k8s之Dashboard插件部署及使用
k8s之Dashboard插件部署及使用
1. Dashboard介绍
Dashboard(仪表盘)是基于Web的Kubernetes用户界面。
可以使用仪表盘将容器化应用程序部署到Kubernetes集群,对容器化应用程序进行故障排除,并管理集群本身机器伴随资源。
可以使用仪表盘来概述集群上运行的应用程序,以及创建或修改单个Kubernetes资源(例如部署,作业,守护进程等)。
例如:可以使用部署向导扩展部署,启动滚动更新,重新启动Pod或部署新应用程序。仪表盘还提供有关集群中Kubernetes资源状态以及可能发生的任何错误的信息。
2. 服务器环境
本次部署环境为k8s多Master节点
3. 在K8S工具目录中创建dashboard工作目录
[root@master01 ~]# mkdir /opt/k8s/dashboard[root@master01 ~]# cd !$cd /opt/k8s/dashboard[root@master01 dashboard]# rz -E#上传Dashboard.zip压缩包rz waiting to receive.[root@master01 dashboard]# unzip Dashboard.zip#解压Archive: Dashboard.zipinflating: dashboard-configmap.yamlinflating: dashboard-controller.yamlinflating: dashboard-rbac.yamlinflating: dashboard-secret.yamlinflating: dashboard-service.yamlinflating: k8s-admin.yamlinflating: dashboard-cert.sh[root@master01 dashboard]# lsdashboard-cert.sh dashboard-controller.yaml dashboard-secret.yaml Dashboard.zipdashboard-configmap.yaml dashboard-rbac.yaml dashboard-service.yaml k8s-admin.yaml
4. 核心文件说明
| 核心文件 | 说明 |
|---|---|
| dashboard-rbac.yaml | 用于访问控制设置,配置各种角色的访问控制权限及角色绑定(绑定角色和服务账户),内容中包含对应各种角色所配置的规则(rules) |
| dashboard-secret.yaml | 提供令牌,访问API服务器所用(个人理解为一种安全认证机制) |
| dashboard-configmap.yaml | 配置模板文件,负责设置Dashboard的文件,ConfigMap提供了将配置数据注入容器的方式,保证容器中的应用程序配置从Image内容中解耦 |
| dashboard-controller.yaml | 负责控制器即服务账户的创建,来管理pod副本 |
| dashboard-service.yaml | 负责将容器中的服务提供出去,供外部访问 |
| Dashboard一共有7个文件,其中包含5个构建该界面的核心文件,一个k8s-admin.yaml文件是自己写的,用来生成待会在浏览器中登录时所用的令牌;一个dashboard-cert.sh,用来快速生成解决谷歌浏览器加密通信所需的证书文件。 | |
| 核心文件官方下载资源地址:https://github.com/kubernetes/kubernetes/tree/master/cluster/addons/dashboard |
4.1 查看dashboard-rbac.yaml
[root@master01 dashboard]# cat dashboard-rbac.yamlkind: RoleapiVersion: rbac.authorization.k8s.io/v1metadata:labels:k8s-app: kubernetes-dashboardaddonmanager.kubernetes.io/mode: Reconcilename: kubernetes-dashboard-minimalnamespace: kube-systemrules:# Allow Dashboard to get, update and delete Dashboard exclusive secrets.- apiGroups: [""]resources: ["secrets"]resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"]verbs: ["get", "update", "delete"]# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.- apiGroups: [""]resources: ["configmaps"]resourceNames: ["kubernetes-dashboard-settings"]verbs: ["get", "update"]# Allow Dashboard to get metrics from heapster.