001)
[root@master01 dashboard]# openssl req -new -key dashboard.key -out dashboard.csr -subj "/O=test/CN=webui.test.com"
[root@master01 dashboard]# ll
total 8
-rw-r--r-- 1 root root 920 Jan 2 14:00 dashboard.csr
-rw-r--r-- 1 root root 1679 Jan 2 13:59 dashboard.key
[root@master01 dashboard]#
使用某个ca签署对应的证书签署请求文件,我这里直接使用k8s上的CA签
[root@master01 dashboard]# openssl x509 -req -in dashboard.csr -CA /etc/kubernetes/pki/ca.crt -CAkey /etc/kubernetes/pki/ca.key -CAcreateserial -out dashboard.crt -days 3650
Signature ok
subject=/O=test/CN=webui.test.com
Getting CA Private Key
[root@master01 dashboard]# ll
total 12
-rw-r--r-- 1 root root 1005 Jan 2 14:04 dashboard.crt
-rw-r--r-- 1 root root 920 Jan 2 14:00 dashboard.csr
-rw-r--r-- 1 root root 1679 Jan 2 13:59 dashboard.key
[root@master01 dashboard]#
提示:正常情况是找互联网上的ca签署,该证书只是用于使用对应域名在浏览器上能够通过https访问到dashboard;
下载部署清单,查看对应对应清单中的名称空间和对应secret的名称
[root@master01 dashboard]# wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.1.0/aio/deploy/recommended.yaml
--2021-01-02 14:14:48-- https://raw.githubusercontent.com/kubernetes/dashboard/v2.1.0/aio/deploy/recommended.yaml
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 199.232.28.133
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|199.232.28.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7552 (7.4K) [text/plain]
Saving to: ‘recommended.yaml’ 100%[=========================================================================>] 7,552 3.08KB/s in 2.4s 2021-01-02 14:14:52 (3.08 KB/s) - ‘recommended.yaml’ saved [7552/7552] [root@master01 dashboard]# ls
dashboard.crt dashboard.csr dashboard.key recommended.yaml
[root@master01 dashboard]#

提示:上述是dashboard的部署清单中的secret资源名称和对应的名称空间,我们如果需要手动替换自己的证书,就必须提前把对应的证书做成和部署清单中相同名称空间相同类型和相同名称的secret资源;
创建kubenetes-dashboard名称空间,把dashboard.crt和dashboard.key映射为k8s上kubenetes-dashboard名称空间下的generic类型的secret资源
[root@master01 dashboard]# kubectl create ns kubernetes-dashboard
namespace/kubernetes-dashboard created
[root@master01 dashboard]# kubectl create secret generic kubernetes-dashboard-certs --from-file=dashboard.crt --from-file=dashboard.key -n kubernetes-dashboard
secret/kubernetes-dashboard-certs created
[root@master01 dashboard]# kubectl get secret -n kubernetes-dashboard
NAME TYPE DATA AGE
default-token-vcw5h kubernetes.io/service-account-token 3 2m31s
kubernetes-dashboard-certs Opaque 2 12s
[root@master01 dashboard]#
应用dashboard部署资源清单
[root@master01 dashboard]# kubectl apply -f recommended.yaml
Warning: resource namespaces/kubernetes-dashboard is missing the kubectl.kubernetes.io/last-applied-configuration annotation which is required by kubectl apply. kubectl apply should only be used on resources created declaratively by either kubectl create --save-config or kubectl apply. The missing annotation will be patched automatically.
namespace/kubernetes-dashboard configured
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
Warning: resource secrets/kubernetes-dashboard-certs is missing the kubectl.kubernetes.io/last-applied-configuration annotation which is required by kubectl apply. kubectl apply should only be used on resources created declaratively by either kubectl create --save-config or kubectl apply. The missing annotation will be patched automatically.
secret/kubernetes-dashboard-certs configured
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
[root@master01 dashboard]#
在线编辑对应service的配置,将clusterip类型更改为nodeport类型
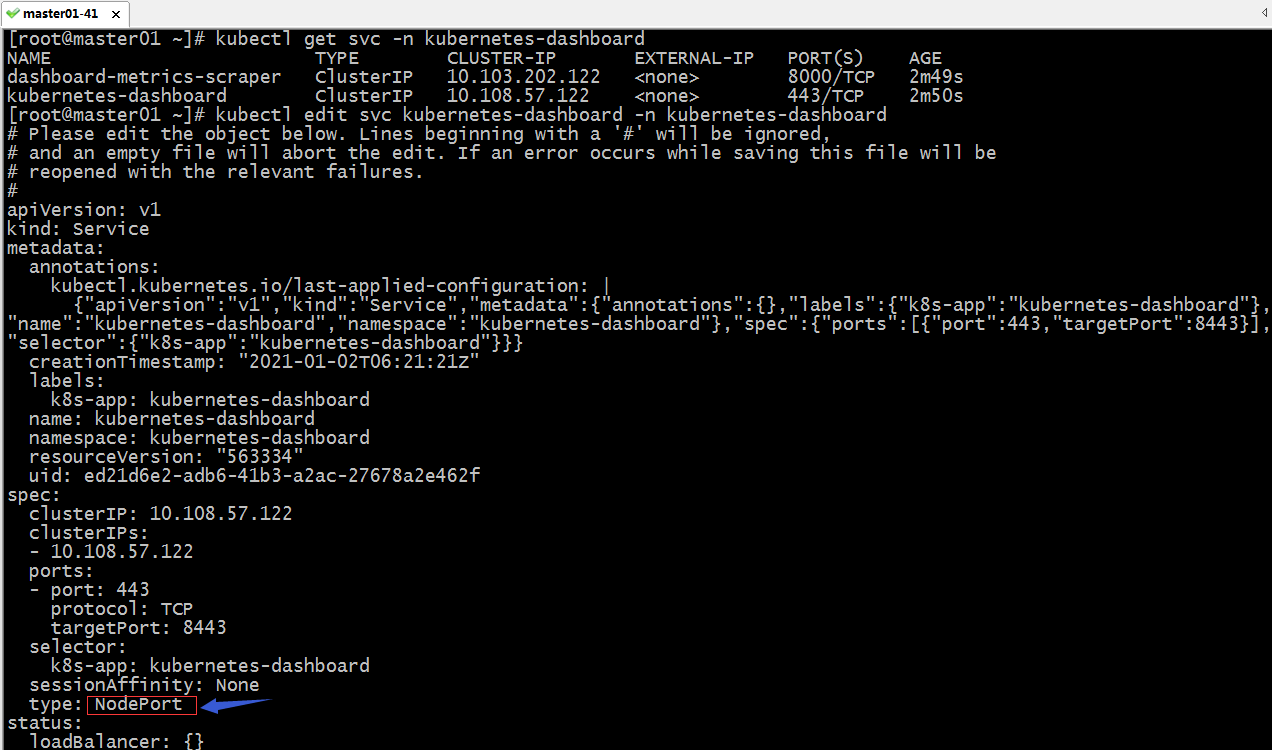
提示:更改为nodeport类型service,对应集群外部的客户端才可以正常访问;
查看对应名称空间下的pod是否启动起来?
