uva 1339
Ancient Roman empire had a strong government system with various departments, including a secret service department. Important documents were sent between provinces and the capital in encrypted form to prevent eavesdropping. The most popular ciphers in those times were so called substitution cipher and permutation cipher. Substitution cipher changes all occurrences of each letter to some other letter. Substitutes for all letters must be different. For some letters substitute letter may coincide with the original letter. For example, applying substitution cipher that changes all letters from `A' to `Y' to the next ones in the alphabet, and changes `Z' to `A', to the message ``VICTORIOUS'' one gets the message ``WJDUPSJPVT''. Permutation cipher applies some permutation to the letters of the message. For example, applying the permutation  2, 1, 5, 4, 3, 7, 6, 10, 9, 8
2, 1, 5, 4, 3, 7, 6, 10, 9, 8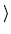 to the message ``VICTORIOUS'' one gets the message ``IVOTCIRSUO''. It was quickly noticed that being applied separately, both substitution cipher and permutation cipher were rather weak. But when being combined, they were strong enough for those times. Thus, the most important messages were first encrypted using substitution cipher, and then the result was encrypted using permutation cipher. Encrypting the message ``VICTORIOUS'' with the combination of the ciphers described above one gets the message ``JWPUDJSTVP''. Archeologists have recently found the message engraved on a stone plate. At the first glance it seemed completely meaningless, so it was suggested that the message was encrypted with some substitution and permutation ciphers. They have conjectured the possible text of the original message that was encrypted, and now they want to check their conjecture. They need a computer program to do it, so you have to write one.
to the message ``VICTORIOUS'' one gets the message ``IVOTCIRSUO''. It was quickly noticed that being applied separately, both substitution cipher and permutation cipher were rather weak. But when being combined, they were strong enough for those times. Thus, the most important messages were first encrypted using substitution cipher, and then the result was encrypted using permutation cipher. Encrypting the message ``VICTORIOUS'' with the combination of the ciphers described above one gets the message ``JWPUDJSTVP''. Archeologists have recently found the message engraved on a stone plate. At the first glance it seemed completely meaningless, so it was suggested that the message was encrypted with some substitution and permutation ciphers. They have conjectured the possible text of the original message that was encrypted, and now they want to check their conjecture. They need a computer program to do it, so you have to write one.
Input
Input file contains several test cases. Each of them consists of two lines. The first line contains the message engraved on the plate. Before encrypting, all spaces and punctuation marks were removed, so the encrypted message contains only capital letters of the English alphabet. The second line contains the original message that is conjectured to be encrypted in the message on the first line. It also contains only capital letters of the English alphabet. The lengths of both lines of the input file are equal and do not exceed 100.
Output
For each test case, print one output line. Output `YES' if the message on the first line of the input file could be the result of encrypting the message on the second line, or `NO' in the other case.
Sample Input
JWPUDJSTVP
VICTORIOUS
MAMA
ROME
HAHA
HEHE
AAA
AAA
NEERCISTHEBEST
SECRETMESSAGES
Sample Output
YES
NO
YES
YES
NO 将字符串输入进去后,用sort排序,再用两个数组将各个字母的个数存进数组里。再对比两个数组的数字是否完全一样。。。
#include <iostream>
#include <cstdio>
#include <cstring>
#include <algorithm>
using namespace std; const int MAXN = ; int main()
{
char str1[MAXN], str2[MAXN];
int a[], b[];
while(scanf("%s%*c", str1) != EOF)
{
scanf("%s%*c", str2); memset(a, , sizeof(a));
memset(b, , sizeof(b)); int len = strlen(str1);
sort(str1, str1+len);
sort(str2, str2+len); for(int i = ; i < len; ++i)
{
a[str1[i] - 'A']++;
b[str2[i] - 'A']++;
} sort(a, a+);
sort(b, b+); int mark = ;
for(int i = ; i < ; ++i)
{
if(a[i] == b[i])
{
mark++;
//printf("%d %d %d", a[i], b[i], mark);
}
}
//printf("%d\n", mark);
if(mark == )
printf("YES\n");
else
printf("NO\n");
}
return ;
}
uva 1339的更多相关文章
- UVa 1339 Ancient Cipher --- 水题
UVa 1339 题目大意:给定两个长度相同且不超过100个字符的字符串,判断能否把其中一个字符串重排后,然后对26个字母一一做一个映射,使得两个字符串相同 解题思路:字母可以重排,那么次序便不重要, ...