- apiGroups: [""]resources: ["services"]resourceNames: ["heapster"]verbs: ["proxy"]- apiGroups: [""]resources: ["services/proxy"]resourceNames: ["heapster", "http:heapster:", "https:heapster:"]verbs: ["get"]---apiVersion: rbac.authorization.k8s.io/v1kind: RoleBindingmetadata:name: kubernetes-dashboard-minimalnamespace: kube-systemlabels:k8s-app: kubernetes-dashboardaddonmanager.kubernetes.io/mode: ReconcileroleRef:apiGroup: rbac.authorization.k8s.iokind: Rolename: kubernetes-dashboard-minimalsubjects:- kind: ServiceAccountname: kubernetes-dashboardnamespace: kube-system#主要参数说明:#kind: ServiceAccount 创建service用户,k8s中有两种用户,一种是ServiceAccount(给集群中的pod来访问集群用的),还有一种是具体的user(给咱们用户使用)#metadata 创建资源对象的一些元数据#labels 标签信息#name 资源对象名称#namespace 命令空间#kind: ClusterRoleBinding 创建用于集群绑定的角色,可以帮ServiceAccount绑定到具体的角色中、组中,使它有相应的访问权限#kind: ClusterRole k8s中有两种角色,一种是ClusterRole(针对于整个集群的命名空间都起作用),还有一种是普通的角色(只对单个命名空间起作用)
4.2 查看dashboard-secret.yaml
[root@master01 dashboard]# cat dashboard-secret.yamlapiVersion: v1kind: Secretmetadata:labels:k8s-app: kubernetes-dashboard# Allows editing resource and makes sure it is created first.addonmanager.kubernetes.io/mode: EnsureExistsname: kubernetes-dashboard-certsnamespace: kube-systemtype: Opaque---apiVersion: v1kind: Secretmetadata:labels:k8s-app: kubernetes-dashboard# Allows editing resource and makes sure it is created first.addonmanager.kubernetes.io/mode: EnsureExistsname: kubernetes-dashboard-key-holdernamespace: kube-systemtype: Opaque
4.3 查看dashboard-configmap.yaml
[root@master01 dashboard]# cat dashboard-configmap.yamlapiVersion: v1kind: ConfigMapmetadata:labels:k8s-app: kubernetes-dashboard# Allows editing resource and makes sure it is created first.addonmanager.kubernetes.io/mode: EnsureExistsname: kubernetes-dashboard-settingsnamespace: kube-system
4.4 查看dashboard-controller.yaml
[root@master01 dashboard]# cat dashboard-controller.yamlapiVersion: v1kind: ServiceAccountmetadata:labels:k8s-app: kubernetes-dashboardaddonmanager.kubernetes.io/mode: Reconcilename: kubernetes-dashboardnamespace: kube-system---apiVersion: apps/v1kind: Deploymentmetadata:name: kubernetes-dashboardnamespace: kube-systemlabels:k8s-app: kubernetes-dashboardkubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcilespec:selector:matchLabels:k8s-app: kubernetes-dashboardtemplate:metadata:labels:k8s-app: kubernetes-dashboardannotations:scheduler.alpha.kubernetes.io/critical-pod: ''seccomp.security.alpha.kubernetes.io/pod: 'docker/default'spec:priorityClassName: system-cluster-criticalcontainers:- name: kubernetes-dashboardimage: siriuszg/kubernetes-dashboard-amd64:v1.8.3resources:limits:cpu: 100mmemory: 300Mirequests:cpu: 50mmemory: 100Miports:- containerPort: 8443protocol: TCPargs:# PLATFORM-SPECIFIC ARGS HERE- --auto-generate-certificatesvolumeMounts:- name: kubernetes-dashboard-certsmountPath: /certs- name: tmp-volumemountPath: /tmplivenessProbe:httpGet:scheme: HTTPSpath: /port: 8443initialDelaySeconds: 30timeoutSeconds: 30volumes:- name: kubernetes-dashboard-certssecret:secretName: kubernetes-dashboard-certs- name: tmp-volumeemptyDir: {}serviceAccountName: kubernetes-dashboardtolerations:- key: "CriticalAddonsOnly"operator: "Exists"#主要参数说明:#kind: Deployment 是整个集群中使用最频繁的对象,咱们应用服务一般都是使用Deployment来创建#spec.selector.matchLabels 匹配某个标签#spec.template.spec.serviceAccountName 指定创建的serviceAccount,使用该账户来访问集群#spec.template.spec.containers.resources 对容器使用资源限制#spec.template.spec.containers.ports.containerPort 指定暴露的端口#spec.template.spec.containers.livenessProbe 健康检查#spec.template.spec.containers.livenessProbe.initialDelaySeconds 检查间隔时间设置#spec.template.spec.containers.livenessProbe.timeoutSeconds 检查超时设置
4.5 查看dashboard-service.yaml
[root@master01 dashboard]# cat dashboard-service.yamlapiVersion: v1kind: Servicemetadata:name: kubernetes-dashboardnamespace: kube-systemlabels:k8s-app: kubernetes-dashboardkubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcilespec:type: NodePortselector:k8s-app: kubernetes-dashboardports:- port: 443targetPort: 8443nodePort: 30001#主要参数说明:#type: NodePort 可以通过在节点上使用nodeIP+端口访问服务#spec.ports.port 为service在clusterIP暴露的端口#spec.ports.targetPort 对应容器映射在pod上的端口#spec.ports.nodePort 为nodeIP暴露的端口
4.6 查看k8s-admin.yaml
[root@master01 dashboard]# cat k8s-admin.yamlapiVersion: v1kind: ServiceAccountmetadata:name: dashboard-adminnamespace: kube-system---kind: ClusterRoleBindingapiVersion: rbac.authorization.k8s.io/v1beta1metadata:name: dashboard-adminsubjects:- kind: ServiceAccountname: dashboard-adminnamespace: kube-systemroleRef:kind: ClusterRolename: cluster-adminapiGroup: rbac.authorization.k8s.io
4.7 查看dashboard-cert.sh
[root@master01 dashboard]# cat dashboard-cert.sh#!/bin/bash#examle: ./dashboard-cert.sh /opt/k8s/k8s-cert/cat > dashboard-csr.json <<EOF{"CN": "Dashboard","hosts": [],"key": {"algo": "rsa","size": 2048},"names": [{"C": "CN","L": "BeiJing","ST": "BeiJing"}]}EOF#定义一个变量,使用位置变量赋值,作用是指定你证书(依赖证书)的位置K8S_CA=$1#根据指定位置的证书进行创建和自签操作cfssl gencert -ca=$K8S_CA/ca.pem -ca-key=$K8S_CA/ca-key.pem -config=$K8S_CA/ca-config.json -profile=kubernetes dashboard-csr.json | cfssljson -bare dashboard#生成的文件:#dashboard.csr:证书请求文件#dashboard-key.pem:证书私钥#dashboard.pem:数字签名证书#清空命名空间中的认证kubectl delete secret kubernetes-dashboard-certs -n kube-system#重新创建生成到指定的目录中(当前目录)kubectl create secret generic kubernetes-dashboard-certs --from-file=./ -n kube-system
5. 通过kubectl create命令创建resources
5.1 dashboard-rbac.yaml
规定kubernetes-dashboard-minimal该角色的权限:例如其中具备获取更新删除等不同的权限
