Spring Boot OAuth 2.0 客户端
在上一篇《OAuth 2.0 授权码请求》中我们已经可以获取到access_token了,本节将使用客户端来访问远程资源
配置资源服务器
授权服务器负责生成并发放访问令牌(access_token),客户端在访问受保护的资源时会带上访问令牌,资源服务器需要解析并验证客户端带的这个访问令牌。
如果你的资源服务器同时也是一个授权服务器(资源服务器和授权服务器在一起),那么资源服务器就不需要考虑令牌解析的事情了,否则这一步是不可或缺的。
To use the access token you need a Resource Server (which can be the same as the Authorization Server). Creating a Resource Server is easy, just add @EnableResourceServer and provide some configuration to allow the server to decode access tokens. If your application is also an Authorization Server it already knows how to decode tokens, so there is nothing else to do. If your app is a standalone service then you need to give it some more configuration.
同时,把它们放在一起的话还有一个问题需要注意,我们知道过滤器是顺序执行的,因此需要确保那些通过访问令牌来访问的资源路径不能被主过滤拦下了,需要单独摘出来。
Note: if your Authorization Server is also a Resource Server then there is another security filter chain with lower priority controlling the API resources. Fo those requests to be protected by access tokens you need their paths not to be matched by the ones in the main user-facing filter chain, so be sure to include a request matcher that picks out only non-API resources in the WebSecurityConfigurer above.
关于Spring Security中过滤器的顺序可以参见
https://docs.spring.io/spring-security/site/docs/5.0.6.RELEASE/reference/htmlsingle/#filter-ordering
这里偷个懒将它们放在一起:
package com.cjs.example.config; import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableResourceServer;
import org.springframework.security.oauth2.config.annotation.web.configuration.ResourceServerConfigurerAdapter;
import org.springframework.security.oauth2.config.annotation.web.configurers.ResourceServerSecurityConfigurer;
import org.springframework.security.oauth2.provider.expression.OAuth2WebSecurityExpressionHandler; @Configuration
@EnableResourceServer
public class ResourceServerConfig extends ResourceServerConfigurerAdapter { @Override
public void configure(ResourceServerSecurityConfigurer resources) throws Exception {
super.configure(resources);
} /**
* 用于配置对受保护的资源的访问规则
* 默认情况下所有不在/oauth/**下的资源都是受保护的资源
* {@link OAuth2WebSecurityExpressionHandler}
*/
@Override
public void configure(HttpSecurity http) throws Exception {
http.requestMatchers().antMatchers("/haha/**")
.and()
.authorizeRequests()
.anyRequest().authenticated();
}
}
这里配置很简洁,很多都用了默认的设置(比如:resourceId,accessDeniedHandler,sessionManagement等等,具体可参见源码)
接下来,看看本例中我们被保护的资源,简单的几个资源(都以/haha开头),只为测试:
package com.cjs.example.controller; import com.cjs.example.domain.UserInfo;
import org.springframework.security.access.prepost.PreAuthorize;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.RestController; import java.security.Principal; @RestController
@RequestMapping("/haha")
public class MainController { @GetMapping("/sayHello")
