Ethical Hacking - GAINING ACCESS(2)
Server Side Attacks - INFORMATION GATHERING
- Need an IP address.
- Very simple if target is on the same network (netdiscover or zenmap).
- If target has a domain, then a simple ping will return its IP.
> ping www.XXXX.com
- Getting the IP is tricker if the target is a personal computer, might be useless if the target is accessing the internet through a network as the IP will be the router IP and not the targets, client side attacks are more effective in this case as reverse connetcion can be use.
INFORMATION GATHERING
- Try default password(ssh iPad case).
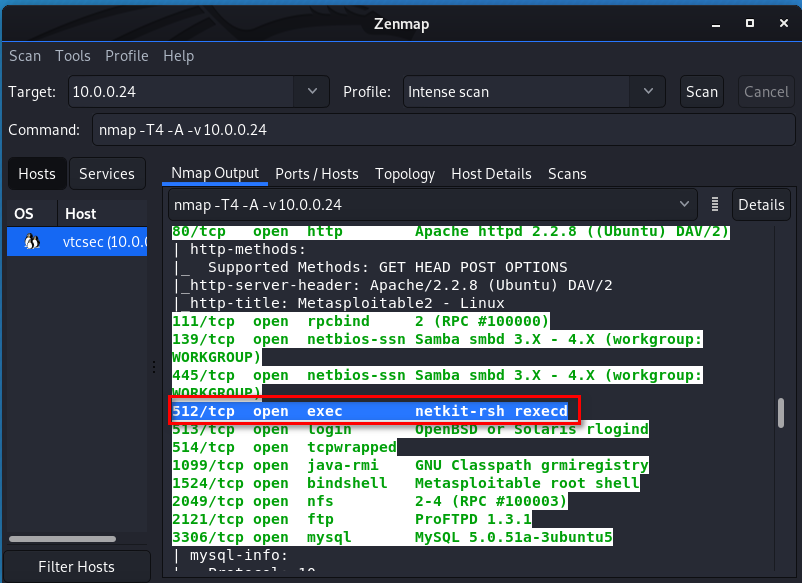
- Services might be mis-configured, such as the "r" service. Ports 512, 513, 514
- Some might even contain a back door!
- Code execution vulnerabilites.
CASE:
Target - Server Metasploitable
Tool - Zenmap on Kali Linux
Start the metasploit server first.(The same network with Kali Linux)
Input the target IP and click start button.
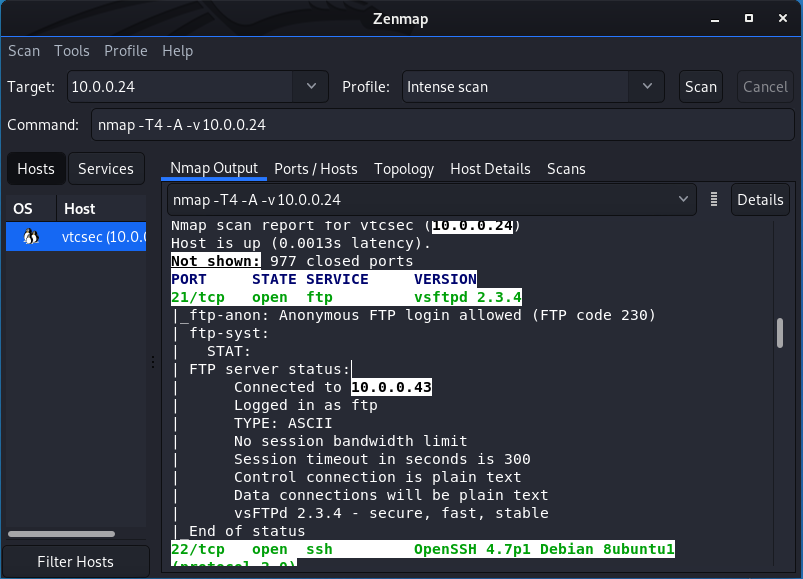
After scan is finished, we need to analyse the scan result.