[root@master01 dashboard]# kubectl create -f dashboard-rbac.yamlrole.rbac.authorization.k8s.io/kubernetes-dashboard-minimal createdrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created#有几个kind就会有几个结果被创建,格式为kind+apiServer/name
查看类型为Role,RoleBinding的资源对象kubernetes-dashboard-minimal是否生成
[root@master01 dashboard]# kubectl get role,rolebinding -n kube-system#-n kube-system表示查看指定命名空间中的pod,缺省值为defaultNAME AGErole.rbac.authorization.k8s.io/extension-apiserver-authentication-reader 3d8hrole.rbac.authorization.k8s.io/kubernetes-dashboard-minimal 2m42srole.rbac.authorization.k8s.io/system::leader-locking-kube-controller-manager 3d8hrole.rbac.authorization.k8s.io/system::leader-locking-kube-scheduler 3d8hrole.rbac.authorization.k8s.io/system:controller:bootstrap-signer 3d8hrole.rbac.authorization.k8s.io/system:controller:cloud-provider 3d8hrole.rbac.authorization.k8s.io/system:controller:token-cleaner 3d8hNAME AGErolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal 2m42srolebinding.rbac.authorization.k8s.io/system::leader-locking-kube-controller-manager 3d8hrolebinding.rbac.authorization.k8s.io/system::leader-locking-kube-scheduler 3d8hrolebinding.rbac.authorization.k8s.io/system:controller:bootstrap-signer 3d8hrolebinding.rbac.authorization.k8s.io/system:controller:cloud-provider 3d8hrolebinding.rbac.authorization.k8s.io/system:controller:token-cleaner 3d8h
5.2 dashboard-secret.yaml
证书和密钥创建
[root@master01 dashboard]# kubectl create -f dashboard-secret.yamlsecret/kubernetes-dashboard-certs createdsecret/kubernetes-dashboard-key-holder created
查看类型为Secret的资源对象kubernetes-bashboard-crets,kubernetes-dashboard-key-holder是否生成
[root@master01 dashboard]# kubectl get secret -n kube-systemNAME TYPE DATA AGEdefault-token-4nhtx kubernetes.io/service-account-token 3 3d8hkubernetes-dashboard-certs Opaque 0 107skubernetes-dashboard-key-holder Opaque 0 107s
5.3 dashboard-configmap.yaml
配置文件,对于集群dashboard设置的创建
[root@master01 dashboard]# kubectl create -f dashboard-configmap.yamlconfigmap/kubernetes-dashboard-settings created
查看类型为ConfigMap的资源对象kubernetes-dashboard-settings是否生成
[root@master01 dashboard]# kubectl get configmap -n kube-systemNAME DATA AGEextension-apiserver-authentication 1 3d8hkubernetes-dashboard-settings 0 73s
5.4 dashboard-controller.yaml
创建容器需要的控制器以及服务账户
[root@master01 dashboard]# kubectl create -f dashboard-controller.yamlserviceaccount/kubernetes-dashboard createddeployment.apps/kubernetes-dashboard created
查看类型为ServiceAccount,Deployment的资源对象kubernetes-dashboard-setting是否生成