[root@master01 ~]# kubectl get all -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
pod/dashboard-metrics-scraper-79c5968bdc-tc79t 1/1 Running 0 6m56s
pod/kubernetes-dashboard-7448ffc97b-v98gk 1/1 Running 0 6m56s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/dashboard-metrics-scraper ClusterIP 10.103.202.122 <none> 8000/TCP 6m56s
service/kubernetes-dashboard NodePort 10.108.57.122 <none> 443:31635/TCP 6m57s NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/dashboard-metrics-scraper 1/1 1 1 6m56s
deployment.apps/kubernetes-dashboard 1/1 1 1 6m56s NAME DESIRED CURRENT READY AGE
replicaset.apps/dashboard-metrics-scraper-79c5968bdc 1 1 1 6m56s
replicaset.apps/kubernetes-dashboard-7448ffc97b 1 1 1 6m56s
[root@master01 ~]#
提示:可以看到对应资源都已经跑起来了,对应service暴露的端口是34635端口,我们可以访问k8s集群任意节点的31635端口就能访问到dashboard,如果使用域名访问,请注意对应域名要解析到对应k8s集群上的任意一个节点ip上;
访问dashboard
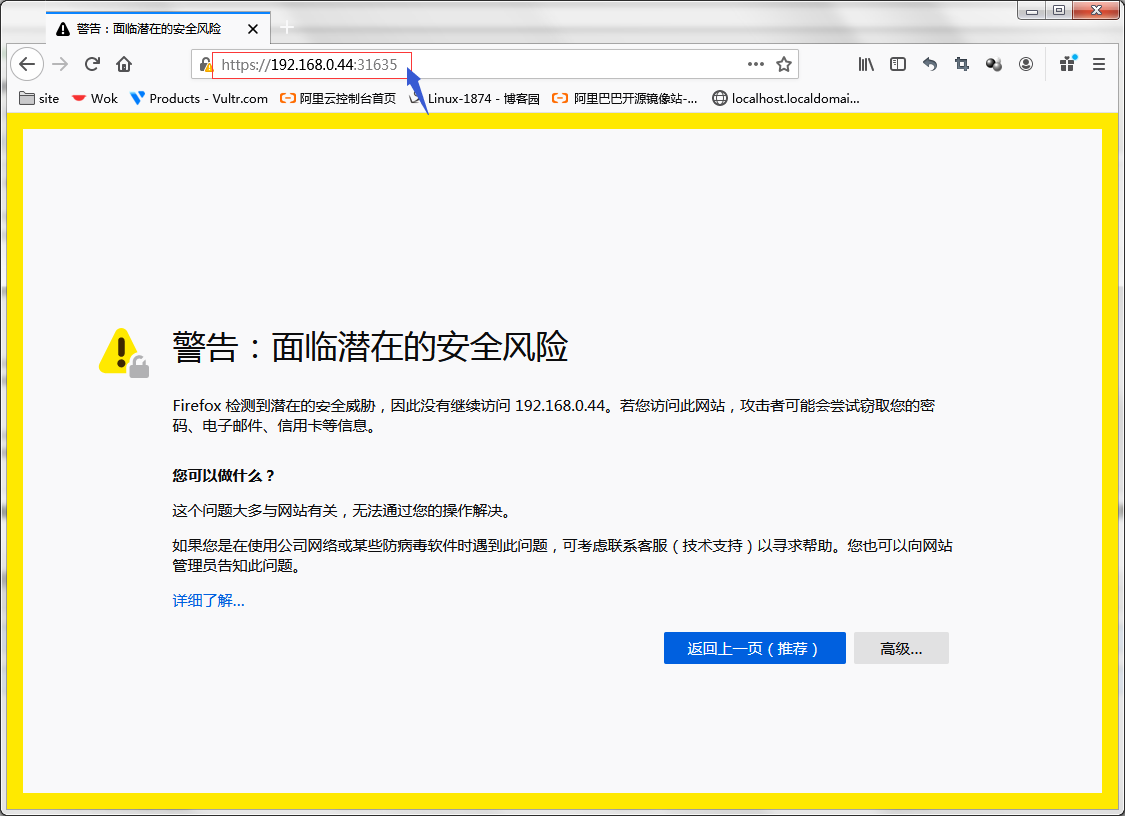
提示:这里要用https访问,因为对应服务是提供的https服务;这里提示我们证书不安全,是因为对应证书不是浏览器认可的ca颁发,所以我们需要自己手动信任下;