public String sayHello(String name) {
return "Hello, " + name;
} @PreAuthorize("hasAnyRole('ADMIN')")
@RequestMapping("/sayHi")
public String sayHi() {
return "hahaha";
} @RequestMapping("/userInfo")
public UserInfo userInfo(Principal principal) {
UserInfo userInfo = new UserInfo();
userInfo.setName(principal.getName());
return userInfo;
}
}
授权服务器配置
package com.cjs.example.config; import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.data.redis.connection.RedisConnectionFactory;
import org.springframework.security.oauth2.config.annotation.configurers.ClientDetailsServiceConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableAuthorizationServer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerSecurityConfigurer;
import org.springframework.security.oauth2.provider.token.TokenStore;
import org.springframework.security.oauth2.provider.token.store.redis.RedisTokenStore; @Configuration
@EnableAuthorizationServer
public class AuthorizationServerConfig extends AuthorizationServerConfigurerAdapter { @Autowired
private RedisConnectionFactory connectionFactory; @Override
public void configure(AuthorizationServerSecurityConfigurer security) throws Exception {
super.configure(security);
} @Override
public void configure(ClientDetailsServiceConfigurer clients) throws Exception {
clients.inMemory()
.withClient("my-client-1")
.secret("$2a$10$0jyHr4rGRdQw.X9mrLkVROdQI8.qnWJ1Sl8ly.yzK0bp06aaAkL9W")
.authorizedGrantTypes("authorization_code", "refresh_token")
.scopes("read", "write", "execute")
.redirectUris("http://localhost:8081/login/oauth2/code/callback");
// .redirectUris("http://www.baidu.com");
} @Override
public void configure(AuthorizationServerEndpointsConfigurer endpoints) throws Exception {
endpoints.tokenStore(tokenStore());
} @Bean
public TokenStore tokenStore() {
return new RedisTokenStore(connectionFactory);
} public static void main(String[] args) {
System.out.println(new org.apache.tomcat.util.codec.binary.Base64().encodeAsString("my-client-1:12345678".getBytes()));
System.out.println(java.util.Base64.getEncoder().encodeToString("my-client-1:12345678".getBytes()));
}
}
和之前相比,我们增加了TokenStore,将Token存储到Redis中。否则默认放在内存中的话每次重启的话token都丢了。下面是一个例子:
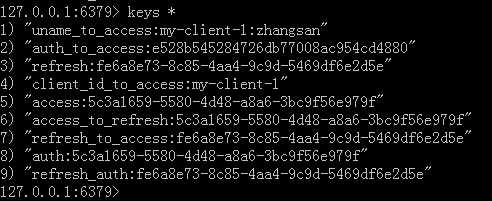
application.yml如下:
server:
port: 8080 spring:
redis:
host: 127.0.0.1
port: 6379 logging:
level:
root: debug
org.springframework.web: debug
org.springframework.security: debug
WebSecurity配置
我们有了资源,有了授权,我们还缺少用户。WebSecurity主要是配置咱们这个项目的一些安全配置,比如用户、认证、授权等等。
package com.cjs.example.config; import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.method.configuration.EnableGlobalMethodSecurity;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.builders.WebSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder; @Configuration