[root@master01 dashboard]# kubectl get serviceaccount,deployment -n kube-systemNAME SECRETS AGEserviceaccount/default 1 3d8hserviceaccount/kubernetes-dashboard 1 2m39sNAME DESIRED CURRENT UP-TO-DATE AVAILABLE AGEdeployment.extensions/kubernetes-dashboard 1 1 1 1 2m39s
5.5 dashboard-service.yaml
将服务发布出去
[root@master01 dashboard]# kubectl create -f dashboard-service.yamlservice/kubernetes-dashboard created
查看创建在指定的kube-system命名空间下的pod和service状态信息
[root@master01 dashboard]# kubectl get pods,svc -n kube-system -o wide#svc为service的缩写,可用NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODEpod/kubernetes-dashboard-65f974f565-nk4r8 1/1 Running 0 5m7s 172.17.97.3 192.168.122.12 <none>NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTORservice/kubernetes-dashboard NodePort 10.0.0.98 <none> 443:30001/TCP 3m37s k8s-app=kubernetes-dashboard
6. 为node节点准备加载dashboard镜像(node节点,以node01为例,该步骤可省略)
为提高速度,我这里已将siriuszg/kubernetes-dashboard-amd64:v1.8.3镜像压缩成tar包,在node节点释放该镜像。
该步骤也可省略,node节点会通过kubernetes公有仓库去自动拉取该镜像。
[root@node01 ~]# cd /opt[root@node01 opt]# rz -E#上传镜像包rz waiting to receive.[root@node01 opt]# docker imagesREPOSITORY TAG IMAGE ID CREATED SIZEnginx latest 87a94228f133 2 weeks ago 133MBcentos 7 eeb6ee3f44bd 6 weeks ago 204MBnginx 1.14 295c7be07902 2 years ago 109MBregistry.cn-hangzhou.aliyuncs.com/google-containers/pause-amd64 3.0 99e59f495ffa 5 years ago 747kB[root@node01 opt]# docker load -i dashboard.tar#载入该镜像23ddb8cbb75a: Loading layer [==================================================>] 102.8MB/102.8MBLoaded image: siriuszg/kubernetes-dashboard-amd64:v1.8.3[root@node01 opt]# docker imagesREPOSITORY TAG IMAGE ID CREATED SIZEnginx latest 87a94228f133 2 weeks ago 133MBcentos 7 eeb6ee3f44bd 6 weeks ago 204MBnginx 1.14 295c7be07902 2 years ago 109MBsiriuszg/kubernetes-dashboard-amd64 v1.8.3 784cf2722f44 3 years ago 102MBregistry.cn-hangzhou.aliyuncs.com/google-containers/pause-amd64 3.0 99e59f495ffa 5 years ago 747kB
7. 访问测试(多浏览器)
不同浏览器的安全访问策略和防护级别是不同的,由于我们没有给dashboard做证书,因此使用不同的浏览器可能会出现不同的效果,本次使用我们最常用的Edge/Chrome、火狐以及360浏览器进行测试。
由于dashboard-service.yaml定义的nodePort: 30001,因此我们的测试地址应该是pod所属node的30001端口。
7.1 Edge浏览器
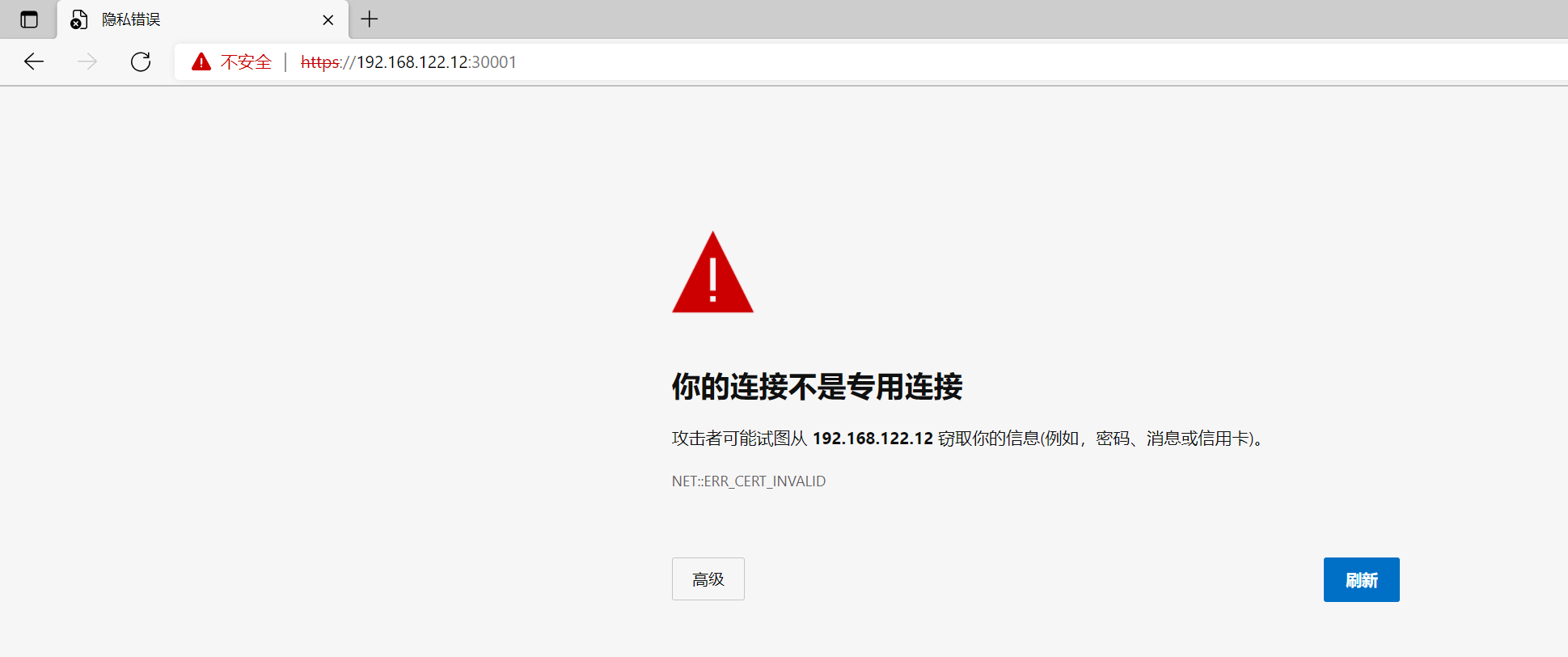
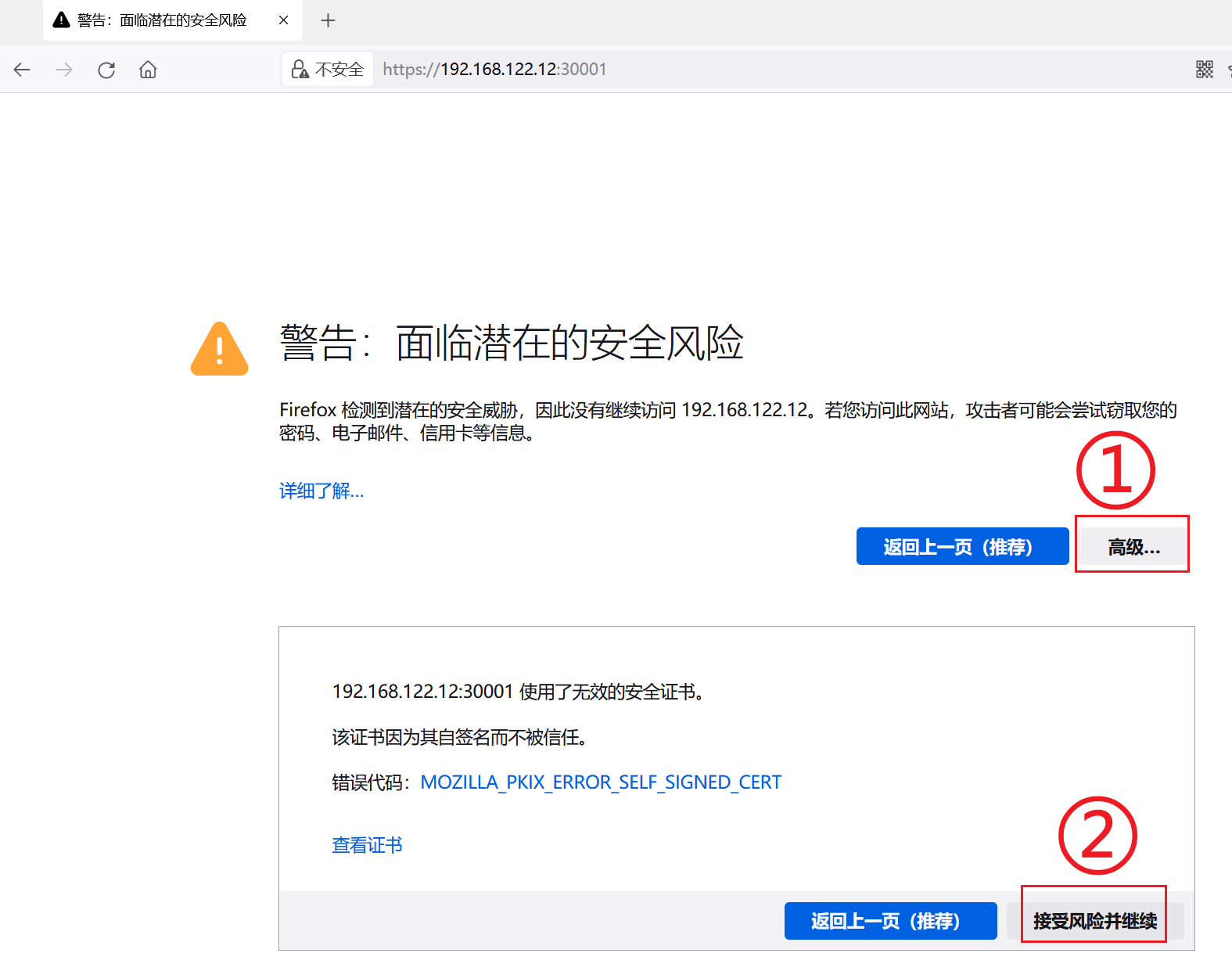
无法访问,由于Edge使用的是Chrome内核,因此Google的Chrome也是相同效果,可通过以下步骤查看问题。
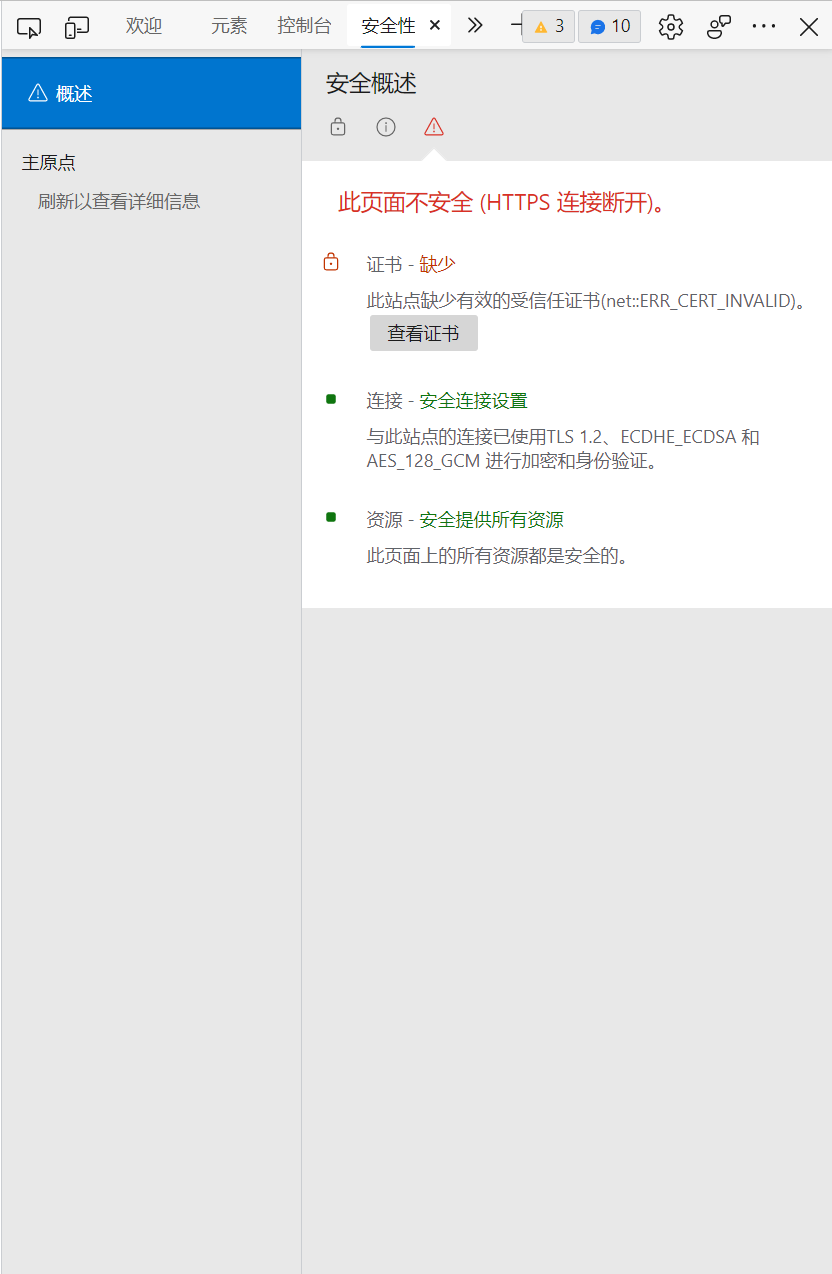
chrome浏览器在Security项下查看
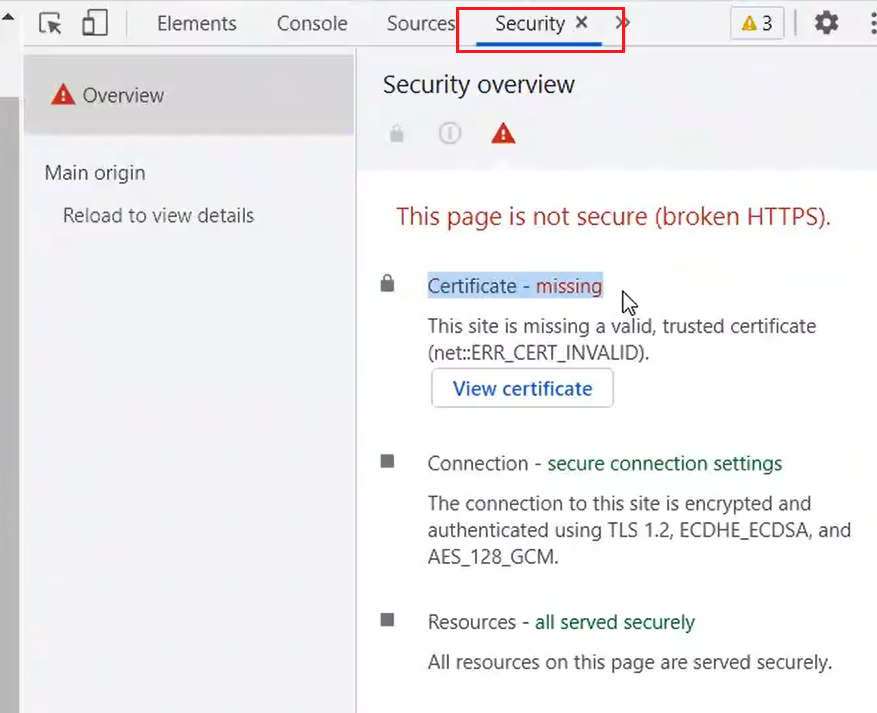
发现问题是缺少证书,那么我们为其制作证书即可。
7.1.1 修改dashbaord-controller.yaml
[root@master01 dashboard]# cd /opt/k8s/dashboard/[root@master01 dashboard]# vim dashboard-controller.yaml......args:# PLATFORM-SPECIFIC ARGS HERE##在文件的第47行下面添加以下两行,指定加密(tls)的私钥和证书文件- --auto-generate-certificates- --tls-key-file=dashboard-key.pem- --tls-cert-file=dashboard.pem
