k8s实战之部署Prometheus+Grafana可视化监控告警平台
写在前面
之前部署web网站的时候,架构图中有一环节是监控部分,并且搭建一套有效的监控平台对于运维来说非常之重要,只有这样才能更有效率的保证我们的服务器和服务的稳定运行,常见的开源监控软件有好几种,如zabbix、Nagios、open-flcon还有prometheus,每一种有着各自的优劣势,感谢的童鞋可以自行百度,但是与k8s集群监控,相对于而已更加友好的是Prometheus,今天我们就看看如何部署一套Prometheus全方位监控K8S
主要内容
1.Prometheus架构
2.K8S监控指标及实现思路
3.在K8S平台部署Prometheus
4.基于K8S服务发现的配置解析
5.在K8S平台部署Grafana
6.监控K8S集群中Pod、Node、资源对象
7.使用Grafana可视化展示Prometheus监控数据
8.告警规则与告警通知
1 Prometheus架构
Prometheus 是什么
Prometheus(普罗米修斯)是一个最初在SoundCloud上构建的监控系统。自2012年成为社区开源项目,拥有非常活跃的开发人员和用户社区。为强调开源及独立维护,Prometheus于2016年加入云原生云计算基金会(CNCF),成为继Kubernetes之后的第二个托管项目。
官网地址:
https://prometheus.io
https://github.com/prometheus
Prometheus 组成及架构

- Prometheus Server:收集指标和存储时间序列数据,并提供查询接口
- ClientLibrary: 客户端库
- Push Gateway:短期存储指标数据。主要用于临时性的任务
- Exporters:采集已有的第三方服务监控指标并暴露metrics
- Alertmanager:告警
- Web UI:简单的Web控制台
数据模型
Prometheus将所有数据存储为时间序列;具有相同度量名称以及标签属于同一个指标。
每个时间序列都由度量标准名称和一组键值对(也成为标签)唯一标识。
时间序列格式:
{=, ...}
示例:api_http_requests_total{method="POST", handler="/messages"}
作业和实例
实例:可以抓取的目标称为实例(Instances)
作业:具有相同目标的实例集合称为作业(Job)
scrape_configs:
-job_name: 'prometheus'
static_configs:
-targets: ['localhost:9090']
-job_name: 'node'
static_configs:
-targets: ['192.168.1.10:9090']
2 K8S监控指标及实现思路
k8S监控指标
Kubernetes本身监控
- Node资源利用率
- Node数量
- Pods数量(Node)
- 资源对象状态
Pod监控
- Pod数量(项目)
- 容器资源利用率
- 应用程序
Prometheus监控K8S架构
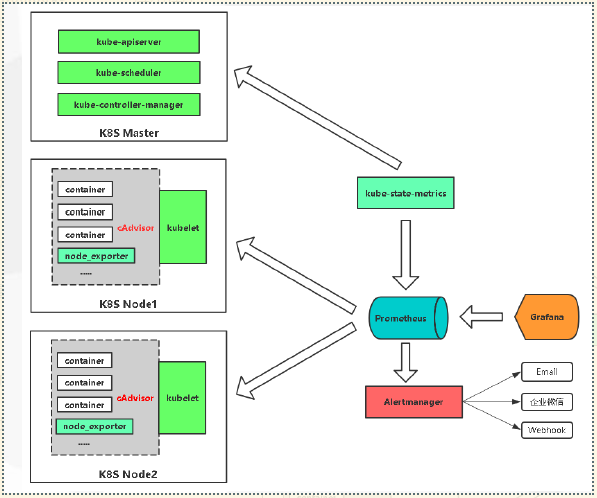
| 监控指标 | 具体实现 | 举例 |
|---|---|---|
| Pod性能 | cAdvisor | 容器CPU |
| Node性能 | node-exporter 节点CPU | 内存利用率 |
| K8S资源对象 | kube-state-metrics | Pod/Deployment/Service |
| 服务发现: | ||
| https://prometheus.io/docs/prometheus/latest/configuration/configuration/#kubernetes_sd_config |
3 在K8S平台部署Prometheus
3.1集群环境
| ip地址 | 角色 | 备注 |
|---|---|---|
| 192.168.73.136 | nfs | |
| 192.168.73.138 | k8s-master | |
| 192.168.73.139 | k8s-node01 | |
| 192.168.73.140 | k8s-node02 | |
| 192.168.73.135 | k8s-node03 |
3.2 项目地址:
[root@k8s-master src]# git clone https://github.com/zhangdongdong7/k8s-prometheus.gitCloning into 'k8s-prometheus'...remote: Enumerating objects: 3, done.remote: Counting objects: 100% (3/3), done.remote: Total 3 (delta 0), reused 0 (delta 0), pack-reused 0Unpacking objects: 100% (3/3), done.[root@k8s-master src]# cd k8s-prometheus/[root@k8s-master k8s-prometheus]# lsalertmanager-configmap.yaml kube-state-metrics-rbac.yaml prometheus-rbac.yamlalertmanager-deployment.yaml kube-state-metrics-service.yaml prometheus-rules.yamlalertmanager-pvc.yaml node_exporter-0.17.0.linux-amd64.tar.gz prometheus-service.yamlalertmanager-service.yaml node_exporter.sh prometheus-statefulset-static-pv.yamlgrafana.yaml OWNERS prometheus-statefulset.yamlkube-state-metrics-deployment.yaml prometheus-configmap.yaml README.md
3.3 授权
RBAC(Role-Based Access Control,基于角色的访问控制):负责完成授权(Authorization)工作。
编写授权yaml
[root@k8s-master prometheus-k8s]# vim prometheus-rbac.yamlapiVersion: v1kind: ServiceAccountmetadata:name: prometheusnamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile---apiVersion: rbac.authorization.k8s.io/v1beta1kind: ClusterRolemetadata:name: prometheuslabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcilerules:- apiGroups:- ""resources:- nodes- nodes/metrics- services- endpoints- podsverbs:- get- list- watch- apiGroups:- ""resources:- configmapsverbs:- get- nonResourceURLs:- "/metrics"verbs:- get---apiVersion: rbac.authorization.k8s.io/v1beta1kind: ClusterRoleBindingmetadata:name: prometheuslabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile"prometheus-rbac.yaml" 55L, 1080C 1,1 TopapiVersion: v1kind: ServiceAccountmetadata:name: prometheusnamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile---apiVersion: rbac.authorization.k8s.io/v1beta1kind: ClusterRolemetadata:name: prometheuslabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile1,1 TopapiVersion: v1kind: ServiceAccountmetadata:name: prometheusnamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile---apiVersion: rbac.authorization.k8s.io/v1beta1kind: ClusterRolemetadata:name: prometheuslabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcilerules:- apiGroups:- ""resources:- nodes- nodes/metrics- services- endpoints- podsverbs:- get- list- watch- apiGroups:- ""resources:- configmapsverbs:- get- nonResourceURLs:- "/metrics"verbs:- get---apiVersion: rbac.authorization.k8s.io/v1beta1kind: ClusterRoleBindingmetadata:name: prometheuslabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: ReconcileroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: prometheussubjects:- kind: ServiceAccountname: prometheusnamespace: kube-system