@EnableWebSecurity
@EnableGlobalMethodSecurity(prePostEnabled = true, proxyTargetClass = true)
public class WebSecurityConfig extends WebSecurityConfigurerAdapter { @Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.inMemoryAuthentication()
.withUser("zhangsan")
.password("$2a$10$qsJ/Oy1RmUxFA.YtDT8RJ.Y2kU3U4z0jvd35YmiMOAPpD.nZUIRMC")
.roles("USER")
.and()
.withUser("lisi")
.password("$2a$10$qsJ/Oy1RmUxFA.YtDT8RJ.Y2kU3U4z0jvd35YmiMOAPpD.nZUIRMC")
.roles("USER", "ADMIN");
} @Override
public void configure(WebSecurity web) throws Exception {
web.ignoring().antMatchers("/css/**", "/js/**", "/plugins/**", "/favicon.ico");
} @Override
protected void configure(HttpSecurity http) throws Exception {
super.configure(http);
} @Bean
public PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
} public static void main(String[] args) {
BCryptPasswordEncoder bCryptPasswordEncoder = new BCryptPasswordEncoder();
System.out.println(bCryptPasswordEncoder.encode("123456"));
System.out.println(bCryptPasswordEncoder.encode("12345678"));
}
}
这里多说两句,关于Endpoint和HttpSecurity
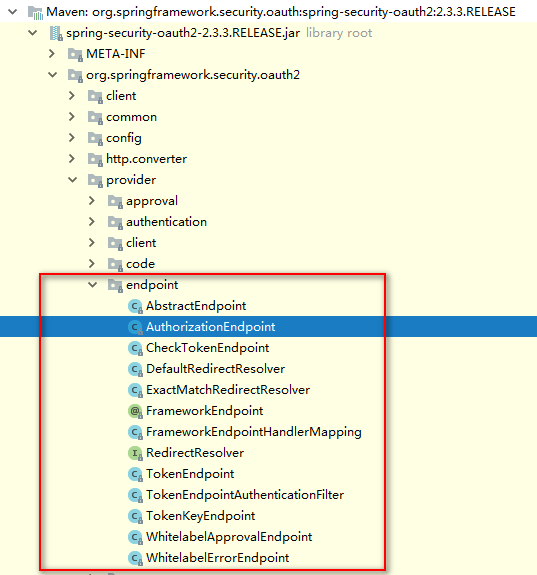
Endpoint
有很多端点我们是可以重写的,比如:/login,/oauth/token等等
HttpSecurity
很多初学者可能会不知道怎么配置HttpSecurity,这个时候其实最好的方法就是看代码或者API文档
下面一起看一下常见的几个配置
我们先来看一下,当我们继承WebSecurityConfigurerAdapter之后它的默认的HttpSecurity是怎么配置的:
// @formatter:off
protected void configure(HttpSecurity http) throws Exception {
logger.debug("Using default configure(HttpSecurity). If subclassed this will potentially override subclass configure(HttpSecurity)."); http
.authorizeRequests()
.anyRequest().authenticated()
.and()
.formLogin().and()
.httpBasic();
}
// @formatter:on
可以看到,所有的请求都需要授权,并且指定登录的uri是/login,同时支持Basic认证。
requestMatchers()
这个方法是用于限定只有特定的HttpServletRequest实例才会导致该HttpSecurity被调用,当然是通过请求uri进行限定的了。它后面可以接多个匹配规则。例如:
@Configuration
@EnableWebSecurity
public class RequestMatchersSecurityConfig extends WebSecurityConfigurerAdapter { @Override
protected void configure(HttpSecurity http) throws Exception {
http
.requestMatchers()
.antMatchers("/api/**")
.antMatchers("/oauth/**")
.and()
.authorizeRequests()
.antMatchers("/**").hasRole("USER")
.and()
.httpBasic();
} /* 与上面那段等价
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.requestMatchers()
.antMatchers("/api/**")
.and()
.requestMatchers()
.antMatchers("/oauth/**")
.and()
.authorizeRequests()
.antMatchers("/**").hasRole("USER")
.and()
.httpBasic();
}
*/ @Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth
.inMemoryAuthentication()
.withUser("user").password("password").roles("USER");
}
}
formLogin()
该方法是用于配置登录相关的设置的。例如:
@Configuration
@EnableWebSecurity
public class FormLoginSecurityConfig extends WebSecurityConfigurerAdapter { @Override