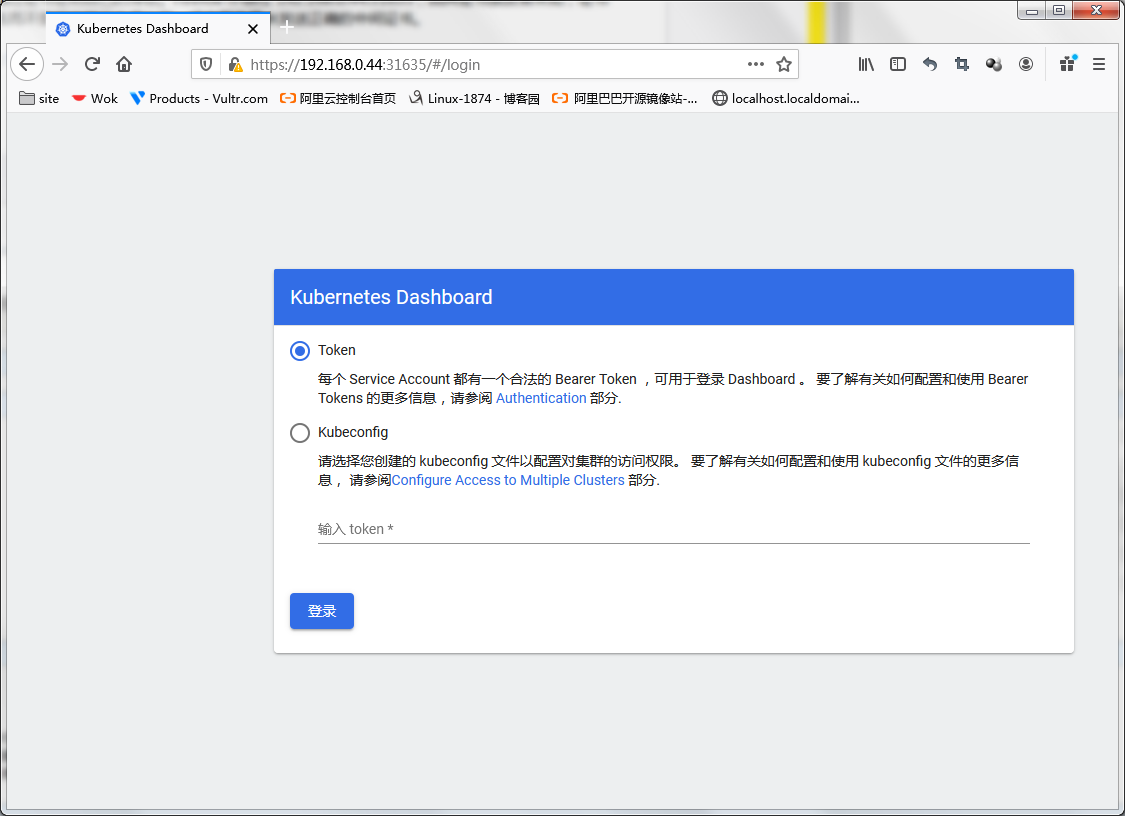
提示:能够看到上面的页面,说明dashboard就运行起来了,接下我们要创建一个账号来登录dashboard;
创建一个sa账号
[root@master01 ~]# kubectl create serviceaccount webui-cluster-admin -n kubernetes-dashboard
serviceaccount/webui-cluster-admin created
[root@master01 ~]# kubectl get sa -n kubernetes-dashboard
NAME SECRETS AGE
default 1 29m
kubernetes-dashboard 1 17m
webui-cluster-admin 1 11s
[root@master01 ~]# kubectl describe sa webui-cluster-admin -n kubernetes-dashboard
Name: webui-cluster-admin
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: webui-cluster-admin-token-bxl2z
Tokens: webui-cluster-admin-token-bxl2z
Events: <none>
[root@master01 ~]#
授权对应sa账号为cluster-admin角色
[root@master01 ~]# kubectl create clusterrolebinding webui-cluster-admin --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:webui-cluster-admin
clusterrolebinding.rbac.authorization.k8s.io/webui-cluster-admin created
[root@master01 ~]# kubectl get clusterrolebinding |grep webui
