Python Ethical Hacking - Malware Packaging(2)
PACKAGING FOR WINDOWS FROM LINUX
- For best results package the program from the same OS as the target.
- EG if the target is Windows then package the program from a Windows computer with a python interpreter.
- Install Windows python interpreter on Linux.
- Use it to convert python programs to Windows executables.
Install wine tool on Kali Linux:
dpkg --add-architecture i386 && apt-get update &&
apt-get install wine32
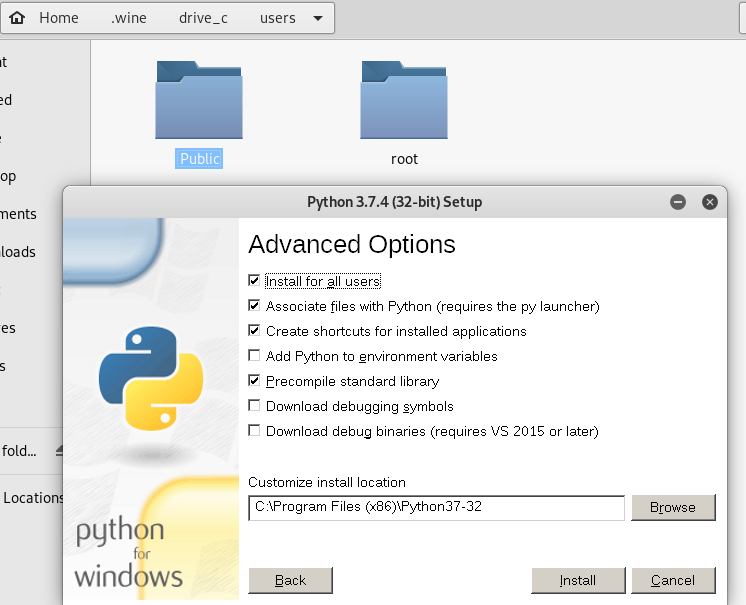
Install Python 3.7.4 using wine.
Install PyInstaller on Kali Linux.
wine python.exe -m pip install /root/Downloads/PyInstaller-3.5.tar.gz

To package the keylogger program, we need to install the pynput module first.
wine python.exe -m pip --default-time= install pynput
Convert the python program to windows executable.
wine ~/.wine/drive_c/'Program Files (x86)'/Python37-/Scripts/pyinstaller.exe zkeylogger.py --onefile --noconsole


Test the zkeylogger.exe file on the Windows 10 PC. It works perfectly.

Python Ethical Hacking - Malware Packaging(2)的更多相关文章
- Python Ethical Hacking - Malware Packaging(1)
PACKAGING Convert python program into an executable that: Packages all program files into a single e ...
- Python Ethical Hacking - Malware Packaging(4)
Converting Python Programs to Linux Executables Note: You can not execute the program on Linux by do ...
- Python Ethical Hacking - Malware Packaging(3)
Convert Python Programs to OS X Executables https://files.pythonhosted.org/packages/4a/08/6ca123073a ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE Download files on a system. Once packaged properly will work on all operating systems. ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- SFTP协议生成公共秘钥文件
[步骤] 1 ssh方式登录服务器 2 执行命令生成秘钥对 ssh-keygen -t rsa 然后给秘钥文件命名 3.查看当前目录的.ssh目录是否有authorized_keys文件 如果有则把新 ...
- 北京开发票/v电13543443967
关于事项:Iㄋ5一★4З44一★ㄋ9.б7开发票的准备资料必须要公司名称个人的话就用个人名字和身份证去税务柜台申请办理!公司的话要提供公司全称就是营业执照上的名称,纳税人税号,如果是开普通增值税发票的 ...
- Java CRC16 MODBUS校验算法实现
/** * CRC校验算法工具类 */ public class CRCUtil { public static String getCRC(String data) { data = data.re ...
- mybatis视频教程2-动态参数
/MyBatis_04_DynamicSQL/src/com/atguigu/mybatis/dao/EmployeeMapperDynamicSQL.java package com.atguigu ...
- mysql性能优化总结(MySql避免重复插入记录的几种方法)
如果我们创建了(area, age,salary)的复合索引,那么其实相当于创建了:(area,age,salary),(area,age).(area)三个索引,这被称为最佳左前缀特性.因此我们在创 ...
- Spring IoC component-scan 节点详解
前言 我们在了解 Spring 容器的扩展功能 (ApplicationContext) 之前,先介绍下 context:component-scan 标签的解析过程,其作用很大是注解能生效的关键所在 ...
- Navicat15安装激活版教程
navicat15安装 一键式安装,安装包如下 链接:https://pan.baidu.com/s/1VTJmJ7ulUySWoWBu-fugiw 提取码:fz5u 先安装软件包点击安装,一直下一步 ...
- tableau入门学习笔记--分页功能
最近在使用tableau来制作报表,对于tableau也是第一次接触并使用,每天学习些新的功能来记录在博客里,给他人方便,也给自己方便 tableau分页功能 很多时候由于工作表过长而出现拖拽条,如果 ...
- js的几个小问题
1.存一个有效期为7天的cookie,key = nickname, val = Ace 代码: function setCookie(key,val,expires){ let now=new Da ...
- Linux中清空docker容器日志
新建文件docker-clear-log,放在/usr/local/bin/目录下,文件内容如下: #!/bin/bash -e if [[ -z $ ]]; then echo "No c ...