protected void configure(HttpSecurity http) throws Exception {
http.authorizeRequests().antMatchers("/**").hasRole("USER").and().formLogin()
.usernameParameter("username") // default is username
.passwordParameter("password") // default is password
.loginPage("/authentication/login") // default is /login with an HTTP get
.failureUrl("/authentication/login?failed") // default is /login?error
.loginProcessingUrl("/authentication/login/process"); // default is /login } @Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.inMemoryAuthentication().withUser("user").password("password").roles("USER");
}
}
当我们没有配置登录的时候,会用默认的登录,有默认的登录页面,还有好多默认的登录配置。具体可参见 FormLoginConfigurer.loginPage(String)方法

authorizeRequests()
该方法允许基于HttpServletRequest进行访问限制,比如角色、权限。例如:
@Configuration
@EnableWebSecurity
public class AuthorizeUrlsSecurityConfig extends WebSecurityConfigurerAdapter { @Override
protected void configure(HttpSecurity http) throws Exception {
http.authorizeRequests().antMatchers("/admin/**").hasRole("ADMIN")
.antMatchers("/**").hasRole("USER").and().formLogin();
} @Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.inMemoryAuthentication().withUser("user").password("password").roles("USER")
.and().withUser("admin").password("password").roles("ADMIN", "USER");
}
}
anyRequest()表示匹配任意请求
authenticated()表示只有认证通过的用户才可以访问
更多可以参见API文档:https://docs.spring.io/spring-security/site/docs/5.0.6.RELEASE/api/
用Postman访问资源
获取授权码
在浏览器中输入http://localhost:8080/oauth/authorize?response_type=code&client_id=my-client-1&redirect_uri=http://www.baidu.com&scope=read
然后跳到登录页面,输入用户名和密码登录,然后从重定向url中拿到code
换取访问令牌
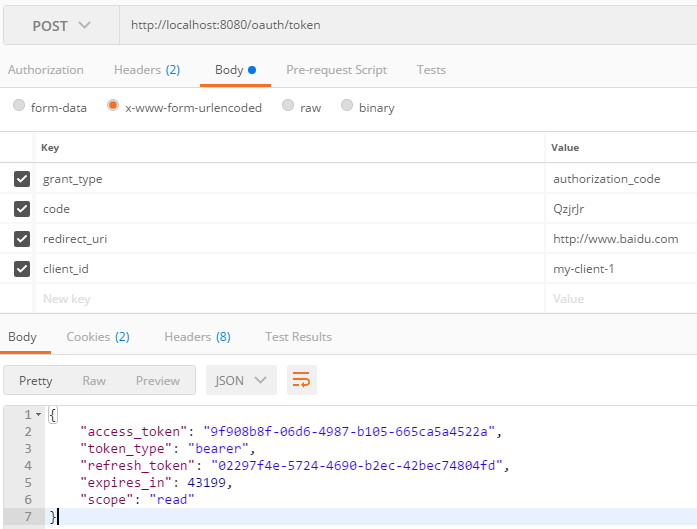
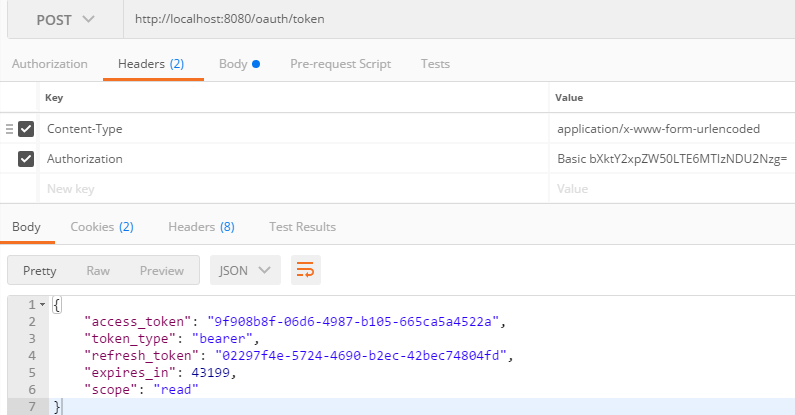
访问资源
http://localhost:8080/haha/sayHi?access_token=9f908b8f-06d6-4987-b105-665ca5a4522a
{
"error": "access_denied",
"error_description": "不允许访问"
}
这里不允许访问是因为我用zhangsan登录的,他不在ADMIN角色中
http://localhost:8080/haha/userInfo?access_token=9f908b8f-06d6-4987-b105-665ca5a4522a
{
"name": "zhangsan"
}
http://localhost:8080/haha/sayHello?name=jack&access_token=9f908b8f-06d6-4987-b105-665ca5a4522a
Hello, jack
通过客户端程序访问资源
访问GitHub
参照SpringBoot官网的示例
https://github.com/spring-projects/spring-boot/tree/master/spring-boot-samples/spring-boot-sample-oauth2-client
https://github.com/spring-projects
https://github.com/spring-projects/spring-boot
可以将代码拷下来 https://github.com/spring-projects/spring-boot.git
第一步 将我们的客户端注册到GitHub上去
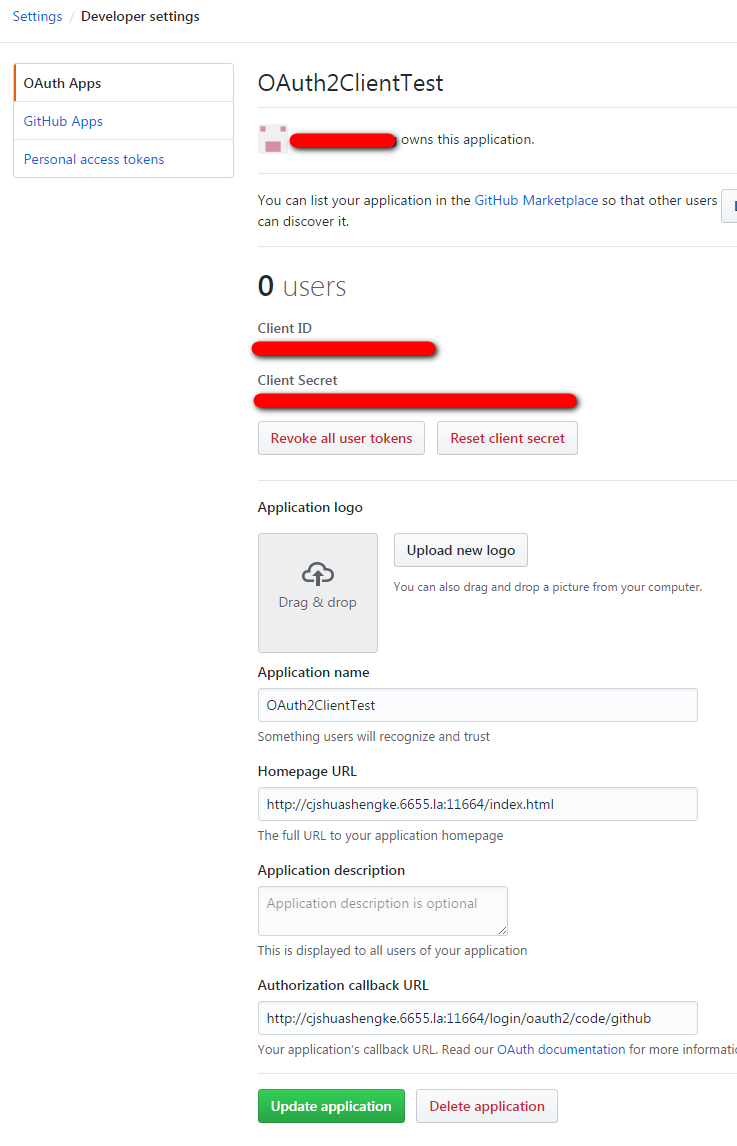
GitHub的OAuth文档在这里 https://developer.github.com/apps/building-oauth-apps/authorizing-oauth-apps/
第二步 浏览器输入http://localhost:8080/后出现如下界面
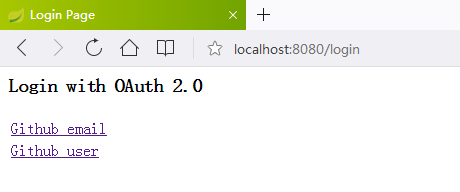
第三步 点击任意一个连接,跳GitHub登录
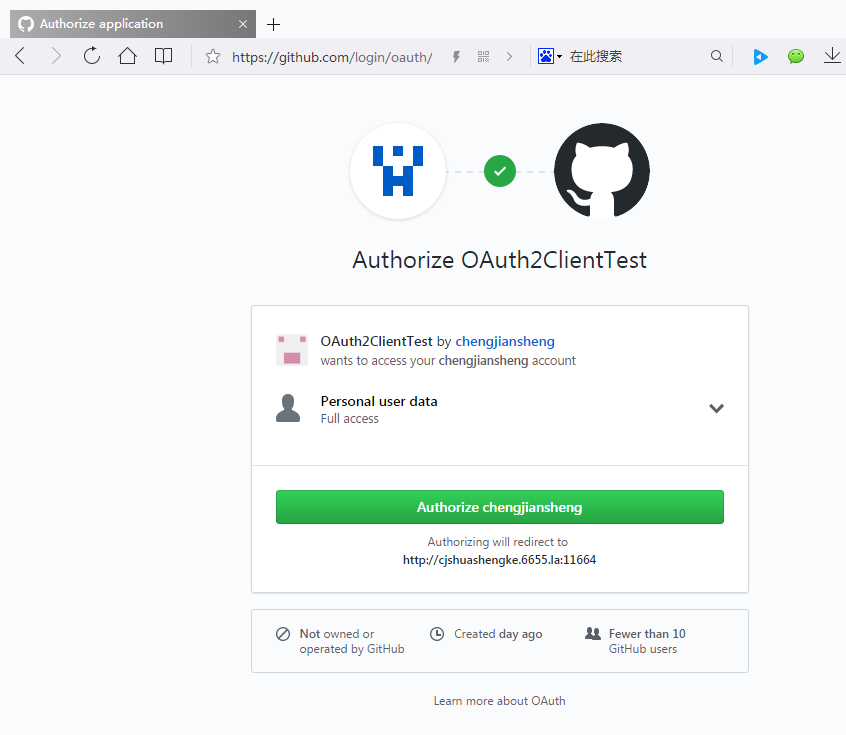
授权以后就可以重定向到我们的localhost:8080/了