7.1.2 执行脚本dashboard-cret.sh
[root@master01 dashboard]# cd /opt/k8s/dashboard/[root@master01 dashboard]# chmod +x dashboard-cert.sh[root@master01 dashboard]# ./dashboard-cert.sh /opt/k8s/k8s-cert/2021/11/01 02:35:39 [INFO] generate received request2021/11/01 02:35:39 [INFO] received CSR2021/11/01 02:35:39 [INFO] generating key: rsa-20482021/11/01 02:35:39 [INFO] encoded CSR2021/11/01 02:35:39 [INFO] signed certificate with serial number 2335413166532312464921212955081092810633860142272021/11/01 02:35:39 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable forwebsites. For more information see the Baseline Requirements for the Issuance and Managementof Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);specifically, section 10.2.3 ("Information Requirements").secret "kubernetes-dashboard-certs" deletedsecret/kubernetes-dashboard-certs created
7.1.3 在dashboard工作目录下将生成两个证书、
[root@master01 dashboard]# ls *.pemdashboard-key.pem dashboard.pem
7.1.4 重新部署dashboard-controller.yaml
注意:当apply不生效时,先使用delete清除资源,再apply创建资源
[root@master01 dashboard]# kubectl apply -f dashboard-controller.yamlWarning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl applyserviceaccount/kubernetes-dashboard configuredWarning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl applydeployment.apps/kubernetes-dashboard configured
7.1.5 查看分配节点和端口号
由于可能会更换所分配的节点,所以要再次查看一下分配的节点服务器地址和端口号
[root@master01 dashboard]# kubectl get pods,svc -n kube-system -o wideNAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODEpod/kubernetes-dashboard-7dffbccd68-d8nzh 1/1 Running 0 2m39s 172.17.54.4 node01 <none>NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTORservice/kubernetes-dashboard NodePort 10.0.0.98 <none> 443:30001/TCP 149m k8s-app=kubernetes-dashboard
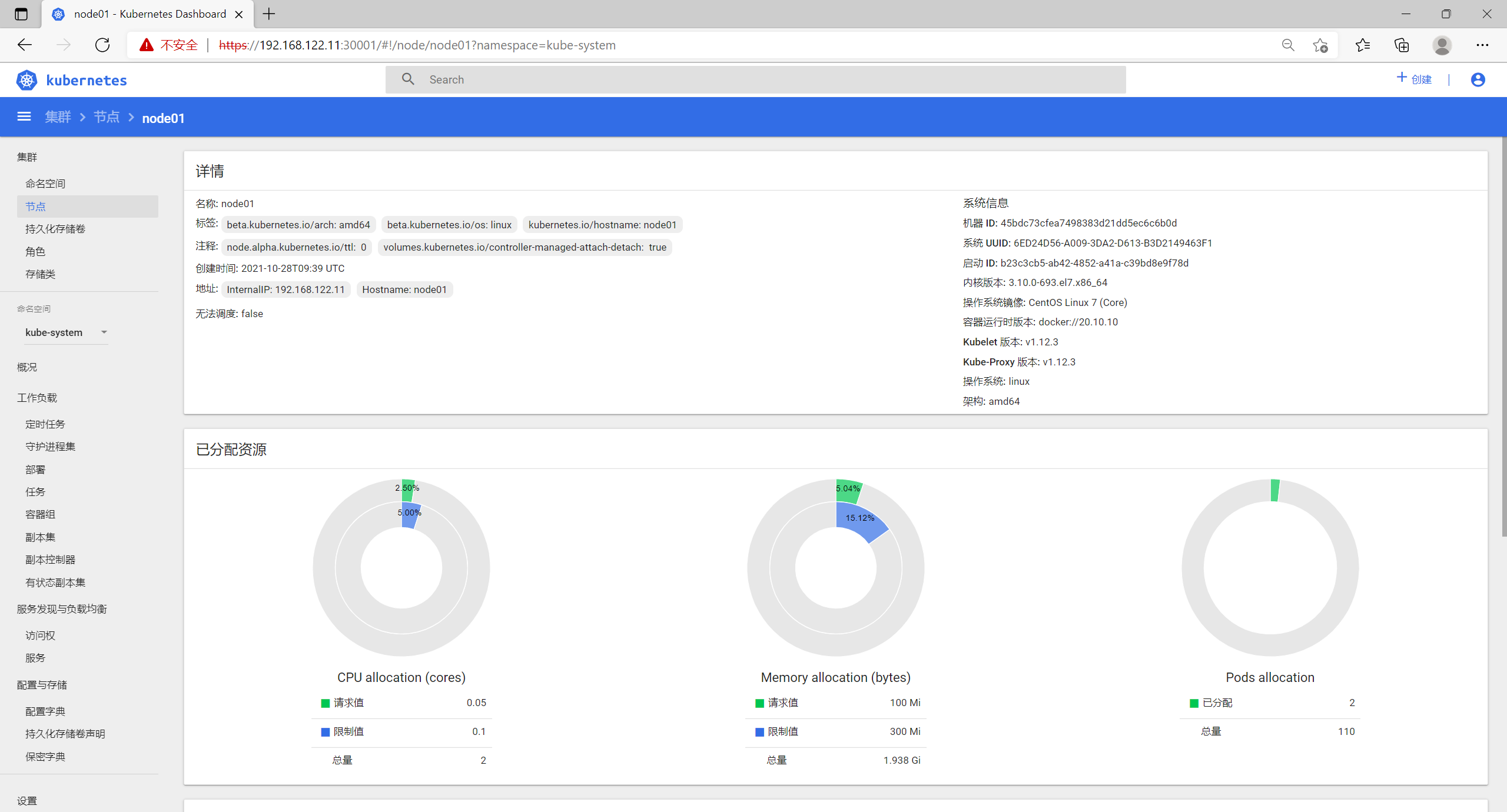
查看发现node节点更换为node1,也就是192.168.122.11。
端口号仍是30001。
7.1.6 访问查看
到此页面,说明可以访问,保持该页面,测试下一个浏览器。
7.2 火狐浏览器
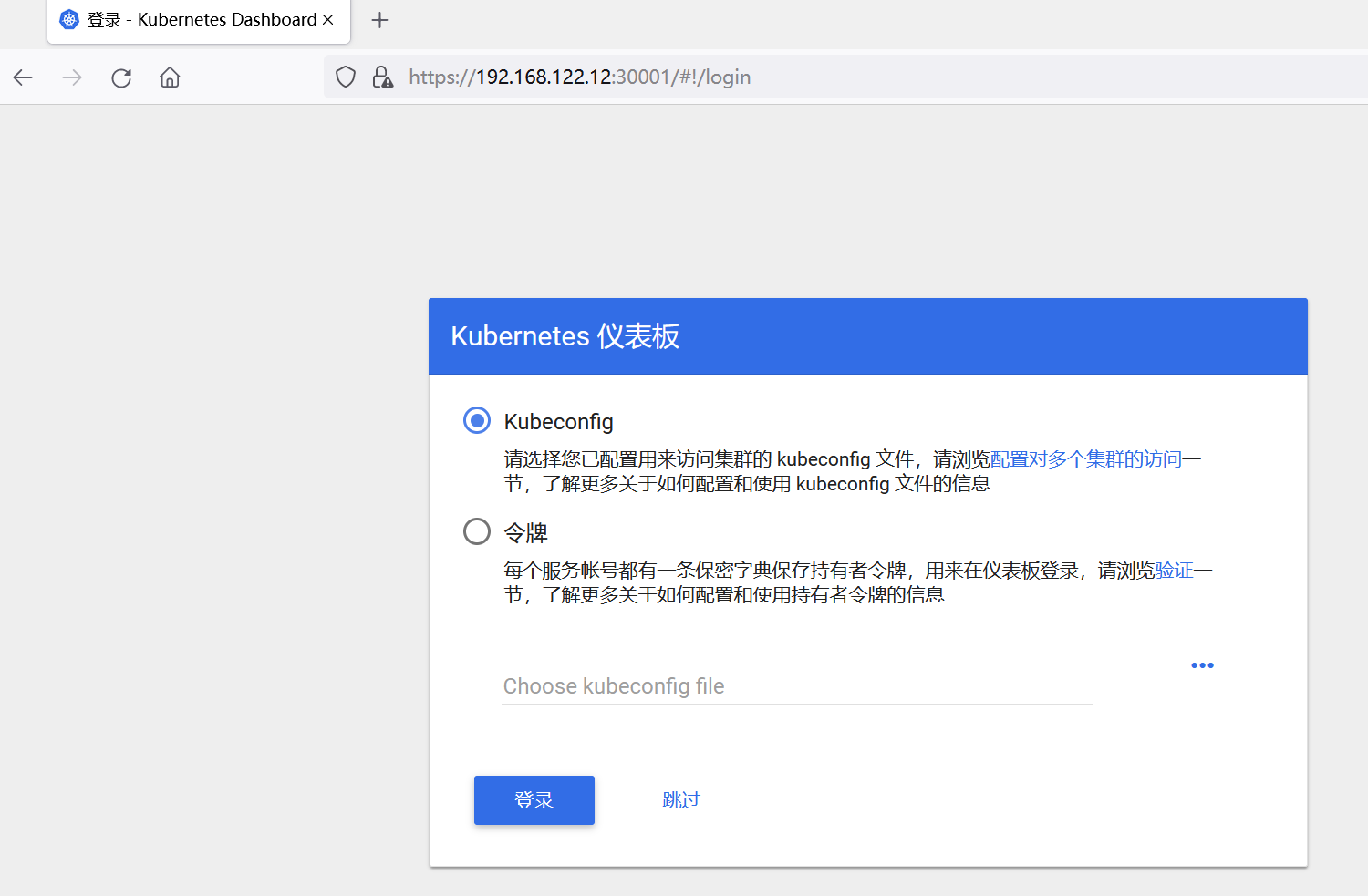
进入该页面,说明可以访问,保持该页面,测试下一个浏览器。
7.3 360浏览器
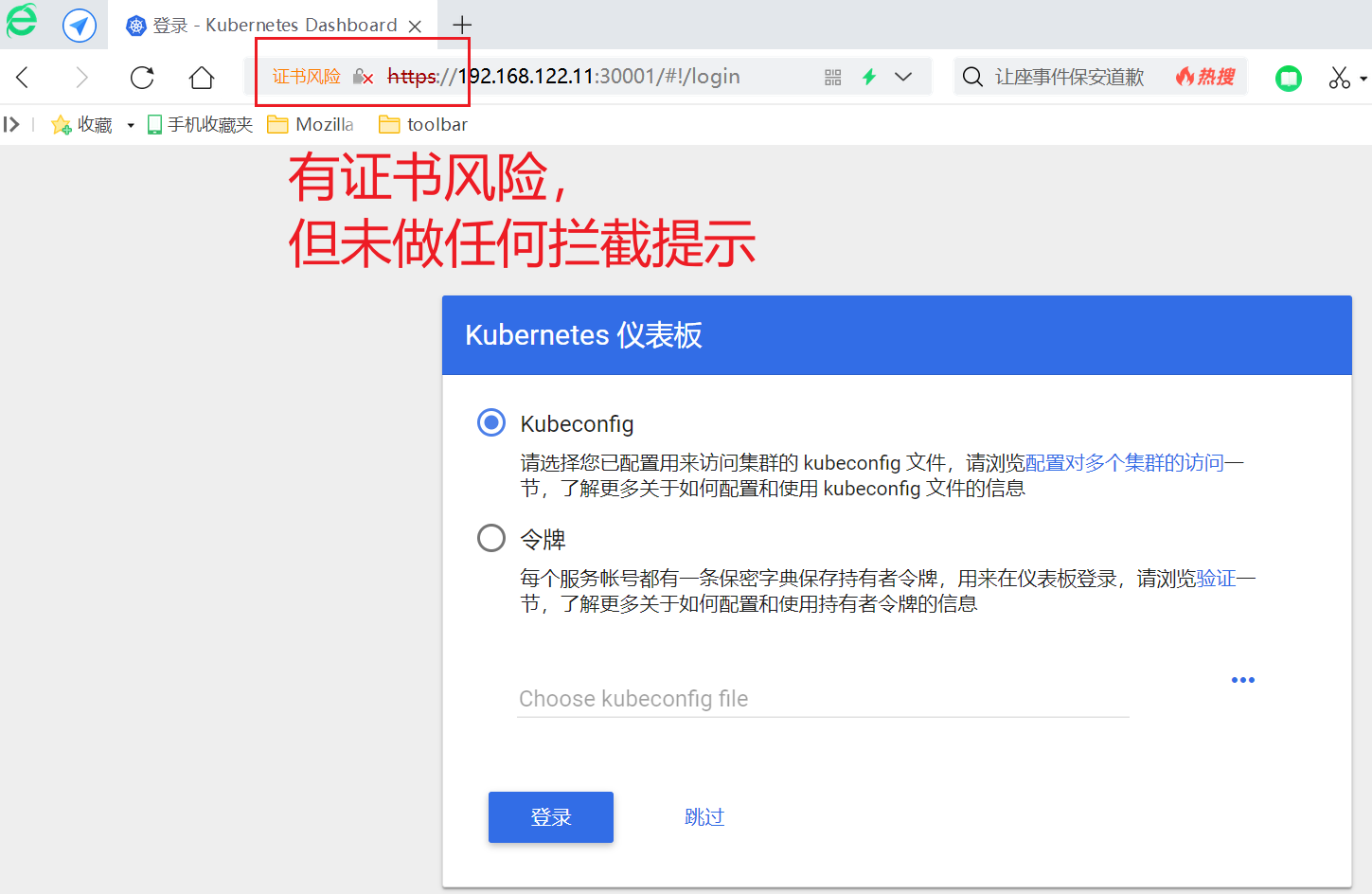
360浏览器虽然显示证书风险,但未出现任何阻止浏览或风险提示窗口,直接可进入登录页面。
7.4 令牌获取
7.4.1 使用k8s-admin.yaml文件进行创建令牌
[root@master01 dashboard]# kubectl create -f k8s-admin.yamlserviceaccount/dashboard-admin createdclusterrolebinding.rbac.authorization.k8s.io/dashboard-admin created
7.4.2 获取token简要信息,名称为dashboard-admin-token-xxxxx