webui-cluster-admin ClusterRole/cluster-admin 41s
[root@master01 ~]# kubectl describe clusterrolebinding webui-cluster-admin
Name: webui-cluster-admin
Labels: <none>
Annotations: <none>
Role:
Kind: ClusterRole
Name: cluster-admin
Subjects:
Kind Name Namespace
---- ---- ---------
ServiceAccount webui-cluster-admin kubernetes-dashboard
[root@master01 ~]#
提示:指定serviceaccount需要指定对应sa的名称空间加“:”对应sa的名称;
使用上面对应sa账号对应的secret中的token登录dashboard
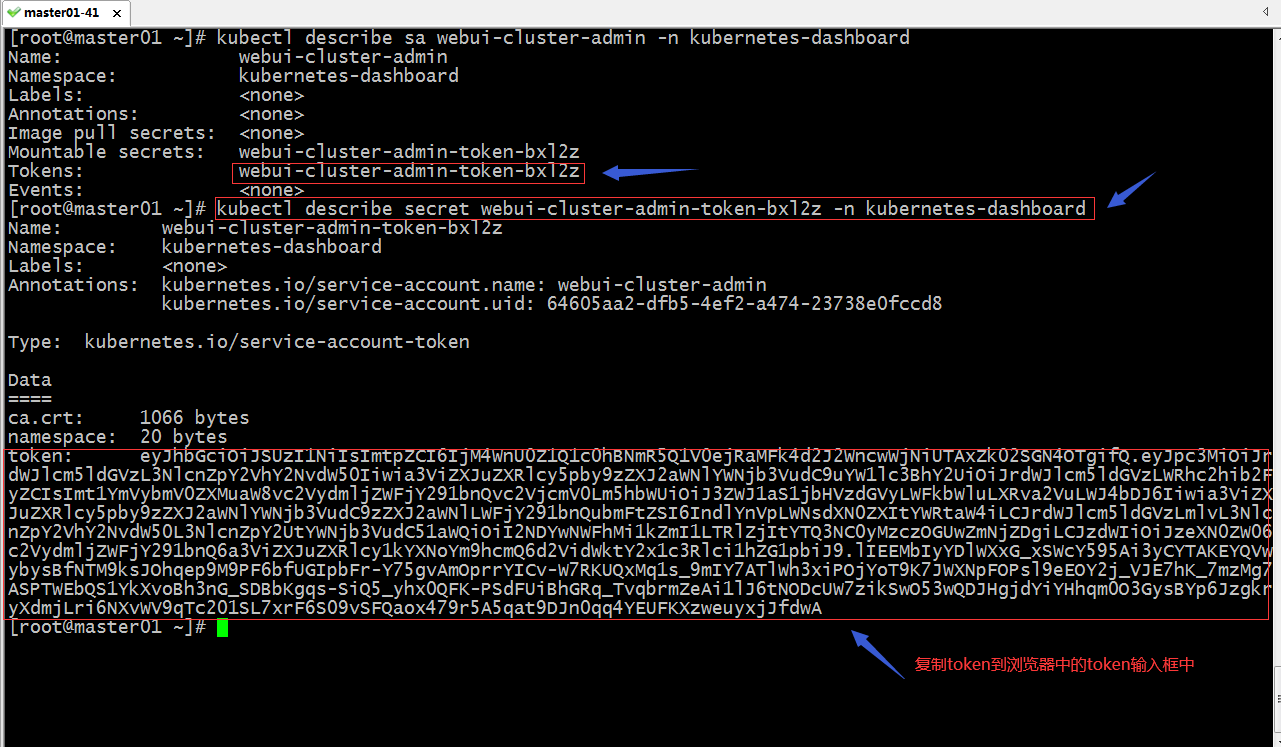
登录dashboard
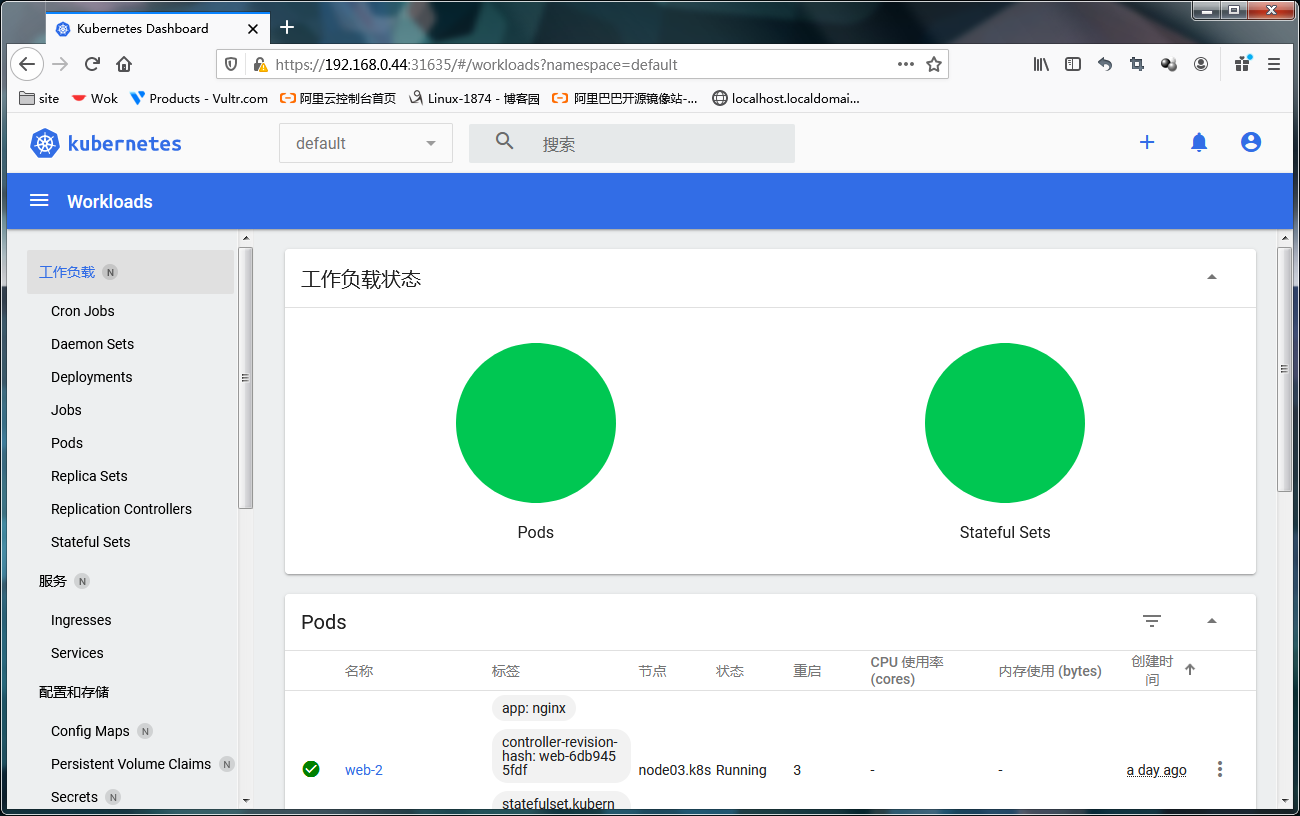
提示:默认登录到dashboard会是在default名称空间,我们可以选择上面的名称空间查看对应名称空间下的资源;
创建某个名称空间下的管理员
[root@master01 ~]# kubectl create serviceaccount myns-admin -n myns
serviceaccount/myns-admin created
[root@master01 ~]# kubectl create rolebinding myns-admin --clusterrole=admin --serviceaccount=myns:myns-admin -n myns
rolebinding.rbac.authorization.k8s.io/myns-admin created
[root@master01 ~]#
提示:rolebinding需要指定名称空间,否则不指定默认表示default名称空间;
查看对应账号的token
[root@master01 ~]# kubectl describe sa -n myns