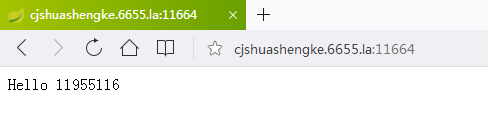
主要配置如下:
APP-CLIENT-ID: 7e304109d91ed8e9bf72
APP-CLIENT-SECRET: 003daa47fa0f350d181c8741d8bac6833aef568a spring:
security:
oauth2:
client:
registration:
github-client-1:
client-id: ${APP-CLIENT-ID}
client-secret: ${APP-CLIENT-SECRET}
client-name: Github user
provider: github
scope: user
redirect-uri-template: http://cjshuashengke.6655.la:11664/login/oauth2/code/github
github-client-2:
client-id: ${APP-CLIENT-ID}
client-secret: ${APP-CLIENT-SECRET}
client-name: Github email
provider: github
scope: user:email
redirect-uri-template: http://cjshuashengke.6655.la:11664/login/oauth2/code/github
pom.xml如下
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion> <groupId>sample.oauth2.client</groupId>
<artifactId>spring-boot-sample-oauth2-client</artifactId>
<version>0.0.1-SNAPSHOT</version>
<packaging>jar</packaging> <parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.0.3.RELEASE</version>
<relativePath/> <!-- lookup parent from repository -->
</parent> <properties>
<project.build.sourceEncoding>UTF-8</project.build.sourceEncoding>
<project.reporting.outputEncoding>UTF-8</project.reporting.outputEncoding>
<java.version>1.8</java.version>
</properties> <dependencies>
<!-- Compile -->
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-config</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-oauth2-client</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-oauth2-jose</artifactId>
</dependency>
<!-- Test -->
<dependency>
<groupId>org.apache.httpcomponents</groupId>
<artifactId>httpclient</artifactId>
<scope>test</scope>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>
启动类
package sample.oauth2.client; import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication; @SpringBootApplication
public class SampleOAuth2ClientApplication { public static void main(String[] args) {
SpringApplication.run(SampleOAuth2ClientApplication.class);
} }
ExampleController
package sample.oauth2.client; import java.security.Principal; import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.RestController; @RestController
public class ExampleController { @RequestMapping("/")
public String email(Principal principal) {
return "Hello " + principal.getName();
} }
访问自定义的Provider
在这里我遇到一些问题,将provider换成自己的localhost:8080就总是报错,不知道什么原因。
想想还是写出来吧,希望有大神看到帮我指点迷津。。。
首先需要明确一点:Spring Security OAuth2提供了一套客户端实现,Spring Boot也有它自己的方式。
这里我是按照Spring Boot的那一套来的
Spring Boot最大的优点莫过于自动配置了
只要在你的classpath下有spring-security-oauth2-client,那么将会自动配置OAuth2 Client。
配置的属性用的是OAuth2ClientProperties
例如:
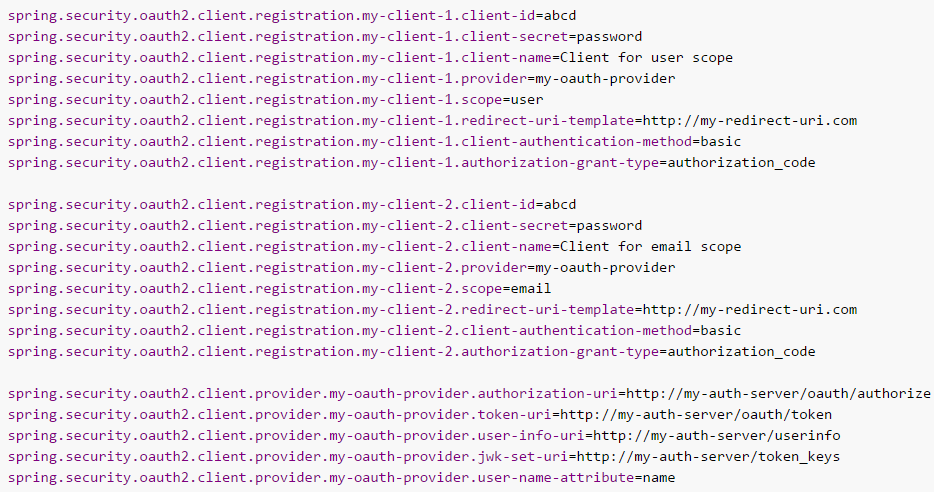
默认情况下,Spring Security的OAuth2LoginAuthenticationFilter只处理URL匹配/login/oauth2/code/*的请求。
如果你想自定义redirect-uri-template可以在WebSecurityConfigurerAdapter中配置。例如:
