Ethical Hacking - GAINING ACCESS(18)
CLIENT SIDE ATTACKS
Backdooring ANY file
- Combine backdoor with any file - Generic solution.
- Users are more likely to run a pdf, image or audio file than an executable.
- Works well with social engineering.
To convert the original(pdf, jpg, mp3) file to an exe, then combine it with a backdoor using veil.
Step 1:
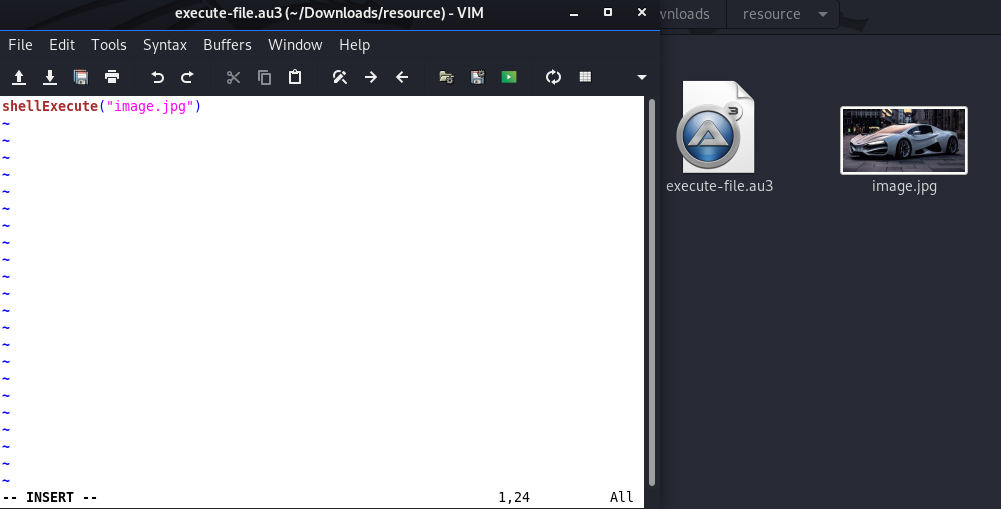
Step 2:
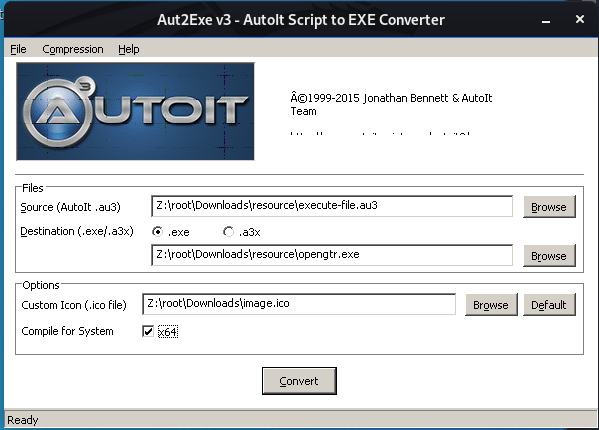
Ethical Hacking - GAINING ACCESS(18)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
- Ethical Hacking - GAINING ACCESS(10)
CLIENT SIDE ATTACKS Use if server-side attacks fail. If IP is probably useless. Require user interac ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
随机推荐
- 团队进行Alpha冲刺--项目测试
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 这个作业要求在哪里 团队作业第五次--Alpha冲刺 这个作业的目标 团队进行Alpha冲刺--项目测试 作业正文 如下 其他参 ...
- mysql语句基本练习
select ename,job from emp where job in ('MANAGER','ANALYET','SALESMAN') 1.查询出工作岗位为MANAGER.ANALYST.SA ...
- Glusterfs读写性能测试与分析
一.测试目的: 1.测试分布卷(Distributed).分布式复制卷(Distributed-Replicate).条带卷(Strip)和分布式条带复制卷(Distributed-Strip-Rep ...
- Nginx功能详细介绍(大而全)
Nginx介绍 Nginx是C语言开发的. HTTP和反向代理Web服务器. Nginx ⼜能做什么事情(应⽤场景) Http服务器(Web服务器) 性能⾮常⾼,⾮常注重效率,能够经受⾼负载的考验. ...
- python之os模块分类整理
OS模块简单介绍: 它是一个Python的系统编程的操作模块,可以处理文件和目录.比如查找文件或目录,对大量的路径与文件处理. 常用操作方法: os.name :指出当前你使用的操作平台,‘nt’代表 ...
- 使用vs2019加.net core 对WeiApi的创建
vs2019创建webapi 1.创建新的项目 2.选择.NET CORE的ASP .NET CORE WEB应用程序 3.定义项目名称和存放地点 4.选择API创建项目 5.删除原本的无用的类 6. ...
- 美国6w刀的远程工作高级工程师职位,说下在线评估, 倒在第一阶段, 认知能力测试?智商不够怎么办?!
前几天刚被裁员了, 然后在Linkedin上面看到一个crossover的senior software engineer的职位,写的可以remote, 6w刀, 我第一次参加这个公司的这种在线测试, ...
- 如何基于 echarts 实现区间柱状图(包括横向)?
目录 需求 借鉴 echarts 的 demo 最终实现思路 实现效果 遇到的问题: 代码映射 源码 最后 始终如一 需求 需要利用 echarts 实现区间柱状图,效果如下: 效果来源于:g2-柱状 ...
- SQL注入笔记-updatexml与extractvalue
0x1介绍 MySQL 5.1.5版本中添加了对XML文档进行查询和修改的函数 EXTRACTVALUE(XML_document, XPath_string); UPDATEXML(XML_docu ...
- springboot freemark linux 找不到ftl文件
文件路径: 再idea中这样写是可以正常导出文件,但是 打成jar放到linux上就找不到文件了. String templatePath =WordUtils.class.getResource(& ...