Name: default
Namespace: myns
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: default-token-n6tg5
Tokens: default-token-n6tg5
Events: <none> Name: myns-admin
Namespace: myns
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: myns-admin-token-p6gh8
Tokens: myns-admin-token-p6gh8
Events: <none>
[root@master01 ~]# kubectl describe secret myns-admin-token-p6gh8 -n myns
Name: myns-admin-token-p6gh8
Namespace: myns
Labels: <none>
Annotations: kubernetes.io/service-account.name: myns-admin
kubernetes.io/service-account.uid: ebaed1a9-4631-42cb-8af9-a14fa35a7098 Type: kubernetes.io/service-account-token Data
====
ca.crt: 1066 bytes
namespace: 4 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IjM4WnU0Z1Q1c0hBNmR5Q1V0ejRaMFk4d2J2WncwWjNiUTAxZk02SGN4OTgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJteW5zIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6Im15bnMtYWRtaW4tdG9rZW4tcDZnaDgiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoibXlucy1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImViYWVkMWE5LTQ2MzEtNDJjYi04YWY5LWExNGZhMzVhNzA5OCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpteW5zOm15bnMtYWRtaW4ifQ.JuZ9WsojEfJai-Z1uLH7AIS-kLyqqln9POzEEoV_RTBKGO4NbtDJwMOw3z4SVeLwdCSiBefh-pD03DCnHmZ-HunrUPXBix2iKRgD42fkQ2L8cZzl8LGEw88jK5mUpSOF2si0wibc1cn7Gtrc5LqMiVtOgLoBMhEXaX2_RDUXj0Q8FtNb_srIcjQe__gXsMGmXxhHuU629IVk7fM99FvHzlDOyLj4goaydMw7F9-JFpL3I-ll2lq46goKDEwB2pMEz_qvsVFHvILNzg318TilMSK4VeMpKUbje6eovvs2IYSMCfVRBtvlpsv3KixYONai1AvYRQz_iISwKzI5JWO4hw
[root@master01 ~]#
使用对应的token登录dashboard
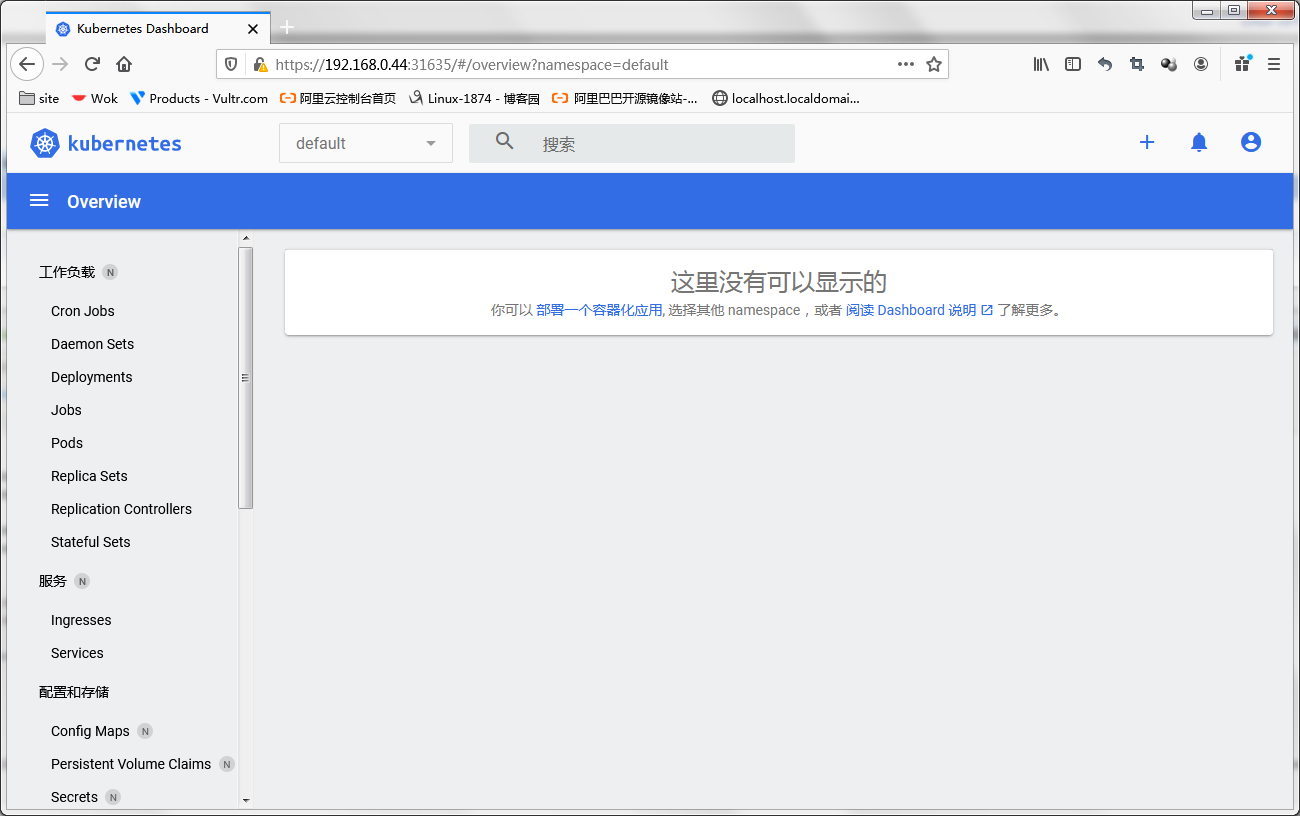
提示:这里默认登录进来是default名称空间,对应账号没有权限,所以它会提示我们没有权限查看当前名称空间下的资源;
切换到myns名称空间
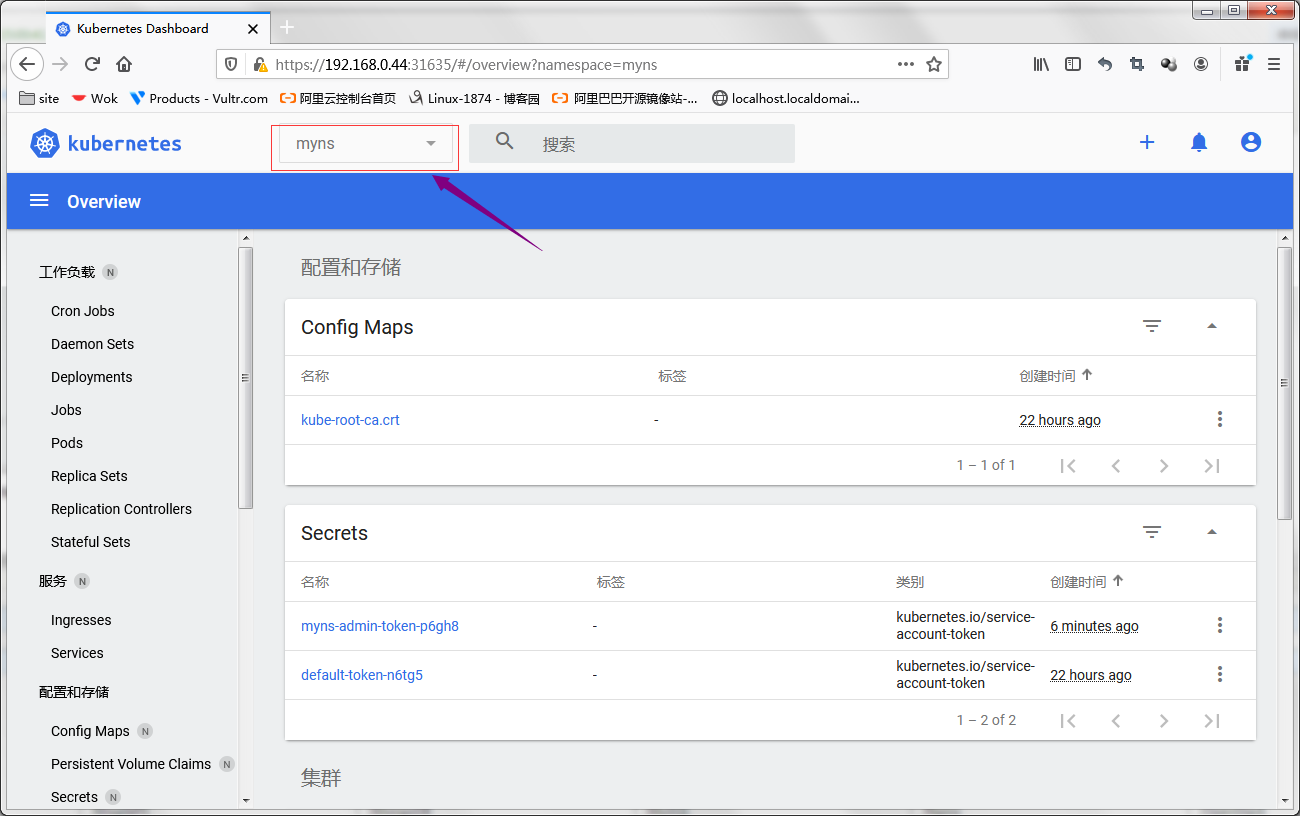
提示:到此对应用户就能在myns名称空间下做响应的管理操作了;
制作kubeconfig文件登录dashboard
[root@master01 ~]# kubectl config set-cluster mykube --server="https://192.168.0.41:6443" --embed-certs --certificate-authority=/etc/kubernetes/pki/ca.crt --kubeconfig=/tmp/test-mykube.config
Cluster "mykube" set.