public class OAuth2LoginSecurityConfig extends WebSecurityConfigurerAdapter {
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.anyRequest().authenticated()
.and()
.oauth2Login()
.redirectionEndpoint()
.baseUri("/custom-callback");
}
}
其实,不仅仅可以自定义重定向端点,其它的比如授权端点也是可以自定义的,可参见源码
下面重点说下我的配置
pom.xml
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion> <groupId>com.cjs.example</groupId>
<artifactId>cjs-oauth2-code-client</artifactId>
<version>0.0.1-SNAPSHOT</version>
<packaging>jar</packaging> <name>cjs-oauth2-code-client</name>
<description></description> <parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.0.2.RELEASE</version>
<relativePath/> <!-- lookup parent from repository -->
</parent> <properties>
<project.build.sourceEncoding>UTF-8</project.build.sourceEncoding>
<project.reporting.outputEncoding>UTF-8</project.reporting.outputEncoding>
<java.version>1.8</java.version>
</properties> <dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-config</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-oauth2-client</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-oauth2-jose</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.security.oauth</groupId>
<artifactId>spring-security-oauth2</artifactId>
<version>2.3.3.RELEASE</version>
</dependency> <dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
</dependencies> <build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build> </project>
application.yml
server:
port: 8081 spring:
security:
oauth2:
client:
registration:
my-client-1:
client-id: my-client-1
client-secret: 12345678
client-name: ABC
provider: my-oauth-provider
scope: read
redirect-uri-template: http://localhost:8081/login/oauth2/code/callback
client-authentication-method: basic
authorization-grant-type: authorization_code
provider:
my-oauth-provider:
authorization-uri: http://localhost:8080/oauth/authorize
token-uri: http://localhost:8080/oauth/token
logging:
level:
root: debug
分别启动两个项目
浏览器输入http://localhost:8080/test
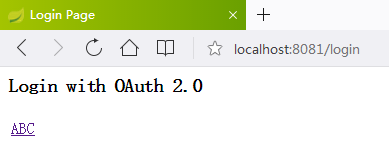
点击链接ABC
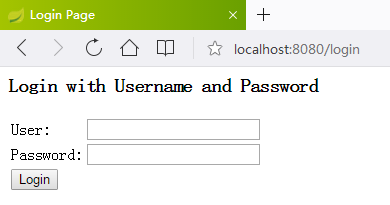
输入zhangsan/123456,结果报错了
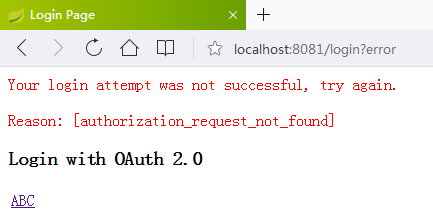
查看控制台错误信息
org.springframework.security.oauth2.core.OAuth2AuthenticationException: [authorization_request_not_found]
at org.springframework.security.oauth2.client.web.OAuth2LoginAuthenticationFilter.attemptAuthentication(OAuth2LoginAuthenticationFilter.java:146)
at org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter.doFilter(AbstractAuthenticationProcessingFilter.java:212)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) [spring-security-web-5.0.5.RELEASE.jar:5.0.5.RELEASE]