We find netkit-rsh and google it. It maybe interesting.
Install rsh-client firstly.
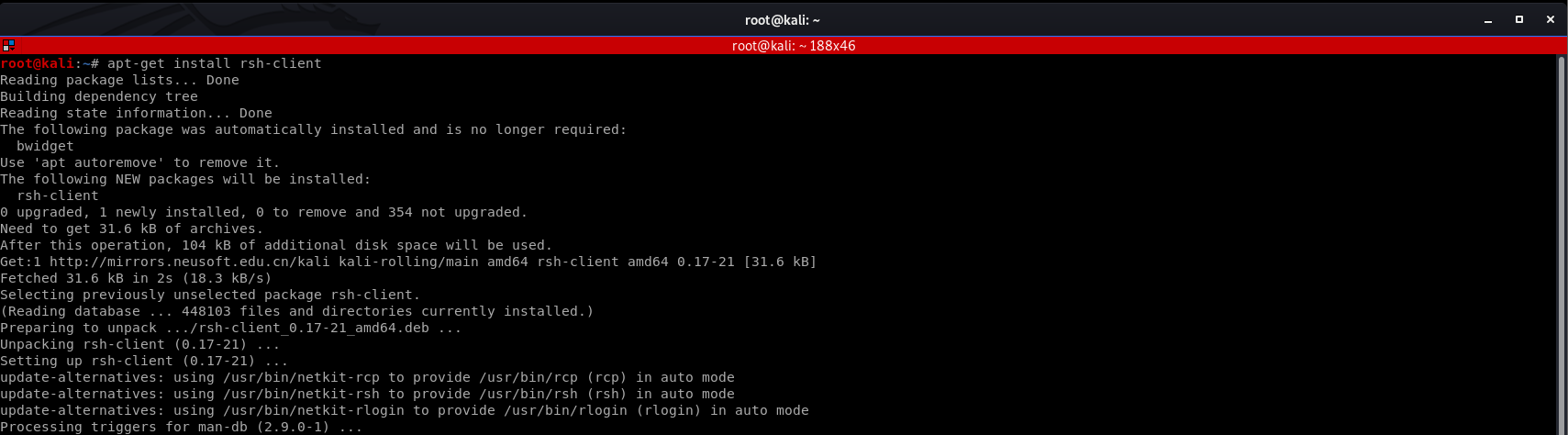
We login the target server with default account - root.
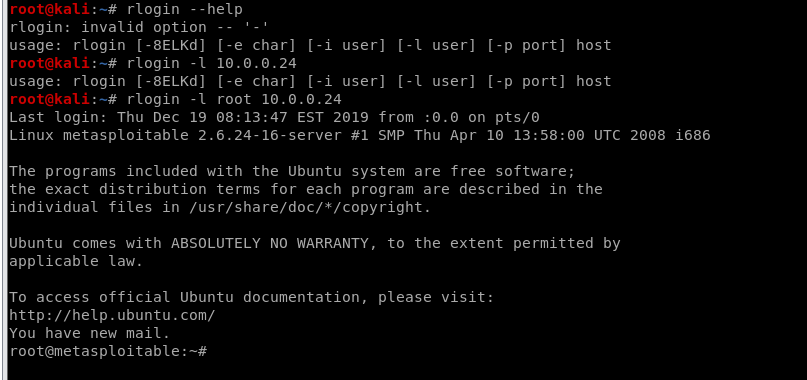
We have the root right now, so can find many useful information about this target server.
Ethical Hacking - GAINING ACCESS(2)的更多相关文章
- Ethical Hacking - GAINING ACCESS(1)
Gaining Access Introduction Everything is a computer Two main approaches (1)Server Side Do not requi ...
- Ethical Hacking - GAINING ACCESS(23)
CLIENT SIDE ATTACK - BeEF Framework Hooking targets using MITMF Tools: MITMF and BeEF Start BeEF and ...