[root@master01 dashboard]# kubectl get secrets -n kube-systemNAME TYPE DATA AGEdashboard-admin-token-n5dcl kubernetes.io/service-account-token 3 86sdefault-token-4nhtx kubernetes.io/service-account-token 3 3d11hkubernetes-dashboard-certs Opaque 11 19mkubernetes-dashboard-key-holder Opaque 2 170mkubernetes-dashboard-token-kkpxs kubernetes.io/service-account-token 3 165m
7.4.3 查看令牌序列号,截取“token:”后面的内容
[root@master01 dashboard]# kubectl describe secrets dashboard-admin-token-n5dcl -n kube-systemName: dashboard-admin-token-n5dclNamespace: kube-systemLabels: <none>Annotations: kubernetes.io/service-account.name: dashboard-adminkubernetes.io/service-account.uid: e3600e3f-3a7b-11ec-adb1-000c2959bebeType: kubernetes.io/service-account-tokenData====ca.crt: 1359 bytesnamespace: 11 bytestoken: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tbjVkY2wiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZTM2MDBlM2YtM2E3Yi0xMWVjLWFkYjEtMDAwYzI5NTliZWJlIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.kCkjHd8bfgecC_sNrsauvkBy7O09dQY7KAbz-2pNnDwEdKNkAR4y7cwC8zCNLsul7uuHVZs5hCp6iGti1EeUUEMoy8cEBlC4WDOxSQdJQzi9RTCSkCHrReql2nGfGpFHx15JkcyB2CY8BBBRaUvIbe6phX5sOmUlJWf5K4FI0sQHYpefH0vYSr8CWWCeccajlDZPEqgLkUpAUMHT2fjhJNfWgbTZDBMEye6nnyQjS92s8qECF1jBgRbIfTZKWHqPRpKmbz9oFKnKlcH2BBgDonpE3cDSfmSTH6SgYDHKQuGAwV_vjIIP_GMxdXmM_ymGZAdcdw9kd0EBCSdOQH8yIw
7.4.5 使用令牌登录dashboard
将令牌序列号复制填入到浏览器页面中,点击登录
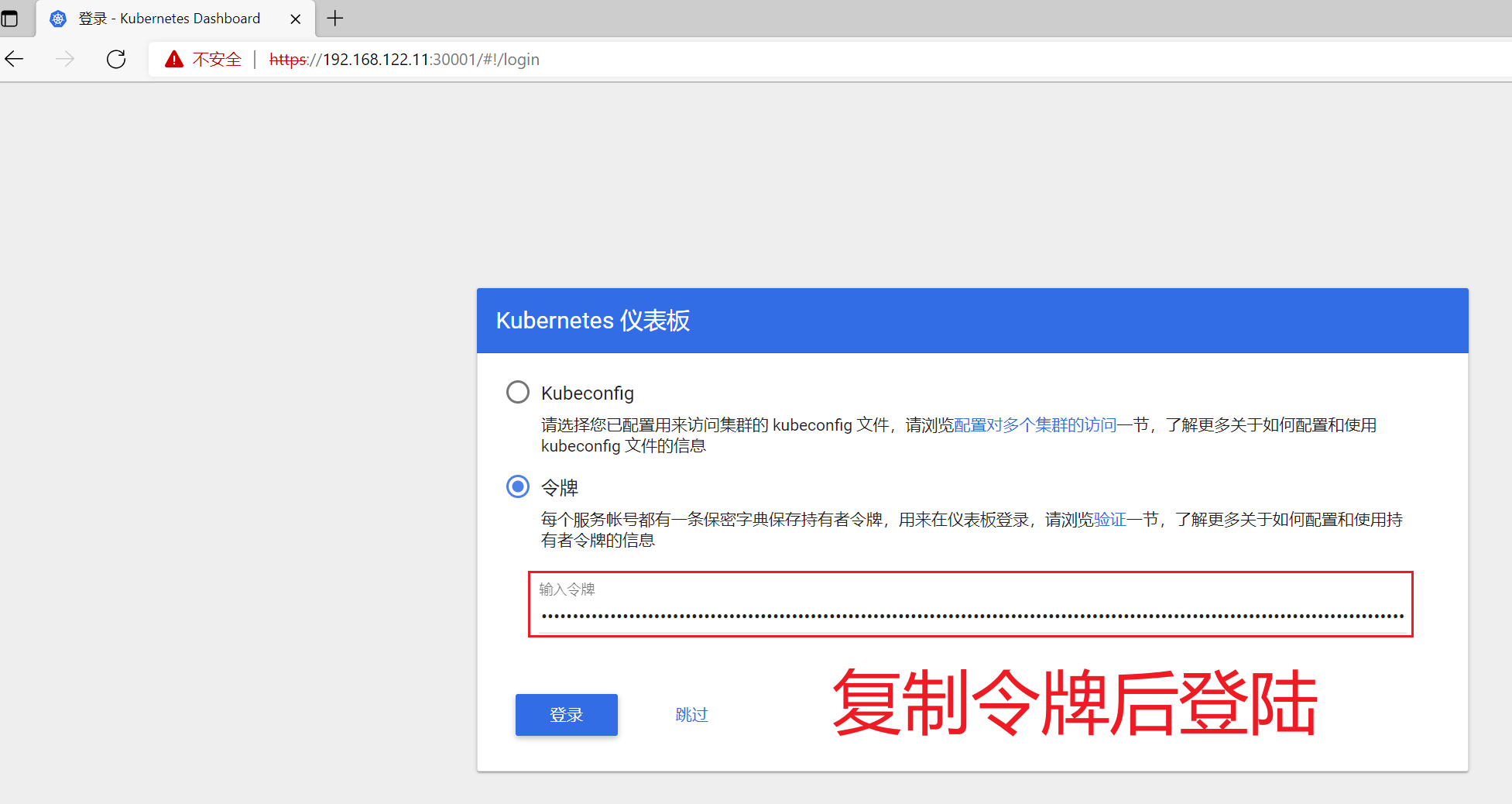
登录成功
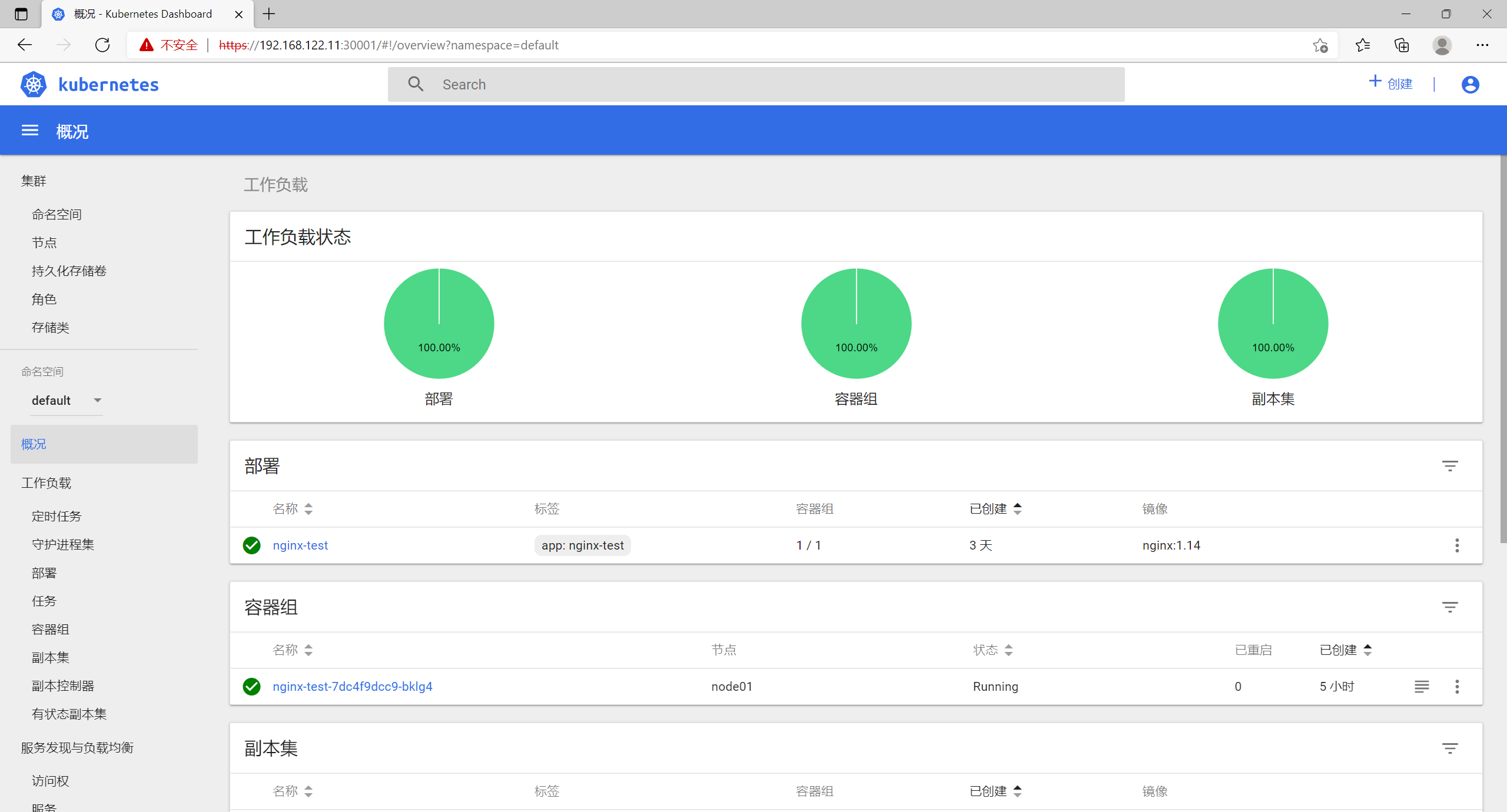
8. dashboard操作
8.1 命名空间
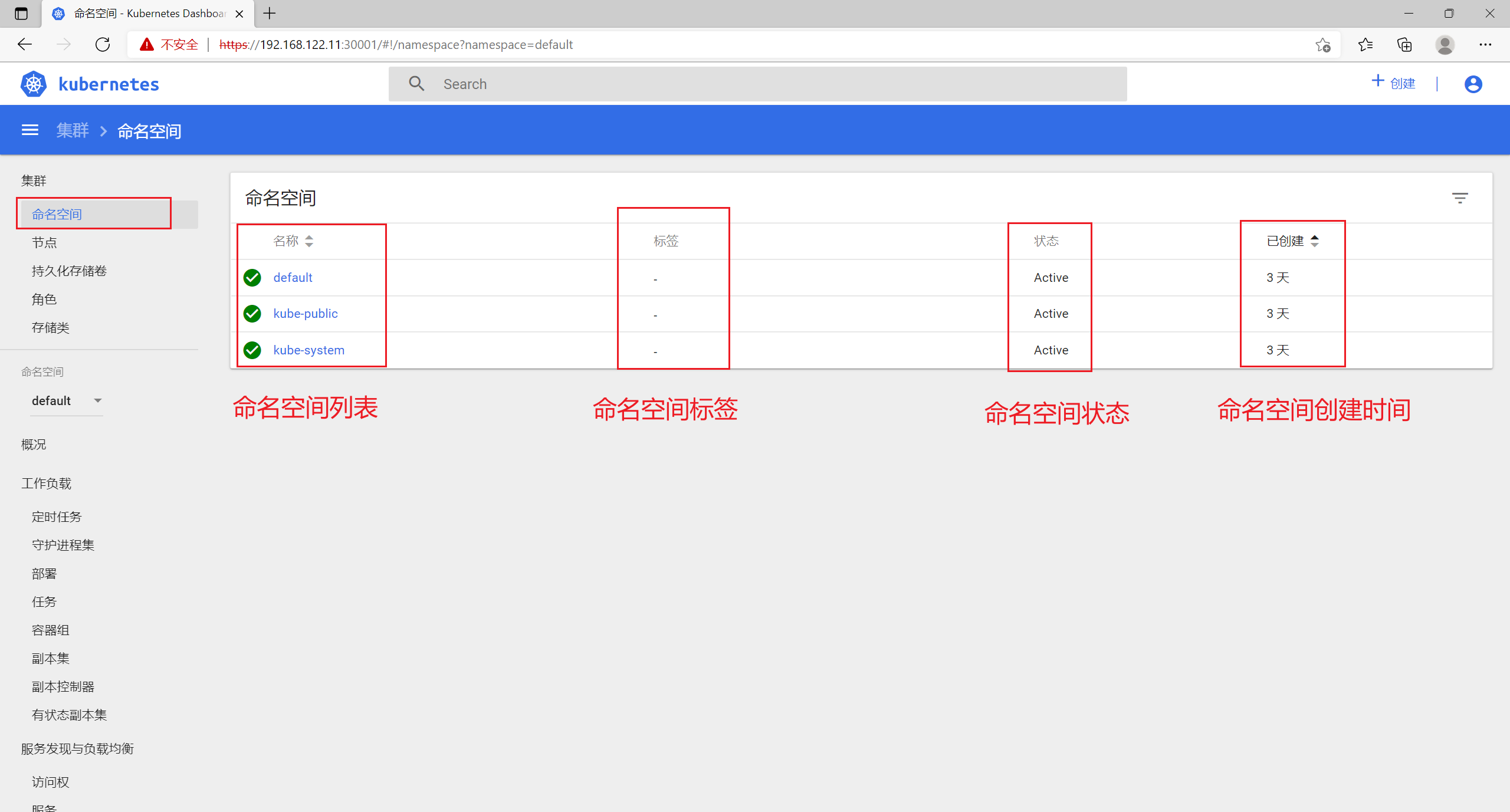
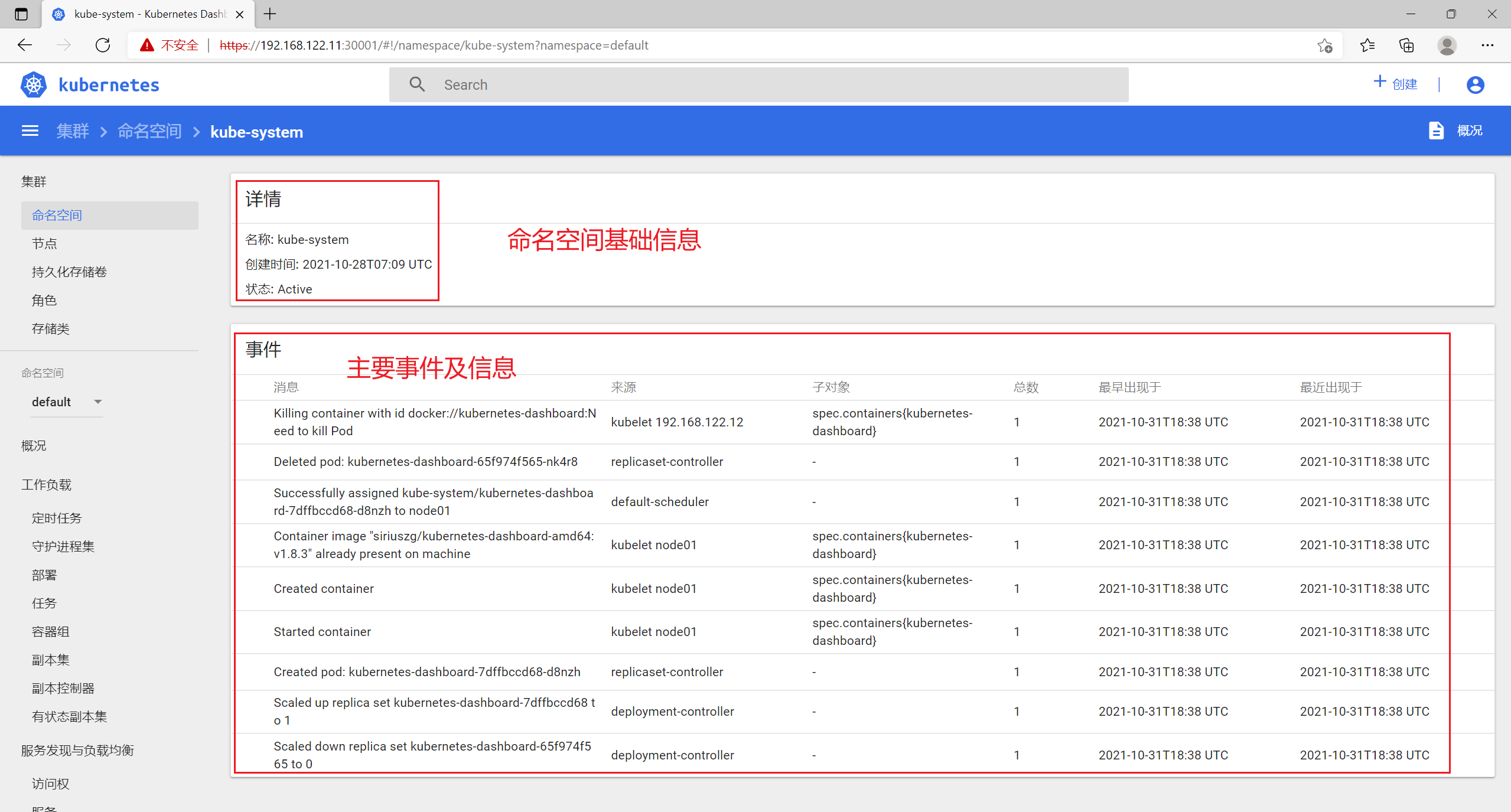
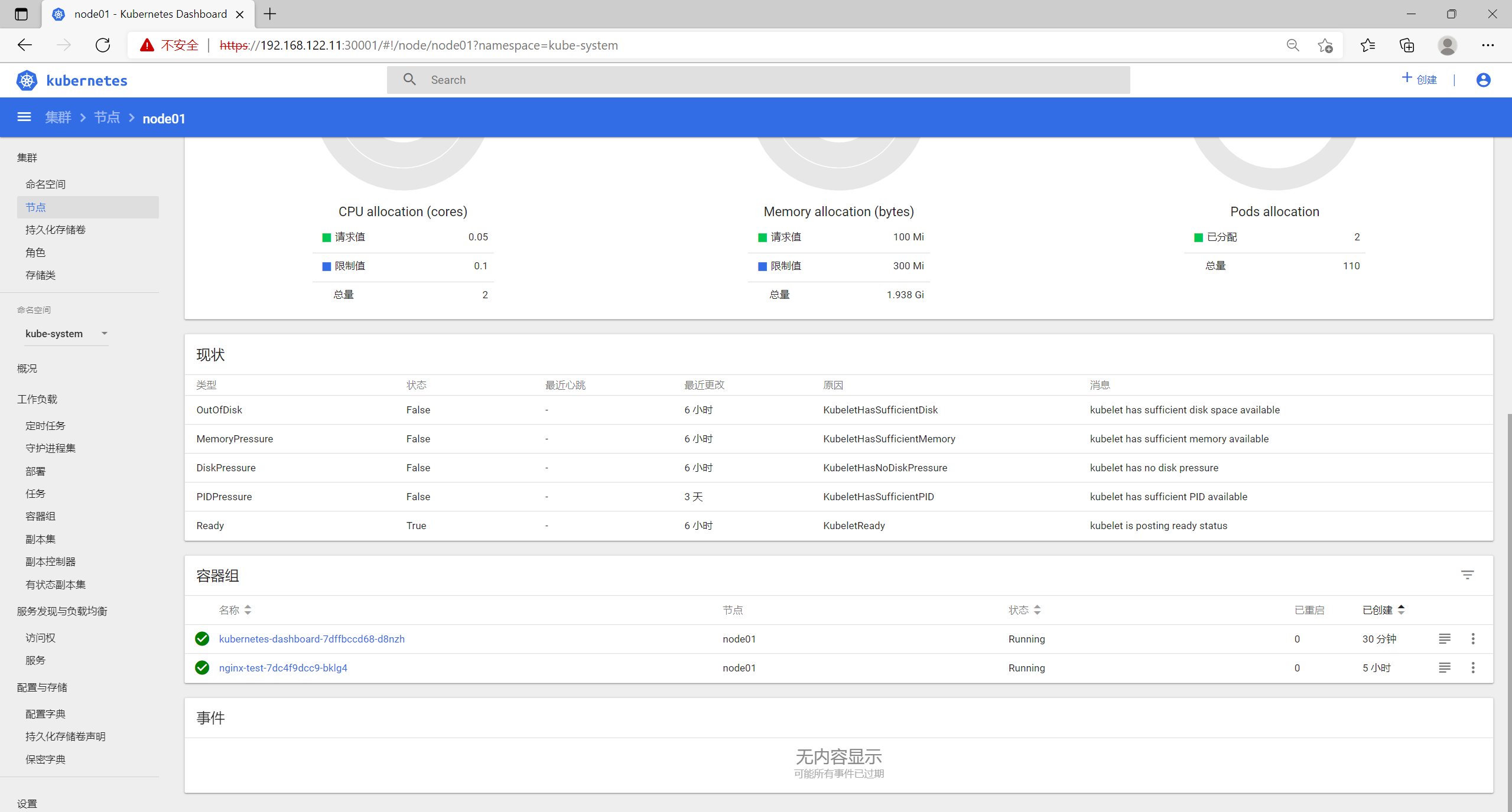
8.2 节点
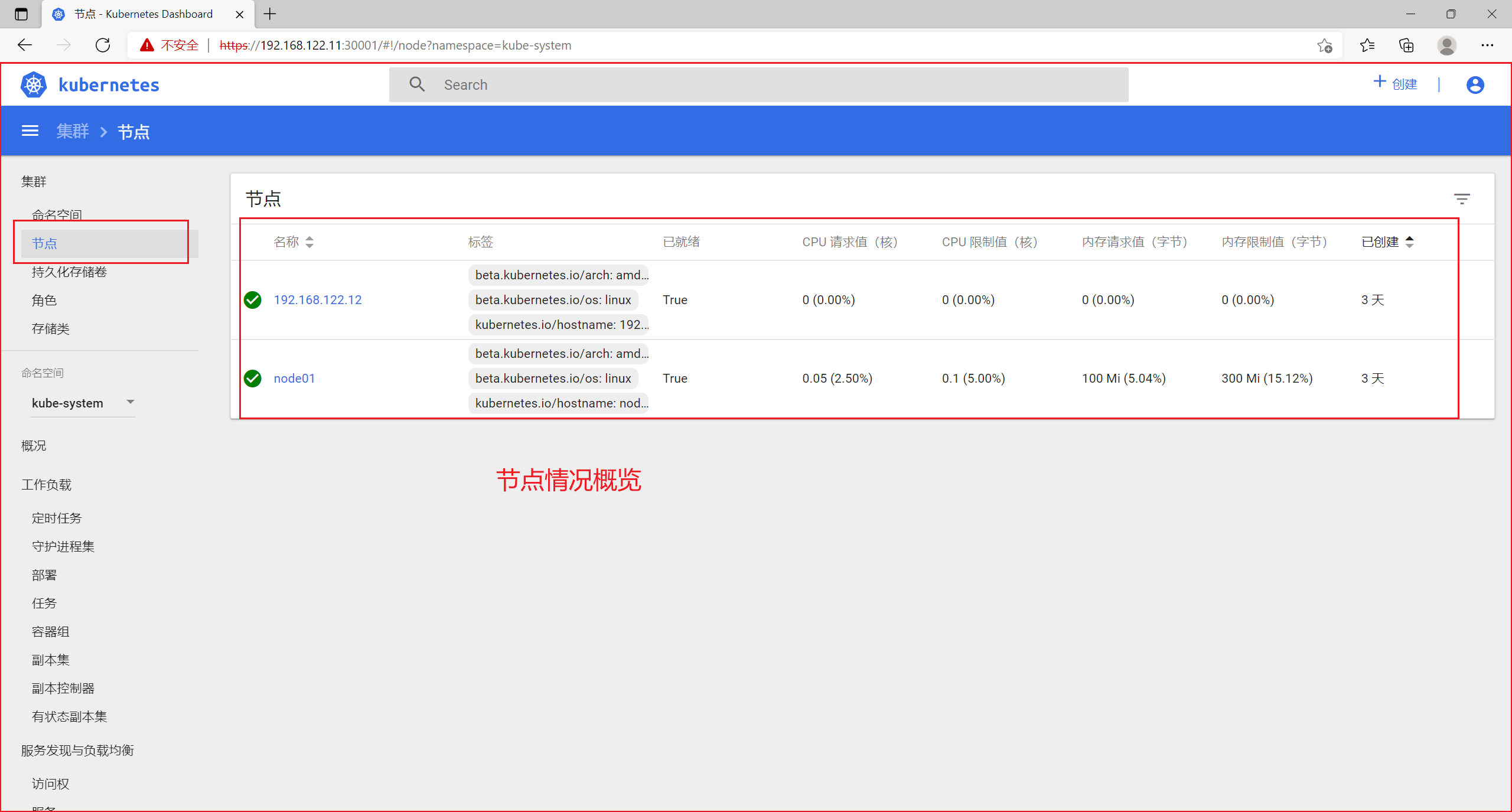
8.3 角色
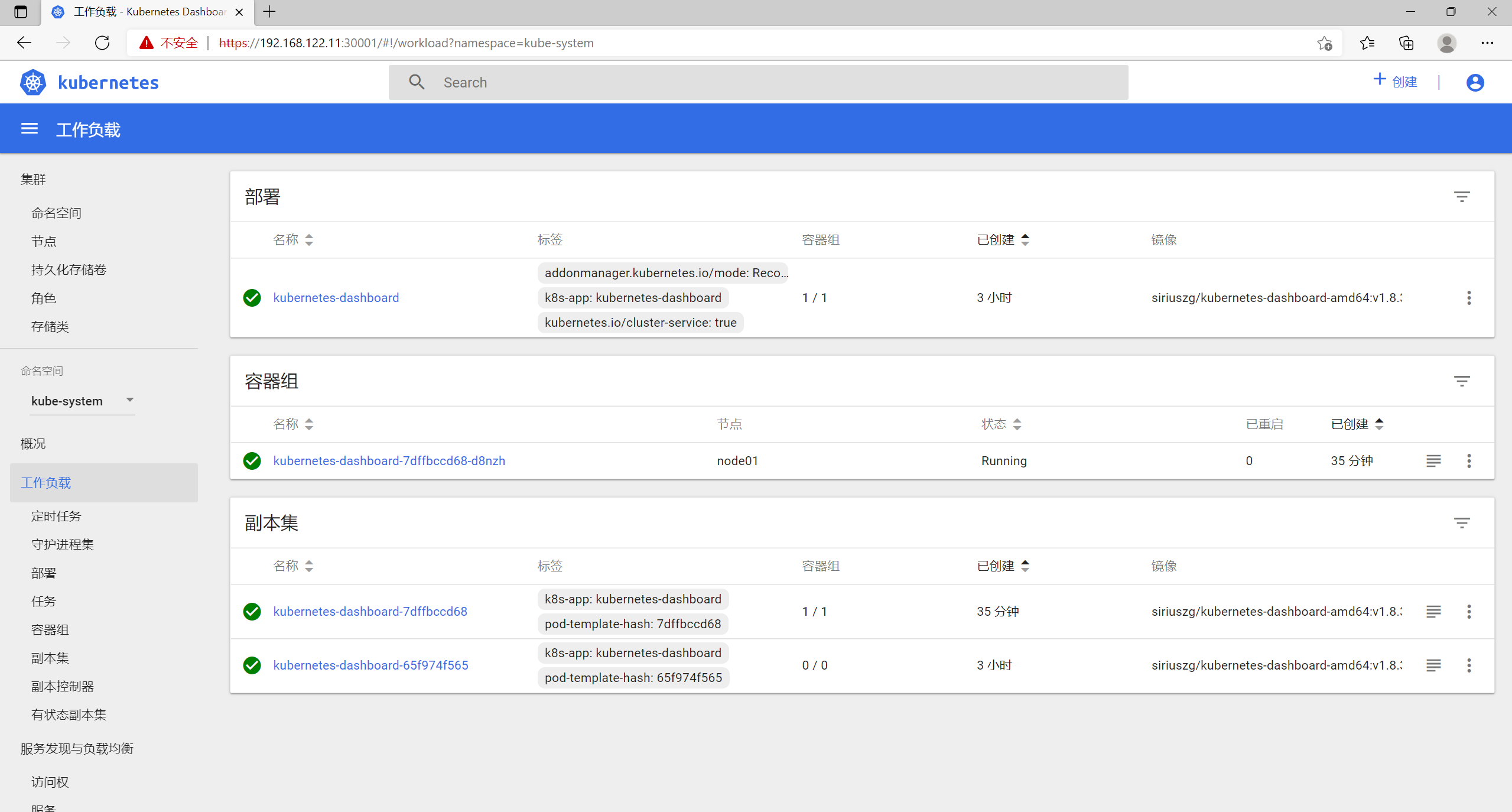
8.4 工作负载
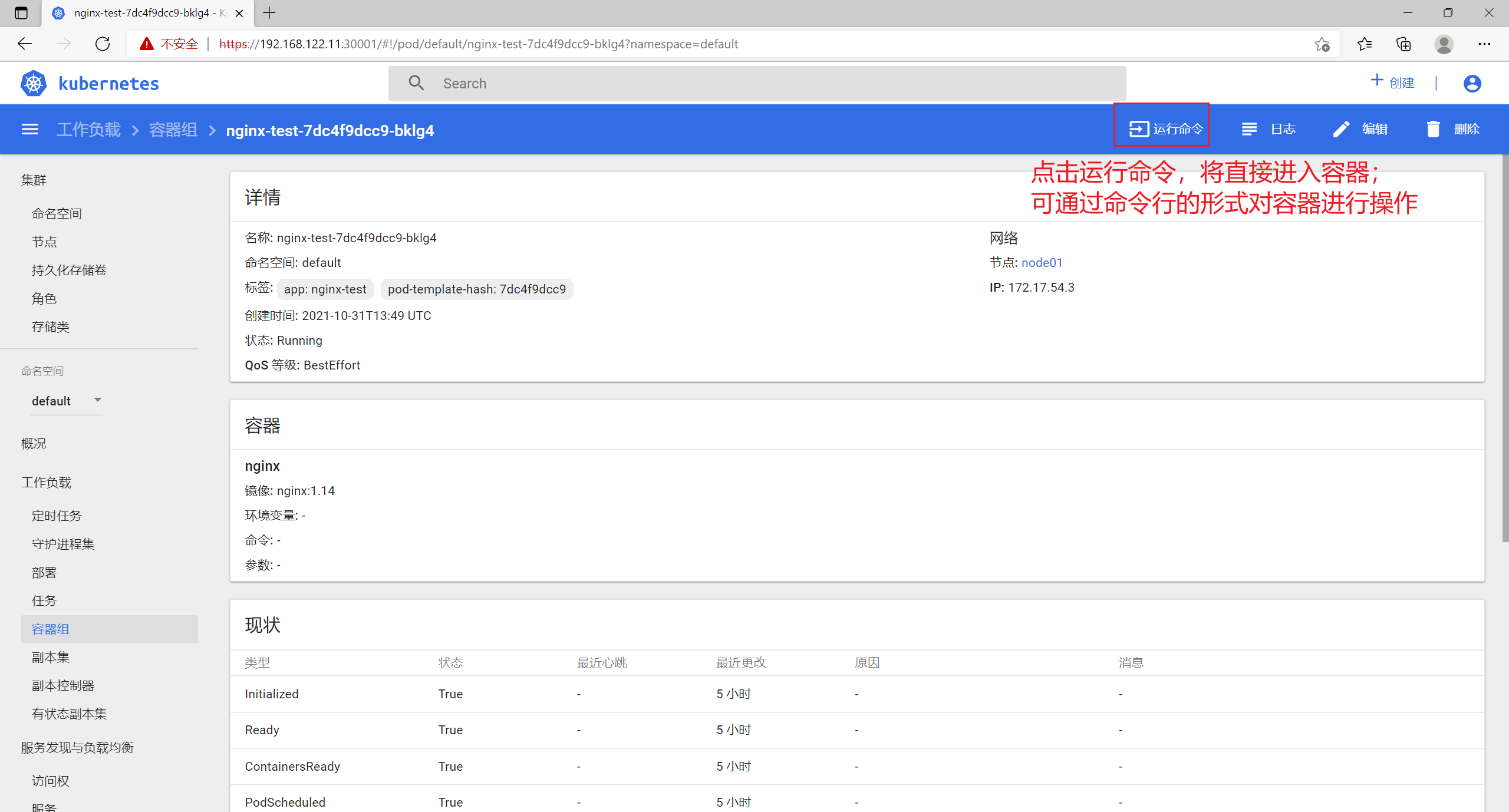
8.5 命令行
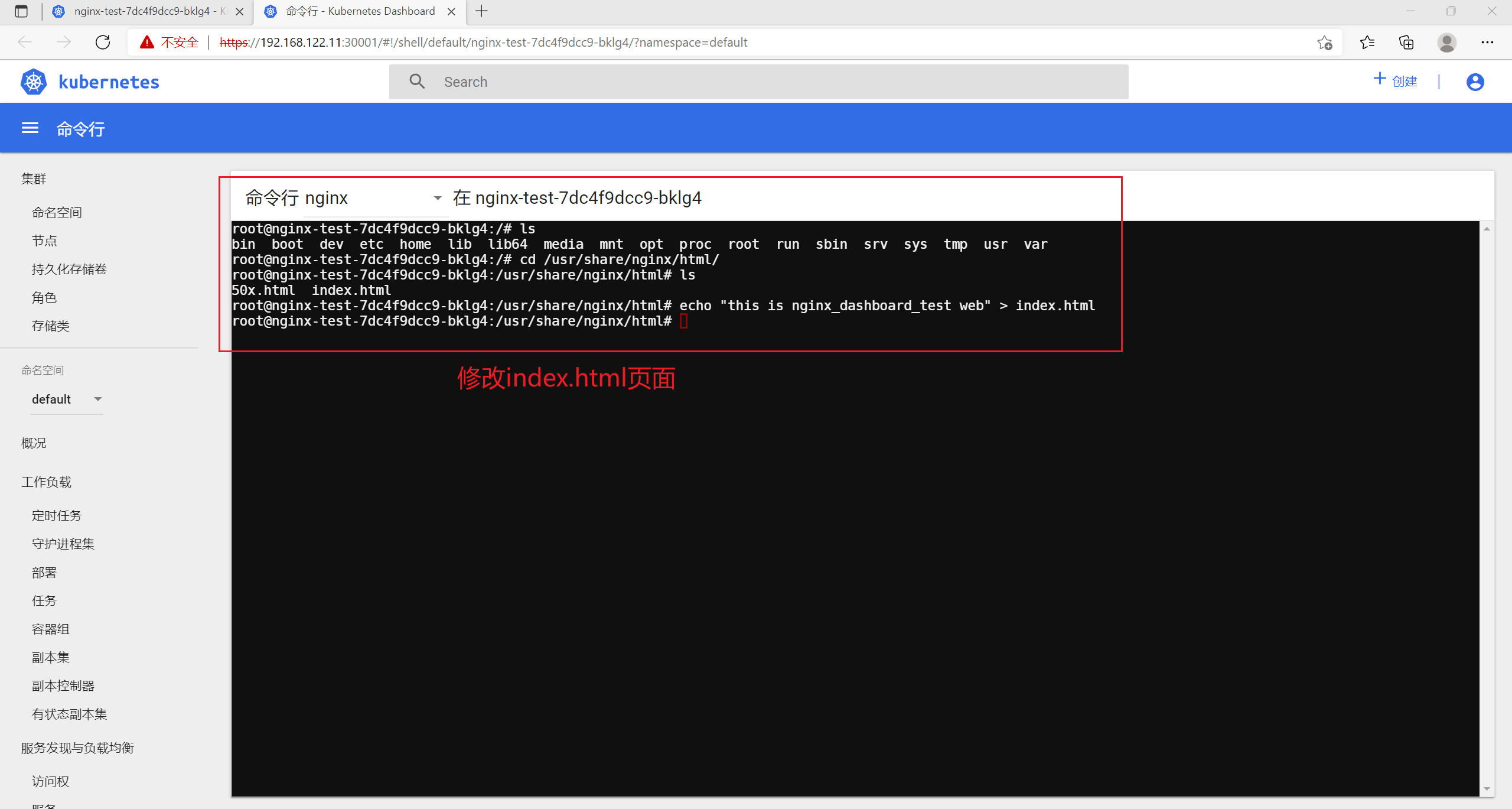
[root@node01 opt]# curl 172.17.54.3this is nginx_dashboard_test web
8.6 日志

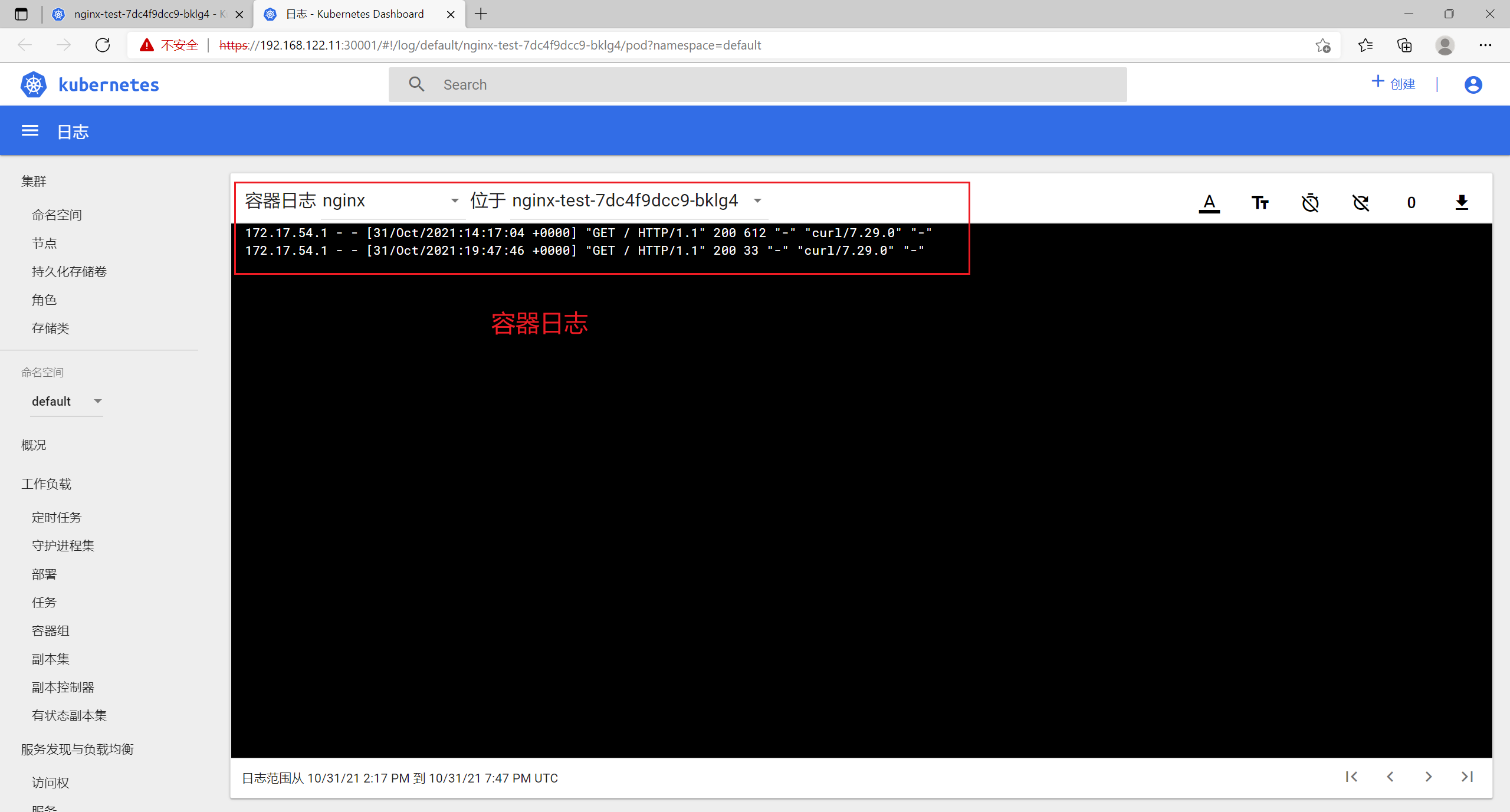
8.7 创建容器
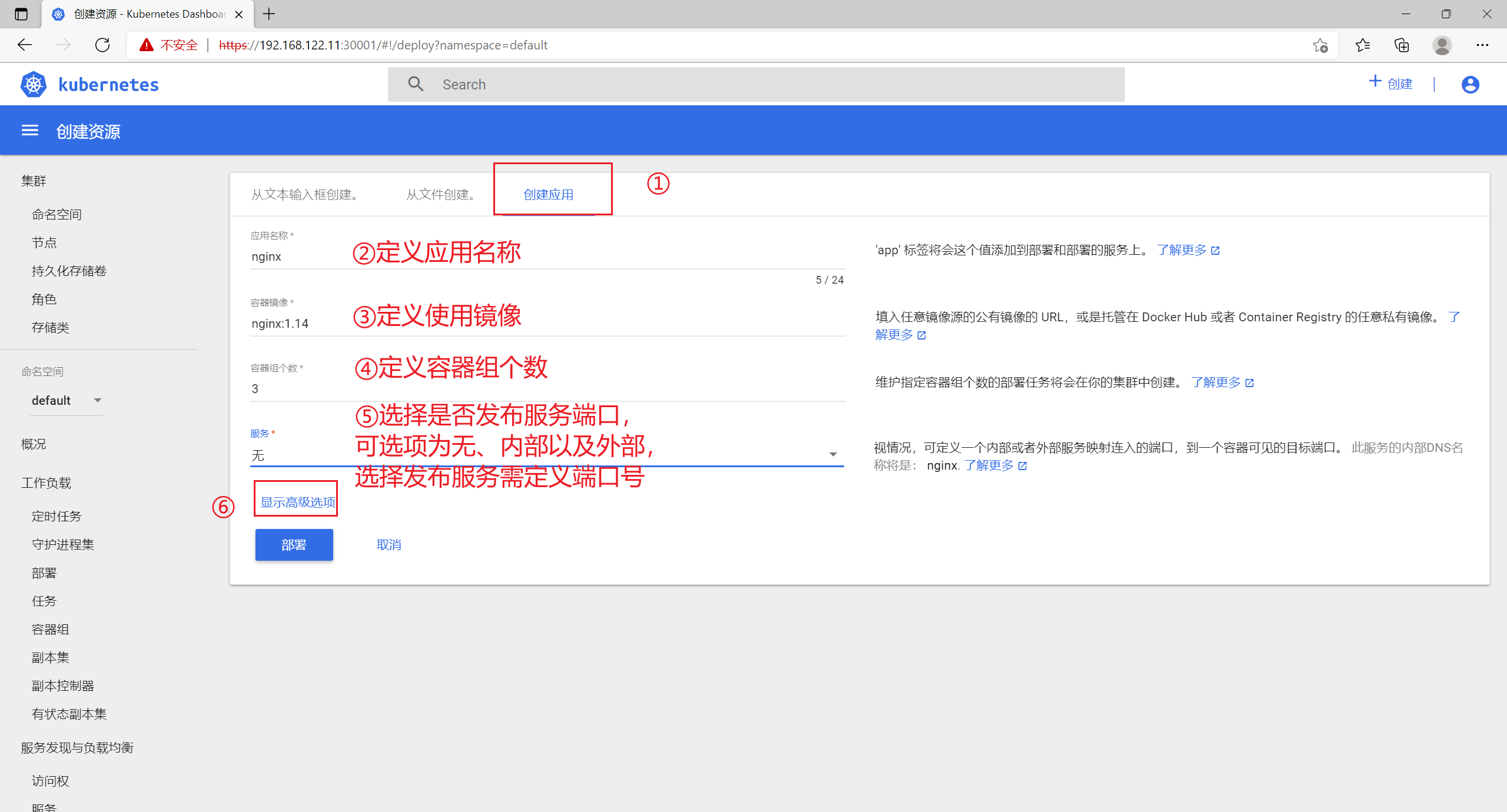
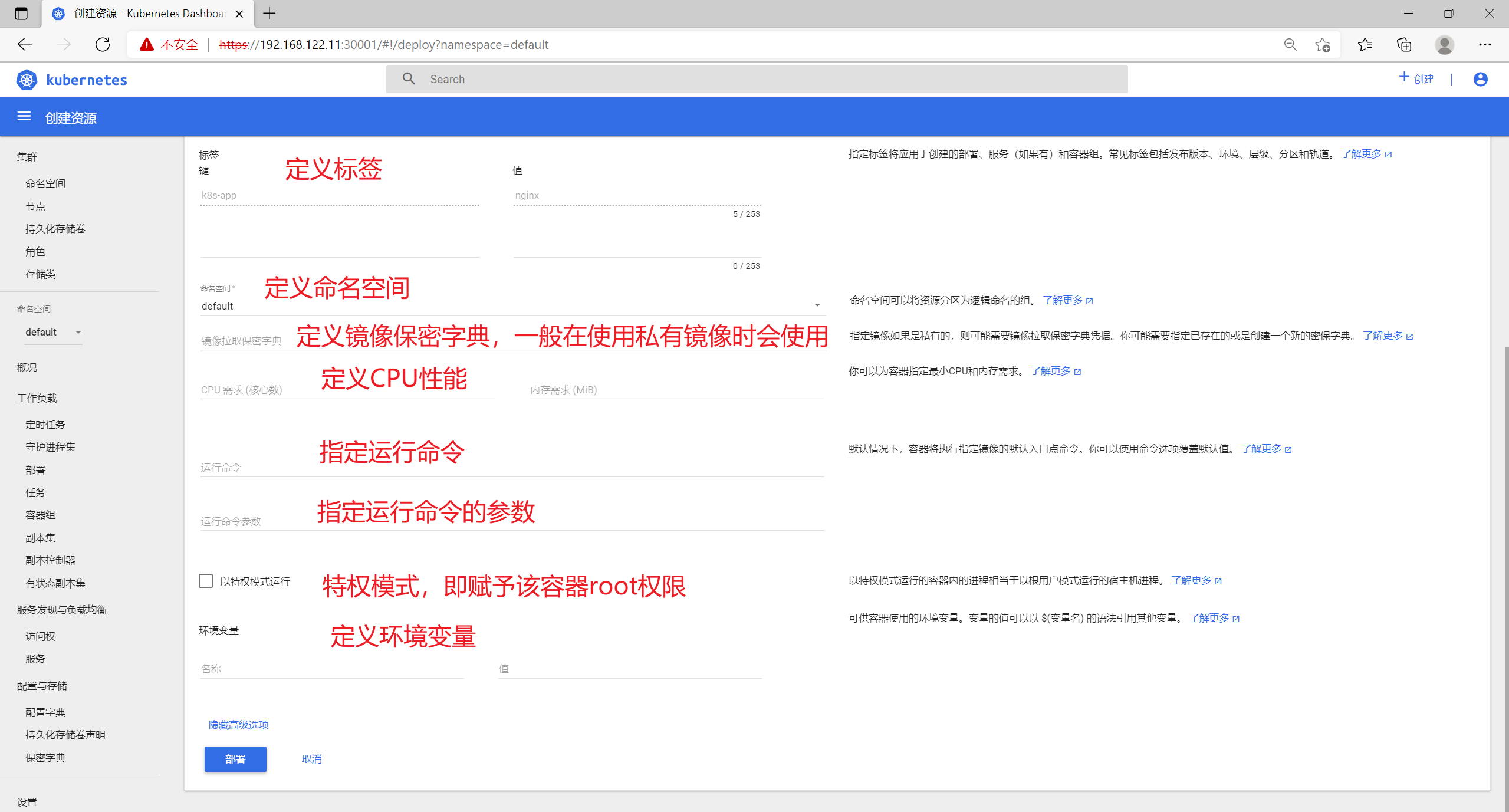
设定完成后,点击部署
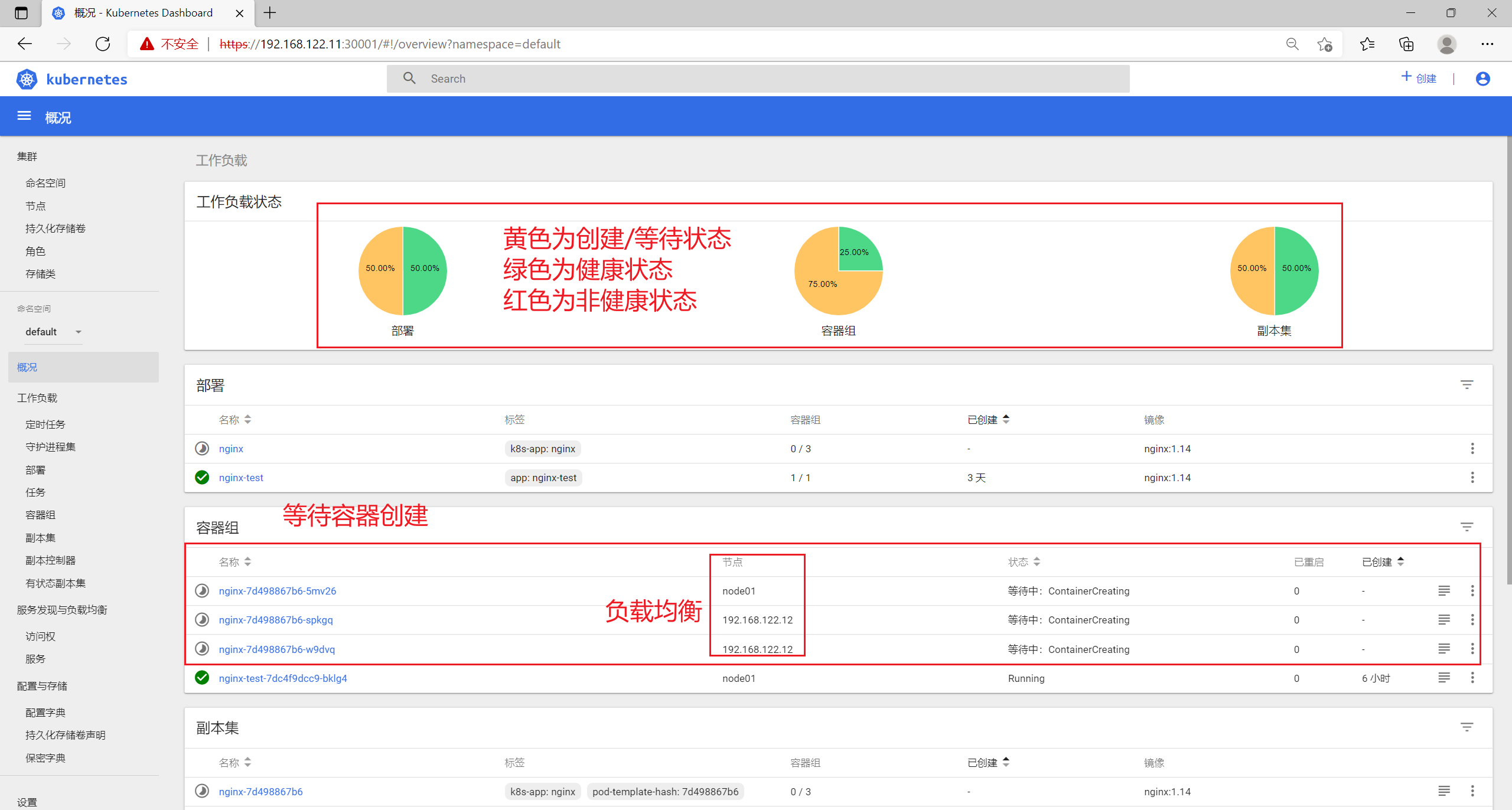
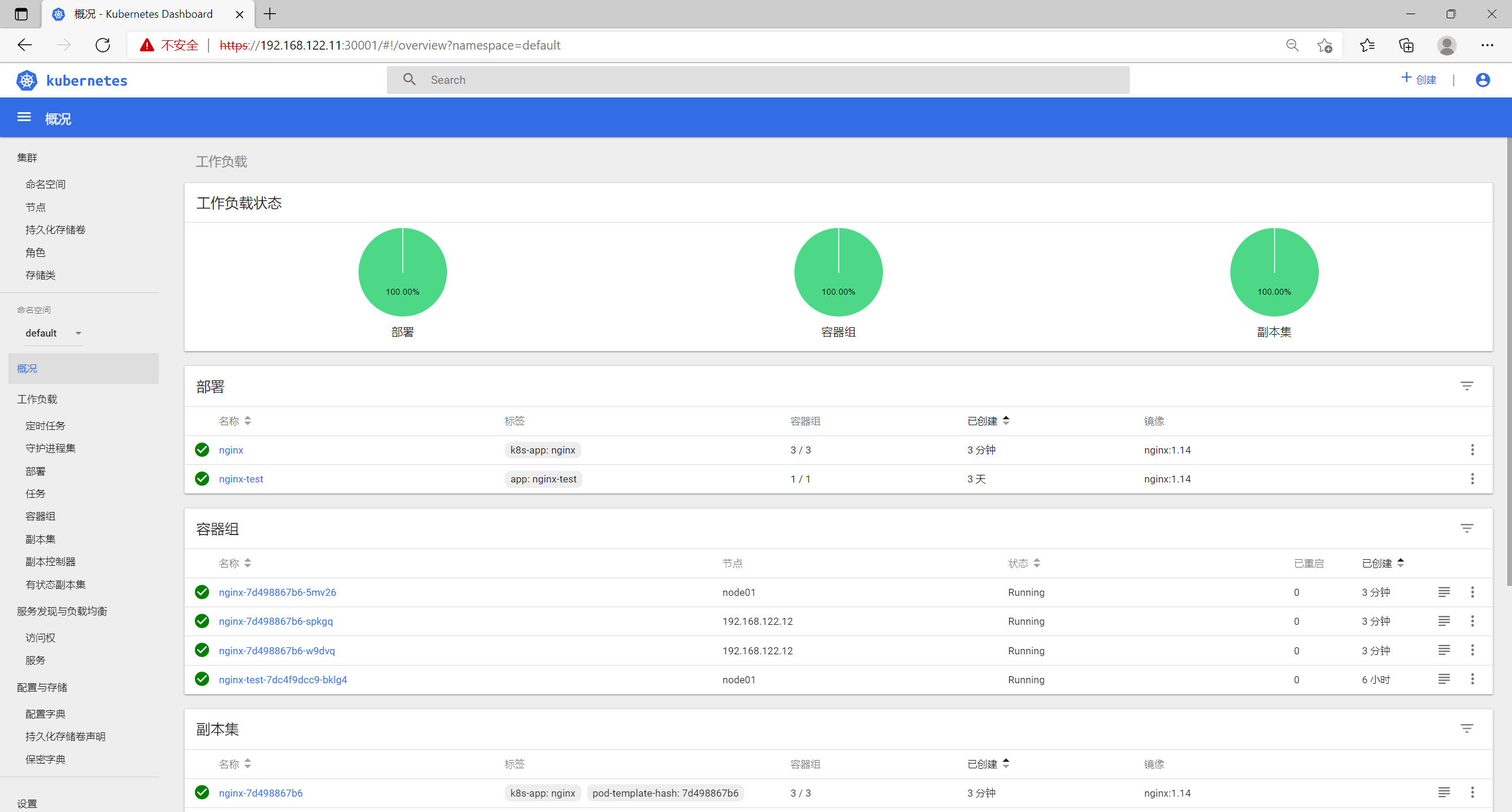
完成部署,通过master节点查看
[root@master01 dashboard]# kubectl get podNAME READY STATUS RESTARTS AGEnginx-7d498867b6-5mv26 1/1 Running 0 5m15snginx-7d498867b6-spkgq 1/1 Running 0 5m15snginx-7d498867b6-w9dvq 1/1 Running 0 5m15snginx-test-7dc4f9dcc9-bklg4 1/1 Running 0 6h18m[root@master01 dashboard]# kubectl get pod -o wideNAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODEnginx-7d498867b6-5mv26 1/1 Running 0 5m20s 172.17.54.5 node01 <none>nginx-7d498867b6-spkgq 1/1 Running 0 5m20s 172.17.97.4 192.168.122.12 <none>nginx-7d498867b6-w9dvq 1/1 Running 0 5m20s 172.17.97.3 192.168.122.12 <none>nginx-test-7dc4f9dcc9-bklg4 1/1 Running 0 6h18m 172.17.54.3 node01 <none>