at org.springframework.security.oauth2.client.web.OAuth2AuthorizationRequestRedirectFilter.doFilterInternal(OAuth2AuthorizationRequestRedirectFilter.java:128)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:107) [spring-web-5.0.6.RELEASE.jar:5.0.6.RELEASE]
打端点,发现重定向过来的HttpServletRequest中session=null
正常情况下session不应该是null,而且属性中还应该有一个key为org.springframework.security.oauth2.client.web.HttpSessionOAuth2AuthorizationRequestRepository.AUTHORIZATION_REQUEST的属性的
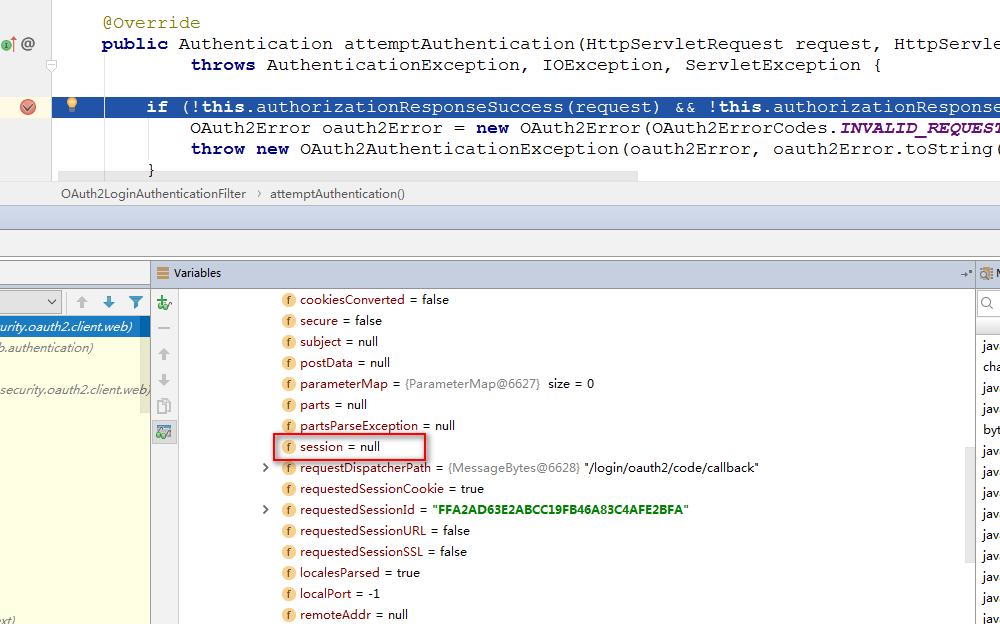

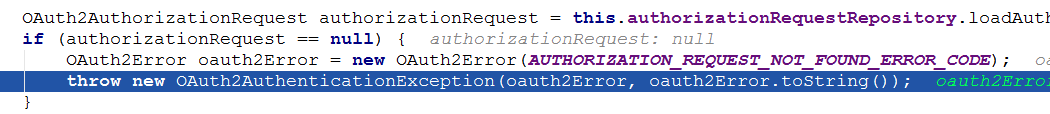
后来看根据Spring Security那一套说用@EnableOAuth2Client
利用OAuth2RestTemplate来访问资源,具体参见《Spring Security OAuth 2.0》
但是我发现加了这些问题依旧,根本问题是服务端带着code重定向到客户端的时候就失败了
在客户端收到的重定向请求中session为null
不知道大家有没有遇到这种问题,求路过的大神们支招。。。
下面贴出客户端完整代码
package com.cjs.example.controller; import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.oauth2.client.OAuth2RestTemplate;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.GetMapping; import java.security.Principal; @Controller
public class MainController { @Autowired
private OAuth2RestTemplate oAuth2RestTemplate; @GetMapping("/test")
public String test(Principal principal) {
return "Hello, " + principal.getName();
} @GetMapping("/hello")
public String hello() {
return oAuth2RestTemplate.getForObject("http://localhost:8080/sayHi", String.class);
}
}
package com.cjs.example; import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
import org.springframework.security.oauth2.client.OAuth2ClientContext;
import org.springframework.security.oauth2.client.OAuth2RestTemplate;
import org.springframework.security.oauth2.client.token.grant.code.AuthorizationCodeResourceDetails;
import org.springframework.context.annotation.Bean;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableOAuth2Client; @EnableOAuth2Client
@SpringBootApplication
public class CjsOauth2CodeClientApplication { public static void main(String[] args) {
SpringApplication.run(CjsOauth2CodeClientApplication.class, args);
} @Autowired
private OAuth2ClientContext oauth2ClientContext; @Bean
public OAuth2RestTemplate restTemplate() {
return new OAuth2RestTemplate(new AuthorizationCodeResourceDetails(), oauth2ClientContext);
}
}
工程截图
代码上传至 https://github.com/chengjiansheng/cjs-oauth2-example.git
参考
https://docs.spring.io/spring-security/site/docs/5.0.6.RELEASE/api/
https://github.com/spring-projects/spring-boot/tree/master/spring-boot-samples
https://segmentfault.com/a/1190000012309216
https://www.jianshu.com/p/bf5dd33aea6d?utm_source=oschina-app
https://www.aliyun.com/jiaocheng/800606.html
https://blog.csdn.net/peter1220/article/details/52413250
https://blog.csdn.net/weixin_42033269/article/details/80086422
Spring Boot OAuth 2.0 客户端的更多相关文章
- Spring Boot Security Oauth2之客户端模式及密码模式实现
Spring Boot Security Oauth2之客户端模式及密码模式实现 示例主要内容 1.多认证模式(密码模式.客户端模式) 2.token存到redis支持 3.资源保护 4.密码模式用户 ...