创建
[root@k8s-master prometheus-k8s]# kubectl apply -f prometheus-rbac.yaml
3.4 配置管理
使用Configmap保存不需要加密配置信息
其中需要把nodes中ip地址根据自己的地址进行修改
[root@k8s-master prometheus-k8s]# vim prometheus-configmap.yaml# Prometheus configuration format https://prometheus.io/docs/prometheus/latest/configuration/configuration/apiVersion: v1kind: ConfigMap #metadata:name: prometheus-confignamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: EnsureExistsdata:prometheus.yml: |rule_files:- /etc/config/rules/*.rulesscrape_configs:- job_name: prometheusstatic_configs:- targets:- localhost:9090- job_name: kubernetes-nodesscrape_interval: 30sstatic_configs:- targets:- 192.168.73.135:9100- 192.168.73.138:9100- 192.168.73.139:9100- 192.168.73.140:9100- job_name: kubernetes-apiserverskubernetes_sd_configs:- role: endpointsrelabel_configs:- action: keepregex: default;kubernetes;httpssource_labels:- __meta_kubernetes_namespace- __meta_kubernetes_service_name- __meta_kubernetes_endpoint_port_namescheme: httpstls_config:ca_file: /var/run/secrets/kubernetes.io/serviceaccount/ca.crtinsecure_skip_verify: truebearer_token_file: /var/run/secrets/kubernetes.io/serviceaccount/token- job_name: kubernetes-nodes-kubeletkubernetes_sd_configs:- role: noderelabel_configs:- action: labelmapregex: __meta_kubernetes_node_label_(.+)scheme: httpstls_config:ca_file: /var/run/secrets/kubernetes.io/serviceaccount/ca.crtinsecure_skip_verify: truebearer_token_file: /var/run/secrets/kubernetes.io/serviceaccount/token- job_name: kubernetes-nodes-cadvisorkubernetes_sd_configs:- role: noderelabel_configs:- action: labelmapregex: __meta_kubernetes_node_label_(.+)- target_label: __metrics_path__replacement: /metrics/cadvisorscheme: httpstls_config:ca_file: /var/run/secrets/kubernetes.io/serviceaccount/ca.crtinsecure_skip_verify: truebearer_token_file: /var/run/secrets/kubernetes.io/serviceaccount/token- job_name: kubernetes-service-endpointskubernetes_sd_configs:- role: endpointsrelabel_configs:- action: keepregex: truesource_labels:- __meta_kubernetes_service_annotation_prometheus_io_scrape- action: replaceregex: (https?)source_labels:- __meta_kubernetes_service_annotation_prometheus_io_schemetarget_label: __scheme__- action: replaceregex: (.+)source_labels:- __meta_kubernetes_service_annotation_prometheus_io_pathtarget_label: __metrics_path__- action: replaceregex: ([^:]+)(?::\d+)?;(\d+)replacement: $1:$2source_labels:- __address__- __meta_kubernetes_service_annotation_prometheus_io_porttarget_label: __address__- action: labelmapregex: __meta_kubernetes_service_label_(.+)- action: replacesource_labels:- __meta_kubernetes_namespacetarget_label: kubernetes_namespace- action: replacesource_labels:- __meta_kubernetes_service_nametarget_label: kubernetes_name- job_name: kubernetes-serviceskubernetes_sd_configs:- role: servicemetrics_path: /probeparams:module:- http_2xxrelabel_configs:- action: keepregex: truesource_labels:- __meta_kubernetes_service_annotation_prometheus_io_probe- source_labels:- __address__target_label: __param_target- replacement: blackboxtarget_label: __address__- source_labels:- __param_targettarget_label: instance- action: labelmapregex: __meta_kubernetes_service_label_(.+)- source_labels:- __meta_kubernetes_namespacetarget_label: kubernetes_namespace- source_labels:- __meta_kubernetes_service_nametarget_label: kubernetes_name- job_name: kubernetes-podskubernetes_sd_configs:- role: podrelabel_configs:- action: keepregex: truesource_labels:- __meta_kubernetes_pod_annotation_prometheus_io_scrape- action: replaceregex: (.