[root@master01 ~]# kubectl config set-credentials webui-admin --token=eyJhbGciOiJSUzI1NiIsImtpZCI6IjM4WnU0Z1Q1c0hBNmR5Q1V0ejRaMFk4d2J2WncwWjNiUTAxZk02SGN4OTgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJ3ZWJ1aS1jbHVzdGVyLWFkbWluLXRva2VuLWJ4bDJ6Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6IndlYnVpLWNsdXN0ZXItYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2NDYwNWFhMi1kZmI1LTRlZjItYTQ3NC0yMzczOGUwZmNjZDgiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6d2VidWktY2x1c3Rlci1hZG1pbiJ9.lIEEMbIyYDlWXxG_xSWcY595Ai3yCYTAKEYQVwybysBfNTM9ksJOhqep9M9PF6bfUGIpbFr-Y75gvAmOprrYICv-W7RKUQxMq1s_9mIY7ATlWh3xiPOjYoT9K7JWXNpFOPsl9eEOY2j_VJE7hK_7mzMg7ASPTWEbQS1YkXvoBh3nG_SDBbKgqs-SiQ5_yhx0QFK-PSdFUiBhGRq_TvqbrmZeAi1lJ6tNODcUW7zikSwO53wQDJHgjdYiYHhqm0O3GysBYp6JzgkryXdmjLri6NXvWV9qTc201SL7xrF6S09vSFQaox479r5A5qat9DJn0qq4YEUFKXzweuyxjJfdwA --kubeconfig=/tmp/test-mykube.config
User "webui-admin" set.
[root@master01 ~]# kubectl config set-context webui-admin@mykube --cluster=mykube --user=webui-admin --kubeconfig=/tmp/test-mykube.config
Context "webui-admin@mykube" created.
[root@master01 ~]# kubectl config view --kubeconfig=/tmp/test-mykube.config
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.0.41:6443
name: mykube
contexts:
- context:
cluster: mykube
user: webui-admin
name: webui-admin@mykube
current-context: ""
kind: Config
preferences: {}
users:
- name: webui-admin
user:
token: REDACTED
[root@master01 ~]# kubectl config use-context webui-admin@mykube --kubeconfig=/tmp/test-mykube.config
Switched to context "webui-admin@mykube".
[root@master01 ~]# kubectl config view --kubeconfig=/tmp/test-mykube.config
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.0.41:6443
name: mykube
contexts:
- context:
cluster: mykube
user: webui-admin
name: webui-admin@mykube
current-context: webui-admin@mykube
kind: Config
preferences: {}
users:
- name: webui-admin
user:
token: REDACTED
[root@master01 ~]#
提示:在设置用户时,选择对应用户的token信息即可;
把对应配置文件导出,在浏览器上使用对应文件登录dashboard
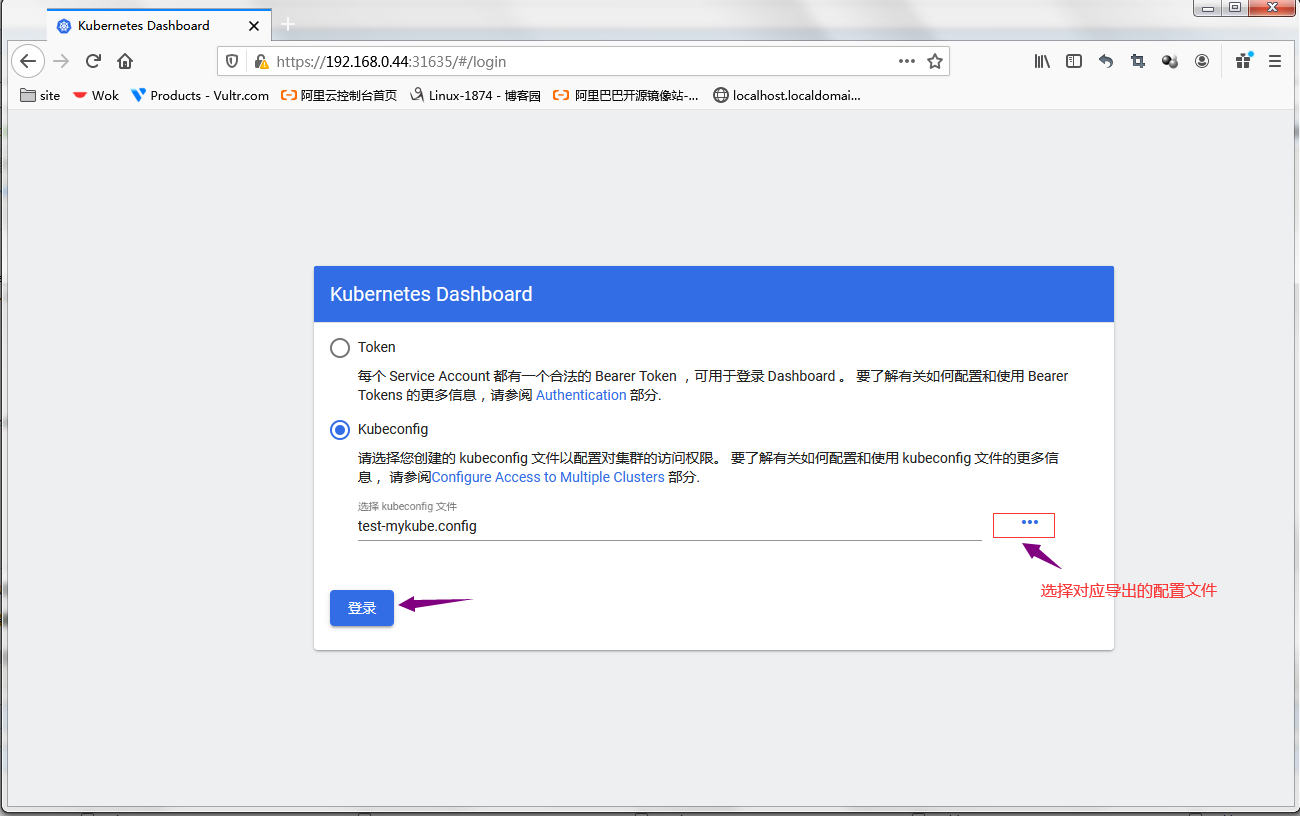
提示:此时登录到dashboard用户就是对应配置文件中的token对应的sa用户;到此dashboard就搭建好了。。
容器编排系统K8s之Dashboard部署的更多相关文章
- 容器编排系统K8s之ConfigMap、Secret资源
前文我们了解了k8s上的pv/pvc/sc资源的使用和相关说明,回顾请参考:https://www.cnblogs.com/qiuhom-1874/p/14188621.html:今天我们主要来聊一下 ...