- Spring Security OAuth 2.0
续·前一篇<OAuth 2.0> OAuth 2.0 Provider 实现 在OAuth 2.0中,provider角色事实上是把授权服务和资源服务分开,有时候它们也可能在同一个应用中, ...
- (转)Spring Boot 2 (九):【重磅】Spring Boot 2.1.0 权威发布
http://www.ityouknow.com/springboot/2018/11/03/spring-boot-2.1.html 如果这两天登录 https://start.spring.io/ ...
- 【重磅】Spring Boot 2.1.0 权威发布
如果这两天登录 https://start.spring.io/ 就会发现,Spring Boot 默认版本已经升到了 2.1.0.这是因为 Spring Boot 刚刚发布了 2.1.0 版本,我们 ...
- Spring Boot 2.4.0 正式发布!全新的配置处理机制,拥抱云原生!
2020年11月12日,Spring官方发布了Spring Boot 2.4.0 GA的公告. 在这个版本中增加了大量的新特性和改进,下面我们一起看看在这个重要版本中都有哪些值得关注的内容! 更新内容 ...
- Spring Boot 2.3.0 新特性Redis 拓扑动态感应
本文为原创文章.欢迎任何形式的转载,但请务必注明出处 冷冷https://lltx.github.io. Spring Boot 2.3 新特性优雅停机详解 Spring Boot 2.3 新特性分层 ...
- Spring Boot 2.5.0 重新设计的spring.sql.init 配置有啥用?
前几天Spring Boot 2.5.0发布了,其中提到了关于Datasource初始化机制的调整,有读者私信想了解这方面做了什么调整.那么今天就要详细说说这个重新设计的配置内容,并结合实际情况说说我 ...
- Spring Boot 2.5.0 重新设计的spring.sql.init 配置有何用?
前几天Spring Boot 2.5.0发布了,其中提到了关于Datasource初始化机制的调整,有读者私信想了解这方面做了什么调整.那么今天就要详细说说这个重新设计的配置内容,并结合实际情况说说我 ...
- Spring Boot 2.7.0发布,2.5停止维护,节奏太快了吧
这几天是Spring版本日,很多Spring工件都发布了新版本, Spring Framework 6.0.0 发布了第 4 个里程碑版本,此版本包含所有针对 5.3.20 的修复补丁,以及特定于 6 ...
随机推荐
- ISP PIPLINE (十五) AF
主流的AF: CDAF, PDAF, laser assist AF(这个只是辅助,在微距或者拍摄纹理不明显的场景下好用). AF的大致原理就是检测图像锐度或者等价于锐度的参数,推动马达实现合焦或者对 ...
- 平时作业七 Java
以下是几本计算机书籍的基本信息编号 书名 价格 出版社1 JAVA基础 32 清华大学出版社2 JAVA WEB开发 40 电子工业出版社3 面向对象程序设计 28 清华大学出版社4 Struts开发 ...
- angular1.3 video
video标签动态获取播放链接是出现 Error: $interpolate:interr Interpolation Error Error: $sce:insecurl Processing of ...
- 【安全性测试】解决关于appscan基于登录会话检测失败问题
有些问题久了忽然就想通怎么解决了,很神奇.这次要说的是,关于appscan无法检测到会话的问题,因为在百度上一直找不到相关的解决方法,这个问题困扰了我很久,今天终于找到方法解决了! 日常配置扫描内容: ...
- vue 使用瞬间
vue 使用瞬间 一, 图片类 <img :src="data.deptLogo | imgUrl" onerror="this.src='../img/headD ...
- 快速幂 ,快速幂优化,矩形快速幂(java)
快速幂形式 public static int f(int a,int b,int c){ int ans =1; int base=a; while(b!=0){ if((b&1)!=0) ...
- Vue(三十二)SSR服务端渲染Nuxt.js
初始化Nuxt.js项目步骤 1.使用脚手架工具 create-nuxt-app 创建Nuxt项目 使用yarn或者npm $ yarn create nuxt-app <项目名> 注:根 ...
- iOS逆向工程概述(转)
逆向工程一词,对很多人来说可能很陌生,在android领域,我们经常会听到“反编译某个apk”,那么逆向工程从某种角度讲也包括反编译这项技术,这样一对比,可能我们就更容易理解逆向工程的定义了. 我们引 ...
- dedecms 后台可以上传mp4,但无法选择
原文链接 找到 /include/dialog/select_media.php 找到rmvb,在其后面加 “|mp4” 即可. 1
- Shell 脚本处理用户输入
传递参数 跟踪参数 移动变量 处理选项 将选项标准化 获得用户的输入 bash shell提供了一些不同的方法来从用户处获取数据,包括命令行参数(添加在命令后数据),命令行选项(可以修改命令行为的单个 ...