+)source_labels:- __meta_kubernetes_pod_annotation_prometheus_io_pathtarget_label: __metrics_path__- action: replaceregex: ([^:]+)(?::\d+)?;(\d+)replacement: $1:$2source_labels:- __address__- __meta_kubernetes_pod_annotation_prometheus_io_porttarget_label: __address__- action: labelmapregex: __meta_kubernetes_pod_label_(.+)- action: replacesource_labels:- __meta_kubernetes_namespacetarget_label: kubernetes_namespace- action: replacesource_labels:- __meta_kubernetes_pod_nametarget_label: kubernetes_pod_namealerting:alertmanagers:- static_configs:- targets: ["alertmanager:80"]
创建
[root@k8s-master prometheus-k8s]# kubectl apply -f prometheus-configmap.yaml
3.5 有状态部署prometheus
这里使用storageclass进行动态供给,给prometheus的数据进行持久化,具体实现办法,可以查看之前的文章《k8s中的NFS动态存储供给》,除此之外可以使用静态供给的prometheus-statefulset-static-pv.yaml进行持久化
[root@k8s-master prometheus-k8s]# vim prometheus-statefulset.yamlapiVersion: apps/v1kind: StatefulSetmetadata:name: prometheusnamespace: kube-systemlabels:k8s-app: prometheuskubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcileversion: v2.2.1spec:serviceName: "prometheus"replicas: 1podManagementPolicy: "Parallel"updateStrategy:type: "RollingUpdate"selector:matchLabels:k8s-app: prometheustemplate:metadata:labels:k8s-app: prometheusannotations:scheduler.alpha.kubernetes.io/critical-pod: ''spec:priorityClassName: system-cluster-criticalserviceAccountName: prometheusinitContainers:- name: "init-chown-data"image: "busybox:latest"imagePullPolicy: "IfNotPresent"command: ["chown", "-R", "65534:65534", "/data"]volumeMounts:- name: prometheus-datamountPath: /datasubPath: ""containers:- name: prometheus-server-configmap-reloadimage: "jimmidyson/configmap-reload:v0.1"imagePullPolicy: "IfNotPresent"args:- --volume-dir=/etc/config- --webhook-url=http://localhost:9090/-/reloadvolumeMounts:- name: config-volumemountPath: /etc/configreadOnly: trueresources:limits:cpu: 10mmemory: 10Mirequests:cpu: 10mmemory: 10Mi- name: prometheus-serverimage: "prom/prometheus:v2.2.1"imagePullPolicy: "IfNotPresent"args:- --config.file=/etc/config/prometheus.yml- --storage.tsdb.path=/data- --web.console.libraries=/etc/prometheus/console_libraries- --web.console.templates=/etc/prometheus/consoles- --web.enable-lifecycleports:- containerPort: 9090readinessProbe:httpGet:path: /-/readyport: 9090initialDelaySeconds: 30timeoutSeconds: 30livenessProbe:httpGet:path: /-/healthyport: 9090initialDelaySeconds: 30timeoutSeconds: 30# based on 10 running nodes with 30 pods eachresources:limits:cpu: 200mmemory: 1000Mirequests:cpu: 200mmemory: 1000MivolumeMounts:- name: config-volumemountPath: /etc/config- name: prometheus-datamountPath: /datasubPath: ""- name: prometheus-rulesmountPath: /etc/config/rulesterminationGracePeriodSeconds: 300volumes:- name: config-volumeconfigMap:name: prometheus-config- name: prometheus-rulesconfigMap:name: prometheus-rulesvolumeClaimTemplates:- metadata:name: prometheus-dataspec:storageClassName: managed-nfs-storageaccessModes:- ReadWriteOnceresources:requests:storage: "16Gi"
创建
[root@k8s-master prometheus-k8s]# kubectl apply -f prometheus-statefulset.yaml
检查状态
[root@k8s-master prometheus-k8s]# kubectl get pod -n kube-systemNAME READY STATUS RESTARTS AGEalertmanager-5d75d5688f-fmlq6 2/2 Running 0 8dcoredns-5bd5f9dbd9-wv45t 1/1 Running 1 8dgrafana-0 1/1 Running 2 14dkube-state-metrics-7c76bdbf68-kqqgd 2/2 Running 6 13dkubernetes-dashboard-7d77666777-d5ng4 1/1 Running 5 14dprometheus-0 2/2 Running 6 14d
可以看到一个prometheus-0的pod,这就刚才使用statefulset控制器进行的有状态部署,状态为Runing则是正常,如果不为Runing可以使用kubectl describe pod prometheus-0 -n kube-system查看报错详情
3.6 创建service暴露访问端口
此处使用nodePort固定一个访问端口,便于记忆
[root@k8s-master prometheus-k8s]# vim prometheus-service.yamlkind: ServiceapiVersion: v1metadata:name: prometheusnamespace: kube-systemlabels:kubernetes.io/name: "Prometheus"kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcilespec:type: NodePortports:- name: httpport: 9090protocol: TCPtargetPort: 9090nodePort: 30090selector:k8s-app: prometheus