- Ethical Hacking - GAINING ACCESS(6)
Server Side Attack Analysing scan results and exploiting target system. Go to the Analysis page and ...
- Ethical Hacking - GAINING ACCESS(24)
CLIENT SIDE ATTACKS - Detecting Trojan manually or using a sandbox Analyzing trojans Check the prope ...
- Ethical Hacking - GAINING ACCESS(22)
CLIENT SIDE ATTACKS - BeEf Framework Browser Exploitation Framework allowing us to launch a number o ...
- Ethical Hacking - GAINING ACCESS(21)
CLIENT SIDE ATTACKS - Trojan delivery method - using email spoofing Use gathered info to contract ta ...
- Ethical Hacking - GAINING ACCESS(20)
CLIENT SIDE ATTACKS - Spoofing backdoor extension Change the extension of the trojan from exe to a s ...
- Ethical Hacking - GAINING ACCESS(19)
Client-Side Attacks - Social Engineering Tool: The FAT RAT Just like Veil, it generates Undetectable ...
- Ethical Hacking - GAINING ACCESS(18)
CLIENT SIDE ATTACKS Backdooring ANY file Combine backdoor with any file - Generic solution. Users ar ...
- Ethical Hacking - GAINING ACCESS(17)
CLIENT SIDE ATTACKS - Backdooring exe' s Download an executable file first. VEIL - FRAMEWORK A backd ...
随机推荐
- 谈谈java中的并发(一)
一.并发的定义 并发:对于这个概念一直就是没怎么搞懂,就是感觉特别的生疏,(自己从从字面上理解就是多个东西,一起出发),所以就上网上查了一些资料: 同时拥有两个或多个线程,如果程序在单核处理器上运行, ...
- 黑马程序员spring data jpa 2019年第一版本
第一步首先创建一个maven工程,导入对于的pom依赖 <project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xs ...
- Spark HA搭建
正文 下载Spark版本,这版本又要求必须和jdk与hadoop版本对应. http://spark.apache.org/downloads.html tar -zxvf 解压到指定目录,进入con ...
- 入门大数据---Spark_RDD
一.RDD简介 RDD 全称为 Resilient Distributed Datasets,是 Spark 最基本的数据抽象,它是只读的.分区记录的集合,支持并行操作,可以由外部数据集或其他 RDD ...
- vue基础入门(1)
1.vue初体验 1.1.vue简介 1.1.1.vue是什么? Vue (读音 /vjuː/,类似于 view) 是一套用于构建用户界面的渐进式框架,什么叫做渐进式呢?通俗的讲就是一层一层的,一步一 ...
- $.post 参数定义
//重置密码 function ResetPassword(id, accounts) { //alert("重置密码id-" + id + "-" + acc ...
- [SCOI2016]背单词 题解
背单词 https://www.luogu.com.cn/problem/P3294 前言: Trie树的省选题(瑟瑟发抖QAQ) 问题汇总:(请忽略) (1)对Trie字典树的运用不熟练 (2)没想 ...
- Python3笔记002 - 1.2 搭建python开发环境
第1章 认识python 1.2 搭建python开发环境 1.2.1 python开发环境概述 python开发环境常见的操作系统: Windows Mac OS Linux 1.2.2 安装pyt ...
- (私人收藏)[开发必备]最全JQuery离线快速查找手册(可查询可学习,带实例)
[开发必备]最全JQuery离线快速查找手册(可查询可学习,带实例) https://pan.baidu.com/s/16bUd4iA3p0c5RHbzaC60IQe4zh
- 使用 Egg + Vue 的第一个线上小产品——远程工作职位信息收集站点 yuancheng.works
小插曲 开始很纠结,买了一个 yuancheng.works 域名会不会冒犯到 yuancheng.work 站长. 还在群里咨询了 @Phodal 等前辈.重新搞一个新域名,yuancheng.wo ...