- 容器编排系统K8s之flannel网络模型
前文我们聊到了k8s上webui的安装和相关用户授权,回顾请参考:https://www.cnblogs.com/qiuhom-1874/p/14222930.html:今天我们来聊一聊k8s上的网络 ...
- 容器编排系统K8s之Prometheus监控系统+Grafana部署
前文我们聊到了k8s的apiservice资源结合自定义apiserver扩展原生apiserver功能的相关话题,回顾请参考:https://www.cnblogs.com/qiuhom-1874/ ...
- 容器编排系统k8s之Ingress资源
前文我们了解了k8s上的service资源的相关话题,回顾请参考:https://www.cnblogs.com/qiuhom-1874/p/14161950.html:今天我们来了解下k8s上的In ...
- 容器编排系统K8s之Volume的基础使用
前文我们聊到了k8s上的ingress资源相关话题,回顾请参考:https://www.cnblogs.com/qiuhom-1874/p/14167581.html:今天们来聊一下k8s上volum ...
- 容器编排系统K8s之StatefulSet控制器
前文我们聊到了k8s的configmap和secret资源的说明和相关使用示例,回顾请参考:https://www.cnblogs.com/qiuhom-1874/p/14194944.html:今天 ...
- 容器编排系统K8s之访问控制--用户认证
前文我们聊到了k8s的statefulset控制器相关使用说明,回顾请参考:https://www.cnblogs.com/qiuhom-1874/p/14201103.html:今天我们来聊一下k8 ...
- 容器编排系统K8s之访问控制--RBAC授权
前文我们了解了k8s上的访问控制机制,主要对访问控制中的第一关用户认证做了相关说明以及常规用户的配置文件的制作,回顾请参考:https://www.cnblogs.com/qiuhom-1874/p/ ...
- 容器编排系统K8s之访问控制--准入控制
前文我们聊到了k8s的访问控制第二关RBAC授权插件的相关话题,回顾请参考:https://www.cnblogs.com/qiuhom-1874/p/14216634.html:今天我们来聊一下k8 ...
随机推荐
- RabbitMQ Go客户端教程5——topic
本文翻译自RabbitMQ官网的Go语言客户端系列教程,本文首发于我的个人博客:liwenzhou.com,教程共分为六篇,本文是第五篇--topic. 这些教程涵盖了使用RabbitMQ创建消息传递 ...
- 通过Dbeaver创建表格的时候,设置主键
通过Dbeaver创建表格的时候,设置主键 Dbeaver介绍: 这是一个开源的数据库连接工具,你需要安装jre才可以使用这个软件 在使用Dbeaver创建表的时候,会发现,不能直观地设置主键 这 ...
- 第6.5节 exec函数:一个自说自话的强大Python动态编译器
在Python动态执行的函数中,exec是用于执行一个字符串内包含的Python源码或其编译后对应的字节码. 一. 语法 1. exec(Code, globals=None, local ...
- Python中import模块时报SyntaxError: (unicode error)utf-8 codec can not decode 错误的解决办法
老猿有个通过UE编辑(其他文本编辑器一样有类似问题)的bmi.py文件,在Python Idle环境打开文件执行时没有问题,但import时报错: SyntaxError: (unicode erro ...
- 第二章、PyQt5应用构建详细过程介绍
老猿Python博文目录 老猿Python博客地址 一.引言 在上节<第一章.PyQt的简介.安装与配置>介绍了PyQt5及其安装和配置过程,本节将编写一个简单的PyQt5应用,介绍基本的 ...
- flask中migrate和scipt进行连用
近期态度消极了,并且还忙着学php,所以可能flask框架的进度不会像之前那么快了.但是还是要保证跟之前高的质量滴.
- 小程序map地图点击makert放大效果和点击放大地图
WXML文件和JS文件代码在下方 <view class='map'> <map id="map" longitude="{{location.lng} ...
- js 二分查找
二分查找也叫对折查找,对于一个从小到大的有序数组,想要在数组中找到某个值,依次对折查找,小于就在从左边开始,大于就从右边开始,再判断对折后当前的那个索引的值和需要查找的值对比,如果小则high-1,小 ...
- 【题解】「SP34013」SEUG - Seetha’s Unique Game
这道题一看就是 贪心 . 使放的石头少,就需要石头大. 那么就可以将石头重量排序,从大到小. 这道题里面看似东西很多,但是很多东西都是没有用的.比如说:箱子的长和宽,因为题目中说「每加一个石头,水的高 ...
- Mongdb优化
1.索引1)基础索引--为集合colt1的x列创建升序基础索引# cd /usr/local/mongodb4.2.2/bin# ./mongo -uroot -p> use db_test&g ...