创建
[root@k8s-master prometheus-k8s]# kubectl apply -f prometheus-service.yaml
检查
[root@k8s-master prometheus-k8s]# kubectl get pod,svc -n kube-systemNAME READY STATUS RESTARTS AGEpod/coredns-5bd5f9dbd9-wv45t 1/1 Running 1 8dpod/kubernetes-dashboard-7d77666777-d5ng4 1/1 Running 5 14dpod/prometheus-0 2/2 Running 6 14dNAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGEservice/kube-dns ClusterIP 10.0.0.2 <none> 53/UDP,53/TCP 13dservice/kubernetes-dashboard NodePort 10.0.0.127 <none> 443:30001/TCP 16dservice/prometheus NodePort 10.0.0.33 <none> 9090:30090/TCP 13d
3.7 web访问
使用任意一个NodeIP加端口进行访问,访问地址:http://NodeIP:Port ,此例就是:http://192.168.73.139:30090
访问成功的界面如图所示:
4 在K8S平台部署Grafana
通过上面的web访问,可以看出prometheus自带的UI界面是没有多少功能的,可视化展示的功能不完善,不能满足日常的监控所需,因此常常我们需要再结合Prometheus+Grafana的方式来进行可视化的数据展示
官网地址:
https://github.com/kubernetes/kubernetes/tree/master/cluster/addons/prometheus
https://grafana.com/grafana/download
刚才下载的项目中已经写好了Grafana的yaml,根据自己的环境进行修改
4.1 使用StatefulSet部署grafana
[root@k8s-master prometheus-k8s]# vim grafana.yamlapiVersion: apps/v1kind: StatefulSetmetadata:name: grafananamespace: kube-systemspec:serviceName: "grafana"replicas: 1selector:matchLabels:app: grafanatemplate:metadata:labels:app: grafanaspec:containers:- name: grafanaimage: grafana/grafanaports:- containerPort: 3000protocol: TCPresources:limits:cpu: 100mmemory: 256Mirequests:cpu: 100mmemory: 256MivolumeMounts:- name: grafana-datamountPath: /var/lib/grafanasubPath: grafanasecurityContext:fsGroup: 472runAsUser: 472volumeClaimTemplates:- metadata:name: grafana-dataspec:storageClassName: managed-nfs-storageaccessModes:- ReadWriteOnceresources:requests:storage: "1Gi"---apiVersion: v1kind: Servicemetadata:name: grafananamespace: kube-systemspec:type: NodePortports:- port : 80targetPort: 3000nodePort: 30091selector:app: grafana
4.2 Grafana的web访问
使用任意一个NodeIP加端口进行访问,访问地址:http://NodeIP:Port ,此例就是:http://192.168.73.139:30091
成功访问界面如下,会需要进行账号密码登陆,默认账号密码都为admin,登陆之后会让修改密码
登陆之后的界面如下
第一步需要进行数据源添加,点击create your first data source数据库图标,根据下图所示进行添加即可
第二步,添加完了之后点击底部的绿色的Save&Test,会成功提示Data sourse is working,则表示数据源添加成功
4.3 监控K8S集群中Pod、Node、资源对象
Pod
kubelet的节点使用cAdvisor提供的metrics接口获取该节点所有Pod和容器相关的性能指标数据。
暴露接口地址:
https://NodeIP:10255/metrics/cadvisor
https://NodeIP:10250/metrics/cadvisor
Node
使用node_exporter收集器采集节点资源利用率。
https://github.com/prometheus/node_exporter
使用文档:https://prometheus.io/docs/guides/node-exporter/
使用node_exporter.sh脚本分别在三台服务器上部署node_exporter收集器,不需要修改可直接运行脚本
[root@k8s-master prometheus-k8s]# cat node_exporter.sh#!/bin/bashwget https://github.com/prometheus/node_exporter/releases/download/v0.17.0/node_exporter-0.17.0.linux-amd64.tar.gztar zxf node_exporter-0.17.0.linux-amd64.tar.gzmv node_exporter-0.17.0.linux-amd64 /usr/local/node_exportercat <<EOF >/usr/lib/systemd/system/node_exporter.service[Unit]Description=https://prometheus.io[Service]Restart=on-failureExecStart=/usr/local/node_exporter/node_exporter --collector.systemd --collector.systemd.unit-whitelist=(docker|kubelet|kube-proxy|flanneld).service[Install]WantedBy=multi-user.targetEOFsystemctl daemon-reloadsystemctl enable node_exportersystemctl restart node_exporter[root@k8s-master prometheus-k8s]# ./node_exporter.sh
- 检测node_exporter的进程,是否生效
[root@k8s-master prometheus-k8s]# ps -ef|grep node_exporterroot 6227 1 0 Oct08 ? 00:06:43 /usr/local/node_exporter/node_exporter --collector.systemd --collector.systemd.unit-whitelist=(docker|kubelet|kube-proxy|flanneld).serviceroot 118269 117584 0 23:27 pts/0 00:00:00 grep --color=auto node_exporter
资源对象
kube-state-metrics采集了k8s中各种资源对象的状态信息,只需要在master节点部署就行
https://github.com/kubernetes/kube-state-metrics
- 创建rbac的yaml对metrics进行授权