- UVa 1339,紫书P73,词频
题目链接:https://uva.onlinejudge.org/external/13/1339.pdf 紫书P73 解题报告: #include <stdio.h> #include ...
- uva 1339 Ancient Cipher
大意:读入两个字符串(都是大写字母),字符串中字母的顺序可以随便排列.现在希望有一种字母到字母的一一映射,从而使得一个字符串可以转换成另一个字符串(字母可以随便排列)有,输出YES:否,输出NO:ex ...
- 【例题 4-1 UVA - 1339】 Ancient Cipher
[链接] 我是链接,点我呀:) [题意] 在这里输入题意 [题解] 位置其实都没关系了. 只要每个字母都有对应的字母,它们的数量相同就可以了. 求出每种字母的数量. 排序之后. 肯定是要一一对应的. ...
- Ancient Cipher UVA - 1339
Ancient Roman empire had a strong government system with various departments, including a secret s ...
- uva 1354 Mobile Computing ——yhx
aaarticlea/png;base64,iVBORw0KGgoAAAANSUhEUgAABGcAAANuCAYAAAC7f2QuAAAgAElEQVR4nOy9XUhjWbo3vu72RRgkF5
- UVA 10564 Paths through the Hourglass[DP 打印]
UVA - 10564 Paths through the Hourglass 题意: 要求从第一层走到最下面一层,只能往左下或右下走 问有多少条路径之和刚好等于S? 如果有的话,输出字典序最小的路径 ...
- UVA 11404 Palindromic Subsequence[DP LCS 打印]
UVA - 11404 Palindromic Subsequence 题意:一个字符串,删去0个或多个字符,输出字典序最小且最长的回文字符串 不要求路径区间DP都可以做 然而要字典序最小 倒过来求L ...
- UVA&&POJ离散概率与数学期望入门练习[4]
POJ3869 Headshot 题意:给出左轮手枪的子弹序列,打了一枪没子弹,要使下一枪也没子弹概率最大应该rotate还是shoot 条件概率,|00|/(|00|+|01|)和|0|/n谁大的问 ...
随机推荐
- Vi 的基本使用
一.Vi入门 Unix 提供了全屏幕的Vi编辑器,这使我们的工作轻松不少.不少DOS用户抱怨Vi编辑器不象DOS下的编辑器如edit那么好用,这 是因为Vi考虑到各种用户的需要,没有使用某些通用的编 ...
- html练习
border-left:100px solid transparent; 左边框隐藏 transform:rotate(45deg); div旋转45度 用css做一个三角形 <sty ...
- 设计模式学习之迭代器模式(Iterator,行为型模式)(17)
参考地址:http://www.cnblogs.com/zhili/p/IteratorPattern.html 一.介绍迭代器是针对集合对象而生的,对于集合对象而言,必然涉及到集合元素的添加删除操作 ...
- 使用RMAN DUPLICATE...FROM ACTIVE DATABASE创建物理standby database
Applies to: Oracle Server - Enterprise Edition - Version 11.1.0.6 to 11.2.0.4 [Release 11.1 to 11.2] ...
- java创建线程的几种方式
1.继承Thread类 /** * @author Ash * @date: 2016年8月6日 下午10:56:45 * @func: 通过继承Thread类来实现多线程 * @email 4086 ...
- BZOJ1004 [HNOI2008]Cards(Polya计数)
枚举每个置换,求在每个置换下着色不变的方法数,先求出每个循环的大小,再动态规划求得使用给定的颜色时对应的方法数. dp[i][j][k]表示处理到当前圈时R,B,G使用量为i,j,k时的方法数,背包思 ...
- 无法定位程序输入点 _glutCreateWindowWithExit于动态链接库glut32.dll上
程序运行提示错误"无法定位程序输入点 _glutCreateWindowWithExit于动态链接库glut32.dll上",网上查了说是opengl的.lib和.dll版本过低, ...
- 数字信号处理实验(五)——IIR滤波器的设计
一.使用自编函数设计IIR滤波器 1.冲激响应法 (1)注给出的数字滤波器指标先化成模拟指标 (2)设计出模拟滤波器: (3)使用冲激响应法转化成数字滤波器 (4)一个demo clear all; ...
- 智能车学习(三)—— ADC学习
一.代码分享: 1.ADC头文件 #ifndef ADC_H_ #define ADC_H_ #include "common.h" typedef enum { // ----- ...
- Servlet的request应用案例
request部分用法如代码: AServlet package cn.yzu; import java.io.IOException; import javax.servlet.ServletExc ...