k8s之Dashboard插件部署及使用的更多相关文章
- suse 12 二进制部署 Kubernetets 1.19.7 - 第12章 - 部署dashboard插件
文章目录 1.12.0.创建namespace 1.12.1.创建Dashboard rbac文件 1.12.2.创建dashboard文件 1.12.3.查看pod以及svc 1.12.4.获取 d ...
- 使用Kubeadm创建k8s集群之部署规划(三十)
前言 上一篇我们讲述了使用Kubectl管理k8s集群,那么接下来,我们将使用kubeadm来启动k8s集群. 部署k8s集群存在一定的挑战,尤其是部署高可用的k8s集群更是颇为复杂(后续会讲).因此 ...
- 二进制部署K8S-3核心插件部署
二进制部署K8S-3核心插件部署 5.1. CNI网络插件 kubernetes设计了网络模型,但是pod之间通信的具体实现交给了CNI往插件.常用的CNI网络插件有:Flannel .Calico. ...
- kubeadm/flannel/dashboard/harbor部署以及服务发布
kubeadm/flannel/dashboard/harbor部署以及服务发布 目录 kubeadm/flannel/dashboard/harbor部署以及服务发布 一.部署kubeadm 1. ...
- k8s可视化工具kubernetes-dashboard部署——小白教程
参考资料: kubernetes官方文档 官方GitHub 创建访问用户 解决chrome无法访问dashboard 官方部署方法如下: kubectl apply -f https://raw.gi ...
- K8S(03)核心插件-Flannel网络插件
系列文章说明 本系列文章,可以基本算是 老男孩2019年王硕的K8S周末班课程 笔记,根据视频来看本笔记最好,否则有些地方会看不明白 需要视频可以联系我 K8S核心网络插件Flannel 目录 系列文 ...
- zz将 VSTO 插件部署给所有用户
原文:zz将 VSTO 插件部署给所有用户 注:本文原作者 Misha Shneerson 是 VSTO 团队的工程师.原文可以在下列地址找到:http://blogs.msdn.com/mshnee ...
- eclipse maven项目中使用tomcat插件部署项目
maven的tomcat插件部署web项目,我简单认为分两种,一种是部署到内置tomcat,另一种是部署到安装的tomcat. 第一种部署,默认是部署在内置tomcat的8080端口,如果不需要改端口 ...
- Gradle 1.12用户指南翻译——第四十九章. Build Dashboard 插件
本文由CSDN博客貌似掉线翻译,其他章节的翻译请参见: http://blog.csdn.net/column/details/gradle-translation.html 翻译项目请关注Githu ...
随机推荐
- java运算符2
续: 位运算符(<<,>>,>>>) 1.<<: 3<<2,二进制左移2位,右边用0补齐 3的二进制:00000000 0 ...
- 初识python:scoket 单用户互发消息
实现功能: 启动"服务器".通过"客户端1"连接"服务器",然后互发消息.在此过程中,有"客户端2"连接到"服 ...
- ADO.NET数据访问基础与综合应用2020年10月31日20:17:09学习笔记
四.创建数据表 1.数据表的名称. 2.表中的字段名.数据类型.是否可以为空.字段的约束.必备的字段(通常会有一个ID,表示实体的唯一性:可以直接手写,也可以使用种子标识自动生成,给定起始值,给定增长 ...
- docker 修改容器env配置
docker 修改容器env配置 场景:修改zabbix数据库密码 zabbix容器构成: 数据库:zabbix-mysql server端:zabbix-server-mysql web端:zabb ...
- Hadoop 代码实现文件上传
本项目主要实现Windows下利用代码实现Hadoop中文件上传至HDFS 实现上传文本文件中单词个数的计数 1.项目结构 2.相关代码 CopyFromLocalFile 1 package com ...
- 【刷题-PAT】A1126 Eulerian Path (25 分)
1126 Eulerian Path (25 分) In graph theory, an Eulerian path is a path in a graph which visits every ...
- gin中使用路由组
package main import ( "github.com/gin-gonic/gin" ) func main() { router := gin.Default() / ...
- CTF web安全45天入门学习路线
前言 因为最近在准备开发CTF学习平台,先做一个学习路线的整理,顺便也是对想学web的学弟学妹的一些建议. 学习路线 初期 刚刚走进大学,入了web安全的坑,面对诸多漏洞必然是迷茫的,这时的首要任务就 ...
- java内部类-局部内部类
1 package face_09; 2 /* 3 * 内部类可以存放在局部位置上. 4 * 5 * 内部类在局部位置上只能访问局部中被final修饰的局部变量. 6 */ 7 /*class Out ...
- sublime Text3编译java文件提示Decode error - output not utf-8
进入sublime Text3安装目录下的package文件夹,用解压缩软件打开Java.sublime-package, 编辑里面的JavaC.sublime-build,修改最后一句 将文件改为 ...