[root@k8s-master prometheus-k8s]# vim kube-state-metrics-rbac.yamlapiVersion: v1kind: ServiceAccountmetadata:name: kube-state-metricsnamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRolemetadata:name: kube-state-metricslabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcilerules:- apiGroups: [""]resources:- configmaps- secrets- nodes- pods- services- resourcequotas- replicationcontrollers- limitranges- persistentvolumeclaims- persistentvolumes- namespaces- endpointsverbs: ["list", "watch"]- apiGroups: ["extensions"]resources:- daemonsets- deployments- replicasetsverbs: ["list", "watch"]- apiGroups: ["apps"]resources:- statefulsetsverbs: ["list", "watch"]- apiGroups: ["batch"]resources:- cronjobs- jobsverbs: ["list", "watch"]- apiGroups: ["autoscaling"]resources:- horizontalpodautoscalersverbs: ["list", "watch"]---apiVersion: rbac.authorization.k8s.io/v1kind: Rolemetadata:name: kube-state-metrics-resizernamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcilerules:- apiGroups: [""]resources:- podsverbs: ["get"]- apiGroups: ["extensions"]resources:- deploymentsresourceNames: ["kube-state-metrics"]verbs: ["get", "update"]---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRoleBindingmetadata:name: kube-state-metricslabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: ReconcileroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: kube-state-metricssubjects:- kind: ServiceAccountname: kube-state-metricsnamespace: kube-system---apiVersion: rbac.authorization.k8s.io/v1kind: RoleBindingmetadata:name: kube-state-metricsnamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: ReconcileroleRef:apiGroup: rbac.authorization.k8s.iokind: Rolename: kube-state-metrics-resizersubjects:- kind: ServiceAccountname: kube-state-metricsnamespace: kube-system[root@k8s-master prometheus-k8s]# kubectl apply -f kube-state-metrics-rbac.yaml
- 编写Deployment和ConfigMap的yaml进行metrics pod部署,不需要进行修改
[root@k8s-master prometheus-k8s]# cat kube-state-metrics-deployment.yamlapiVersion: apps/v1kind: Deploymentmetadata:name: kube-state-metricsnamespace: kube-systemlabels:k8s-app: kube-state-metricskubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcileversion: v1.3.0spec:selector:matchLabels:k8s-app: kube-state-metricsversion: v1.3.0replicas: 1template:metadata:labels:k8s-app: kube-state-metricsversion: v1.3.0annotations:scheduler.alpha.kubernetes.io/critical-pod: ''spec:priorityClassName: system-cluster-criticalserviceAccountName: kube-state-metricscontainers:- name: kube-state-metricsimage: lizhenliang/kube-state-metrics:v1.3.0ports:- name: http-metricscontainerPort: 8080- name: telemetrycontainerPort: 8081readinessProbe:httpGet:path: /healthzport: 8080initialDelaySeconds: 5timeoutSeconds: 5- name: addon-resizerimage: lizhenliang/addon-resizer:1.8.3resources:limits:cpu: 100mmemory: 30Mirequests:cpu: 100mmemory: 30Mienv:- name: MY_POD_NAMEvalueFrom:fieldRef:fieldPath: metadata.name- name: MY_POD_NAMESPACEvalueFrom:fieldRef:fieldPath: metadata.namespacevolumeMounts:- name: config-volumemountPath: /etc/configcommand:- /pod_nanny- --config-dir=/etc/config- --container=kube-state-metrics- --cpu=100m- --extra-cpu=1m- --memory=100Mi- --extra-memory=2Mi- --threshold=5- --deployment=kube-state-metricsvolumes:- name: config-volumeconfigMap:name: kube-state-metrics-config---# Config map for resource configuration.apiVersion: v1kind: ConfigMapmetadata:name: kube-state-metrics-confignamespace: kube-systemlabels:k8s-app: kube-state-metricskubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconciledata:NannyConfiguration: |-apiVersion: nannyconfig/v1alpha1kind: NannyConfiguration[root@k8s-master prometheus-k8s]# kubectl apply -f kube-state-metrics-deployment.yaml
- 编写Service的yaml对metrics进行端口暴露
[root@k8s-master prometheus-k8s]# cat kube-state-metrics-service.yamlapiVersion: v1kind: Servicemetadata:name: kube-state-metricsnamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcilekubernetes.io/name: "kube-state-metrics"annotations:prometheus.io/scrape: 'true'spec:ports:- name: http-metricsport: 8080targetPort: http-metricsprotocol: TCP- name: telemetryport: 8081targetPort: telemetryprotocol: TCPselector:k8s-app: kube-state-metrics[root@k8s-master prometheus-k8s]# kubectl apply -f kube-state-metrics-service.yaml
- 检查pod和svc的状态,可以看到正常运行了pod/kube-state-metrics-7c76bdbf68-kqqgd 和对外暴露了8080和8081端口
[root@k8s-master prometheus-k8s]# kubectl get pod,svc -n kube-systemNAME READY STATUS RESTARTS AGEpod/alertmanager-5d75d5688f-fmlq6 2/2 Running 0 9dpod/coredns-5bd5f9dbd9-wv45t 1/1 Running 1 9dpod/grafana-0 1/1 Running 2 15dpod/kube-state-metrics-7c76bdbf68-kqqgd 2/2 Running 6 14dpod/kubernetes-dashboard-7d77666777-d5ng4 1/1 Running 5 16dpod/prometheus-0 2/2 Running 6 15dNAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGEservice/alertmanager ClusterIP 10.0.0.207 <none> 80/TCP 13dservice/grafana NodePort 10.0.0.74 <none> 80:30091/TCP 15dservice/kube-dns ClusterIP 10.0.0.2 <none> 53/UDP,53/TCP 14dservice/kube-state-metrics ClusterIP 10.0.0.194 <none> 8080/TCP,8081/TCP 14dservice/kubernetes-dashboard NodePort 10.0.0.127 <none> 443:30001/TCP 17dservice/prometheus NodePort 10.0.0.33 <none> 9090:30090/TCP 14d[root@k8s-master prometheus-k8s]#
5 使用Grafana可视化展示Prometheus监控数据
通常在使用Prometheus采集数据的时候我们需要监控K8S集群中Pod、Node、资源对象,因此我们需要安装对应的插件和资源采集器来提供api进行数据获取,在4.3中我们已经配置好,我们也可以使用Prometheus的UI界面中的Staus菜单下的Target中的各个采集器的状态情况,如图所示:

只有当我们各个Target的状态都是UP状态时,我们可以使用自带的的界面去获取到某一监控项的相关的数据,如图所示:
从上面的图中可以看出Prometheus的界面可视化展示的功能较单一,不能满足需求,因此我们需要结合Grafana来进行可视化展示Prometheus监控数据,在上一章节,已经成功部署了Granfana,因此需要在使用的时候添加dashboard和Panel来设计展示相关的监控项,但是实际上在Granfana社区里面有很多成熟的模板,我们可以直接使用,然后根据自己的环境修改Panel中的查询语句来获取数据
https://grafana.com/grafana/dashboards
推荐模板:
- 集群资源监控:3119
当模板添加之后如果某一个Panel不显示数据,可以点击Panel上的编辑,查询PromQL语句,然后去Prometheus自己的界面上进行调试PromQL语句是否可以获取到值,最后调整之后的监控界面如图所示
资源状态监控:6417
同理,添加资源状态的监控模板,然后经过调整之后的监控界面如图所示,可以获取到k8s中各种资源状态的监控展示
Node监控:9276
同理,添加资源状态的监控模板,然后经过调整之后的监控界面如图所示,可以获取到各个node上的基本情况
6 在K8S中部署Alertmanager
6.1 部署Alertmanager
6.2 部署告警
我们以Email来进行实现告警信息的发送
- 首先需要准备一个发件邮箱,开启stmp发送功能
- 使用configmap存储告警规则,编写报警规则的yaml文件,可根据自己的实际情况进行修改和添加报警的规则,prometheus比zabbix就麻烦在这里,所有的告警规则需要自己去定义
[root@k8s-master prometheus-k8s]# vim prometheus-rules.yamlapiVersion: v1kind: ConfigMapmetadata:name: prometheus-rulesnamespace: kube-systemdata:general.rules: |groups:- name: general.rulesrules:- alert: InstanceDownexpr: up == 0for: 1mlabels:severity: errorannotations:summary: "Instance {{ $labels.instance }} 停止工作"description: "{{ $labels.instance }} job {{ $labels.job }} 已经停止5分钟以上."node.rules: |groups:- name: node.rulesrules:- alert: NodeFilesystemUsageexpr: 100 - (node_filesystem_free_bytes{fstype=~"ext4|xfs"} / node_filesystem_size_bytes{fstype=~"ext4|xfs"} * 100) > 80for: 1mlabels:severity: warningannotations:summary: "Instance {{ $labels.instance }} : {{ $labels.mountpoint }} 分区使用率过高"description: "{{ $labels.instance }}: {{ $labels.mountpoint }} 分区使用大于80% (当前值: {{ $value }})"- alert: NodeMemoryUsageexpr: 100 - (node_memory_MemFree_bytes+node_memory_Cached_bytes+node_memory_Buffers_bytes) / node_memory_MemTotal_bytes * 100 > 80for: 1mlabels:severity: warningannotations:summary: "Instance {{ $labels.instance }} 内存使用率过高"description: "{{ $labels.instance }}内存使用大于80% (当前值: {{ $value }})"- alert: NodeCPUUsageexpr: 100 - (avg(irate(node_cpu_seconds_total{mode="idle"}[5m])) by (instance) * 100) > 60for: 1mlabels:severity: warningannotations:summary: "Instance {{ $labels.instance }} CPU使用率过高"description: "{{ $labels.instance }}CPU使用大于60% (当前值: {{ $value }})"[root@k8s-master prometheus-k8s]# kubectl apply -f prometheus-rules.yaml
- 编写告警configmap的yaml文件部署,增加alertmanager告警配置,进行配置邮箱发送地址
[root@k8s-master prometheus-k8s]# vim alertmanager-configmap.yamlapiVersion: v1kind: ConfigMapmetadata:name: alertmanager-confignamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: EnsureExistsdata:alertmanager.yml: |global:resolve_timeout: 5msmtp_smarthost: 'mail.goldwind.com.cn:587' #登陆邮件进行查看smtp_from: 'goldwindscada@goldwind.com.cn' #根据自己申请的发件邮箱进行配置smtp_auth_username: 'goldwindscada@goldwind.com.cn'smtp_auth_password: 'Dbadmin@123'receivers:- name: default-receiveremail_configs:- to: "zhangdongdong27459@goldwind.com.cn"route:group_interval: 1mgroup_wait: 10sreceiver: default-receiverrepeat_interval: 1m[root@k8s-master prometheus-k8s]# kubectl apply -f alertmanager-configmap.yaml
- 创建PVC进行数据持久化,我这个yaml文件使用的跟Prometheus安装时用的存储类来进行自动供给,需要根据自己的实际情况修改
[root@k8s-master prometheus-k8s]# vim alertmanager-pvc.yamlapiVersion: v1kind: PersistentVolumeClaimmetadata:name: alertmanagernamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: EnsureExistsspec:storageClassName: managed-nfs-storageaccessModes:- ReadWriteOnceresources:requests:storage: "2Gi"[root@k8s-master prometheus-k8s]# kubectl apply -f alertmanager-pvc.yaml
- 编写deployment的yaml来部署alertmanager的pod
[root@k8s-master prometheus-k8s]# vim alertmanager-deployment.yamlapiVersion: apps/v1kind: Deploymentmetadata:name: alertmanagernamespace: kube-systemlabels:k8s-app: alertmanagerkubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcileversion: v0.14.0spec:replicas: 1selector:matchLabels:k8s-app: alertmanagerversion: v0.14.0template:metadata:labels:k8s-app: alertmanagerversion: v0.14.0annotations:scheduler.alpha.kubernetes.io/critical-pod: ''spec:priorityClassName: system-cluster-criticalcontainers:- name: prometheus-alertmanagerimage: "prom/alertmanager:v0.14.0"imagePullPolicy: "IfNotPresent"args:- --config.file=/etc/config/alertmanager.yml- --storage.path=/data- --web.external-url=/ports:- containerPort: 9093readinessProbe:httpGet:path: /#/statusport: 9093initialDelaySeconds: 30timeoutSeconds: 30volumeMounts:- name: config-volumemountPath: /etc/config- name: storage-volumemountPath: "/data"subPath: ""resources:limits:cpu: 10mmemory: 50Mirequests:cpu: 10mmemory: 50Mi- name: prometheus-alertmanager-configmap-reloadimage: "jimmidyson/configmap-reload:v0.1"imagePullPolicy: "IfNotPresent"args:- --volume-dir=/etc/config- --webhook-url=http://localhost:9093/-/reloadvolumeMounts:- name: config-volumemountPath: /etc/configreadOnly: trueresources:limits:cpu: 10mmemory: 10Mirequests:cpu: 10mmemory: 10Mivolumes:- name: config-volumeconfigMap:name: alertmanager-config- name: storage-volumepersistentVolumeClaim:claimName: alertmanager[root@k8s-master prometheus-k8s]# kubectl apply -f alertmanager-deployment.yaml
- 创建 alertmanager的service对外暴露的端口
[root@k8s-master prometheus-k8s]# vim alertmanager-service.yamlapiVersion: v1kind: Servicemetadata:name: alertmanagernamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcilekubernetes.io/name: "Alertmanager"spec:ports:- name: httpport: 80protocol: TCPtargetPort: 9093selector:k8s-app: alertmanagertype: "ClusterIP"[root@k8s-master prometheus-k8s]# kubectl apply -f alertmanager-service.yaml
- 检测部署状态,可以发现pod/alertmanager-5d75d5688f-fmlq6和service/alertmanager正常运行
[root@k8s-master prometheus-k8s]# kubectl get pod,svc -n kube-system -o wideNAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATESpod/alertmanager-5d75d5688f-fmlq6 2/2 Running 4 10d 172.17.15.2 192.168.73.140 <none> <none>pod/coredns-5bd5f9dbd9-qxvmz 1/1 Running 0 42m 172.17.33.2 192.168.73.138 <none> <none>pod/grafana-0 1/1 Running 3 16d 172.17.31.2 192.168.73.139 <none> <none>pod/kube-state-metrics-7c76bdbf68-hv56m 2/2 Running 0 23h 172.17.15.3 192.168.73.140 <none> <none>pod/kubernetes-dashboard-7d77666777-d5ng4 1/1 Running 6 17d 172.17.31.4 192.168.73.139 <none> <none>pod/prometheus-0 2/2 Running 8 16d 172.17.83.2 192.168.73.135 <none> <none>NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTORservice/alertmanager ClusterIP 10.0.0.207 <none> 80/TCP 14d k8s-app=alertmanagerservice/grafana NodePort 10.0.0.74 <none> 80:30091/TCP 16d app=grafanaservice/kube-dns ClusterIP 10.0.0.2 <none> 53/UDP,53/TCP 42m k8s-app=kube-dnsservice/kube-state-metrics ClusterIP 10.0.0.194 <none> 8080/TCP,8081/TCP 15d k8s-app=kube-state-metricsservice/kubernetes-dashboard NodePort 10.0.0.127 <none> 443:30001/TCP 18d k8s-app=kubernetes-dashboardservice/prometheus NodePort 10.0.0.33 <none> 9090:30090/TCP 15d k8s-app=prometheus
6.3 测试告警发送
k8s实战之部署Prometheus+Grafana可视化监控告警平台的更多相关文章
- Spring Boot 微服务应用集成Prometheus + Grafana 实现监控告警
Spring Boot 微服务应用集成Prometheus + Grafana 实现监控告警 一.添加依赖 1.1 Actuator 的 /prometheus端点 二.Prometheus 配置 部 ...
- Prometheus+Grafana企业监控系统
Prometheus+Grafana企业监控系统 作者 刘畅 实验配置: 主机名称 Ip地址 controlnode 172.16.1.70/24 slavenode1 172.16.1.71/24 ...
- 基于k8s集群部署prometheus监控ingress nginx
目录 基于k8s集群部署prometheus监控ingress nginx 1.背景和环境概述 2.修改prometheus配置 3.检查是否生效 4.配置grafana图形 基于k8s集群部署pro ...
- 基于k8s集群部署prometheus监控etcd
目录 基于k8s集群部署prometheus监控etcd 1.背景和环境概述 2.修改prometheus配置 3.检查是否生效 4.配置grafana图形 基于k8s集群部署prometheus监控 ...
- go-zero docker-compose 搭建课件服务(七):prometheus+grafana服务监控
0.转载 go-zero docker-compose 搭建课件服务(七):prometheus+grafana服务监控 0.1源码地址 https://github.com/liuyuede123/ ...
- Prometheus Grafana可视化展示Linux资源使用率
Prometheus Grafana可视化展示Linux资源使用率 Grfana官方仪表盘下载:https://grafana.com/dashboards 数据源推荐:https://grafan ...
- 部署Prometheus+Grafana监控
Prometheus 1.不是很友好,各种配置都手写 2.对docker和k8s监控有成熟解决方案 Prometheus(普罗米修斯) 是一个最初在SoudCloud上构建的监控系统,开源项目,拥有非 ...
- Rancher2.x 一键式部署 Prometheus + Grafana 监控 Kubernetes 集群
目录 1.Prometheus & Grafana 介绍 2.环境.软件准备 3.Rancher 2.x 应用商店 4.一键式部署 Prometheus 5.验证 Prometheus + G ...
- k8b部署prometheus+grafana
来源: https://juejin.im/post/5c36054251882525a50bbdf0 https://github.com/redhatxl/k8s-prometheus-grafa ...
随机推荐
- 「MySql高级查询与编程」练习:企业员工管理
题目:企业员工管理 一.语言和环境 1.实现语言:SQL. 2.开发环境:MySQL,navicat for mysql. 二.题目(100分): 1.创建数据库及数据表: (1)创建数据库,名称为d ...
- x86-2-保护模式
x86-2-保护模式 操作系统负责计算机上的所有软件和硬件的管理,它可以百分百操作计算机的所有内容.但是,操作系统上编写的用户程序却应当有所限制,只允许用户程序访问属于自己程序的内容,不然整个生态就很 ...
- Windows实现桌面录屏、指定窗口录制直播,低延时,H5页面播放
接着前面记录的3种方式实现桌面推流直播: 1.Windows 11实现录屏直播,搭建Nginx的rtmp服务 的方式需要依赖与Flash插件,使用场景有限 2.Windows 11实现直播,VLC超简 ...
- Python_获取全部异常信息
import traceback try: os.getcwd('exc') except Exception: exc = traceback.format_exc() print(exc)
- vue2.0与vue3.0项目创建
脚手架安装与卸载 安装 npm install -g vue-cli //or npm install -g @vue/cli 卸载 npm uninstall -g vue-cli //or npm ...
- Typora+PicGo-Core实现图片自动上传gitee图床
说明: 使用gitee作为图床: 客户机为Mac M1: Typora版本:1.0.2 (5990). gitee配置步骤 需要拥有一个gitee账号,创建一个公有仓库用于存储图片,然后需要生成一个t ...
- 使用Crossplane构建专属PaaS体验:Kubernetes,OAM和CoreWorkflows
关键点:•许多组织的目标是构建自己的云平台,这些平台通常由内部部署架构和云供应商共建完成.•虽然Kubernetes没有提供开箱即用的完整PaaS平台式服务,但其具备完整的API,清晰的技术抽取和易理 ...
- 手把手教你分析解决MySQL死锁问题
在生产环境中如果出现MySQL死锁问题该如何排查和解决呢,本文将模拟真实死锁场景进行排查,最后总结下实际开发中如何尽量避免死锁发生. 一.准备好相关数据和环境 当前自己的数据版本是8.0.22 mys ...
- 【分享】让prometheus支持PUSH模式,可以使用remote write协议推送数据
2021-10-21补充: 我通过修改源码来让prometheus支持remote-write,纯属多此一举: --enable-feature=remote-write-receiver这个命令行参 ...
- CesiumJS新增官方TypeScript类型定义
Cesium中文网:http://cesiumcn.org/ | 国内快速访问:http://cesium.coinidea.com/ 在当前的1.70版本中,CesiumJS现在附带了正式的Type ...
